"Alarmware" in Google Play: will not stop an alarm until you install another malicious app
 One of the offensive apps
One of the offensive apps
We have found several alive samples of a new variant of a downloader known as "Stew.B" that we covered a few months ago. But this time they work in a different way, even more annoyingly. They maybe should be called, "alarmware".
How it works
The apps are supposed to be Minecraft or Clash of Clans guides. Even pizza recipes or weigh loss advice. The analyzed app shows some ads and then it just removes the icon from the desktop, so the user is not able to launch it again. Although, in the background, the app installs a service that will launch itself on every reboot.
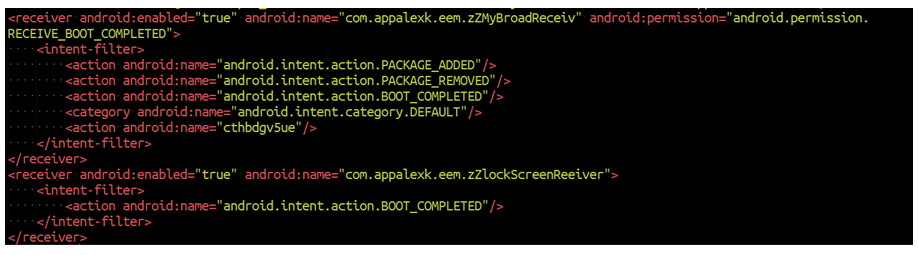 Part of the configuration of the service This service is ready to respond to two events, when the screen locks and unlocks and when an app is installed or uninstalled. The service has a random function to calculate how many
hours or minutes to wait since the first application has been installed until it visits again the attacker's server and gets some instructions. Between them, the URL pointing at a package to be downloaded that could be literally, anything.
Part of the configuration of the service This service is ready to respond to two events, when the screen locks and unlocks and when an app is installed or uninstalled. The service has a random function to calculate how many
hours or minutes to wait since the first application has been installed until it visits again the attacker's server and gets some instructions. Between them, the URL pointing at a package to be downloaded that could be literally, anything.
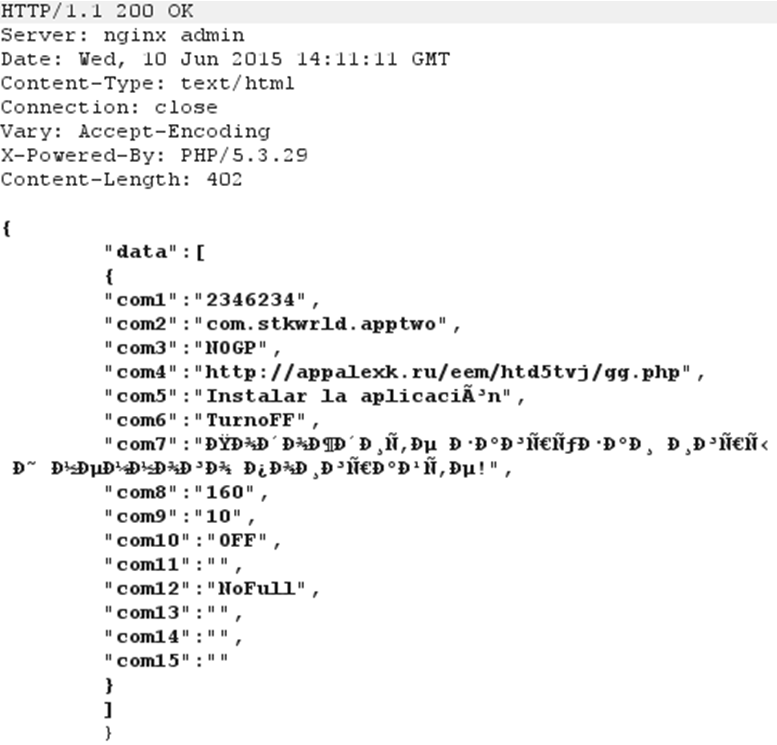 The program requests which new app to download and what message to show
The program requests which new app to download and what message to show
Then this fresh downloaded APK starts and... it will really try hard to be installed. Even if you do not have your phone condivd to install from outside Google Play.
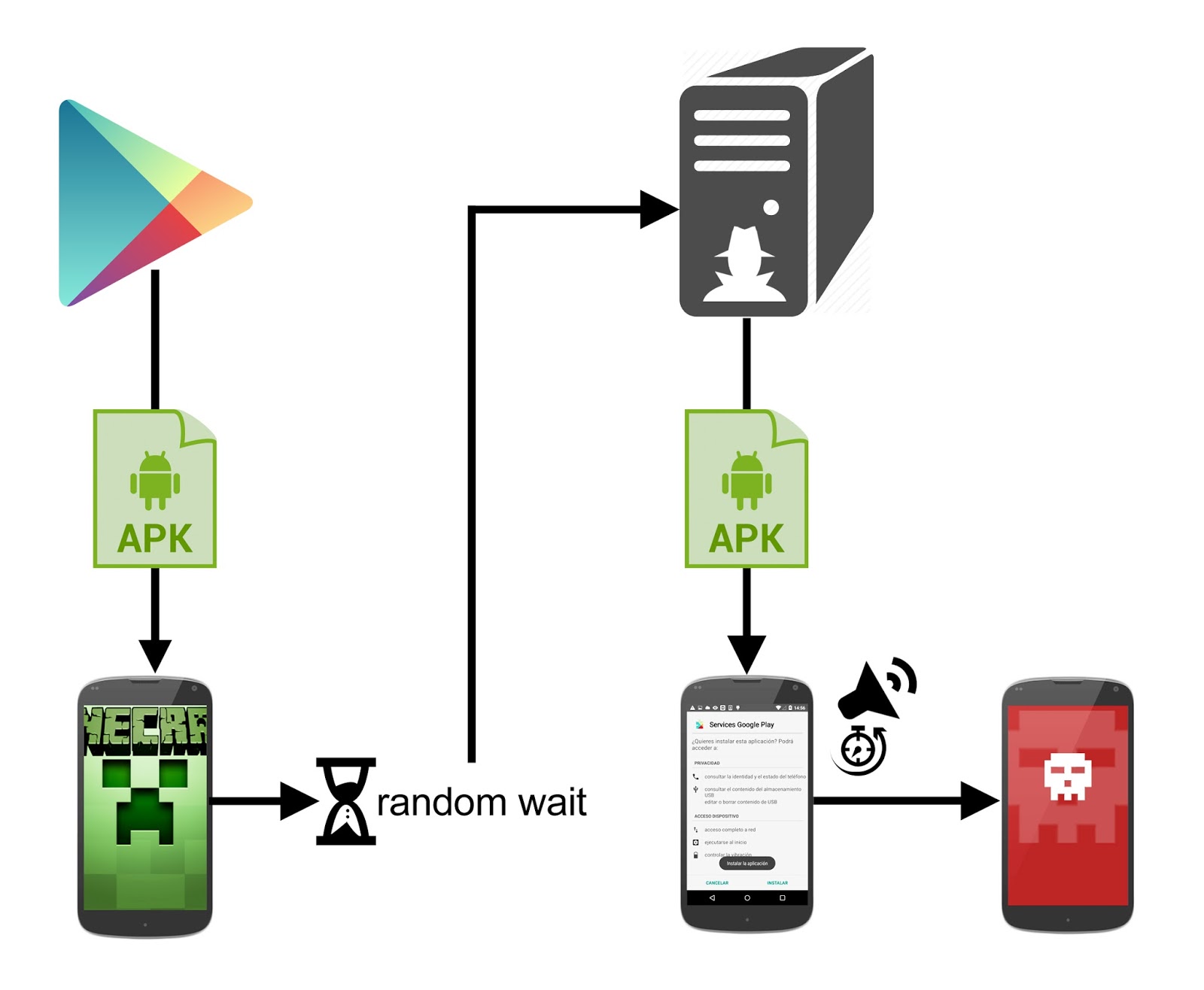 Basic scheme of the malware program Many of the devices will maybe have the security measure enabled: "do not install APKs from untrusted sources" (outside Google Play).
So the just downloaded attacker's program will not be able to be installed and one of these screens will appear again and again.
Basic scheme of the malware program Many of the devices will maybe have the security measure enabled: "do not install APKs from untrusted sources" (outside Google Play).
So the just downloaded attacker's program will not be able to be installed and one of these screens will appear again and again.
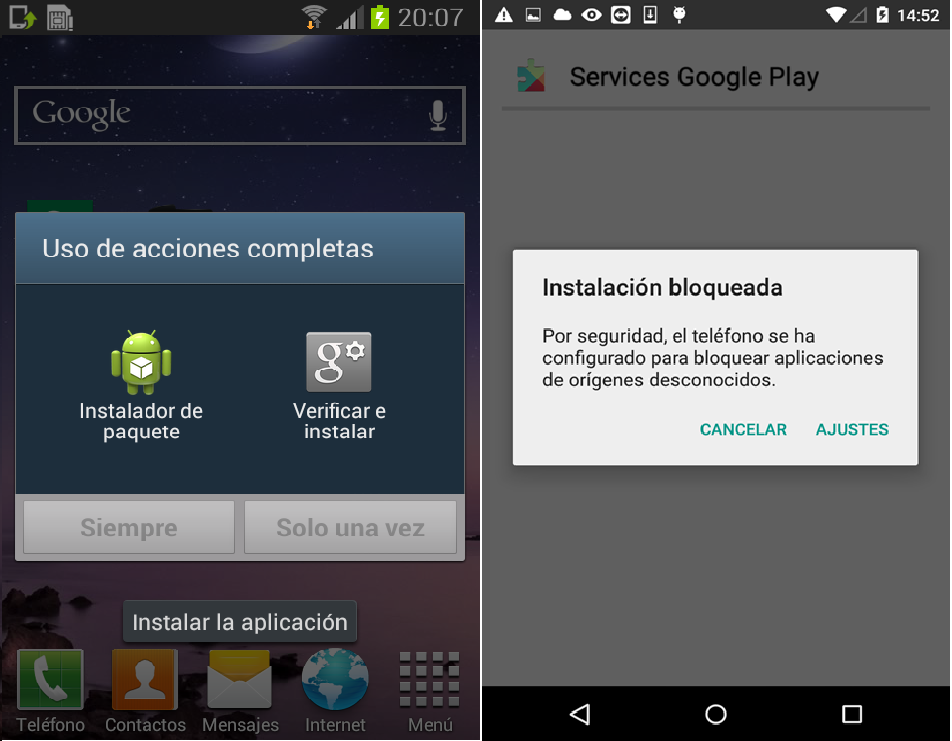 APKs from outside Google Play are not allowed,
APKs from outside Google Play are not allowed,
and the telephone is not condivd to use VerifyApps by default
And, showing these screens again and again, the user experience with the telephone will become quite annoying. Using a trick with a toast component (a special notification text that appears when you are connected to a new Wi-Fi or any other important system message) it will start popping again and again a message and a very annoying sound. Even vibrating. If you cancel or go back, it will start again (sound and message) trying to convince you it is a Google Service update or something like that. This will happen every few seconds. If the user does allow to install APKs from outside Google Play, or it finally condivs it because he can not stand the sound anymore, this screen will appear.
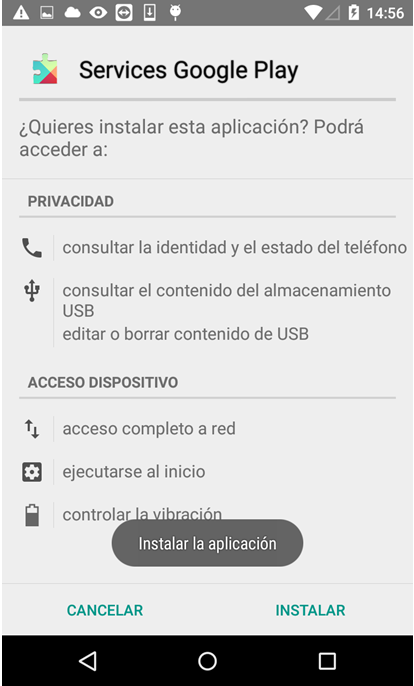 Just before installing the downloaded APK
Just before installing the downloaded APK
The installation toast message and alert will keep on appearing and beeping again and again. Even if the device is silenced. The shown text will be in the browser language (it was taken from the attacker's server). It will be very difficult to use the telephone normally anymore, unless you uninstall the original app (if you can in such a short time with the annoying screen request and sounds). It will continue annoying the user until the downloaded app is installed or the original app from Google Play uninstalled.
If the user finally installs it, the alarm will stop, and there will be "two" Google Service programs... who will dare to uninstall any of them?
 One of the Service Google Play is fake
One of the Service Google Play is fake
Funny enough, the application installed (the fake Google Service program) is just again the same code as the original one, which is weird. It is supposed the attacker is testing, but this could change in any minute. This attacker is from Russia, and used a similar technique back in March, but Google removed them.
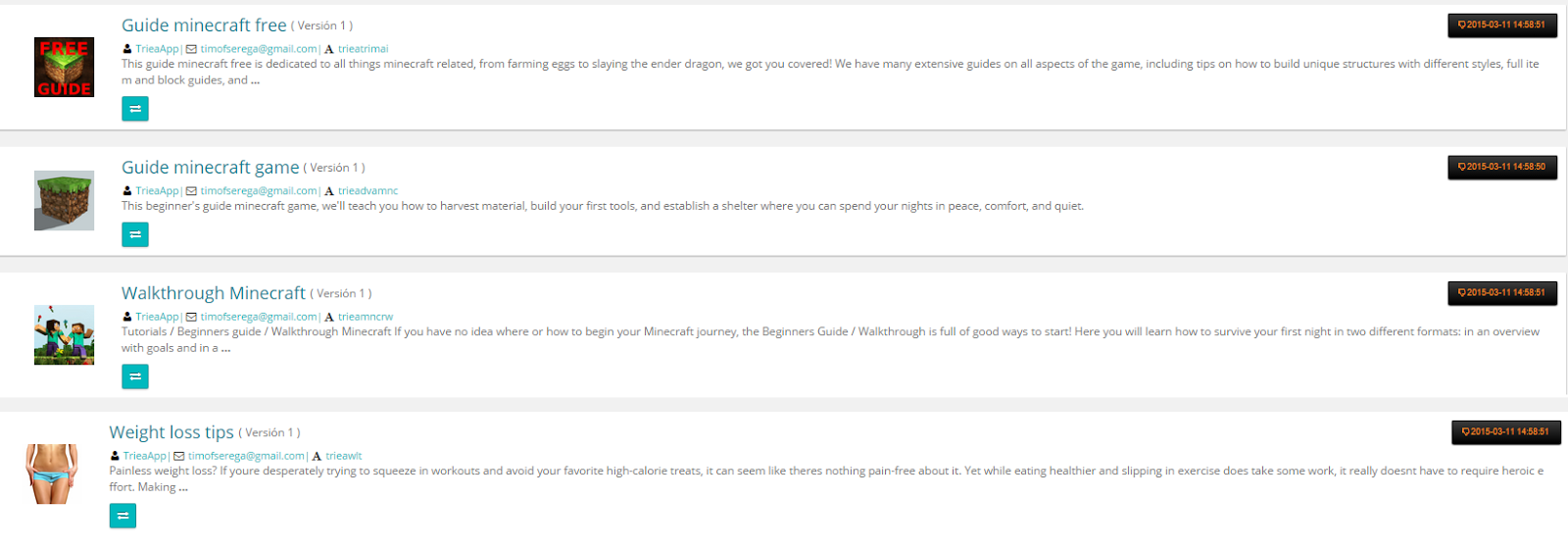 Some apps of the same kind were removed back in March A few weeks ago, the attacker got to upload some other apps again.
Some of them are still online. These are the ones we found thanks to
Tacyt, as we have done before with
JSDialers,
JSSMSers,
Clickers,
Shuabang, etc.
Some apps of the same kind were removed back in March A few weeks ago, the attacker got to upload some other apps again.
Some of them are still online. These are the ones we found thanks to
Tacyt, as we have done before with
JSDialers,
JSSMSers,
Clickers,
Shuabang, etc.
- Guide minecraft game, com.appalexk.mcs, 965559baa77650d9c6249626d33ad14c5210c272
- Guide Minecraft Free, com.appalexk.aam, bde1502855e2d9912937906c1d85bec24b3b6246
- Guide for Clash of Clans, com.appalexk.cofc, 30c4db4033478007a1bdc86a40e37b5cd4053633
- Recipes Pizza, com.appalexk.pizza, a84197a150285f04aee1096e96374255ccf5c2aa
- Гайд для Earn to Die, com.appalexk.dde
 Cloud Híbrida
Cloud Híbrida Ciberseguridad & NaaS
Ciberseguridad & NaaS AI & Data
AI & Data IoT y Conectividad
IoT y Conectividad Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consultoría y Servicios Profesionales
Consultoría y Servicios Profesionales Pequeña y Mediana Empresa
Pequeña y Mediana Empresa Sanidad y Social
Sanidad y Social Industria
Industria Retail
Retail Turismo y Ocio
Turismo y Ocio Transporte y Logística
Transporte y Logística Energía y Utilities
Energía y Utilities Banca y Finanzas
Banca y Finanzas Ciudades Inteligentes
Ciudades Inteligentes Sector Público
Sector Público



