ElevenPaths finds a XSS problem in Play Framework
When Play framework had a problem with the URL parameter. When it parses the view, it translates it to an URL that will work as a GET reques t. If the parameter value starts with ":", some exception is launched and fails to escape the value:
@{Controller.action(URLparameterWithInjection)}
How to get the URL parameter:
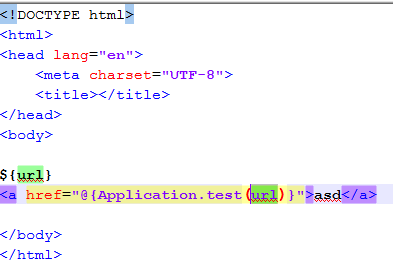 How to get the URL parameter where the XSS may be encoded
How to get the URL parameter where the XSS may be encoded
Then, URL goes through the program. Example of XSS injection encoded:
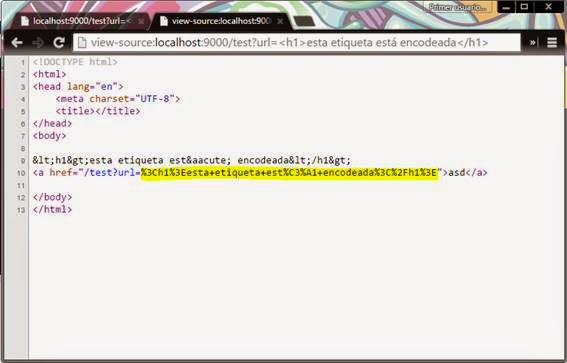 Result of the injected URL, encoded (which is Ok)
Result of the injected URL, encoded (which is Ok)
But once we "inject" the ":" character...
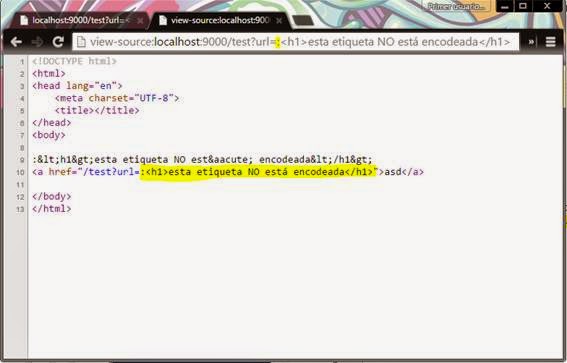 Result of the injected URL, not encoded (which is a problem)
Result of the injected URL, not encoded (which is a problem)
There is a condition that does not allow to encode the injection. In fact, the code in Play Framework made it clear:
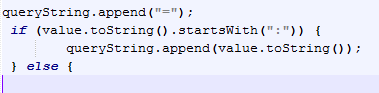 There is an specific condition that does not encode strings beginning with ":"
There is an specific condition that does not encode strings beginning with ":"
Whenever the view is interpreted, when translating to an URL that will work as a GET request, we may use it as a parameter to print it as a result.
We developed a PoC and sent it to developers. Versions 1.2.7 to 1.3.0 have been tested to be vulnerable. Just a week after making them aware of the problem, this alert has been released, that solves the problem: https://www.playframework.com/security/vulnerability/20150506-XssUrlParamerter.
 Cloud Híbrida
Cloud Híbrida Ciberseguridad & NaaS
Ciberseguridad & NaaS AI & Data
AI & Data IoT y Conectividad
IoT y Conectividad Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consultoría y Servicios Profesionales
Consultoría y Servicios Profesionales Pequeña y Mediana Empresa
Pequeña y Mediana Empresa Sanidad y Social
Sanidad y Social Industria
Industria Retail
Retail Turismo y Ocio
Turismo y Ocio Transporte y Logística
Transporte y Logística Energía y Utilities
Energía y Utilities Banca y Finanzas
Banca y Finanzas Deporte
Deporte Ciudades Inteligentes
Ciudades Inteligentes



