Facebook affected by compromise of JavaScript development packages
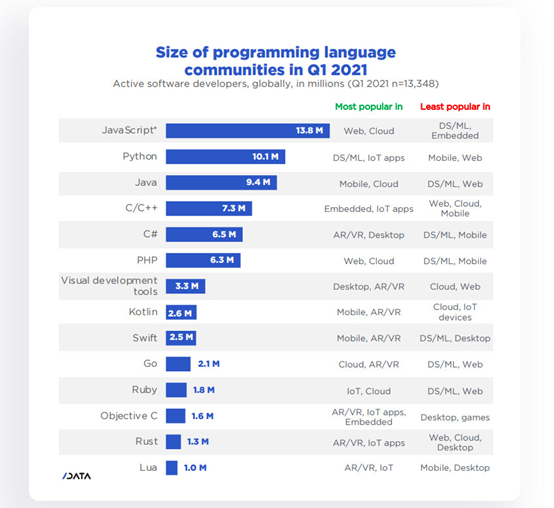
Programming languages such as Python and JavaScript, which in 2021 are competing for the top spot according to programmer ratings, are found in the services that we find on the Internet or on mobile phones and with which we interact every day.
For these developments to work and communities to grow at these rates, it is necessary to abstract the complexity of the languages, which is why most of them have repositories where communities make available packages that simplify development tasks.
For example, in the PyPi library for Python, we made available to the public a package that allows you to use DIARIO from any development done in this language and thus simplify the detection of malware embedded in documents, protecting the privacy of your information.
However, third-party packages have become an attack vector that criminals are taking advantage of more and more every day and which we have been talking about and studying since the end of 2019, allowing us to generate an opensource framework that allows developers to analyse the packages they are going to use from development libraries, called PackageDNA.
Unfortunately, this type of attack is in the news again when one of the compromised packages puts one of the main companies in the technology sector, Facebook, at risk. Recently, one of the packages that this company uses (and many others) in its developments to recognise which operating system is accessing its services from was reported as compromised on its own GitHub.
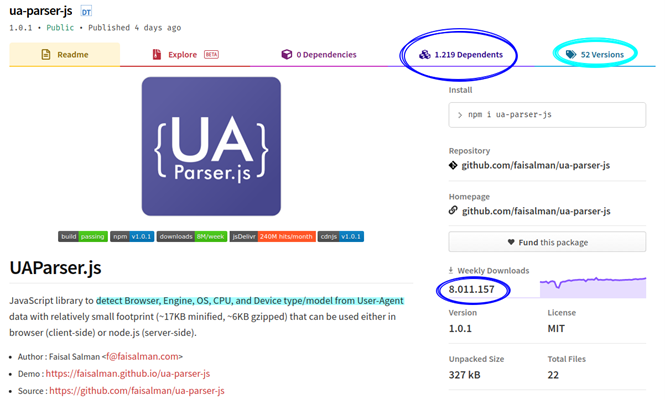
The compromised package is UA-parser-js, one of the most used with just over 8 million downloads in a week and with 1219 packages that use it as a dependency.
As can be seen, the system reports that it has 52 versions. Versions 0.7.29, 0.8.0 and 1.0.0 are given as compromised in the GitHub advisories, but none of these are available in the library anymore.
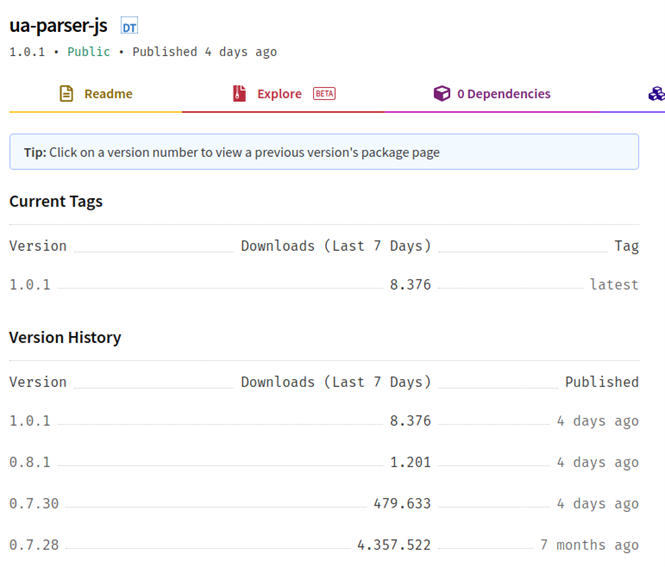 Figure 3: Available versions of ua-parser-js
Figure 3: Available versions of ua-parser-js
When trying to analyse all versions with PackageDNA, we found that the NPMjs library only allows downloading the latest versions.
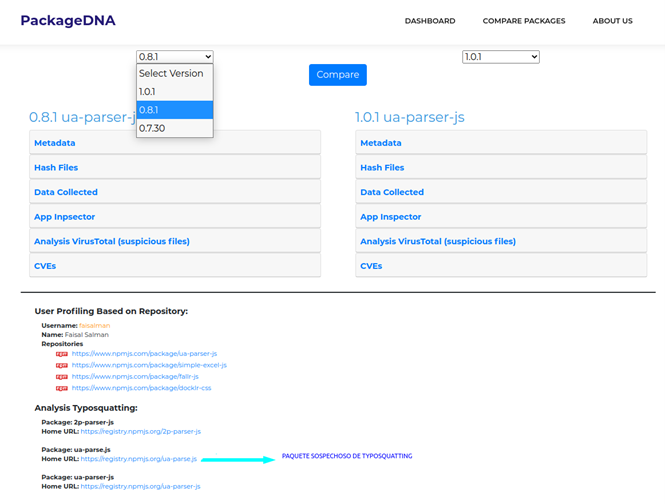 Figure 4: PackageDNA analysed versions of the UA-parser-js package
Figure 4: PackageDNA analysed versions of the UA-parser-js package
In the analysis, a suspicious TypoSquatting library is detected (note the ua-parsers.js, which is not exactly the same as ua-parser-js) and by following the link to the library in question, we can see that it has already been decommissioned.
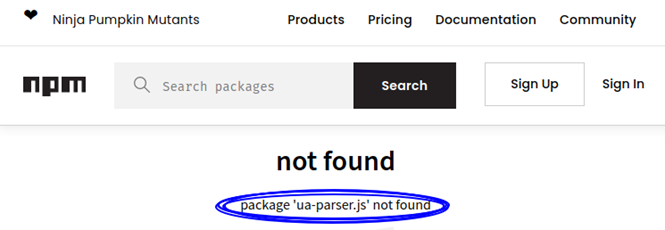 Figure 5: Possible typosquatting package from ua-parser-js
Figure 5: Possible typosquatting package from ua-parser-js
Although this package was decommissioned, it is still possible to download it and scan it as if it were local on PackageDNA, but fortunately it does not contain any malicious reports. The developer is not the same as the original ua-parser-js. His nickname is joenix and he has 172 packages in the NPM library.
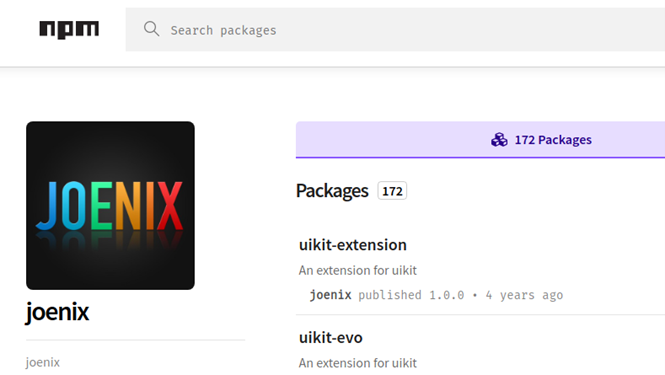 Figure 6: Developer of the possible typo package of ua-parser-js
Figure 6: Developer of the possible typo package of ua-parser-js
Another detection made by PackageDNA is the use of dependencies on an Audio Video Media Codec, which is rated as high in confidentiality risk and critical risk severity.
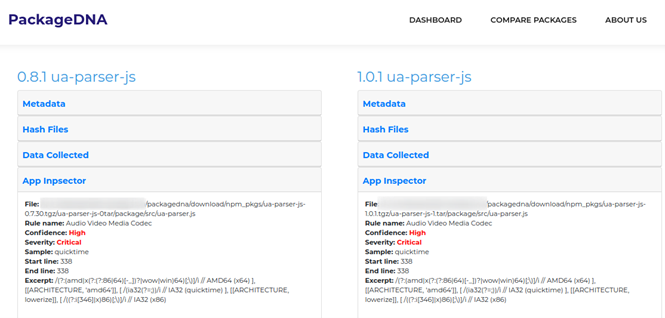 Figure 7: AppInspector detection on UA-parser-js
Figure 7: AppInspector detection on UA-parser-js
This is further evidence of the need to implement code security reviews of the packages required by developments, as they can be compromised at any time and put the services they deploy at risk.
It is becoming increasingly common to find this type of threat and criminals continue to look for loopholes that can be used from the supply chain to affect larger targets or deploy threats that generate profits, as in this case where the compromise inserted a cryptominner into the system..
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector