Nobody on The Internet Knows You Are A Dog, Even If You Use TLS Certificates
You may have noticed that most websites have a little padlock on them. If you click on it, a window will pop up stating that "the connection is secure". Secure? What kind of secure? How secure?
In this article we will put digital certificates on the table and break them down thoroughly to get to the bottom of the issue: what security does TLS provide?
TLS, The Security Protocol Behind Secure HTTPS Websites
A website protected by Transport Layer Security (TLS), the protocol behind the little padlock, offers three security guarantees or services.
- Confidentiality: the communication between your browser and the web server is encrypted, so that if an attacker intercepts the data, they will not be able to find out what it contains.
- Integrity: if an unexpected error occurs in the transmission or an adversary attempts to interfere in the communication, the modification will be detected.
- Authentication: a digital certificate will tell you who is the (supposed) owner of the website you are visiting.
In short, if a page is protected with TLS, you have the (almost) absolute guarantee that nobody except the target web server will be able to see the data you exchange with each other. In other words, confidentiality is guaranteed. The problem that remains unsolved is: who is really behind this server? In other words, who are you sending your encrypted data to?
Nobody on The Internet Knows You Are a Dog
 Illustration by Peter Steiner. The New Yorker, issued on 5 July 1993 (Vol.69 (LXIX) no. 20), page 61.
Illustration by Peter Steiner. The New Yorker, issued on 5 July 1993 (Vol.69 (LXIX) no. 20), page 61.
This joke dates back to 1993 and it couldn't be more relevant today because in 30 years we haven't made much progress! If you are reading this article on the business.blogthinkbig.com website, how do you know it is the actual Telefónica blogthinkbig.com website and not a fake one? You only have one recourse left: click on the little padlock and open the certificate.
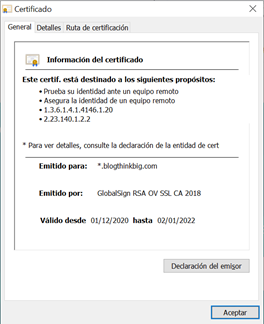
And what do you find? That the certificate has been issued by the company GlobalSign in the name of *.blogthinkbig.com. Are you now reassured about the identity of the owner of the website? Well, this doesn't help much, does it?
But a certificate contains much more information than this initial summary. Select the Details tab and you will see a whole host of fields. In particular, the Subject field reveals that, in this example, the company behind *.blogthinkbig.com is Telefonica SA.
But do not think that all certificates provide this information: some provide less, they do not reveal the entity behind the website; others provide more. Let's break them down so you understand what each field represents.
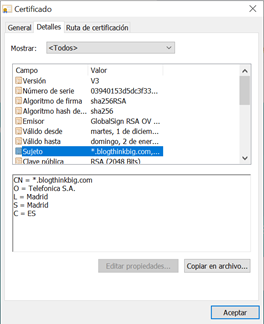
Breaking Down a TLS Certificate
Digital certificates are electronic documents that guarantee (to a certain extent) the identity of a natural or legal person and that this person possesses a certain public key. A trusted third party, called the Certification Authority (CA), is in charge of validating this identity and issuing the certificates linking identity and public key. A TLS certificate contains the following information:
- Version of the X509 standard, version 3 is currently used.
- Serial number used by the certification authority. Now required to be random, non-sequential, with a minimum entropy of 20 bits.
- Algorithm identifier, which must be the same as the "Certificate Signing Algorithm", described below. It is placed in this position to be protected by the signature.
- Identification of the certification authority, through a unique Distinguished Name (DN):
- CN – CommonName
- L – LocalityName
- ST – StateOrProvinceName
- O – OrganizationName
- OU – OrganizationalUnitName
- C – CountryName
- The period of validity of the certificate: from when until when it is valid.
- The unique distinguished name of the certificate holder. This can be a natural or legal person. The authority verifies this identity more or less reliably, as will be shown below.
- Holder's public key information, specified by:
- Algorithm
- Ley size
- Exponent
- Module
- Extensions (optional): These were introduced in version 3 to make the previous rigid structure more flexible. A CA can use extensions to issue a certificate only for a specific purpose, e.g., only for web servers. Extensions can be "critical" or "non-critical". Non-critical extensions can be ignored, while critical extensions must be applied and a certificate will be rejected if the system does not recognise a critical extension.
- Certificate signing algorithm. There are multitude of secure algorithms in use: RSA, DSA, ECC, etc.
- Certificate signature: the value of the signature. For those experts in cryptography, this value corresponds to the result of encrypting the hash of the certificate's information with the CA's private key. This signature makes it possible to verify that the public key appearing in the certificate actually belongs to the certificate holder, because this is certified by the certification authority.
In short, a digital certificate is a guarantee from an authority that a public key belongs to a given person (natural or legal). How much can you trust their word? Let's see.
Not All Certificates Were Created with The Same Level of Trust
The main task of a certificate authority is to validate the identity of the entity requesting a certificate. And not all certificates offer the same degree of trust in the identity of the certificate holder, because the validation process can vary greatly from one type of certificate to another.
There are three levels of validation for websites:
- Domain Validation: Domain Validation (DV) certificates represent the lowest level of validation, as the CA only verifies that the certificate holder owns the domain for which the certificate is requested and that the domain is registered in Whois. Domain ownership is typically verified through a confirmation email sent to an address in that domain. If the recipient follows the link in the email, the certificate is issued. The issuance of DV certificates is fully automated and can be very fast. The duration depends mostly on how quickly the confirmation email is responded to. They do not include the name of the entity holding the domain, only the domain name. For example, Let's Encrypt certificates belong to this category. What guarantees do they provide about the identity of the domain holder? None! A website with a DV certificate is secure in the sense of protecting confidentiality, but it does not guarantee the identity of the site at all. You know that your data is encrypted, but you have no idea who you are sending it to. They are ideal for websites for individuals, SMEs, blogs, forums, with no intention of offering paid services and without dealing with personal data.
- Organisation validation: Validated organisation certificates (OV) require verification of the identity of the domain holder. The practices for validating the identity of the applicant vary drastically from one certification authority to another, with great inconsistency and diversity of guarantees, although all require the submission of some official document to verify the domain, VAT number, telephone number, physical address and some other requirement. The process can take from one to three working days. The name of the organisation is included in the content of the certificate. These certificates are suitable for institutions and companies that want a strong Internet presence, but do not offer transactional services via the web.
- Extended Validation: Extended Validation (EV) certificates offer the highest degree of trust. They also require verification of identity and authenticity, but with very strict requirements. They were introduced to solve the inconsistency of OV certificates. They require even more documentation than OV certificates to reliably verify the applicant's identity and business operations. They also include on the certificate the name of the organisation to which it has been issued and even the organisation is visible when clicking on the small padlock, without the need to dig into the details of the certificate, making it easier for visitors on your website to verify your identity. It is best suited for websites that offer services involving financial transactions. It is typically used by banks, large organisations and reputable online shops. Due to the controls in place, it usually takes 5 to 15 days to obtain an EV certificate.
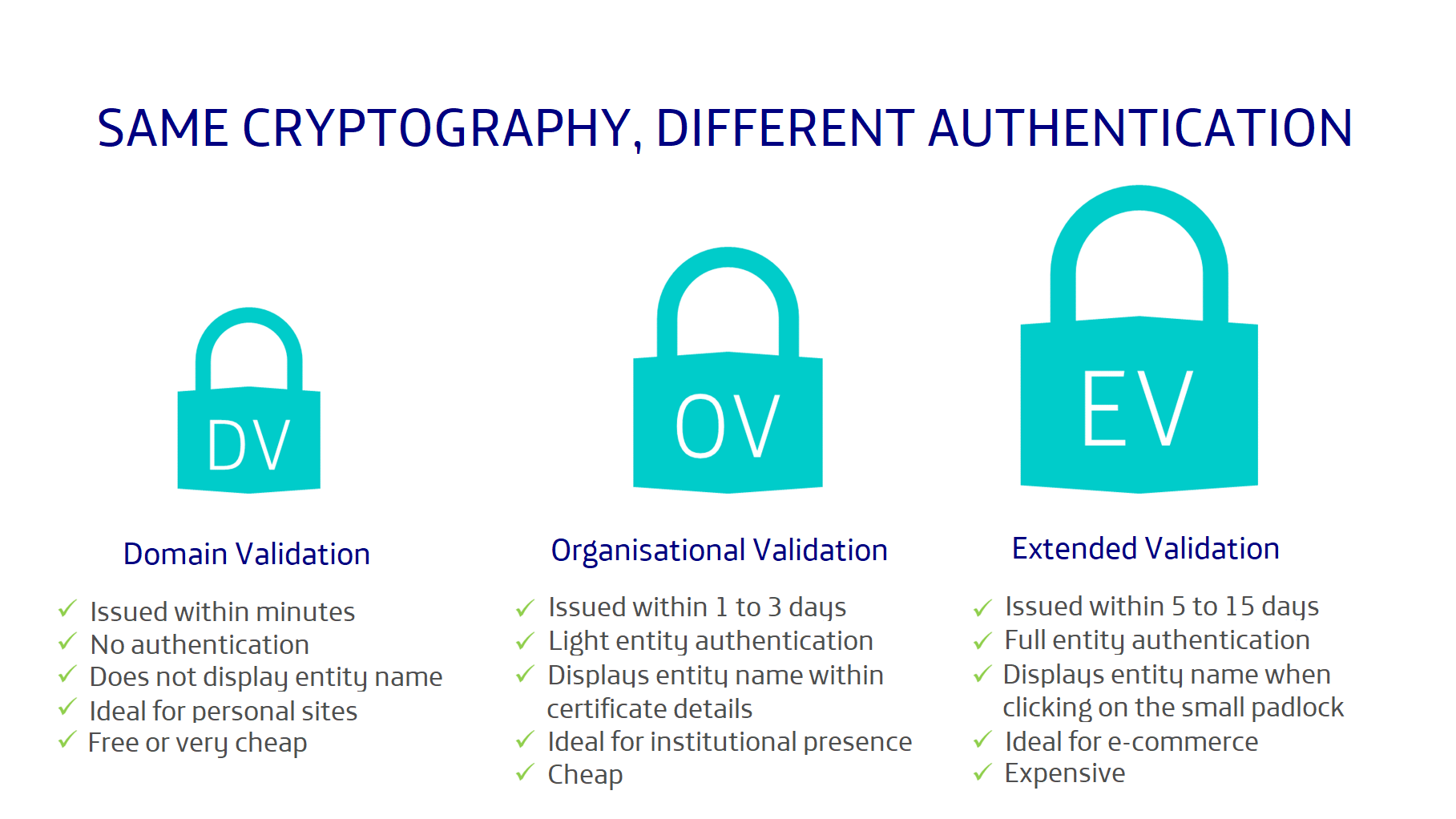
It is important to note that they all offer the same cryptographic strength: 256 bits of symmetric encryption and 2,048 bits of public key encryption. The difference between them does not lie in the cryptography, which is identical for all of them, but in the validation processes, which are more or less strict and which offer more or less guarantees about the identity of the person (natural or legal) behind a website.
Cryptography Works Wonderfully, it is the Processes That Fail
In short, for a public key infrastructure (PKI) to work, certificate authorities must do a good job, among other critical tasks, verifying the identity of certificate applicants. If this validation is not executed correctly, cryptography only works to ensure confidentiality: the data communicated between the web server and your browser travels encrypted, yes, no attacker can get hold of it, but who are you sending it to, who are you receiving it from.
This question can only be answered by the information in the website's certificate. And here, unfortunately, mathematics has little to add as it is the ACs' mission. This is why incidents such as the recent one with Camerfirma occur: Google questioned the good practices of this certification authority. It is not cryptography that is being questioned, but identity validation processes.
In the end, cyber security is a balanced combination of technology, processes and people. In cryptography you can trust, but in the rest...
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector



