Technically analysing a SIEM… are your logs secure?
In one of our webinars a while ago #11PathsTalks, @holesec and @DaPriMar spoke to us about what a SIEM is and also advanced correlation. We will analyze the different issues which can influence a SIEM's security in a positive or negative way, but in this case we base it upon Splunk. As with any SIEM, it allows us to search for, monitor and analyze information generated by different equipment within the infrastructure, in this case through a web interface. This software captures, indexes and correlates information in real time in a repository which allows us to generate graphics, reports, alerts and different visualisations. According to their website, it has more than 3700 clients, including more than half of the Fortune 100. The three most utilized versions of Splunk are: Splunk Free, Splunk Enterprise and Splunk Cloud. Also there is a light version which is mainly utilized for AWS, however we will not discuss this now.
Although it is possible to analyze a SIEM from multiple possible attack vectors, for this first particular approximation we would like to focus upon these four key points:
- Authentication methods
- User installation
- Application Installation and Administration
- Internet Exposure
Splunk Enterprise possesses various authentication method options to choose from (Splunk, LDAP, Scripted, SAML, ProxySS) which condiv within the file:
$SPLUNK_HOME/etc/system/local/authentication.conf.
Splunk’s own authentication (an authentication method selected by default) is neither adequate for corporate environments since the only parameter that the password can be set to is the length, and by default it is set to 0. Splunk does not allow you to set up a blocking rule for failed access attempts, thus it is acceptable to strong attacks; neither does it enforce rules which guarantee password complexity. The user by default is the admin of their corresponding password ‘changeme’.
Splunk Cloud comes from two different versions, Managed Splunk Cloud and Self-Service Splunk Cloud. In order to differentiate one from the other you can analyze the URL. The URLs from the Self-Service are in this format: https://prd-*.cloud.splunk.com and the URLs from Managed are in this format https://*.splunkcloud.com. In Splunk Self-Service the users can authenticate themselves with their splunk.com account which has long and complex password restrictions. In Splunk Managed the users can authenticate themselves through SAML, although they normally utilize Splunk’s own authentication, since it comes with it by default. Although, it has a length of eight characters set, it is still the only parameter used.
It is important to take into account that by configuring Splunk, in order to utilize another authentication method which is not its own authentication (for example LDAP), all of the local user’s accounts with Splunk’s own authentication will continue to be active (including the admin account). In order to eliminate all of the local accounts you must leave the file $SPLUNK_HOME/etc/passwd blank. This file should not be deleted, since otherwise, it will be returned to the user by the admin with the password ‘changeme’.
In Splunk Cloud you do not have access to administrate Splunk from the CLI nor by the system file to modify the file settings. You can utilize Splunk Web and the REST API in order to carry out some administrative tasks. Neither can you install any application, but only those which are approved by Splunk in order to be used in the cloud environment. Before the applications are approved, they go through a validation process by the tool AppInspect which determines if it complies with the requirements of the defined security, for example: it does not require privilege increases with sudo, su, groupadd or useradd, it does not use reverse shells, it does not manipulate files outside of the application’s directory and it does not manipulate processes outside of the application’s control nor the operating system nor reset the server.
[dirección ip="" n=""]:[puerto]/en-US/account/login?return_to=%2Fen-US%2F[/puerto][/dirección]
- "isFree":true it indicates to us that it deals with a Free Splunk Version (without authentication)
- "instance_type":"cloud" it indicates to us that it deals with a Cloud Splunk Version
- "instance_type":"download" and "product_type":"enterprise" it indicates to use that it deals with a Splunk Enterprise Version
- "hasLoggedIn":false it indicates to us that no user started the session in the system, which is a clear indicator that this Splunk still maintains the default password since nobody could start the session to change it.
$SPLUNK_HOME/etc/auth/splunk.secret
Which is unique for each Splunk installation. The applications which are downloaded from Splunkbase (for example the add-on which allows its integration with the Active Directory, or which allows them to integrate Splunk with communication depositories) they need to store the credentials in the file settings from its own application. Splunk decrypts these passwords by using splunk.secret. The risk in this case, is that once the Splunk server is compromised, you can use the same Splunk API to decrypt the password from these applications with a simple Python script and thus it can compromise other components of the infrastructure.
- To utilize a non-privileged user (not the root nor the administrator) for the installation
- To modify the default passwords as soon as they are installed
- To select a robust and secure authentication method which does not exist in simple forms to conceal it (as we saw in the Splunk case which needed to erase the file $SPLUNK_HOME/etc/passwd)
- To utilize certificates on the web interface, which are preferably not auto generated
- To disable the web component if you do not use it
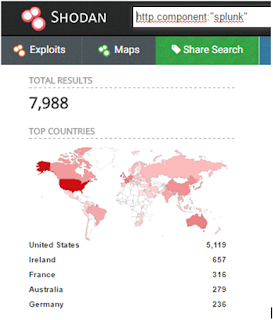
- Do not expose the SIEM ports to untrustworthy networks
- To update the SIEM regularly, and to incorporate it into the the audit scope or intrusion test, which are carried out periodically
- To activate SIEMs own audit and monitor the resulting events
Finally, given that we have spoken about Splunk throughout our analysis, we can continue to explore this with the following links from the vendor, which shows the best practices to utilise in order to protect these systems.
- Best practices in protecting splunk enterprise
- Community: Deploy Hardened Splunk
- Documentation Splunk latest security hardeningstandards
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector