Analysis of an intrusion on the Aristeo platform as a demo of Its predictive capabilities
While some people were still sending out New Year’s wishes, one of Aristeo’s decoys was compromised by an unknown attacker in late January. In this post, we’ll walk through a brief analysis of that intrusion as an illustration of Aristeo’s capabilities and its ability to deliver valuable predictive intelligence to our clients.
This is not a technical deep dive into a specific threat, actor, or APT group. Rather, it’s a snapshot of what Aristeo can do to detect actors and threats that had previously flown under the radar.
If you’re not familiar with Aristeo, here’s a quick overview:
- Aristeo is a predictive intelligence platform purpose-built to combat industrial cyber threats. The industrial landscape today blends OT, IT, and IoT components, so any effective solution needs to natively understand and interpret data tied to those domains.
- Aristeo generates intelligence by deploying a network of honeypot sensors built with real industrial hardware. These sensors bait and capture real-world industrial cyber threats, learning from them and identifying those that pose the greatest potential risk.
- Using actual industrial hardware ensures authentic and contextual threats. And since the system is exposed 24/7 to global attack surfaces, the data remains both timely and highly reliable.
- The honeypot concept is like a Petri dish used to culture viruses and bacteria, studying threats in a controlled setting so we can build better detection tools, vaccines, treatments, and mitigation strategies.
 Aristeo threat dashboard.
Aristeo threat dashboard.
1. Background
It was a cold January morning when the Aristeo alert system flagged an issue. A subsystem inside one of our honeypots had gone down.
We jumped on it immediately—was it a system glitch? An unexpected update? Did someone kick a cable loose?
Nope. What actually happened was that someone had broken into the engineering bay of one of the Aristeo decoys and gone a bit too far, severing the connection and effectively cutting the incident short.
That kind of network cutoff ensures the attacker can’t pivot or escalate beyond the honeypot. Nothing in Aristeo’s infrastructure can be weaponized for third-party attacks.
2. Post-mortem
With the alert triggered, the real analysis began.
On Aristeo’s end, we had logs showing multiple successful RDP logins to the engineering bay over several days. But when we checked the logs on the bay itself, nothing. Clean. The first inference: the attacker wiped the system logs to cover their tracks.
We knew right away that this wasn’t some rookie. Our RDP service is hardened and patched, and the password is no joke—20 characters, not dictionary-based. Connections are encrypted using CredSSP over TLS 1.2 (preferably), leveraging elliptic curve cryptography.
2.1 How did this happen?
As mentioned, Aristeo detected successful access attempts, but once we checked the actual machine, no trace. Nothing in the event logs. The breach might as well not have happened. Except… there was a folder sitting in the Recycle Bin. Inside was KPortScan, a well-known port scanner among cybercriminals.
The folder, as seen in the screenshot below, also contained two text files: one in French, listing potential targets, and another named "results" showing the IPs the attacker scanned on January 27th. There were also a handful of Qt libraries (a dev framework), which aren’t malicious in themselves or necessarily indicative of a threat.
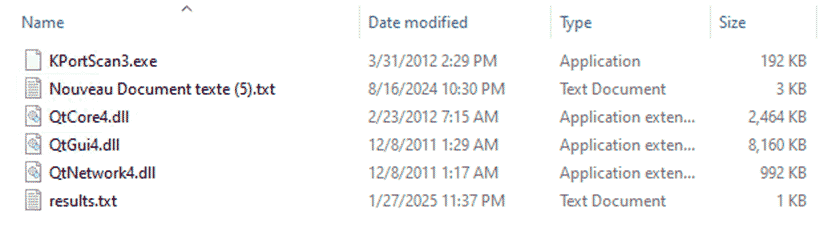
Note the French-named file. Smart enough to scrub logs, sloppy enough to leave tools in the trash?
Also worth asking: what other tools did the attacker download?
None. No evidence of any typical hacking or audit tools. But they installed a common piece of software: Anydesk. It’s a legit remote access tool widely used by companies for IT support. Nobody blinks when it shows up on a device—could even be preinstalled on machines in offices or industrial plants.
The problem? That’s all we had. No logs. No timestamps. No IPs. No usernames.
We were stuck.
2.2 Aristeo, we need you
At this point, a typical analyst would hit a wall. But once you put on Aristeo goggles, the picture changes.
First, we checked whether the IPs that successfully accessed the machine (coming from Morocco) had any history with Aristeo or other major threat intel platforms. Nothing. Clean IPs.
Then we tapped deeper into Aristeo’s intelligence and found related IPs showing activity a month before the intrusion. Not enough to brute-force anything, but there was coordinated probing. Here's a sample table of what we saw.
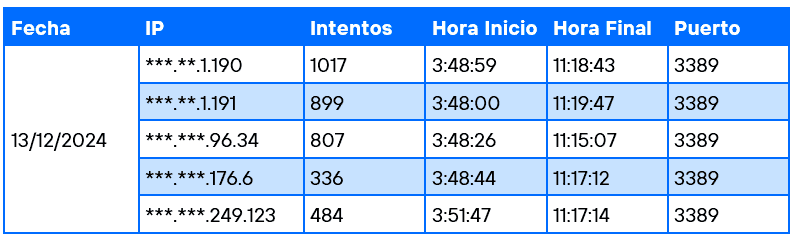 IP addresses have been partially redacted to comply with EU data protection laws.
IP addresses have been partially redacted to comply with EU data protection laws.
We also built a timeline showing key interactions with the decoy leading up to and following the successful intrusions.
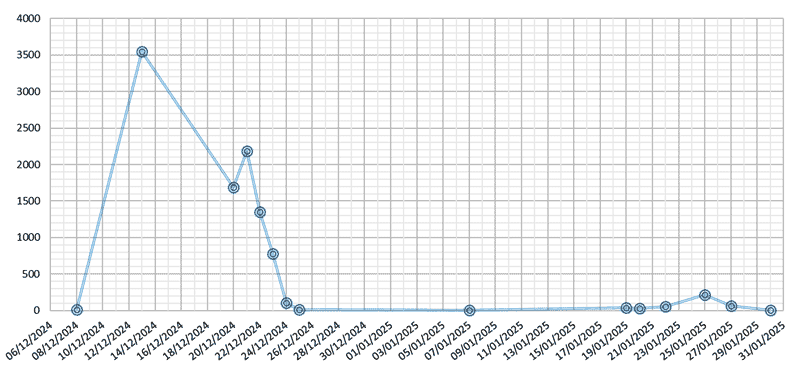 Timeline of related activity
Timeline of related activity
You can see there wasn’t nearly enough traffic to brute-force the password. Public estimates suggest it would take 7 quadrillion years to crack it that way.
But Aristeo was able to trace successful access attempts that weren’t in the host logs. When we pulled all the threads together, a picture started to form. It looked like we were dealing with two different actors—which would explain the odd switch between surgical precision one day and amateur missteps the next.
- One actor compromised the machine. We’re keeping the how to ourselves, but once they had access, they installed Anydesk to maintain persistence in case they lost the RDP session. Thanks to Aristeo—since local logs were spotless—we found clear traces of direct connections via Anydesk after the initial breach.
- A second actor most likely bought access to a bundle of pre-compromised machines. That French-language document with targets? Likely part of the package. These don’t seem to be high-profile or public targets, just previous victims of actor one (or someone else).
But second actor never launched their plan. They tried scanning 621 IPs from a UK ISP—at which point their connection dropped. From their perspective, the internet just vanished. And with it, their access to our machine.
2.3 So... now what?
Now comes the learning phase. We need to assess whether Aristeo or its honeypot network can be improved. We're happy with its performance, but there’s always room to push further.
As for the intelligence generated, client protection kicked in immediately. As soon as the incident occurred, we passed the data in real time to our DOC (Digital Operations Center) to reinforce defensive postures across the board.
3. Appendix: IoC
3.1 Files Recovered from the System

______
AUTHORS
GABRIEL ÁLVAREZ
Head of OT Innovation
SERGIO VIDAL
OT Innovation Specialist
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector