Cyber Security challenges and solutions for IoT medical devices
The healthcare sector is immersed in an unstoppable process of adoption of medical IoMT devices (Internet of Medical Things) driven by the undoubted benefits they provide in terms of productivity, innovation, and improved service to patients.
However, like with any new technology, its emergence comes with some challenges that must be addressed for its successful adoption. In this sense, this growing number of connected devices entails an increase in the number and diversity of the organisation's points of exposure, increasing what is often referred to as the "attack surface".
Some reports point to continued growth of almost 20% per year in the number of IoMT devices in hospitals in the first half of the current decade. Source: Juniper Research.
This requires enabling mechanisms to identify these devices, know their potential vulnerabilities, continuously assess the risk of their possible exploitation, and implement the necessary measures to keep the level of risk at reasonable levels.
Specific challenges in the health sector
A common problem in the healthcare sector, which is also replicated in organisations in other sectors, is the lack of complete visibility of devices connected to networks; a problem that is exacerbated in the case of IoTM devices, which are more heterogeneous than traditional IT systems.
The organic and inorganic growth of these organisations, such as the addition of new healthcare facilities and healthcare units or mergers and acquisitions, results in a heterogeneous and constantly changing network and systems infrastructure, making it difficult to define and implement consistent governance models and security controls across the organisation.
In addition, the uninterrupted availability of their systems and technologies is of vital importance to healthcare organisations, both because of the nature of their business and the need to provide a quality service and protect their reputation.
The project: definition of the architecture, implementation, and operation
In order to meet the usual requirements in projects of this type, different monitoring technologies specialised in healthcare environments are available. One of them is Medigate by Claroty.
This technology takes as input a passive copy of the traffic and is able to identify the devices, their communication relationships with other equipment in the network and their potential vulnerabilities.
To deploy this type of technology, it is necessary to implement a probe in each hospital (Medigate Collection Service) that communicates with the MAS (Medigate Analysis Server), a Cloud platform that provides centralised management of the deployment.
In order to get the most out of the technology, integrations with other systems must also be carried out for two main purposes:
- Feed the monitoring solution with information from other network services to complement its deep packet inspection (DPI) capability. This is the case of network management systems (SNMP), active directory (AD) or asset repositories (CMDB).
- Feed other Cybersecurity solutions with the information that the monitoring solution is able to provide. This makes it possible to obtain greater performance from other cyber security solutions, allowing the application of more granular segmentation and filtering rules (FW, EDR) or access control (NAC) thanks to the greater capacity for device identification and recognition provided by the technology.
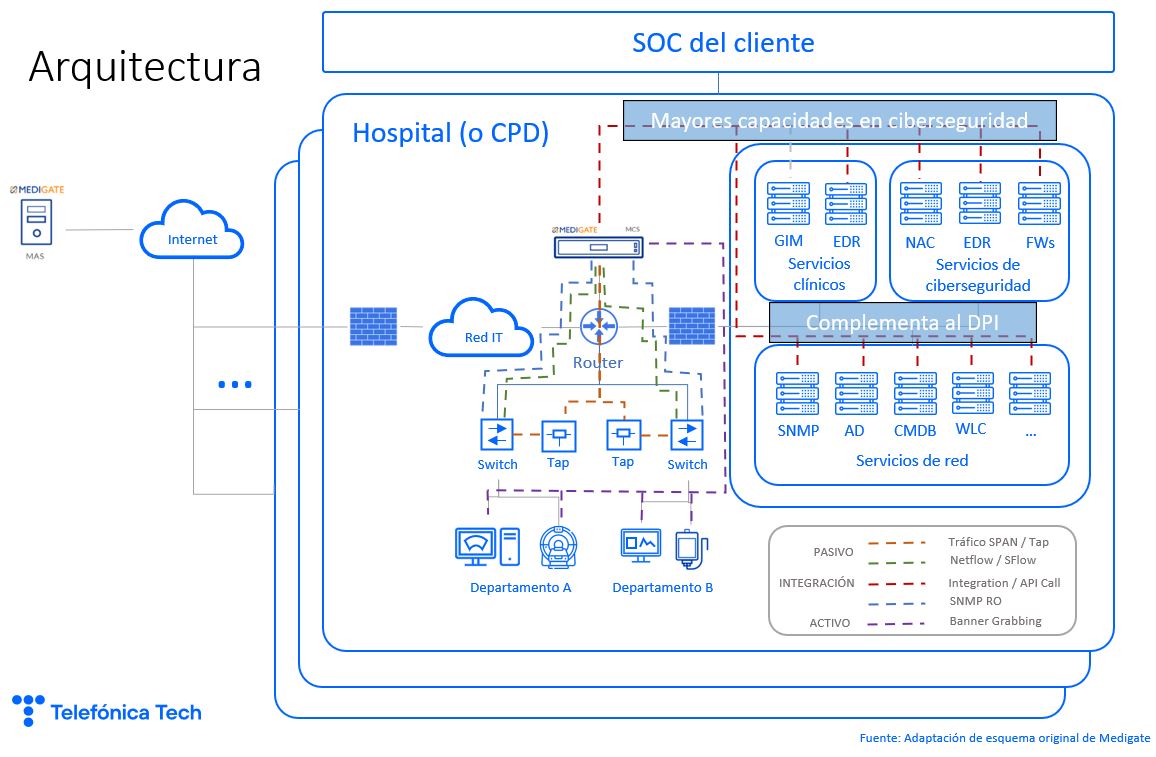
Once the deployment architecture and the necessary integrations have been defined, the equipment is deployed and configured in each of the healthcare centres involved in the project.
After the deployment, configuration and integration phase, an exploitation phase begins, which is a key activity in these projects to make the investment in technologies profitable, as it allows to continue obtaining value from their use. In fact, it is from this point onwards that activities with a significant impact on the cybersecurity posture begin to be carried out:
- Risk management: taking as a starting point information about each device, its vulnerabilities and its communications, an assessment is made of the level of risk in the initial circumstances and its potential reduction through the implementation of some countermeasures or remediation actions such as those described below.
- Supporting network segmentation to limit the exposure of devices: this is a basic measure but requires an analysis of the organisation's network segments (VLANs) and their proper management.
- Definition of network policies: In order to reduce the attack surface at the network level on medical devices, network policies are applied on communication flows, protocols and ports customised for the organisation. While the technology provides policies based on manufacturer's guidelines, these do not consider pre-existing communications characteristics and must be customised.
- Alert management: like any monitoring solution, it generates alerts which, in the case of healthcare environments, can be classified into two groups: specific alerts for medical environments (e.g., unencrypted patient data) and general alerts (e.g., communications with malicious IPs). Procedures in the form of playbooks have been and continue to be defined in order to automate the handling of alerts.
- Vulnerability remediation: some of the vulnerabilities trigger actions in the form of targeted projects to eliminate them or to mitigate the risk they pose. Examples are moving critical equipment to a specific network segment, studying SMBv1 communications per hospital, or addressing vulnerabilities per manufacturer to find a remediation mechanism.
Conclusion
The implementation of security monitoring solutions in healthcare environments responds to the demands and challenges associated with the construction of a better-quality healthcare model, focused on the patient.
In this regard, Telefónica Tech's Cyber Security products and services, such as those described in this article, are key to tackling Cyber Security risks and increasing the resilience of healthcare infrastructures.
AUTHORS
VICENTE SEGURA,
OT & IoT Cyber Security Product Manager
&
MIGUEL GARCÍA PARRONDO
OT consultant
***
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector.jpg)




