NIS2 Directive (III): Main obligations, security measures and key requirements
In response to the rise in cyber threats and increasing digital dependency, the NIS2 Directive sets out its guidelines to enhance the cybersecurity of critical infrastructures, while also ensuring supply chain cyber resilience and governance. Who is required to comply with the directive? What provisions must be followed?
It is important to note that the NIS2 guidelines cover a wide range of entities deemed either "essential" or "important". These entities may have fewer than 10 employees or more, and an annual turnover or balance sheet below or above 43 million euros, and must meet the established requirements.
However, entities considered relevant to national security or economic stability—regardless of their size—may also be designated as subject to NIS2 obligations.
Entity classification and levels of supervision
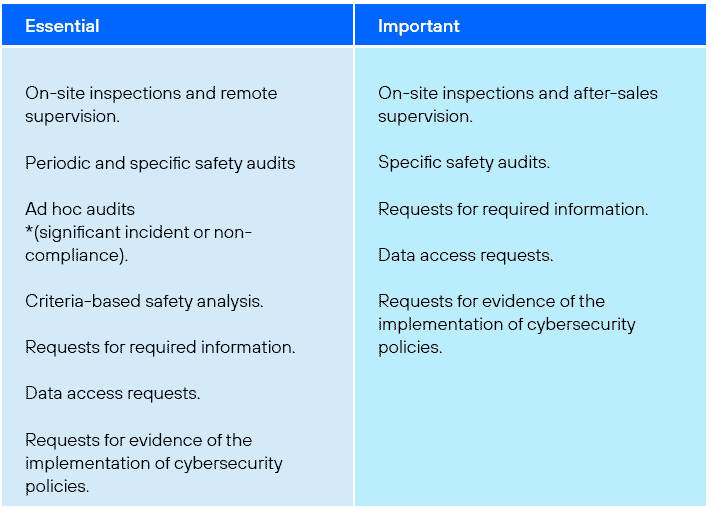
Entities are classified into two groups based on their importance and potential impact:
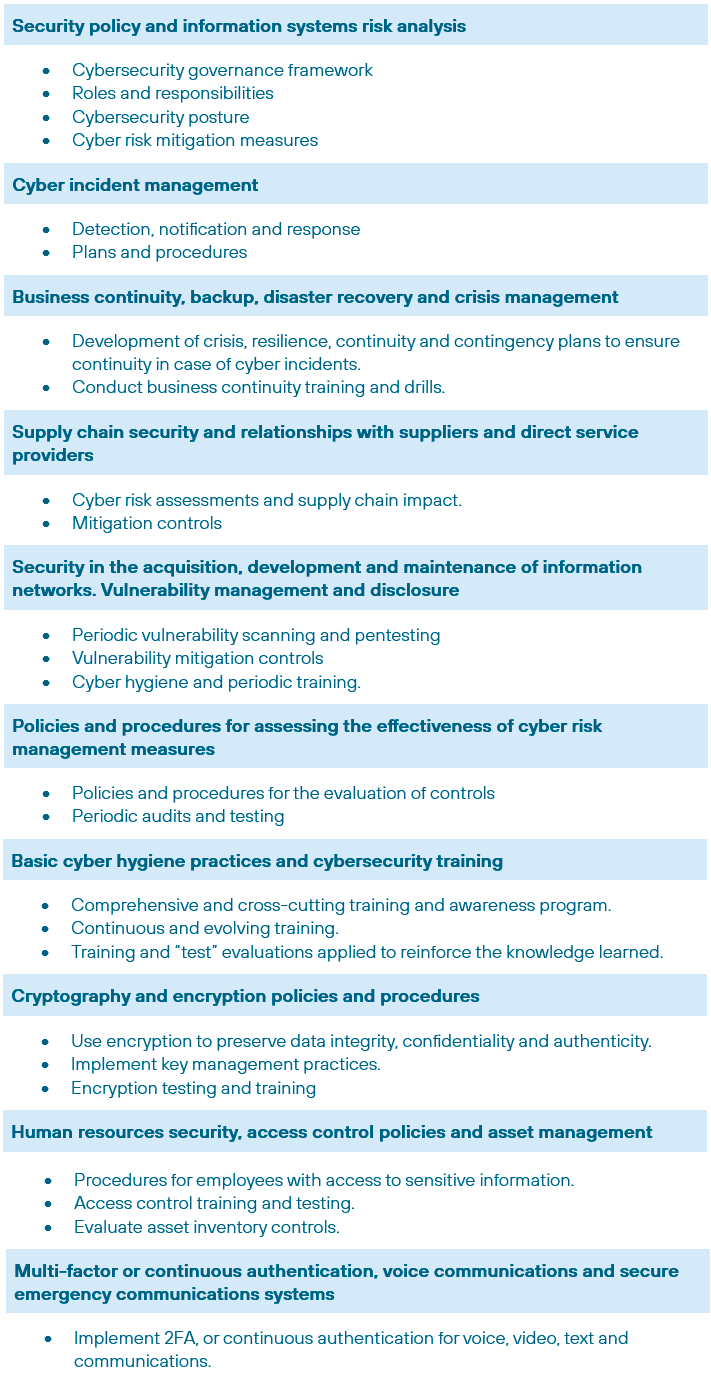
- Essential: These are subject to stricter regulatory supervision, including periodic audits and proactive cybersecurity assessments. Measures must be applied both “ex ante and ex post”, particularly in the event of cyber incidents, which may lead to suspensions, fines, or bans. It is crucial to consider the concept of “professional civil liability” for non-compliance.
- Important: These face a less stringent enforcement regime, where actions are typically taken only after incidents or breaches are detected. Here too, the supervisory regime—led by qualified professionals—can be affected by “professional civil liability” in the event of non-compliance.
Key responsibilities in cyber risk management
Management bodies play a vital role, regardless of the classification of the entity, as failure to comply with the directive can have significant consequences. They are responsible for:
- Approving the adequacy of cyber risk management measures.
- Overseeing the implementation of cyber risk management measures.
- Acquiring sufficient knowledge and skills to identify and assess cyber risks and their business impact.
- Developing a culture of awareness and ongoing training across all levels of the organization.
- Being accountable for non-compliance.
These responsibilities must materialize through the implementation of technical, operational, and strategic measures or controls that are proportionate to the level of risk, with the aim of preventing and minimizing their impact on the business and third-party supply chain services.
Sanctions and measures for non-compliance with the NIS2 directive
NIS2 also grants national regulatory authorities powers over affected entities following non-compliance. These powers include suspension, fines, the appointment of a supervisory officer, orders to inform involved parties, enforcement of corrective measures, and/or formal warnings for breaches.
It is important to highlight that the temporary prohibition from holding executive functions for the CEO or legal representative would apply only to essential entities, not to important ones.
■ Sanctions for non-compliance may include fines of up to €10 million or 2% of global annual turnover for essential entities, and up to €7 million or 1.4% of global annual turnover for important entities.
Conclusion
The new financial and operational demands introduced by NIS2 are clear, including investments in technology, cybersecurity, training, and mandatory cyber insurance to mitigate the financial exposure resulting from a cyber incident.
To align these compliance costs and efforts with business strategy, organizations must prioritize cyber risk quantification, cost-benefit analysis, and make strategic investments in robust, proactive cybersecurity.
MORE FROM THIS SERIES
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector