Protect your credentials: Job offer scams
The rise of online fraud is becoming more and more common in the digital age, whether in social networks, online shopping, emails, or job offers. Any activity of a person on the Internet involves exposing certain data, and there is a race to the bottom among cybercriminals to steal all kinds of information, such as passwords and personal data.
The theft of credentials has become the gold mine of the cybercrime business. This phenomenon arises from the ease with which cybercriminals gain access to compromised accounts, establishing itself as a gateway for phishing and targeted attacks on businesses.
What happens if your credentials are compromised, and what is the risk of your passwords or confidential data ending up in unwanted hands? Personal data breaches or digital security are often underestimated, but would you worry just as much if you lost your house or car keys? When cybercriminals get hold of your passwords, they check if you use the same one in all applications and social networks.
Protect your data like you protect your keys!
Once the credentials have been stolen, cybercriminals opt for different actions of use: they sell the credentials in underground forums or through Telegram, carry out impersonation attacks or execute access attacks on systems to get into organizations, among other attacks. This is reflected in our report on cyber threats in 2023, which warns of the buying and selling of credentials as one of the main ways to compromise corporate networks.
The scale of the business is so large that there are actors known as initial access brokers (IABs). These are criminal groups engaged in selling credentials and all kinds of illegitimate information on Deep Web forums. These forums have a direct impact on data breaches and cyberattacks, as ransomware groups resort to these marketplaces to trade credentials and fulfill their criminal activities.
There are different techniques to steal user credentials, such as phishing campaigns, social engineering attacks, malware programs, "infostealers" or exploits.
Deception through social engineering in social networks is the most common, and one of the most recently used platforms to obtain credentials is the social network Linkedin.
Linkedin: Fake recruiter profiles
In the realm of social networks, cybercriminals are employing different and increasingly sophisticated manipulation techniques to deceive their victims, becoming more and more difficult to identify as fraudulent. This challenge manifests itself on the Linkedin platform, where there is a proliferation of fake profiles of supposed recruiters, attractive fake job offers and account spoofing in order to obtain confidential and user data.
The success of these malicious actors is evident, as LinkedIn is one of the most impersonated brands in the world, according to Check Point Research's (CPR) 2023 Brand Phishing Report.
The recently used modus operandi is impersonation campaigns on recruiter profiles. Cybercriminals use these profiles to contact potential victims, offering them attractive job offers via direct messages, containing malicious links or inviting them to request more information via chat.
⚠️ The goal of these fake recruiters is to obtain victims' credentials, as well as to distribute malware on mobile devices to execute malicious code. This tactic is distinguished by sending personalized messages to candidates, without misspellings to deceive job seekers or people with job aspirations.
How do fake LinkedIn recruiters work?
- Malicious actors use legitimate Linkedin recruiter profiles, profiles that have been compromised before or obtained from some data leak (e.g., the 2023 leak of 35 million Linkedin users). At other times, they create fake profiles or bots to extend the fraud scheme and generate credibility.
- They use sophisticated fraud structures with many fake profiles, which allow sharing publications of the alleged company to simulate legitimacy.
- Attack targeting professional profiles, focusing on a specific sector and professional profile to carry out a massive campaign.
- Preparation and sending of messages via private chat, accompanied by an image that simulates a PDF or Word document with the details of the job offer. But beware, it's just the bait with the malicious link!
- Cybercriminal groups initiate an exchange of messages that look real in order to gain the victim's trust.
One of the ways to detect and combat scams is through the use of OSINT (Open-Source Intelligence) techniques, which consists of the analysis of open source information and facilitates fraud detection. Let's take a look at an example below:
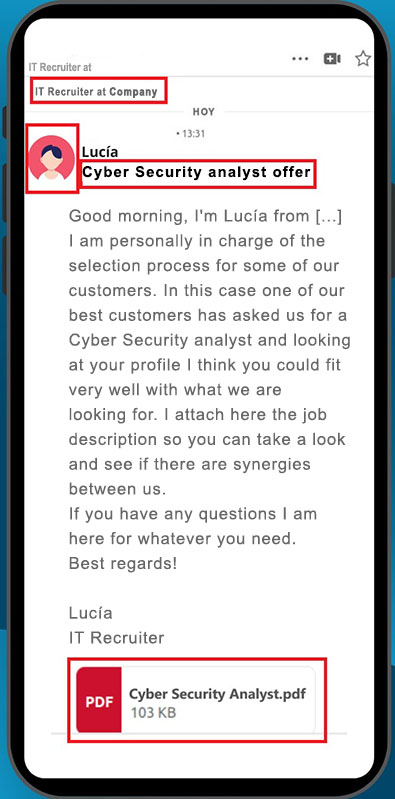 Example of fake job offer on Linkedin. Own source.
Example of fake job offer on Linkedin. Own source.
It all starts with a private message from a supposed recruiter. At first it looks like a legitimate message and without any pattern of suspicion: there are no spelling errors, the recruiter's profile is detailed, provides contact information of the company, and attaches a personalized document of the job offer for the candidate.
When looking at the recruiter's profile and suspecting a possible scam, a simple “Google Lens” search of the recruiter's profile image can be performed.
⚠️ When reviewing the image of the supposed IT recruiter who calls herself Marta, surprisingly she also appears as Nicole, Alaska, Anna, and Celina, and the curious thing is that she works in different companies and locations around the world!
Fraudsters use both stolen images and images created by Artificial Intelligence, and the sample is that during the year 2022 thousands of profiles were identified on Linkedin that were created by AI faces.
Another pattern of suspicion is the sending of a PDF or Word document, as clicking on the link to the juicy "job offer" displays a web page that simulates access to Linkedin, granting credentials to the malicious actors.
Copy the link of the supposed document instead and enter it on a web page that confirms if it is safe. There are different tools to analyze the link obtained, such as filescan, which helps us to confirm if it is malicious and definitively report the scam.
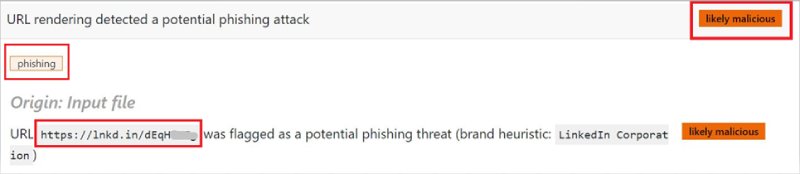 “Image: Example of malicious link in Filescan. Own source.”
“Image: Example of malicious link in Filescan. Own source.”
Despite LinkedIn adding new security features in October 2022 to combat fake profiles, cybercriminals continue to update their modus operandi to evade detection and reach more victims in the shortest possible time.
This is where cyber intelligence plays a key role in protecting data. From Telefónica Tech's DRP team, suspicious activities are detected early. By monitoring and integrating intelligence across multiple platforms, the risk of compromised credentials can be mitigated, and threats can be dealt with quickly.
Recommendations to avoid scams in job offers
- Be wary of suspicious messages: If you receive a private message that seems unusual, do not click on any link, check the recruiter's profile and activity on the social network before taking any action.
- Keep an eye on friend requests: Ask their motives and check their communication channels before accepting.
- Check the privacy settings of the social network: display the necessary information to keep your data protected.
- Use strong passwords and enable two-factor authentication.
- Verify the legitimacy of the company: Investigate if the company really exists and do not hesitate to call to confirm that they are looking for employees.
Protect yourself to keep your information safe in the digital world, security is in your hands!
Image by Sergeycauselove at Freepik.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector





