¿Ransomware in Pandemic or Ransomware Pandemic?
No one imagined what could happen in the field of cyber security during the Covid-19 pandemic. Perhaps some colleagues were visionary, or others were basically guided by the statistics of recent years regarding incidents and security breaches, which have been steadily increasing. I hope everyone understands that no one is free from a cyber incident nowadays.
A Little Bit of History
The beginnings of ransomware do not date back to the 2000's as most people believe. As early as December 1989, when the first website had not even been created yet, 20,000 diskettes of 5¼" were sent from London to companies in the UK and abroad, to subscribers to PC Business World magazine and also to participants at an AIDS conference organised by the World Health Organisation. On the sticker of these diskettes was written AIDS Information Introductory Diskette, it was and said to be from the PC Cyborg Corporation. All of this was a deceit, it encrypted the hard drive of the computers and asked for a ransom. AIDS was the first ransomware to also spread globally, reaching over 90 countries by postal mail.
Nowadays, 31 years have passed, and ransomware has already become an industry, with incredible advances in the field. The Covid-19 pandemic has only accelerated the development of infection campaigns. The numbers and incidents that have occurred in the pandemic, I would say, are unprecedented. Remote working could be one of the causes, as cyber security controls are weaker in the home than in the corporate environment, but mainly it has to do with our anxiety and uncertainty, which makes us more "prone" to fall into a phishing operation containing ransomware. However, this increase in numbers in the region is already evident in several studies since last year:
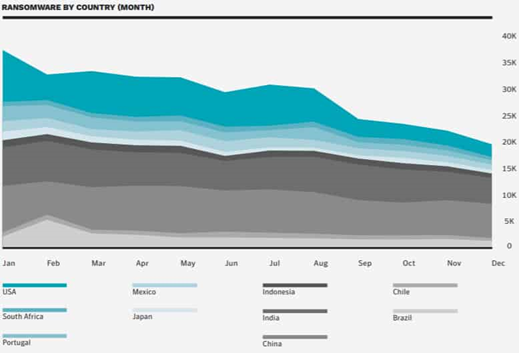 Ransomware by country. Source:
Symantec
Ransomware by country. Source:
Symantec
The Ransomware Business
Not long ago, ransomware was classified as an incident (DBIR) rather than a breach, because data encryption does not necessarily involve a disclosure of confidentiality. However, that has changed: the business of ransomware is no longer so much about encryption but about making money from the threat of information leakage, and there are cases to back this statement up.
Not long ago, ransomware was classified as an incident (DBIR) rather than a breach, because data encryption does not necessarily involve a disclosure of confidentiality. However, that has changed: the business of ransomware is no longer so much about encryption but about making money from the threat of information leakage, and there are cases that demonstrate this.
At Elevenpaths, we have been tracking the several ransomware campaigns that exist and shared them with the community through our weekly briefings and cyber security research reports.
I also talked about it a month ago, after giving many interviews about the incident at Banco Estado de Chile, allegedly provoked by Sodinokibi. A ransomware whose campaigns, we at ElevenPaths, had already been following since January this year.
On the other hand, advances in ransomware development are evident. For example, Conti occupies 32 CPU threads in parallel during the infection process of a computer. Sergio de los Santos wrote a highly recommended post called " What Do Criminals in the Ransomware Industry Recommend so that Ransomware Does Not Affect You?" which may be useful to understand what is happening in this new era.
To sum up, the non-profit volunteer hacker initiative called the CTI League (Cyber Threat Intelligence League), a global community of emergency response volunteers who defend and neutralize cyber security threats and vulnerabilities to life-saving sectors related to the current Covid-19 pandemic, should be highlighted for the great work they have done in helping and preventing more health institutions from being affected by these types of cyber attacks.
Just a question: what will be the next level in this battle?
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector




