SSDLC: The key to shielded software
In a digital landscape where cyberattacks evolve along with technologies, shielding our applications is a priority.
That's where the Secure Software Development Life Cycle (SSDLC) comes in. It is the backbone that allows us to minimize risks and deliver much more robust products.
What is the SSDLC?
The SSDLC is a framework that integrates security controls and practices into every phase of the software development process. It is the evolution of the traditional SDLC (Software Development Life Cycle) concept, which focused more on functionality, but neglected the cyber security aspect.
Why is SSDLC important?
Adopting an SSDLC approach brings numerous benefits to companies, including:
- Early detection of vulnerabilities: By encouraging security from the outset, SSDLC allows potential risks and weaknesses to be identified before the product is finished, saving significant time and costs in rectifications.
- More secure products: A security-by-design mentality leads to systems that are much more resistant to cyberattacks.
- Reduced costs: Software full of vulnerabilities means costs for remediation, patching, and even potential lawsuits in case of security breaches. SSDLC is like a vaccine: it costs much less to prevent than to cure.
- Reputation and trust: Customers value trusting their data to companies that demonstrate a strong commitment to security. A strong SSDLC is a competitive advantage.
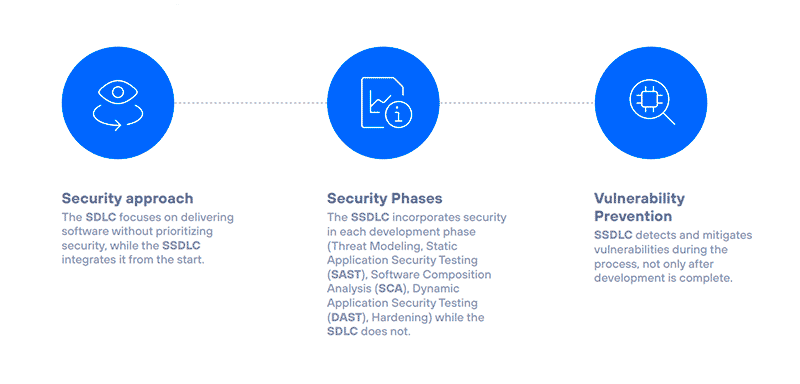 Infographic: Deploying Secure Software Development Life Cycle
Infographic: Deploying Secure Software Development Life Cycle
Example: The vulnerable app
Let's take as an example a company developing a password management app. This app could contain flaws that allow attackers to access user passwords if appropriate security measures are not implemented during development. This would have terrible consequences:
- Data theft: Cybercriminals could steal users' passwords and use them to access their bank accounts, social networks, or other online services.
- Loss of trust: Users would lose trust in the company and stop using the app.
- Reputational damage: The company would suffer a serious loss of reputation and could be sued by affected users.
- Regulatory non-compliance and fines: The company could be sanctioned by the competent authorities for non-compliance with data protection regulations, which could result in fines in the millions of dollars.
An SSDLC implementation would have made it possible to identify and correct these security flaws during app development, thus avoiding the aforementioned serious consequences.
How do we do it?
Typical SSDLC phases
A common SSDLC model includes the following phases, although different methodologies exist:
- Planning: Definition of objectives, requirements, and scope of the project.
- Design: Creation of a detailed software design.
- Development: Implementation of the software code and unit testing.
- Testing: Exhaustive testing to detect and correct errors.
- Deployment: Deployment of the software in the production environment.
- Maintenance: Constant monitoring, security patching, and incident response.
Best practices in an SSDLC
- Continuous training of developers: Cyber security is a constantly evolving field.
- Threat Modeling: Identify potential attacks at each stage of the development cycle.
- Automated analysis tools: Use of software (SAST, DAST) specialized in finding vulnerabilities in code.
- Code reviews: Human reviews to reinforce automated analysis.
- Vulnerability management: Clear procedures for prioritization and remediation of discovered vulnerabilities.
Conclusion
SSDLC is a paradigm shift. It transforms security from being an afterthought to being an integrated feature from the initial concept of a software.
SSDLC is not an option in today's world, it is a necessity for any company that is serious about protecting its systems and its customers' systems.
Image by Freepik.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector





