Pentesting and Security Assessment: two sides of the same coin in Cyber Security
The constant identification and mitigation of vulnerabilities is essential in the field of cyber security to protect the systems, applications, and digital assets of companies.
In this context, Pentesting and Security Assessment are two tactics that differ in their approach, methodology and results, but complement each other within a complete Cyber Security strategy.
What is pentesting?
The term 'pentesting' ('pen test') refers to controlled and authorized 'penetration testing' on an organization's systems and applications to identify and exploit vulnerabilities and security breaches.
This practice is distinguished by its active nature and offensive orientation. Its objective is to practically evaluate the security of systems, networks or applications in search of weaknesses by applying attack scenarios involving multiple steps and vectors.
Therefore, when performing penetration testing or pentesting, different techniques and tools are used, just as in real attacks, to get as deep as possible into a company's infrastructure.
This allows the resilience and effectiveness of its defenses and layers of protection to be evaluated from a Cyber Security point of view.
The role of the pentester
The professionals who carry out these tests, known as 'pentesters', assume the role of attackers. Their purpose is to compromise security systems to discover vulnerabilities and security gaps. This involves thinking and acting like a real cybercriminal, to expose potential flaws in the system.
Penetration testing is generally conducted in stages, which include gathering information, identifying vulnerabilities, exploiting them, and finally reporting. This approach allows vulnerabilities in systems to be proactively identified and addressed before malicious attackers and cybercriminals can exploit them.
These penetration tests reflect how advanced targeted attacks operate in the real world. So these tests provide a concrete view of the impact that a real attack could have, exploiting misconfigurations or vulnerabilities in systems.
✅ Companies such as Tesla or Microsoft have reward programs in place to incentivize the search for vulnerabilities: Tesla on its vehicles, which rewards between $100 and $100,000, and Microsoft for its Azure platform, with up to $60,000. The goal is to detect and resolve vulnerabilities before they can be maliciously exploited.
What is a Security Assessment?
The main purpose of a Security Assessment is to identify, categorize and manage vulnerabilities that may affect an organization, covering technical, operational, and human aspects.
These vulnerabilities can range from insecure system configurations to bad programming practices and lack of security patches or updates.
Its approach includes the identification of vulnerabilities in the organization. This ranges from a thorough review of policies and procedures to deficiencies in employee security training or knowledge, among other aspects.
Pentesting and Security Assessment: why both are important
Security assessment and pentesting are two fundamental security tactics, each with a different focus, purpose, and outcome:
Pentesting (penetration testing)
- It is designed to test whether a mature defense can prevent an attacker from achieving one or more specific objectives.
- It targets the entire organization or relevant vulnerabilities from previous assessments.
- The test result details what was tested, how it was tested (including exploitation paths) and the test results, along with recommendations for improving the security posture.
Security assessment
- It is designed to find as many defects as possible to make a prioritized list of items to remediate.
- It focuses on specific assets such as infrastructure, software or employees.
- The test result provides a prioritized list of all vulnerabilities and risks found on the tested assets, along with recommendations for improving the security posture.
Despite their differences, both tactics are essential within a comprehensive cyber security strategy:
- Pentesting focuses on identifying specific, real-world flaws that can be imminently exploited.
- Security assessment offers a panoramic view and provides a long-term analysis of security postures and policies, allowing for more robust strategic planning.
✅ Example: a hospital could employ pentesting to test the resilience of its network against external attacks, such as ransomware. At the same time, a comprehensive security assessment would review its medical records access policies, the level of cyber security training of its staff, and the effectiveness of its incident response procedures. This dual strategy would ensure that the hospital is prepared for both immediate threats and risks inherent to its organization.
Telefónica Tech's Security Assessment and Pentesting Service
Telefónica Tech offers a comprehensive security and pentesting service for organizations of different sizes and sectors (SMEs and large enterprises) that provides an independent and objective assessment of multiple aspects of security, including technology infrastructure, software and employee training and awareness:
- Technological infrastructure to identify potential vulnerabilities and uncontrolled access.
- Software to identify security gaps in web applications, apps and APIs, with actionable recommendations to improve security.
- Employee training to identify risks associated with social engineering attacks and assess employee preparedness for security incidents.
✅ Example: A company in the financial sector can use our service to perform a comprehensive pentesting of its infrastructure and applications. This would not only help the company identify and fix vulnerabilities, but also facilitate compliance with regulations such as GDPR or PCI DSS.
Pentesting and Security Assessment Methodology
Our methodology consists of four main phases:
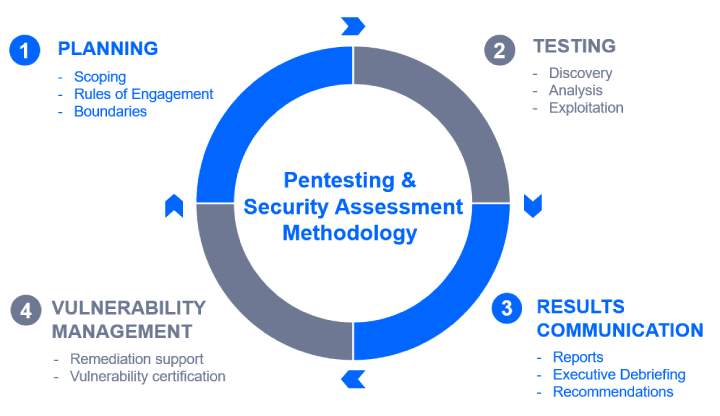
- Planning: Defines scope, limits, success criteria and reviews past threats and vulnerabilities.
- Testing: Performs security testing, considering different scenarios and standards.
- Findings: Delivers a detailed technical report with recommendations.
- Vulnerability management: Clients prioritize and mitigate vulnerabilities found.
This comprehensive approach enables organizations to take effective preventive and corrective actions.
Our methodology provides clear and concise guidance on how to protect customer information against real attacks.
Analysts specialized in Pentesting and Security Assessment
We have a global team of analysts highly specialized in the execution of Cyber Security testing that stands out for their expertise, covering a wide range of sectors, from banking to healthcare and transportation, and their constant training to stay updated on the latest trends in risk and compliance.
Our team also holds industry certifications that support our capabilities and expertise. This solid foundation allows us to effectively adapt to each client's specific environment, applying proven methodologies to deliver effective solutions.
Our team of analysts ensures a cyber security strategy prepared to address both immediate threats and long-term risks.
Our Pentesting and Security Assessment service is comprehensive and adapts to the needs of various types of organizations, offering an unbiased security assessment for any company seeking to strengthen its security posture with preventive and corrective measures to protect its critical assets and data.
Image from Freepik.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector.jpg)





