What is the Fifth Domain and what is its strategic importance?
In recent years, conflict and stability in cyberspace have become a growing concern for many countries and organisations that consider cyberspace as a strategic domain and have strengthened their cyber defence, cyber intelligence and offensive capabilities.
The National Institute of Standards and Technology (NIST) defines cyberspace as a global domain within the information environment consisting of the interdependent network of information systems infrastructures..
The term "cyberspace" comes from the American writer William Gibson, who used it in his 1984 novel 'Neuromancer'
This includes the internet, telecommunications networks, computer systems and embedded processors and controllers in critical industries characterised as a complex environment resulting from the interaction of people, software and services on the internet through technological devices and networks connected to it, which does not exist in any physical form.
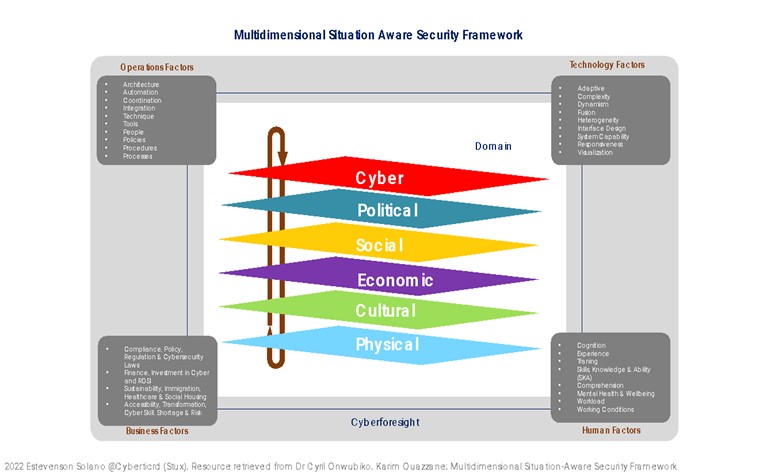
Cyberspace, the fifth domain
Cyberspace has been called the ''fifth domain'', of equal strategic importance to land, sea, air and space. This has intensified international competition in this field with major powers competing to dominate cyberspace.
Concerned about how to prioritise so many security activities amidst such a changing landscape? Are we joining forces to rethink cybersecurity? What is the impact of cyberspace on economic growth and development? Do we accurately understand the connotation, characteristics and essence of cyberspace?
The dynamic nature of cyberspace can introduce challenges in decision-making. Leaders routinely face difficult decisions in managing cyber risk, as exposure to cyber risk can threaten reputation, customer trust and competitive positioning, and possibly result in fines and lawsuits.
New Cybersecurity Challenges
In this context, leaders must simultaneously address changing organisational priorities, shifts in budgets, technologies and employee headcounts, as well as evolving adversarial tactics and emerging security events, among other things. Cyberspace has faced many security challenges such as identity tracking, identity theft, terrorism, espionage and warfare. The continued exponential growth of cyber-attacks puts more pressure on executive decision-makers to stay ahead of the curve.
Cyberspace connects everything and everyone with applications, data, purchases, services and communications... Securing it is essential to protect organisations, the environment and society.
Reacting after the fact can be very costly and increase the need for ex post regulatory assessment and sanction. We see and understand that cyber risk is dynamic in nature, and we must now act accordingly.
Recent developments and changes in cyberspace, such as the increase in cyber threats, the shift to hybrid working and the ability to bring your own device into the work environment, have increased discussions about the need to improve the overall cybersecurity posture across organisations.
Challenges for the management of cyber crises
Zero trust has emerged as a potential solution and a challenge that creates confusion in cybersecurity circles about its effectiveness. What policies, practices and partnerships are needed to prevent a cyber pandemic? Are our organisations prepared for a confrontation in cyberspace?
It also reveals where the greatest challenges lie in managing cyber crises, which are induced in cyberspace and have characteristics that make them difficult to deal with, such as the fact that they can be induced remotely and instantaneously in multiple locations.
As the dangers transform, so must our responses; digital threats demand vigilance, determination and resolve to react with precision to an ever-growing risk.
Cyber crises are also not always easily traceable, and it is sometimes difficult to see that the cause of a particular crisis in the offline world is an act in cyberspace. Finally, the borderless nature of cyberspace leads to a potential large-scale geographical spread of cyber crises and cyber resilience.
Security system complexity, created by disparate technologies and lack of in-house expertise, can amplify these costs. However, organisations with a comprehensive cybersecurity strategy, governed by best practices and automated using advanced analytics, Artificial Intelligence (AI) and machine learning, can fight cyber threats more effectively and reduce the lifecycle and impact of breaches when they do occur.
An expanding risk surface
Indeed, the risk surface is still expanding, with thousands of new vulnerabilities being reported in old and new applications and devices. And opportunities for human error, specifically by negligent employees or contractors inadvertently causing a data breach, continue to increase.
While cybersecurity professionals work hard to close security breaches, attackers are always looking for new ways to escape IT's notice, evade defence measures and exploit emerging weaknesses.
Digitalisation has led to increased exposure of our technology assets in cyberspace, requiring a worldview of risk, resilience and trust.
The latest cybersecurity threats are putting a new spin on "known" threats, taking advantage of work-from-home environments, remote access tools and new cloud services.
Today's organisations are connected like never before. Their systems, users and data live and operate in different environments. Perimeter-based security is no longer adequate, but implementing security controls within each environment creates complexity.
The result in both cases is degraded protection for your most important assets. A strategy focused on zero trust to the cyberspace and environment makes the commitment and establishes controls to validate every user, device and connection in the business for authenticity and purpose.
To successfully execute a zero trust strategy, organisations need a way to combine security information to generate the context (device security, location, etc.) that informs and enforces validation controls.
Cyberspace is increasingly exploding. It requires greater coordination among all of us. It requires the development of standards to provide a stable and secure environment.
A cyber resilient organisation in the face of disruptions from cyberspace is one that can identify, prevent, detect, contain and recover from a myriad of serious threats to data, applications, and information technology (IT) and technology operations (TO) infrastructure.
We should remember that a defence-in-depth strategy, also known as a defence-in-depth strategy, helps us to address a cybersecurity approach that uses multiple layers of security for holistic protection.
The importance of a layered defence
A layered defence helps security organisations reduce vulnerabilities, contain threats and mitigate risk. Simply put, with a defence-in-depth approach, if a bad actor breaches one layer of defence, it could be contained in the next layer of defence.
Traditional perimeter-based IT security models, designed to control access to trusted enterprise networks, are not suited to the digital world.
Organizations today are developing and deploying applications in corporate data centres, private clouds and public clouds, as well as leveraging SaaS solutions. Most enterprises are evolving their defence-in-depth strategies to protect cloud workloads and defend against the new attack vectors that accompany digital transformation.
The digital world has transformed the way we live, work and play. However, it is a digital world that is constantly open to attack, and because there are so many potential attackers, we need to ensure we have the right security in place to prevent systems and networks from being compromised.
There are plenty of risks, but so are the solutions, including those based on Artificial Intelligence and the "Zero Trust" model"
There is unfortunately no single method that can successfully protect against every type of attack. This is where a defence-in-depth architecture comes in.
Rethinking and refocusing Cybersecurity
Although cyberspace has become a central element of all vital processes in the global economy and in people's social lives, it also carries a wide variety of risks. Framing these risks is no easy task: some cause damage in cyberspace itself, while others cause damage in the offline world as well.
Moreover, sometimes the damage is intentional, while other times it may be the result of accidents. The "cyber damage model" brings together these challenges and offers the opportunity to gain a comprehensive overview of different types of cyberspace-related incidents.
Cyber crises also bring with them a number of specific challenges for leadership, especially in terms of sense-making, decision-making, termination and learning.
Leading without a cyber strategy is like playing a game of whack-a-mole: as soon as one incident is squashed, another one pops up.
Cybersecurity strategies aimed at meeting the grand challenges are characterised by a holistic, cross-cutting and comprehensive approach as a catalyst for added value from governance, risk and compliance frameworks. Including the establishment of axes, principles, structures and practices necessary for their design, construction, implementation, monitoring and improvement, from the strategic to the tactical and operational level, resulting in emerging and disruptive innovation.
It is important to rethink and refocus cybersecurity when establishing a cyber strategy, giving scope in its spectrum to cover preparations and precautions taken against cyber crimes, cyber wars, cyber attacks, cyber incidents and cyber threats from the cyber surface.
More than ever, there are many positives. We have come a long way in a short time and we are doing a good job, but the key is not to settle, it is to reaffirm the commitment to do better, as our adversary comes with new skills.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector







