Wireless attacks on OT
Wireless networks are now present in all types of industries. It is undoubtedly one of the most notable changes brought about by smart industry because it has increased productivity and reduced costs. However, in several scenarios it has been shown that wireless networks do not generate security conditions that can be considered optimal.
To change this, two wireless transmission protocols have been developed that strive to improve cyber security levels: Ultra-WideBand (UWB) connectivity and the UWB variation of the Real Time Location System (RTLS).
Nonetheless, researchers specialised in OT security at Nozomi Networks (a company acquired by Telefónica Tech) conducted a series of security tests on these protocols and found some 0-day vulnerabilities where it is possible to gain access to sensitive information being exchanged in the transmission.
Security test results
To focus the research a bit specific models of equipment and its use in the industrial and hospital sector were taken, where it was decided to test Sewio Indoor and Avalue Renity, which are two UWB RTLS packages that deliver location, protection functionalities are used in maintenance operations and others.
Once these elements were in place, we proceeded to carry out the research on communications and data analysis that are executed in a traditional operation infrastructure with these elements, which is composed of locators, information anchors, the UWB and the RTLS processing server.
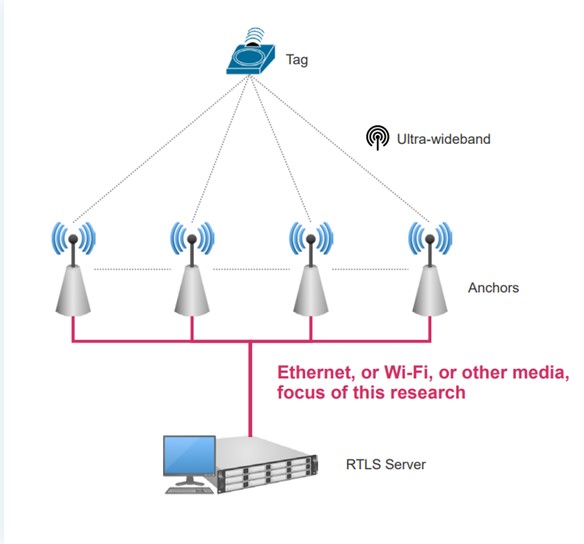
Using this network architecture, the researchers initiated reverse engineering and analysis processes in various scenarios and responses, which are fully documented in the research team's final report.
In the following report you can see the tactics, techniques and procedures that were performed to simulate how an actor can gain access to information by executing a Man in the Middle (MitM) attack and an access to the communication network.
Possible consequences and options for mitigating this attack
When an attacker applies these methods in real life, he or she can easily know the position of people or assets in factories, which are used for rescuing people in remote jobs or in cases of emergencies within an operating plant.
In hospitals, it is widely used in cases of emergencies and in order to attend to serious medical symptoms. Therefore, in a passive attack, criminals could access information on staff behaviour and habits or know the location of valuable assets.
Now, one of the most common RTLS application functionalities is the creation of geofences, which are used from a personnel and asset protection point of view, using the entrances or exits of specific areas, which can generate an alert for proximity to dangerous equipment or other alerts.
In testing attacks on these configurations, it was possible to modify the monitored areas or actions taken in the geofence, generating manufacturing stoppages or allowing access to dangerous areas or the possibility of eliminating anti-theft monitoring.
Conclusion
All these analysis and results were shown in the BlackHat USA 2022 edition, where it was very well qualified and received. The demonstrations showed that all types of industries can be victims of this type of attack and that the consequences can be not only operational, but also life-threatening.
It is important for the industry to validate the possibility of remediating or mitigating the possible impact through network segmentation and the use of industrial firewalls, as well as the implementation of intrusion detection in operating environments that allow for the detection of anomalous behaviour or unexpected movements in the network, and finally, the possibility of implementing encrypted data transmission.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector






