23andme or how to not manage a security incident
No company wants to appear in the media for suffering a security incident, although, as is tirelessly repeated in our industry, there is no such thing as 100% security.
It is not, therefore, a question of whether a security incident will occur (the answer to which is, inevitably, yes), but how the organization prepares for its detection, management, and response. Basically, prepare the procedures, carry out simulations and enter into a cycle of continuous improvement.
Imagen generada automáticamente con IA
As a result of what has been published in the media recently, it seems that the genetic analysis company 23andme did not prepare too conscientiously for this, at least from a communication point of view, and thus suffered a significant discredit for its management, with obvious errors that have been angering both its users, with more than 30 massive complaints filed, and the cyber security community.
Timeline of the attack
- October 6, 2023: An actor threatening under the pseudonym Golem offers for sale personal information of 1 million people extracted from the 23andme platform.
- October 10, 2023: 23andme has asked all of its users to reset their passwords as a precautionary measure.
- October 17, 2023: the same threat actor publishes a new dataset on the BreachForums darkweb forum with personal data of another 4 million people.
- October 20, 2023: 23andme disables the DNA sharing option to find potential relatives.
- November 6, 2023: 23andme adds 2FA by default for its clients in an attempt to protect users from credential stuffing attacks.
- November 30, 2023: 23andme makes a change to its terms and conditions defining mediation as the default dispute resolution mechanism.
The following are some of the mistakes made in the management of this incident to try to learn from them so that other organizations do not repeat them.
Error: minimize the incidence
This is a common mistake made by organizations in the management of security incidents. First, they tend to minimize the impact of the incident in order to downplay its importance and try to silence the noise generated.
In the case of 23andme, it was mentioned in an early blog post that the incident only affected 14,000 customers, less than 0.1% of its user base of 14 million.
While this statement may be technically correct, the attacker only gained direct access to the accounts of these thousands of customers through a credential stuffing attack. For the general public, it is the impact that matters.
The reality is that the attacker gained access to the personal information of 6.9 million users through optional features that allow sharing information with other users to find relatives (DNA relatives feature) and family tree (Family Tree feature), which is equivalent to approximately half of its users.
Error: blaming the users
After receiving a number of mass complaints from users, the company's surprising response was to somehow roll over like a cat on its belly and issue a letter to some of the complainants blaming the incident on users and their management of passwords, according to information published in TechCrunch this January.
This finger pointing makes no sense. 23andMe knew or should have known that many customers use recycled passwords and, therefore, 23andMe should have implemented some of the many safeguards available to protect against credential stuffing, especially considering that 23andMe stores personally identifiable information, health information and genetic information on its platform.
Error: change of terms and conditions
Again after receiving more than 30 complaints regarding the security incident suffered 23andme has decided to change the terms and conditions of the contract with its users as reported by stackdiary. This change will force its users to enter into binding arbitration, which is a means of resolving disputes (such as a security breach) out of court.
In this process, both disagreeing parties present their cases to an arbitrator, who is a neutral third party. The arbitrator hears both sides, reviews the evidence and decides. The key aspect of binding arbitration is that the arbitrator's decision is final, which means that both parties must accept it and cannot appeal to an ordinary court.
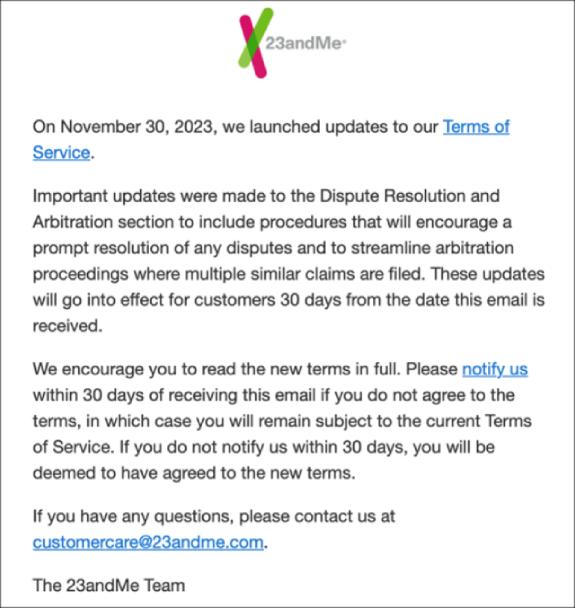 23andme's communication of its new terms and conditions.
23andme's communication of its new terms and conditions.
In the event of a security breach, this means that if you have a dispute with 23andMe, you should first try to resolve it with their customer service. If that doesn't work, you would go to arbitration, not a lawsuit.
This is what 23andMe wants to achieve in light of what happened in this incident and paving the way for their protection going forward, a partisan move to say the least.
To add fuel to the fire, this change of conditions is automatically enforceable and it is up to the users to refuse the arbitration process by communicating directly to an email provided by 23andme (arbitrationoptout@23andme.com) within 30 days of receiving the communication of the change of conditions.
This will naturally mean that a good percentage of users will ignore the message, another good percentage will see it, but will not act on it, and finally another percentage, this time smaller, will do so after the deadline and therefore it will not be effective. All these users will end up being incorporated into the arbitration process.
Correctness
Not everything in the management of the incident was negative, some actions were adequate and correct. Therefore, it is also fair to list them to give a complete perspective of the incident and its management.
- The internal investigation was fast and effective, it is also true that it was technically simple, being a credential stuffing attack. Sometimes this is delayed in time leaving time for the attackers to maximize the impact and for rumors to run rampant.
- Quick preventive measures were taken, such as a password reset requests for all users. Although this is a precautionary measure, with proper communication, we believe that these quickwins are important and correct to minimize the impact and evidence the proactivity of the organization to solve the problem.
- A long-term security measure, such as 2FA by default, was developed and incorporated to minimize the recurrence of this problem in the future on the platform.
This is the official communication from 23andme on their blog about the incident which they have been continuously updating as action was taken or new information was found.
Conclusions
The management of security incidents must seek a balance that is complex to say the least: speed of action versus in-depth analysis of the incident, preventive measures versus long-term measures, transparency of information versus overexposure, etc.
We believe that in the particular case of the 23andme attack, a series of easily avoidable errors were made, which generated more controversy than the incident, at least from the point of view of technical security responsibility, perhaps deserved.
This shows that it is not only the direct impact and the inherent "guilt" of a given organization in the face of an attack that is important, but also how the associated communication is managed, and this will largely shape public opinion and the final impact on reputation.
In general, the recommendation for organizations would be that they should establish clear processes for detecting and responding to security incidents. Not only from a technical point of view, but also from a communication and legal point of view.
And launch simulations that involve all the parties involved in the organization so that when the day comes when the breach is real, which it will come, there is a known way of dealing with it and all parties know what their role is so that they can act diligently.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector





