Hiding malware in Blockchain: Free hosting and takedown testing
What else could happen to the crypto world after the continuous attacks and the countless appearances in the media with large thefts of funds?
Well, along comes what, for many, is nothing more than a proof of maturity, a coming of age or a sweet sixteen, as the Americans would say. It has recently been discovered malware that uses its fundamental characteristics.
The advantages of decentralized environments, such as Blockchain, are often cited, and rightly so, to achieve differentiating features of an application from a security point of view: for example, the immutability of stored information, non-repudiation in the event of a subsequent dispute, etc.
It seems that attackers are also observing these differentiating characteristics and there are some that have attracted their attention: deregulation in these decentralized environments, anonymity, and persistence.
Background
Randy McFoin published an analysis of a malware he named ClearFake due to its low degree of obfuscation, in August 2023. This malware executes a recognizable pattern of defacement of a compromised site with an invitation to a very credible download of a browser update.... or rather, the download of advanced information-stealing malware.
Traditionally these malware campaigns usually end, or at least become more expensive for the attackers, when, after an analysis by a security team, IoCs (Indicators of Compromise) are detected and the blocking or takedown of these assets (domains, IPs, etc.) is requested.
In the particular case of ClearFake, it was analyzed and discovered that it makes use of Cloudfare Workers, Cloudfare was notified, and the accounts associated with those services were blocked. The attack was stalled until a new variant was created.
Yet, what happens if that new variant uses a decentralized Smart Contracts-type environment? Well, as discovered in an analysis by Guardio Labs, which we strongly encourage you to read, that is precisely what the new ClearFake variant does.
Why Smart Contracts?
Binance, one of the world's largest cryptocurrency exchange platforms. three years ago, created Binance Smart Contracts (BSCs) to compete with Ethereum in the creation of smart contracts. These contracts allow for automated execution of actions if several conditions are met.
Analysts have discovered that this ClearFake variant, uses precisely these BSCs to retrieve the payload that will contact the attacker's Command&Control and continue the attack chain.
The following is a flowchart of the attack extracted from the Guardio Labs analysis
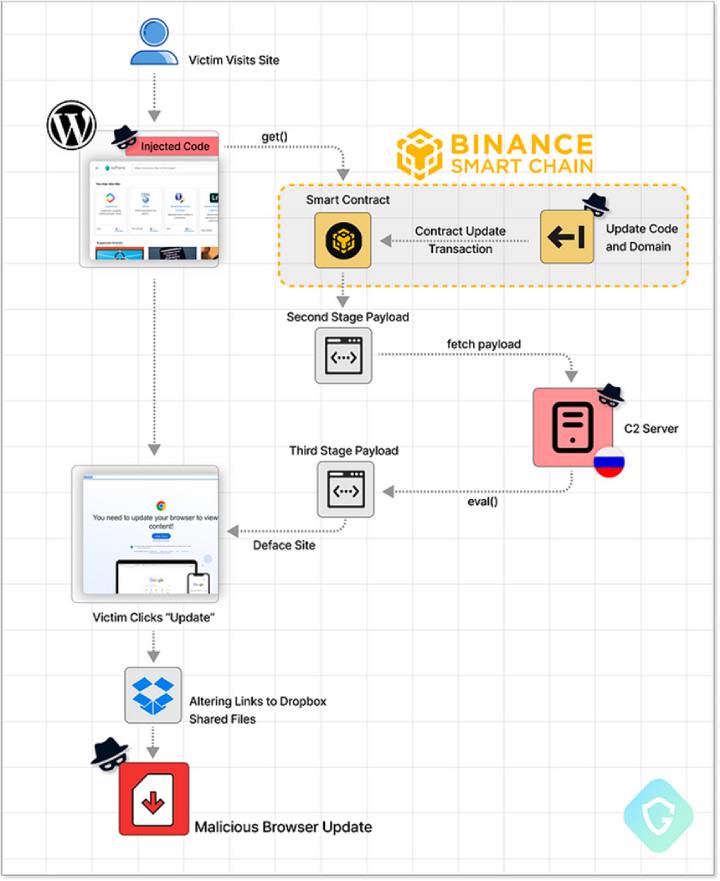 Image from Guardio Labs
Image from Guardio Labs
What are the advantages of using a smart contract?
- Once a smart contract is created, Binance cannot "delete" it, so takedown is not possible. Binance has BScSCan, a malpractice identification service to alert the community of potential malicious use of a contract. But this is of little consequence as it is not a blockchain address used for financial fraud purposes. In fact, it remains a valid contract and address today.
- It is an anonymous service.
- The contract has a simple function of reading and updating a variable. The read function is used for the attack, and the update function allows it to pivot, switch to another domain and different payload each time it is detected at a very low cost of about 50 cents. The contract in question was updated 30 times, i.e., 30 malicious domains blocked as of October 6.
- To top it off the function used by the attacker of the Binance eth_call SDK is intended for testing, its execution is free of charge, and it is not registered on blockchain. This means that the attacker has also obtained a robust and free mechanism that leaves no traces to send the malicious payload.
Conclusions
Many malicious campaigns are traditionally mitigated by blocking domains and IPs, or issuing abuse reports to providers, etc.
However, the advent of Web3.0 alternatives such as Blockchain poses new challenges from its use for malware propagation, to data leakage of credentials and stolen files. All while bypassing the traditional methods of lockdown that law enforcement agencies rely on.
As long as these decentralized platforms do not establish effective control measures over their smart contracts (e.g., disabling queries to contracts from addresses labeled as malicious), this trend will continue to grow. Anonymity is too attractive a siren song for an attacker.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector

.jpg)