Malware distribution: Files in GitHub comments
Cybercriminals are always trying to find new ways of distributing malware that look the more legitimate and innocuous the better. In this article we will have a look at the latest chapter in this eternal saga with the abuse of Github, comments, an attack recently discovered by researchers at security firm McAfee.
What happened?
McAfee researchers have published a technical report on the distribution of the Redline Infostealer malware. The interesting thing about the report from our point of view is that within the attack chain an abuse of uploading files within comments on Github issues of Microsoft projects has been discovered. For example, in the well-known c++ library management project, vcpck.
It is not that a Microsoft repository was distributing malware since February, but that the legitimate repository was used for the malware to host files that are not part of vcpkg but were uploaded as part of a comment left in a commit or issue. The attackers were able to make the distribution url look completely legitimate, even though it distributed malware.
How does this distribution mechanism work?
McAfee publishes this distribution scheme for the case of the stealer they were analyzing:
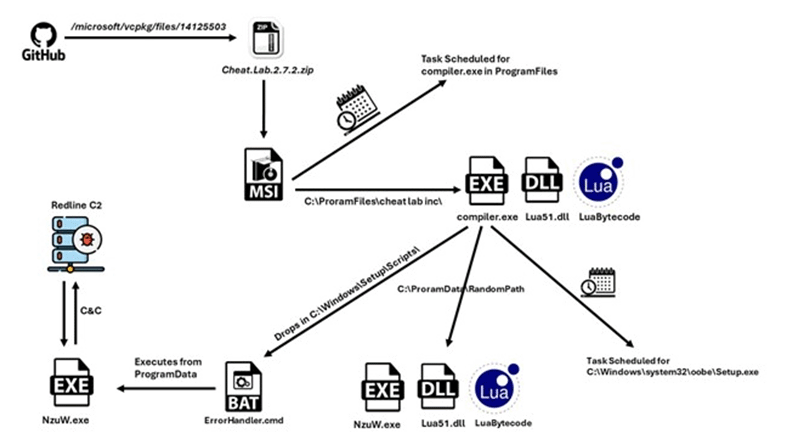 Image extracted from the McAfee study on the Redline InfoStealer distribution.
Image extracted from the McAfee study on the Redline InfoStealer distribution.
Focusing on the initial part of the attack chain, one can see the use of Microsoft's vcpkg GitHub repository as the initial url.
This is possible since, by leaving a comment, a GitHub user can attach a file (compressed files, documents, etc.), which will be uploaded to GitHub's CDN (Cloud Delivery Network) and associated with the related project using a unique URL in the following format:
https://www[.]github[.]com/{usuario_del_proyecto}/{nombre_del_repositorio}/files/{id_del_archivo}/{nombre_del_archivo}
This is due to a potential bug or bad design decision by GitHub. Instead of generating the url after a comment is posted, GitHub automatically generates the download link after adding the file to an unsaved comment. This allows threat actors to attach their malware to any repository without them knowing.
Even if the attacker decides not to publish the comment or delete it after it has been published, the files are not removed from the GitHub CDN, and the download URLs continue to work.
Impact
Since the URL of the file contains the name of the repository in which the comment was created, and since almost all software companies use GitHub, this flaw can allow cybercriminals to develop extraordinarily robust and trusted malicious urls.
Although the detected attack focused on Microsoft code repositories, the attack surface is actually very wide, any public code repository hosted on Github (or even Gitlab which made the same design decision as evidenced).
Let's review three examples of potentially relevant uses of this attack technique:
- Impersonation of security tools: An attacker could upload malicious versions of popular security patches or tools within repositories that host cybersecurity software. They could, for example, upload a trojanized version of an update file for a popular antivirus tool, tricking users into downloading and executing malware under the guise of improved security.
- Plugins for IDE development tools: In repositories that store development tools or plugins, attackers could upload malicious updates or extensions. This could be particularly effective in repositories for IDEs such as Visual Studio Code or popular development frameworks, where additional files could be presented as performance improvements or new features.
- Exploitation of firmware and hardware projects: In repositories dealing with firmware or hardware drivers, uploading compromised firmware files or driver updates could lead to direct manipulation of physical devices. Users downloading these updates could unknowingly install firmware that could alter device behavior or allow remote access.
Mitigation
Unfortunately, even if a company learns that their repositories are being abused to distribute malware, there is no configuration to manage the files attached to their projects.
Once detected an organization can contact GitHub to individually remove such a file... but clearly this mitigation does not scale properly.
Another alternative to protect a GitHub account from being abused in this way and undermining your reputation would be to disable comments. GitHub allows you to temporarily disable comments for up to six months at a time.
However, restricting comments can significantly affect the development of a project, as it will not allow users to report bugs or suggestions.
Conclusions
Malware distribution continues and will continue to creatively search for trusted places where it can generate assets to unleash its attack chains.... this will be a reality today as you read this or 5, 10 years from now is what is called an "evergreen" field where attackers are still looking for fish in the sea.
In this article we have reviewed how a "slight" design flaw in the uploading of files within the Github code management platform can cause a significant flow of apparently legitimate urls to appear for malware distribution. We warn about the special relevance of this new attack vector in firmware projects, hardware, IDEs and their add-ons and security tool repositories.
🧠 Mental Note: Until an effective mitigation by GitHub, which will undoubtedly come, it is necessary to be especially attentive to Github urls not included in official releases and downloadable source code repositories.
As a final curiosity, creativity is not only found on the attackers' side. There have been detected "legitimate" uses of this ability to enter CDN prior to publication on Github, for example, for storing images for a blog as we can see in the following tweet:
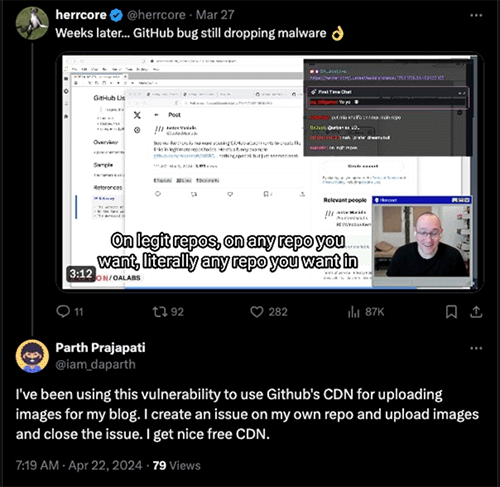 Tweet with reference to the use of Github's CDN for blog image storage.
Tweet with reference to the use of Github's CDN for blog image storage.
Sooner or later it will be addressed by the platform and is not a long term alternative.
______
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector

.jpg)



