New tool: PySCTChecker
When a server implements Certificate Transparency, it must offer at least one SCT (a proof of inclusion of the server TLS Certificate into a Transparency Log). A SCT can be offered by three different ways:
- Embedded in the certificate
- As a TLS extension
- Via OCSP Stapling
Using PySCTChecker is possible to identify the delivery options that the server uses and the logs where certificate has been sent to. Also, it is possible to check if the offered SCTs are valid and legitimately signed by logs.
This script needs just a list of domains as input. For each domain, it will check if the server implements Certificate Transparency. If the server offers any SCT, the script will show extra information about it, such for example the logs where the TLS certificate has been sent and which method the server uses to deliver the SCT.
Usage:
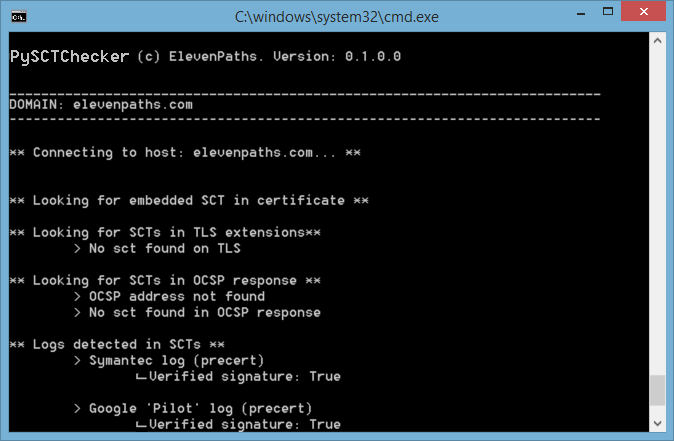
Output example:
This is a quick and dirty implementation since it uses OpenSSL for some features, but we hope it helps understand how certificate transparency works.
You can download and check source code from here.
This tool reinforces our set of tools related with Certificate Transparency developed from ElevenPaths:
- ElevenPaths creates an addon to make Firefox compatible with Certificate Transparency
- Nuevo plugin para FOCA: SCT Checker
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector