Attacking the risk of false friends
 When a company or individual acquires a software or application, they not only get the functionality of the required service or development, but also integrate a new partner or supplier to their ecosystem. This adds a new element to their supply chain or network of allies.
When a company or individual acquires a software or application, they not only get the functionality of the required service or development, but also integrate a new partner or supplier to their ecosystem. This adds a new element to their supply chain or network of allies.
It is not necessary, from a Cyber Security point of view, to maintain an ongoing business relationship with the software or hardware supplier that joins the network. However, by integrating these elements, they become part of the supply chain, becoming a critical factor to consider in security strategies.
Third-party attacks or supply chain attacks are the third most costly attack and in the TOP 5 of the most common.
In most security statistical studies you will find that third party attacks or “Supply Chain Attacks”, for example, in 2022 IBM indicated that they are the third most costly attack and in turn the 4th most repeated.
This is mainly due to two key reasons:
Trusting our “friends”
The risks associated with a piece of software or hardware are often not analyzed before integrating it into the network. It is often assumed that if others use it or if a business relationship has been stable for years, everything will remain the same.
This happens, for example, when solutions from industrial device manufacturers and traffic protection software providers converge. In this case, traffic protection systems from one manufacturer embedded in industrial devices from another manufacturer generate an interdependency with software developed by third parties. As a consequence, any reported vulnerability in one part of the software puts the industrial systems using those devices at risk.
In these cases, if a critical software vulnerability occurs in one of the parts, this forces the manufacturers of industrial devices to generate a special report in addition to their regular report to notify the criticality of this risk in all the hardened control systems that used that software.
The risks associated with software or hardware are often not analyzed before integrating it into the enterprise network.
In practice, there are hundreds or thousands of similar cases in all types of industry, some of them we have included in our blog and that something that may be happening in your company. Therefore, each software or hardware should be analyzed before being acquired, we know if its development and design was thought taking into account Cyber Security, we also think every IP camera or IP sensor that we acquire as can be monitored, validating its impact.
Lack of knowledge of what we are acquiring
Many companies or individuals acquire technology or software because they need to cover an immediate need, without thoroughly analyzing its characteristics. An example of daily life is downloading applications to cell phones simply because it is fashionable or because I need to meet a need but never check the permissions or who is the developer, in some cases not even validate the legitimacy of the development.
In enterprise environments, this is reflected in the incorporation of software or hardware in data center services, where they install their applications on the provider's servers, also known as infrastructure as a service, but rarely is it validated if the equipment has management services from the manufacturer, which remain enabled and public.
Just as a reference example, we can take the management service that comes preconfigured on IBM servers, called WebSphere. More than 400 vulnerabilities have been reported and one of the last ones allows remote command execution on the server, as indicated in the IBM report.
A search for this service on the Internet using Shodan, shows more than 7300 exposed servers worldwide and with more than 5 public vulnerabilities exposed, as shown in the following image.
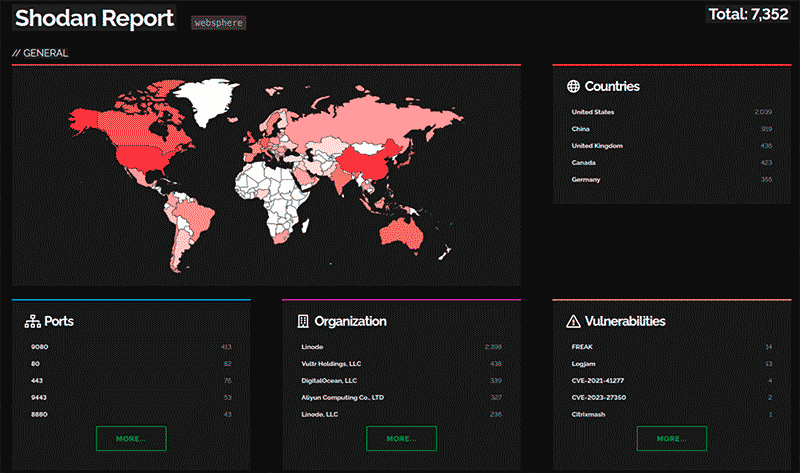
This is why there are many companies that are vulnerable, not only because of the third party but also because of the supplier's supplier, which is not new and we have talked about it before in our blog.
Less trust and more strategy
Controlling this risk is very complex and requires several strategies working in conjunction with a clear Cyber Security management policy by the organization. That being said, each organization should develop these strategies and incorporate them into their information security controls, however, using our experience we can outline some strategies for securing this threat.
Define a process for incorporating software or hardware or supplier
Perform a Cyber Security analysis of that supplier, looking for threat reports, analyzing the response times in correcting a reported vulnerability, asking for the details of the attack surface and any other data that the organization considers that implies a risk for the management of its information.
Every software or hardware must be analyzed before being purchased to find out if it meets the premise 'Cyber Security by design'.
Nothing goes in without confirmation and assurance
Sometimes the rush is to cover the need, but each element should be validated with a security test and with the execution of an assurance process, which validates that our second cause is not present.
Strengthening authentication
Undoubtedly the most critical risk is that they can impersonate any user on the network, when placing any hardware or software it will know the authentication mechanisms that are used and in many occasions can be used to impersonate users. However, if the authentication and authorization is constantly reinforced and has multiple confirmation factors, this greatly reduces the possibility of exploiting this threat.
Monitoring to determine behavior
It is almost impossible to monitor every bit or every asset in depth, but it is essential to determine what is the typical behavior of each of the elements of the network. Therefore, once a new element is incorporated, it must have a constant and in-depth monitoring to be clear about that behavior and in a short period of time reduce the monitoring and be able to generate valid alerts when something is abnormal.
Minimize access to data
Both software, hardware and third-party personnel must be very clearly controlled for authorization and traceability. Being able to determine in detail which provider has the ability to access a service or server is fundamental in an incident response to determine the access points. In addition, having this control allows to place effective alerts on a misuse of these permissions or attempts of lateral movements with these users, increasing the level of prevention and detection of threats.
Cyber Security in the supply chain is a challenge, but with a solid strategy and appropriate preventive measures, companies can significantly reduce their exposure to risk.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector




