CBOM: advanced cryptographic visibility for risk management and post-quantum readiness
Complete visibility into corporate cryptography takes a step forward with CBOMs—key elements for understanding and managing the cryptographic makeup of every asset. After exploring the cryptographic inventory, asset discovery, visibility for risk mitigation and crypto agility as an adaptation capability, we now take a deeper look into how Cryptographic Bills of Materials (CBOMs) make it possible to expose, validate and govern the cryptographic posture across the entire lifecycle of a system or product.
______
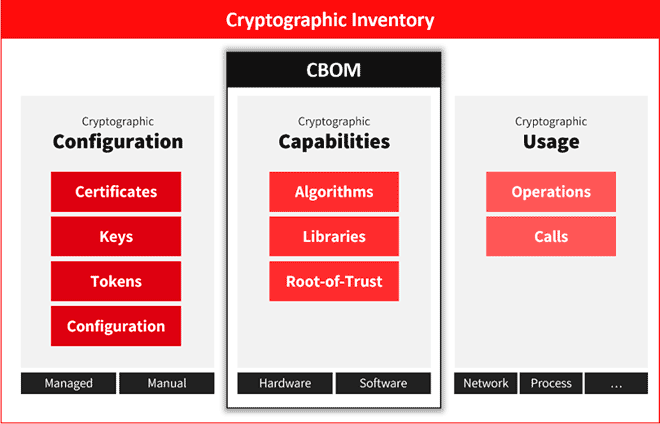
A CBOM is a machine-readable manifest that lists all cryptographic components and configurations embedded in a product, application, service or system. This includes algorithms, libraries, protocols, keys, certificates, verified stores and associated parameters present across the full software stack and infrastructure.
It is similar to an SBOM (Software Bill of Materials), but focuses exclusively on cryptography, making the cryptographic posture of an asset explicit for the purposes of security, compliance and supply chain assurance.
A CBOM is most effective when it is automatically generated and maintained, and linked to a broader cryptographic inventory to ensure full end-to-end visibility and control.
A CBOM makes a system’s cryptographic composition visible, searchable and verifiable.
What’s in a CBOM?
The core elements that make up a CBOM are crucial for understanding both its scope and its value in cryptographic security management. These components are essential for identifying and assessing the cryptographic posture of any technology asset.
- Algorithms and parameters such as asymmetric/symmetric schemes, key sizes, modes, hash/MAC functions, PRNGs, approved cipher suites and protocol versions (e.g. TLS, SSH, IPsec).
- Key material and certificates including key types and lifecycles, issuers, certificate chains, trust anchors, use of mTLS and custody details from KMS/HSM—at the right level for governance metadata.
- Cryptographic libraries and modules in use, their versions, FIPS or other validations, and dependencies on hardware roots of trust.
- Usage context—where and how cryptography is applied (data in transit, at rest, in use, signing and authentication), with links to business services and data criticality to enable risk-based prioritisation.
- Agility and PQC fields such as supported alternatives, migration paths, obsolescence indicators and exposure to quantum risk.
The value of a CBOM lies in its detail: algorithms, keys, modules, usage and post-quantum preparedness.
CBOM for complete cryptographic visibility
A CBOM describes the cryptographic composition of a specific asset or product and is typically exchanged along the supply chain. In contrast, a cryptographic inventory is a dynamic, enterprise-wide record that covers all cryptographic objects across all environments for operational and risk management purposes.
In practice, CBOMs are integrated and validated against the enterprise cryptographic inventory to enable consistent governance, remediation and reporting.
CBOMs enable faster vulnerability classification, compliance testing and third-party risk assessments by making cryptographic dependencies explicit and searchable.
They also support crypto agility and quantum readiness by linking specific components to risk scenarios, data sensitivity and regulatory obligations.
■ Regulators, authorities and industry bodies are raising expectations around cryptographic visibility. CBOMs provide evidence of standards alignment and best practice adoption, helping to meet compliance requirements.
Integrating CBOMs with the cryptographic inventory creates a unified view for governance, risk and compliance.
How to implement a CBOM?
To successfully implement a CBOM, a set of key steps must be taken to ensure alignment with enterprise security and compliance objectives. The main aspects to address in order to execute this process in a structured and comprehensive way include:
- Define a schema that aligns CBOM fields with the organisation’s risk models and frameworks.
- Automate generation via CI/CD, scanners, API collectors for KMS/PKI and telemetry.
- Govern with a trusted source that validates CBOMs against the cryptographic inventory.
- Operationalise by integrating CBOMs into vulnerability workflows, SOC/SIEM, change management and compliance processes.
- Plan for crypto agility and post-quantum cryptography (PQC) by including migration paths and deprecation timelines.
It is vital to recognise that cryptography is everywhere: complex, diverse and often invisible.
Photo by Cinthya González / Unsplash.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector