Cryptographic asset discovery: the prerequisite to inventory governance and Q-Day readiness
Knowing which cryptographic assets are deployed across the infrastructure is the first step toward effective governance. Following our previous post on cryptographic inventory and the post-quantum transition, we now take a deeper look at cryptographic asset discovery, the process that enables you to uncover what cryptography is actually in use, where it is, and under what conditions.
Without cryptographic asset discovery, there is no useful inventory; without visibility, governance is not possible.
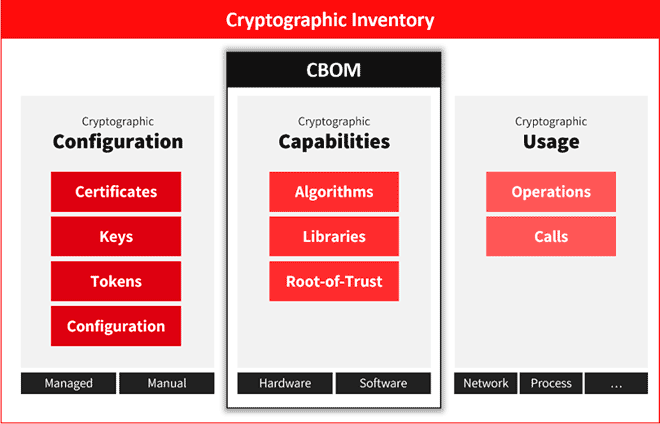
Cryptographic asset discovery is the systematic process of identifying, locating, and cataloging all cryptographic assets deployed across an organisation’s extended IT infrastructure. This comprehensive effort aims to answer key questions about the organisation’s cryptographic posture: What do I have? Where are the assets? How effective are they? How much trust can we place in our cryptographic processes? and What should I prioritise?
Cryptographic discovery in large-scale or legacy environments is often hindered by several structural and technical challenges:
- Heterogeneous sources: cryptographic assets (keys, certificates, algorithms) are distributed across applications, file systems, networks, hardware, Cloud environments, and legacy systems.
—Hard to locate and consolidate; require multiple detection methods. - Legacy system complexity: dynamic, multilayered environments combining legacy, cloud-based and third-party systems.
—Limited visibility; not designed for cryptographic transparency; risk of unmanaged or unknown assets. - Embedded cryptography in applications: cryptographic elements hidden within compiled or third-party applications.
—Complex integration and inventory processes; require specialised tools and techniques for detection.
■ Discovery and inventory management are complementary, interdependent processes that are essential to achieve effective cryptographic governance.
Cryptographic asset discovery and inventory management
The discovery phase is therefore the first step, focused on the identification and location of cryptographic assets, including software, network, operational, managed and hardware-based elements, to provide a clear view of cryptography implementation. It also enables the detection of potential vulnerabilities related to cryptographic assets.
In contrast, inventory management is a continuous, governance-driven process aimed at cataloguing, monitoring, and controlling the lifecycle of these assets to ensure accountability, traceability, and integrity.
When treated in isolation, discovery without inventory leads to asset drift and cryptographic blind spots, while inventory without continuous cryptographic asset discovery results in outdated and incomplete records. When effectively integrated, both processes enable visibility, control, and resilience across dynamic cryptographic ecosystems.
Discovery without inventory leaves blind spots; inventory without discovery leads to errors.
Specialised tools and automated solutions
The industry has recognised the need to develop specialised and automated solutions, leading to the emergence of tools dedicated to cryptographic discovery. These tools fall into several categories:
- PKI scanners: tools designed to identify X.509 certificates and certification authorities across networks.
- API trackers: capable of interacting with key management systems and cloud services to enumerate cryptographic assets.
- Network probes: identify the cryptographic capabilities exposed by various endpoints, including SSH, TLS, IPsec, and other protocols.
⚠️ It’s important to consider the limitations of some tools due to restricted coverage or compatibility, which may create blind spots in cryptographic visibility.
Why visibility and governance of cryptographic inventory matter
Cryptographic discovery must evolve into a continuous process rather than a periodic audit. The urgency of the quantum timeline places added pressure on organisations to maintain ongoing oversight.
The arrival of Q-Day, the moment when cryptographically relevant quantum computers (CRQC) become a reality, demands continuous visibility over cryptographic infrastructure, with no room for vulnerability windows.
In this context, governance becomes a critical success factor in cryptographic discovery, and its effectiveness relies on the active collaboration of all stakeholders.
Cryptography has cross-cutting impact across the organisation, which requires a clearly accountable role to oversee its management and ensure effective governance.
Establishing a multidisciplinary team and involving business teams to define cryptography use cases and acceptable risk levels are key conditions for success.
The CISO and security leads play a central role. In large organisations, this responsibility typically falls under the CIO or CISO. A clearly defined cryptography owner must oversee all cryptographic functions and their associated inventory. Cryptography affects the organisation as a whole and must be centrally managed to enable effective governance.
■ Successfully implementing cryptographic discovery programmes requires a holistic understanding of both technical and organisational challenges. This allow organisations to build resilient cryptographic infrastructures, secured against today’s vulnerabilities and tomorrow’s quantum threats.
Image: asier_relampagoestudio on Freepik.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector