CitrixBleed, a vulnerability in massive exploitation phase
Introduction
NetScaler published a security bulletin on October 10 with a patch for a vulnerability detected in Citrix ADC (Application Controller) and Citrix Gateway for on premises managed systems.
The vulnerability with the CVE-2023-4966 identifier is rated as a critical risk, with a CVSS score of 9.4 out of 10. It has been dubbed, by the security community, as CitrixBleed, in honor of the well-known HeartBleed vulnerability that affected, back in 2014, countless organizations and OpenSSL implementations.
This vulnerability has generated a great deal of concern within the community due to its potential to allow attacks on critical systems. Recommendations for patching and mitigation measures have come (unsurprisingly) from NetScaler itself, as well as from organizations such as the U.S. Cybersecurity Agency (CISA).
We know that this vulnerability is in a massive exploitation phase with major ransonware groups like LockBit using this gateway to attack major organizations internationally. Let's find out what CitrixBleed is, what kind of attack it can perform, the impact it can have and some recommendations on how to mitigate your risk.
What is CitrixBleed?
CitrixBleed is a vulnerability affecting Citrix ADC and Gateway on premises products. It is characterized by allowing an attacker to gain unauthorized access to sensitive data, such as user session tokens.
In a nutshell, the vulnerability allows unauthorized access to memory through a simple, specially crafted request. If session tokens are inside that memory, an attacker could bypass any kind of multi-factor protection to gain access to systems with a manipulated replay attack. This can be achieved with a simple Chrome browser extension by representing that it doesn't take much, technically speaking.
A very dangerous feature of this vulnerability, and one that resembles what was found in HeartBleed, is that the manipulated attack leaves no logs in the logs, which makes it very difficult to detect.
Several security companies have identified massive attempts to exploit this vulnerability with over 100 unique IPs probing the network for unpatched systems and climbing.
The Impact of CitrixBleed
The impact of CitrixBleed is significant due to the popularity of Citrix products in large enterprise environments, mostly in the United States, but not only there as we can see in the following image:
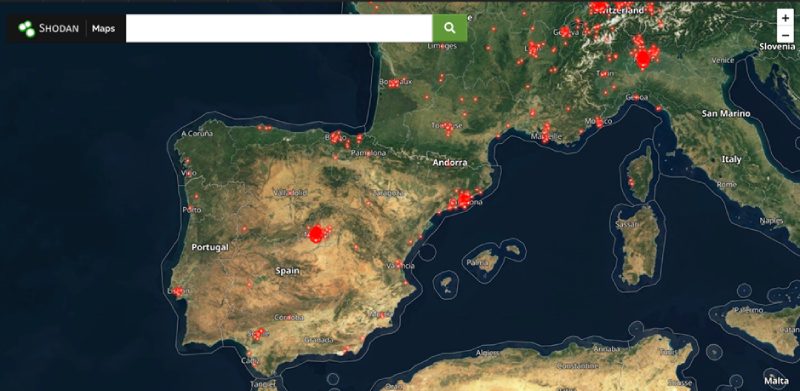 Locations with potentially affected Citrix products
Locations with potentially affected Citrix products
◾The above image shows locations with Citrix ADC and Gateway products, it is not filtered whether they are vulnerable or if they have already been patched.
Below is a sample of companies attacked using this vulnerability:
- Allen & Overy - One of the largest law firms in the world.
- ICBC - Industrial and Commercial Bank of China: The largest bank in the world. Its American subsidiary has been affected.
- DP World - Major Australian high-volume logistics company.
- Boeing.
As is often the case, this is only the tip of the iceberg. Using scanners such as shodan.io, we know that there are still more than 5,000 unpatched systems today. Once ransomware groups industrialize the vulnerability and weaponize it, many organizations will be exposed and, unfortunately, attacked for the usual ransom. It is clear, despite all odds, that this vulnerability will be one of the most important vulnerabilities of 2023..
Mitigation measures and recommendations
First of all, detect whether our organization has affected assets, patch the vulnerable systems following Netscaler's recommendations and reboot the systems.
That, by itself, will not eliminate the risk of improper authentication if attackers already have session tokens, so close all open connections and invalidate existing session tokens.
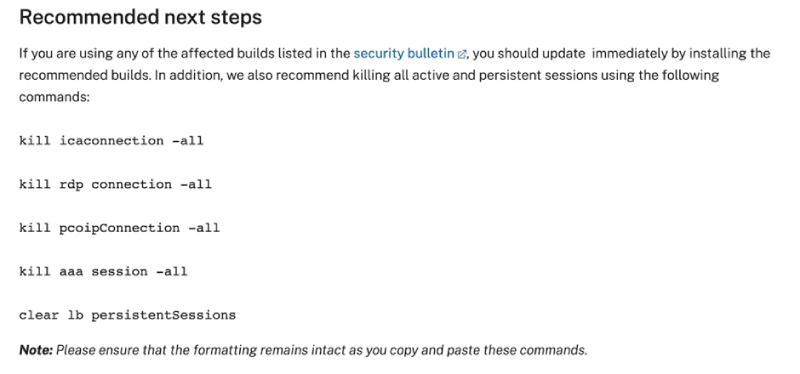 A screenshot taken from the NetScaler recommendations.
A screenshot taken from the NetScaler recommendations.
Should we have assets of the identified vulnerable products, an in-depth investigation using the IoCs published for example by CISA is required to ensure that the system has not been compromised. If evidence of access is found, a global examination of the internal network and systems must be carried out to rule out persistence mechanisms.
Conclusions
The conclusions regarding this type of vulnerability are not new but should not be ignored.
- Large corporations, or at least their security teams, must ensure that they have the capacity to provide basic Cyber Security services in a timely manner. A vulnerability as critical as CitrixBleed, must be patchable in less than 24-48 hours or it should make us reflect on whether our choice of systems or security capabilities or processes are adequate. The siren songs of the new next big thing are very tempting, but critical vulnerabilities must override all priorities at key moments.
- Manufacturers of relevant software products in large corporations and critical infrastructures must step forward to integrate security into their products natively and by design, as well as respond in a timely manner to bugs found by facilitating patching where possible. Applying a patch-on-patch policy is not sustainable for anyone in the long term.
CitrixBleed is yet another important reminder of the need to remain vigilant in the Cyber Security arena. Organizations must be proactive in applying security patches, monitoring their systems, and continuing cyber security education to protect against such vulnerabilities.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector


.jpg)



