From technical data to strategic action: effective vulnerability prioritization
Continuing with vulnerability management, one of the key challenges for organizations—regardless of their size—is how to prioritize the remediation of reports and how to link them directly to the reported level of risk.
To do this, it’s important to understand that the risk ratings provided in pentesting or vulnerability analysis reports, as discussed in our previous article, are based purely on a technical Cyber Security analysis using the CVSS (Common Vulnerability Scoring System). This tool classifies vulnerabilities as low, medium, high or critical based on their impact on Cyber Security pillars and the complexity of their exploitation.
Therefore, reports are usually accompanied by CVEs (Common Vulnerabilities and Exposures), which group known vulnerabilities. However, this rating is generic and does not take into account factors like the likelihood of exploitation, the existence of an exploit, or business-specific data on the asset’s importance.
There are, however, two other tools that are often overlooked in prioritization analyses and can be extremely helpful in making risk-based decisions:
- EPSS (Exploit Prediction Scoring System), which aims to score the probability that a vulnerability will be exploited.
- KEV (Known Exploited Vulnerabilities), a catalog that documents known exploits, who developed them, and which vulnerabilities they target.
How do these tools interact?
Reports always support findings with CVEs. From this baseline, information should be organized using CVSS scoring, which helps us identify the technical severity of each vulnerability and determine the attack vectors that should be analyzed.
Once that initial categorization is complete, two key elements must be considered: first, whether the vulnerability is currently being exploited, regardless of its CVSS rating. Second, the likelihood of future exploitation, based on threat intelligence analyses.
These capabilities are provided by KEV and EPSS, respectively. So, using the vulnerability identifier, we search KEV to identify the highest-priority items—regardless of the CVSS risk level. Then, with the remaining vulnerabilities, we sort them according to CVSS and check their EPSS score to estimate the probability of future exploitation and plan a proactive remediation strategy.
Practical example
Let’s suppose we’re using a business messaging service such as The TeleMessage, and our automated vulnerability management system detects and reports CVE-2025-48927, which has a CVSS v3.1 score of 5.3—i.e., a medium severity level.
CVSS provides the technical data on the attack vectors, which we can review using the basic calculator from version 4.0, the most up-to-date version.
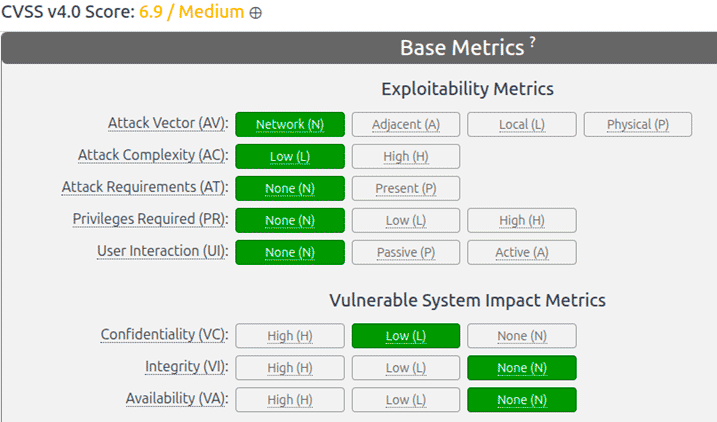
It shows that the attack is conducted over the network, does not require privileges or user interaction, but its impact is limited to confidentiality and is low.
Based on this data, remediation might be considered a low priority. However, this decision should be guided by threat intelligence data, starting with KEV reports and, if not listed there, then EPSS.
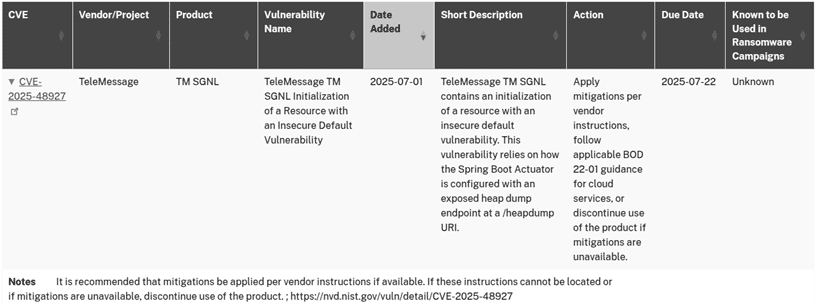
When we search KEV, we find that this vulnerability is actively being exploited in conjunction with two other vulnerabilities that have not been patched by the vendor. Therefore, additional control measures must be implemented.
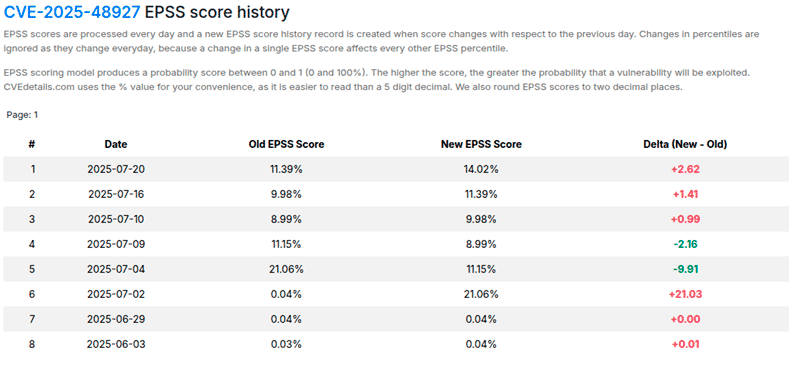
If it hadn’t been listed in KEV, we would refer to the EPSS score provided by the tool, where we can see the scoring history and observe how the probability of exploitation has increased over time.
This management process is not simple, but there are online tools that make it easier—for example, CVEDetails. Using the analysis from the report we examined, we can find here the information.
On the other hand, it’s always important to remember that this is a technical analysis, but final prioritization should be based on: the criticality of the analyzed asset or service, its exposure to external networks or third parties, and the effort required to remediate or mitigate the impact.
Imagen: Chris Yang / Unsplash.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector





