'Living off the land': how attackers use your own tools to their advantage
One of the principles of cybercriminals (and on the side of the good guys, the pentesters or read team) is that both the exploits and tools used are detected by defense systems, both networked and local.
Although they are not infallible systems, they can ruin the job if they catch suspicious activity and raise an alarm. As a pentester, it hurts your pride to get an email or a call saying you've been caught in the act; but it's part of the game.
At the end of the life cycle of malware, exploits and other malicious elements there is always the "police" token in the form of a signature, rule or pattern that serves to detect it and raise alarms. Thus, malware in general has an expiration date, sooner or later it will be hunted down, and each use is a ticket to end up at the castle gates or in the crocodile pit.
Malware in general has an expiration date: each use is a ticket to end up in the crocodile pit.
Given this situation, someone thought that why bother writing a complex malware with rootkit functions and end up being discovered a few days later. After all, what is such malware going to do, search for information on the computer and exfiltrate it? steal domain administrator account tokens? And ended up answering: why not use the tools that are already in the system?
On the one hand, they are all whitelisted and on the other hand you save a good handful of hours developing an original piece that is going to end up x-rayed on a yara ruler.
What are LOLBins
These types of techniques were given a name: "Living off the land" (LOLBins).
It is the military equivalent of being released alone in the middle of a mountain to make a living and get to a specific point dozens of kilometers away. A frightening but enriching test, which teaches you to achieve a goal with few or no resources and no tools other than your own hands.
LOLBins techniques are a goldmine for cybercriminals, but it is also a fertile area for pentesters and researchers.
Something so obvious and simple a priori, has become a lode for cybercriminals, but also a fertile area for pentesters and researchers who use this type of techniques and tools ethically but with the opposite intention.
In light of this reality, lists of this type of tools have been appearing for some time now to classify them in terms of use, location in systems, techniques used, etc. Authentic catalogs to consult and use them depending on the context in which we find ourselves.
Let's take a look at a handful of them, many of them spin-offs of the original project and that choose to specialize in a particular operating system or a specific area.
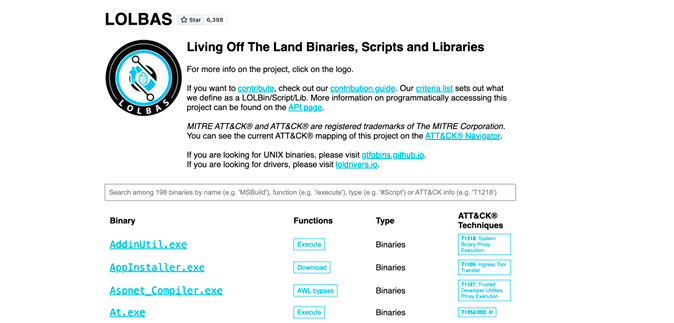
LOLBAS (Living off the land binaries)
It is arguably the original project. It accumulates about 200 entries between binaries, scripts, and libraries. It also has a unique virtue and that is that it maps each entry with its corresponding entry in the ATT&CK framework; widely used in advanced threat modeling.
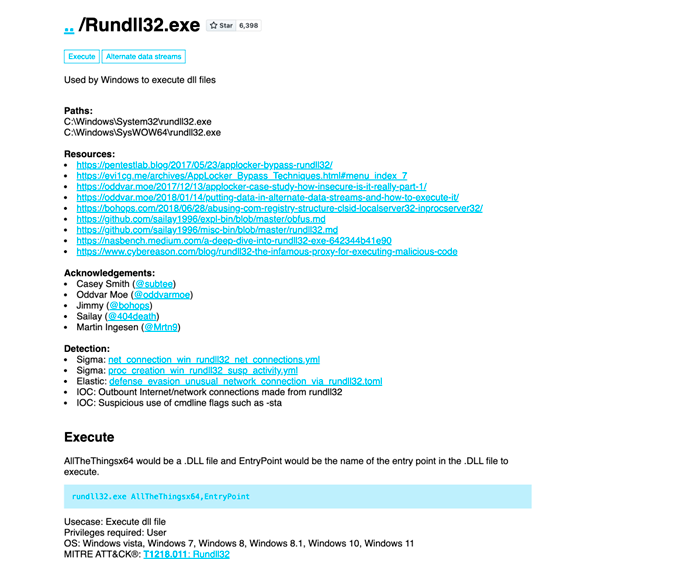
One of the popular entries is Rundll32.exe, used to execute DLL functions (libraries), which makes them practically executable; one of the most used and omnipresent (and all-powerful) in Microsoft Windows operating systems along with the king of LOLBins: Powershell.
For each entry we have additional information about its use and in which APT operations it has been used; together with ATT&CK we have a very instructive overview.
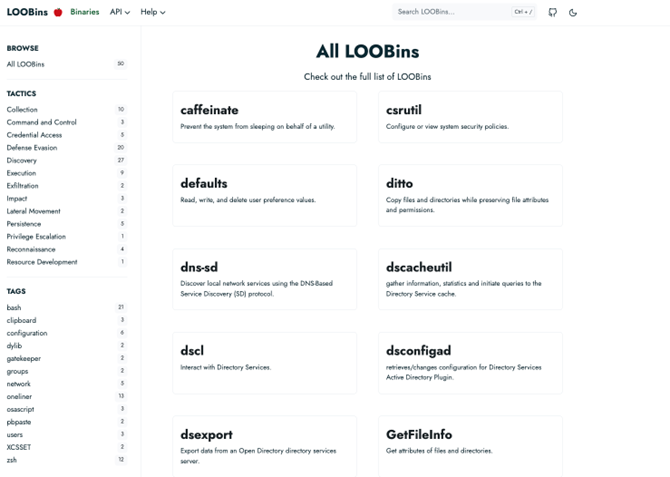
All of this started with Microsoft Windows systems, but when it was seen to be productive, the same scheme was transferred to other systems. For example, the LOOBins (Living off the orchard) project, devoted to the Apple system: MacOS.
It is basically the same idea as the original but transferred to the operating system of the Cupertino company.
We even found a classification by the tactic to be employed (once again, ATT&CK).
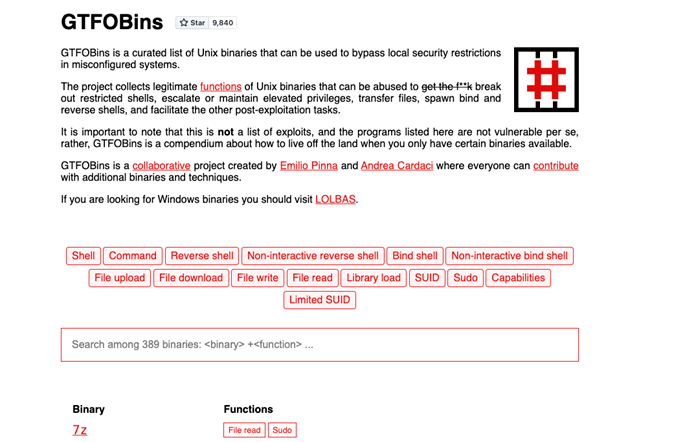
GTFOBins
Same scheme but focused on UNIX systems with Linux in particular. In a way, as MacOS is a UNIX derivative, it would also be useful for that system, in addition to the one we have seen above.
It is surprising that with almost 400 detailed tools (UNIX systems are rich in this aspect), it is possible to take advantage of such unlikely tools for this aspect as "bc", the classic UNIX command line calculator.

These are the main and most important ones, but it doesn't end there. The idea of listing items that pass under the radar of EDR (Endpoint Detection and Response) systems has flourished to such an extent that we no longer only have sites dedicated to binaries, but to domains that are usually whitelisted and known not to be blocked.
They also often allow the uploading of files or text that is then used as a download point or, on the contrary, to exfiltrate information.
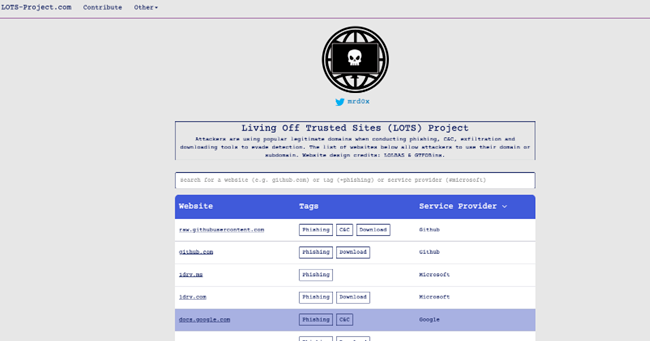 An example is https://lots-project.com (Living off Trusted Sites):
An example is https://lots-project.com (Living off Trusted Sites):
A clear example is docs.google.com or github, services widely used for phishing schemes, malware, etc.
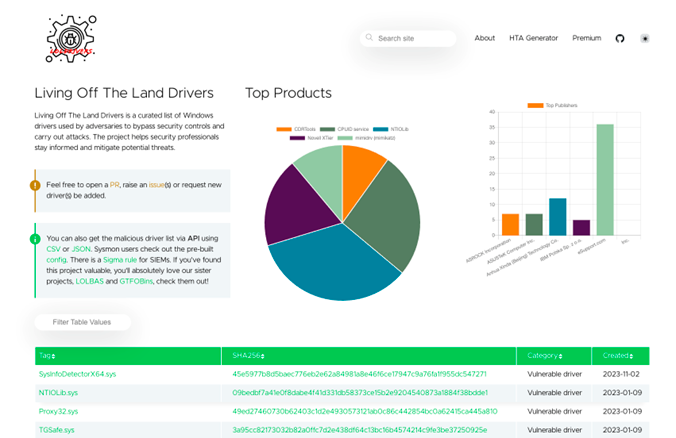 Another with file extensions (!), https://filesec.io o drivers en https://www.loldrivers.io
Another with file extensions (!), https://filesec.io o drivers en https://www.loldrivers.io
We left out a few, such as APIs: https://malapi.io or cheat sheets of code snippets that can be used in Windows pentesting and Active Directory in particular: https://wadcoms.github.io.
Surprisingly, there is an arsenal available for an unauthorized user wandering around in the systems themselves. As we can see, it doesn't take complex, latest tools to achieve results. We have a vast repertoire of techniques at our disposal with the ingenuity and knowledge that these types of compendiums possess.
It is the maxim of doing a lot with practically nothing:
Something similar to what MacGyver would do with his legendary little Swiss Army Knife, but in a digital version.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector

.jpg)



