Malware distributed during fraudulent job interviews
Introduction
A social engineering campaign, called DEV#POPPER, has recently been detected using fake npm packages under the guise of job offers to trick developers into downloading a Python backdoor.
The attack chain starts with fraudulent interviews, asking developers to download malware disguised as legitimate software. In this case, it is a ZIP archive hosted on GitHub that contains a seemingly harmless npm module, but actually hosts a malicious JavaScript file called BeaverTail and a Python backdoor called InvisibleFerret.
As reported in an initial analysis by Securonix, this activity has been linked to North Korean threat actors who continue to refine their arsenal of attacks, constantly updating their techniques and operational capabilities.
In this post we will review, at a high level, the attack chain, and capabilities, ending with some recommendations and conclusions.
Are you a developer looking for a job? we have "good news/bad news"
In a high-demand environment such as software development, the practice of including technical tests during the selection process to evaluate the capabilities of candidates has become established.
Leaving aside the appropriateness or not of this alternative (in my view not very effective, to demonstrate the technical capability of a potential new employee), the reality is that it is a fairly widespread practice and that, from the point of view of the attacker, it generates the ideal stress situation in the candidate. The candidate is likely to act in a less than cautious and complacent manner since an important step in his professional life is at stake.
Conducting technical tests in job interviews can create a stressful environment for candidates, who may act recklessly and complacently as they feel their professional future is at stake.
Urgency and trust in a third party in order not to lose the open opportunity are classic mechanisms of psychological manipulation used in social engineering campaigns and which seek typical human psychological vulnerabilities as deep-rooted as trust, fear, or the simple desire to be useful.
Attack chain
The following is a simplified image of the attack chain:
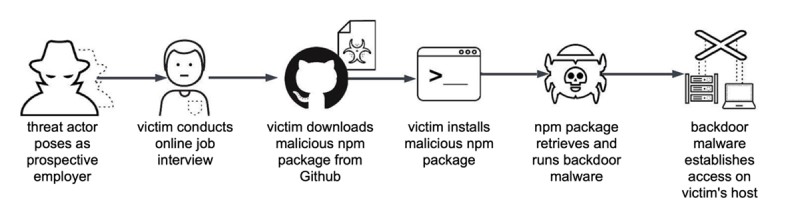 Image extracted from the analysis of Palo Alto.
Image extracted from the analysis of Palo Alto.
In short, attackers set up fake job interviews for developers, pretending to be legitimate job interviewers. During these fraudulent interviews, developers are often asked to perform tasks that involve downloading and running software from sources that appear legitimate, such as GitHub. The software contains a malicious Node JS payload that, once executed, compromises the developer's system.
In the case analyzed by Securonix, the attack trigger is hidden in a javascript file, called ImageDetails.js, in the backend of the job candidate's supposed practical exercise. Apparently simple code that uses Mongoose, a well-known Mongoose, atabase object modeling package in Node JS. However, hidden in an abnormally long line and after a comment is the initial payload obfuscated by base64 encoding, variable substitution and other common techniques.
In the following image we can see an animation of the hiding of the initial code:
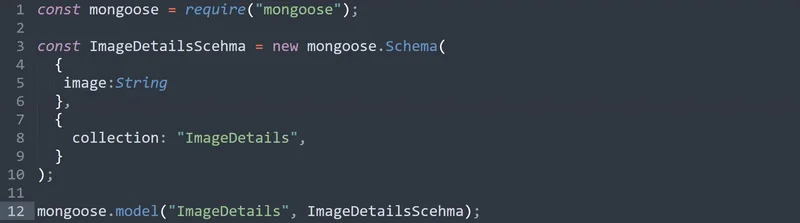
When the victim then installs this npm (Node Package Manager) package, the attack is triggered, which consists of four phases detailed in the securonix analysis, which we invite all those who are more technically curious to read.
Attack capabilities
The attack consists of two main components: The installation of an information-stealing malware and a backdoor on the victim's machine.
As an information extractor on the victim user's machine, data such as the following is tracked and sent to the attacker's server:
- Cryptocurrency wallets and payment method information found in the victim's browser.
- Data for fingerprinting.
- Name of the victim's host.
- Type and version of the Operating System.
- Login user name.
- Etc.
The second part of the attack is the most damaging, installing a remote access trojan (usually known as RAT, Remote Access Trojan), which in turn gives the attacker the following capabilities once the exploit has been initiated:
- Persistence: Network connection and session creation: Used for persistent connections: This establishes persistent TCP connections, including structuring and sending data in JSON format.
- File system access: Contains functions to traverse directories and filter files based on specific extensions and directories to exclude. It can also locate and potentially exfiltrate files that do not meet certain criteria, such as file size and extension.
- Remote command execution: The script contains several functions that allow the execution of system shell commands and scripts. This includes browsing the file system and executing shell commands. Included is the ability to download the popular AnyDesk client to gain additional control of the victim's machine.
- Exfiltration of information: the Python script is able to send files to a remote FTP server with the ability to filter files based on their extension. Other functions exist to help automate this process by collecting data from various user directories such as Documents and Downloads.
- Clipboard and keystroke logging: The script includes capabilities to monitor and exfiltrate clipboard contents and keylogger.
Conclusions
Social engineering is, and will continue to be, the main attack vector for breaching security from a human perspective. The particular case of using uncomfortable, urgent or stressful environments for victims, such as a job interview, fits what cybercriminals are looking for to maximize the likelihood of a successful attack.
This method is effective because it exploits the developer's professional commitment and trust in the job application process, where refusal to perform the interviewer's actions could compromise the job opportunity.
Attackers tailor their approach to appear as credible as possible, often by mimicking real companies and replicating real interview processes. This appearance of professionalism and legitimacy lulls the interviewee into a false sense of security, making it easier to deploy malware without arousing suspicion.
This type of attack is not new; Palo Alto unit 42 analyzed previous attacks during job interviews in late 2023 and even in 2022.
The protection mechanisms against these threats could be summarized as follows:
- Work computers should not be used for personal activities, such as job interviews.
- In general, no one should install unknown files from unverified sources on their computers.
- GitHub accounts that contain a single repository with few or no updates should be distrusted. It is becoming increasingly difficult to differentiate between potential fraudulent accounts with the ability to generate networks of "controlled" users to grant themselves activity by attackers.
Perhaps the most important and effective thing, in these cases, is to verify, slowly, the existence and legitimacy of the companies offering job interviews, and also to confirm that the interviewers really work for the companies they claim to represent.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector





