Your company after a Cyber Security assessment: What now?
Imagine that your company, an SME or a medium-sized enterprise like many others, has just received the results of a pentest or security assessment. A shiver runs down your spine as you read the report: the number of vulnerabilities detected is overwhelming. Where to start? What measures to take? How to protect your business from cyberattacks?
Uncertainty and fear are common reactions. Feeling lost in the face of a security report full of technical terms and potential threats is natural. But you are not alone. TTECH is your cyber security expert and we're here to help you navigate this sea of information and make the right decisions to protect your business.
Common challenges for small and medium businesses
Businesses, especially medium and small businesses, often lack the resources and knowledge needed to effectively manage IT security. This is where the implementation of a service specialized in accompanying risk mitigation becomes crucial to shield against cyberattacks, system vulnerabilities or implementation failures.
What are the most common scenarios?
The flood of vulnerabilities
The report reveals a plethora of vulnerabilities, from flaws in software configuration to weaknesses in access controls. You feel overwhelmed and don't know where to start.
Lack of resources
The assessment has revealed the need to implement additional security measures, but your company does not have the human or financial resources to carry them out.
Lack of technical knowledge
The technical terms and recommendations in the report are difficult to understand. You need help to understand what it all means and how to implement it.
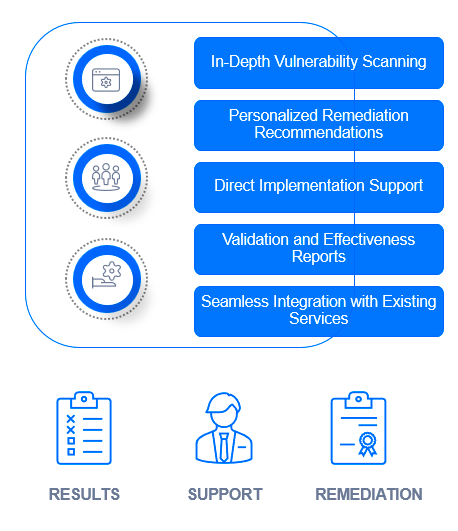
How does a risk mitigation support service work?
Operational risk mitigation involves minimizing the chances of security breaches by implementing effective and validated remediation, supported by expert operational risk management support.
This allows companies to respond quickly to emerging threats, adapting nimbly to new risks discovered during assessments such as pentesting, Red Team, DFIR or Vulnerability Scanning.
1. Triage and Prioritization
- Recent security assessments are reviewed, and additional discovery exercises are conducted if necessary.
- This analysis focuses on three critical elements: technology, people and processes.
- Based on your risk analysis, the value offered by each countermeasure and the cost of implementation, prioritizing security improvements.
2. Security improvement planning
Leveraging the insights from the first phase, you create a structured improvement plan to reduce your risk exposure over three timeframes:
- Short term: Focuses on addressing urgent vulnerabilities with quick fixes for the most critical threats.
- Medium term: Recommendations are made to improve and secure your organization over a designated period.
- Long term: Explores more complex mitigation strategies for long-term protection against cyber risks and strategic security initiatives.
3. Implementation and Improvement
Cyber security specialists work collaboratively with business teams to implement the improvement plan in a modular way.
- Quick fixes for vulnerabilities are top priority.
- Long-term risk mitigation strategies are planned with clearly defined milestones to track progress.
- A scalable and skilled team enables simultaneous execution of multiple high-impact projects. Each step is measured and validated to ensure demonstrable improvements.
Can it help me if I don't have the knowledge to implement the necessary measures?
Security audits, post-incident reports, penetration tests and other system analyses reveal valuable information about system health. TTECH helps prioritize, advise and guide you in resolving these diagnostics to understand your overall risk exposure and develop a robust and sustainable security improvement plan.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector





