TIBER-EU and TLPT: advanced cyber resilience testing for the financial sector under the DORA framework
Cyber resilience in the financial sector no longer relies on traditional audits, but on advanced testing methodologies such as TIBER-EU and Threat-Led Penetration Testing (TLPT), which simulate real-world attacks based on threat intelligence to uncover technical, human and strategic vulnerabilities.
Under the framework of DORA and the guidelines of the European Central Bank, these methodologies have become a regulatory and operational standard that assesses institutions’ actual ability to detect, withstand and recover from sophisticated adversaries, thereby strengthening critical infrastructures and trust across the entire financial ecosystem.
______
It was past midnight when the Security Operations Center (SOC) monitors and the Computer Security Incident Response Team (CSIRT) screens began to flicker. Nothing seemed out of the ordinary: servers were responding, traffic was steady, and no alarms were triggered. But in the shadows of the digital landscape, a silent adversary was moving laterally, collecting credentials, accessing critical applications, and strategically positioning themselves to compromise the bank’s essential functions.
Hours later, after the attacker had carefully withdrawn, the bank received a confidential report: it hadn’t been a cybercriminal, but an ethical red team simulating real-world techniques under the framework developed by the European Central Bank (ECB) — the Threat Intelligence-Based Ethical Red Teaming (TIBER-EU) — integrating Threat-Led Penetration Testing (TLPT) and combining CBEST threat intelligence.
The exercise didn’t just reveal technical flaws — it also exposed human, strategic, and structural weaknesses. More than a simulation, it was a real shake-up for the organisation’s cyber resilience model.
Advanced simulations and regulation: the new standard in cyber resilience testing
With the rapid expansion of financial systems, which are increasingly interconnected and exposed to sophisticated cyber threats, traditional cybersecurity assessments are struggling to address systemic vulnerabilities.
This is why, through the implementation of the Digital Operational Resilience Act (DORA), TLPTs have gone from being a voluntary practice to a mandatory requirement for certain financial entities — making technical competence in this area essential for cybersecurity professionals.
TLPTs are not just a compliance checkbox — they are a strategic capability that tests an organisation’s true readiness in realistic, high-impact scenarios.
TIBER-EU guides red teams in carrying out testing in a controlled, customised and intelligence-led way, focused on the entity’s critical or important functions (CIFs) and the underlying systems that support them — namely people, processes and technologies. It imitates real-life adversary tactics, techniques and procedures (TTPs), referencing the MITRE ATT&CK matrix to align with current threat actor capabilities.
Integrating threat intelligence into test scenarios ensures that red teams replicate current adversary tactics — making the results more relevant and actionable.
Key phases and best practices in executing TIBER-EU
Beyond assessment, the framework also supports the strengthening and preparation of protection, detection and response capabilities — meaning it’s not a pass/fail exercise, but rather a continuous improvement process.
The TIBER-EU testing process consists of three mandatory phases: preparation, testing and closure.
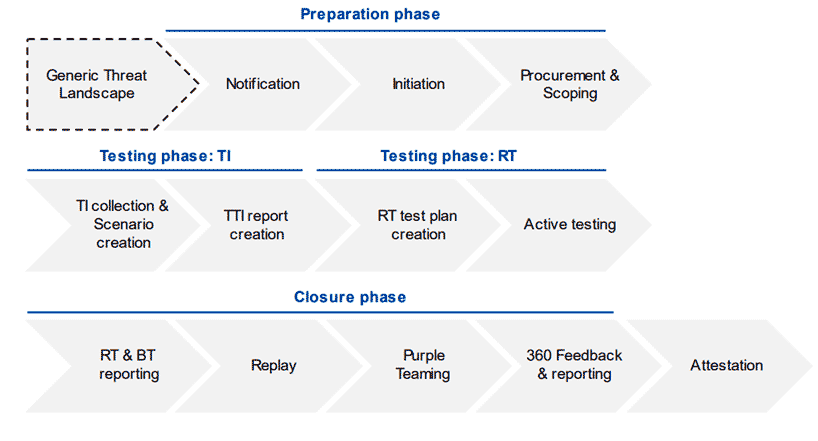 Source: TIBER-EU Framework.
Source: TIBER-EU Framework.
- Preparation phase (up to 6 months): The TIBER-EU test begins when a TIBER authority notifies an entity of the upcoming test, either voluntarily or due to regulatory requirements like DORA. A test manager (TM) is assigned and the entity forms a control team (CT) to oversee the process. Key steps include defining the critical or important functions (CIFs), setting attack goals (“flags”), and selecting external providers: a Threat Intelligence Provider (TIP) and Red Team Testers (RTT).
—The scope and focus are formalised in the Scope Specification Document (SSD), and the test officially begins with a joint kickoff meeting. - Testing phase (minimum 12 weeks): This phase involves threat intelligence gathering and the red team simulation. Over 4–6 weeks, the TIP develops tailored attack scenarios in the Targeted Threat Intelligence Report (TTIR). Then, the RTT prepares a Red Team Test Plan (RTTP) and executes stealth attacks over a minimum of 12 weeks to reach the agreed flags without alerting the blue team.
—The CT and TM are kept informed throughout to ensure coordination and oversight. - Closure phase (up to 18+ weeks): After the test, the RTT drafts the Red Team Test Report (RTTR), while the blue team responds with its own Blue Team Test Report (BTTR). A replay exercise and purple team session follow to enhance understanding and resilience. Stakeholders take part in a 360° feedback session, and the entity prepares a Test Summary Report (TSR) and a remediation plan.
—Once approved by the TM, the TIBER authority issues a certificate confirming compliance with the TIBER-EU framework — enabling mutual recognition of the test results.
Strategic balance and continuous strengthening of cyber resilience
Despite the complex workflows required for deployment and execution, clear guidelines have been established for the procurement and onboarding of threat intelligence providers, with due diligence processes in place to ensure the chosen vendor meets all defined criteria.
Effective implementation of threat-based penetration testing depends on a balance between technical rigour and operational pragmatism — ensuring meaningful outcomes without disrupting systems or breaching compliance. This focus on continuous improvement and collaboration is key to evolving cybersecurity capabilities to counter emerging threats.
Collaboration between red, blue and purple teams fosters a shared learning culture, where detection gaps become opportunities to build resilience.
Looking ahead, these methodologies will continue adapting to new technologies and regulatory demands — reinforcing the need for professionals skilled in both cyber offence and defence, while remaining aligned with governance and risk frameworks. This framework plays a critical role in strengthening the cyber resilience of critical financial infrastructures across the EU, providing a reliable benchmark for regulators and the wider financial ecosystem.
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector





